一些difficulty内存取证
1337UP Live - Liikt#1337
描述

wp
下载 zip 文件后,使用密码提取内容
这样做strings,
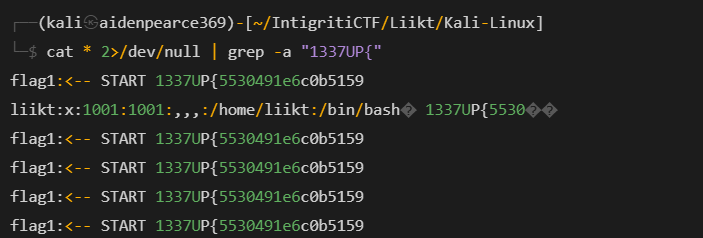
好像我们找到了flag的第一部分
它是 VMWare 映像的内存映像和虚拟硬盘
将其导入 VMWare 并开始启动它,我们将面对登录提示,完全不知道登录凭据
绕过这个的唯一方法是使用一个小技巧GRUB来生成root shell
将 GRUB更改ro ...为rw init=/bin/bash并加载它会给我们一个 root 级别的 shell,我们可以在其中使用passwd命令来更改root用户的密码
详细
获取shell后,我们可以看到一个用户名为liikt
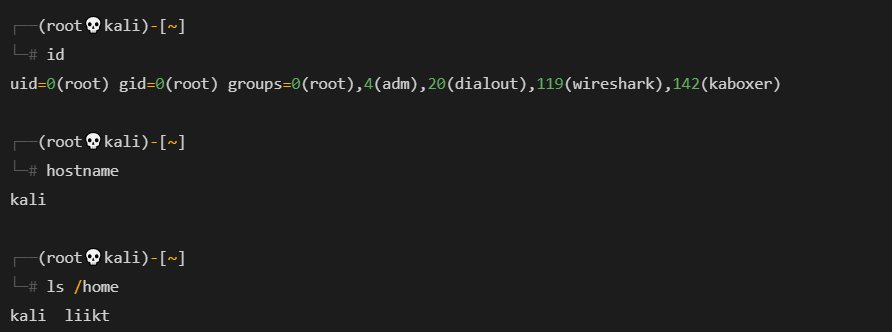
似乎我们必须为后门/数据转储找到一些凭据
枚举时我看到MySQL并Postgres安装在这台机器上
我的想法是尝试那些
启动后MySQL service,
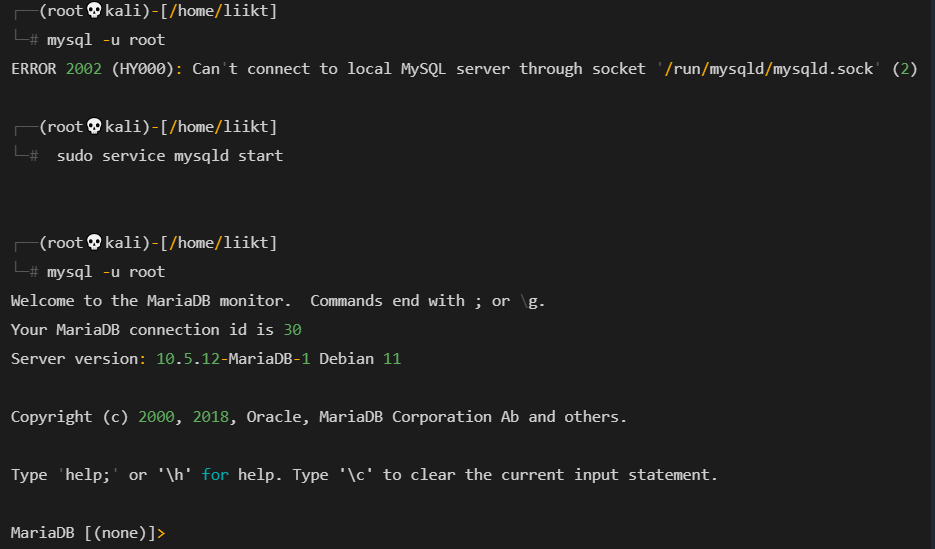
让我们进一步列举,
MariaDB [(none)]> show databases;
+--------------------+
| Database |
+--------------------+
| information_schema |
| mysql |
| performance_schema |
| yeeter_dump |
+--------------------+
4 rows in set (0.000 sec)
MariaDB [(none)]> use yeeter_dump;
Reading table information for completion of table and column names
You can turn off this feature to get a quicker startup with -A
Database changed
MariaDB [yeeter_dump]> show tables;
+-----------------------+
| Tables_in_yeeter_dump |
+-----------------------+
| creds |
+-----------------------+
1 row in set (0.000 sec)
MariaDB [yeeter_dump]> select * from creds;
+----------------------------------+---------------------------------+
| email | password |
+----------------------------------+---------------------------------+
| peter@email.com | Lowstreet4 |
| amy@fake.com | Applest652 |
| hannah@loser.net | Mountain21!#13$f |
| michael54@lousymail.com | Valley345$fs |
| sandy@spongebob.com | Oceanblvd2 |
| betty@meme.com | GreenGrass1 |
| johnhammond@youtuber.com | PlzSubscribe!#XD |
