kubernetes 之dashboard
部署
kubectl apply -f https://raw.githubusercontent.com/kubernetes/dashboard/v2.5.0/aio/deploy/recommended.yaml [machangwei@mcwk8s-master ~]$ kubectl apply -f recommended.yaml namespace/kubernetes-dashboard created serviceaccount/kubernetes-dashboard created service/kubernetes-dashboard created secret/kubernetes-dashboard-certs created secret/kubernetes-dashboard-csrf created secret/kubernetes-dashboard-key-holder created configmap/kubernetes-dashboard-settings created role.rbac.authorization.k8s.io/kubernetes-dashboard created clusterrole.rbac.authorization.k8s.io/kubernetes-dashboard created rolebinding.rbac.authorization.k8s.io/kubernetes-dashboard created clusterrolebinding.rbac.authorization.k8s.io/kubernetes-dashboard created deployment.apps/kubernetes-dashboard created service/dashboard-metrics-scraper created deployment.apps/dashboard-metrics-scraper created [machangwei@mcwk8s-master ~]$ kubectl get pod --namespace=kubernetes-dashboard NAME READY STATUS RESTARTS AGE dashboard-metrics-scraper-799d786dbf-kmxqs 1/1 Running 0 4m14s kubernetes-dashboard-546cbc58cd-292lp 1/1 Running 0 4m15s [machangwei@mcwk8s-master ~]$ kubectl get service --namespace=kubernetes-dashboard NAME TYPE CLUSTER-IP EXTERNAL-IP PORT(S) AGE dashboard-metrics-scraper ClusterIP 10.106.156.251 <none> 8000/TCP 4m26s kubernetes-dashboard ClusterIP 10.103.171.207 <none> 443/TCP 4m28s [machangwei@mcwk8s-master ~]$ kubectl get deployment --namespace=kubernetes-dashboard NAME READY UP-TO-DATE AVAILABLE AGE dashboard-metrics-scraper 1/1 1 1 4m50s kubernetes-dashboard 1/1 1 1 4m52s 将部署配置文件kubernetes-dashboard这个service修改为NodePort类型,这里没有,直接添加 kind: Service apiVersion: v1 metadata: labels: k8s-app: kubernetes-dashboard name: kubernetes-dashboard namespace: kubernetes-dashboard spec: ports: - port: 443 targetPort: 8443 selector: k8s-app: kubernetes-dashboard type: NodePort
[machangwei@mcwk8s-master ~]$ vim recommended.yaml [machangwei@mcwk8s-master ~]$ kubectl apply -f recommended.yaml namespace/kubernetes-dashboard unchanged serviceaccount/kubernetes-dashboard unchanged service/kubernetes-dashboard configured secret/kubernetes-dashboard-certs unchanged secret/kubernetes-dashboard-csrf configured Warning: resource secrets/kubernetes-dashboard-key-holder is missing the kubectl.kubernetes.io/last-applied-configuration annotation which is required by kubectl apply. kubectl apply should only be used on resources created declaratively by either kubectl create --save-config or kubectl apply. The missing annotation will be patched automatically. secret/kubernetes-dashboard-key-holder configured configmap/kubernetes-dashboard-settings unchanged role.rbac.authorization.k8s.io/kubernetes-dashboard unchanged