第二篇 信息收集之服务信息收集
服务信息收集主要包括:域名信息、服务器相关信息(比如IP、CDN、端口等)、Web指纹信息、旁站信息等
1 域名信息收集
通过域名收集,目的是找到服务的相关信息,比如域名所有人、注册商、注册商邮箱等,一般对于小型的网站,注册商一般就是个人,即找到注册商信息,就是个人信息
1.1 whois的使用
可以用来查询域名的IP及所有者信息
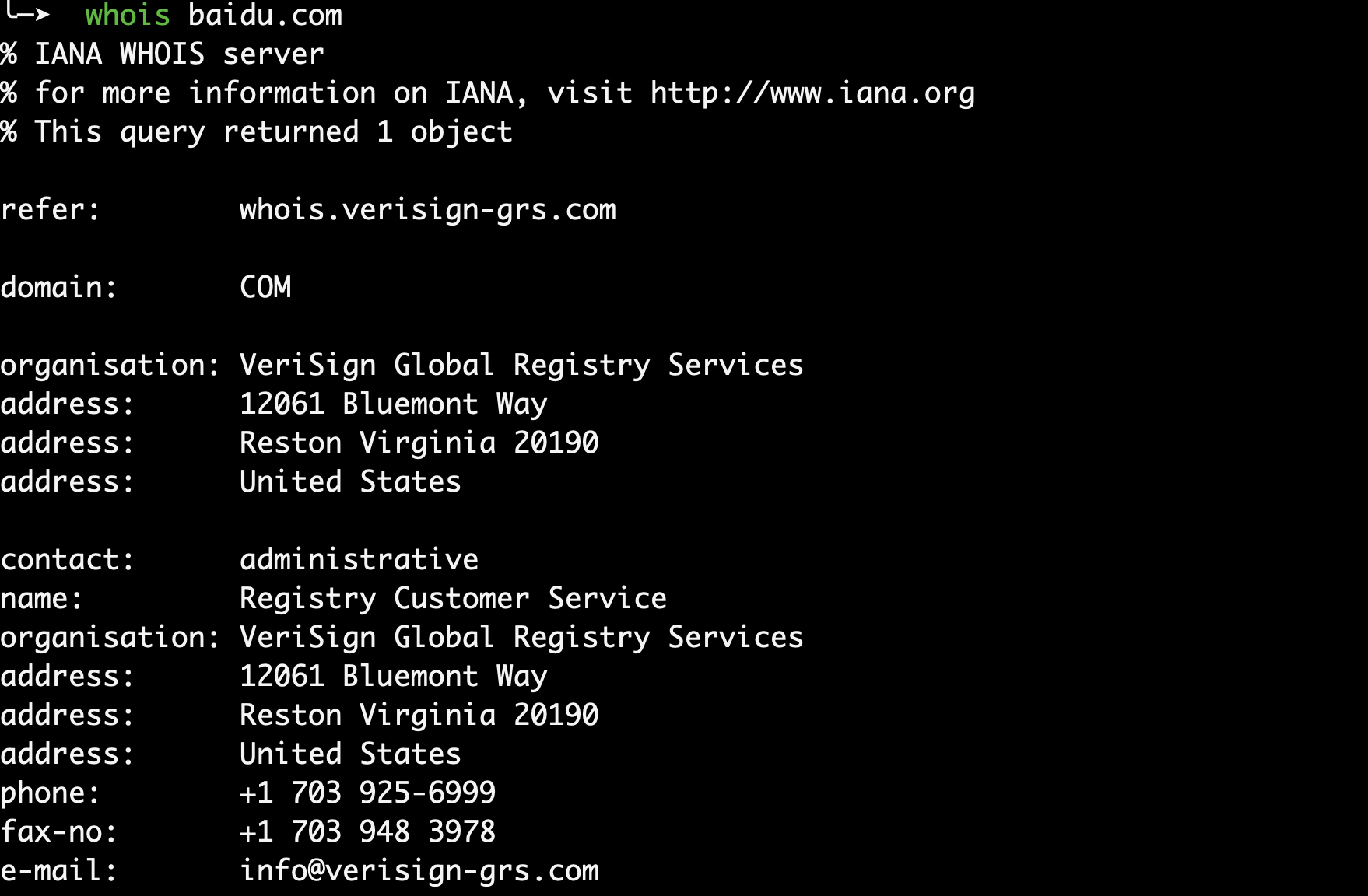
使用whois进行查询的时候,展示的内容不是很直观,可以直接使用一些在线网站进行查询,比如:
站长之家 http://whois.chinaz.com/
爱站网域名 https://whois.aizhan.com/
中国万网域名 https://whois.aliyun.com/
国外WHOIS信息查询地址 https://who.is/
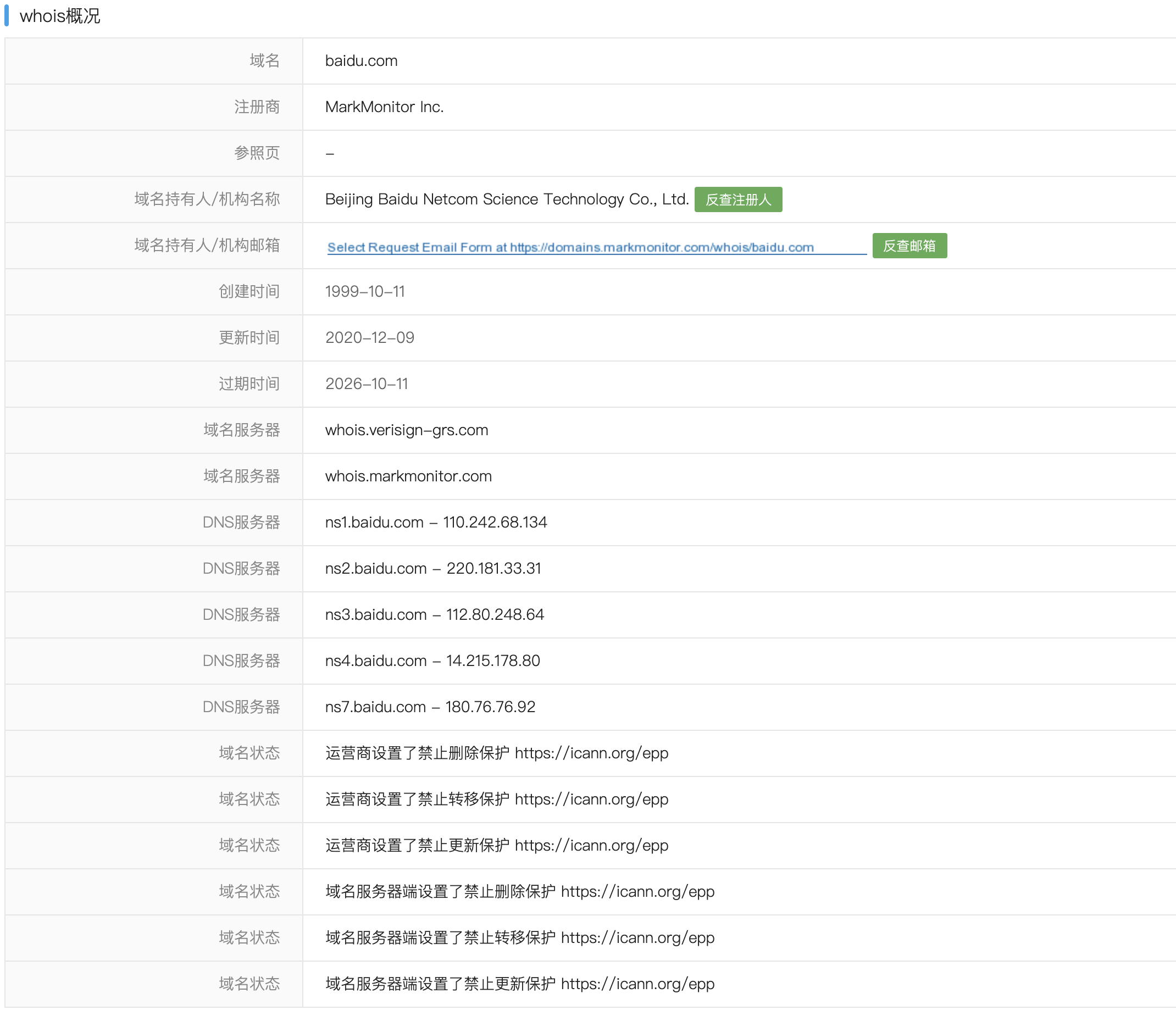
- 使用爱站查询
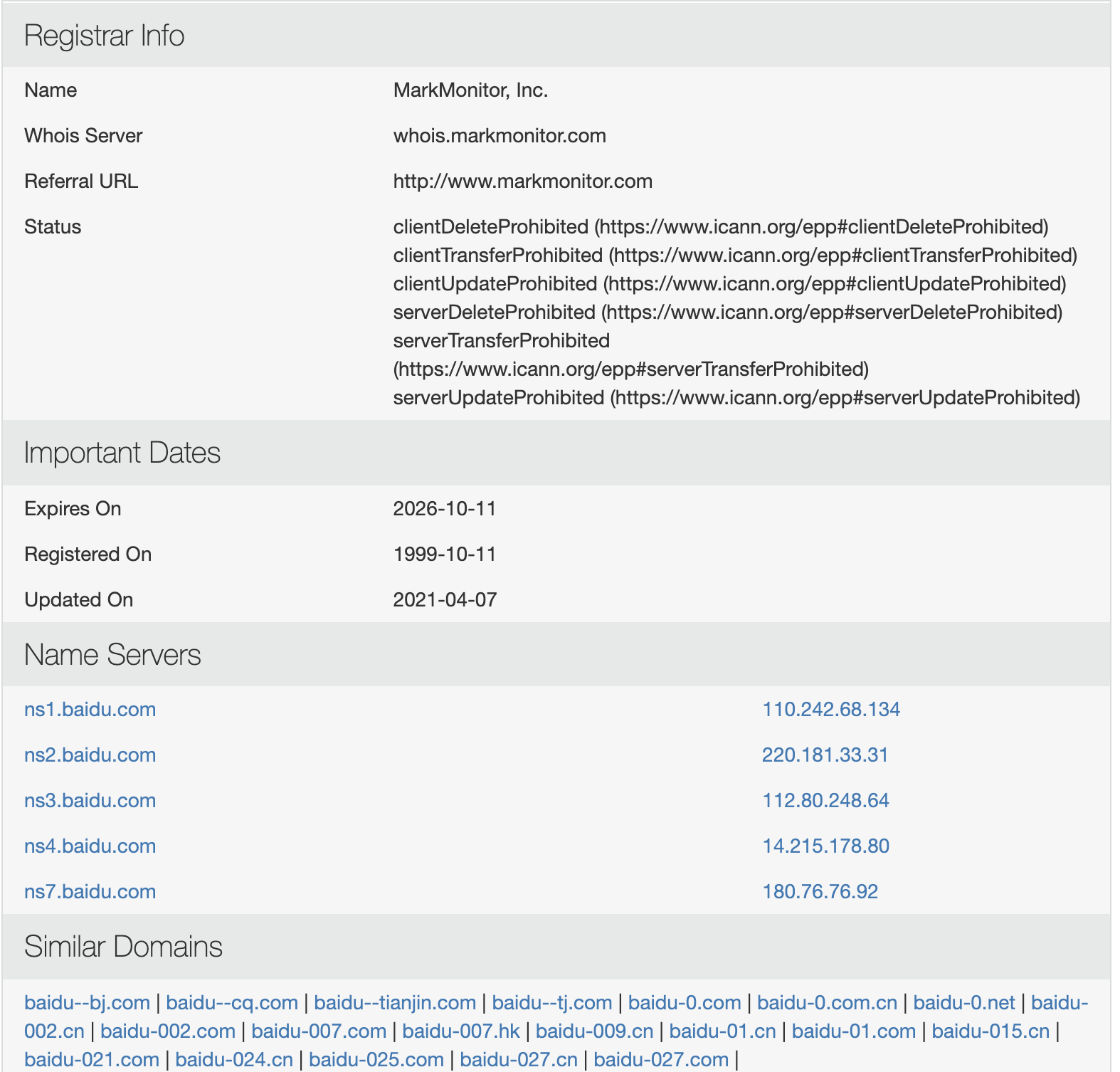
- 使用国外网站进行查询
1.2 子域名收集
在对目标进行渗透测试时候,目标做的各种防护可能比较完善,这是可以借助子域名去发现更多服务,这些服务可能使用的都是同一套代码模版,不重要的服务出现漏洞的几率更大。
对于子域名的收集,可以借助搜索引擎的方式,也可以借用一些现成工具来完成
- Layer子域名挖掘机
链接: https://pan.baidu.com/s/1DBC2NdLYm7qIUjT0sUIJ7g 提取码: bjyv
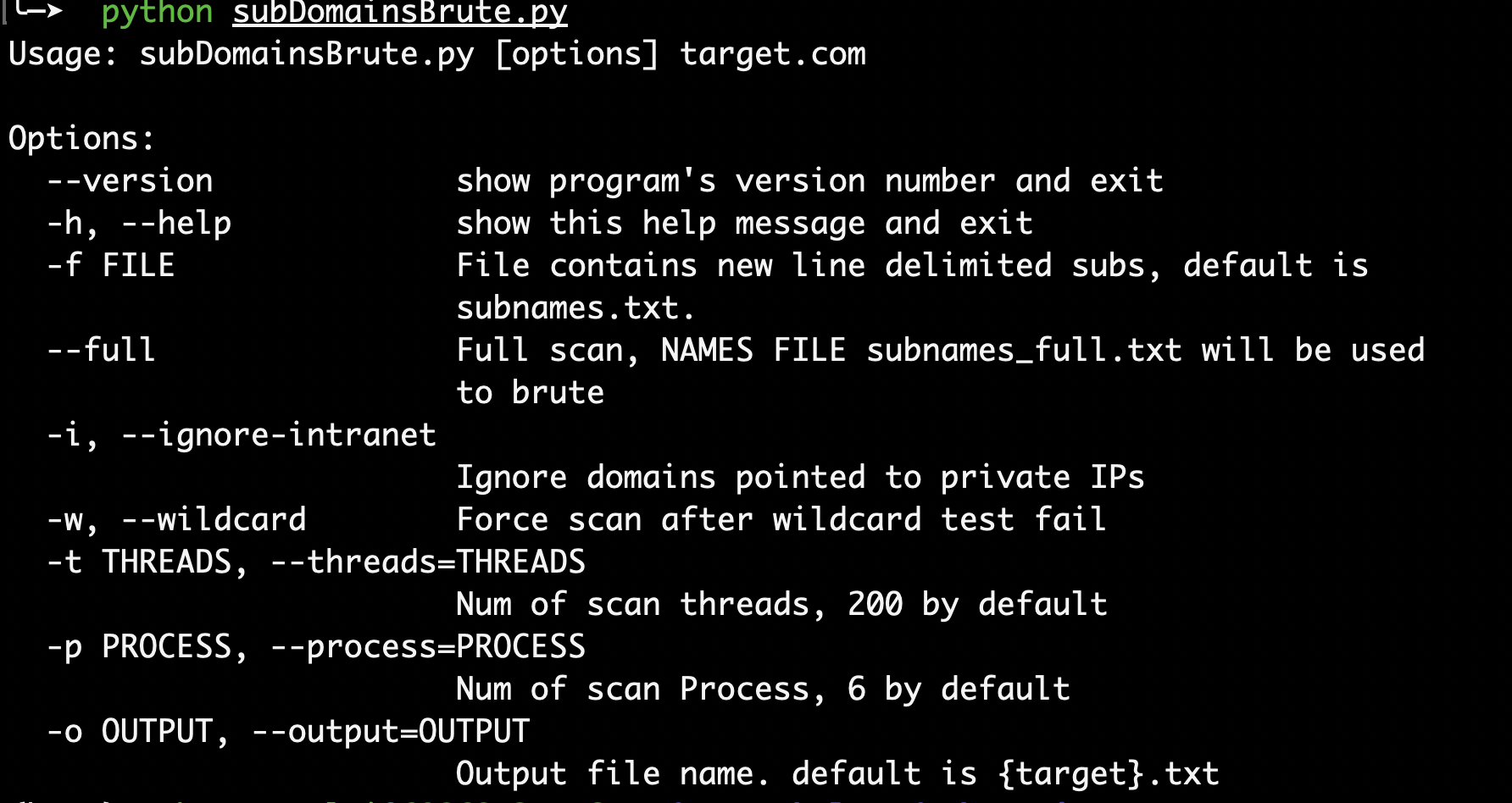
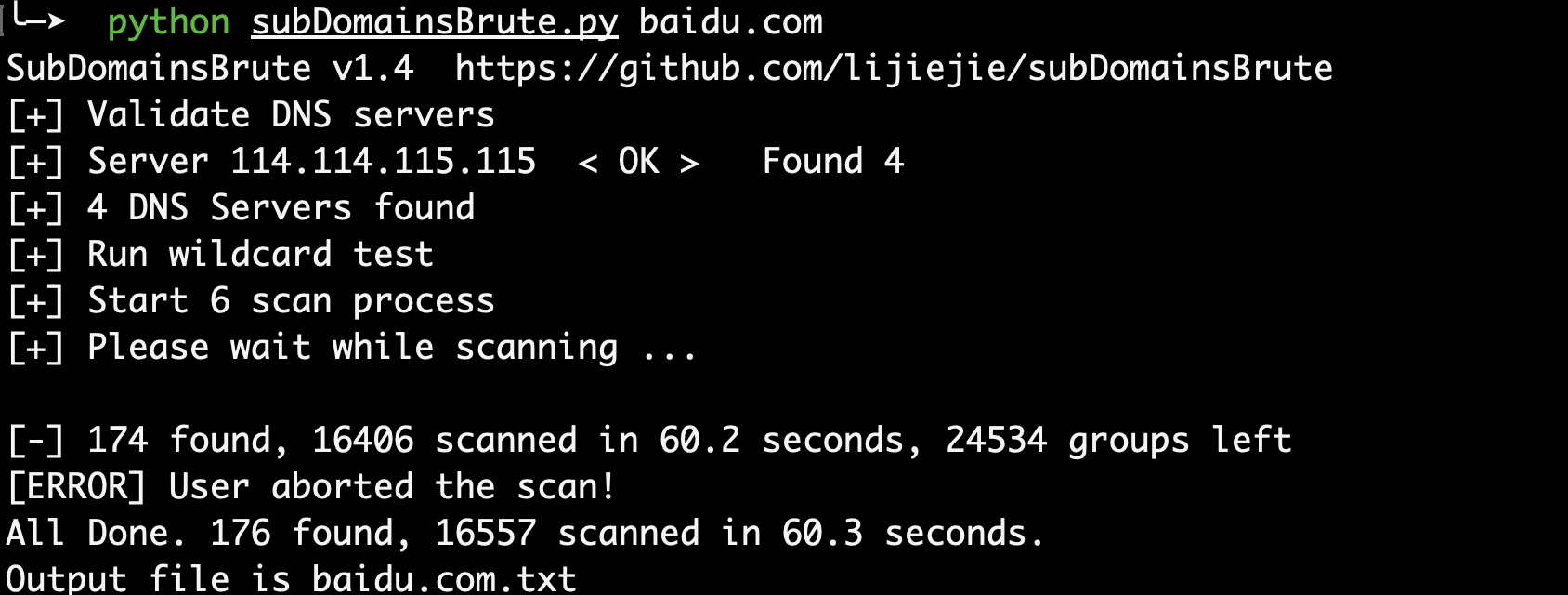
- subDomainsBrute
https://github.com/lijiejie/subDomainsBrute
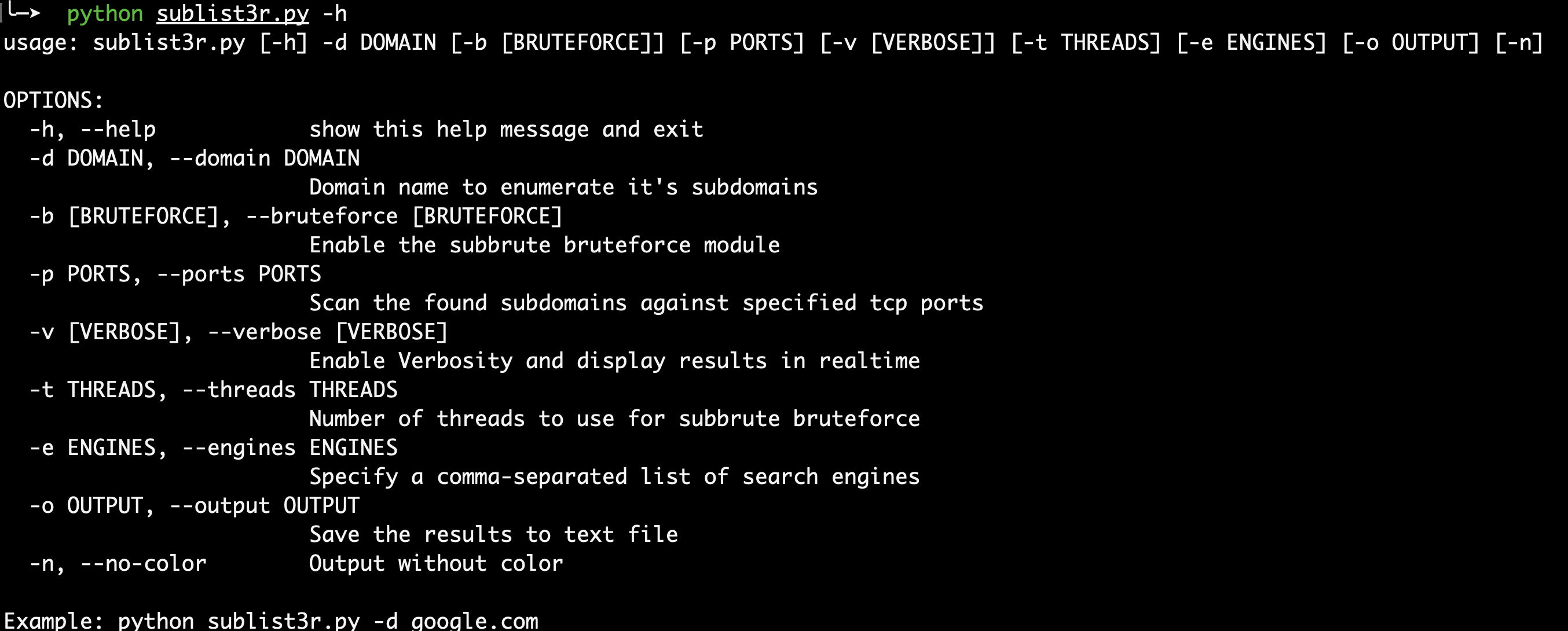
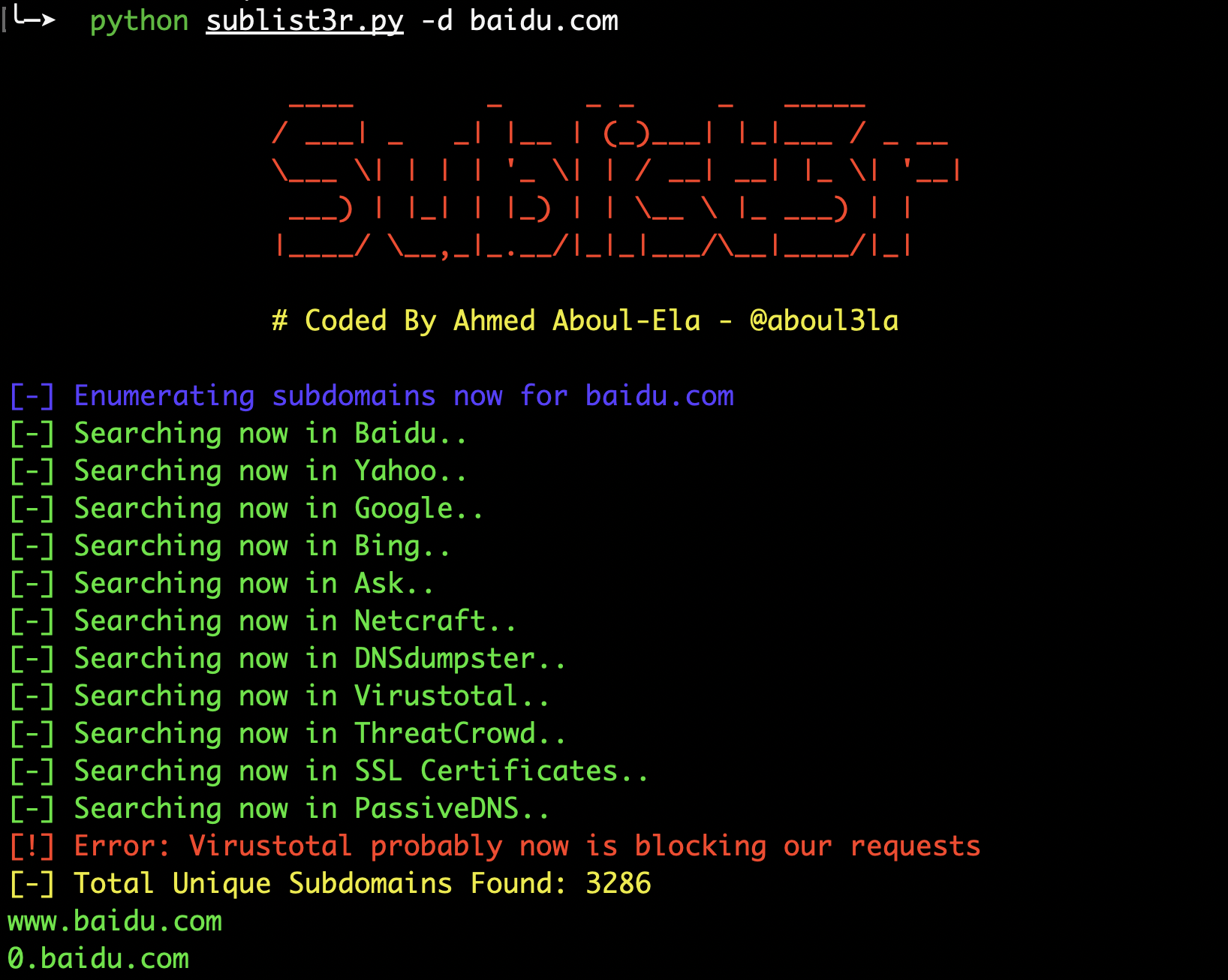
- Sublist3r
https://github.com/aboul3la/Sublist3r
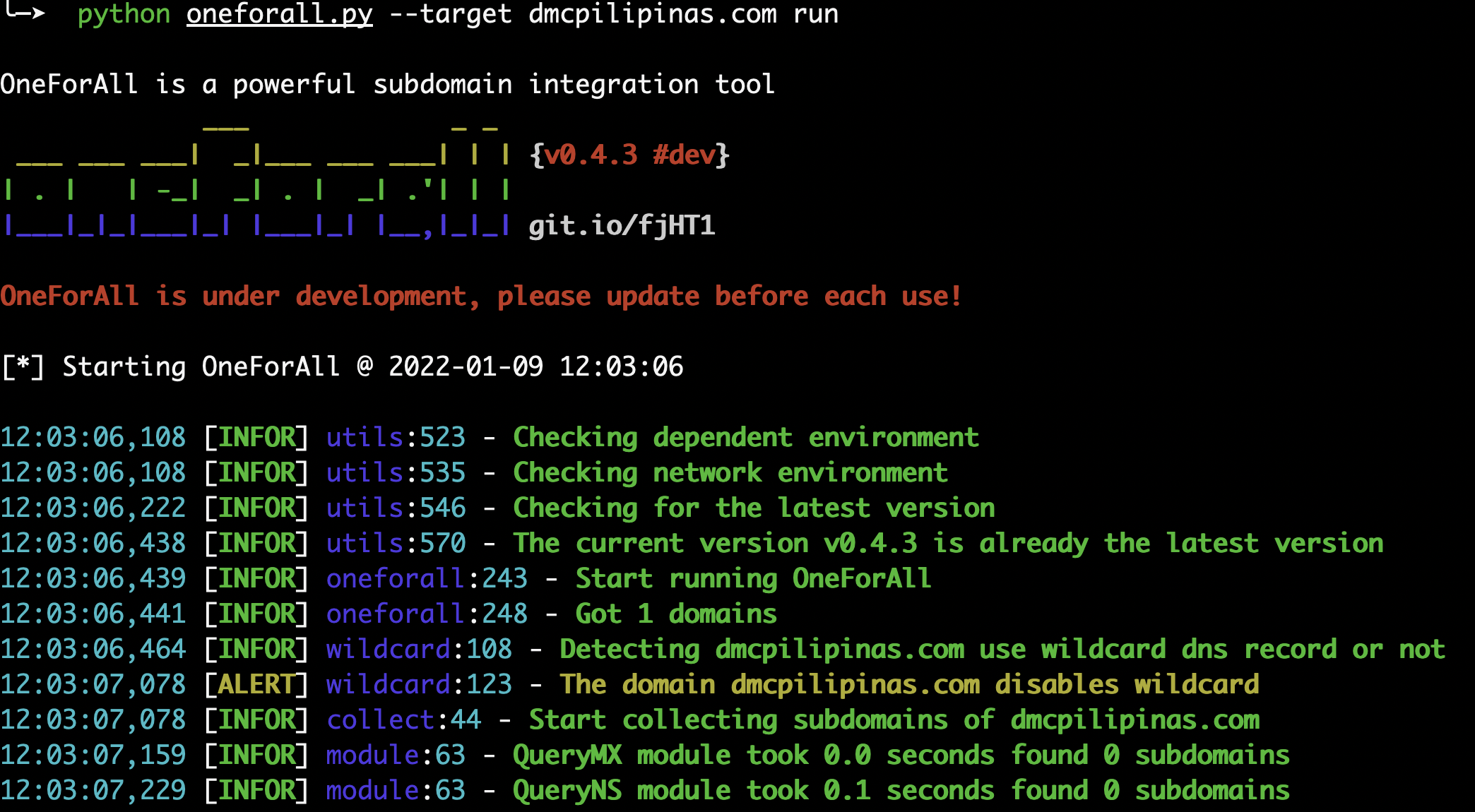
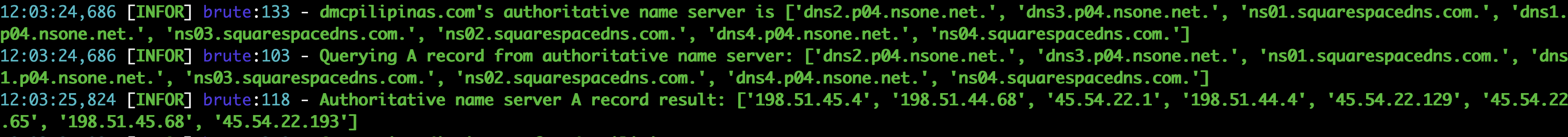
