ssl协议存在弱加密算法修复,禁用低版本的TLS
验证用网站:https://www.ssleye.com/ssltool/cipher_suites.html
https://www.site24x7.com/zhcn/tools/tls-checker.html
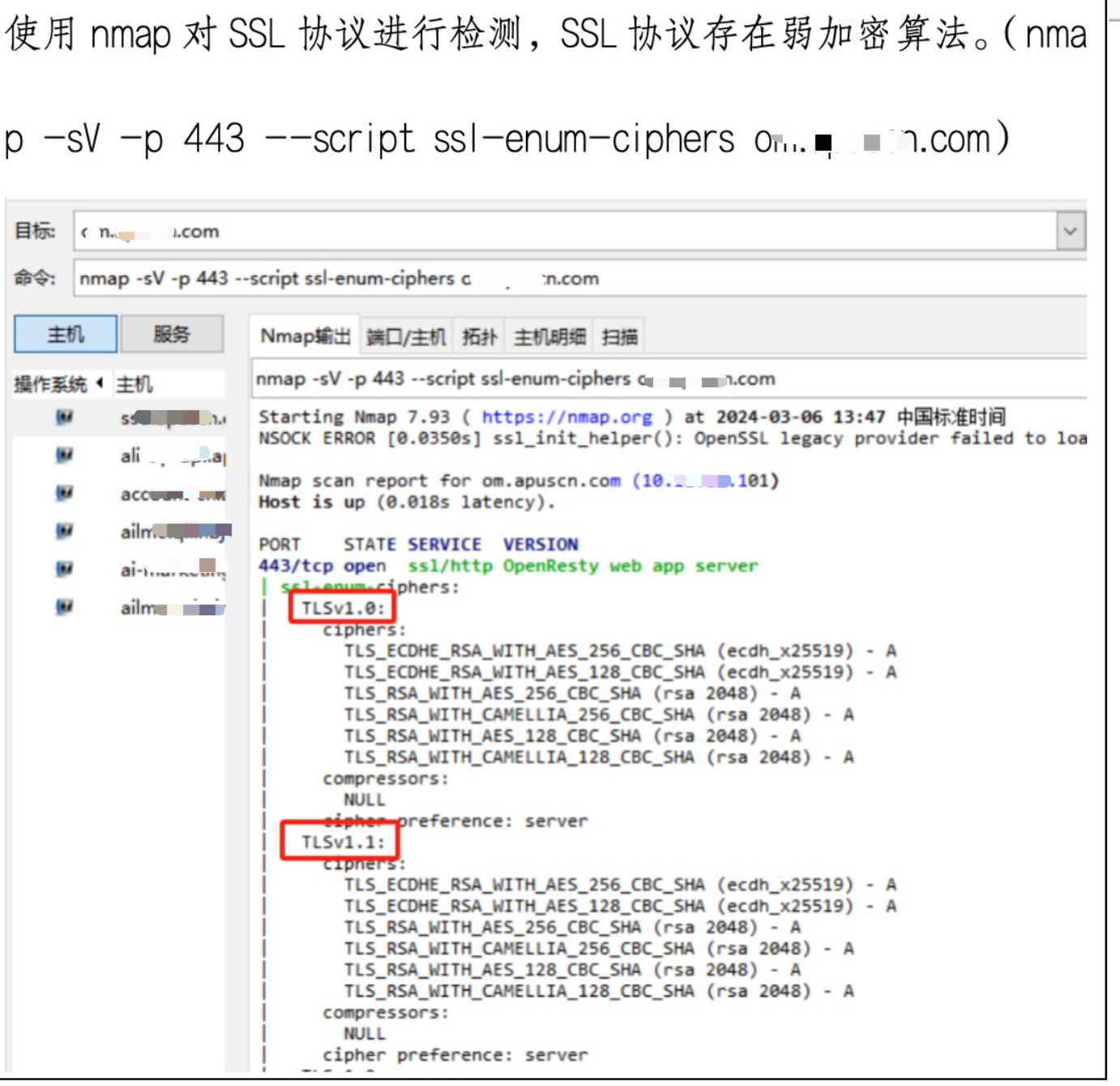
使用 nmap 对 SSL 协议进行检测,SSL协议存在弱加密算法。( nma
-sV -p 443--script ssl-enum-ciphers om.apuscn.com)
# nmap -sV -p 443 --script ssl-enum-ciphers cax.xx.cn Starting Nmap 6.40 ( http://nmap.org ) at 2024-03-12 14:55 CST Nmap scan report for cax.xx.cn (10x.xx.x.x2) Host is up (0.013s latency). Other addresses for cax.xx.cn (not scanned): 10x.x.xx.234 PORT STATE SERVICE VERSION 443/tcp open ssl/https? | ssl-enum-ciphers: | SSLv3: No supported ciphers found | TLSv1.0: | ciphers: | TLS_RSA_WITH_AES_128_CBC_SHA - strong | TLS_RSA_WITH_AES_256_CBC_SHA - strong | TLS_RSA_WITH_CAMELLIA_128_CBC_SHA - strong | TLS_RSA_WITH_CAMELLIA_256_CBC_SHA - strong | compressors: | NULL | TLSv1.1: | ciphers: | TLS_RSA_WITH_AES_128_CBC_SHA - strong | TLS_RSA_WITH_AES_256_CBC_SHA - strong | TLS_RSA_WITH_CAMELLIA_128_CBC_SHA - strong | TLS_RSA_WITH_CAMELLIA_256_CBC_SHA - strong | compressors: | NULL | TLSv1.2: | ciphers: | TLS_RSA_WITH_AES_128_CBC_SHA - strong | TLS_RSA_WITH_AES_128_CBC_SHA256 - strong | TLS_RSA_WITH_AES_128_CCM - strong | TLS_RSA_WITH_AES_128_CCM_8 - strong | TLS_RSA_WITH_AES_128_GCM_SHA256 - strong | TLS_RSA_WITH_AES_256_CBC_SHA - strong | TLS_RSA_WITH_AES_256_CBC_SHA256 - strong | TLS_RSA_WITH_AES_256_CCM - strong | TLS_RSA_WITH_AES_256_CCM_8 - strong | TLS_RSA_WITH_AES_256_GCM_SHA384 - strong | TLS_RSA_WITH_ARIA_128_GCM_SHA256 - strong | TLS_RSA_WITH_ARIA_256_GCM_SHA384 - strong | TLS_RSA_WITH_CAMELLIA_128_CBC_SHA - strong | TLS_RSA_WITH_CAMELLIA_128_CBC_SHA256 - strong | TLS_RSA_WITH_CAMELLIA_256_CBC_SHA - strong | TLS_RSA_WITH_CAMELLIA_256_CBC_SHA256 - strong | compressors: | NULL |_ least strength: strong 1 service unrecognized despite returning data. If you know the service/version, please submit the following fingerprint at http://www.insecure.org/cgi-bin/servicefp-submit.cgi : SF-Port443-TCP:V=6.40%T=SSL%I=7%D=3/12%Time=65EFFC5F%P=x86_64-redhat-linux SF:-gnu%r(GetRequest,CC,"HTTP/1\.1\x20404\x20Not\x20Found\r\nServer:\x20op SF:enresty\r\nDate:\x20Tue,\x2012\x20Mar\x202024\x2006:55:27\x20GMT\r\nCon SF:tent-Type:\x20text/html;\x20charset=UTF-8\r\nConnection:\x20close\r\nVa SF:ry:\x20Accept-Encoding\r\nAccess-Control-Allow-Credentials:\x20true\r\n SF:\r\n")%r(HTTPOptions,CC,"HTTP/1\.1\x20404\x20Not\x20Found\r\nServer:\x2 