【Azure API 管理】在APIM中使用客户端证书验证API的请求,但是一直提示错误"No client certificate received."
API 管理 (APIM) 是一种为现有后端服务创建一致且现代化的 API 网关的方法。
问题描述
在设置了APIM客户端证书,用户保护后端API,让请求更安全。 但是,最近发现使用客户端证书的API全部出现错误,无法收到客户端证书,通过浏览器中查看,发现证书也是无效的。
在API请求的Trace中,错误消息为:
{ "source": "client-certificate-handler", "timestamp": "2021-07-13T12:23:51.8172847Z", "elapsed": "00:00:00.00053", "data": "Requesting client certificate because next handler requires access to it." }, { "source": "client-certificate-handler", "timestamp": "2021-07-13T12:23:51.8172847Z", "elapsed": "00:00:00.00048", "data": "No client certificate received." }
在浏览器中查看证书发现无效:
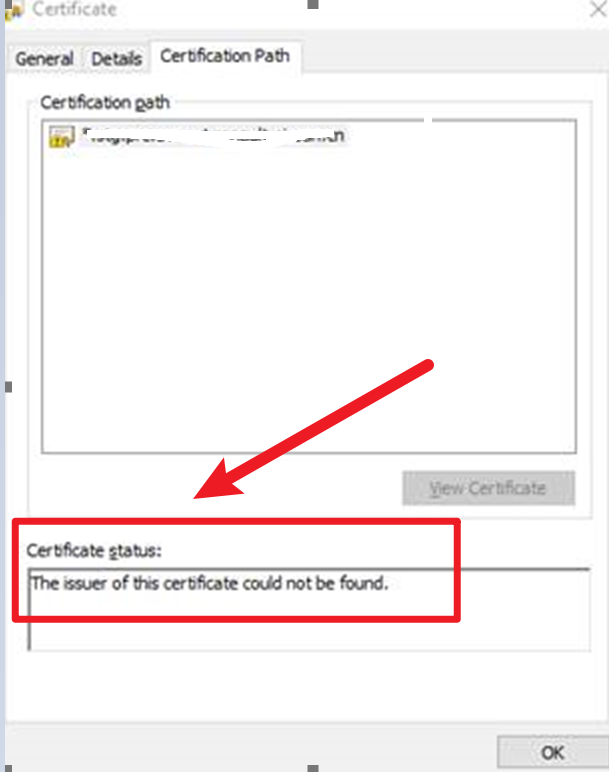
问题验证
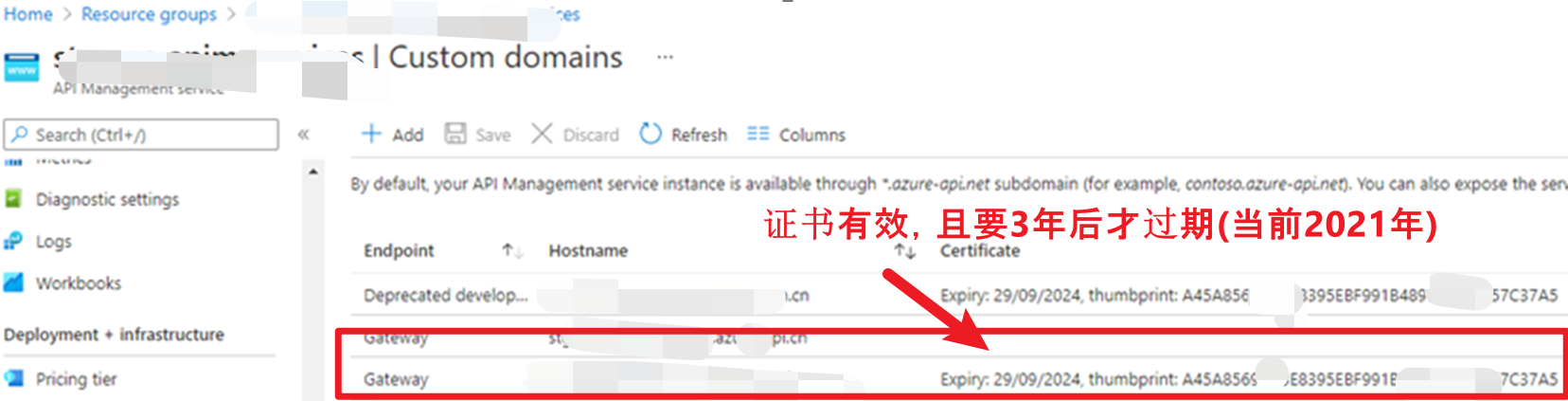
根据消息提示,第一反应检查APIM的客户端证书是否有效,是否过期
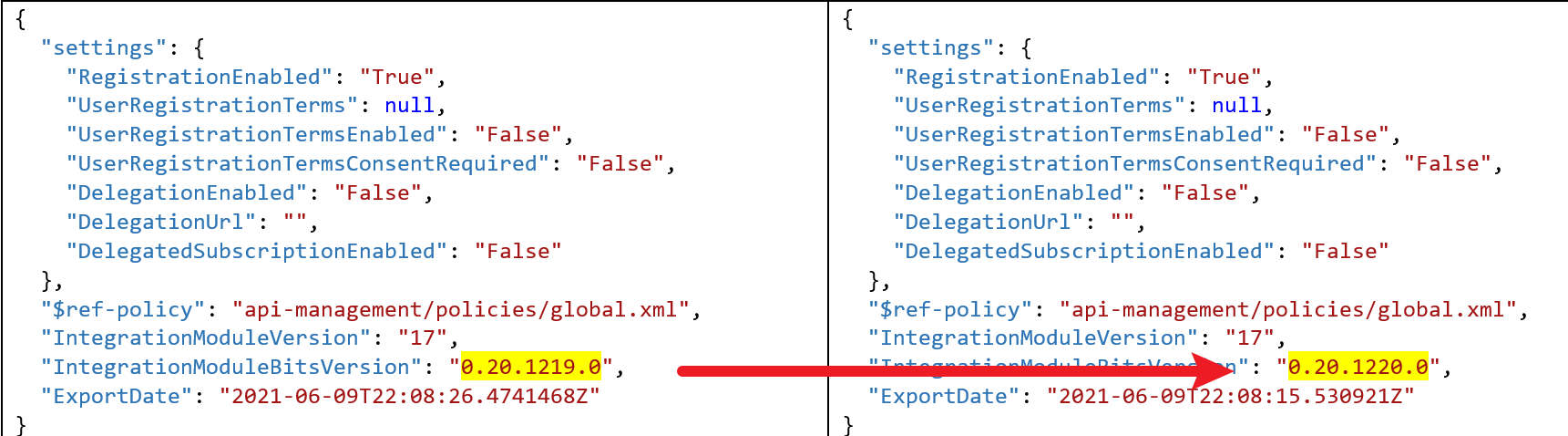
第二步当证书并无异常(没有过期)时,则调查APIM是否有变动,通过配置的Git存储库(APIM Repository), Clone最新的文件后发现版本有变动。发现前后有版本变动 ( IntegrationModuleBitsVersion )
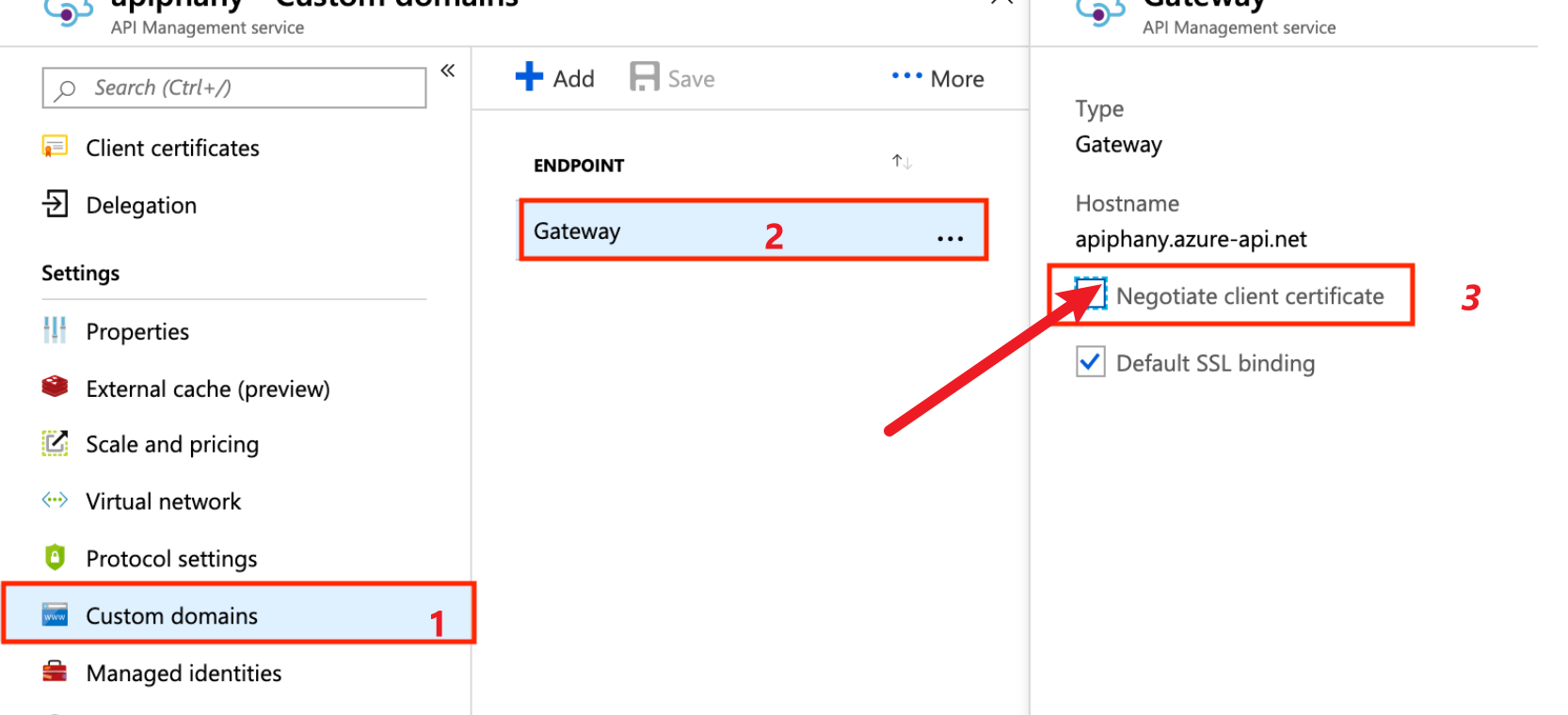