- OneForAll
https://github.com/shmilylty/OneForAll
2 服务相关信息收集
2.1 获取服务的真实IP
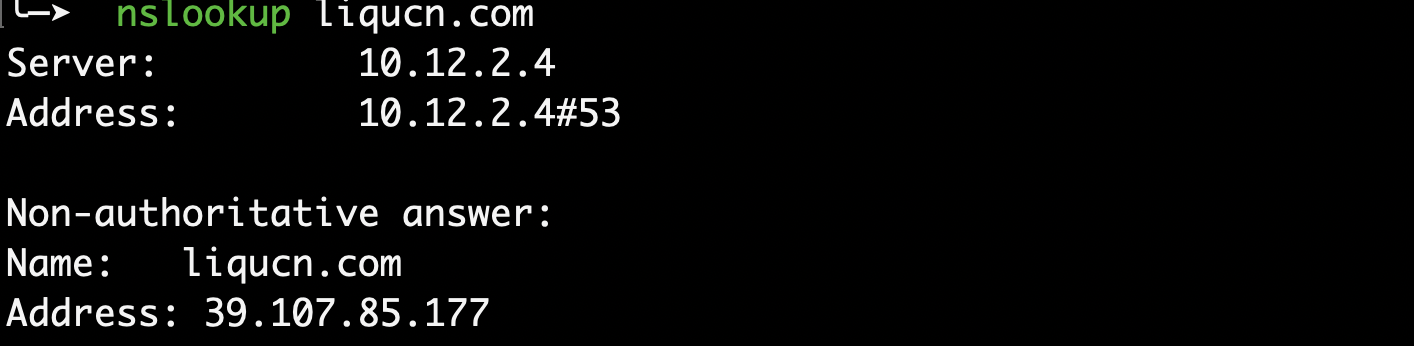
目前很多网站都使用CDN,所以想要获取真实的IP的,就需要对CDN进行绕过,简单做法就是使用ping命令多次对一个域名进行尝试,查看IP是否发现变化,如果有VPN,可以通过切换VPN的方式进行尝试,一般情况下,使用VPN的都是主站,比如www.xxx.com, 这个时候也可以通过尝试ping其他的域名,比如:xxx.com
- 使用nslookup命令
使用cdn
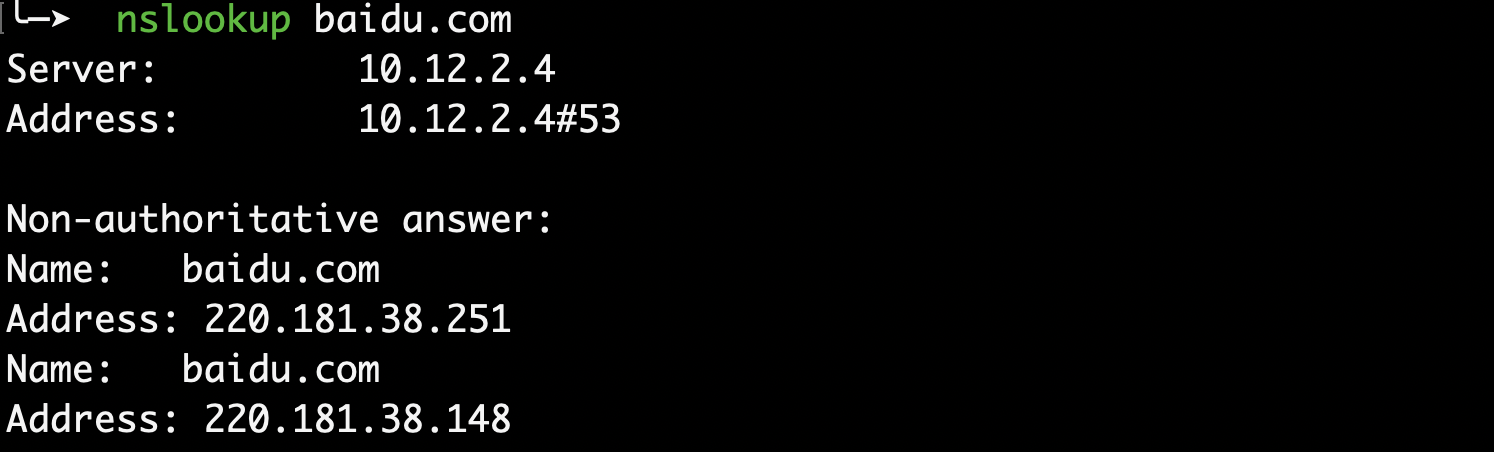
没有使用cdn
- 使用在线网站查询
-- www.baidu.com
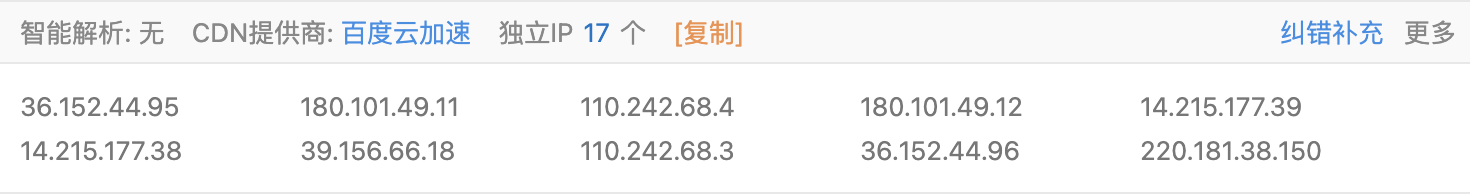
-- liqucn.com
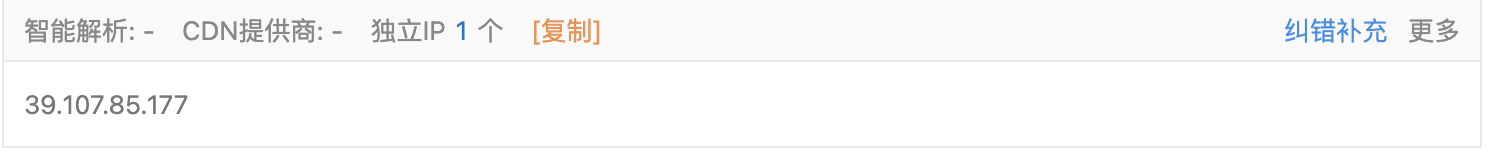
2.1.1 绕过CDN
- 获取内部邮箱服务IP
- 子域名查询
- 异地访问,特别流量比较小的区域,网络不发达的区域,如果是国内网站,可以使用国外IP访问
- 查询dns历史解析记录,根据重复多的IP进行猜测
http://viewdns.info/
https://x.threatbook.cn/
http://www.17ce.com/
2.2 端口信息收集
指的是开放端口的信息收集,常用的工具有nmap和masscan
2.2.1 nmap的使用
$ nmap -h
Nmap 7.91 ( https://nmap.org )
Usage: nmap [Scan Type(s)] [Options] {target specification}
TARGET SPECIFICATION:
Can pass hostnames, IP addresses, networks, etc.
Ex: scanme.nmap.org, microsoft.com/24, 192.168.0.1; 10.0.0-255.1-254
-iL <inputfilename>: Input from list of hosts/networks
-iR <num hosts>: Choose random targets