SF:0openresty\r\nDate:\x20Tue,\x2012\x20Mar\x202024\x2006:55:33\x20GMT\r\n SF:Content-Type:\x20text/html;\x20charset=UTF-8\r\nConnection:\x20close\r\ SF:nVary:\x20Accept-Encoding\r\nAccess-Control-Allow-Credentials:\x20true\ SF:r\n\r\n")%r(RTSPRequest,9A,"<html>\r\n<head><title>400\x20Bad\x20Reques SF:t</title></head>\r\n<body>\r\n<center><h1>400\x20Bad\x20Request</h1></c SF:enter>\r\n<hr><center>openresty</center>\r\n</body>\r\n</html>\r\n")%r( SF:RPCCheck,12F,"HTTP/1\.1\x20400\x20Bad\x20Request\r\nServer:\x20openrest SF:y\r\nDate:\x20Tue,\x2012\x20Mar\x202024\x2006:55:33\x20GMT\r\nContent-T SF:ype:\x20text/html\r\nContent-Length:\x20154\r\nConnection:\x20close\r\n SF:\r\n<html>\r\n<head><title>400\x20Bad\x20Request</title></head>\r\n<bod SF:y>\r\n<center><h1>400\x20Bad\x20Request</h1></center>\r\n<hr><center>op SF:enresty</center>\r\n</body>\r\n</html>\r\n")%r(DNSVersionBindReq,12F,"H SF:TTP/1\.1\x20400\x20Bad\x20Request\r\nServer:\x20openresty\r\nDate:\x20T SF:ue,\x2012\x20Mar\x202024\x2006:55:33\x20GMT\r\nContent-Type:\x20text/ht SF:ml\r\nContent-Length:\x20154\r\nConnection:\x20close\r\n\r\n<html>\r\n< SF:head><title>400\x20Bad\x20Request</title></head>\r\n<body>\r\n<center>< SF:h1>400\x20Bad\x20Request</h1></center>\r\n<hr><center>openresty</center