Nmap工具的使用
NMAP 可用于:
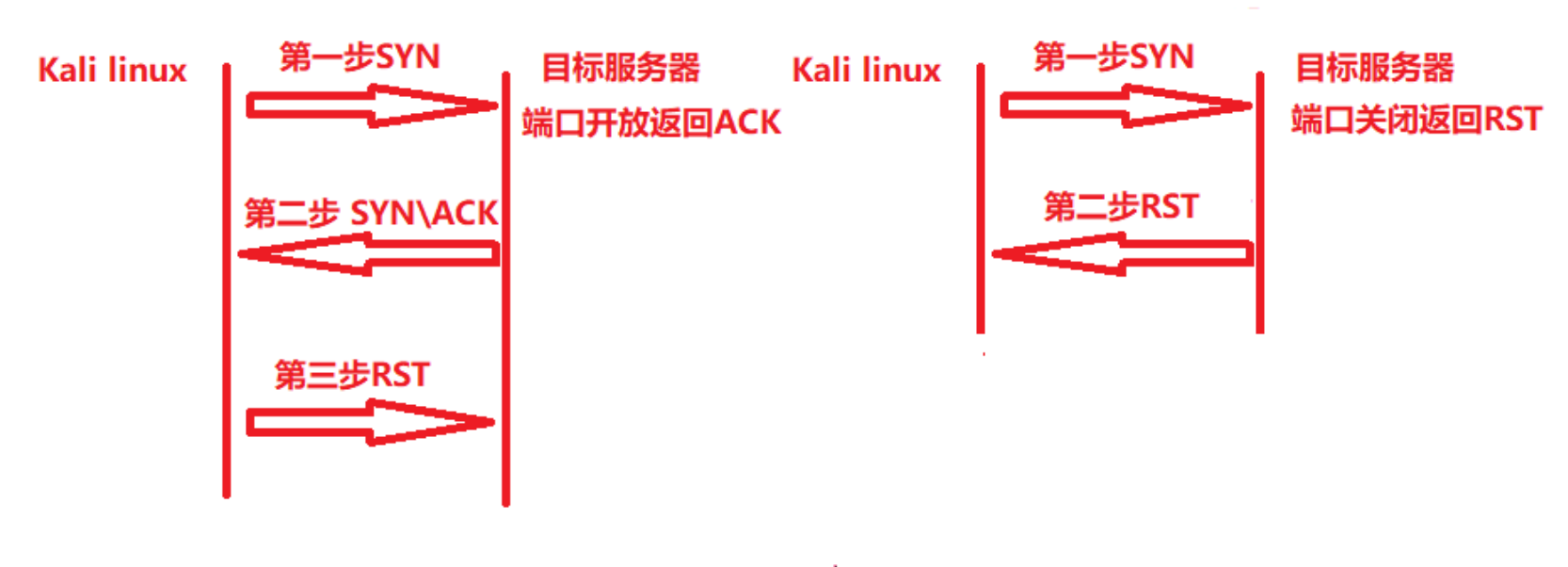
1.检测活在网络上的主机(主机发现)
2.检测主机上开放的端口(端口发现或枚举)
3.检测到相应的端口(服务发现)的软件和版本
4.检测操作系统,硬件地址,以及软件版本
5.检测脆弱性的漏洞(Nmap 的脚本)
使用:
1.默认情况下,Nmap 会扫描 1000 个最有可能开放的 TCP 端口。(也可以对一个网段进行扫描:192.168.1.0/24)
meng@mengs-MacBook-Air ~ % nmap 49.232.106.183
Starting Nmap 7.92 ( https://nmap.org ) at 2022-01-19 13:50 CST
Nmap scan report for 49.232.106.183
Host is up (0.028s latency).
Not shown: 991 closed tcp ports (conn-refused)
PORT STATE SERVICE
22/tcp open ssh
80/tcp open http
135/tcp filtered msrpc
139/tcp filtered netbios-ssn
445/tcp filtered microsoft-ds
593/tcp filtered http-rpc-epmap
3306/tcp open mysql
4444/tcp filtered krb524
5003/tcp open filemaker
Nmap done: 1 IP address (1 host up) scanned in 7.03 seconds
2.判断操作系统
meng@mengs-MacBook-Air ~ % sudo nmap -sS -O 49.232.106.183
Starting Nmap 7.92 ( https://nmap.org ) at 2022-01-19 14:30 CST
Nmap scan report for 49.232.106.183
Host is up (0.027s latency).