--exclude <host1[,host2][,host3],...>: Exclude hosts/networks
--excludefile <exclude_file>: Exclude list from file
HOST DISCOVERY:
-sL: List Scan - simply list targets to scan
-sn: Ping Scan - disable port scan
-Pn: Treat all hosts as online -- skip host discovery
-PS/PA/PU/PY[portlist]: TCP SYN/ACK, UDP or SCTP discovery to given ports
-PE/PP/PM: ICMP echo, timestamp, and netmask request discovery probes
-PO[protocol list]: IP Protocol Ping
-n/-R: Never do DNS resolution/Always resolve [default: sometimes]
--dns-servers <serv1[,serv2],...>: Specify custom DNS servers
--system-dns: Use OS's DNS resolver
--traceroute: Trace hop path to each host
SCAN TECHNIQUES:
-sS/sT/sA/sW/sM: TCP SYN/Connect()/ACK/Window/Maimon scans
-sU: UDP Scan
-sN/sF/sX: TCP Null, FIN, and Xmas scans
--scanflags <flags>: Customize TCP scan flags
-sI <zombie host[:probeport]>: Idle scan
-sY/sZ: SCTP INIT/COOKIE-ECHO scans
-sO: IP protocol scan
-b <FTP relay host>: FTP bounce scan
PORT SPECIFICATION AND SCAN ORDER:
-p <port ranges>: Only scan specified ports
Ex: -p22; -p1-65535; -p U:53,111,137,T:21-25,80,139,8080,S:9
--exclude-ports <port ranges>: Exclude the specified ports from scanning
-F: Fast mode - Scan fewer ports than the default scan
-r: Scan ports consecutively - don't randomize
--top-ports <number>: Scan <number> most common ports
--port-ratio <ratio>: Scan ports more common than <ratio>
SERVICE/VERSION DETECTION:
-sV: Probe open ports to determine service/version info
--version-intensity <level>: Set from 0 (light) to 9 (try all probes)
--version-light: Limit to most likely probes (intensity 2)
--version-all: Try every single probe (intensity 9)
--version-trace: Show detailed version scan activity (for debugging)
SCRIPT SCAN:
-sC: equivalent to --script=default
--script=<Lua scripts>: <Lua scripts> is a comma separated list of
directories, script-files or script-categories
--script-args=<n1=v1,[n2=v2,...]>: provide arguments to scripts
--script-args-file=filename: provide NSE script args in a file
--script-trace: Show all data sent and received
--script-updatedb: Update the script database.