SF:>\r\n</body>\r\n</html>\r\n")%r(DNSStatusRequest,12F,"HTTP/1\.1\x20400\ SF:x20Bad\x20Request\r\nServer:\x20openresty\r\nDate:\x20Tue,\x2012\x20Mar SF:\x202024\x2006:55:33\x20GMT\r\nContent-Type:\x20text/html\r\nContent-Le SF:ngth:\x20154\r\nConnection:\x20close\r\n\r\n<html>\r\n<head><title>400\ SF:x20Bad\x20Request</title></head>\r\n<body>\r\n<center><h1>400\x20Bad\x2 SF:0Request</h1></center>\r\n<hr><center>openresty</center>\r\n</body>\r\n SF:</html>\r\n")%r(Help,12F,"HTTP/1\.1\x20400\x20Bad\x20Request\r\nServer: SF:\x20openresty\r\nDate:\x20Tue,\x2012\x20Mar\x202024\x2006:55:33\x20GMT\ SF:r\nContent-Type:\x20text/html\r\nContent-Length:\x20154\r\nConnection:\ SF:x20close\r\n\r\n<html>\r\n<head><title>400\x20Bad\x20Request</title></h SF:ead>\r\n<body>\r\n<center><h1>400\x20Bad\x20Request</h1></center>\r\n<h SF:r><center>openresty</center>\r\n</body>\r\n</html>\r\n"); Service detection performed. Please report any incorrect results at http://nmap.org/submit/ . Nmap done: 1 IP address (1 host up) scanned in 27.18 seconds
修复建议:
