XCTF-NaNNaNNaNNaN-Batman
下载附件,打开后发现有乱码
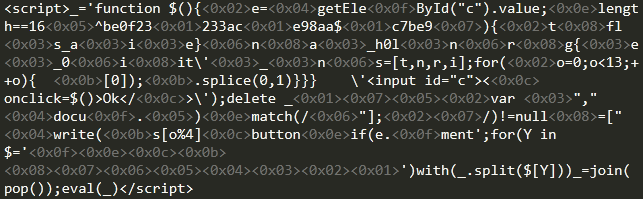
使用网页打开后发现是一个输入框
我们把最后的eval()函数换成console.log()过滤一下乱码
再重新排版一下得到:
function $(){ var e=document.getElementById("c").value; if(e.length==16)//输入参数要为16位 if(e.match(/^be0f23/)!=null) // if(e.match(/233ac/)!=null) if(e.match(/e98aa$/)!=null) if(e.match(/c7be9/)!=null){ var t=["fl","s_a","i","e}"]; var n=["a","_h0l","n"]; var r=["g{","e","_0"]; var i=["it'","_","n"]; var s=[t,n,r,i]; for(var o=0;o<13;++o){ document.write(s[o%4][0]);s[o%4].splice(0,1)} } } document.write('<input id="c"><button onclick=$()>Ok</button>'); delete _
审计代码后发现flag没有我们输入的参数,直接控制台运行:
var t=["fl","s_a","i","e}"]; var n=["a","_h0l","n"]; var r=["g{","e","_0"]; var i=["it'","_","n"]; var s=[t,n,r,i]; var r=""; for(var o=0;o<13;++o){ r+=s[o%4][0]; s[o%4].splice(0,1); } r
得到flag



 浙公网安备 33010602011771号
浙公网安备 33010602011771号