深入了解安全工具Vault,vault详解大全
了解安全工具Vault、Vault根令牌和解封密钥,详细整理部署Vault
一、深入了解安全工具Vault
Vault是一种开源工具,用于安全地存储、管理和控制访问各种机密信息,如密码、API令牌、安全配置和其他敏感数据。Vault使用强大的加密和安全管理技术来保护这些机密信息,并为应用程序和服务提供安全的访问控制机制。该工具支持各种云平台和技术堆栈,并提供多种API和CLI接口,使其易于集成和使用。Vault的主要特点包括中心化管理、角色分配和权限控制、审计和日志记录、动态秘钥持续更新等。这些功能使得Vault成为一款颇受开发者和企业信赖的安全工具。
二、Vault根令牌和解封密钥的含义和作用
Vault 中的根令牌和解封密钥是用于管理和保护 Vault 中加密数据的重要凭据。
根令牌是 Vault 中的最高权限凭据,拥有此令牌的用户可以在 Vault 中进行任何操作,包括创建和删除机密、管理策略、配置身份验证等。因此,根令牌需要严格保密,并只在必要时进行使用。
解封密钥则是用于解密 Vault 中加密数据的重要凭据,可以用于解密 Vault 的存储密钥,解密后可以访问存储在 Vault 中的机密信息。因此,解封密钥也需要严格保密,通常会将其存储在冷存储中,以防止未经授权的访问和泄露。只有在必要时才使用解封密钥,例如在进行恢复操作或在创建新的存储密钥时。
三、centos7上部署和启动Vault的流程
在CentOS 7上部署和启动Vault可以按照以下步骤进行:
下载Vault二进制文件:可以从官网下载,也可以使用wget命令从Vault的GitHub页面下载。
安装Vault:将Vault二进制文件移到/usr/local/bin目录下,并添加执行权限。
配置Vault:可以在/etc目录下创建一个Vault配置文件,指定Vault的监听地址和端口,以及存储Vault数据的路径。
启动Vault:使用vault server命令启动Vault服务,会自动读取/etc目录下的配置文件并启动服务。
初始化Vault:使用vault init命令初始化Vault,生成一组Root Token和Unseal Key。
解封Vault:使用vault unseal命令输入Unseal Key解封Vault服务。
登录Vault:使用vault login命令输入Root Token登录Vault。
四、vault下载地址
vault下载地址:
vault官方下载地址
选择下载的版本
sudo yum install -y yum-utils
sudo yum-config-manager --add-repo https://rpm.releases.hashicorp.com/RHEL/hashicorp.repo
sudo yum -y install vault
五、安装vault
执行命令:
sudo yum install -y yum-utils
sudo yum install -y yum-utils
Loaded plugins: fastestmirror, langpacks, priorities, versionlock
Determining fastest mirrors
epel | 4.7 kB 00:00:00
extras | 2.9 kB 00:00:00
hashicorp | 1.4 kB 00:00:00
os | 3.6 kB 00:00:00
pgdg-common/7/x86_64/signature | 198 B 00:00:00
pgdg-common/7/x86_64/signature | 2.9 kB 00:00:00 !!!
pgdg11/7/x86_64/signature | 198 B 00:00:00
pgdg11/7/x86_64/signature | 3.6 kB 00:00:00 !!!
pgdg12/7/x86_64/signature | 198 B 00:00:00
pgdg12/7/x86_64/signature | 3.6 kB 00:00:00 !!!
pgdg13/7/x86_64/signature | 198 B 00:00:00
pgdg13/7/x86_64/signature | 3.6 kB 00:00:00 !!!
pgdg14/7/x86_64/signature | 198 B 00:00:00
pgdg14/7/x86_64/signature | 3.6 kB 00:00:00 !!!
pgdg15/7/x86_64/signature | 198 B 00:00:00
pgdg15/7/x86_64/signature | 3.6 kB 00:00:00 !!!
updates | 2.9 kB 00:00:00
(1/2): pgdg-common/7/x86_64/primary_db | 181 kB 00:00:02
(2/2): hashicorp/7/x86_64/primary | 165 kB 00:00:05
hashicorp 1196/1196
Package yum-utils-1.1.31-54.el7_8.noarch already installed and latest version
Nothing to do
执行命令:sudo yum-config-manager --add-repo https://rpm.releases.hashicorp.com/RHEL/hashicorp.repo
sudo yum-config-manager --add-repo https://rpm.releases.hashicorp.com/RHEL/hashicorp.repo
Loaded plugins: fastestmirror, langpacks, priorities, versionlock
adding repo from: https://rpm.releases.hashicorp.com/RHEL/hashicorp.repo
grabbing file https://rpm.releases.hashicorp.com/RHEL/hashicorp.repo to /etc/yum.repos.d/hashicorp.repo
repo saved to /etc/yum.repos.d/hashicorp.repo
执行命令:sudo yum -y install vault
sudo yum -y install vault
Loaded plugins: fastestmirror, langpacks, priorities, versionlock
Loading mirror speeds from cached hostfile
Resolving Dependencies
--> Running transaction check
---> Package vault.x86_64 0:1.13.3-1 will be installed
--> Finished Dependency Resolution
Dependencies Resolved
==================================================================================================================================================
Package Arch Version Repository Size
==================================================================================================================================================
Installing:
vault x86_64 1.13.3-1 hashicorp 92 M
Transaction Summary
==================================================================================================================================================
Install 1 Package
Total download size: 92 M
Installed size: 234 M
Downloading packages:
Delta RPMs disabled because /usr/bin/applydeltarpm not installed.
warning: /var/cache/yum/x86_64/7/hashicorp/packages/vault-1.13.3-1.x86_64.rpm: Header V4 RSA/SHA256 Signature, key ID a621e701: NOKEY00:00:00 ETA
Public key for vault-1.13.3-1.x86_64.rpm is not installed
vault-1.13.3-1.x86_64.rpm | 92 MB 00:00:24
Retrieving key from https://rpm.releases.hashicorp.com/gpg
Importing GPG key 0xA621E701:
Userid : "HashiCorp Security (HashiCorp Package Signing) <security+packaging@hashicorp.com>"
Fingerprint: 798a ec65 4e5c 1542 8c8e 42ee aa16 fcbc a621 e701
From : https://rpm.releases.hashicorp.com/gpg
Running transaction check
Running transaction test
Transaction test succeeded
Running transaction
Installing : vault-1.13.3-1.x86_64 1/1Generating Vault TLS key and self-signed certificate...
Generating a 4096 bit RSA private key
.......................++
.................................................................................................++
writing new private key to 'tls.key'
-----
Vault TLS key and self-signed certificate have been generated in '/opt/vault/tls'.
Verifying : vault-1.13.3-1.x86_64 1/1
Installed:
vault.x86_64 0:1.13.3-1
Complete!
六、启动Vault
执行启动命令:
vault server -dev -dev-root-token-id=“dev-only-token”
vault server -dev -dev-root-token-id="dev-only-token"
==> Vault server configuration:
Api Address: http://127.0.0.1:8200
Cgo: disabled
Cluster Address: https://127.0.0.1:8201
Environment Variables: CLASSPATH, FLINK_HOME, GODEBUG, HADOOP_HOME, HISTFILE, HISTSIZE, HISTTIMEFORMAT, HIVE_HOME, HOME, HOSTNAME, JAVA_HOME, LANG, LESSOPEN, LOGNAME, LS_COLORS, MAIL, MONGODB_HOME, MSSQL_HOME, PATH, PROMPT_COMMAND, PWD, PYTHON3_HOME, QT_GRAPHICSSYSTEM, QT_GRAPHICSSYSTEM_CHECKED, SHELL, SHLVL, SPARK_HOME, SUDO_COMMAND, SUDO_GID, SUDO_UID, SUDO_USER, TERM, TMOUT, USER, USERNAME, XDG_SESSION_ID, ZOOKEEP_HOME, _
Go Version: go1.20.4
Listener 1: tcp (addr: "127.0.0.1:8200", cluster address: "127.0.0.1:8201", max_request_duration: "1m30s", max_request_size: "33554432", tls: "disabled")
Log Level:
Mlock: supported: true, enabled: false
Recovery Mode: false
Storage: inmem
Version: Vault v1.13.3, built 2023-06-06T18:12:37Z
Version Sha: 3bedf816cbf851656ae9e6bd65dd4a67a9ddff5e
==> Vault server started! Log data will stream in below:
2023-06-19T10:38:19.735+0800 [INFO] proxy environment: http_proxy="" https_proxy="" no_proxy=""
2023-06-19T10:38:19.735+0800 [WARN] no `api_addr` value specified in config or in VAULT_API_ADDR; falling back to detection if possible, but this value should be manually set
2023-06-19T10:38:19.736+0800 [INFO] core: Initializing version history cache for core
2023-06-19T10:38:19.736+0800 [INFO] core: security barrier not initialized
2023-06-19T10:38:19.736+0800 [INFO] core: security barrier initialized: stored=1 shares=1 threshold=1
2023-06-19T10:38:19.737+0800 [INFO] core: post-unseal setup starting
2023-06-19T10:38:19.751+0800 [INFO] core: loaded wrapping token key
2023-06-19T10:38:19.751+0800 [INFO] core: successfully setup plugin catalog: plugin-directory=""
2023-06-19T10:38:19.751+0800 [INFO] core: no mounts; adding default mount table
2023-06-19T10:38:19.753+0800 [INFO] core: successfully mounted: type=cubbyhole version="v1.13.3+builtin.vault" path=cubbyhole/ namespace="ID: root. Path: "
2023-06-19T10:38:19.753+0800 [INFO] core: successfully mounted: type=system version="v1.13.3+builtin.vault" path=sys/ namespace="ID: root. Path: "
2023-06-19T10:38:19.754+0800 [INFO] core: successfully mounted: type=identity version="v1.13.3+builtin.vault" path=identity/ namespace="ID: root. Path: "
2023-06-19T10:38:19.755+0800 [INFO] core: successfully mounted: type=token version="v1.13.3+builtin.vault" path=token/ namespace="ID: root. Path: "
2023-06-19T10:38:19.756+0800 [INFO] rollback: starting rollback manager
2023-06-19T10:38:19.757+0800 [INFO] core: restoring leases
2023-06-19T10:38:19.758+0800 [INFO] expiration: lease restore complete
2023-06-19T10:38:19.758+0800 [INFO] identity: entities restored
2023-06-19T10:38:19.759+0800 [INFO] identity: groups restored
2023-06-19T10:38:19.759+0800 [INFO] core: Recorded vault version: vault version=1.13.3 upgrade time="2023-06-19 02:38:19.759135384 +0000 UTC" build date=2023-06-06T18:12:37Z
2023-06-19T10:38:19.981+0800 [INFO] core: post-unseal setup complete
2023-06-19T10:38:19.981+0800 [INFO] core: root token generated
2023-06-19T10:38:19.981+0800 [INFO] core: pre-seal teardown starting
2023-06-19T10:38:19.981+0800 [INFO] rollback: stopping rollback manager
2023-06-19T10:38:19.982+0800 [INFO] core: pre-seal teardown complete
2023-06-19T10:38:19.982+0800 [INFO] core.cluster-listener.tcp: starting listener: listener_address=127.0.0.1:8201
2023-06-19T10:38:19.982+0800 [INFO] core.cluster-listener: serving cluster requests: cluster_listen_address=127.0.0.1:8201
2023-06-19T10:38:19.982+0800 [INFO] core: post-unseal setup starting
2023-06-19T10:38:19.982+0800 [INFO] core: loaded wrapping token key
2023-06-19T10:38:19.982+0800 [INFO] core: successfully setup plugin catalog: plugin-directory=""
2023-06-19T10:38:19.983+0800 [INFO] core: successfully mounted: type=system version="v1.13.3+builtin.vault" path=sys/ namespace="ID: root. Path: "
2023-06-19T10:38:19.983+0800 [INFO] core: successfully mounted: type=identity version="v1.13.3+builtin.vault" path=identity/ namespace="ID: root. Path: "
2023-06-19T10:38:19.983+0800 [INFO] core: successfully mounted: type=cubbyhole version="v1.13.3+builtin.vault" path=cubbyhole/ namespace="ID: root. Path: "
2023-06-19T10:38:19.984+0800 [INFO] core: successfully mounted: type=token version="v1.13.3+builtin.vault" path=token/ namespace="ID: root. Path: "
2023-06-19T10:38:19.984+0800 [INFO] rollback: starting rollback manager
2023-06-19T10:38:19.984+0800 [INFO] core: restoring leases
2023-06-19T10:38:19.985+0800 [INFO] identity: entities restored
2023-06-19T10:38:19.985+0800 [INFO] identity: groups restored
2023-06-19T10:38:19.985+0800 [INFO] expiration: lease restore complete
2023-06-19T10:38:19.985+0800 [INFO] core: post-unseal setup complete
2023-06-19T10:38:19.985+0800 [INFO] core: vault is unsealed
2023-06-19T10:38:19.987+0800 [INFO] expiration: revoked lease: lease_id=auth/token/root/h272562f04a210e20b2b4d865e2a84db2d53929c149d30e4e06dcd93ebe88dbac
2023-06-19T10:38:19.989+0800 [INFO] core: successful mount: namespace="" path=secret/ type=kv version=""
WARNING! dev mode is enabled! In this mode, Vault runs entirely in-memory
and starts unsealed with a single unseal key. The root token is already
authenticated to the CLI, so you can immediately begin using Vault.
You may need to set the following environment variables:
$ export VAULT_ADDR='http://127.0.0.1:8200'
The unseal key and root token are displayed below in case you want to
seal/unseal the Vault or re-authenticate.
Unseal Key: DY/t5B7OSPzH1XZq5RJoEr0o7l4Ea5epNl9h0b/zaF4=
Root Token: dev-only-token
Development mode should NOT be used in production installations!