修复建议: 1.打开Nginx配置文件: sudo nano /etc/nginx/nginx.conf 2.在配置文件中找到SSL配置部分。通常在server块中的location块中配置SSL。您需要确保以下配置中包含了安全的TLS版本和密码套件。 停用不安全的TLS版本: ssl_protocols TLSv1.2 TLSv1.3; 这将仅启用TLS 1.2和1.3版本,而禁用TLS 1.0和1.1版本。 停用弱密码套件和加密算法: ssl_ciphers 'TLS_AES_128_GCM_SHA256:TLS_AES_256_GCM_SHA384:ECDHE-RSA-AES128-GCM-SHA256:ECDHE-RSA-AES256-GCM-SHA384:ECDHE-RSA-AES256-SHA384:ECDHE-RSA-AES128-SHA256:!DES:!RC4:!MD5:!3DES'; 这将配置Nginx使用更安全的密码套件,以及支持前向安全性的ECDHE(椭圆曲线Diffie-Hellman)密钥交换。 3.重新加载Nginx配置以使更改生效: sudo systemctl reload nginx
修改配置:注意ssl_protocols和ssl_ciphers的值需要加上引号
git:(machangwei5) cat rewrite/2gexxch-ssl ssl_certificate ssl/gx x x.cn.crt; ssl_certificate_key ssl/xxx.cn.key; ssl_session_timeout 5m; ssl_protocols 'TLSv1.2'; ssl_ciphers 'Hxxxxxxxxxx5'; ssl_prefer_server_ciphers on;
效果如下
# nmap -sV -p 443 --script ssl-enum-ciphers machangweitest.xxxh.cn Starting Nmap 6.40 ( http://nmap.org ) at 2024-03-13 10:18 CST Nmap scan report for machangweitest.xxx.cn (10x.x.x.32) Host is up (0.013s latency). PORT STATE SERVICE VERSION 443/tcp open ssl/https? | ssl-enum-ciphers: |_ SSLv3: No supported ciphers found 1 service unrecognized despite returning data. If you know the service/version, please submit the following fingerprint at http://www.insecure.org/cgi-bin/servicefp-submit.cgi : SF-Port443-TCP:V=6.40%T=SSL%I=7%D=3/13%Time=65F10D1C%P=x86_64-redhat-linux