| followmytwitter@BlacknoteSec.com | BlacknoteSec |
| liikt@hacker.com | best_h3ckerman!69- |
| peter_parker@avengers.com | Sp00derm4n |
| thor@asgard.com | StrongestAvenger1 |
| pink@draconian.com | MainRoad989 |
| viola@email.com | ViolaPlaysViolin00 |
| uanikolayf@gmailya.com | qwertyuiop |
| willing@mail.com | SF4ss4fds56 |
| sdfdslike@mail.com | Password01 |
| pinkdraconian@youtuber.com | IntigritiRockz6969_ |
| perfect@blue.com | dizCTF2ez! |
| matt_e@dev.com | Pwn2Ez4m3 |
| fumenoid@dev.com | I4mJust4N00b |
| congon4tor@dev.com | webm3up! |
| lorem@ipsumdolor.sit | amet!consectetur |
| qwerty@qwerty.com | asdfghjkl1234 |
| thegamer@games.com | wtfgames!$ |
| justemail@random.com | fhcnawisg456 |
| whateberafsd@asdf.com | bjhgawf243 |
| igiveup@mails.com | randomasd |
| afdasdf.mail.com | kjhgfwff123 |
| hjsadf@asd.com | nbxvcsduycg |
| sinister_matrix@coolguy.com | jbhaf#jyavnw54 |
| pwnfunction@youtuber.com | hackercamp.co |
| optional@ctf.com | I4amJust4Ch4d |
| badboy17@byteforce.com | h4xl33terrrrrr45 |
| streaker_rules@byteforce.com | cryptog0d6969 |
| lucas@byteforce.com | lukeflima69 |
| szymex73@ctf.com | justanothern00b |
| calebjstewart@dev.com | UsePwnCat |
| ashok_b_simping@mlp.com | IAmAcl0wn69 |
| d0minik@mlp.com | polarbears4recute137 |
| smellycharlie@oldman.com | ageisjustanumber!#$ |
| liveoverflow@youtuber.com | isthereanyoneelsebetter?! |
| kevinmitnick@oldschool.com | legend |
| ippsec@youtube.com | whatsgoingonyoutubethisisippsec |
| sfsd@sgsg.com | asdfasdfkjhg2354 |
| jhgaf@nbasaf.com | hbadjegf546 |