如上所示,成功启动Vault,至此成功安装部署Vault
注意命令行输出的解封密钥和根令牌,要妥善保存解封密钥和根令牌:
Unseal Key: DY/t5B7OSPzH1XZq5RJoEr0o7l4Ea5epNl9h0b/zaF4=
Root Token: dev-only-token
[root@mcw02 ~]# curl https://rpm.releases.hashicorp.com/RHEL/hashicorp.repo -o /etc/yum. yum.conf yum.repos.d/ [root@mcw02 ~]# curl https://rpm.releases.hashicorp.com/RHEL/hashicorp.repo -o /etc/yum.repos.d/hashicorp.repo % Total % Received % Xferd Average Speed Time Time Time Current Dload Upload Total Spent Left Speed 100 381 100 381 0 0 54 0 0:00:07 0:00:06 0:00:01 86 [root@mcw02 ~]# yum -y install vault Loaded plugins: fastestmirror base | 3.6 kB 00:00:00 epel | 4.3 kB 00:00:00 extras | 2.9 kB 00:00:00 glusterfs | 2.9 kB 00:00:00 hashicorp | 1.4 kB 00:00:00 salt-3004-repo | 2.9 kB 00:00:00 selfmcw | 2.9 kB 00:00:00 updates | 2.9 kB 00:00:00 zabbix | 2.9 kB 00:00:00 zabbix-non-supported | 2.9 kB 00:00:00 (1/6): epel/x86_64/group | 399 kB 00:00:00 (2/6): extras/7/x86_64/primary_db | 253 kB 00:00:00 (3/6): epel/x86_64/updateinfo | 1.0 MB 00:00:01 (4/6): hashicorp/7/x86_64/primary | 243 kB 00:00:01 (5/6): epel/x86_64/primary_db | 8.7 MB 00:00:10 (6/6): updates/7/x86_64/primary_db | 27 MB 00:00:33 Determining fastest mirrors * base: mirrors.aliyun.com * extras: mirrors.aliyun.com * updates: mirrors.aliyun.com hashicorp 1762/1762 Resolving Dependencies --> Running transaction check ---> Package vault.x86_64 0:1.16.2-1 will be installed --> Finished Dependency Resolution Dependencies Resolved ======================================================================================================================================================================= Package Arch Version Repository Size ======================================================================================================================================================================= Installing: vault x86_64 1.16.2-1 hashicorp 143 M Transaction Summary ======================================================================================================================================================================= Install 1 Package Total download size: 143 M Installed size: 402 M Downloading packages: warning: /var/cache/yum/x86_64/7/hashicorp/packages/vault-1.16.2-1.x86_64.rpm: Header V4 RSA/SHA256 Signature, key ID a621e701: NOKEY] 7.2 MB/s | 141 MB 00:00:00 ETA Public key for vault-1.16.2-1.x86_64.rpm is not installed vault-1.16.2-1.x86_64.rpm | 143 MB 00:00:25 Retrieving key from https://rpm.releases.hashicorp.com/gpg Importing GPG key 0xA621E701: Userid : "HashiCorp Security (HashiCorp Package Signing) <security+packaging@hashicorp.com>" Fingerprint: 798a ec65 4e5c 1542 8c8e 42ee aa16 fcbc a621 e701 From : https://rpm.releases.hashicorp.com/gpg Running transaction check Running transaction test Transaction test succeeded Running transaction Installing : vault-1.16.2-1.x86_64 1/1Generating Vault TLS key and self-signed certificate... Generating a 4096 bit RSA private key .......................................................................................................................................................++ ............................................++ writing new private key to 'tls.key' ----- Vault TLS key and self-signed certificate have been generated in '/opt/vault/tls'. Verifying : vault-1.16.2-1.x86_64 1/1 Installed: vault.x86_64 0:1.16.2-1 Complete! [root@mcw02 ~]# vault server -dev -dev-root-token-id=“dev-only-token” ==> Vault server configuration: Administrative Namespace: Api Address: http://127.0.0.1:8200 Cgo: disabled Cluster Address: https://127.0.0.1:8201 Environment Variables: HADOOP_HOME, HISTCONTROL, HISTIMEFORMAT, HISTSIZE, HOME, HOSTNAME, JAVA_HOME, LANG, LESSOPEN, LOGNAME, LS_COLORS, MAIL, PATH, PORMPT_COMMADN, PWD, SHELL, SHLVL, SSH_CLIENT, SSH_CONNECTION, SSH_TTY, TERM, USER, XDG_RUNTIME_DIR, XDG_SESSION_ID, _ Go Version: go1.21.9 Listener 1: tcp (addr: "127.0.0.1:8200", cluster address: "127.0.0.1:8201", disable_request_limiter: "false", max_request_duration: "1m30s", max_request_size: "33554432", tls: "disabled") Log Level: Mlock: supported: true, enabled: false Recovery Mode: false Storage: inmem Version: Vault v1.16.2, built 2024-04-22T16:25:54Z Version Sha: c6e4c2d4dc3b0d57791881b087c026e2f75a87cb ==> Vault server started! Log data will stream in below: 2024-05-21T08:40:29.857+0800 [INFO] proxy environment: http_proxy="" https_proxy="" no_proxy="" 2024-05-21T08:40:29.857+0800 [INFO] incrementing seal generation: generation=1 2024-05-21T08:40:29.857+0800 [WARN] no `api_addr` value specified in config or in VAULT_API_ADDR; falling back to detection if possible, but this value should be manually set 2024-05-21T08:40:29.857+0800 [INFO] core: Initializing version history cache for core 2024-05-21T08:40:29.857+0800 [INFO] events: Starting event system 2024-05-21T08:40:29.858+0800 [INFO] core: security barrier not initialized 2024-05-21T08:40:29.858+0800 [INFO] core: security barrier initialized: stored=1 shares=1 threshold=1 2024-05-21T08:40:29.858+0800 [INFO] core: post-unseal setup starting 2024-05-21T08:40:29.873+0800 [INFO] core: loaded wrapping token key 2024-05-21T08:40:29.873+0800 [INFO] core: successfully setup plugin runtime catalog 2024-05-21T08:40:29.873+0800 [INFO] core: successfully setup plugin catalog: plugin-directory="" 2024-05-21T08:40:29.873+0800 [INFO] core: no mounts; adding default mount table 2024-05-21T08:40:29.874+0800 [INFO] core: successfully mounted: type=cubbyhole version="v1.16.2+builtin.vault" path=cubbyhole/ namespace="ID: root. Path: " 2024-05-21T08:40:29.875+0800 [INFO] core: successfully mounted: type=system version="v1.16.2+builtin.vault" path=sys/ namespace="ID: root. Path: " 2024-05-21T08:40:29.875+0800 [INFO] core: successfully mounted: type=identity version="v1.16.2+builtin.vault" path=identity/ namespace="ID: root. Path: " 2024-05-21T08:40:29.878+0800 [INFO] core: successfully mounted: type=token version="v1.16.2+builtin.vault" path=token/ namespace="ID: root. Path: " 2024-05-21T08:40:29.878+0800 [INFO] rollback: Starting the rollback manager with 256 workers 2024-05-21T08:40:29.879+0800 [INFO] core: restoring leases 2024-05-21T08:40:29.880+0800 [INFO] expiration: lease restore complete 2024-05-21T08:40:29.880+0800 [INFO] rollback: starting rollback manager 2024-05-21T08:40:29.880+0800 [INFO] identity: entities restored 2024-05-21T08:40:29.880+0800 [INFO] identity: groups restored 2024-05-21T08:40:29.881+0800 [INFO] core: Recorded vault version: vault version=1.16.2 upgrade time="2024-05-21 00:40:29.881043663 +0000 UTC" build date=2024-04-22T16:25:54Z 2024-05-21T08:40:29.881+0800 [INFO] core: post-unseal setup complete 2024-05-21T08:40:29.881+0800 [INFO] core: root token generated 2024-05-21T08:40:29.881+0800 [INFO] core: pre-seal teardown starting 2024-05-21T08:40:29.881+0800 [INFO] rollback: stopping rollback manager 2024-05-21T08:40:29.881+0800 [INFO] core: pre-seal teardown complete 2024-05-21T08:40:29.882+0800 [INFO] core.cluster-listener.tcp: starting listener: listener_address=127.0.0.1:8201 2024-05-21T08:40:29.882+0800 [INFO] core.cluster-listener: serving cluster requests: cluster_listen_address=127.0.0.1:8201 2024-05-21T08:40:29.882+0800 [INFO] core: post-unseal setup starting 2024-05-21T08:40:29.882+0800 [INFO] core: loaded wrapping token key 2024-05-21T08:40:29.882+0800 [INFO] core: successfully setup plugin runtime catalog 2024-05-21T08:40:29.882+0800 [INFO] core: successfully setup plugin catalog: plugin-directory="" 2024-05-21T08:40:29.883+0800 [INFO] core: successfully mounted: type=system version="v1.16.2+builtin.vault" path=sys/ namespace="ID: root. Path: " 2024-05-21T08:40:29.883+0800 [INFO] core: successfully mounted: type=identity version="v1.16.2+builtin.vault" path=identity/ namespace="ID: root. Path: " 2024-05-21T08:40:29.883+0800 [INFO] core: successfully mounted: type=cubbyhole version="v1.16.2+builtin.vault" path=cubbyhole/ namespace="ID: root. Path: " 2024-05-21T08:40:29.884+0800 [INFO] core: successfully mounted: type=token version="v1.16.2+builtin.vault" path=token/ namespace="ID: root. Path: " 2024-05-21T08:40:29.884+0800 [INFO] rollback: Starting the rollback manager with 256 workers 2024-05-21T08:40:29.884+0800 [INFO] core: restoring leases 2024-05-21T08:40:29.884+0800 [INFO] identity: entities restored 2024-05-21T08:40:29.884+0800 [INFO] identity: groups restored 2024-05-21T08:40:29.884+0800 [INFO] core: post-unseal setup complete 2024-05-21T08:40:29.884+0800 [INFO] core: vault is unsealed 2024-05-21T08:40:29.886+0800 [INFO] expiration: revoked lease: lease_id=auth/token/root/h3514d1c95b4d2e0108dc129ebd305e12342b57fb544e4ccd978af76ebfdb3b5d 2024-05-21T08:40:29.930+0800 [INFO] expiration: lease restore complete 2024-05-21T08:40:29.930+0800 [INFO] rollback: starting rollback manager 2024-05-21T08:40:29.932+0800 [INFO] core: successful mount: namespace="" path=secret/ type=kv version="v0.17.0+builtin" WARNING! dev mode is enabled! In this mode, Vault runs entirely in-memory and starts unsealed with a single unseal key. The root token is already authenticated to the CLI, so you can immediately begin using Vault. You may need to set the following environment variables: $ export VAULT_ADDR='http://127.0.0.1:8200' The unseal key and root token are displayed below in case you want to seal/unseal the Vault or re-authenticate. Unseal Key: +sPbWdhzUK3Xr+s4SiW4Jvy7T7iGkW1rNsdTtCnXo78= Root Token: “dev-only-token” Development mode should NOT be used in production installations! 夯住不动
但是端口已经已经启动了,访问8200端口,没有成功,把上面夯住的进程停掉,应该跟启动ip有关,
[root@mcw02 ~]# netstat -lntup|grep vault tcp 0 0 127.0.0.1:8200 0.0.0.0:* LISTEN 1885/vault tcp 0 0 127.0.0.1:8201 0.0.0.0:* LISTEN 1885/vault [root@mcw02 ~]#
记录需要的信息
Unseal Key: +sPbWdhzUK3Xr+s4SiW4Jvy7T7iGkW1rNsdTtCnXo78=
Root Token: “dev-only-token”
停掉
^[[B^C==> Vault shutdown triggered 2024-05-21T08:51:12.026+0800 [INFO] core: marked as sealed 2024-05-21T08:51:12.026+0800 [INFO] core: pre-seal teardown starting 2024-05-21T08:51:12.026+0800 [INFO] rollback: stopping rollback manager 2024-05-21T08:51:12.026+0800 [INFO] core: pre-seal teardown complete 2024-05-21T08:51:12.026+0800 [INFO] core: stopping cluster listeners 2024-05-21T08:51:12.026+0800 [INFO] core.cluster-listener: forwarding rpc listeners stopped 2024-05-21T08:51:12.161+0800 [INFO] core.cluster-listener: rpc listeners successfully shut down 2024-05-21T08:51:12.161+0800 [INFO] core: cluster listeners successfully shut down 2024-05-21T08:51:12.161+0800 [INFO] core: vault is sealed [root@mcw02 ~]#
[root@mcw02 ~]# netstat -lntup|grep vault
[root@mcw02 ~]#
Vault 作为客户端-服务器应用程序运行。Vault 服务器是唯一与数据存储和后端交互的 Vault 架构。通过 Vault CLI 完成的所有操作都通过 TLS 连接与服务器交互。
在本篇博客中,启动以开发模式运行的 Vault 服务器并与之交互。
启动Vault服务器
一、启动开发服务器
以开发模式(开发服务器)启动 Vault 服务器。开发服务器是一个内置的、预配置的服务器,它不是很安全,但对于在本地使用 Vault 很有用。
vault server -dev
输出如下所示:
vault server -dev
==> Vault server configuration:
Api Address: http://127.0.0.1:8200
Cgo: disabled
Cluster Address: https://127.0.0.1:8201
Environment Variables: CLASSPATH, FLINK_HOME, GODEBUG, HADOOP_HOME, HISTFILE, HISTSIZE, HISTTIMEFORMAT, HIVE_HOME, HOME, HOSTNAME, JAVA_HOME, LANG, LESSOPEN, LOGNAME, LS_COLORS, MAIL, MONGODB_HOME, MSSQL_HOME, PATH, PROMPT_COMMAND, PWD, PYTHON3_HOME, QT_GRAPHICSSYSTEM, QT_GRAPHICSSYSTEM_CHECKED, SHELL, SHLVL, SPARK_HOME, SUDO_COMMAND, SUDO_GID, SUDO_UID, SUDO_USER, TERM, TMOUT, USER, USERNAME, VAULT_ADDR, XDG_SESSION_ID, ZOOKEEP_HOME, _