SF:-gnu%r(GetRequest,CC,"HTTP/1\.1\x20404\x20Not\x20Found\r\nServer:\x20op SF:enresty\r\nDate:\x20Wed,\x2013\x20Mar\x202024\x2002:19:08\x20GMT\r\nCon SF:tent-Type:\x20text/html;\x20charset=UTF-8\r\nConnection:\x20close\r\nVa SF:ry:\x20Accept-Encoding\r\nAccess-Control-Allow-Credentials:\x20true\r\n SF:\r\n")%r(HTTPOptions,CC,"HTTP/1\.1\x20404\x20Not\x20Found\r\nServer:\x2 SF:0openresty\r\nDate:\x20Wed,\x2013\x20Mar\x202024\x2002:19:13\x20GMT\r\n SF:Content-Type:\x20text/html;\x20charset=UTF-8\r\nConnection:\x20close\r\ SF:nVary:\x20Accept-Encoding\r\nAccess-Control-Allow-Credentials:\x20true\ SF:r\n\r\n")%r(RTSPRequest,9A,"<html>\r\n<head><title>400\x20Bad\x20Reques SF:t</title></head>\r\n<body>\r\n<center><h1>400\x20Bad\x20Request</h1></c SF:enter>\r\n<hr><center>openresty</center>\r\n</body>\r\n</html>\r\n")%r( SF:RPCCheck,12F,"HTTP/1\.1\x20400\x20Bad\x20Request\r\nServer:\x20openrest SF:y\r\nDate:\x20Wed,\x2013\x20Mar\x202024\x2002:19:13\x20GMT\r\nContent-T SF:ype:\x20text/html\r\nContent-Length:\x20154\r\nConnection:\x20close\r\n SF:\r\n<html>\r\n<head><title>400\x20Bad\x20Request</title></head>\r\n<bod SF:y>\r\n<center><h1>400\x20Bad\x20Request</h1></center>\r\n<hr><center>op