ingress-nginx 部署使用
输入下面网址:选择版本
https://github.com/kubernetes/ingress-nginx/blob/nginx-0.30.0/deploy/static/mandatory.yaml

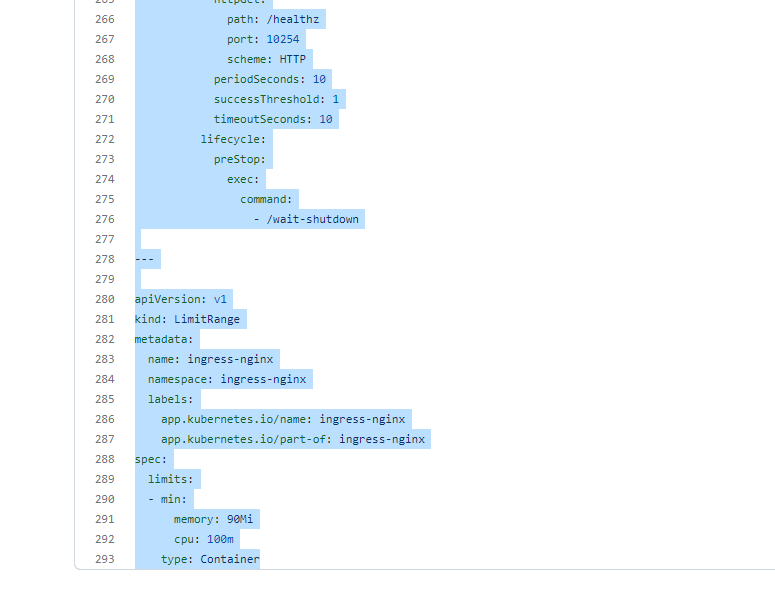
vim mandatory.yaml #新建一个yaml文件直接复制粘贴 ps: vim 编辑器 需要 set paste 防止格式错误

官网提示(0.30版本):!!! tip If you are using a Kubernetes version previous to 1.14, you need to change kubernetes.io/os to beta.kubernetes.io/os at line 217 of
把第217 行 的 kubernetes.io/os 替换成 beta.kubernetes.io/os
kubectl version 查看集群版本
Client Version: version.Info{Major:"1", Minor:"13", GitVersion:"v1.13.3", GitCommit:"721bfa751924da8d1680787490c54b9179b1fed0", GitTreeState:"clean", BuildDate:"2019-02-01T20:08:12Z", GoVersion:"go1.11.5", Compiler:"gc", Platform:"linux/amd64"}
Server Version: version.Info{Major:"1", Minor:"13", GitVersion:"v1.13.3", GitCommit:"721bfa751924da8d1680787490c54b9179b1fed0", GitTreeState:"clean", BuildDate:"2019-02-01T20:00:57Z", GoVersion:"go1.11.5", Compiler:"gc", Platform:"linux/amd64"}
214 terminationGracePeriodSeconds: 300
215 serviceAccountName: nginx-ingress-serviceaccount
216 nodeSelector:
217 beta.kubernetes.io/os: linux
218 containers:
219 - name: nginx-ingress-controller
:set nu
修改完创建资源
[root@localhost ~/test/ingress]# kubectl apply -f mandatory.yaml
namespace/ingress-nginx created
configmap/nginx-configuration created
configmap/tcp-services created
configmap/udp-services created
serviceaccount/nginx-ingress-serviceaccount created
clusterrole.rbac.authorization.k8s.io/nginx-ingress-clusterrole created
role.rbac.authorization.k8s.io/nginx-ingress-role created