Go Version: go1.20.4
Listener 1: tcp (addr: "127.0.0.1:8200", cluster address: "127.0.0.1:8201", max_request_duration: "1m30s", max_request_size: "33554432", tls: "disabled")
Log Level:
Mlock: supported: true, enabled: false
Recovery Mode: false
Storage: inmem
Version: Vault v1.13.3, built 2023-06-06T18:12:37Z
Version Sha: 3bedf816cbf851656ae9e6bd65dd4a67a9ddff5e
==> Vault server started! Log data will stream in below:
2023-06-19T13:14:08.399+0800 [INFO] proxy environment: http_proxy="" https_proxy="" no_proxy=""
2023-06-19T13:14:08.399+0800 [WARN] no `api_addr` value specified in config or in VAULT_API_ADDR; falling back to detection if possible, but this value should be manually set
2023-06-19T13:14:08.400+0800 [INFO] core: Initializing version history cache for core
2023-06-19T13:14:08.400+0800 [INFO] core: security barrier not initialized
2023-06-19T13:14:08.400+0800 [INFO] core: security barrier initialized: stored=1 shares=1 threshold=1
2023-06-19T13:14:08.401+0800 [INFO] core: post-unseal setup starting
2023-06-19T13:14:08.416+0800 [INFO] core: loaded wrapping token key
2023-06-19T13:14:08.416+0800 [INFO] core: successfully setup plugin catalog: plugin-directory=""
2023-06-19T13:14:08.416+0800 [INFO] core: no mounts; adding default mount table
2023-06-19T13:14:08.417+0800 [INFO] core: successfully mounted: type=cubbyhole version="v1.13.3+builtin.vault" path=cubbyhole/ namespace="ID: root. Path: "
2023-06-19T13:14:08.418+0800 [INFO] core: successfully mounted: type=system version="v1.13.3+builtin.vault" path=sys/ namespace="ID: root. Path: "
2023-06-19T13:14:08.418+0800 [INFO] core: successfully mounted: type=identity version="v1.13.3+builtin.vault" path=identity/ namespace="ID: root. Path: "
2023-06-19T13:14:08.420+0800 [INFO] core: successfully mounted: type=token version="v1.13.3+builtin.vault" path=token/ namespace="ID: root. Path: "
2023-06-19T13:14:08.420+0800 [INFO] rollback: starting rollback manager
2023-06-19T13:14:08.423+0800 [INFO] core: restoring leases
2023-06-19T13:14:08.425+0800 [INFO] expiration: lease restore complete
2023-06-19T13:14:08.426+0800 [INFO] identity: entities restored
2023-06-19T13:14:08.426+0800 [INFO] identity: groups restored
2023-06-19T13:14:08.426+0800 [INFO] core: Recorded vault version: vault version=1.13.3 upgrade time="2023-06-19 05:14:08.426587913 +0000 UTC" build date=2023-06-06T18:12:37Z
2023-06-19T13:14:08.696+0800 [INFO] core: post-unseal setup complete
2023-06-19T13:14:08.696+0800 [INFO] core: root token generated
2023-06-19T13:14:08.696+0800 [INFO] core: pre-seal teardown starting
2023-06-19T13:14:08.697+0800 [INFO] rollback: stopping rollback manager
2023-06-19T13:14:08.697+0800 [INFO] core: pre-seal teardown complete
2023-06-19T13:14:08.697+0800 [INFO] core.cluster-listener.tcp: starting listener: listener_address=127.0.0.1:8201
2023-06-19T13:14:08.697+0800 [INFO] core.cluster-listener: serving cluster requests: cluster_listen_address=127.0.0.1:8201
2023-06-19T13:14:08.697+0800 [INFO] core: post-unseal setup starting
2023-06-19T13:14:08.697+0800 [INFO] core: loaded wrapping token key
2023-06-19T13:14:08.697+0800 [INFO] core: successfully setup plugin catalog: plugin-directory=""
2023-06-19T13:14:08.698+0800 [INFO] core: successfully mounted: type=system version="v1.13.3+builtin.vault" path=sys/ namespace="ID: root. Path: "
2023-06-19T13:14:08.698+0800 [INFO] core: successfully mounted: type=identity version="v1.13.3+builtin.vault" path=identity/ namespace="ID: root. Path: "
2023-06-19T13:14:08.698+0800 [INFO] core: successfully mounted: type=cubbyhole version="v1.13.3+builtin.vault" path=cubbyhole/ namespace="ID: root. Path: "
2023-06-19T13:14:08.699+0800 [INFO] core: successfully mounted: type=token version="v1.13.3+builtin.vault" path=token/ namespace="ID: root. Path: "
2023-06-19T13:14:08.699+0800 [INFO] rollback: starting rollback manager
2023-06-19T13:14:08.699+0800 [INFO] core: restoring leases
2023-06-19T13:14:08.700+0800 [INFO] identity: entities restored
2023-06-19T13:14:08.700+0800 [INFO] identity: groups restored
2023-06-19T13:14:08.700+0800 [INFO] expiration: lease restore complete
2023-06-19T13:14:08.700+0800 [INFO] core: post-unseal setup complete
2023-06-19T13:14:08.700+0800 [INFO] core: vault is unsealed
2023-06-19T13:14:08.703+0800 [INFO] core: successful mount: namespace="" path=secret/ type=kv version=""
WARNING! dev mode is enabled! In this mode, Vault runs entirely in-memory
and starts unsealed with a single unseal key. The root token is already
authenticated to the CLI, so you can immediately begin using Vault.
You may need to set the following environment variables:
$ export VAULT_ADDR='http://127.0.0.1:8200'
The unseal key and root token are displayed below in case you want to
seal/unseal the Vault or re-authenticate.
Unseal Key: jp2vzZPjYufsXNsJsEFTuKHMJzvx2FvnC5M3H6+y3vc=
Root Token: hvs.WNSdITpoYX5HvRZWYyGjvZaj
Development mode should NOT be used in production installations!
开发服务器将其所有数据存储在内存中(但仍然加密),在localhost没有 TLS 的情况下进行侦听,并自动解封并向您显示解封密钥和根访问密钥。
跟上面的一样,是前台运行程序
[root@mcw02 ~]# vault server -dev ==> Vault server configuration: Administrative Namespace: Api Address: http://127.0.0.1:8200 Cgo: disabled Cluster Address: https://127.0.0.1:8201 Environment Variables: HADOOP_HOME, HISTCONTROL, HISTIMEFORMAT, HISTSIZE, HOME, HOSTNAME, JAVA_HOME, LANG, LESSOPEN, LOGNAME, LS_COLORS, MAIL, PATH, PORMPT_COMMADN, PWD, SHELL, SHLVL, SSH_CLIENT, SSH_CONNECTION, SSH_TTY, TERM, USER, XDG_RUNTIME_DIR, XDG_SESSION_ID, _ Go Version: go1.21.9 Listener 1: tcp (addr: "127.0.0.1:8200", cluster address: "127.0.0.1:8201", disable_request_limiter: "false", max_request_duration: "1m30s", max_request_size: "33554432", tls: "disabled") Log Level: Mlock: supported: true, enabled: false Recovery Mode: false Storage: inmem Version: Vault v1.16.2, built 2024-04-22T16:25:54Z Version Sha: c6e4c2d4dc3b0d57791881b087c026e2f75a87cb ==> Vault server started! Log data will stream in below: 2024-05-21T08:52:25.522+0800 [INFO] proxy environment: http_proxy="" https_proxy="" no_proxy="" 2024-05-21T08:52:25.522+0800 [INFO] incrementing seal generation: generation=1 2024-05-21T08:52:25.522+0800 [WARN] no `api_addr` value specified in config or in VAULT_API_ADDR; falling back to detection if possible, but this value should be manually set 2024-05-21T08:52:25.522+0800 [INFO] core: Initializing version history cache for core 2024-05-21T08:52:25.522+0800 [INFO] events: Starting event system 2024-05-21T08:52:25.522+0800 [INFO] core: security barrier not initialized 2024-05-21T08:52:25.522+0800 [INFO] core: security barrier initialized: stored=1 shares=1 threshold=1 2024-05-21T08:52:25.523+0800 [INFO] core: post-unseal setup starting 2024-05-21T08:52:25.537+0800 [INFO] core: loaded wrapping token key 2024-05-21T08:52:25.537+0800 [INFO] core: successfully setup plugin runtime catalog 2024-05-21T08:52:25.538+0800 [INFO] core: successfully setup plugin catalog: plugin-directory="" 2024-05-21T08:52:25.538+0800 [INFO] core: no mounts; adding default mount table 2024-05-21T08:52:25.539+0800 [INFO] core: successfully mounted: type=cubbyhole version="v1.16.2+builtin.vault" path=cubbyhole/ namespace="ID: root. Path: " 2024-05-21T08:52:25.540+0800 [INFO] core: successfully mounted: type=system version="v1.16.2+builtin.vault" path=sys/ namespace="ID: root. Path: " 2024-05-21T08:52:25.541+0800 [INFO] core: successfully mounted: type=identity version="v1.16.2+builtin.vault" path=identity/ namespace="ID: root. Path: " 2024-05-21T08:52:25.543+0800 [INFO] core: successfully mounted: type=token version="v1.16.2+builtin.vault" path=token/ namespace="ID: root. Path: " 2024-05-21T08:52:25.543+0800 [INFO] rollback: Starting the rollback manager with 256 workers 2024-05-21T08:52:25.544+0800 [INFO] rollback: starting rollback manager 2024-05-21T08:52:25.544+0800 [INFO] core: restoring leases 2024-05-21T08:52:25.545+0800 [INFO] identity: entities restored 2024-05-21T08:52:25.545+0800 [INFO] identity: groups restored 2024-05-21T08:52:25.545+0800 [INFO] core: Recorded vault version: vault version=1.16.2 upgrade time="2024-05-21 00:52:25.545806587 +0000 UTC" build date=2024-04-22T16:25:54Z 2024-05-21T08:52:25.546+0800 [INFO] core: post-unseal setup complete 2024-05-21T08:52:25.546+0800 [INFO] core: root token generated 2024-05-21T08:52:25.546+0800 [INFO] core: pre-seal teardown starting 2024-05-21T08:52:25.546+0800 [INFO] expiration: lease restore complete 2024-05-21T08:52:25.557+0800 [INFO] rollback: stopping rollback manager 2024-05-21T08:52:25.557+0800 [INFO] core: pre-seal teardown complete 2024-05-21T08:52:25.557+0800 [INFO] core.cluster-listener.tcp: starting listener: listener_address=127.0.0.1:8201 2024-05-21T08:52:25.557+0800 [INFO] core.cluster-listener: serving cluster requests: cluster_listen_address=127.0.0.1:8201 2024-05-21T08:52:25.557+0800 [INFO] core: post-unseal setup starting 2024-05-21T08:52:25.557+0800 [INFO] core: loaded wrapping token key 2024-05-21T08:52:25.557+0800 [INFO] core: successfully setup plugin runtime catalog 2024-05-21T08:52:25.557+0800 [INFO] core: successfully setup plugin catalog: plugin-directory="" 2024-05-21T08:52:25.558+0800 [INFO] core: successfully mounted: type=system version="v1.16.2+builtin.vault" path=sys/ namespace="ID: root. Path: " 2024-05-21T08:52:25.559+0800 [INFO] core: successfully mounted: type=identity version="v1.16.2+builtin.vault" path=identity/ namespace="ID: root. Path: " 2024-05-21T08:52:25.559+0800 [INFO] core: successfully mounted: type=cubbyhole version="v1.16.2+builtin.vault" path=cubbyhole/ namespace="ID: root. Path: " 2024-05-21T08:52:25.560+0800 [INFO] core: successfully mounted: type=token version="v1.16.2+builtin.vault" path=token/ namespace="ID: root. Path: " 2024-05-21T08:52:25.560+0800 [INFO] rollback: Starting the rollback manager with 256 workers 2024-05-21T08:52:25.560+0800 [INFO] core: restoring leases 2024-05-21T08:52:25.561+0800 [INFO] expiration: lease restore complete 2024-05-21T08:52:25.561+0800 [INFO] rollback: starting rollback manager 2024-05-21T08:52:25.561+0800 [INFO] identity: entities restored 2024-05-21T08:52:25.561+0800 [INFO] identity: groups restored 2024-05-21T08:52:25.561+0800 [INFO] core: post-unseal setup complete 2024-05-21T08:52:25.561+0800 [INFO] core: vault is unsealed 2024-05-21T08:52:25.564+0800 [INFO] core: successful mount: namespace="" path=secret/ type=kv version="v0.17.0+builtin" WARNING! dev mode is enabled! In this mode, Vault runs entirely in-memory and starts unsealed with a single unseal key. The root token is already authenticated to the CLI, so you can immediately begin using Vault. You may need to set the following environment variables: $ export VAULT_ADDR='http://127.0.0.1:8200' The unseal key and root token are displayed below in case you want to seal/unseal the Vault or re-authenticate. Unseal Key: PCgwWZQZ91BLne/Xh8yIekhgrJzu38p/LqPNr8ndlDo= Root Token: hvs.HPHBPfqKpbOUKJFOqTvdXPT6 Development mode should NOT be used in production installations!