SF:enresty</center>\r\n</body>\r\n</html>\r\n")%r(DNSVersionBindReq,12F,"H SF:TTP/1\.1\x20400\x20Bad\x20Request\r\nServer:\x20openresty\r\nDate:\x20W SF:ed,\x2013\x20Mar\x202024\x2002:19:13\x20GMT\r\nContent-Type:\x20text/ht SF:ml\r\nContent-Length:\x20154\r\nConnection:\x20close\r\n\r\n<html>\r\n< SF:head><title>400\x20Bad\x20Request</title></head>\r\n<body>\r\n<center>< SF:h1>400\x20Bad\x20Request</h1></center>\r\n<hr><center>openresty</center SF:>\r\n</body>\r\n</html>\r\n")%r(DNSStatusRequest,12F,"HTTP/1\.1\x20400\ SF:x20Bad\x20Request\r\nServer:\x20openresty\r\nDate:\x20Wed,\x2013\x20Mar SF:\x202024\x2002:19:13\x20GMT\r\nContent-Type:\x20text/html\r\nContent-Le SF:ngth:\x20154\r\nConnection:\x20close\r\n\r\n<html>\r\n<head><title>400\ SF:x20Bad\x20Request</title></head>\r\n<body>\r\n<center><h1>400\x20Bad\x2 SF:0Request</h1></center>\r\n<hr><center>openresty</center>\r\n</body>\r\n SF:</html>\r\n")%r(Help,12F,"HTTP/1\.1\x20400\x20Bad\x20Request\r\nServer: SF:\x20openresty\r\nDate:\x20Wed,\x2013\x20Mar\x202024\x2002:19:13\x20GMT\ SF:r\nContent-Type:\x20text/html\r\nContent-Length:\x20154\r\nConnection:\ SF:x20close\r\n\r\n<html>\r\n<head><title>400\x20Bad\x20Request</title></h