第三步:从APIM的证书设置入手,发现有新功能 ”协商客户端证书(Negotiate client certificate)“ 功能,在通过启用它之后,APIM的"No client certificate received" 问题消失
问题原因
因为在设置APIM时候,有一句提示消息为:”若要在开发人员层、基本层、标准层或高级层中通过 HTTP/2 接收和验证客户端证书,必须在“自定义域”边栏选项卡上启用“协商客户端证书”设置“” 。也就是说:如果不使用HTTP/2则不用启用"协商客户端证书"设置。这也是为什么在最初设置时,没有启用该功能的原因。
但是现在验证了问题的关键就是APIM升级后,必须启用"协商客户端证书", 通过对APIM的版本改动所发布的Release Notification(新版通知)看,是因为:
附录一:使用APIM Repository获取当前APIM中的所有文件,包含根目录的configuration.json文件
第一步:在APIM中启用Repository
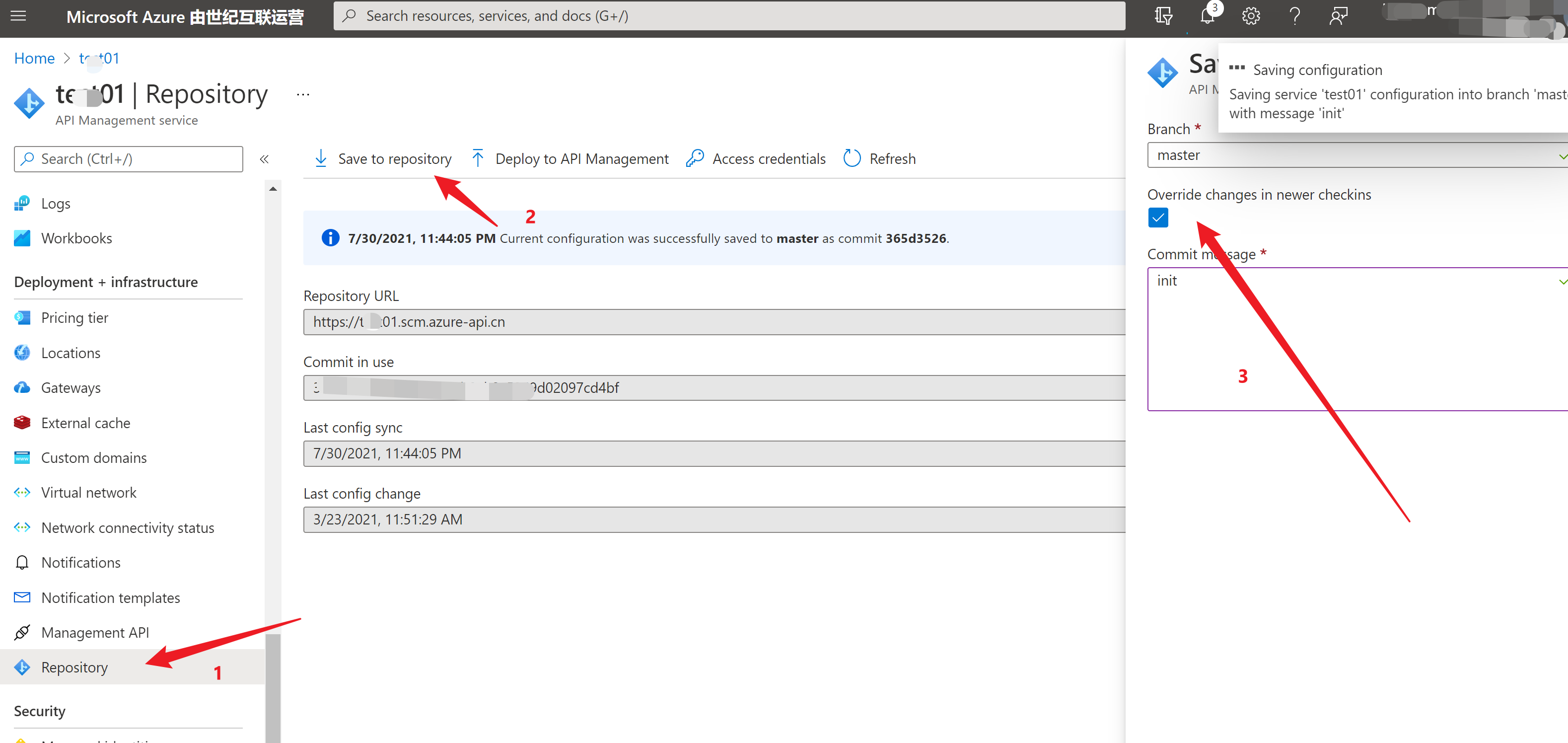
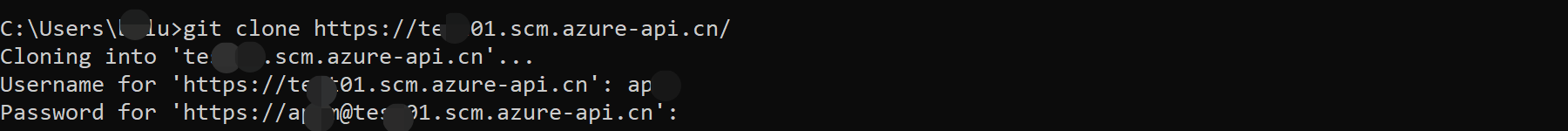
第二步:通过 git clone https://username:password@{name}.scm.azure-api.cn/ 下载APIM所有文件到本地
第三步:查看configuration.json文件 IntegrationModuleBitsVersion 信息
{ "settings": { "RegistrationEnabled": "True", "UserRegistrationTerms": null, "UserRegistrationTermsEnabled": "False", "UserRegistrationTermsConsentRequired": "False", "DelegationEnabled": "False", "DelegationUrl": "", "DelegatedSubscriptionEnabled": "False" }, "$