--script-help=<Lua scripts>: Show help about scripts.
<Lua scripts> is a comma-separated list of script-files or
script-categories.
OS DETECTION:
-O: Enable OS detection
--osscan-limit: Limit OS detection to promising targets
--osscan-guess: Guess OS more aggressively
TIMING AND PERFORMANCE:
Options which take <time> are in seconds, or append 'ms' (milliseconds),
's' (seconds), 'm' (minutes), or 'h' (hours) to the value (e.g. 30m).
-T<0-5>: Set timing template (higher is faster)
--min-hostgroup/max-hostgroup <size>: Parallel host scan group sizes
--min-parallelism/max-parallelism <numprobes>: Probe parallelization
--min-rtt-timeout/max-rtt-timeout/initial-rtt-timeout <time>: Specifies
probe round trip time.
--max-retries <tries>: Caps number of port scan probe retransmissions.
--host-timeout <time>: Give up on target after this long
--scan-delay/--max-scan-delay <time>: Adjust delay between probes
--min-rate <number>: Send packets no slower than <number> per second
--max-rate <number>: Send packets no faster than <number> per second
FIREWALL/IDS EVASION AND SPOOFING:
-f; --mtu <val>: fragment packets (optionally w/given MTU)
-D <decoy1,decoy2[,ME],...>: Cloak a scan with decoys
-S <IP_Address>: Spoof source address
-e <iface>: Use specified interface
-g/--source-port <portnum>: Use given port number
--proxies <url1,[url2],...>: Relay connections through HTTP/SOCKS4 proxies
--data <hex string>: Append a custom payload to sent packets
--data-string <string>: Append a custom ASCII string to sent packets
--data-length <num>: Append random data to sent packets
--ip-options <options>: Send packets with specified ip options
--ttl <val>: Set IP time-to-live field
--spoof-mac <mac address/prefix/vendor name>: Spoof your MAC address
--badsum: Send packets with a bogus TCP/UDP/SCTP checksum
OUTPUT:
-oN/-oX/-oS/-oG <file>: Output scan in normal, XML, s|<rIpt kIddi3,
and Grepable format, respectively, to the given filename.
-oA <basename>: Output in the three major formats at once
-v: Increase verbosity level (use -vv or more for greater effect)
-d: Increase debugging level (use -dd or more for greater effect)
--reason: Display the reason a port is in a particular state
--open: Only show open (or possibly open) ports
--packet-trace: Show all packets sent and received
--iflist: Print host interfaces and routes (for debugging)
--append-output: Append to rather than clobber specified output files
--resume <filename>: Resume an aborted scan
--stylesheet <path/URL>: XSL stylesheet to transform XML output to HTML
--webxml: Reference stylesheet from Nmap.Org for more portable XML
--no-stylesheet: Prevent associating of XSL stylesheet w/XML output
MISC:
-6: Enable IPv6 scanning
-A: Enable OS detection, version detection, script scanning, and traceroute
--datadir <dirname>: Specify custom Nmap data file location
--send-eth/--send-ip: Send using raw ethernet frames or IP packets
--privileged: Assume that the user is fully privileged
--unprivileged: Assume the user lacks raw socket privileges
-V: Print version number
-h: Print this help summary page.
EXAMPLES:
nmap -v -A scanme.nmap.org
nmap -v -sn 192.168.0.0/16 10.0.0.0/8
nmap -v -iR 10000 -Pn -p 80
SEE THE MAN PAGE (https://nmap.org/book/man.html) FOR MORE OPTIONS AND EXAMPLES
常用命令:
-A:全面扫描
-sV:服务版本探测
-O:操作系统
-p:端口
-v:显示详细扫描内容
-F:快速扫描
-sS:SYN扫描
-sP:ping扫描
- nmap -A 192.168.2.143
Starting Nmap 7.91 ( https://nmap.org ) at 2022-01-09 00:56 EST
Nmap scan report for 192.168.2.143
Host is up (0.00064s latency).
Not shown: 978 closed ports
PORT STATE SERVICE VERSION
21/tcp open ftp vsftpd 2.3.4
|_ftp-anon: Anonymous FTP login allowed (FTP code 230)
| ftp-syst:
| STAT:
| FTP server status:
| Connected to 192.168.2.128
| Logged in as ftp
| TYPE: ASCII
| No session bandwidth limit
| Session timeout in seconds is 300
| Control connection is plain text
| Data connections will be plain text
| vsFTPd 2.3.4 - secure, fast, stable
|_End of status
22/tcp open ssh OpenSSH 4.7p1 Debian 8ubuntu1 (protocol 2.0)
| ssh-hostkey:
| 1024 60:0f:cf:e1:c0:5f:6a:74:d6:90:24:fa:c4:d5:6c:cd (DSA)
|_ 2048 56:56:24:0f:21:1d:de:a7:2b:ae:61:b1:24:3d:e8:f3 (RSA)
23/tcp open telnet Linux telnetd
25/tcp open smtp Postfix smtpd
|_smtp-commands: metasploitable.localdomain, PIPELINING, SIZE 10240000, VRFY, ETRN, STARTTLS, ENHANCEDSTATUSCODES, 8BITMIME, DSN,
| ssl-cert: Subject: commonName=ubuntu804-base.localdomain/organizationName=OCOSA/stateOrProvinceName=There is no such thing outside US/countryName=XX
| Not valid before: 2010-03-17T14:07:45
|_Not valid after: 2010-04-16T14:07:45
|_ssl-date: 2022-01-09T05:56:37+00:00; 0s from scanner time.
| sslv2:
| SSLv2 supported
| ciphers:
| SSL2_RC2_128_CBC_EXPORT40_WITH_MD5
| SSL2_RC2_128_CBC_WITH_MD5
| SSL2_DES_64_CBC_WITH_MD5
| SSL2_DES_192_EDE3_CBC_WITH_MD5
| SSL2_RC4_128_WITH_MD5
|_ SSL2_RC4_128_EXPORT40_WITH_MD5
80/tcp open http Apache httpd 2.2.8 ((Ubuntu) DAV/2)
|_http-server-header: Apache/2.2.8 (Ubuntu) DAV/2
|_http-title: Metasploitable2 - Linux
111/tcp open rpcbind 2 (RPC #100000)
| rpcinfo:
| program version port/proto service
| 100000 2 111/tcp rpcbind
| 100000 2 111/udp rpcbind
| 100003 2,3,4 2049/tcp nfs
| 100003 2,3,4 2049/udp nfs
| 100005 1,2,3 40608/tcp mountd
| 100005 1,2,3 59833/udp mountd
| 100021 1,3,4 44962/udp nlockmgr
| 100021 1,3,4 56658/tcp nlockmgr
| 100024 1 42170/udp status
|_ 100024 1 56496/tcp status
139/tcp open netbios-ssn Samba smbd 3.X - 4.X (workgroup: WORKGROUP)
445/tcp open netbios-ssn Samba smbd 3.0.20-Debian (workgroup: WORKGROUP)
512/tcp open exec netkit-rsh rexecd
513/tcp open login OpenBSD or Solaris rlogind
514/tcp open tcpwrapped
1099/tcp open java-rmi GNU Classpath grmiregistry
1524/tcp open bindshell Metasploitable root shell
2049/tcp open nfs 2-4 (RPC #100003)
2121/tcp open ftp ProFTPD 1.3.1
3306/tcp open mysql MySQL 5.0.51a-3ubuntu5
| mysql-info:
| Protocol: 10
| Version: 5.0.51a-3ubuntu5
| Thread ID: 19
| Capabilities flags: 43564
| Some Capabilities: SupportsTransactions, Support41Auth, SwitchToSSLAfterHandshake, LongColumnFlag, Speaks41ProtocolNew, ConnectWithDatabase, SupportsCompression
| Status: Autocommit
|_ Salt: efP@,[hw=ixB!ya\(Q@-
5432/tcp open postgresql PostgreSQL DB 8.3.0 - 8.3.7
| ssl-cert: Subject: commonName=ubuntu804-base.localdomain/organizationName=OCOSA/stateOrProvinceName=There is no such thing outside US/countryName=XX
| Not valid before: 2010-03-17T14:07:45
|_Not valid after: 2010-04-16T14:07:45
|_ssl-date: 2022-01-09T05:56:37+00:00; 0s from scanner time.