二、设置环境变量
启动一个新的终端会话。
export VAULT_ADDR …从终端输出复制并运行命令。这将配置 Vault 客户端与开发服务器对话。
export VAULT_ADDR='http://127.0.0.1:8200'
Vault CLI 使用环境变量确定哪些 Vault 服务器发送请求 VAULT_ADDR。
将解封密钥保存在某处。不要担心如何安全地保存它。现在,只需将它保存在任何地方。
将环境变量值VAULT_TOKEN设置为终端输出中显示的生成的根令牌值。
export VAULT_TOKEN="hvs.6j4cuewowBGit65rheNoceI7"
要与 Vault 交互,必须提供有效的令牌。设置此环境变量是一种通过 CLI 向 Vault 提供令牌的方法。在身份验证教程中,将学习使用vault login <token_value>命令对 Vault 进行身份验证。
三、验证服务器正在运行
通过运行命令验证服务器是否正在运行vault status。如果运行成功,输出应如下所示:
vault status
Key Value
--- -----
Seal Type shamir
Initialized true
Sealed false
Total Shares 1
Threshold 1
Version 1.13.3
Build Date 2023-06-06T18:12:37Z
Storage Type inmem
Cluster Name vault-cluster-488bbee6
Cluster ID 6fd0289e-dd56-af7f-c188-6f8ea08e3f2e
HA Enabled false
[root@mcw02 ~]# netstat -lntup|grep vault tcp 0 0 127.0.0.1:8200 0.0.0.0:* LISTEN 1945/vault tcp 0 0 127.0.0.1:8201 0.0.0.0:* LISTEN 1945/vault [root@mcw02 ~]# vault status WARNING! VAULT_ADDR and -address unset. Defaulting to https://127.0.0.1:8200. Error checking seal status: Get "https://127.0.0.1:8200/v1/sys/seal-status": http: server gave HTTP response to HTTPS client [root@mcw02 ~]# export VAULT_ADDR='http://127.0.0.1:8200' [root@mcw02 ~]# export VAULT_TOKEN="hvs.HPHBPfqKpbOUKJFOqTvdXPT6" [root@mcw02 ~]# vault status Key Value --- ----- Seal Type shamir Initialized true Sealed false Total Shares 1 Threshold 1 Version 1.16.2 Build Date 2024-04-22T16:25:54Z Storage Type inmem Cluster Name vault-cluster-85e02789 Cluster ID b6561f47-7fed-1417-6998-59962ec7c23e HA Enabled false [root@mcw02 ~]#
四、vault命令汇总
在开发模式下运行 Vault 时,Key/Value v2 机密引擎在 secret/ 路径下启用。Key/Value 机密引擎是一个通用的键值存储,用于在为 Vault 配置的物理存储中存储任意机密。写入 Vault 的秘密被加密,然后写入后端存储。因此,后端存储机制永远看不到未加密的值,也没有必要的手段在没有 Vault 的情况下对其进行解密。
Key/Value 机密引擎有版本 1 和 2。不同之处在于 v2 提供机密的版本控制,而 v1 不提供。
使用 vault kv [options] [args] 命令与 K/V 秘密引擎交互。
可用的子命令:
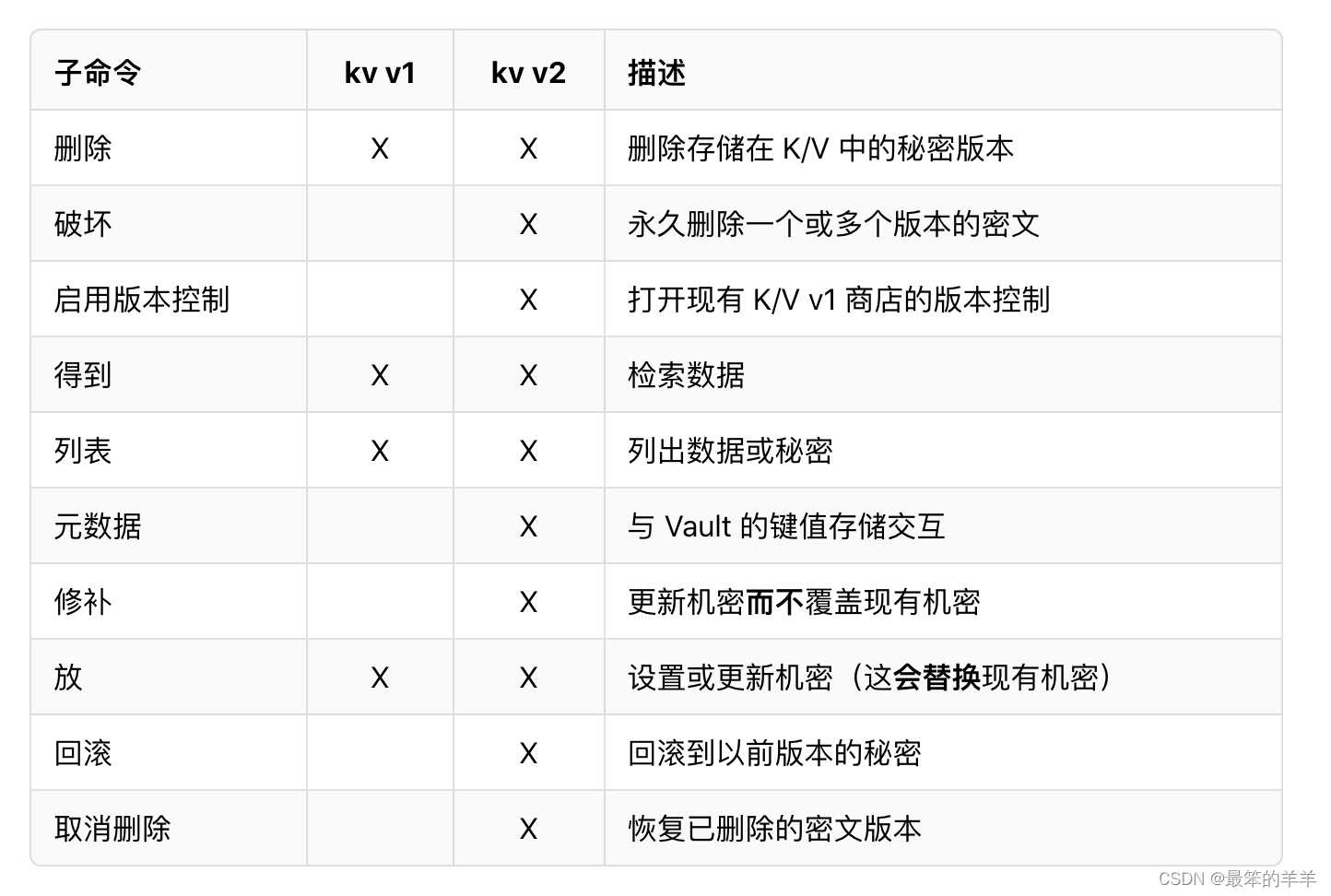
写入密码、读取密码、删除密码
一、写一个密码
现在,使用 vault kv put 命令对挂载路径 secret 写入一个键值 secret 到路径 hello ,键为 foo ,值为 world ,这是安装 KV v2 secrets 引擎的地方。此命令创建新版本的机密,并替换路径中任何预先存在的数据(如果有)。
[root@mcw02 ~]# vault kv put -mount=secret hello foo=world == Secret Path == secret/data/hello ======= Metadata ======= Key Value --- ----- created_time 2024-05-21T01:28:12.539206785Z custom_metadata <nil> deletion_time n/a destroyed false version 1 [root@mcw02 ~]# [root@mcw02 ~]# vault kv put -mount=secret hello foo=world excited=yes == Secret Path == secret/data/hello ======= Metadata ======= Key Value --- ----- created_time 2024-05-21T01:28:37.306367454Z custom_metadata <nil> deletion_time n/a destroyed false version 2 [root@mcw02 ~]# [root@mcw02 ~]# ls /data/ gv0 gv1 gv2 gv3 [root@mcw02 ~]#
请注意version现在是2。
二、读取密码
如您所料,可以使用 vault kv get 检索机密。
[root@mcw02 ~]# vault kv get -mount=secret hello == Secret Path == secret/data/hello ======= Metadata ======= Key Value --- ----- created_time 2024-05-21T01:28:37.306367454Z custom_metadata <nil> deletion_time n/a destroyed false version 2 ===== Data ===== Key Value --- ----- excited yes foo world [root@mcw02 ~]#
Vault 在 secret/hello 返回最新版本的秘密(在本例中为版本 2)。
要仅打印给定字段的值,请使用 -field=<key_name> 标志。
[root@mcw02 ~]# vault kv get -mount=secret -field=excited hello yes [root@mcw02 ~]#
可选的 JSON 输出对于脚本非常有用。例如,您可以使用 jq 工具来提取 excited secret 的值。
[root@mcw02 ~]# vault kv get -mount=secret -format=json hello { "request_id": "6805e2fb-2728-bc42-14ac-c4284bb23adc", "lease_id": "", "lease_duration": 0, "renewable": false, "data": { "data": { "excited": "yes", "foo": "world" }, "metadata": { "created_time": "2024-05-21T01:28:37.306367454Z", "custom_metadata": null, "deletion_time": "", "destroyed": false, "version": 2 } }, "warnings": null, "mount_type": "kv" } [root@mcw02 ~]# vault kv get -mount=secret -format=json hello | jq -r .data.data.excited yes [root@mcw02 ~]#
三、删除密码
现在你已经学会了如何读写一个秘密,让我们继续删除它。可以使用 vault kv delete 命令执行此操作。
[root@mcw02 ~]# vault kv delete -mount=secret hello Success! Data deleted (if it existed) at: secret/data/hello [root@mcw02 ~]#
尝试阅读刚刚删除的秘密。
[root@mcw02 ~]# vault kv get -mount=secret hello == Secret Path == secret/data/hello ======= Metadata ======= Key Value --- ----- created_time 2024-05-21T01:28:37.306367454Z custom_metadata <nil> deletion_time 2024-05-21T01:33:11.09269757Z destroyed false version 2 [root@mcw02 ~]#
输出仅显示具有 deletion_time 的元数据。一旦删除,它不会显示数据本身。请注意,destroyed 参数为 false,这意味着如果删除是无意的,您可以恢复已删除的数据。
[root@mcw02 ~]# vault kv undelete -mount=secret -versions=2 hello Success! Data written to: secret/undelete/hello [root@mcw02 ~]#
现在,数据已恢复。
[root@mcw02 ~]# vault kv get -mount=secret hello == Secret Path == secret/data/hello ======= Metadata ======= Key Value --- ----- created_time 2024-05-21T01:28:37.306367454Z custom_metadata <nil> deletion_time n/a destroyed false version 2 ===== Data ===== Key Value --- ----- excited yes foo world [root@mcw02 ~]#
使用python代码连接Vault服务器,存储密码、读取密码
一、创建Vault客户端
pip3 install hvac
初始化一个新的 Vault 客户端,该客户端将对其所有请求使用基于令牌的身份验证:
import hvac
import sys
client = hvac.Client(
url='http://127.0.0.1:8200',
token='hvs.BvXow4DjJ8VntB57DjQnd2hY',
)

二、存储密码
秘密是我们不应该存储在我们的代码或配置文件中的敏感数据,例如 API 密钥和密码。相反,我们希望在 Vault 中存储这样的值。
我们将使用刚刚初始化的 Vault 客户端向 Vault 写入密码,如下所示:
create_response = client.secrets.kv.v2.create_or_update_secret(
path='my-secret-password',
secret=dict(password='Hashi123'),
)
print('Secret written successfully.')
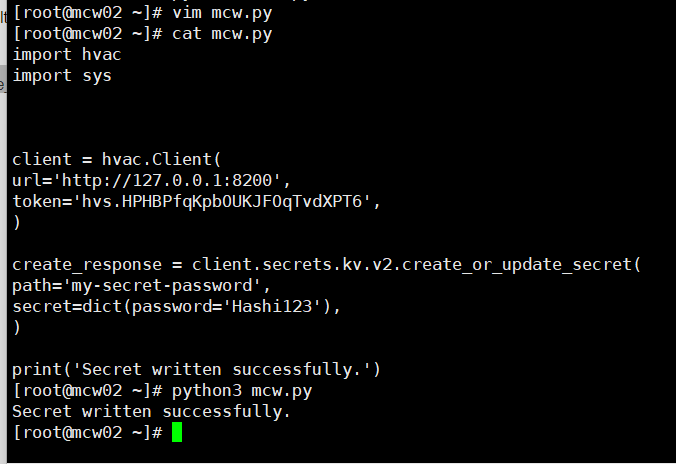
三、写入密码的完整代码
import hvac import sys client = hvac.Client( url='http://127.0.0.1:8200', token='hvs.HPHBPfqKpbOUKJFOqTvdXPT6', ) create_response = client.secrets.kv.v2.create_or_update_secret( path='my-secret-password', secret=dict(password='Hashi123'), ) print('Secret written successfully.')
四、命令行查看密码
执行代码后,命令行查看密码
新起一个终端,使用根令牌
export VAULT_ADDR='http://127.0.0.1:8200'
export VAULT_TOKEN="hvs.HPHBPfqKpbOUKJFOqTvdXPT6"
查看my-secret-password密码
[root@mcw02 ~]# vault kv get -mount=secret my-secret-password ========= Secret Path ========= secret/data/my-secret-password ======= Metadata ======= Key Value --- ----- created_time 2024-05-22T00:44:02.895434068Z custom_metadata <nil> deletion_time n/a destroyed false version 1 ====== Data ====== Key Value --- ----- password Hashi123 [root@mcw02 ~]#
五、使用代码查看密码
read_response = client.secrets.kv.read_secret_version(path='my-secret-password') password = read_response['data']['data']['password'] print(password) if password != 'Hashi123': sys.exit('unexpected password') print('Access granted!')
执行代码,输出如下所示:
Hashi123
Access granted!