Not shown: 991 closed tcp ports (reset)
PORT STATE SERVICE
22/tcp open ssh
80/tcp open http
135/tcp filtered msrpc
139/tcp filtered netbios-ssn
445/tcp filtered microsoft-ds
593/tcp filtered http-rpc-epmap
3306/tcp open mysql
4444/tcp filtered krb524
5003/tcp open filemaker
Device type: general purpose
Running (JUST GUESSING): Linux 3.X|4.X (87%)
OS CPE: cpe:/o:linux:linux_kernel:3 cpe:/o:linux:linux_kernel:4.4
Aggressive OS guesses: Linux 3.10 - 3.12 (87%), Linux 4.4 (87%), Linux 4.9 (86%), Linux 4.0 (86%)
No exact OS matches for host (test conditions non-ideal).
Network Distance: -186 hops
OS detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 6.26 seconds
3.对一个ip文本进行扫描
nmap -iL ip.txt
4.nmap脚本的使用
(1)nmap --script=vulne 49.232.106.183 (漏洞扫描)
(2)nmap --script=brute 49.232.106.183 (暴力破解)
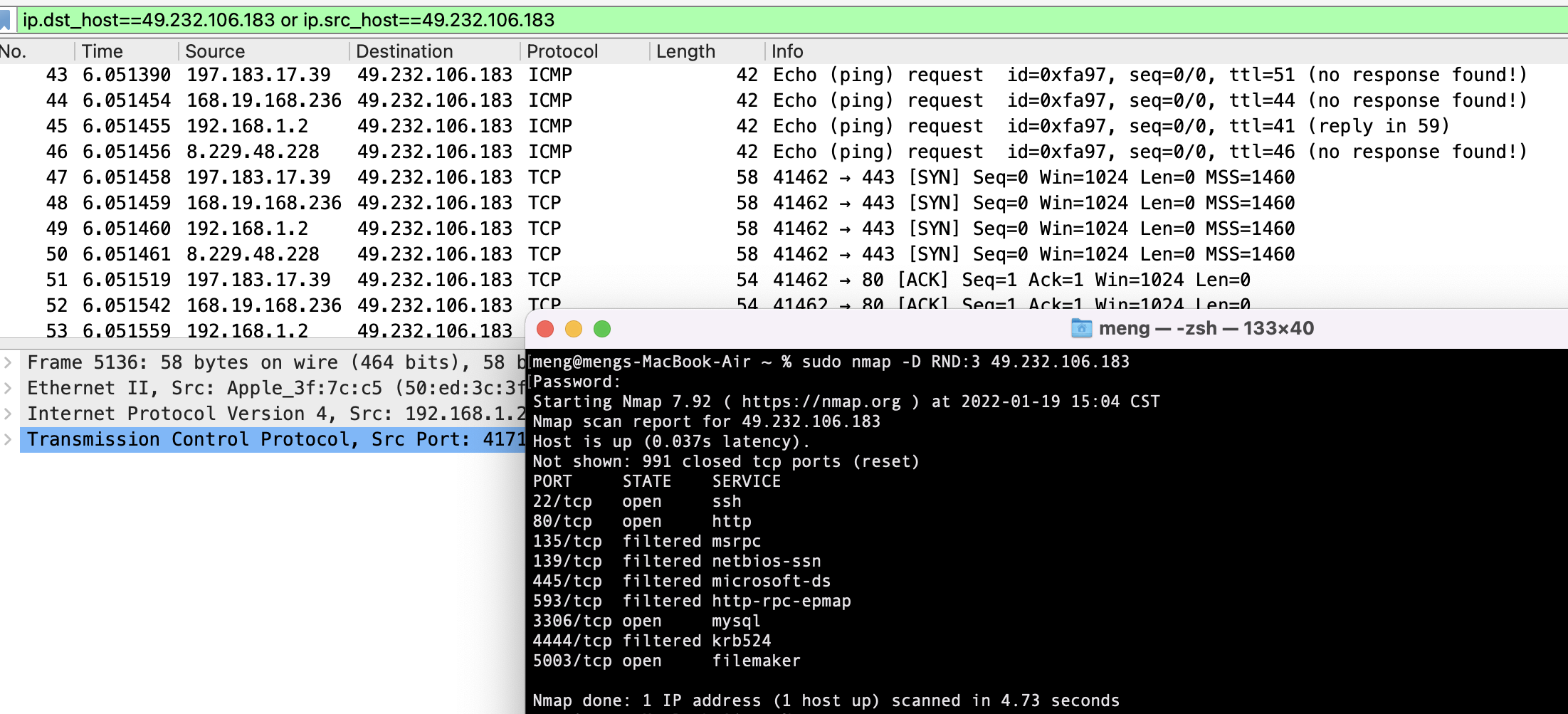
5.诱饵的使用(防止封ip)
nmap -D RND:3 49.232.106.183 随机三个诱饵
6.其他参数说明:
-sn: ping扫描
-Pn:非ping扫描