| bjhacwg@afsjhgkwsjf.com | ajhfskgseuf |
| nbmygf@sajh.com | bvjhhgf |
| postmalone@music.com | makingApostRequest |
| lame@lame.com | sadfgsf |
| whateven@what.com | wgfasgb |
+----------------------------------+---------------------------------+
50 rows in set (0.001 sec)
MariaDB [yeeter_dump]>
看起来像登录凭据,但为什么
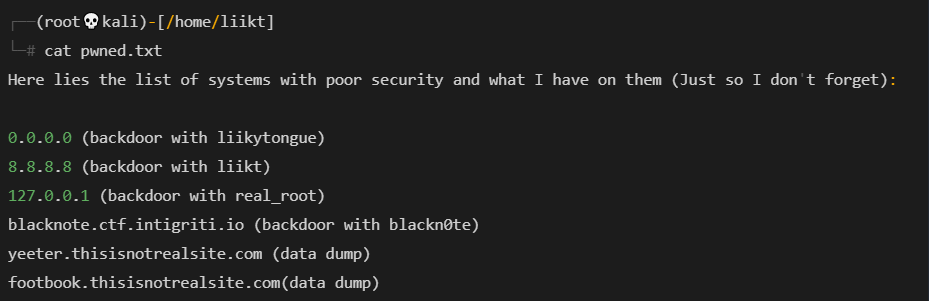
从pwned.txt我们可以看到有一个合法的主机名的提示blacknote.ctf.intigriti.io
因为,CTF 托管在 上ctf.intigriti.io,它只是一个子域
使用 扫描此主机名nmap,
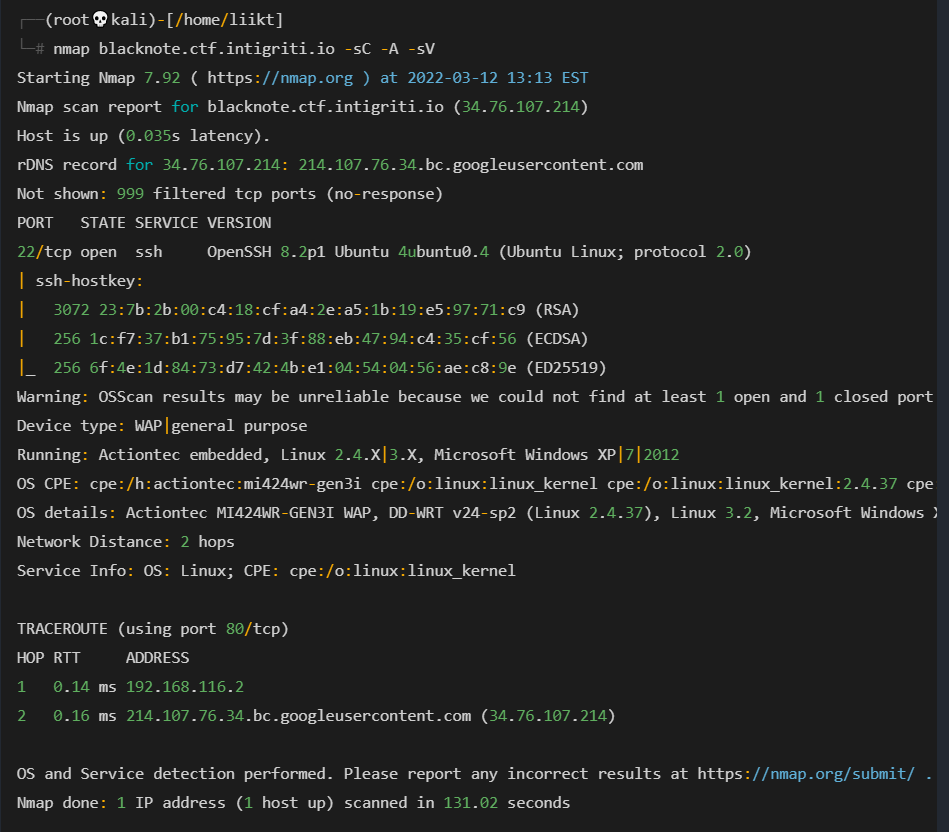
好像SSH开了
从pwned.txt提示中说,backdoor with blackn0te
假设用户名是blackn0te
并且从倾倒的信用中,liikt@hacker.com:best_h3ckerman!69-与描述相匹配
连接时ssh,提示输入id_rsa密码,
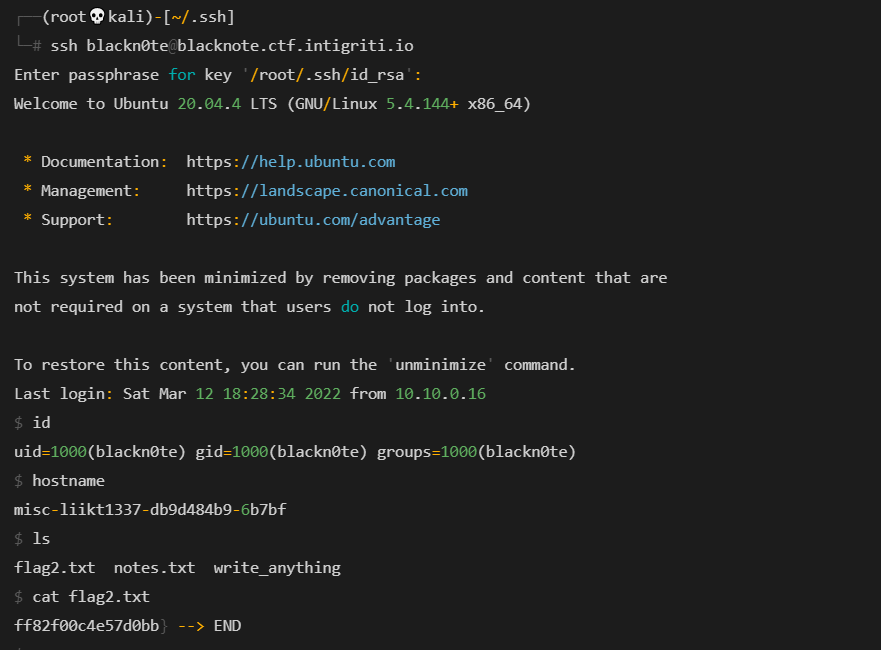
pragyan-ctf-22-Frank's little beauty
描述
Frank has never been a "tech person". He reuses passwords, is too lazy to type, the whole nine yards. And it's just not tech, he's blind as a bat and about as sharp as a round ball too. I mean, he doesn't even know about the shortcut to paddys. Help his son Dennis sift through this memory dump and reconstruct the flag
Note: Use the Win7SP1x64 profile to analyse the dump. All relevant files for this challenge are only present in the C drive and in no other drive
wp
慢速打字机暗示弗兰克依靠剪贴板功能来避免打字 volatility -f MemDump.DMP --profile=Win7SP1x64 clipboard
1 WinSta0 CF_UNICODETEXT 0x300265 0xfffff900c1c0b4a0 https://pastebin.com/3Ecrm2DY
转到
查看正在运行的进程: volatility -f MemDump.DMP --profile=Win7SP1x64 pslist唯一值得注意的似乎是 WinRAR.exe。要查看使用 WinRAR 访问 volatility -f MemDump.DMP --profile=Win7SP1x64 consoles | grep WinRAR.exe