clusterrole.rbac.authorization.k8s.io/kubernetes-dashboard unchanged rolebinding.rbac.authorization.k8s.io/kubernetes-dashboard unchanged clusterrolebinding.rbac.authorization.k8s.io/kubernetes-dashboard unchanged deployment.apps/kubernetes-dashboard unchanged service/dashboard-metrics-scraper unchanged deployment.apps/dashboard-metrics-scraper unchanged [machangwei@mcwk8s-master ~]$ kubectl get service --namespace=kubernetes-dashboard NAME TYPE CLUSTER-IP EXTERNAL-IP PORT(S) AGE dashboard-metrics-scraper ClusterIP 10.106.156.251 <none> 8000/TCP 11m kubernetes-dashboard NodePort 10.103.171.207 <none> 443:30766/TCP 11m [machangwei@mcwk8s-master ~]$ kubectl get pod --namespace=kubernetes-dashboard NAME READY STATUS RESTARTS AGE dashboard-metrics-scraper-799d786dbf-kmxqs 1/1 Running 0 11m kubernetes-dashboard-546cbc58cd-292lp 1/1 Running 0 11m [machangwei@mcwk8s-master ~]$ kubectl get pod --namespace=kubernetes-dashboard -o wide NAME READY STATUS RESTARTS AGE IP NODE NOMINATED NODE READINESS GATES dashboard-metrics-scraper-799d786dbf-kmxqs 1/1 Running 0 11m 10.244.1.2 mcwk8s-node1 <none> <none> kubernetes-dashboard-546cbc58cd-292lp 1/1 Running 0 11m 10.244.2.2 mcwk8s-node2 <none> <none> [machangwei@mcwk8s-master ~]$
由上可知,访问地址是:https://10.0.0.6:30766/ 或者是.4 .5的ip也行
mcwk8s-node2 10.0.0.6
dashboard部署配置文件

# Copyright 2017 The Kubernetes Authors. # # Licensed under the Apache License, Version 2.0 (the "License"); # you may not use this file except in compliance with the License. # You may obtain a copy of the License at # # http://www.apache.org/licenses/LICENSE-2.0 # # Unless required by applicable law or agreed to in writing, software # distributed under the License is distributed on an "AS IS" BASIS, # WITHOUT WARRANTIES OR CONDITIONS OF ANY KIND, either express or implied. # See the License for the specific language governing permissions and # limitations under the License. apiVersion: v1 kind: Namespace metadata: name: kubernetes-dashboard --- apiVersion: v1 kind: ServiceAccount metadata: labels: k8s-app: kubernetes-dashboard name: kubernetes-dashboard namespace: kubernetes-dashboard --- kind: Service apiVersion: v1 metadata: labels: k8s-app: kubernetes-dashboard name: kubernetes-dashboard namespace: kubernetes-dashboard spec: ports: - port: 443 targetPort: 8443 selector: k8s-app: kubernetes-dashboard type: NodePort --- apiVersion: v1 kind: Secret metadata: labels: k8s-app: kubernetes-dashboard name: kubernetes-dashboard-certs namespace: kubernetes-dashboard type: Opaque --- apiVersion: v1 kind: Secret metadata: labels: k8s-app: kubernetes-dashboard name: kubernetes-dashboard-csrf namespace: kubernetes-dashboard type: Opaque data: csrf: "" --- apiVersion: v1 kind: Secret metadata: labels: k8s-app: kubernetes-dashboard