Transit Secrets Engine
一、Transit Secrets Engine
传输机密引擎处理传输中数据的加密功能。 Vault 不存储发送到机密引擎的数据。也可以将其视为“密码学即服务”或“加密即服务”。 transit secrets 引擎还可以对数据进行签名和验证;生成数据的散列和 HMAC;并充当随机字节的来源。
传输的主要用例是加密来自应用程序的数据,同时仍将加密数据存储在一些主要数据存储中。这减轻了应用程序开发人员进行适当加密/解密的负担,并将负担推给了 Vault 的操作员。
支持密钥派生,通过基于用户提供的上下文值派生新密钥,允许将同一密钥用于多种用途。在这种模式下,可以选择支持收敛加密,允许相同的输入值产生相同的密文。
数据密钥生成允许进程请求返回给定位长度的高熵密钥,并使用命名密钥加密。通常这也会以明文形式返回密钥以允许立即使用,但可以禁用它以满足审计要求。
二、工作集管理
Transit 引擎支持密钥的版本控制。早于密钥指定的 min_decryption_version 的密钥版本被存档,其余密钥版本属于工作集。这是保持密钥快速加载的性能考虑,也是安全考虑:通过不允许解密旧版本密钥,发现大多数用户无法解密与过时(但敏感)数据对应的密文,但在紧急情况下min_decryption_version 可以移回以允许合法解密。
当前,此存档存储在单个存储条目中。对于某些存储后端,特别是那些使用 Raft 或 Paxos 实现 HA 功能的后端,频繁轮换可能会导致存档的存储条目大小大于存储后端可以处理的大小。对于频繁的轮换需求,使用与时间范围相对应的命名键(例如,五分钟的时间段为最接近的五的倍数)可能是一个很好的选择,允许多个键同时生效,并以一种确定性的方式来决定哪个键在任何给定时间使用。
三、NIST 轮换指南
建议定期轮换加密密钥,即使在没有妥协的情况下也是如此。对于 AES-GCM 密钥,按照 NIST 出版物 800-38D 的指导方针,旋转应该在密钥版本执行大约 232 次加密之前发生。建议操作员估计密钥的加密率,并使用它来确定防止达到指导限制的轮换频率。例如,如果确定估计速率为每天 4000 万次操作,则每三个月轮换一次密钥就足够了。
四、Key类型
截至目前,transit secrets 引擎支持以下密钥类型(所有密钥类型也会生成单独的 HMAC 密钥):
aes128-gcm96:具有 128 位 AES 密钥和 96 位随机数的 AES-GCM;支持加密、解密、密钥派生、收敛加密
aes256-gcm96:具有 256 位 AES 密钥和 96 位随机数的 AES-GCM;支持加密、解密、密钥派生、收敛加密(默认)
chacha20-poly1305:带有 256 位密钥的 ChaCha20-Poly1305;支持加密、解密、密钥派生、收敛加密
ed25519:Ed25519;支持签名、签名验证和密钥派生
ecdsa-p256:使用曲线 P-256 的 ECDSA;支持签名和签名验证
ecdsa-p384:使用曲线 P-384 的 ECDSA;支持签名和签名验证
ecdsa-p521:使用曲线 P-521 的 ECDSA;支持签名和签名验证
rsa-2048:2048 位 RSA 密钥;支持加密、解密、签名、验签
rsa-3072:3072 位 RSA 密钥;支持加密、解密、签名、验签
rsa-4096:4096 位 RSA 密钥;支持加密、解密、签名、验签
hmac: HMAC;支持 HMAC 生成和验证。
managed_key:托管密钥;支持多种操作,具体取决于后备密钥管理解决方案。有关详细信息,请参阅托管密钥。
注意:在 FIPS 140-2 模式下,以下算法未经认证,因此不应使用:chacha20-poly1305 和 ed25519。
注意:所有密钥类型都通过使用第二个随机生成的密钥创建密钥创建时间或轮换来支持 HMAC 操作。 HMAC 密钥类型仅支持 HMAC,并且在 HMAC 操作方面与其他算法的行为相同,但支持密钥导入。默认情况下,HMAC 密钥类型使用 256 位密钥。
RSA 操作使用以下方法之一:
OAEP(加密、解密),具有 SHA-256 哈希函数和 MGF,
PSS(签名、验证),具有也用于 MGF 的可配置哈希函数,以及
PKCS#1v1.5:(签名、验证),具有可配置的散列函数。
五、融合加密
收敛加密是一种相同的明文+上下文集合总是产生相同密文的模式。它通过使用密钥派生函数派生密钥以及确定性地派生随机数来实现这一点。由于这些属性对于大小为 2^256 的密钥空间上的明文和密文的任意组合都不同,因此随机数重用的风险接近于零。
这有很多实际用途。一种常见的使用模式是允许将值加密存储在数据库中,但具有有限的查找/查询支持,以便可以从查询返回特定字段具有相同值的行。
为了适应任何需要的算法升级,历史上支持不同版本的融合加密:
版本 1 要求客户端提供他们自己的随机数,这种方式非常灵活,但如果操作不当可能会很危险。这仅在 Vault 0.6.1 中,使用此版本的密钥无法升级。
版本 2 使用算法方法来导出参数。但是,所使用的算法容易受到离线明文确认攻击,如果明文较小,攻击者可能会暴力破解。使用版本 2 的密钥可以通过简单地执行到新密钥版本的旋转操作来升级;然后可以根据新密钥版本重新包装现有值,并将使用版本 3 算法。
版本 3 使用不同的算法来抵抗离线明文确认攻击。它类似于 AES-SIV,因为它使用 PRF 从明文生成随机数。
六、部署
大多数秘密引擎必须提前配置才能执行其功能。这些步骤通常由操作员或配置管理工具完成。
启用 Transit 秘密引擎:
[root@mcw02 ~]# vault secrets enable transit Success! Enabled the transit secrets engine at: transit/ [root@mcw02 ~]#
默认情况下,秘密引擎将安装在引擎的名称上。要在不同的路径启用秘密引擎,请使用 -path 参数。
创建一个命名的加密密钥:
vault write -f transit/keys/my-key
Success! Data written to: transit/keys/my-key
[root@mcw02 ~]# vault write -f transit/keys/my-key Key Value --- ----- allow_plaintext_backup false auto_rotate_period 0s deletion_allowed false derived false exportable false imported_key false keys map[1:1716393579] latest_version 1 min_available_version 0 min_decryption_version 1 min_encryption_version 0 name my-key supports_decryption true supports_derivation true supports_encryption true supports_signing false type aes256-gcm96 [root@mcw02 ~]#
通常每个应用程序都有自己的加密密钥。
七、使用
在配置了秘密引擎并且用户/机器拥有具有适当权限的 Vault 令牌后,它可以使用这个秘密引擎。
1.使用带有命名密钥的 /encrypt 端点加密一些明文数据:
注意:**所有明文数据都必须采用 base64 编码。之所以有这个要求,是因为 Vault 不要求明文是“文本”。它可以是二进制文件,例如 PDF 或图像。**作为 JSON 有效负载的一部分,此数据最简单的安全传输机制是对其进行 base64 编码。
vault write transit/encrypt/my-key plaintext=$(echo "my secret data" | base64)
Key Value
--- -----
ciphertext vault:v1:54d6PQ5i6jOWL/61cpEB4AKsJlZoJXHAhzhoHGRwLv+GOuweyKzfZQRuLw==
key_version 1
[root@mcw02 ~]# vault write transit/encrypt/my-key plaintext=$(echo "my secret data" | base64) Key Value --- ----- ciphertext vault:v1:mBjeXHGFxgEPd10yi1/booYvxOY58UaIA236J5bh3DhXRfQk8nJ193nUtA== key_version 1 [root@mcw02 ~]#
返回的密文以 vault:v1: 开头。第一个前缀 (vault) 标识它已被 Vault 包装。 v1 表示密钥版本 1 用于加密明文;因此,当您轮换密钥时,Vault 知道使用哪个版本进行解密。其余部分是初始化向量 (IV) 和密文的 base64 串联。
请注意,Vault 不存储任何此类数据。调用者负责存储加密后的密文。当调用者想要明文时,它必须将密文提供回 Vault 以解密该值。
Vault HTTP API 规定最大请求大小为 32MB 以防止拒绝服务攻击。这可以在 Vault 服务器配置中针对每个侦听器块进行调整。
2.使用带有命名密钥的 /decrypt 端点解密一段数据:
vault write transit/decrypt/my-key ciphertext=vault:v1:54d6PQ5i6jOWL/61cpEB4AKsJlZoJXHAhzhoHGRwLv+GOuweyKzfZQRuLw==
Key Value
--- -----
plaintext bXkgc2VjcmV0IGRhdGEK
[root@mcw02 ~]# vault write transit/encrypt/my-key plaintext=$(echo "my secret data" | base64) Key Value --- ----- ciphertext vault:v1:mBjeXHGFxgEPd10yi1/booYvxOY58UaIA236J5bh3DhXRfQk8nJ193nUtA== key_version 1 [root@mcw02 ~]# vault write transit/decrypt/my-key ciphertext=vault:v1:mBjeXHGFxgEPd10yi1/booYvxOY58UaIA236J5bh3DhXRfQk8nJ193nUtA== Key Value --- ----- plaintext bXkgc2VjcmV0IGRhdGEK [root@mcw02 ~]#
生成的数据是 base64 编码的(有关原因的详细信息,请参阅上面的注释)。对其进行解码以获得原始明文:
base64 --decode <<< "bXkgc2VjcmV0IGRhdGEK"
my secret data
[root@mcw02 ~]# base64 --decode <<<"bXkgc2VjcmV0IGRhdGEK" my secret data [root@mcw02 ~]#
也可以在一个命令中使用一些巧妙的 shell 脚本编写此解密脚本:
vault write -field=plaintext transit/decrypt/my-key ciphertext=vault:v1:54d6PQ5i6jOWL/61cpEB4AKsJlZoJXHAhzhoHGRwLv+GOuweyKzfZQRuLw== | base64 --decode
my secret data
[root@mcw02 ~]# vault write -field=plaintext transit/decrypt/my-key ciphertext=vault:v1:mBjeXHGFxgEPd10yi1/booYvxOY58UaIA236J5bh3DhXRfQk8nJ193nUtA== | base64 --decode
my secret data
[root@mcw02 ~]#
使用 ACL,可以限制传输秘密引擎的使用,以便受信任的操作员可以管理命名密钥,并且应用程序只能使用他们需要访问的命名密钥进行加密或解密。
3.轮换底层加密密钥。这将生成一个新的加密密钥并将其添加到指定密钥的密钥环中:
vault write -f transit/keys/my-key/rotate
Success! Data written to: transit/keys/my-key/rotate