SF:ead>\r\n<body>\r\n<center><h1>400\x20Bad\x20Request</h1></center>\r\n<h SF:r><center>openresty</center>\r\n</body>\r\n</html>\r\n"); Service detection performed. Please report any incorrect results at http://nmap.org/submit/ . Nmap done: 1 IP address (1 host up) scanned in 19.05 seconds Segmentation fault (core dumped)
但是上面,还是不行,可以用检查网站测试一下
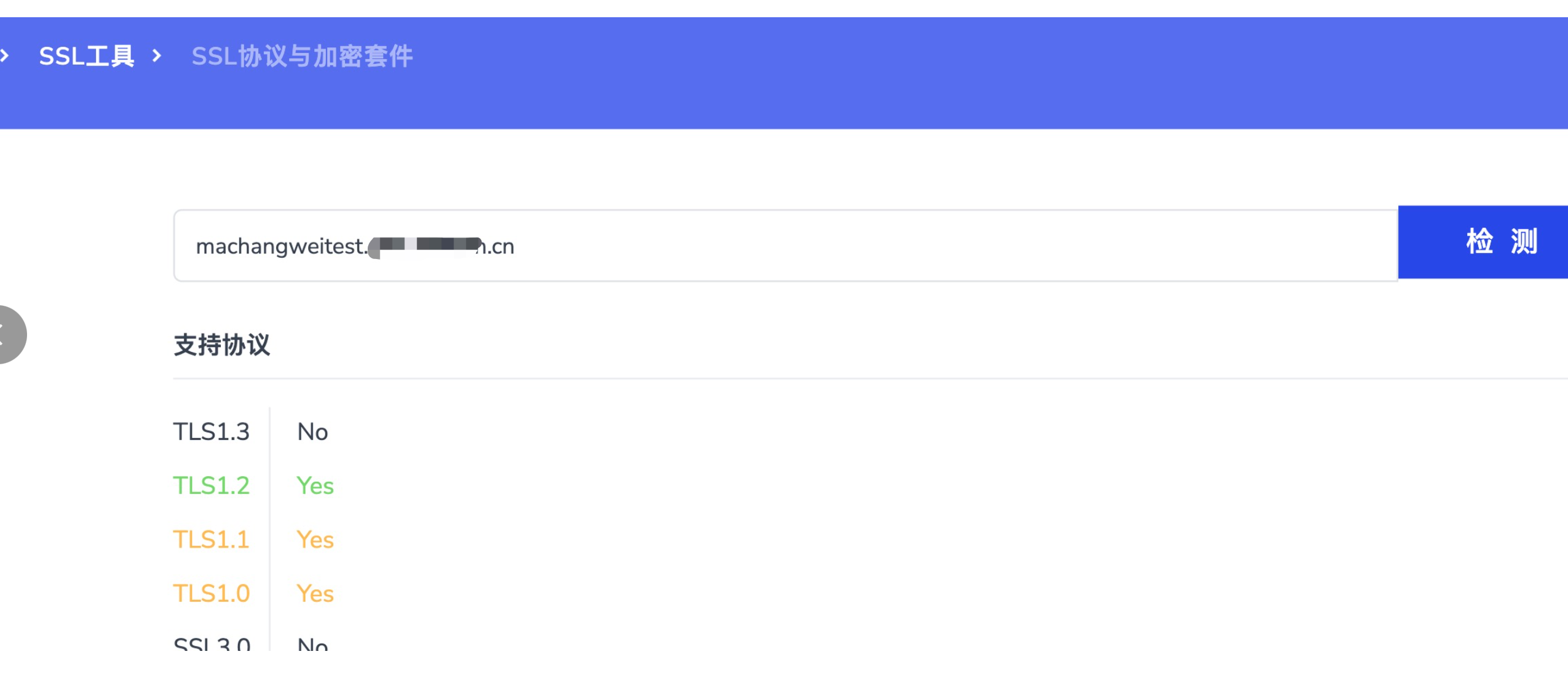
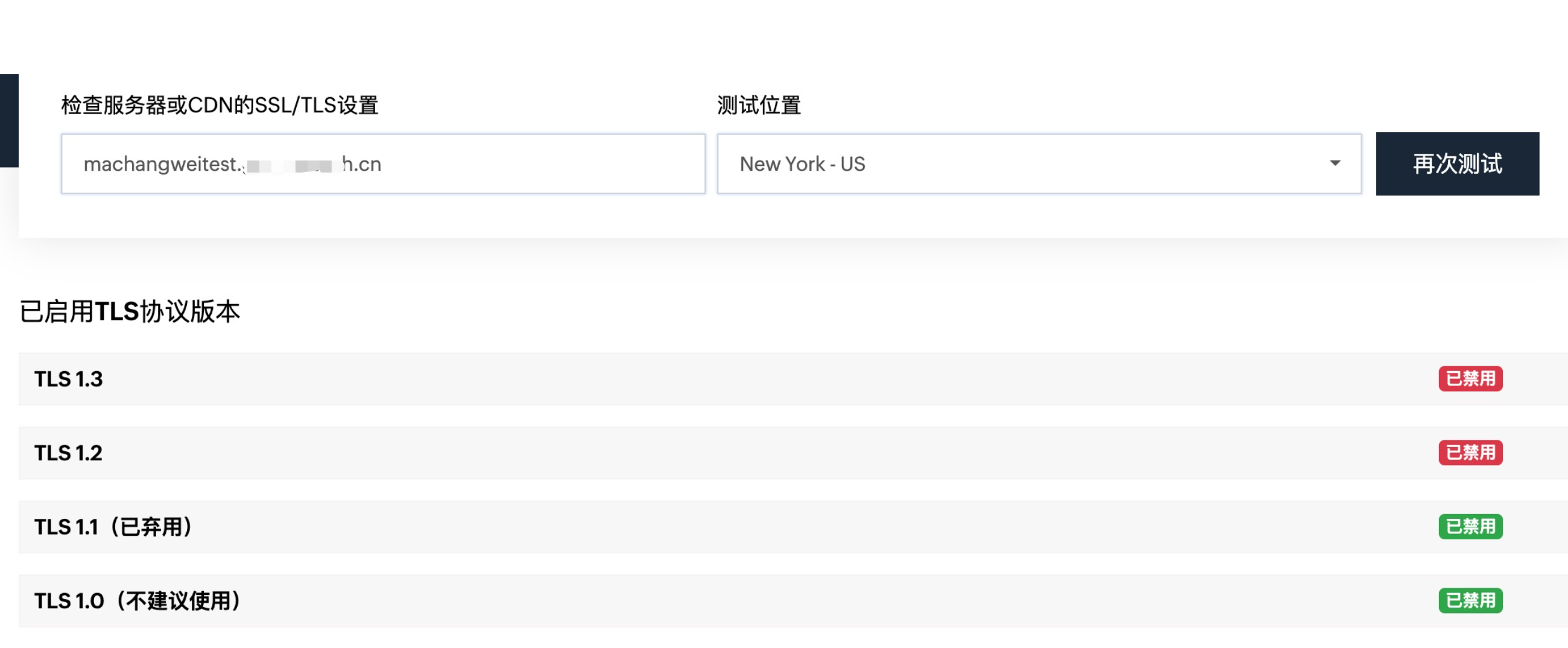
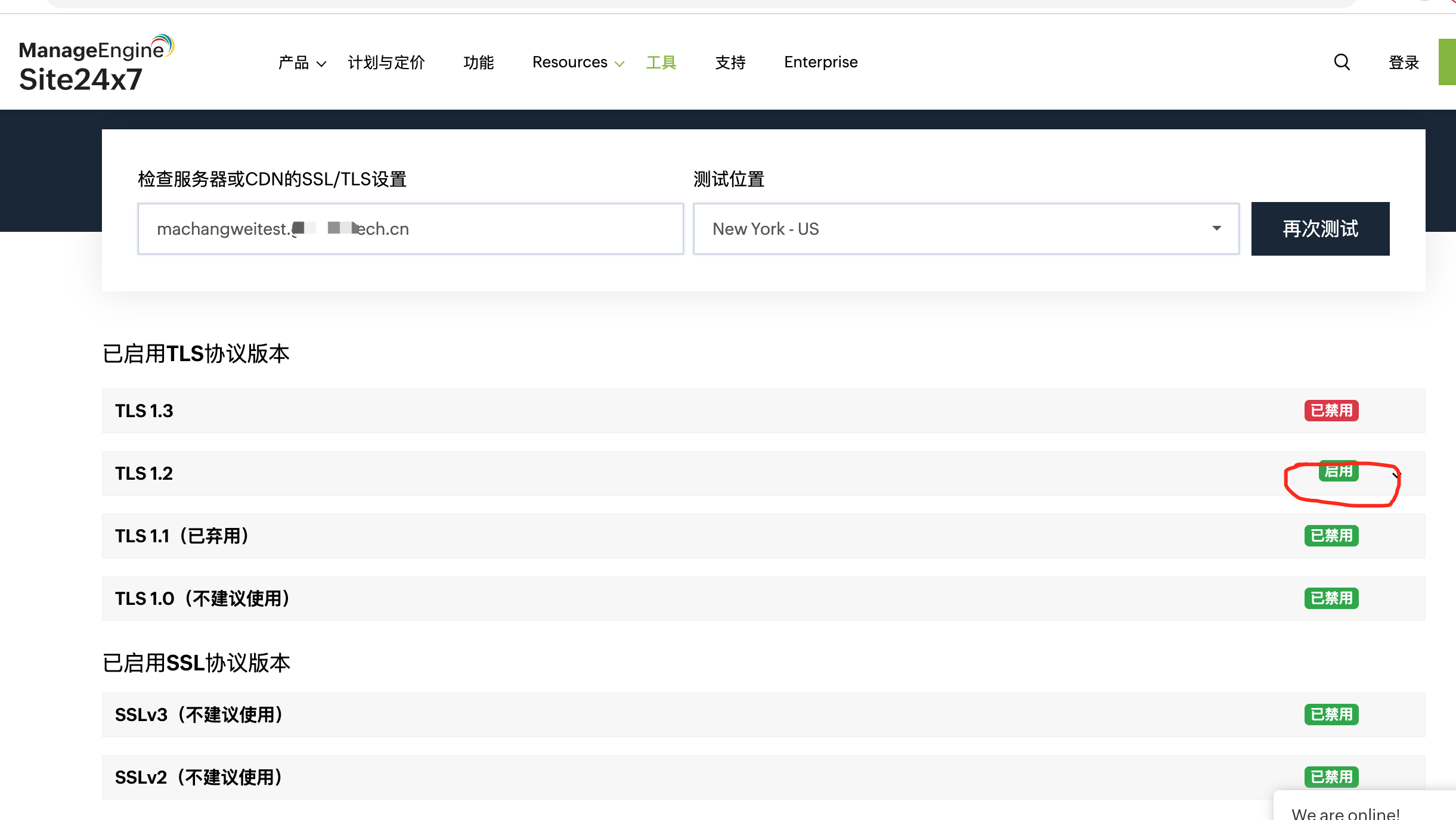
修改为如下:
ssl_protocols TLSv1.2 TLSv1.3; ssl_ciphers 'TLS_AES_128_GCM_SHA256:TLS_AES_256_GCM_SHA384:ECDHE-RSA-AES128-GCM-SHA256:ECDHE-RSA-AES256-GCM-SHA384:ECDHE-RSA-AES256-SHA384:ECDHE-RSA-AES128-SHA256:!DES:!RC4:!MD5:!3DES';
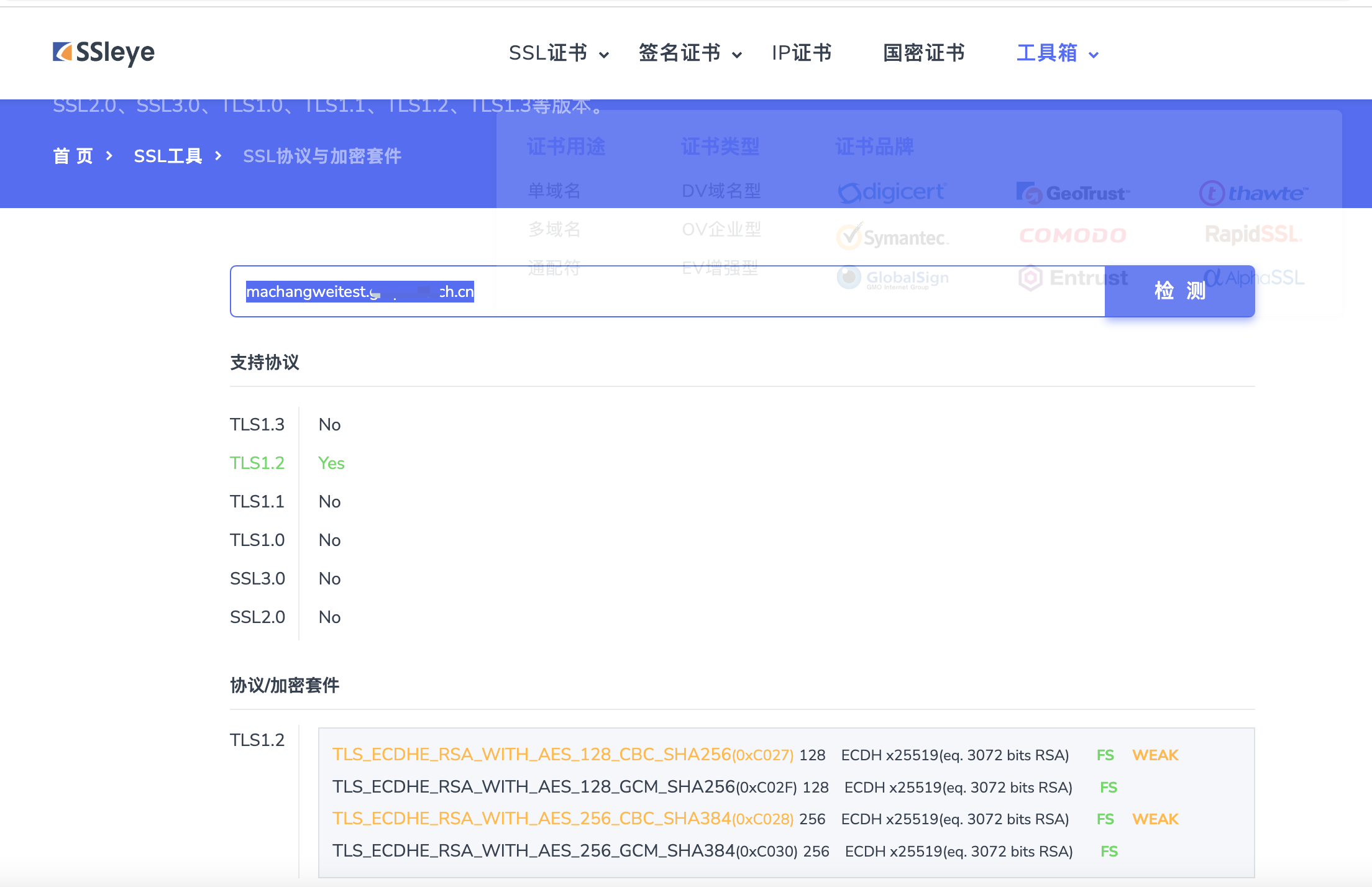
再次检查,其他禁用,1.2启用,而1.3是不支持
验证用网站:
https://www.site24x7.com/zhcn/tools/tls-checker.html
https://www.ssleye.com/ssltool/cipher_suites.html





【推荐】国内首个AI IDE,深度理解中文开发场景,立即下载体验Trae
【推荐】编程新体验,更懂你的AI,立即体验豆包MarsCode编程助手
【推荐】抖音旗下AI助手豆包,你的智能百科全书,全免费不限次数
【推荐】轻量又高性能的 SSH 工具 IShell:AI 加持,快人一步
· 无需6万激活码!GitHub神秘组织3小时极速复刻Manus,手把手教你使用OpenManus搭建本
· C#/.NET/.NET Core优秀项目和框架2025年2月简报
· 什么是nginx的强缓存和协商缓存
· 一文读懂知识蒸馏
· Manus爆火,是硬核还是营销?
2023-03-12 openstack原理
2023-03-12 大型网站核心架构要素
2023-03-12 数据结构与算法2
2023-03-12 部署发布的技术类型