rolebinding.rbac.authorization.k8s.io/nginx-ingress-role-nisa-binding created
clusterrolebinding.rbac.authorization.k8s.io/nginx-ingress-clusterrole-nisa-binding created
deployment.apps/nginx-ingress-controller created
limitrange/ingress-nginx created
查看控制器Pod 已经正常运行
[root@localhost ~/test/ingress]# kubectl get pods -n ingress-nginx
NAME READY STATUS RESTARTS AGE
nginx-ingress-controller-97547988b-jh9q4 1/1 Running 0 3m32s
创建个service 集群外访问
[root@localhost ~/test/ingress]# vim service-nodeport.yaml
apiVersion: v1
kind: Service
metadata:
name: ingress-nginx
namespace: ingress-nginx
spec:
type: NodePort
ports:
- name: http
port: 80
targetPort: 80
protocol: TCP
nodePort: 30080
- name: https
port: 443
targetPort: 443
protocol: TCP
nodePort: 30443
selector:
app.kubernetes.io/name: ingress-nginx
app.kubernetes.io/part-of: ingress-nginx
kubectl apply -f service-nodeport.yaml
创建一组应用pod和对应的service
[root@localhost ~/test/ingress/tomcat]# vim deploy-tomcat.yaml
apiVersion: v1
kind: Service
metadata:
name: tomcat
namespace: default
spec:
selector:
app: tomcat
release: canary
ports:
- name: http
port: 80
targetPort: 8080
# - name: ajp
# port: 8009
# targetPort: 8009
---
apiVersion: apps/v1
kind: Deployment
metadata:
name: tomcat-deploy
spec:
replicas: 3
selector:
matchLabels:
app: tomcat
release: canary
template:
metadata:
labels:
app: tomcat
release: canary
spec:
containers:
- name: tomcat
image: tomcat:7-alpine
ports:
- name: httpd
containerPort: 8080
# - name: ajp
# containerPort: 8009
kubectl apply -f deploy-tomcat.yaml
配置 ingress 规则
[root@localhost ~/test/ingress/tomcat]# vim tomcat.yaml