name: kubernetes-dashboard-key-holder namespace: kubernetes-dashboard type: Opaque --- kind: ConfigMap apiVersion: v1 metadata: labels: k8s-app: kubernetes-dashboard name: kubernetes-dashboard-settings namespace: kubernetes-dashboard --- kind: Role apiVersion: rbac.authorization.k8s.io/v1 metadata: labels: k8s-app: kubernetes-dashboard name: kubernetes-dashboard namespace: kubernetes-dashboard rules: # Allow Dashboard to get, update and delete Dashboard exclusive secrets. - apiGroups: [""] resources: ["secrets"] resourceNames: ["kubernetes-dashboard-key-holder", "kubernetes-dashboard-certs", "kubernetes-dashboard-csrf"] verbs: ["get", "update", "delete"] # Allow Dashboard to get and update 'kubernetes-dashboard-settings' config map. - apiGroups: [""] resources: ["configmaps"] resourceNames: ["kubernetes-dashboard-settings"] verbs: ["get", "update"] # Allow Dashboard to get metrics. - apiGroups: [""] resources: ["services"] resourceNames: ["heapster", "dashboard-metrics-scraper"] verbs: ["proxy"] - apiGroups: [""] resources: ["services/proxy"] resourceNames: ["heapster", "http:heapster:", "https:heapster:", "dashboard-metrics-scraper", "http:dashboard-metrics-scraper"] verbs: ["get"] --- kind: ClusterRole apiVersion: rbac.authorization.k8s.io/v1 metadata: labels: k8s-app: kubernetes-dashboard name: kubernetes-dashboard rules: # Allow Metrics Scraper to get metrics from the Metrics server - apiGroups: ["metrics.k8s.io"] resources: ["pods", "nodes"] verbs: ["get", "list", "watch"] --- apiVersion: rbac.authorization.k8s.io/v1 kind: RoleBinding metadata: labels: k8s-app: kubernetes-dashboard name: kubernetes-dashboard namespace: kubernetes-dashboard roleRef: apiGroup: rbac.authorization.k8s.io kind: ClusterRole name: cluster-admin subjects: - kind: ServiceAccount name: kubernetes-dashboard namespace: kubernetes-dashboard --- apiVersion: rbac.authorization.k8s.io/v1 kind: ClusterRoleBinding metadata: name: kubernetes-dashboard roleRef: apiGroup: rbac.authorization.k8s.io kind: ClusterRole name: cluster-admin subjects: - kind: ServiceAccount name: kubernetes-dashboard namespace: kubernetes-dashboard --- kind: Deployment apiVersion: apps/v1 metadata: labels: k8s-app: kubernetes-dashboard name: kubernetes-dashboard namespace: kubernetes-dashboard spec: replicas: 1 revisionHistoryLimit: 10 selector: matchLabels: k8s-app: kubernetes-dashboard template: metadata: labels: k8s-app: kubernetes-dashboard spec: securityContext: seccompProfile: type: RuntimeDefault containers: - name: kubernetes-dashboard image: kubernetesui/dashboard:v2.5.0 imagePullPolicy: Always ports: - containerPort: 8443 protocol: TCP args: - --auto-generate-certificates - --namespace=kubernetes-dashboard # Uncomment the following