[root@mcw02 ~]# vault write -f transit/keys/my-key/rotate Key Value --- ----- allow_plaintext_backup false auto_rotate_period 0s deletion_allowed false derived false exportable false imported_key false keys map[1:1716393579 2:1716394239] latest_version 2 min_available_version 0 min_decryption_version 1 min_encryption_version 0 name my-key supports_decryption true supports_derivation true supports_encryption true supports_signing false type aes256-gcm96 [root@mcw02 ~]#
未来的加密将使用这个新密钥。由于使用了密钥环,旧数据仍然可以被解密。
4.将已加密的数据升级为新密钥。 Vault 将使用密钥环中的适当密钥解密该值,然后使用密钥环中的最新密钥加密生成的明文。
vault write transit/rewrap/my-key ciphertext=vault:v1:54d6PQ5i6jOWL/61cpEB4AKsJlZoJXHAhzhoHGRwLv+GOuweyKzfZQRuLw==
Key Value
--- -----
ciphertext vault:v2:fhsQPtZtEns2j7ZXLn28EYWh5NF0tFk9i5fa0jq7qkNsft/ZEFlVook1pg==
key_version 2
[root@mcw02 ~]# vault write transit/rewrap/my-key ciphertext=vault:v1:mBjeXHGFxgEPd10yi1/booYvxOY58UaIA236J5bh3DhXRfQk8nJ193nUtA== Key Value --- ----- ciphertext vault:v2:DN1dD0XNGPv2iCsaYGO4UdFZF7m+3IfKIvKjl7FpC5U8HbruYO2aqcIdMQ== key_version 2 [root@mcw02 ~]#
此过程不会泄露明文数据。因此,Vault 策略可以授予几乎不受信任的进程“重新包装”加密数据的能力,因为该进程将无法访问明文数据。
八、自带钥匙 (BYOK)
注意:密钥导入功能支持需要从 HSM 或其他外部系统导入现有密钥的情况。让 Transit 在 Vault 中生成和管理密钥更加安全。
首先,需要从传输中读取包装密钥:
vault read transit/wrapping_key
[root@mcw02 ~]# vault read transit/wrapping_key Key Value --- ----- public_key -----BEGIN PUBLIC KEY----- MIICIjANBgkqhkiG9w0BAQEFAAOCAg8AMIICCgKCAgEAxKCPhPQzhhy9PfCkcq5+ uzpFYjUy4kKpUqClZNz+Oj9bVwYpZY0ePfCO0NPnoDQktXIq6svXob0KayT1Vp3d n/mEnQ7ALQQ5AL2f6J1cFbdw8fJ1/rq232Wi30f18mjCfGsk5ErWecDDqd1i2p8J yC9krE/F6Ll1Bvg3IXDsLE5PtP6vBBlz6Bfzk61wAYNY1wFhhZ5HK7UhqY0u2nwi jzcfRs37YxRbh4aHVpGkKN6mK+HEfsJfT88Q2y9FAU6yCQwdF6TAPzYknGPLEZBA Y50QlGkAuliPeerDXbrarrL4SwDQjKAsvLj2JkGV9Do2KgVVb6ZEmfbuiZ07yv1Y I4Lp+Ab8vlK1oUF3YOCsqpalvchJ7iXsJXLoNUo2saYi0TdZh0i94VJXx9/SSJxN gE02P/Mh4YE30VeRaps36yBM5vQwT2ngSGemUFG2h91zFYckz9f4E4MbmIENxrDV 9FbCk9UvB21hg/wNFzsjDuWUQviF6OQJWZQvg0zDM7y7moJydlWU8BBErINtZmG1 mG2hmimB9IpsJdmN0tJ1d0cwKDaSX0MRNoc/afOyWlnroVuE60yiPIF9dEJ6IMRC hPznw3f41cCvmEnBK9YiqGIOUupveP+NIKCPglrEj7XaVv5ZII7pflRxnqBzHwsH J0ZGJF+R6YzL8eOkoq6w2h8CAwEAAQ== -----END PUBLIC KEY----- [root@mcw02 ~]#
包装密钥将是一个 4096 位 RSA 公钥。
然后包装密钥用于为导入端点创建密文输入,如下所述。在下面,目标密钥是指正在导入的密钥。
HSM
如果密钥是从支持 PKCS#11 的 HSM 导入的,则有两种可能的情况:
- 如果 HSM 支持 CKM_RSA_AES_KEY_WRAP 机制,则可以使用包装密钥来包装目标密钥。
- 否则,可以结合两种机制来包装目标密钥。首先,应生成一个 256 位 AES 密钥,然后使用 CKM_AES_KEY_WRAP_KWP 机制将其用于包装目标密钥。然后,应使用 MGF1 和 SHA-1、SHA-224、SHA-256、SHA-384 或 SHA-512 使用 CKM_RSA_PKCS_OAEP 机制将 AES 密钥包装在包装密钥下。
密文是通过将包装的目标密钥附加到包装的 AES 密钥来构造的。
密文字节应该是 base64 编码的。
手动流程
如果目标密钥未存储在 HSM 或 KMS 中,则可以使用以下步骤为导入端点的输入构造密文:
生成一个临时的 256 位 AES 密钥。
使用带有 AES-KWP 的临时 AES 密钥包装目标密钥。
注意:包装对称密钥(例如 AES 或 ChaCha20 密钥)时,包装密钥的原始字节。例如,对于 AES 128 位密钥,这将是一个长度为 16 个字符的字节数组,将直接包装而不使用 base64 或其他编码。
包装非对称密钥(例如 RSA 或 ECDSA 密钥)时,以原始 DER/二进制格式包装此密钥的 PKCS8 编码格式。在加密之前不要将 PEM 编码应用于此 blob,也不要对其进行 base64 编码。
使用带有 MGF1 和 SHA-1、SHA-224、SHA-256、SHA-384 或 SHA-512 的 RSAES-OAEP 将 AES 密钥包装在 Vault 包装密钥下。
删除临时 AES 密钥。
将包装的目标密钥附加到包装的 AES 密钥。
Base64 编码结果。
二进制方式安装systemd管理并启动,页面登录
安装部分直接略过,我这里yum装的有/urs/bin/vault了
安装版本
vault 1.3.2
https://releases.hashicorp.com/vault/1.3.2/vault_1.3.2_linux_amd64.zip
开始安装
首先下载安装包
wget https://releases.hashicorp.com/vault/1.3.2/vault_1.3.2_linux_amd64.zip
解压安装包
unzip vault_1.3.2_linux_amd64.zip
移动文件vault到/usr/bin目录
mv vault /usr/bin
配置服务
创建service文件
vi /lib/systemd/system/vault.service
[Unit] Description=vault Requires=network-online.target After=network-online.target [Service] Restart=on-failure ExecStart=/usr/bin/vault server -config=/etc/vault/vault.json ExecStop=/usr/bin/vault step-down [Install] WantedBy=multi-user.target
创建vault启动配置文件
vi /etc/vault/vault.hcl
disable_mlock = true
ui = true
backend "file" {
path = "/var/lib/vault/file"
}
listener "tcp" {
address = "0.0.0.0:8200"
tls_disable = 1
}
api_addr = "http://0.0.0.0:8200"
启动服务
systemctl start vault
设置开机启动
systemctl enable vault
配置环境变量
vi /etc/profile
export VAULT_ADDR=http://127.0.0.1:8200
初始化vault
vault operator init -key-shares=5 -key-threshold=3 # -key-shares:指定密钥的总股数, # -key-threshold:指定需要几股可解锁 # 以上参数为默认,可不设置
解封vault,数据初始化的时候获取的5个密钥中的3个对Vault进行解封操作
vault operator unseal
@@@
查看yum安装的,服务配置
[root@mcw02 ~]# systemctl status vault ● vault.service - "HashiCorp Vault - A tool for managing secrets" Loaded: loaded (/usr/lib/systemd/system/vault.service; disabled; vendor preset: disabled) Active: inactive (dead) Docs: https://developer.hashicorp.com/vault/docs May 23 00:26:09 mcw02 systemd[1]: [/usr/lib/systemd/system/vault.service:7] Unknown lvalue 'StartLimitIntervalSec' in section 'Unit' May 23 00:26:09 mcw02 systemd[1]: [/usr/lib/systemd/system/vault.service:8] Unknown lvalue 'StartLimitBurst' in section 'Unit' [root@mcw02 ~]# cat /lib/systemd/system/vault.service [Unit] Description="HashiCorp Vault - A tool for managing secrets" Documentation=https://developer.hashicorp.com/vault/docs Requires=network-online.target After=network-online.target ConditionFileNotEmpty=/etc/vault.d/vault.hcl StartLimitIntervalSec=60 StartLimitBurst=3 [Service] Type=notify EnvironmentFile=/etc/vault.d/vault.env User=vault Group=vault ProtectSystem=full ProtectHome=read-only PrivateTmp=yes PrivateDevices=yes SecureBits=keep-caps AmbientCapabilities=CAP_IPC_LOCK CapabilityBoundingSet=CAP_SYSLOG CAP_IPC_LOCK NoNewPrivileges=yes ExecStart=/usr/bin/vault server -config=/etc/vault.d/vault.hcl ExecReload=/bin/kill --signal HUP $MAINPID KillMode=process KillSignal=SIGINT Restart=on-failure RestartSec=5 TimeoutStopSec=30 LimitNOFILE=65536 LimitMEMLOCK=infinity LimitCORE=0 [Install] WantedBy=multi-user.target [root@mcw02 ~]#
修改启动文件
[root@mcw02 ~]# cp /lib/systemd/system/vault.service . [root@mcw02 ~]# vim /lib/systemd/system/vault.service [root@mcw02 ~]# cat /lib/systemd/system/vault.service [Unit] Description=vault Requires=network-online.target After=network-online.target [Service] Restart=on-failure ExecStart=/usr/bin/vault server -config=/etc/vault/vault.json ExecStop=/usr/bin/vault step-down [Install] WantedBy=multi-user.target [root@mcw02 ~]#