apiVersion: extensions/v1beta1
kind: Ingress
metadata:
name: ingress-tomcat
namespace: default
annotations:
kubernets.io/ingress.class: "nginx"
spec:
rules:
- host: tomcat.luoluo.com
http:
paths:
- path:
backend:
serviceName: tomcat
servicePort: 8080
kubectl apply -f tomcat.yaml
浏览器输入 tomcat.luoluo.com:30080 验证 #测试需要修改宿主机 C:\Windows\System32\drivers\etc 下 HOSTS文件 映射
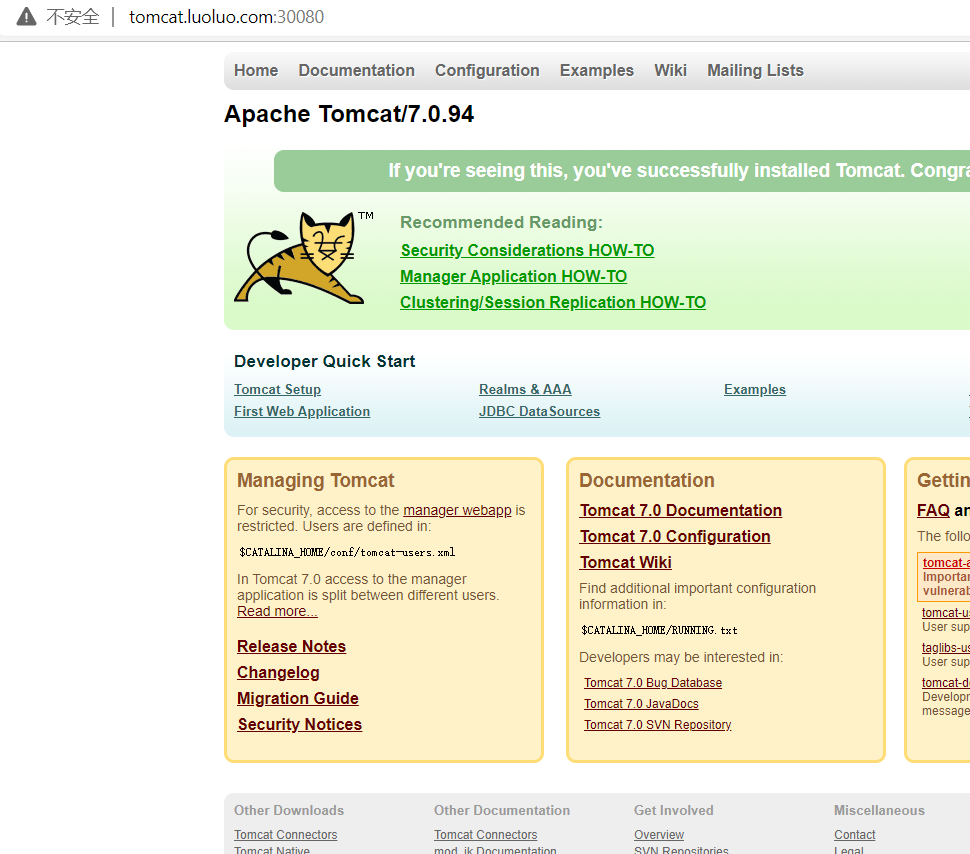
对tomcat服务添加httpds服务
创建私有证书及secret
openssl genrsa -out tls.key 2048
[root@localhost ~/test/ingress/tomcat]# openssl req -new -x509 -key tls.key -out tls.crt -subj /C=CN/ST=Beijing/L=Beijing/O=DevOps/CN=tomcat.luoluo.com #注意域名要和服务的域名一致
kubectl create secret tls tomcat-ingress-secret --cert=tls.crt --key=tls.key #创建secret
将证书应用至tomcat服务中
[root@localhost ~/test/ingress/tomcat]# vim ingress-tomcat-tls.yaml
apiVersion: extensions/v1beta1
kind: Ingress
metadata:
name: ingress-tomcat-tls
namespace: default
annotations:
kubernets.io/ingress.class: "nginx"
spec:
tls:
- hosts:
- tomcat.luoluo.com #与secret证书的域名需要保持一致
secretName: tomcat-ingress-secret #secret证书的名称
rules:
- host: tomcat.luoluo.com
https:
paths:
- path:
backend:
serviceName: tomcat
servicePort: 8080
~
~
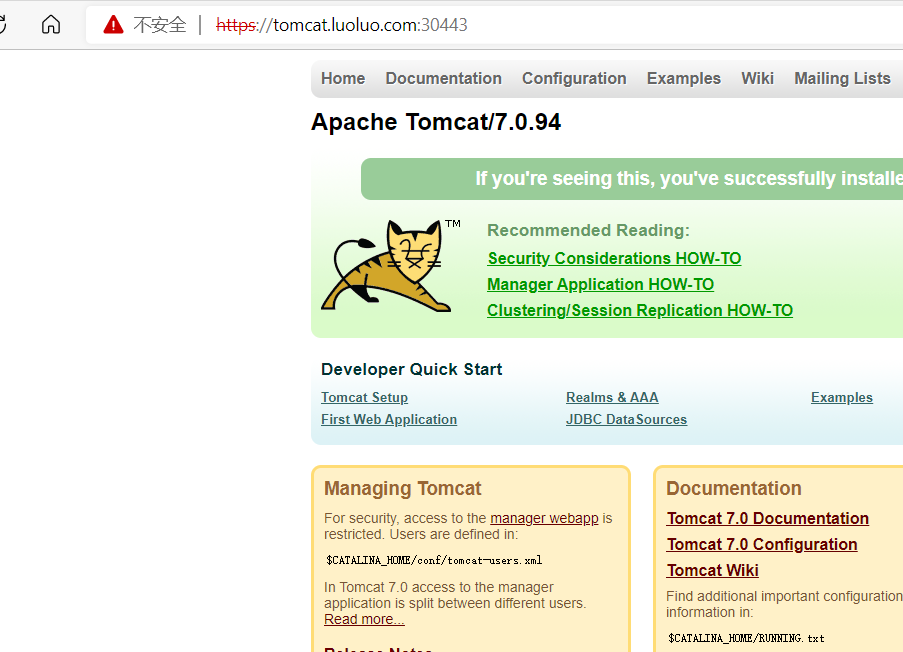
kubectl apply -f ingress-tomcat-tls.yaml
~





【推荐】国内首个AI IDE,深度理解中文开发场景,立即下载体验Trae
【推荐】编程新体验,更懂你的AI,立即体验豆包MarsCode编程助手
【推荐】抖音旗下AI助手豆包,你的智能百科全书,全免费不限次数
【推荐】轻量又高性能的 SSH 工具 IShell:AI 加持,快人一步
· winform 绘制太阳,地球,月球 运作规律
· AI与.NET技术实操系列(五):向量存储与相似性搜索在 .NET 中的实现
· 超详细:普通电脑也行Windows部署deepseek R1训练数据并当服务器共享给他人
· 【硬核科普】Trae如何「偷看」你的代码?零基础破解AI编程运行原理
· 上周热点回顾(3.3-3.9)