line to manually specify Kubernetes API server Host # If not specified, Dashboard will attempt to auto discover the API server and connect # to it. Uncomment only if the default does not work. # - --apiserver-host=http://my-address:port volumeMounts: - name: kubernetes-dashboard-certs mountPath: /certs # Create on-disk volume to store exec logs - mountPath: /tmp name: tmp-volume livenessProbe: httpGet: scheme: HTTPS path: / port: 8443 initialDelaySeconds: 30 timeoutSeconds: 30 securityContext: allowPrivilegeEscalation: false readOnlyRootFilesystem: true runAsUser: 1001 runAsGroup: 2001 volumes: - name: kubernetes-dashboard-certs secret: secretName: kubernetes-dashboard-certs - name: tmp-volume emptyDir: {} serviceAccountName: kubernetes-dashboard nodeSelector: "kubernetes.io/os": linux # Comment the following tolerations if Dashboard must not be deployed on master tolerations: - key: node-role.kubernetes.io/master effect: NoSchedule --- kind: Service apiVersion: v1 metadata: labels: k8s-app: dashboard-metrics-scraper name: dashboard-metrics-scraper namespace: kubernetes-dashboard spec: ports: - port: 8000 targetPort: 8000 selector: k8s-app: dashboard-metrics-scraper --- kind: Deployment apiVersion: apps/v1 metadata: labels: k8s-app: dashboard-metrics-scraper name: dashboard-metrics-scraper namespace: kubernetes-dashboard spec: replicas: 1 revisionHistoryLimit: 10 selector: matchLabels: k8s-app: dashboard-metrics-scraper template: metadata: labels: k8s-app: dashboard-metrics-scraper spec: securityContext: seccompProfile: type: RuntimeDefault containers: - name: dashboard-metrics-scraper image: kubernetesui/metrics-scraper:v1.0.7 ports: - containerPort: 8000 protocol: TCP livenessProbe: httpGet: scheme: HTTP path: / port: 8000 initialDelaySeconds: 30 timeoutSeconds: 30 volumeMounts: - mountPath: /tmp name: tmp-volume securityContext: allowPrivilegeEscalation: false readOnlyRootFilesystem: true runAsUser: 1001 runAsGroup: 2001 serviceAccountName: kubernetes-dashboard nodeSelector: "kubernetes.io/os": linux # Comment the following tolerations if Dashboard must not be deployed on master tolerations: - key: node-role.kubernetes.io/master effect: NoSchedule volumes: - name: tmp-volume emptyDir: {}
页面访问
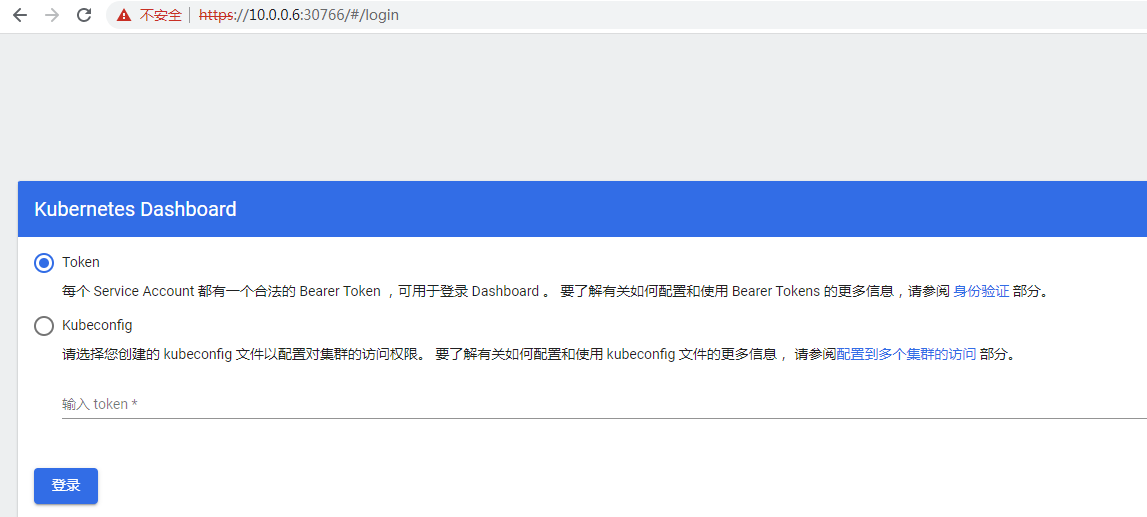
需要使用token,如果没有创建账号和secret的话,
可以创建账号,这里其实部署的时候已经创建好了
[machangwei@mcwk8s-master ~]$ cat rolebd.yaml apiVersion: rbac.authorization.k8s.io/v1 kind: ClusterRoleBinding metadata: name: kubernetes-dashboard labels: k8s-app: kubernetes-dashboard roleRef: apiGroup: rbac.authorization.k8s.io kind: ClusterRole name: Cluster-admin subjects: - kind: ServiceAccount name: kubernetes-dashboard namespace: kubernetes-dashboard [machangwei@mcwk8s-master ~]$