5900/tcp open vnc VNC (protocol 3.3)
| vnc-info:
| Protocol version: 3.3
| Security types:
|_ VNC Authentication (2)
6000/tcp open X11 (access denied)
6667/tcp filtered irc
8009/tcp open ajp13 Apache Jserv (Protocol v1.3)
|_ajp-methods: Failed to get a valid response for the OPTION request
8180/tcp open http Apache Tomcat/Coyote JSP engine 1.1
|_http-favicon: Apache Tomcat
|_http-server-header: Apache-Coyote/1.1
|_http-title: Apache Tomcat/5.5
Service Info: Host: metasploitable.localdomain; OSs: Unix, Linux; CPE: cpe:/o:linux:linux_kernel
Host script results:
|_clock-skew: mean: 1h15m00s, deviation: 2h30m00s, median: 0s
|_nbstat: NetBIOS name: METASPLOITABLE, NetBIOS user: <unknown>, NetBIOS MAC: <unknown> (unknown)
| smb-os-discovery:
| OS: Unix (Samba 3.0.20-Debian)
| Computer name: metasploitable
| NetBIOS computer name:
| Domain name: localdomain
| FQDN: metasploitable.localdomain
|_ System time: 2022-01-09T00:56:30-05:00
| smb-security-mode:
| account_used: guest
| authentication_level: user