创建配置文件
[root@mcw02 ~]# mkdir /etc/vault [root@mcw02 ~]# vim /etc/vault/vault.hcl [root@mcw02 ~]# cat /etc/vault/vault.hcl disable_mlock = true ui = true backend "file" { path = "/var/lib/vault/file" } listener "tcp" { address = "0.0.0.0:8200" tls_disable = 1 } api_addr = "http://0.0.0.0:8200" [root@mcw02 ~]#
启动
[root@mcw02 ~]# systemctl daemon-reload [root@mcw02 ~]# systemctl start vault [root@mcw02 ~]# vim /etc/profile [root@mcw02 ~]# tail -1 /etc/profile VAULT_ADDR=http://127.0.0.1:8200 [root@mcw02 ~]# systemctl status vault ● vault.service - vault Loaded: loaded (/usr/lib/systemd/system/vault.service; disabled; vendor preset: disabled) Active: failed (Result: start-limit) since Thu 2024-05-23 00:32:39 CST; 40s ago Process: 57295 ExecStop=/usr/bin/vault step-down (code=exited, status=127) Process: 57289 ExecStart=/usr/bin/vault server -config=/etc/vault/vault.json (code=exited, status=1/FAILURE) Main PID: 57289 (code=exited, status=1/FAILURE) May 23 00:32:39 mcw02 systemd[1]: vault.service: control process exited, code=exited status=127 May 23 00:32:39 mcw02 systemd[1]: Unit vault.service entered failed state. May 23 00:32:39 mcw02 systemd[1]: vault.service failed. May 23 00:32:39 mcw02 systemd[1]: vault.service holdoff time over, scheduling restart. May 23 00:32:39 mcw02 systemd[1]: start request repeated too quickly for vault.service May 23 00:32:39 mcw02 systemd[1]: Failed to start vault. May 23 00:32:39 mcw02 systemd[1]: Unit vault.service entered failed state. May 23 00:32:39 mcw02 systemd[1]: vault.service failed. [root@mcw02 ~]#
报错:
May 23 00:32:39 mcw02 systemd[1]: Starting vault... May 23 00:32:39 mcw02 vault[57289]: error loading configuration from /etc/vault/vault.json: stat /etc/vault/vault.json: no such file or directory May 23 00:32:39 mcw02 systemd[1]: vault.service: main process exited, code=exited, status=1/FAILURE May 23 00:32:39 mcw02 vault[57295]: Usage: vault <command> [args]
修改为正确的配置文件,然后重启,正常运行
[root@mcw02 ~]# vim /lib/systemd/system/vault.service [root@mcw02 ~]# cat /lib/systemd/system/vault.service [Unit] Description=vault Requires=network-online.target After=network-online.target [Service] Restart=on-failure ExecStart=/usr/bin/vault server -config=/etc/vault/vault.hcl ExecStop=/usr/bin/vault step-down [Install] WantedBy=multi-user.target [root@mcw02 ~]# systemctl restart vault Warning: vault.service changed on disk. Run 'systemctl daemon-reload' to reload units. [root@mcw02 ~]# systemctl daemon-reload [root@mcw02 ~]# systemctl restart vault [root@mcw02 ~]# systemctl status vault.service ● vault.service - vault Loaded: loaded (/usr/lib/systemd/system/vault.service; disabled; vendor preset: disabled) Active: active (running) since Thu 2024-05-23 00:36:53 CST; 7s ago Main PID: 57458 (vault) CGroup: /system.slice/vault.service └─57458 /usr/bin/vault server -config=/etc/vault/vault.hcl May 23 00:36:53 mcw02 vault[57458]: Mlock: supported: true, enabled: false May 23 00:36:53 mcw02 vault[57458]: Recovery Mode: false May 23 00:36:53 mcw02 vault[57458]: Storage: file May 23 00:36:53 mcw02 vault[57458]: Version: Vault v1.16.2, built 2024-04-22T16:25:54Z May 23 00:36:53 mcw02 vault[57458]: Version Sha: c6e4c2d4dc3b0d57791881b087c026e2f75a87cb May 23 00:36:53 mcw02 vault[57458]: ==> Vault server started! Log data will stream in below: May 23 00:36:53 mcw02 vault[57458]: 2024-05-23T00:36:53.847+0800 [INFO] proxy environment: http_proxy="" https_proxy="" no_proxy="" May 23 00:36:53 mcw02 vault[57458]: 2024-05-23T00:36:53.847+0800 [INFO] incrementing seal generation: generation=1 May 23 00:36:53 mcw02 vault[57458]: 2024-05-23T00:36:53.848+0800 [INFO] core: Initializing version history cache for core May 23 00:36:53 mcw02 vault[57458]: 2024-05-23T00:36:53.848+0800 [INFO] events: Starting event system [root@mcw02 ~]#
使用命令访问,source环境变量的不可以,但是加上地址参数可以使用命令
[root@mcw02 ~]# vault status WARNING! VAULT_ADDR and -address unset. Defaulting to https://127.0.0.1:8200. Error checking seal status: Get "https://127.0.0.1:8200/v1/sys/seal-status": http: server gave HTTP response to HTTPS client [root@mcw02 ~]# tail -1 /etc/profile VAULT_ADDR=http://127.0.0.1:8200 [root@mcw02 ~]# source /etc/profile [root@mcw02 ~]# vault status WARNING! VAULT_ADDR and -address unset. Defaulting to https://127.0.0.1:8200. Error checking seal status: Get "https://127.0.0.1:8200/v1/sys/seal-status": http: server gave HTTP response to HTTPS client [root@mcw02 ~]# vault status -address='http://127.0.0.1:8200' WARNING! VAULT_ADDR and -address unset. Defaulting to https://127.0.0.1:8200. Key Value --- ----- Seal Type shamir Initialized false Sealed true Total Shares 0 Threshold 0 Unseal Progress 0/0 Unseal Nonce n/a Version 1.16.2 Build Date 2024-04-22T16:25:54Z Storage Type file HA Enabled false [root@mcw02 ~]#
上面是因为缺少了export ,导致无法使用命令,必须接地址:
[root@mcw02 ~]# tail -1 /etc/profile VAULT_ADDR=http://127.0.0.1:8200 [root@mcw02 ~]# vim /etc/profile [root@mcw02 ~]# tail -1 /etc/profile export VAULT_ADDR=http://127.0.0.1:8200 [root@mcw02 ~]# source /etc/profile [root@mcw02 ~]# vault status Key Value --- ----- Seal Type shamir Initialized false Sealed true Total Shares 0 Threshold 0 Unseal Progress 0/0 Unseal Nonce n/a Version 1.16.2 Build Date 2024-04-22T16:25:54Z Storage Type file HA Enabled false [root@mcw02 ~]#
页面可以正常访问,现在
初始化vault
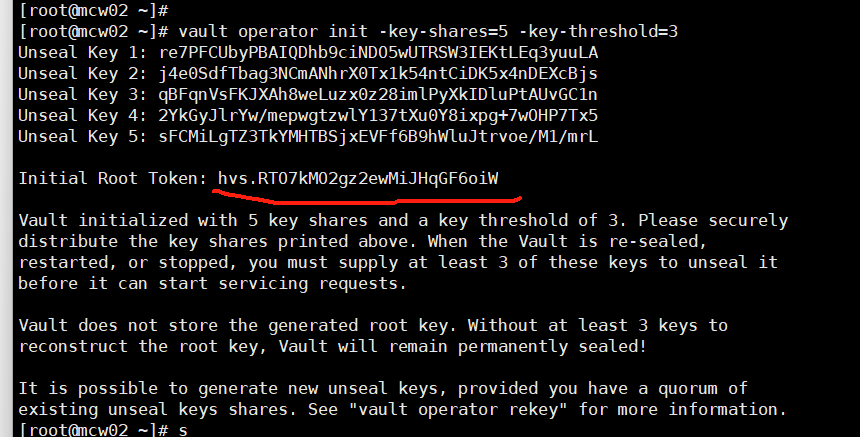
