HGAME 2022 misc
Week1
这个压缩包有点麻烦
破解压缩包密码 483279 。
解压后,根据提示,考虑所给的 password-note.txt 是密码本,故字典攻击,得到密码 &- `;qpCKliw2yTR\ 。
再次解压后,经过尝试发现所给 README.txt 与下一层压缩包中的 README.txt 的CRC值相同,故结合提 示,构造一个仅存储的压缩包,然后进行明文攻击。
好康的流量
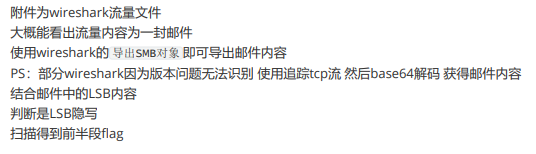
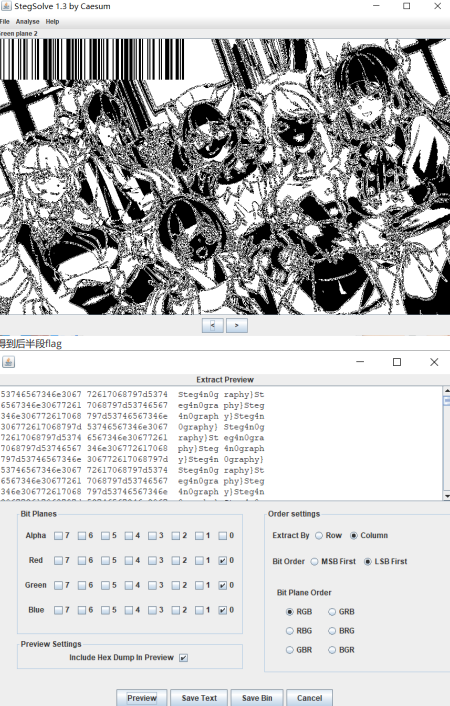
zsteg梭也可以
群青(其实是幽灵东京)
Week2
奇妙小游戏
一张怪怪的名片
你上当了 我的很大
Week3
卡中毒
volaility 取证得到Wannaren
信息搜集
WannarenDecrypt-master解密
谁不喜欢猫猫呢
缩略图提取
from PIL import Image
img=Image.open('a.png')
width,height=img.size
flag=Image.new(mode='RGBA',size=(216,216),color=(255,255,255))
tempi=0
tempj=0
for i in range(5,height,11):
tempi+=1
tempj=0
for j in range(5,width,11):
tempj+=1
flag.putpixel((tempi,tempj),img.getpixel((i,j)))
print(tempi,tempj)
flag.save('flag1.png')
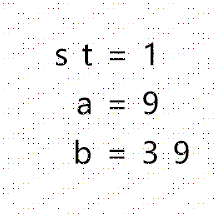
from PIL import Image
img=Image.open('a.png')
width,height=img.size
flag=Image.new(mode='RGBA',size=(44,44),color=(255,255,255))
tempi=0
tempj=0
for i in range(3,height,5):
tempi+=1
tempj=0
for j in range(3,width,5):
tempj+=1
flag.putpixel((tempi,tempj),img.getpixel((i,j)))
print(tempi,tempj)
flag.save('flag2.png')
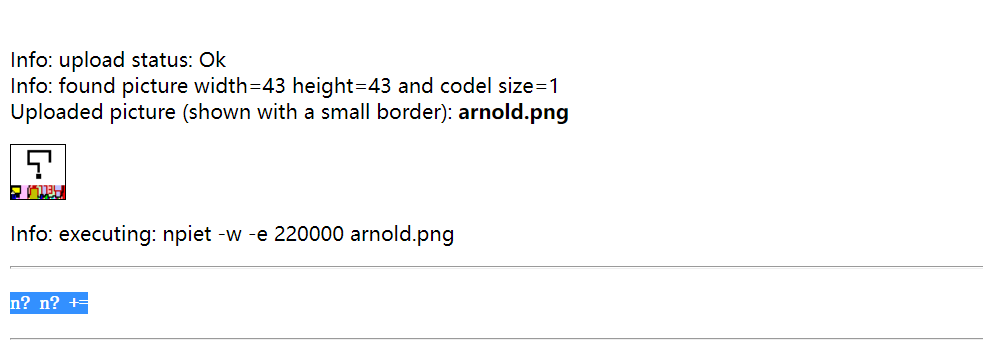
再提取一次
进行arnold decode
import matplotlib.pyplot as plt
import cv2
import numpy as np
from PIL import Image
it=cv2.imread('flag2.png')
def arnold_decode(image, shuffle_times, a, b):
""" decode for rgb image that encoded by Arnold
Args:
image: rgb image encoded by Arnold
shuffle_times: how many times to shuffle
Returns:
decode image
"""
# 1:创建新图像
decode_image = np.zeros(shape=image.shape)
# 2:计算N
h, w = image.shape[0], image.shape[1]
N = h # 或N=w
# 3:遍历像素坐标变换
for time in range(shuffle_times):
for ori_x in range(h):
for ori_y in range(w):
# 按照公式坐标变换
new_x = ((a*b+1)*ori_x + (-b)* ori_y)% N
new_y = ((-a)*ori_x + ori_y) % N
decode_image[new_x, new_y, :] = image[ori_x, ori_y, :]
cv2.imwrite('flag.png',decode_image, [int(cv2.IMWRITE_PNG_COMPRESSION), 0])
return decode_image
arnold_decode(it,1,9,39)

再把初始图片分离出的list1与list2
a=[776686, 749573, 6395443, 2522866, 279584, 587965, 4012670, 1645156, 2184634]
b=[6065523, 6419830, 1421837, 5103682, 5963053, 2842996, 1113825, 1594064, 4578755]
from Crypto.Util.number import *
result=[]
flag=b''
for i in range(0,len(a)):
result.append(a[i]+b[i])
for i in result:
flag+=long_to_bytes(i)
print(flag)
hgame{wH@t_4_AM4Z1N9_1m4g3}


 浙公网安备 33010602011771号
浙公网安备 33010602011771号