[machangwei@mcwk8s-master ~]$ kubectl get secret --namespace=kubernetes-dashboard #查看它的secret NAME TYPE DATA AGE default-token-jv99x kubernetes.io/service-account-token 3 58m kubernetes-dashboard-certs Opaque 0 58m kubernetes-dashboard-csrf Opaque 1 58m kubernetes-dashboard-key-holder Opaque 2 58m kubernetes-dashboard-token-bszwp kubernetes.io/service-account-token 3 58m [machangwei@mcwk8s-master ~]$ kubectl describe secret kubernetes-dashboard-token-bszwp --namespace=kubernetes-dashboard #查看dashboard的token的详情 Name: kubernetes-dashboard-token-bszwp Namespace: kubernetes-dashboard Labels: <none> Annotations: kubernetes.io/service-account.name: kubernetes-dashboard kubernetes.io/service-account.uid: 2fdc3d0f-3d90-4231-be4b-408af9bc8b02 Type: kubernetes.io/service-account-token Data ==== ca.crt: 1099 bytes namespace: 20 bytes token: eyJhbGciOiJSUzI1NiIsImtpZCI6InVZcVJ4N09mRTZMMWRYWThlTkY3T01JMFBrdnA3emhOTW1kMXpsVzFZUGMifQ.eyJpc3MiOiJrdWJlcm5ldGVzL3NlcnZpY2VhY2NvdW50Iiwia3ViZXJuZXRlcy5pby9zZXJ2aWNlYWNjb3VudC9uYW1lc3BhY2UiOiJrdWJlcm5ldGVzLWRhc2hib2FyZCIsImt1YmVybmV0ZXMuaW8vc2VydmljZWFjY291bnQvc2VjcmV0Lm5hbWUiOiJrdWJlcm5ldGVzLWRhc2hib2FyZC10b2tlbi1ic3p3cCIsImt1YmVybmV0ZXMuaW8vc2VydmljZWFjY291bnQvc2VydmljZS1hY2NvdW50Lm5hbWUiOiJrdWJlcm5ldGVzLWRhc2hib2FyZCIsImt1YmVybmV0ZXMuaW8vc2VydmljZWFjY291bnQvc2VydmljZS1hY2NvdW50LnVpZCI6IjJmZGMzZDBmLTNkOTAtNDIzMS1iZTRiLTQwOGFmOWJjOGIwMiIsInN1YiI6InN5c3RlbTpzZXJ2aWNlYWNjb3VudDprdWJlcm5ldGVzLWRhc2hib2FyZDprdWJlcm5ldGVzLWRhc2hib2FyZCJ9.jZZRCvgQVUc_xS2R4hABNqmQ2DeU8DxXChihQ3gg-d7QmhPrqX8iSlijLwbAwPfZh8X8OArmZy6Fi2ijHpERvkSCXsQGKOrPpVtrlNURUhGwo4MNNEvxqjdbE2llDRLZm7Vdshf5GKiJpbrLjlLMx0KpUOYfaLG6Sv3macXzOmW39W-Hj9KflsvT_Zo4B5J36wsaI7d_Wex4pO6MPwJJUnoQ1bLHuPs8rRar5U_UAowDz78gWum42H_2NkD7IRkAL7b8UD-CaN9j2nVadnChRGes_nBELcP1EpPm-VCdxidkTKfzukL7EsqsifxUedTchzjDzl4AKDgGk3BeT_BJYg [machangwei@mcwk8s-master ~]$ #直接复制上面token的值粘贴到输入token的框中,点击登录进入
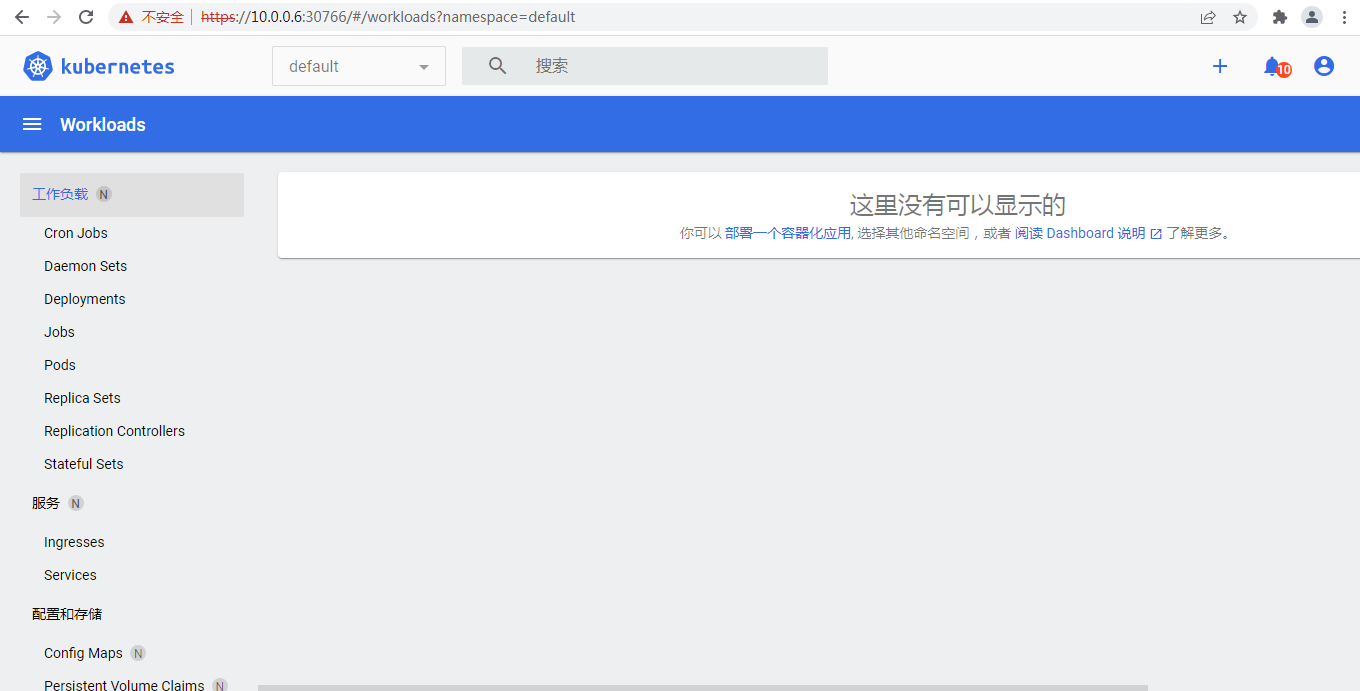
刚刚的操作这里有提示:
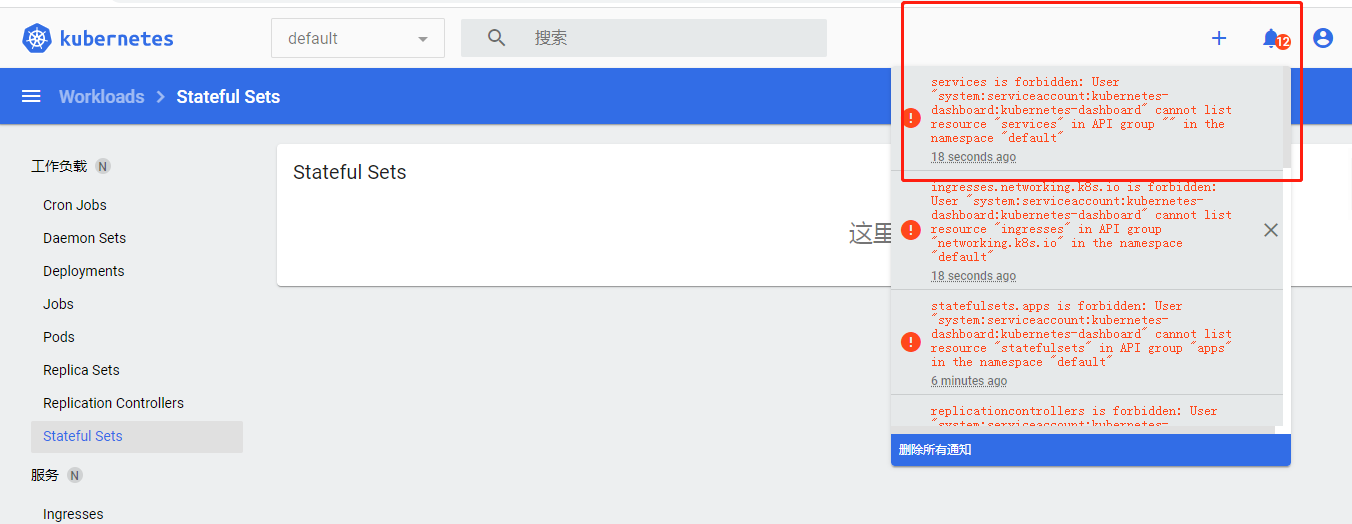
右边可以创建资源,左边这个可以选择命名空间
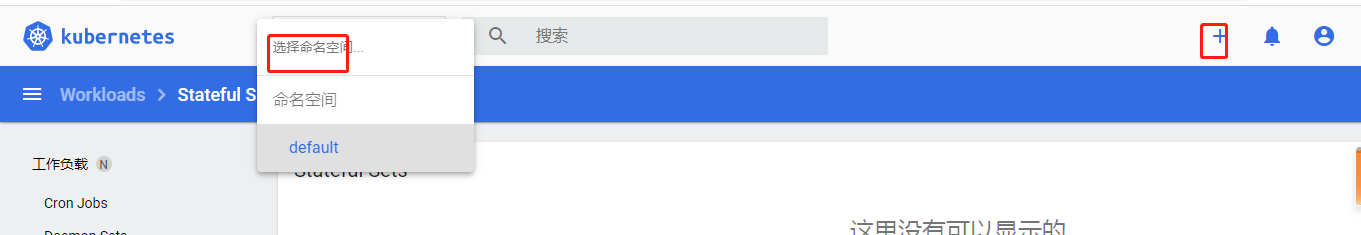
点一点又出来了,貌似没有权限把,额好像是没资源的提示
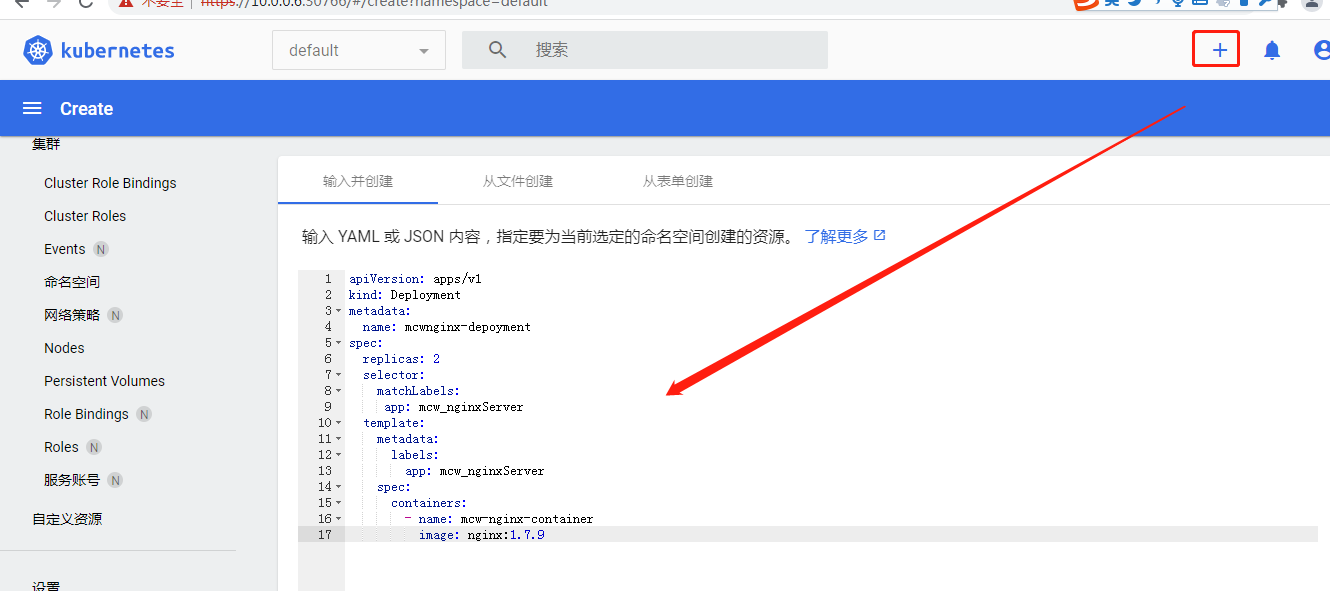
添加一个,并上传
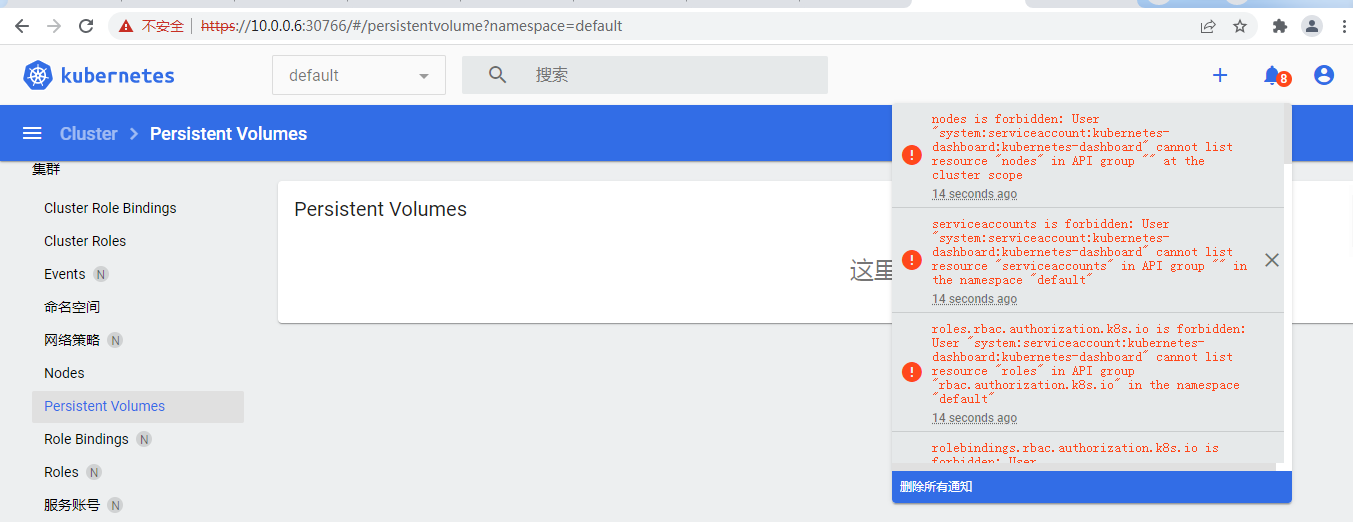
还真是没有权限呀
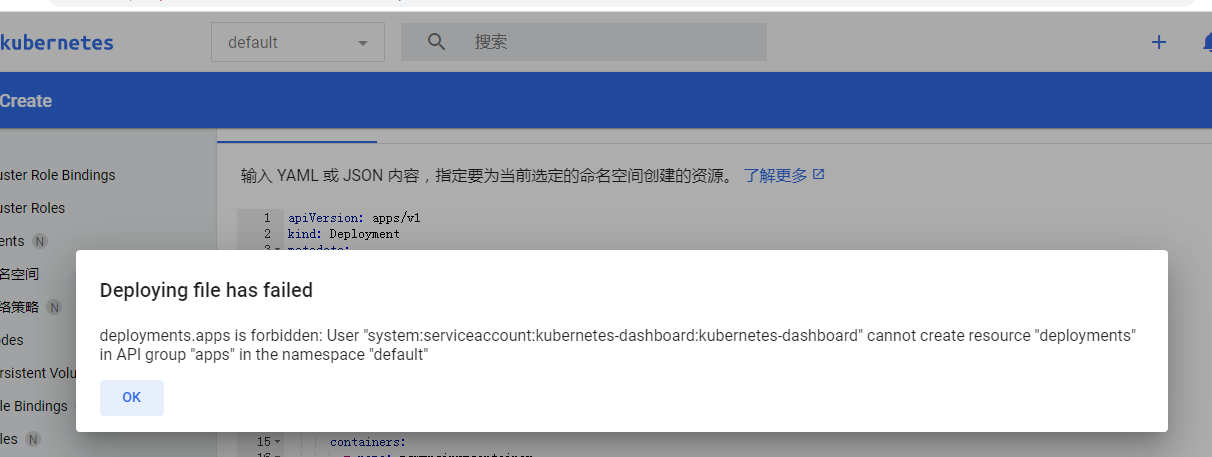
点了加号之后,左边有个创建了,然后下面可以选择创建的资源
修改权限后部署不行,删除了再部署貌似就管用了
[machangwei@mcwk8s-master ~]$ vim recommended.yaml [machangwei@mcwk8s-master ~]$ kubectl apply -f recommended.yaml namespace/kubernetes-dashboard unchanged serviceaccount/kubernetes-dashboard unchanged service/kubernetes-dashboard unchanged secret/kubernetes-dashboard-certs unchanged secret/kubernetes-dashboard-csrf unchanged secret/kubernetes-dashboard-key-holder unchanged configmap/kubernetes-dashboard-settings unchanged role.rbac.authorization.k8s.io/kubernetes-dashboard unchanged