RGW如何设置Policy策略
Bucket Policy 是基于资源的授权策略。操作简单,Bucket 拥有者直接可以进行访问授权。Bucket Policy 支持向其他账号的 RAM 用户授予访问权限,以及向匿名用户授予带特定IP条件限制的访问权限。
环境信息
ceph 12.2.12
boto3 sdk 使用案例如下:
import json
from boto3.session import Session
endpoint = 'http://server_ip'
access_key = 'your key'
secret_key = 'your secret key'
policy = {
"Version": "2012-10-17",
"Statement": [{
"Effect": "Allow",
"Principal": {"AWS": ["arn:aws:iam:::user/fred"]},
"Action": "s3PutObjectAcl",
"Resource": [
"arn:aws:s3:::happybucket/*"
]
}]
}
session = Session(access_key, secret_key)
client = session.client('s3', endpoint_url=endpoint)
client.put_bucket_policy(Bucket='happybucket', Policy=json.dumps(policy))
# 查看策略
client.get_bucket_policy(Bucket='happybucket')
特别提醒
- 自身拥有的Bucket才有权限设置(见Bucket来源)
策略参数
-
Version: policy版本,当前最新版本为"2012-10-17"
-
Sid: 策略名称,非必须
-
Effect: 枚举值:Allow、Deny
-
Principal: 指定规则生效的对象 > 格式为
"Principal":{"AWS":"arn:aws:iam::
:user/ "} -
Action: 操作,也就是允许执行的方法
-
Resource : 限定的资源,一般就是指bucket
warning::备注
ceph RGW 当前不支持aws的account-ID,用tenant代替,如果没有区分租户,则为空即可
当前支持策略
当前支持 actions 如下:
- s3:AbortMultipartUpload
- s3:GetBucketAcl
- s3:GetBucketCORS
- s3:GetBucketLocation
- s3:GetBucketLogging
- s3:GetBucketPolicy
- s3:GetBucketRequestPayment
- s3:GetBucketVersioning
- s3:GetObjectAcl
- s3:GetObject
- s3:ListBucketMultiPartUploads
- s3:ListBucket
- s3:ListBucketVersions
- s3:PutBucketAcl
- s3:PutBucketCORS
- s3:PutBucketRequestPayment
- s3:PutBucketVersioning
- s3:PutObjectAcl
- s3:PutObject
当前支持 condition keys 如下
-
aws:CurrentTime
- DateEquals 不支持
- DateNotEquals 不支持
-
aws:EpochTime
- DateEquals 不支持
- DateNotEquals 不支持
-
aws:PrincipalType
-
aws:Referer
-
aws:SourceIp
-
aws:UserAgent
-
aws:username
常见场景使用
场景一: 某公司A,希望合作伙伴可以访问指定Bucket下指定目录data下文件
api方式
data = {
"Version": "2012-10-17",
"Statement": [
{
"Effect": "Allow",
"Principal": {"AWS": "arn:aws:iam:::user/cap"},
"Action": [ 's3:GetObject'],
"Resource": [
"arn:aws:s3:::<Bucket>/data/*",
]
}
]
}
场景二:某公司A,希望内部公开文档存放在Bukcet 的 public目录下,员工在办公室可以直接访问,假设办公室出口IP为 ip1、ip2
api方式
data = {
"Version": "2012-10-17",
"Statement": [
{
"Effect": "Allow",
"Principal": {"AWS": "*"},
"Action": [ 's3:GetObject'],
"Resource": [
"arn:aws:s3:::<Bucket>/public/*",
],
"Condition": {
"IpAddress": {"aws:SourceIp": [
"<ip1>/32",
"<ip2>/32"
]
}
}
}
]
}
多条件判定
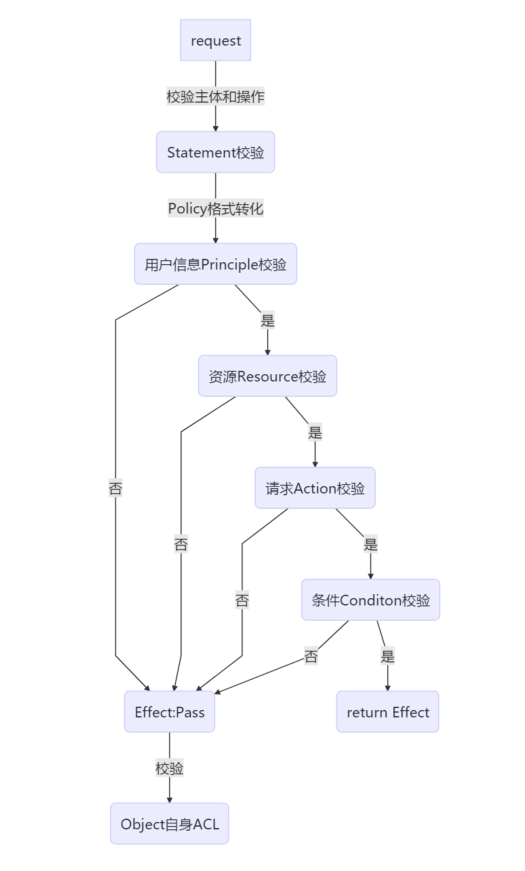
总结如下
- 多个条件同时命中,Deny 优先级较高
- 都没命中时,看集群自身ACL,比如:private,public-read



 浙公网安备 33010602011771号
浙公网安备 33010602011771号