[root@mcw02 ~]# vault operator init -key-shares=5 -key-threshold=3 Unseal Key 1: re7PFCUbyPBAIQDhb9ciNDO5wUTRSW3IEKtLEq3yuuLA Unseal Key 2: j4e0SdfTbag3NCmANhrX0Tx1k54ntCiDK5x4nDEXcBjs Unseal Key 3: qBFqnVsFKJXAh8weLuzx0z28imlPyXkIDluPtAUvGC1n Unseal Key 4: 2YkGyJlrYw/mepwgtzwlY137tXu0Y8ixpg+7wOHP7Tx5 Unseal Key 5: sFCMiLgTZ3TkYMHTBSjxEVFf6B9hWluJtrvoe/M1/mrL Initial Root Token: hvs.RTO7kMO2gz2ewMiJHqGF6oiW Vault initialized with 5 key shares and a key threshold of 3. Please securely distribute the key shares printed above. When the Vault is re-sealed, restarted, or stopped, you must supply at least 3 of these keys to unseal it before it can start servicing requests. Vault does not store the generated root key. Without at least 3 keys to reconstruct the root key, Vault will remain permanently sealed! It is possible to generate new unseal keys, provided you have a quorum of existing unseal keys shares. See "vault operator rekey" for more information. [root@mcw02 ~]#
再次访问:

使用命令初始化的5个密钥中的第一个,上面初始化命令下可以看到这5个密钥,进行解封,可以看到进程是1/3,还需要两个,执行两次
[root@mcw02 ~]# vault operator unseal Unseal Key (will be hidden): Key Value --- ----- Seal Type shamir Initialized true Sealed true Total Shares 5 Threshold 3 Unseal Progress 1/3 Unseal Nonce 0c4f2aed-a6b1-7437-f854-edbeef84f5fb Version 1.16.2 Build Date 2024-04-22T16:25:54Z Storage Type file HA Enabled false [root@mcw02 ~]#
访问页面,也显示了解封进度

解封三次,完成
[root@mcw02 ~]# vault operator unseal Unseal Key (will be hidden): Key Value --- ----- Seal Type shamir Initialized true Sealed true Total Shares 5 Threshold 3 Unseal Progress 2/3 Unseal Nonce 0c4f2aed-a6b1-7437-f854-edbeef84f5fb Version 1.16.2 Build Date 2024-04-22T16:25:54Z Storage Type file HA Enabled false [root@mcw02 ~]# vault operator unseal Unseal Key (will be hidden): Key Value --- ----- Seal Type shamir Initialized true Sealed false Total Shares 5 Threshold 3 Version 1.16.2 Build Date 2024-04-22T16:25:54Z Storage Type file Cluster Name vault-cluster-c76eee89 Cluster ID 5e02f5ad-8e66-1462-51a7-e34bd5411c96 HA Enabled false [root@mcw02 ~]#
页面变成这样了,可以用token访问
还有其它登录方式:
初始化vault的时候,不只是有key,还有token,使用它登录下
成功登录页面
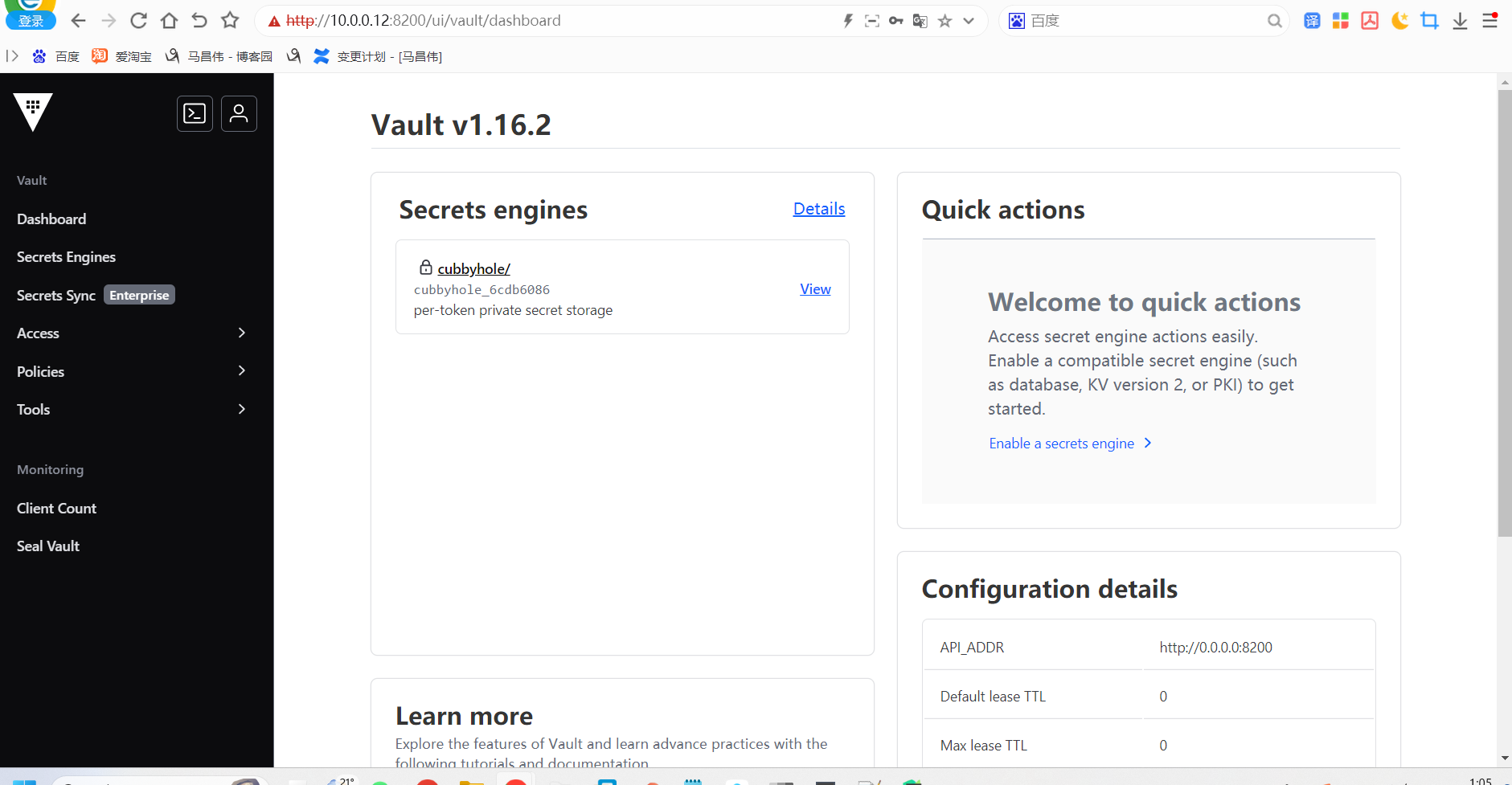
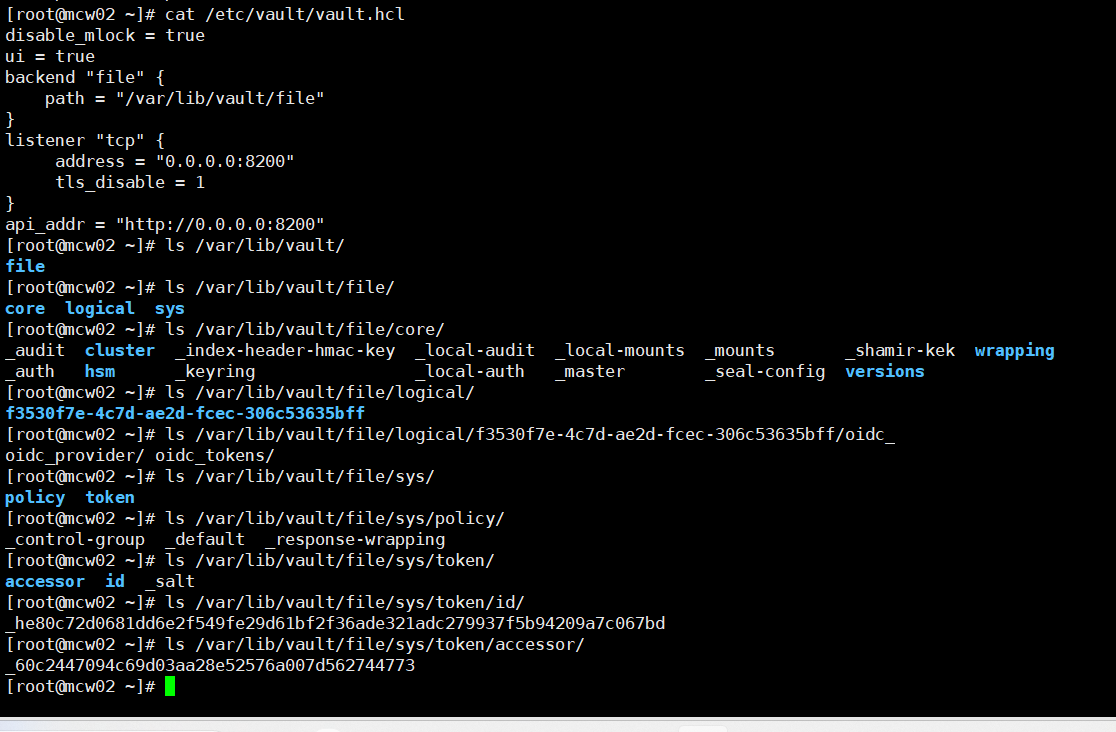
vault页面查看


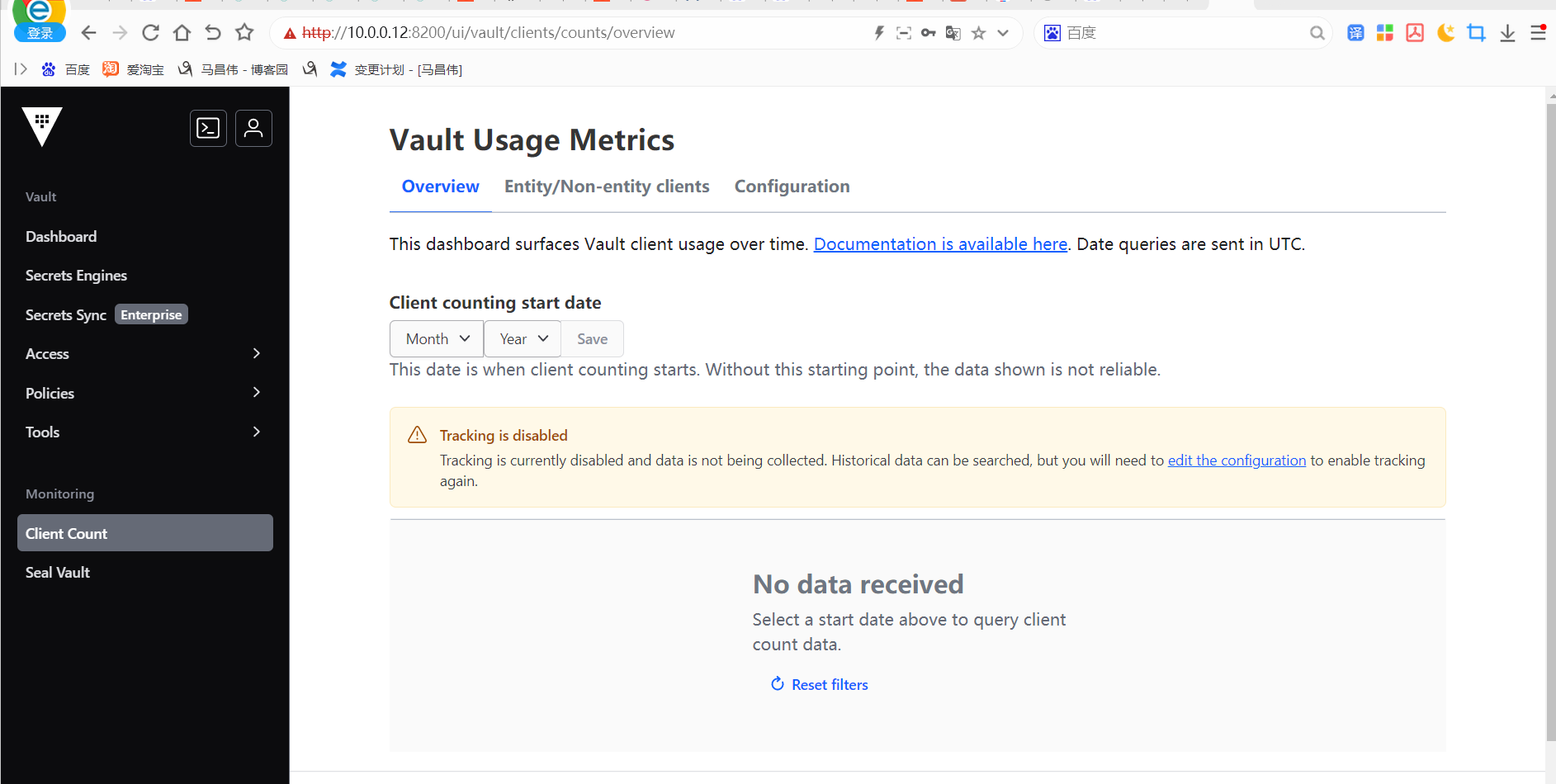
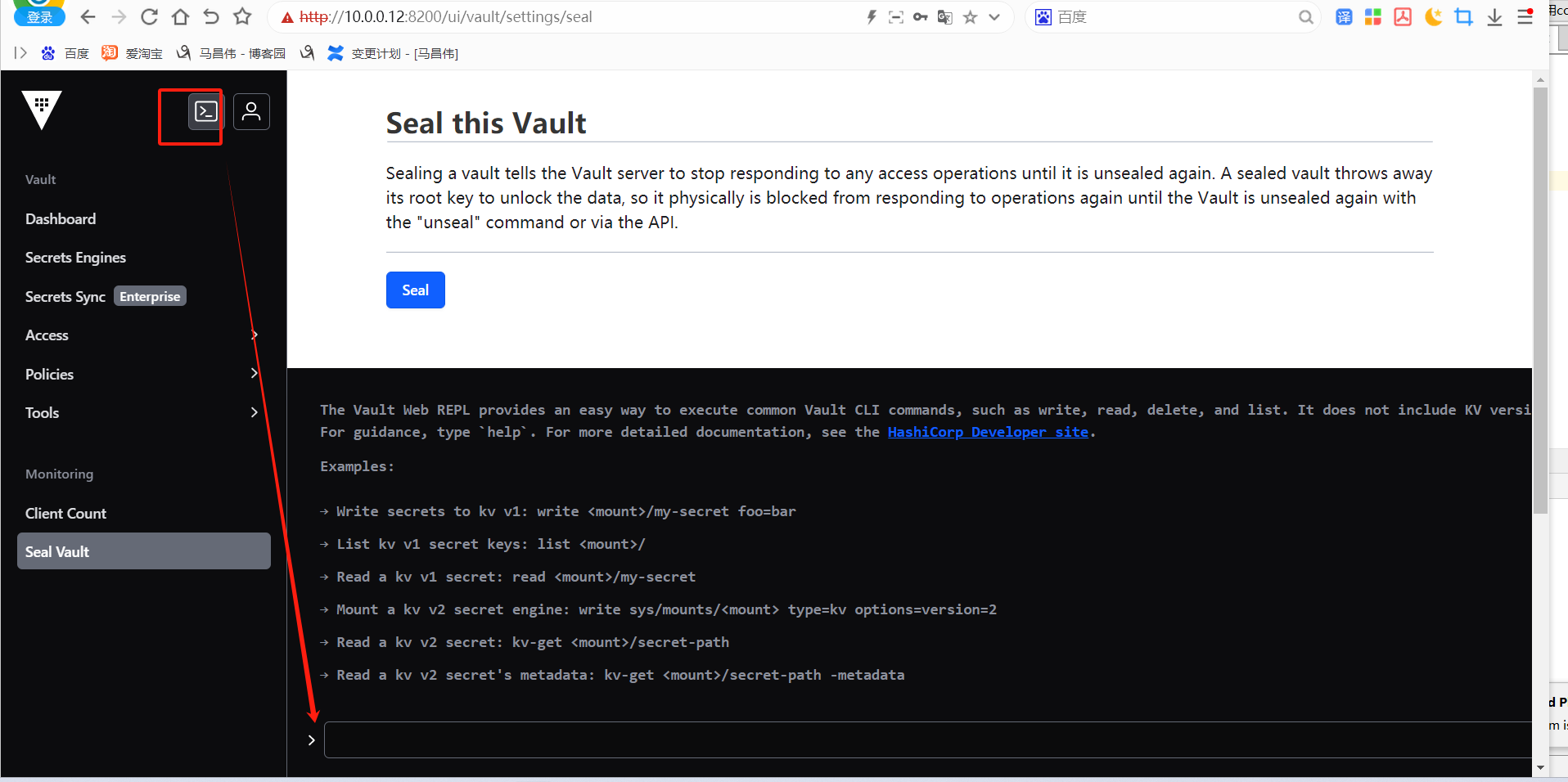
→ Write secrets to kv v1: write <mount>/my-secret foo=bar
→ List kv v1 secret keys: list <mount>/
→ Read a kv v1 secret: read <mount>/my-secret
→ Mount a kv v2 secret engine: write sys/mounts/<mount> type=kv options=version=2
→ Read a kv v2 secret: kv-get <mount>/secret-path
→ Read a kv v2 secret's metadata: kv-get <mount>/secret-path -metadata
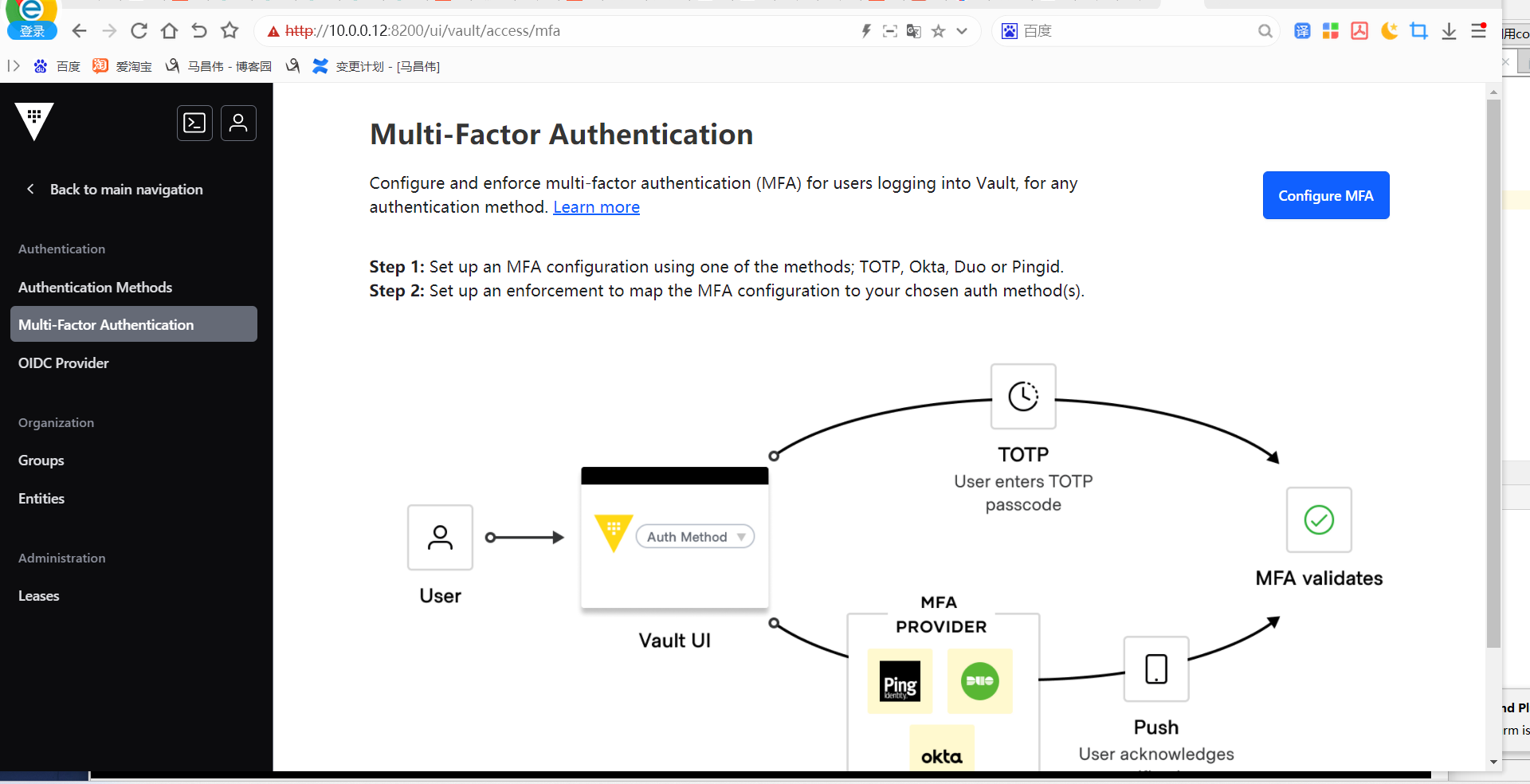
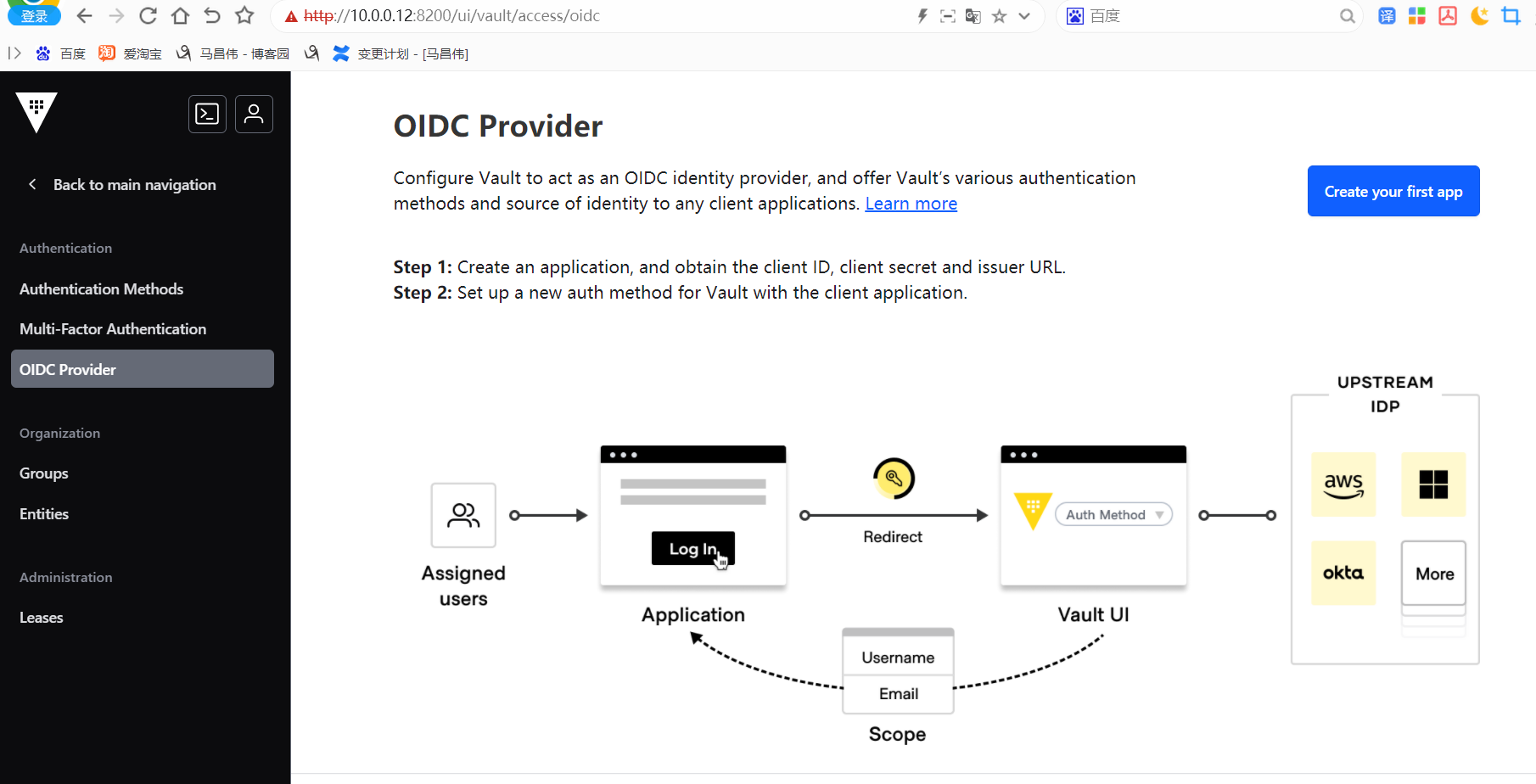



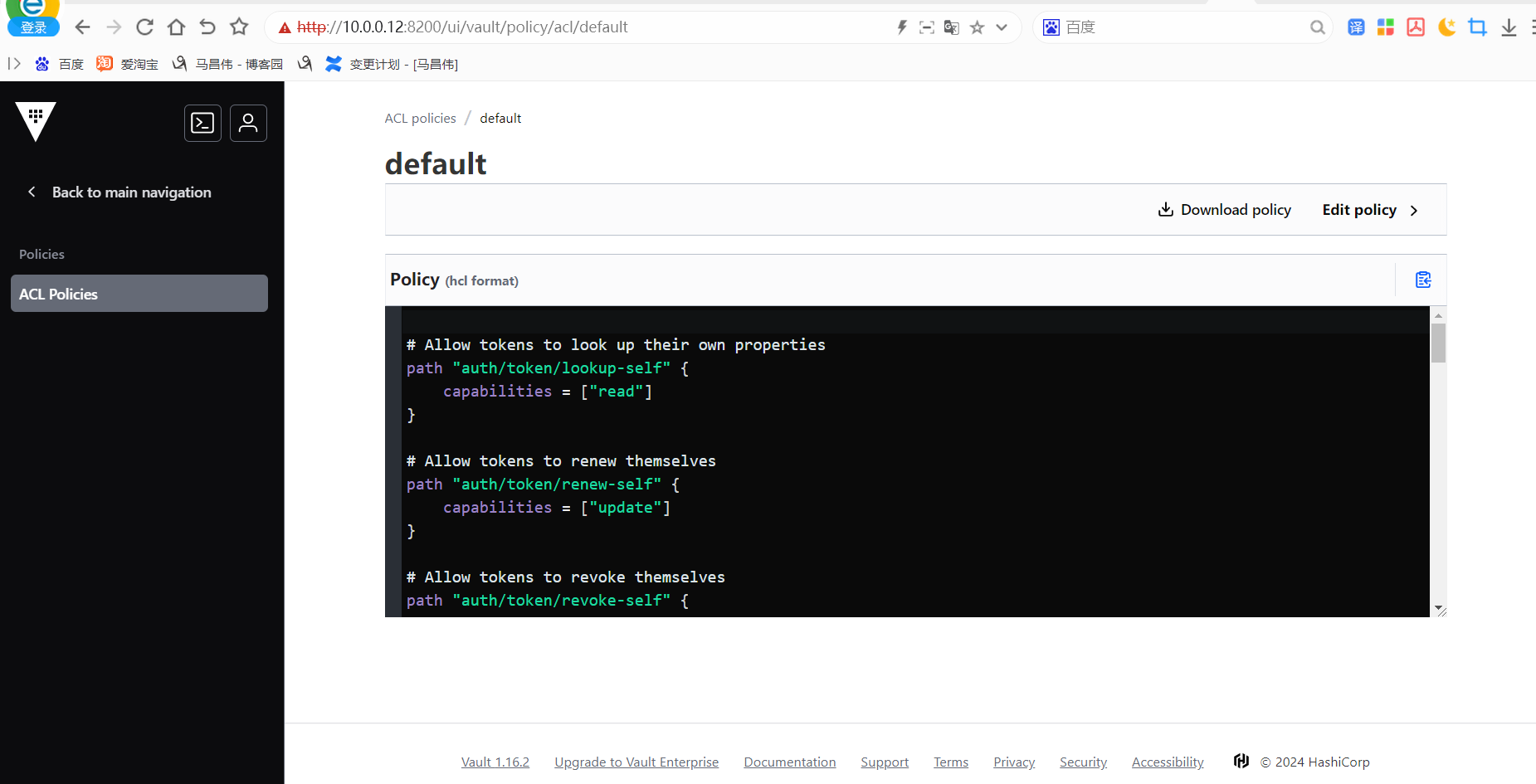
# Allow tokens to look up their own properties path "auth/token/lookup-self" { capabilities = ["read"] } # Allow tokens to renew themselves path "auth/token/renew-self" { capabilities = ["update"] } # Allow tokens to revoke themselves path "auth/token/revoke-self" { capabilities = ["update"] } # Allow a token to look up its own capabilities on a path path "sys/capabilities-self" { capabilities = ["update"] } # Allow a token to look up its own entity by id or name path "identity/entity/id/{{identity.entity.id}}" { capabilities = ["read"] } path "identity/entity/name/{{identity.entity.name}}" { capabilities = ["read"] } # Allow a token to look up its resultant ACL from all policies. This is useful # for UIs. It is an internal path because the format may change at any time # based on how the internal ACL features and capabilities change. path "sys/internal/ui/resultant-acl" { capabilities = ["read"] } # Allow a token to renew a lease via lease_id in the request body; old path for # old clients, new path for newer path "sys/renew" { capabilities = ["update"] } path "sys/leases/renew" { capabilities = ["update"] } # Allow looking up lease properties. This requires knowing the lease ID ahead # of time and does not divulge any sensitive information. path "sys/leases/lookup" { capabilities = ["update"] } # Allow a token to manage its own cubbyhole path "cubbyhole/*" { capabilities = ["create", "read", "update", "delete", "list"] } # Allow a token to wrap arbitrary values in a response-wrapping token path "sys/wrapping/wrap" { capabilities = ["update"] } # Allow a token to look up the creation time and TTL of a given # response-wrapping token path "sys/wrapping/lookup" { capabilities = ["update"] } # Allow a token to unwrap a response-wrapping token. This is a convenience to # avoid client token swapping since this is also part of the response wrapping # policy. path "sys/wrapping/unwrap" { capabilities = ["update"] } # Allow general purpose tools path "sys/tools/hash" { capabilities = ["update"] } path "sys/tools/hash/*" { capabilities = ["update"] } # Allow checking the status of a Control Group request if the user has the # accessor path "sys/control-group/request" { capabilities = ["update"] } # Allow a token to make requests to the Authorization Endpoint for OIDC providers. path "identity/oidc/provider/+/authorize" { capabilities = ["read", "update"] }




生产中使用配置案例,以及使用consul作为存储
原文链接:https://blog.csdn.net/zhengzaifeidelushang/article/details/131283430
原文链接:https://blog.csdn.net/zhengzaifeidelushang/article/details/131286740
原文链接:https://blog.csdn.net/zhengzaifeidelushang/article/details/131287041
https://blog.csdn.net/zhengzaifeidelushang/article/details/131287833
https://blog.csdn.net/zhengzaifeidelushang/article/details/131291390






【推荐】国内首个AI IDE,深度理解中文开发场景,立即下载体验Trae
【推荐】编程新体验,更懂你的AI,立即体验豆包MarsCode编程助手
【推荐】抖音旗下AI助手豆包,你的智能百科全书,全免费不限次数
【推荐】轻量又高性能的 SSH 工具 IShell:AI 加持,快人一步
· 无需6万激活码!GitHub神秘组织3小时极速复刻Manus,手把手教你使用OpenManus搭建本
· C#/.NET/.NET Core优秀项目和框架2025年2月简报
· 什么是nginx的强缓存和协商缓存
· 一文读懂知识蒸馏
· Manus爆火,是硬核还是营销?
2019-05-21 mysql命令.md
2019-05-21 mysql数据库命令大全