clusterrole.rbac.authorization.k8s.io/kubernetes-dashboard unchanged deployment.apps/kubernetes-dashboard unchanged service/dashboard-metrics-scraper unchanged deployment.apps/dashboard-metrics-scraper unchanged Error from server (Invalid): error when applying patch: {"metadata":{"annotations":{"kubectl.kubernetes.io/last-applied-configuration":"{\"apiVersion\":\"rbac.authorization.k8s.io/v1\",\"kind\":\"RoleBinding\",\"metadata\":{\"annotations\":{},\"labels\":{\"k8s-app\":\"kubernetes-dashboard\"},\"name\":\"kubernetes-dashboard\",\"namespace\":\"kubernetes-dashboard\"},\"roleRef\":{\"apiGroup\":\"rbac.authorization.k8s.io\",\"kind\":\"ClusterRole\",\"name\":\"cluster-admin\"},\"subjects\":[{\"kind\":\"ServiceAccount\",\"name\":\"kubernetes-dashboard\",\"namespace\":\"kubernetes-dashboard\"}]}\n"}},"roleRef":{"kind":"ClusterRole","name":"cluster-admin"}} to: Resource: "rbac.authorization.k8s.io/v1, Resource=rolebindings", GroupVersionKind: "rbac.authorization.k8s.io/v1, Kind=RoleBinding" Name: "kubernetes-dashboard", Namespace: "kubernetes-dashboard" for: "recommended.yaml": RoleBinding.rbac.authorization.k8s.io "kubernetes-dashboard" is invalid: roleRef: Invalid value: rbac.RoleRef{APIGroup:"rbac.authorization.k8s.io", Kind:"ClusterRole", Name:"cluster-admin"}: cannot change roleRef Error from server (Invalid): error when applying patch: {"metadata":{"annotations":{"kubectl.kubernetes.io/last-applied-configuration":"{\"apiVersion\":\"rbac.authorization.k8s.io/v1\",\"kind\":\"ClusterRoleBinding\",\"metadata\":{\"annotations\":{},\"name\":\"kubernetes-dashboard\"},\"roleRef\":{\"apiGroup\":\"rbac.authorization.k8s.io\",\"kind\":\"ClusterRole\",\"name\":\"cluster-admin\"},\"subjects\":[{\"kind\":\"ServiceAccount\",\"name\":\"kubernetes-dashboard\",\"namespace\":\"kubernetes-dashboard\"}]}\n"}},"roleRef":{"name":"cluster-admin"}} to: Resource: "rbac.authorization.k8s.io/v1, Resource=clusterrolebindings", GroupVersionKind: "rbac.authorization.k8s.io/v1, Kind=ClusterRoleBinding" Name: "kubernetes-dashboard", Namespace: "" for: "recommended.yaml": ClusterRoleBinding.rbac.authorization.k8s.io "kubernetes-dashboard" is invalid: roleRef: Invalid value: rbac.RoleRef{APIGroup:"rbac.authorization.k8s.io", Kind:"ClusterRole", Name:"cluster-admin"}: cannot change roleRef [machangwei@mcwk8s-master ~]$ kubectl delete -f recommended.yaml namespace "kubernetes-dashboard" deleted serviceaccount "kubernetes-dashboard" deleted service "kubernetes-dashboard" deleted secret "kubernetes-dashboard-certs" deleted secret "kubernetes-dashboard-csrf" deleted secret "kubernetes-dashboard-key-holder" deleted configmap "kubernetes-dashboard-settings" deleted role.rbac.authorization.k8s.io "kubernetes-dashboard" deleted