| challenge_response: supported
|_ message_signing: disabled (dangerous, but default)
|_smb2-time: Protocol negotiation failed (SMB2)
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 20.37 seconds
从扫描结果可以看到开放的端口信息,比如:21、80等
返回状态结果说明:
open:端口对外开放
closed:端口对外关闭
filtered:无法判断,被防火墙设备拦截
unfiltered:未被过滤,使用ACK扫描才可能出现这种情况
- nmap -sP -O 192.168.2.1/24
扫描在线的主机
└─$ nmap -sP 192.168.2.1/24
Starting Nmap 7.91 ( https://nmap.org ) at 2022-01-09 01:05 EST
Nmap scan report for 192.168.2.1
Host is up (0.00069s latency).
Nmap scan report for 192.168.2.2
Host is up (0.00053s latency).
Nmap scan report for 192.168.2.128
Host is up (0.00020s latency).
Nmap scan report for 192.168.2.143
Host is up (0.00038s latency).
Nmap done: 256 IP addresses (4 hosts up) scanned in 2.56 seconds
2.2.2 masscan的使用
一般用来扫描大的目标,5分钟内扫描整个互联网,用法类似nmap
- masscan -p80 192.168.2.1/24

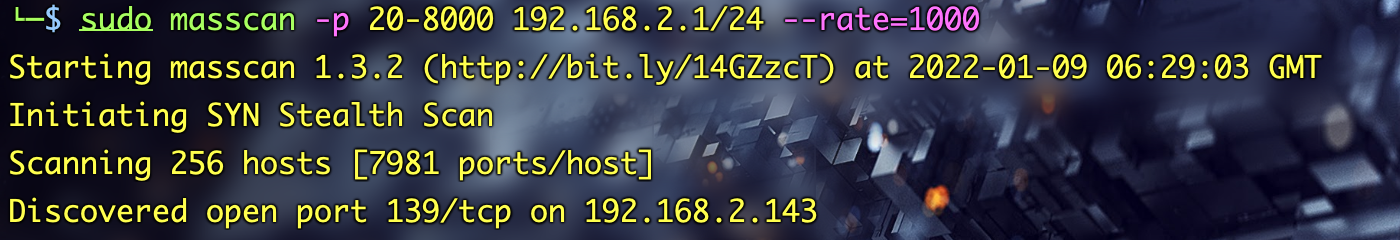
2.2.3 使用在线网站查询
在使用工具进行查询的时候,往往会留下痕迹,所以也可以使用在线网站的方式进行查询

也可以通过shodan、fofa等进行搜索
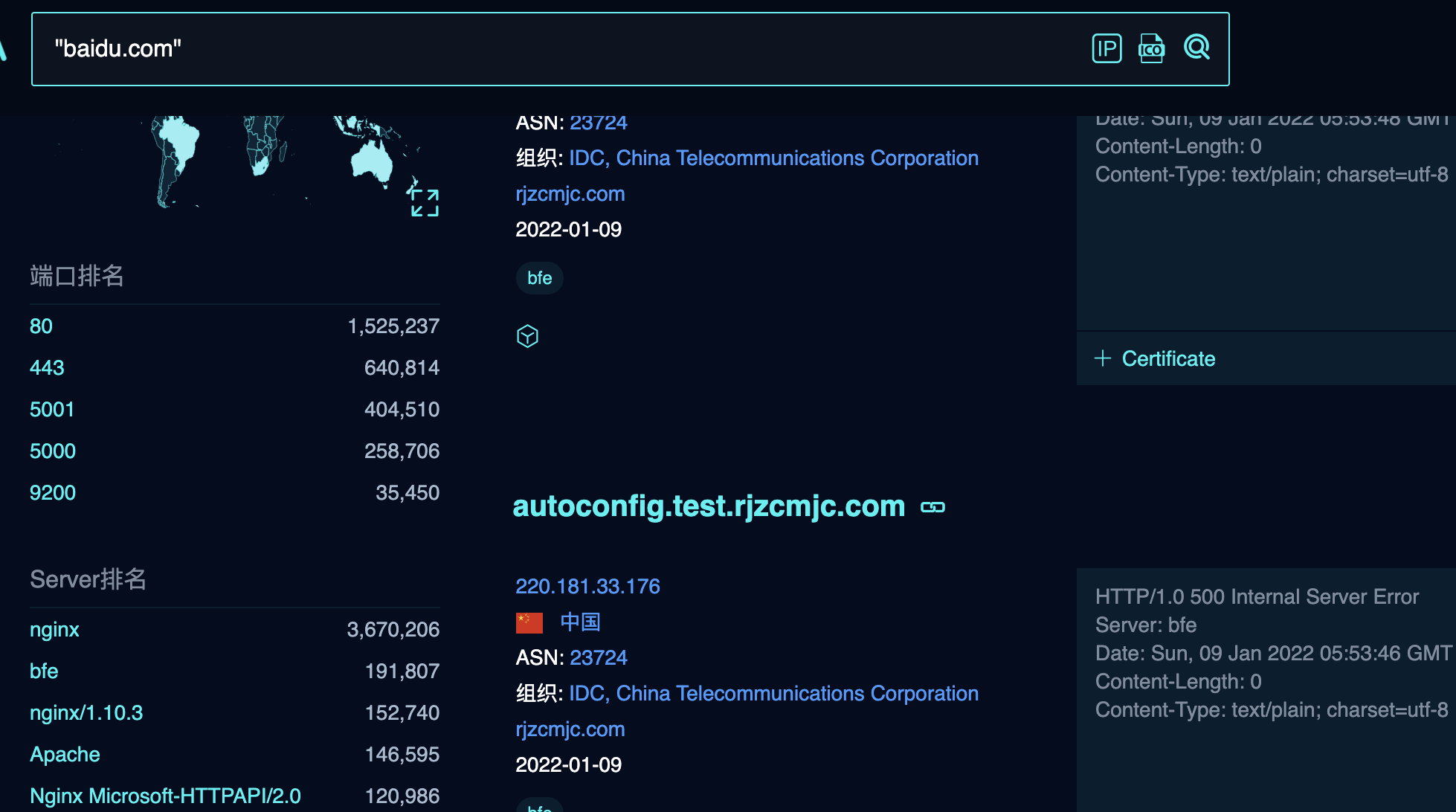
