关于在Wireshark中注意到TCP传输长度大于MSS的现象
关于在Wireshark中注意到TCP传输长度大于MSS的现象
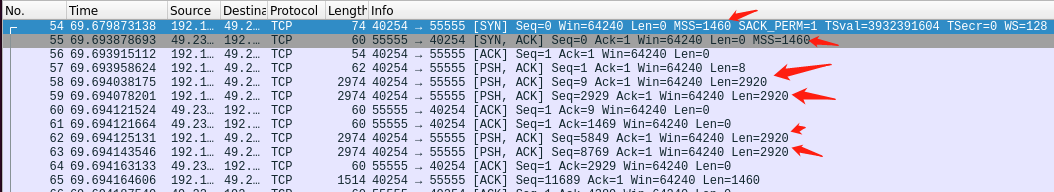
在进行TTCP传输的实验复习TCP的过程中,注意到某些报文段的数据长度要大于MSS。
在https://osqa-ask.wireshark.org/questions/24699/tcp-packet-length-was-much-greater-than-mtu/找到了答案:
Probably you captured on the host that transmitted the oversized packet, and TCP Large Segment Offload is enabled. (Sometimes abbreviated TSO and sometimes LSO.) The operating system is passing packets larger than MTU to the network adapter, and the network adapter driver is breaking them up so that they fit within the MTU. If you capture from the wire, instead of from an endpoint involved in the communication, you will see that the packets are correctly sized when they are transmitted. This is one reason of several to capture from the wire, instead of on an endpoint.
TSO is a performance enhancement, but you can turn it off, in which case, the OS will no longer generate oversized frames.
To show the size of the TCP segment, add a custom column using the field "tcp.len".
简单来说就是为了优化处理大包传输,将TCP分段的功能下放到网络适配器中,处理网络的性能。
如果不是在主机抓包而是在网络传输过程中抓包就不会超过MSS。其实也有另外的证明就是另一端传输过来的ACK不是以2920递增的,而是以1460递增的,这个需要关闭Nagle算法。
还有一个问题就是:为什么TCP并未表现出传统所学的拥塞避免算法???中文网络并未解释,再找找。