的文件: 我们要查找的文件是 comp.rar。运行 volatility -f MemDump.DMP --profile=Win7SP1x64 filescan | grep comp.rar转储它: volatility -f MemDump.DMP --profile=Win7SP1x64 dumpfiles -n -Q 0x000000003df4e450 --dump-dir .并将文件重命名为comp.rar,然后运行, unrar e comp.rar 但它需要密码。
直接利用mimikatz进行密码提取
trolltoll 为我们提供了包含flag第二部分的 flag.png:"_i5_v3ry_h4ndy_at"
非预期
当时我是利用对flag的猜测肯定有_}故strings找也能得到第三段
最新学习
这个问题引用了稻田的捷径。在 Windows 7 中,快捷方式的扩展名为“.lnk”。搜索 'paddys.lnk': volatility -f MemDump.DMP --profile=Win7SP1x64 filescan | grep -i "paddys.lnk"并 volatility -f MemDump.DMP --profile=Win7SP1x64 dumpfiles -n -Q 0x000000003e1891d0 --dump-dir . 用用十六进制编辑器打开它,我们看到它指向 C:\Program Files\Microsoft Games\Minesweeper\sysinfo.txt
运行volatility -f MemDump.DMP --profile=Win7SP1x64 filescan | grep sysinfo并转储它, volatility -f MemDump.DMP --profile=Win7SP1x64 dumpfiles -n -Q 0x000000003ef7bce0 --dump-dir . 但没有文件得到dumped,表示已被删除。
我们需要从 NTFS 系统使用的 MFT 中获取文件 volatility -f MemDump.DMP --profile=Win7SP1x64 mftparser | grep -C10 sysinfo > mftsysinfo
$STANDARD_INFORMATION 创建修改的 MFT 更改的访问日期类型
2022-02-07 15:58:00 UTC+0000 2022-02-07 14:07:12 UTC+0000 2022-02-07 15:59:56 UTC+0000 2022-02-07 15:58:00 UTC +0000 存档
$FILE_NAME 创建修改的 MFT 更改的访问日期名称/路径
2022-02-07 15:58:00 UTC+0000 2022-02-07 15:58:00 UTC+0000 2022-02-07 15:58:00 UTC+0000 2022-02-07 15:58:00 UTC +0000 程序文件\Microsoft > 游戏\Minesweeper\sysinfo.txt
$ Object_ID对象ID:E069804C-2E88-EC11-B47E-080027E4EB34出生卷ID:80000000-3000-0000-0000-180000000100出生对象ID:15000000-333464316CA67出生域ID:5F64756D-7035-5F69- 6173-69707d000000
$DATA 0000000000:5f 72 33 34 64 31 6e 67 5f 64 75 6d 70 35 5f 69_r34d1ng_dump5_i0000000010:61 73 69 70 7d asip}