2.3 Web指纹收集
指纹识别指的是网站CMS(Content Management System)内容管理系统的探测、计算机操作系统及Web容器的指纹识别等,应用程序一般在HTML、JS、CSS文件中包含一些特征码,而这些特征码就是指纹,指纹识别主要分为两种,一种是特定页面文件内容匹配,另一种特定文件MD5值匹配。
常见的CMS有:WordPress、Dedecms、Discuz、PhpWeb、PhpWind、Dvbbs、PhpCMS、ECShop、SiteWeaver、AspCMS、Z-Blog等
2.3.1 在线网站识别
BugScaner:http://whatweb.bugscaner.com/look/
云悉指纹:http://www.yunsee.cn/finger.html
潮汐指纹:http://finger.tidesec.com/
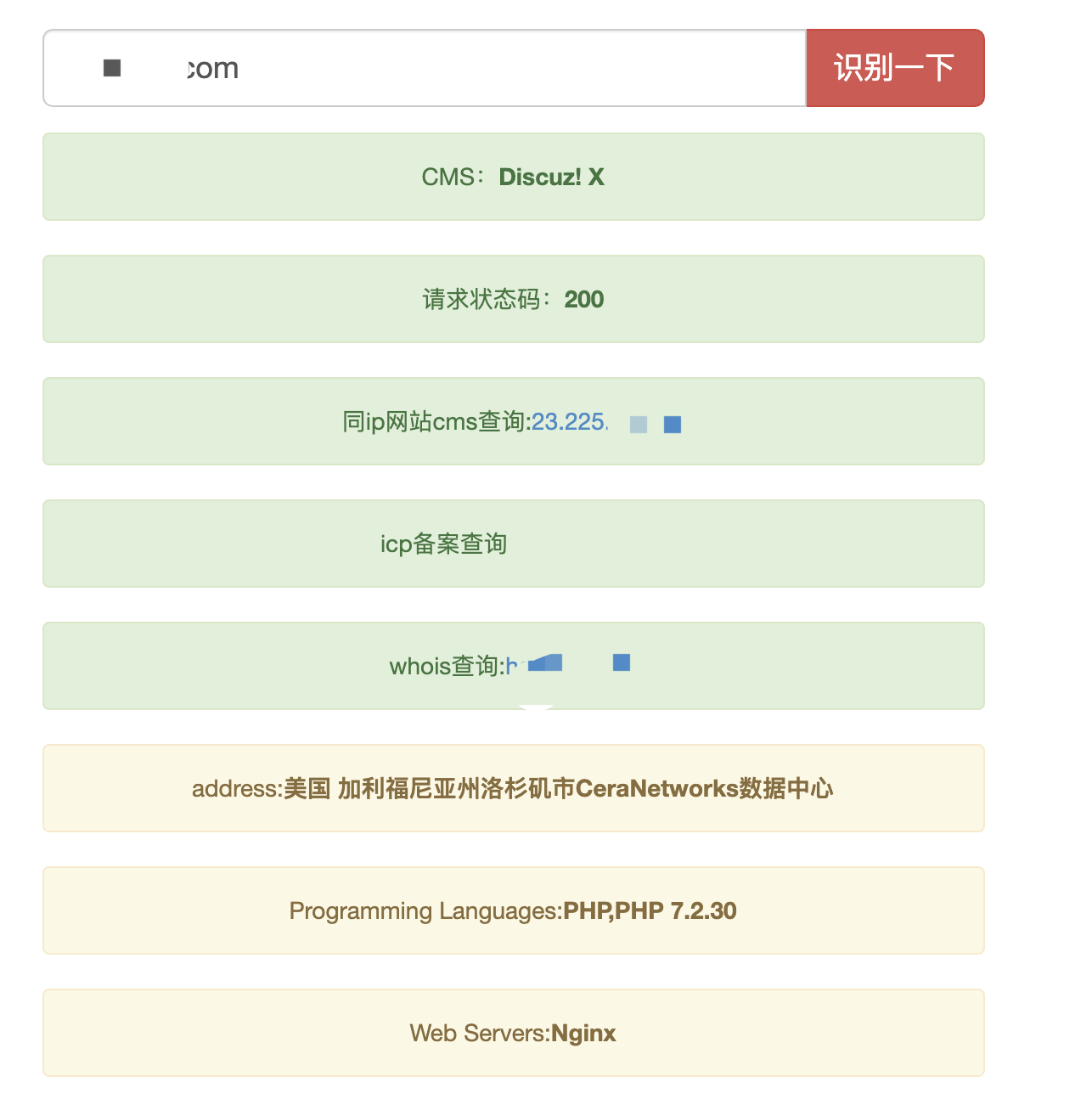
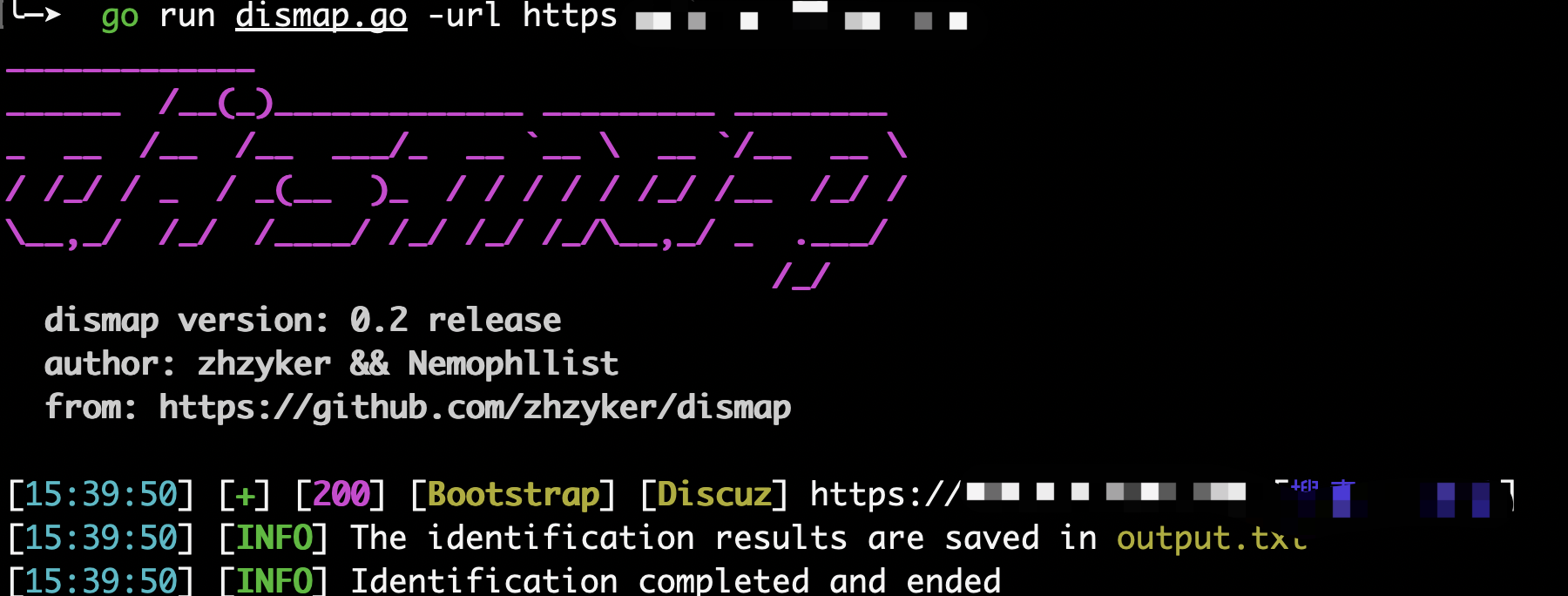
2.3.2 本地工具识别
TideFinger:https://github.com/TideSec/TideFinger
剑客:https://github.com/s7ckTeam/Glass
dismap:https://github.com/zhzyker/dismap
Vxscan:https://github.com/al0ne/Vxscan
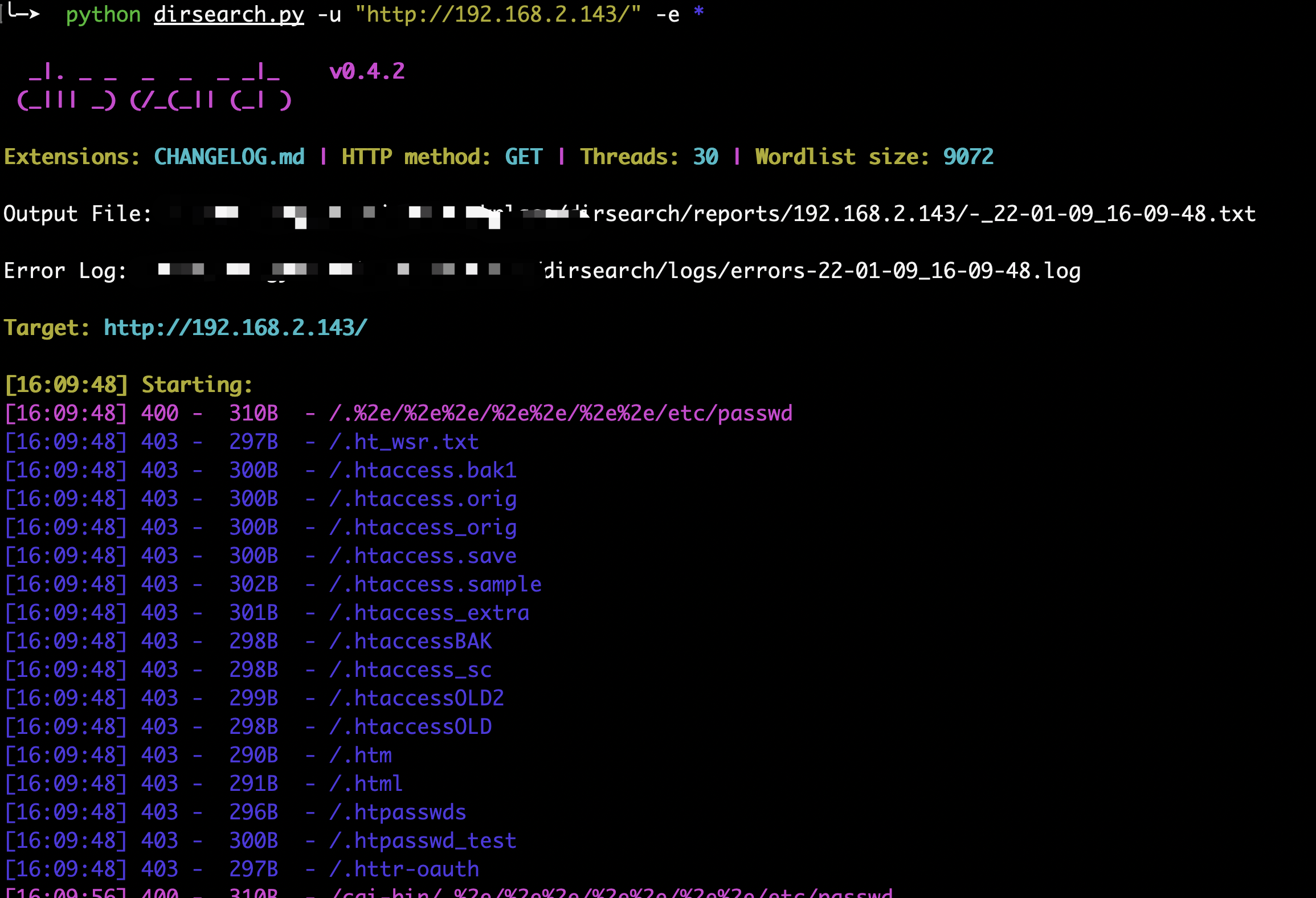
2.4 敏感目录扫描
通过穷举字典的方法对目标进行目录探测,比如可以扫描出管理员后台、备份文件、文件上传页面等
扫描工具:dirsearch
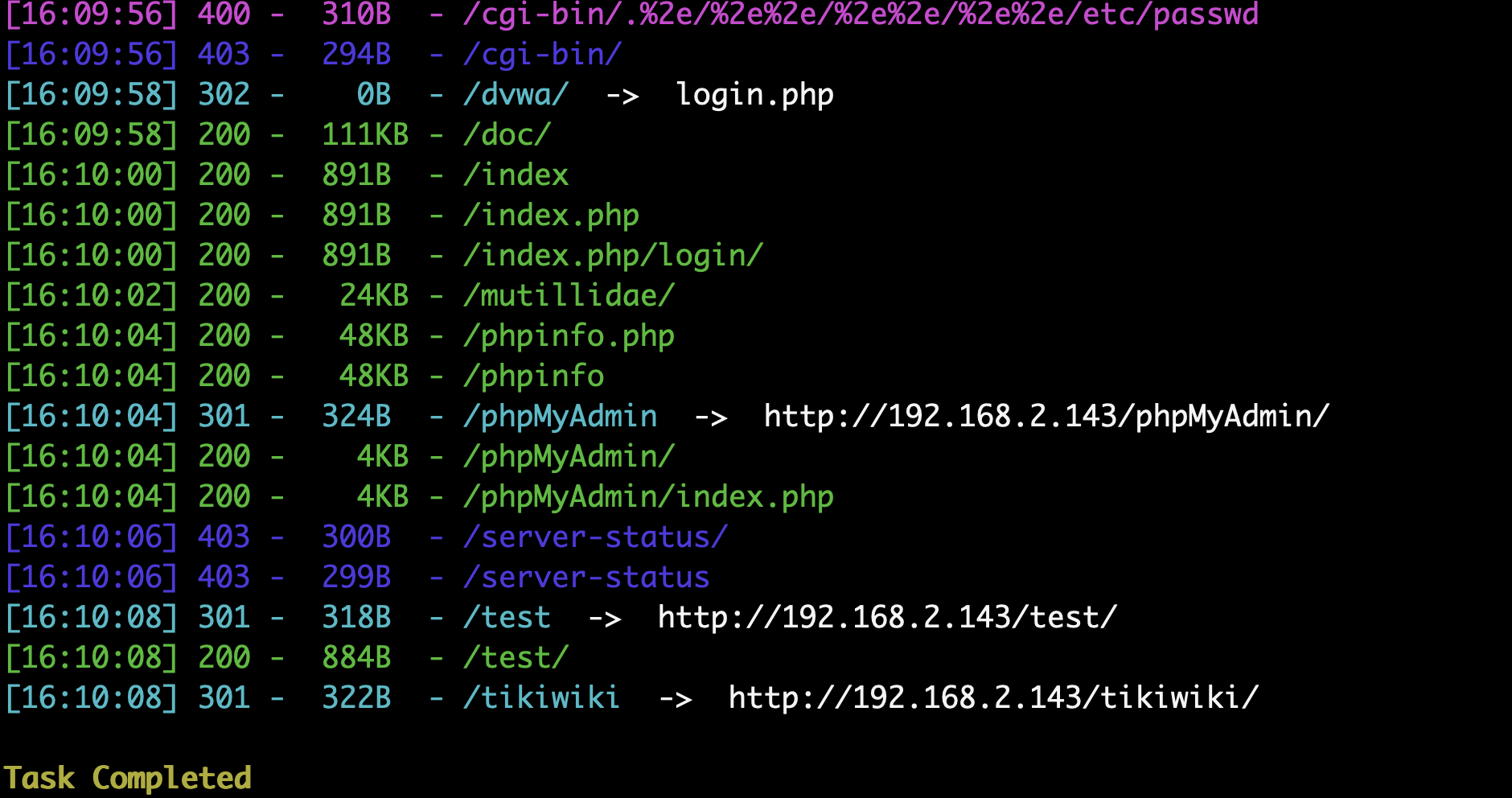
2.4 旁站和C段信息收集
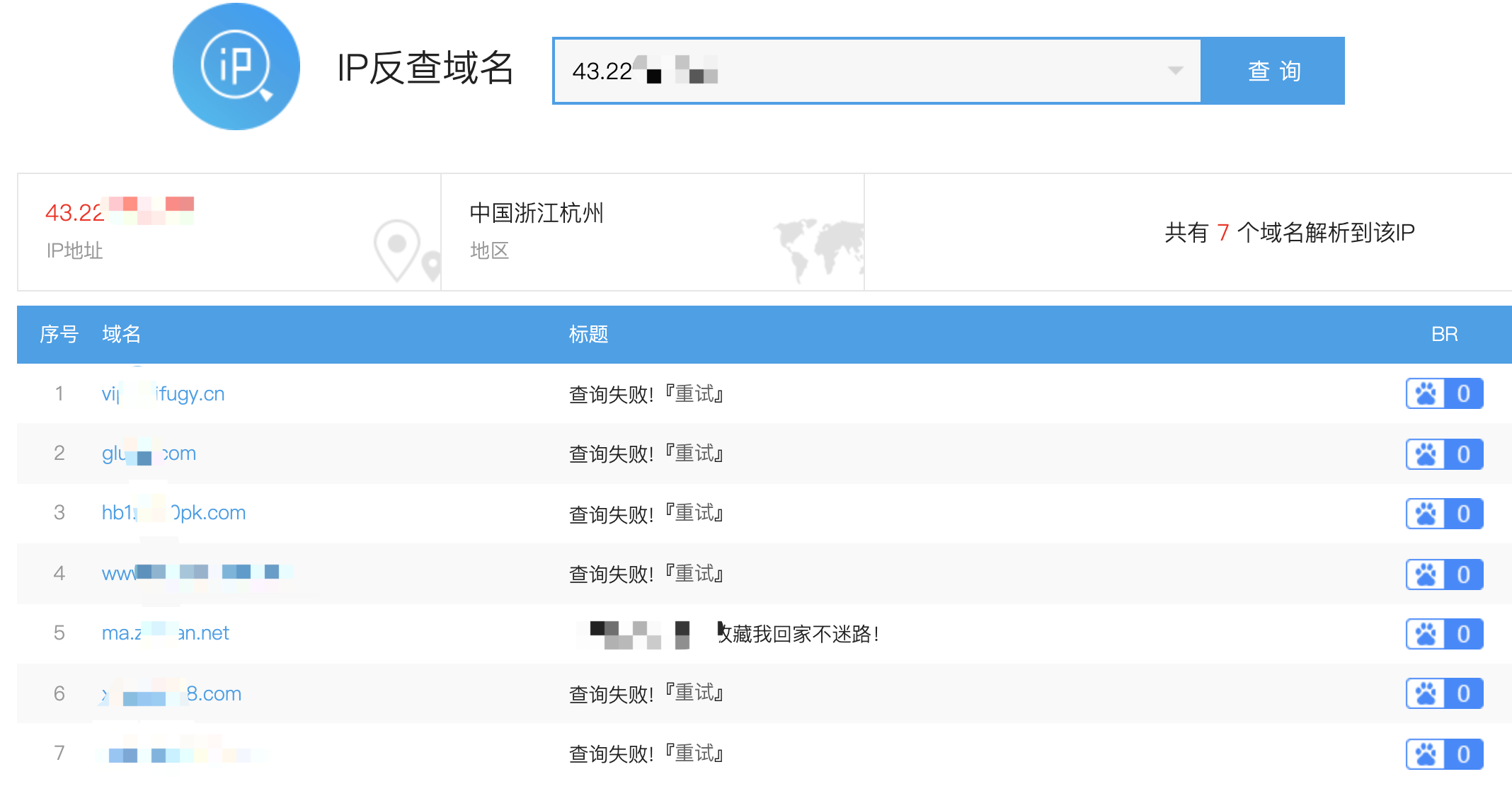
旁站指的是目标域名IP下的其他网站,可以通过IP反查域名
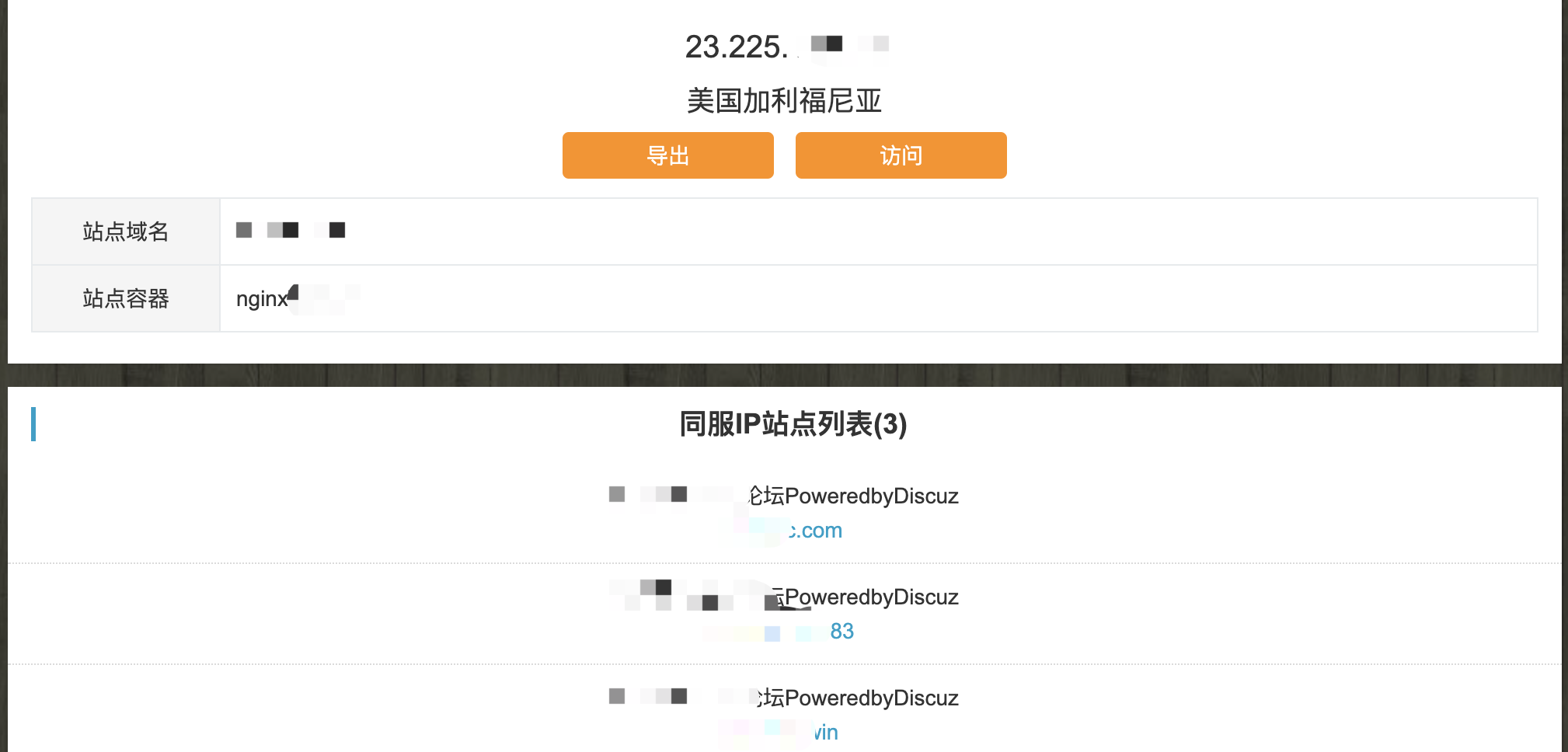
C段信息收集指的是探测目标服务器局域网段下的其他资产信息



 浙公网安备 33010602011771号
浙公网安备 33010602011771号