clusterrole.rbac.authorization.k8s.io "kubernetes-dashboard" deleted rolebinding.rbac.authorization.k8s.io "kubernetes-dashboard" deleted clusterrolebinding.rbac.authorization.k8s.io "kubernetes-dashboard" deleted deployment.apps "kubernetes-dashboard" deleted service "dashboard-metrics-scraper" deleted deployment.apps "dashboard-metrics-scraper" deleted [machangwei@mcwk8s-master ~]$ [machangwei@mcwk8s-master ~]$ kubectl apply -f recommended.yaml namespace/kubernetes-dashboard created serviceaccount/kubernetes-dashboard created service/kubernetes-dashboard created secret/kubernetes-dashboard-certs created secret/kubernetes-dashboard-csrf created secret/kubernetes-dashboard-key-holder created configmap/kubernetes-dashboard-settings created role.rbac.authorization.k8s.io/kubernetes-dashboard created clusterrole.rbac.authorization.k8s.io/kubernetes-dashboard created rolebinding.rbac.authorization.k8s.io/kubernetes-dashboard created clusterrolebinding.rbac.authorization.k8s.io/kubernetes-dashboard created deployment.apps/kubernetes-dashboard created service/dashboard-metrics-scraper created deployment.apps/dashboard-metrics-scraper created
修改如下:
roleRef: apiGroup: rbac.authorization.k8s.io kind: Role name: kubernetes-dashboard 将上面修改如下: roleRef: apiGroup: rbac.authorization.k8s.io kind: ClusterRole name: cluster-admin
另一个的角色依据名字也改成admin了
如下:查看信息并重新输入token访问登录
[machangwei@mcwk8s-master ~]$ kubectl get service --namespace=kubernetes-dashboard NAME TYPE CLUSTER-IP EXTERNAL-IP PORT(S) AGE dashboard-metrics-scraper ClusterIP 10.107.147.61 <none> 8000/TCP 73s kubernetes-dashboard NodePort 10.101.43.54 <none> 443:31906/TCP 73s [machangwei@mcwk8s-master ~]$ kubectl get pod --namespace=kubernetes-dashboard NAME READY STATUS RESTARTS AGE dashboard-metrics-scraper-799d786dbf-ksljt 1/1 Running 0 2m7s kubernetes-dashboard-546cbc58cd-qcbfd 1/1 Running 0 2m7s [machangwei@mcwk8s-master ~]$ [machangwei@mcwk8s-master ~]$ [machangwei@mcwk8s-master ~]$ kubectl get secret --namespace=kubernetes-dashboard NAME TYPE DATA AGE default-token-4xvxl kubernetes.io/service-account-token 3 2m53s kubernetes-dashboard-certs Opaque 0 2m53s kubernetes-dashboard-csrf Opaque 1 2m53s kubernetes-dashboard-key-holder Opaque 2 2m53s kubernetes-dashboard-token-blsl7 kubernetes.io/service-account-token 3 2m53s [machangwei@mcwk8s-master ~]$ kubectl describe secret kubernetes-dashboard-token-blsl7 --namespace=kubernetes-dashboard Name: kubernetes-dashboard-token-blsl7 Namespace: kubernetes-dashboard Labels: <none> Annotations: kubernetes.io/service-account.name: kubernetes-dashboard kubernetes.io/service-account.uid: 0f668db3-f409-4d1e-a1f6-131a9d35c917 Type: kubernetes.io/service-account-token Data ==== ca.crt: 1099 bytes namespace: 20 bytes token: eyJhbGciOiJSUzI1NiIsImtpZCI6InVZcVJ4N09mRTZMMWRYWThlTkY3T01JMFBrdnA3emhOTW1kMXpsVzFZUGMifQ.eyJpc3MiOiJrdWJlcm5ldGVzL3NlcnZpY2VhY2NvdW50Iiwia3ViZXJuZXRlcy5pby9zZXJ2aWNlYWNjb3VudC9uYW1lc3BhY2UiOiJrdWJlcm5ldGVzLWRhc2hib2FyZCIsImt1YmVybmV0ZXMuaW8vc2VydmljZWFjY291bnQvc2VjcmV0Lm5hbWUiOiJrdWJlcm5ldGVzLWRhc2hib2FyZC10b2tlbi1ibHNsNyIsImt1YmVybmV0ZXMuaW8vc2VydmljZWFjY291bnQvc2VydmljZS1hY2NvdW50Lm5hbWUiOiJrdWJlcm5ldGVzLWRhc2hib2FyZCIsImt1YmVybmV0ZXMuaW8vc2VydmljZWFjY291bnQvc2VydmljZS1hY2NvdW50LnVpZCI6IjBmNjY4ZGIzLWY0MDktNGQxZS1hMWY2LTEzMWE5ZDM1YzkxNyIsInN1YiI6InN5c3RlbTpzZXJ2aWNlYWNjb3VudDprdWJlcm5ldGVzLWRhc2hib2FyZDprdWJlcm5ldGVzLWRhc2hib2FyZCJ9.I4PmedFBvibfRUyCvTKuqEaFFh-x5bNFqXfllLJMCl8YfG7dVui9mDcJIrjeCwuic6mOEX0bWO85ce2Puxip9myyE9SX6cMwLBdxxll03VxvBQthOAbD5Xlt5E-21aNngHByJ7k0R3FAhWNJxoNOfOwbKGk6aYZxLFi4VrazZXXn3w_oJU1wyK9Xn7BKTL0jOcGv7JBgULJxzNkm_dBXn8UOgblz6-iOKsEo9Bh3z91Ja3r4kejWYb-zW6Q7Egz3an2MFl5R7fnX97Uvx9sT76NpIGeuyW_RciVFthMS0o6D92-3thQcj_GchmMIj4xv8tikQHqAK4qlri5sEbD1hw [machangwei@mcwk8s-master ~]$
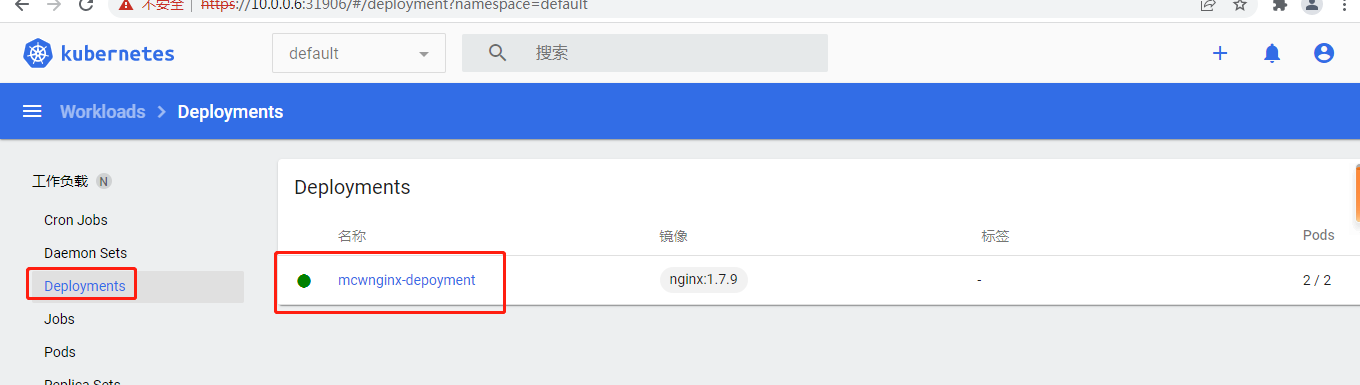
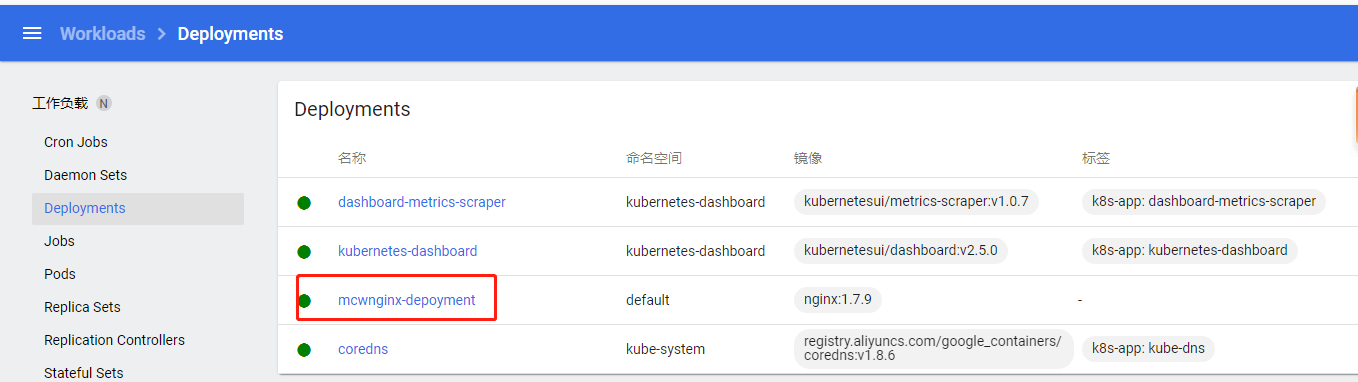
可以查看到我刚刚命令行创建的deployment了
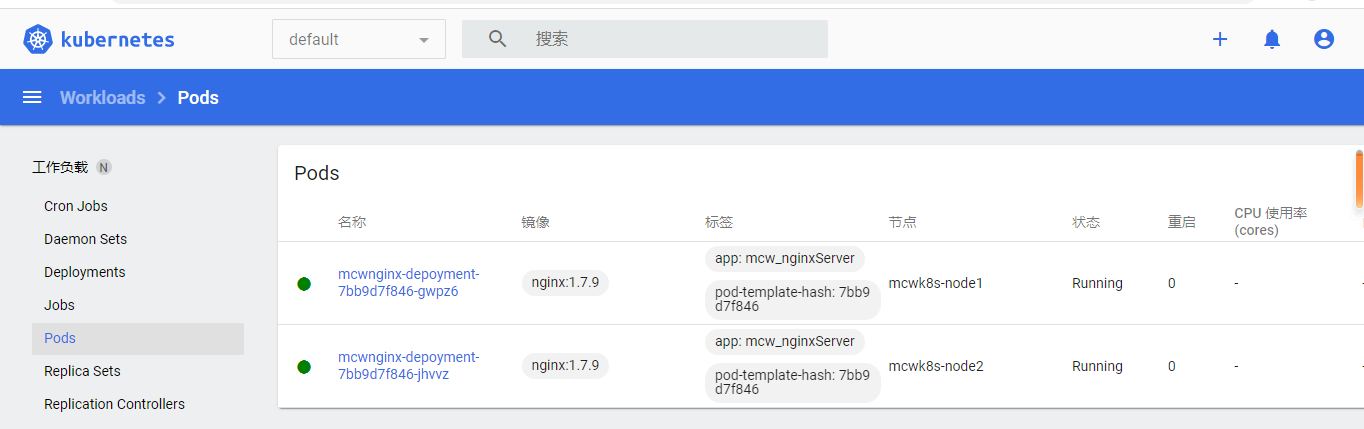
命名空间也能看很多了
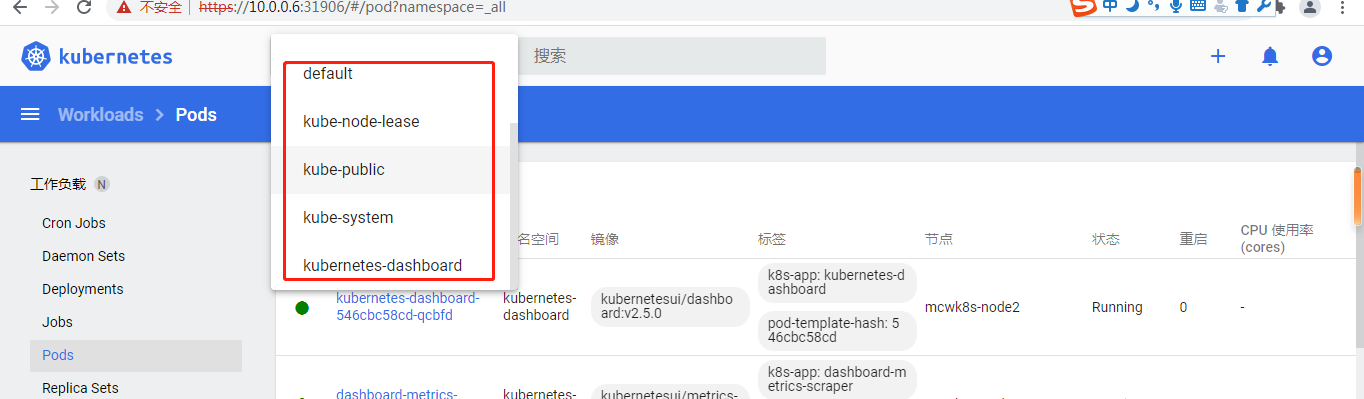
其中还有个全部,可以查看全部命名空间的资源
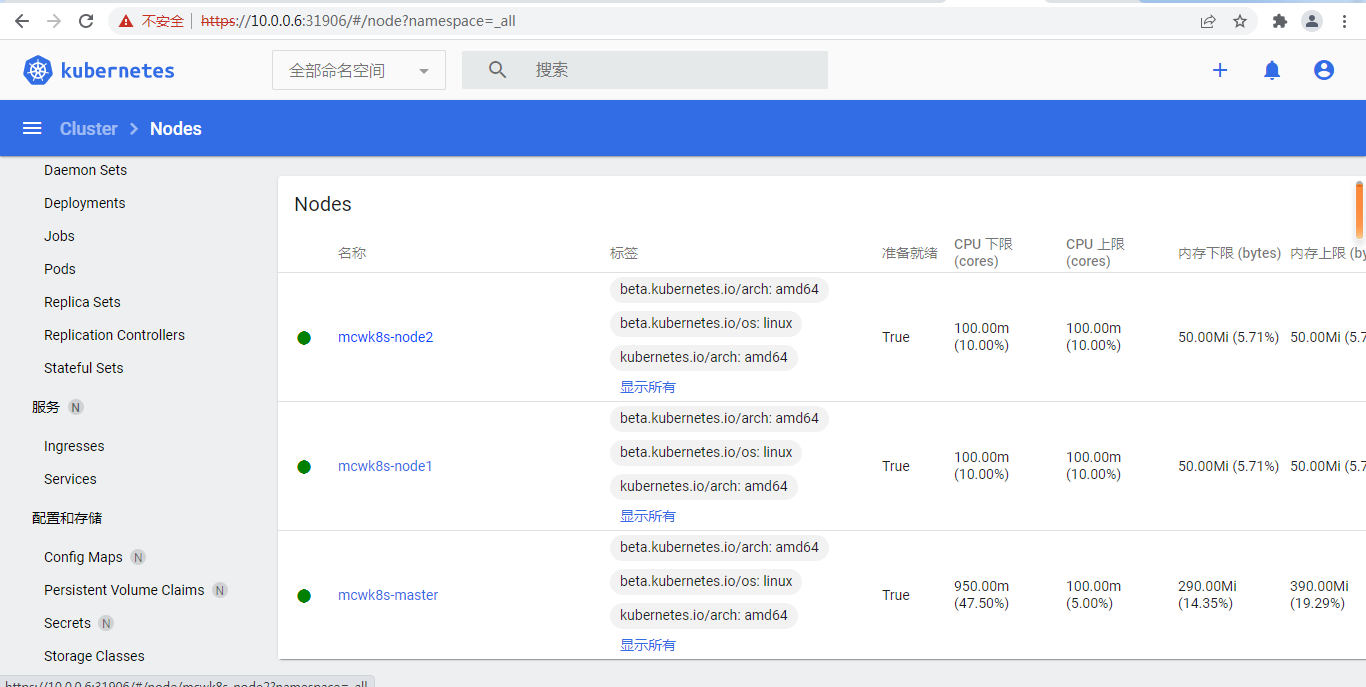
下面是查看所有node
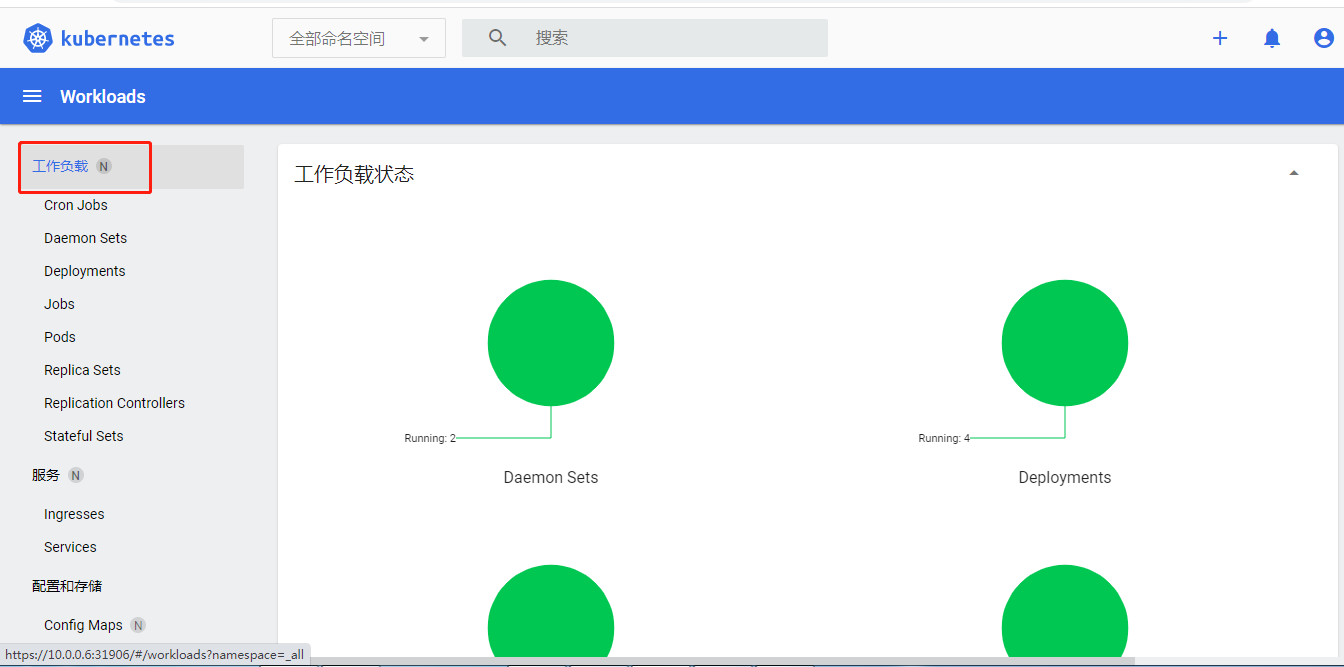
工作负载有图
deployment点击去的详情:
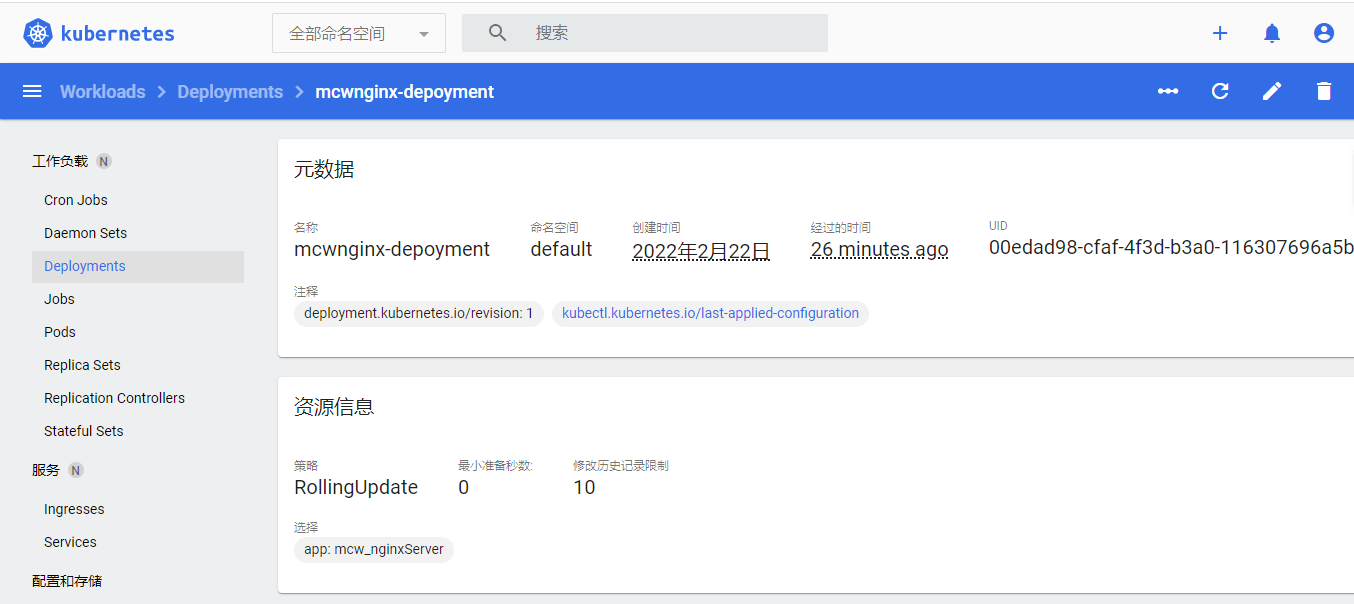
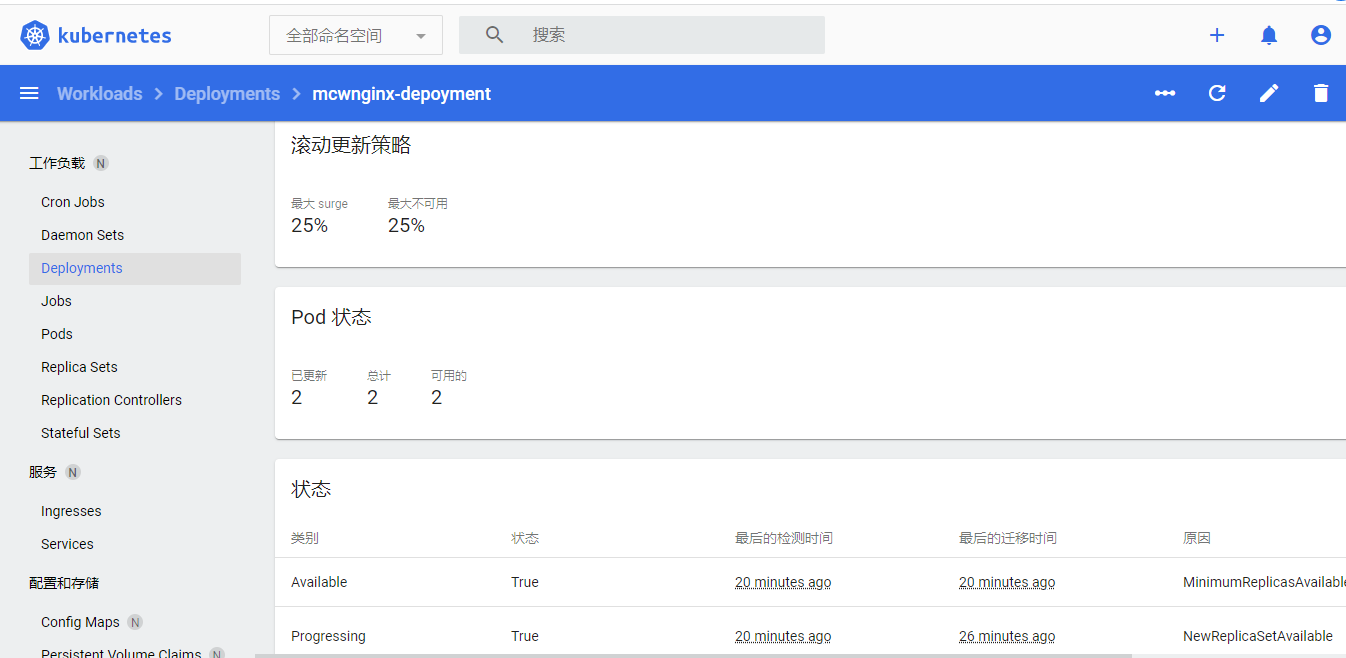

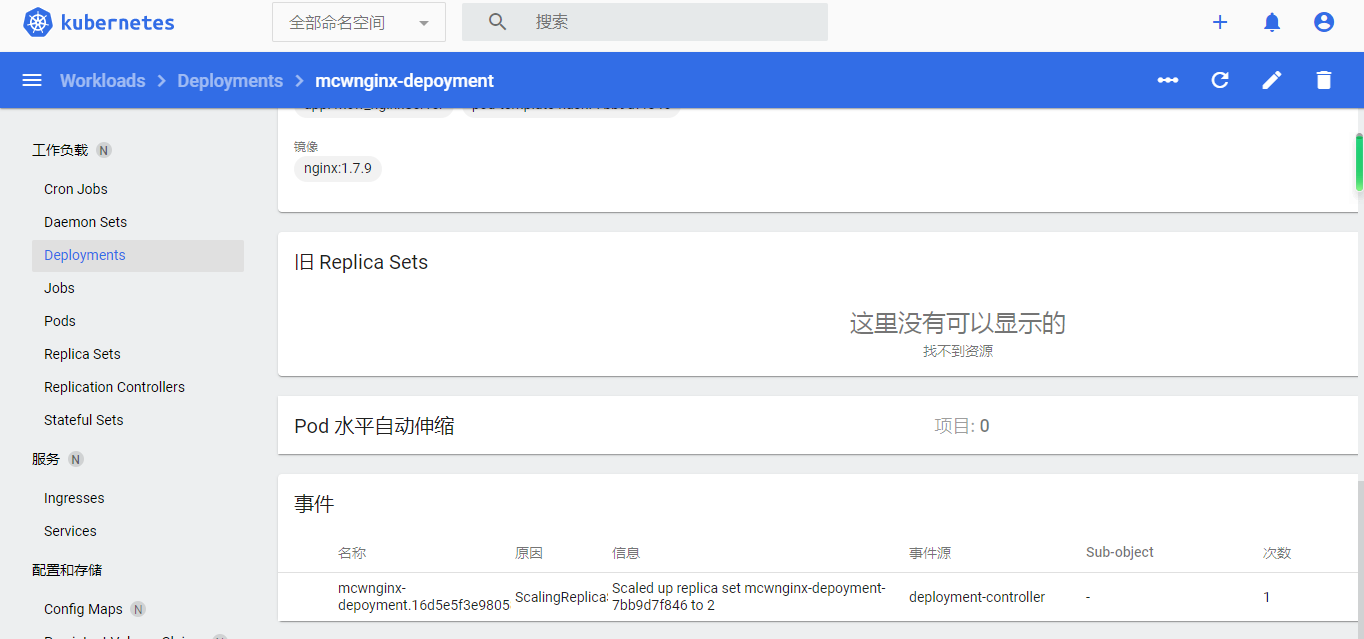
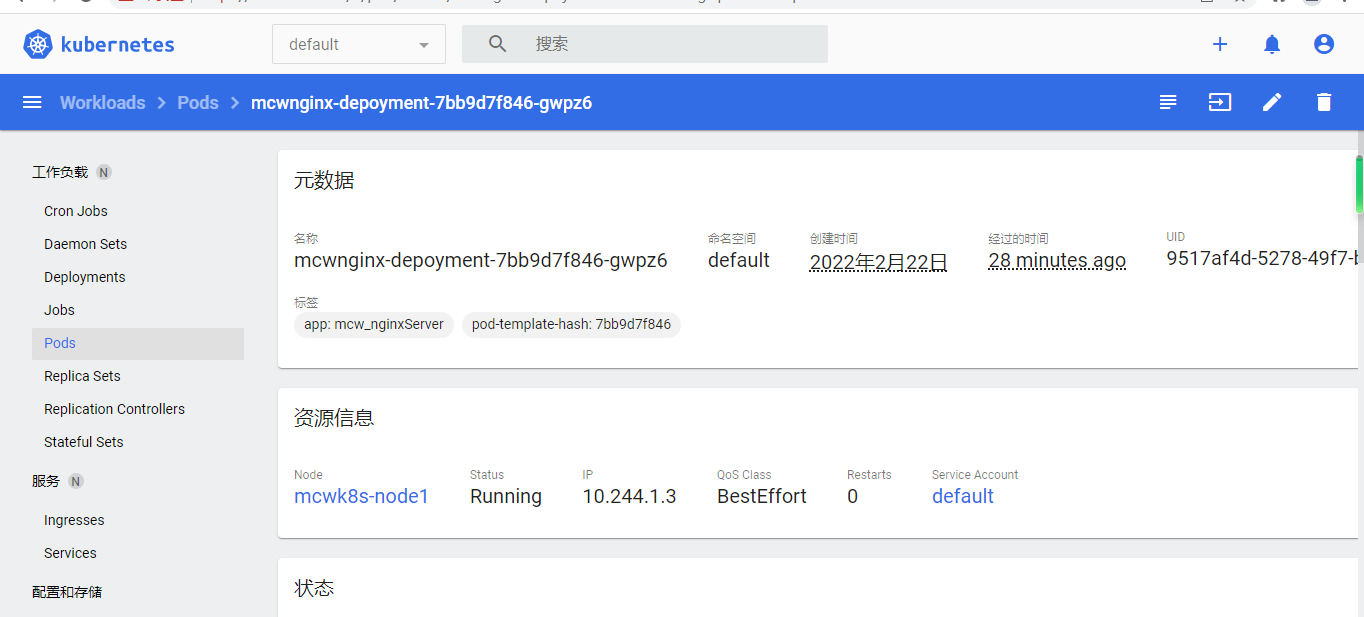
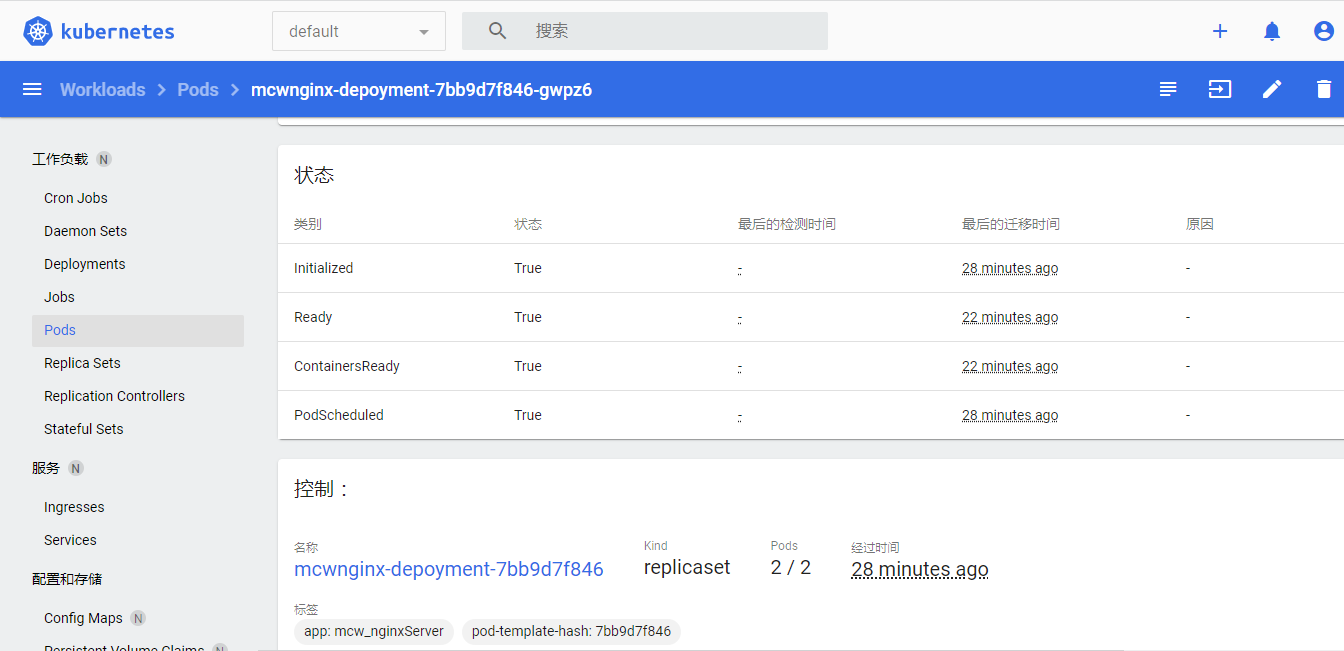
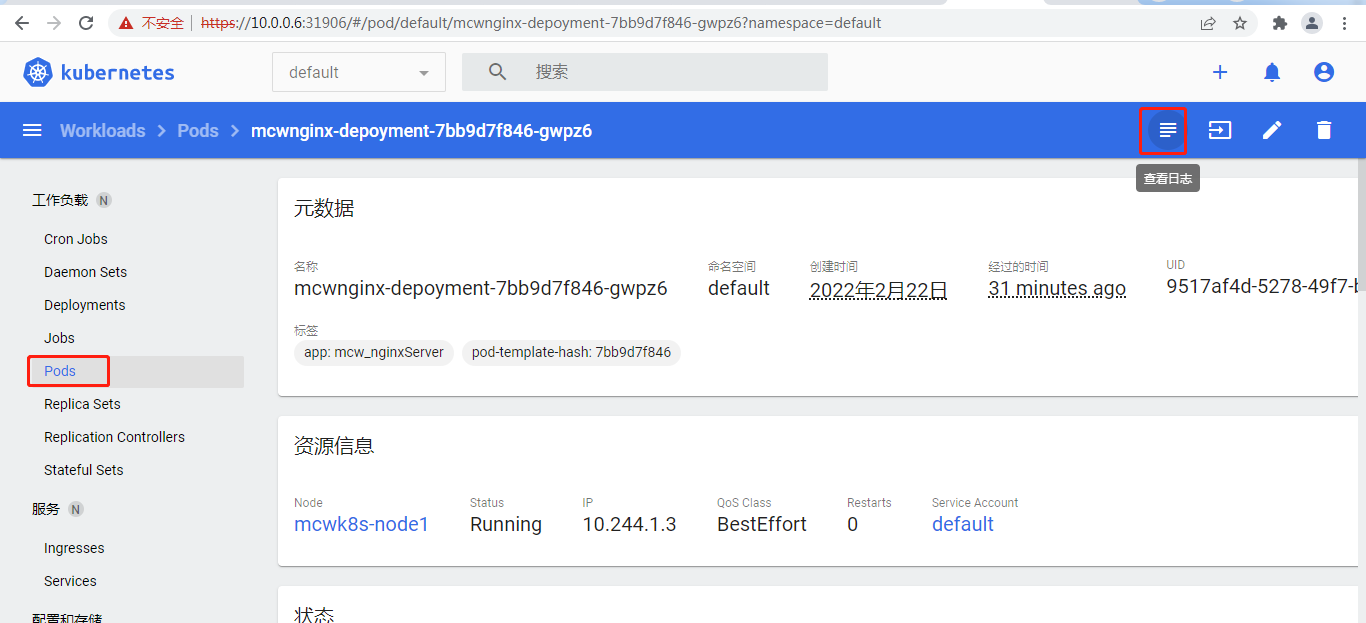
下面看一个pod的详情:
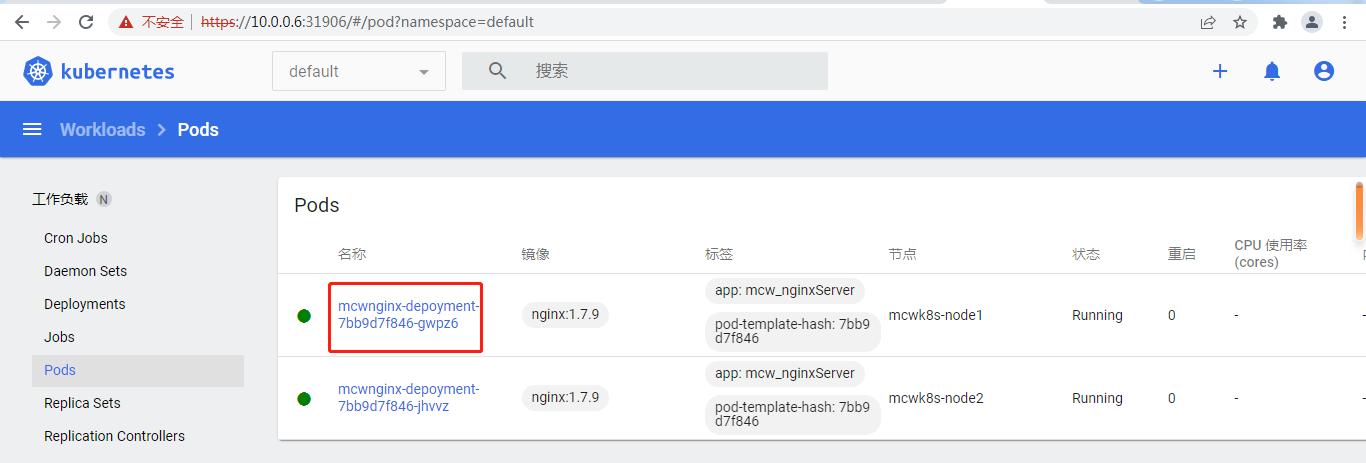
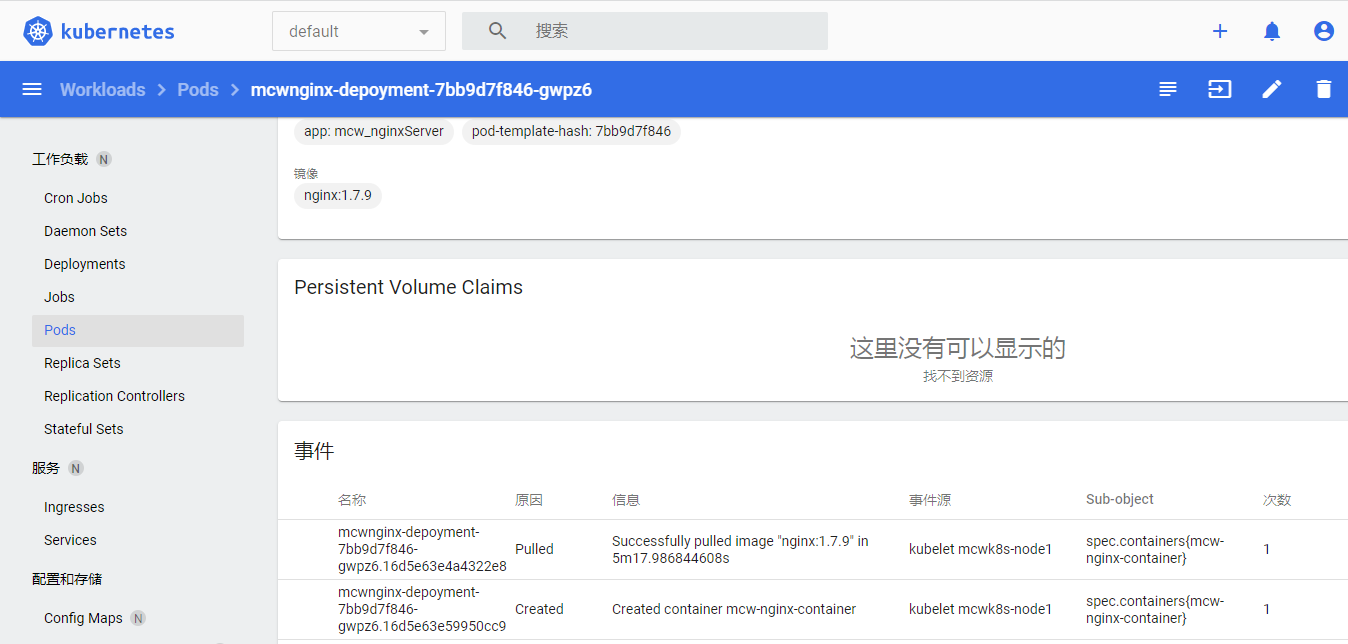
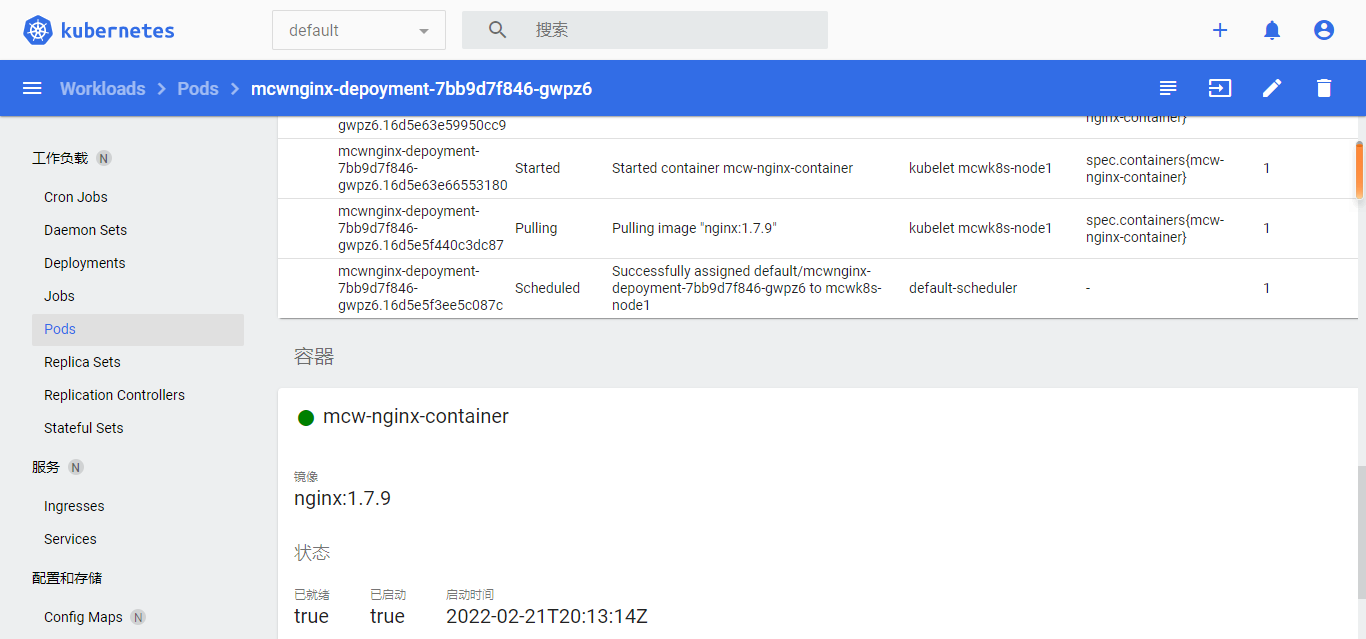
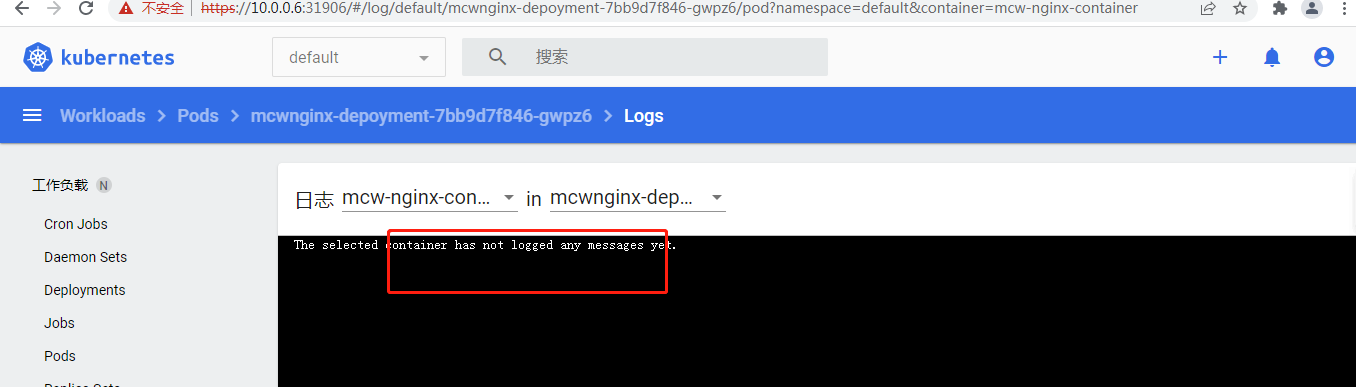
点进资源详情可以查看日志:
还可以点击运行
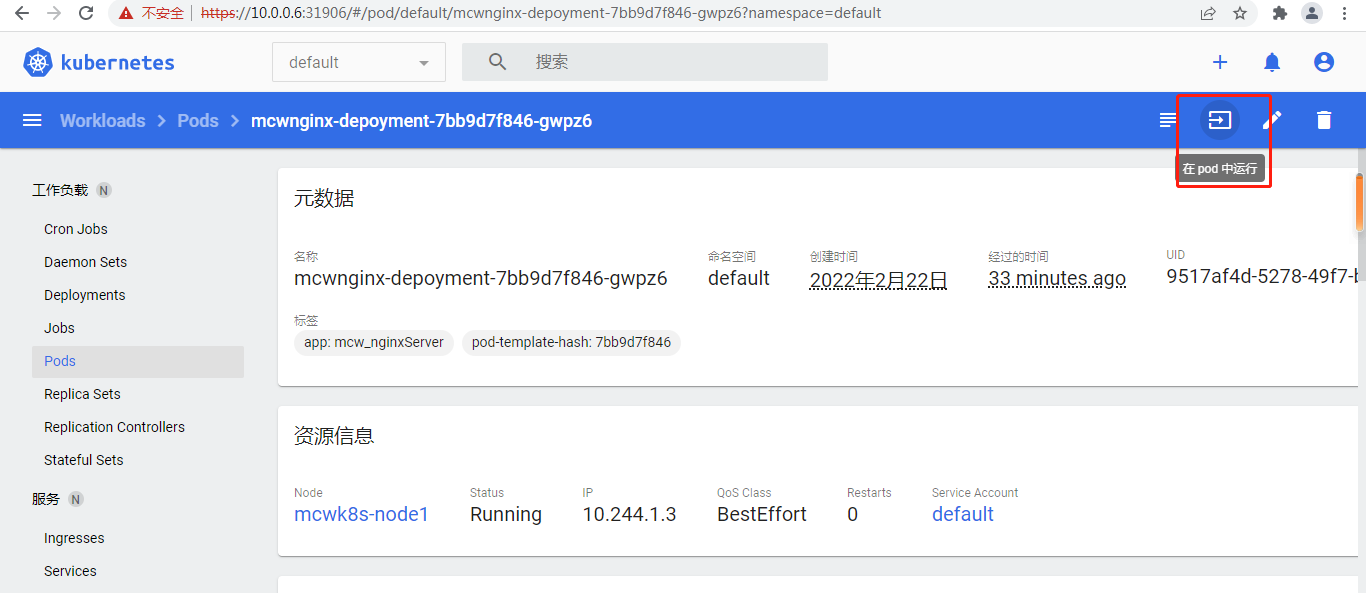
这样就进入这个pod下的容器了
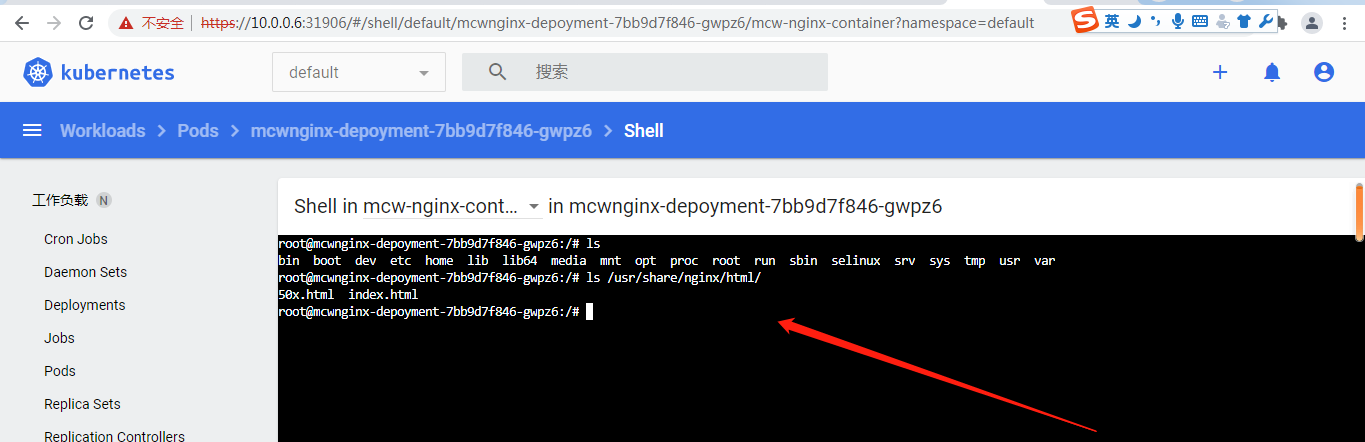
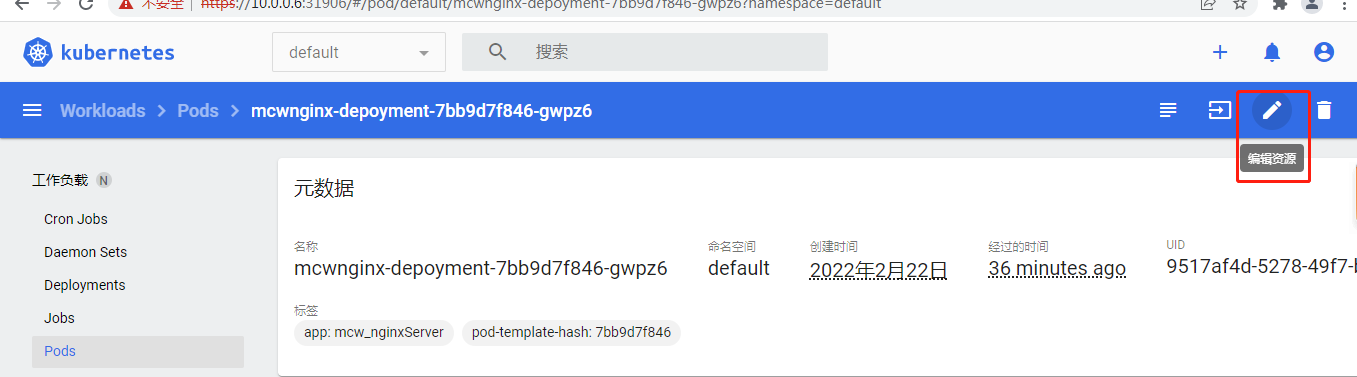
还可以编辑资源
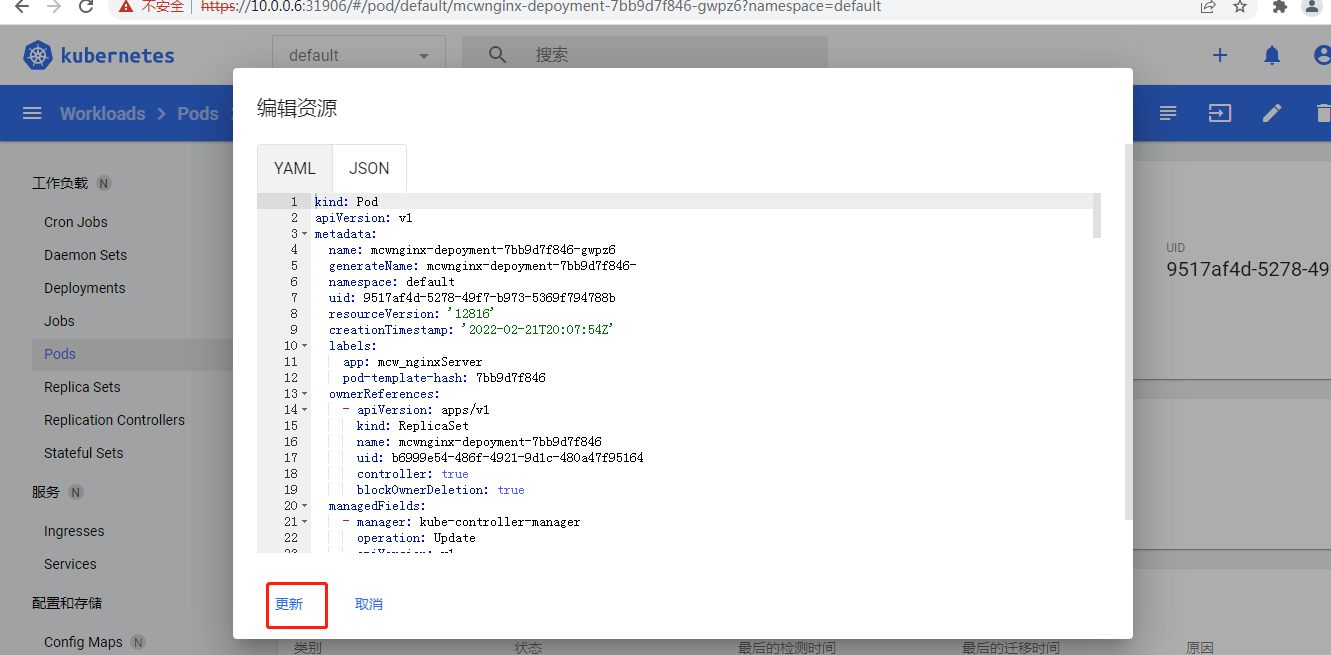
修改之后点击更新
还可以删除这个资源
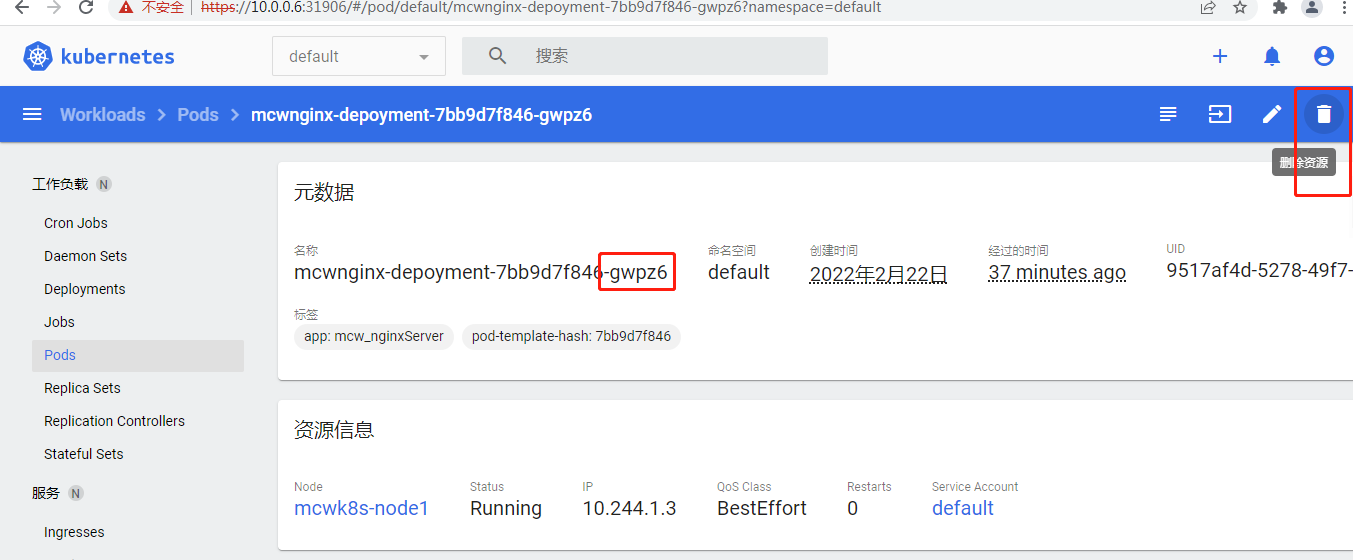
进的是这个pod,删除的也是这个pod
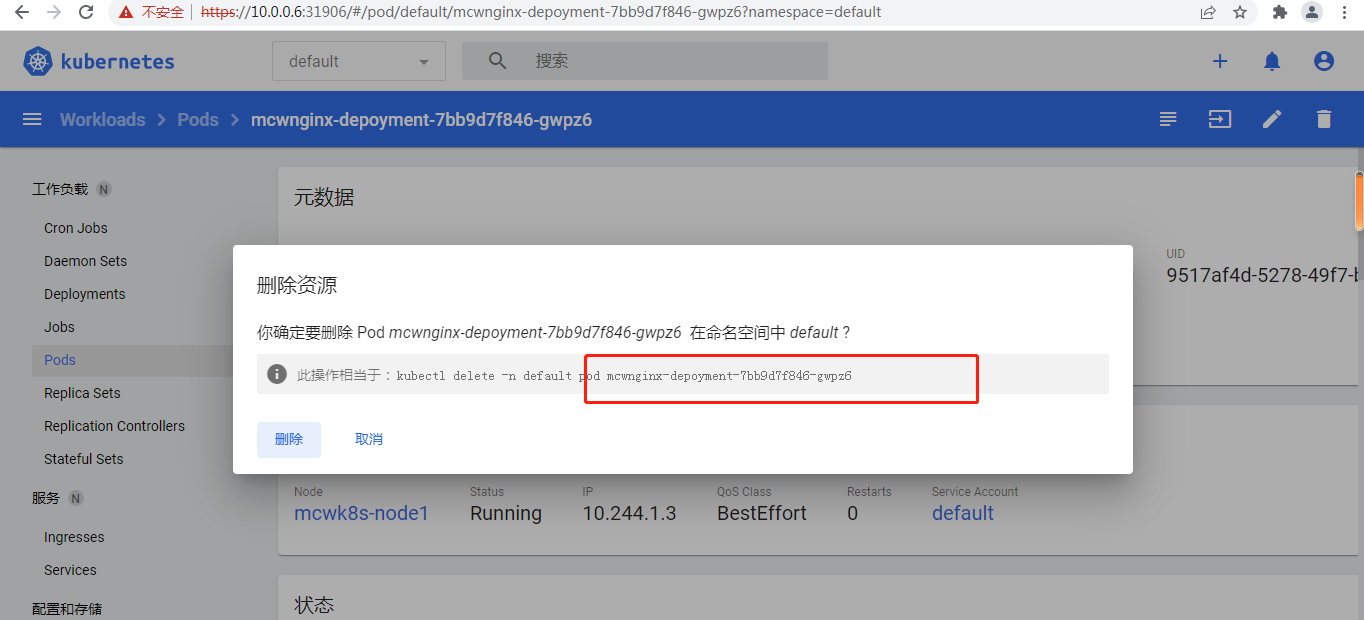
显示一个终止,另一个在创建
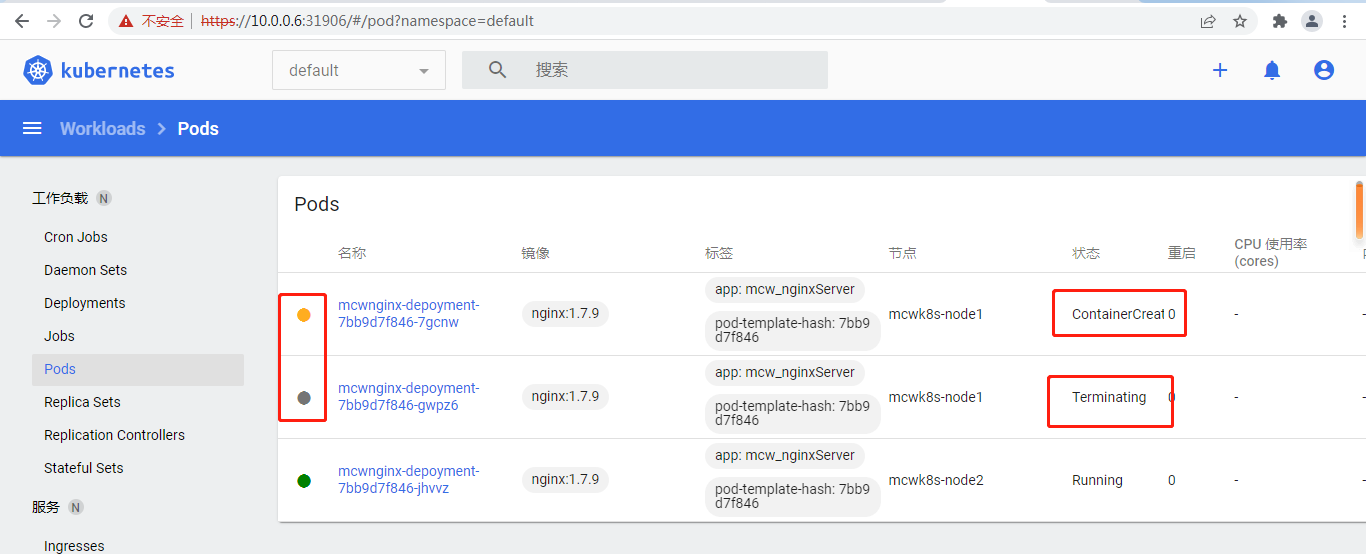
不一会,刚刚那个pod没了,新的pod起来了
 资源后面还有操作的按钮的
资源后面还有操作的按钮的
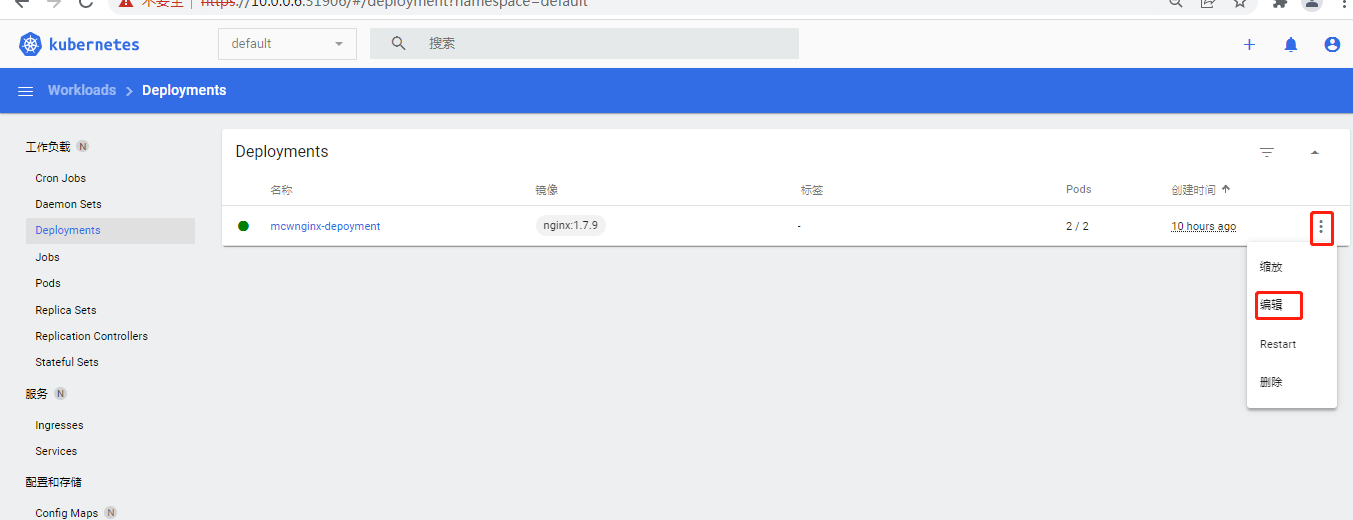
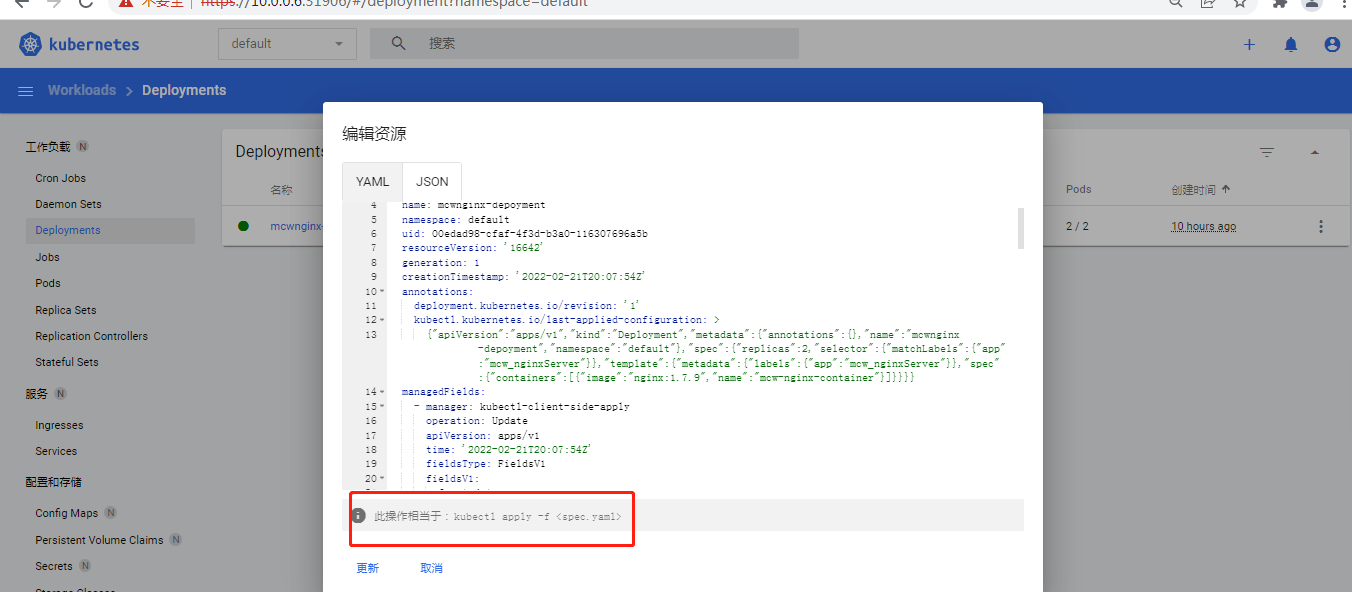
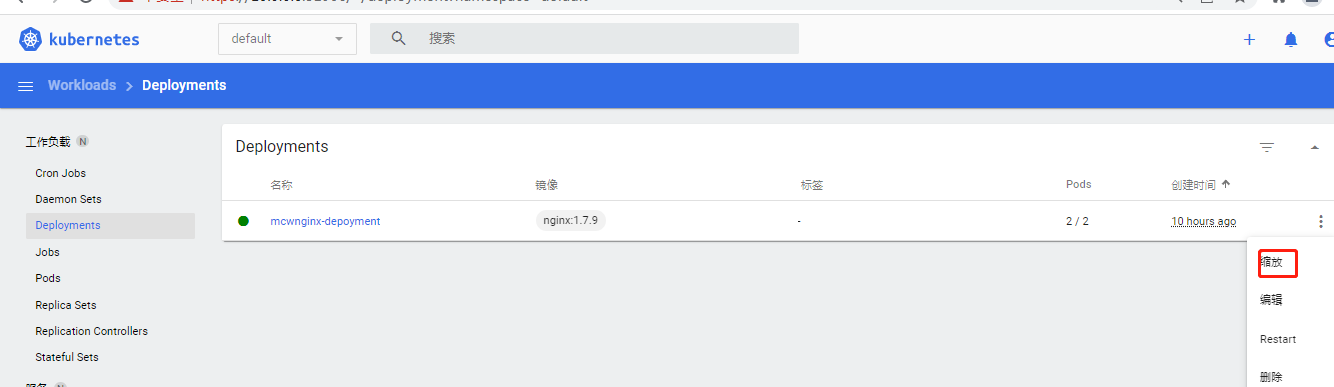
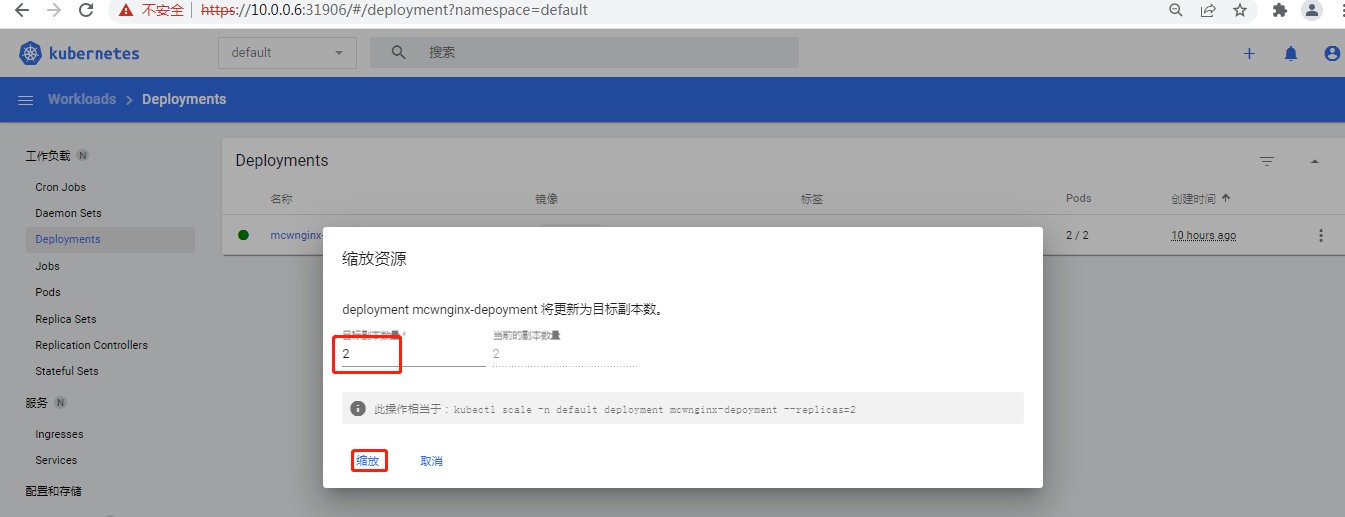
这里这个缩放是修改副本数量






【推荐】国内首个AI IDE,深度理解中文开发场景,立即下载体验Trae
【推荐】编程新体验,更懂你的AI,立即体验豆包MarsCode编程助手
【推荐】抖音旗下AI助手豆包,你的智能百科全书,全免费不限次数
【推荐】轻量又高性能的 SSH 工具 IShell:AI 加持,快人一步
· 无需6万激活码!GitHub神秘组织3小时极速复刻Manus,手把手教你使用OpenManus搭建本
· C#/.NET/.NET Core优秀项目和框架2025年2月简报
· 什么是nginx的强缓存和协商缓存
· 一文读懂知识蒸馏
· Manus爆火,是硬核还是营销?
2019-02-22 crond定时任务
2019-02-22 虚拟机网络不通故障解决
2019-02-22 jumpserver审计堡垒机