ref-policy": "api-management/policies/global.xml", "IntegrationModuleVersion": "17", "IntegrationModuleBitsVersion": "0.20.1220.0", "ExportDate": "2021-06-09T22:08:15.530921Z" }
参考文档
如何使用 API 管理中的客户端证书身份验证确保 API 安全:https://docs.azure.cn/zh-cn/api-management/api-management-howto-mutual-certificates-for-clients
APIM Release: https://github.com/Azure/API-Management/releases/tag/release-service-2021-05
A regular Azure API Management service update was started on May 5, 2021, and included the following new features, bug fixes, and other improvements. It may take several weeks for your API Management service to receive the update.
Featured
- Open-source API Portal is now generally available.
- Azure API Management's support for Availability Zones is now generally available.
- Request and response validation policies are now generally available.
New
- You can now validate the client certificate with the new
<validate-client-certificate>policy. Documentation and support in the Azure portal are coming soon.- The Visual Studio Code extension now supports policy debugging for self-hosted gateways running locally.
- The Visual Studio Code extension now supports Dapr and validation policies.
- The developer portal now supports resource owner password grant flow.
- The new Ciphers + Protocols page in the Azure portal lets you manage API gateways' cipher and protocol configuration and displays a warning if a weak cipher or protocol is enabled.
- The Locations page in the Azure portal lets you now configure Availability Zones.
- You can now apply validation policies with the visual policy editors in the Azure portal, without writing any policy code.
- The
timeoutattribute of thesend-requestpolicy now supports policy expressions.Fixed
- Caching issues, which might have resulted in a broken developer portal's administrative interface, are now resolved.
Changed
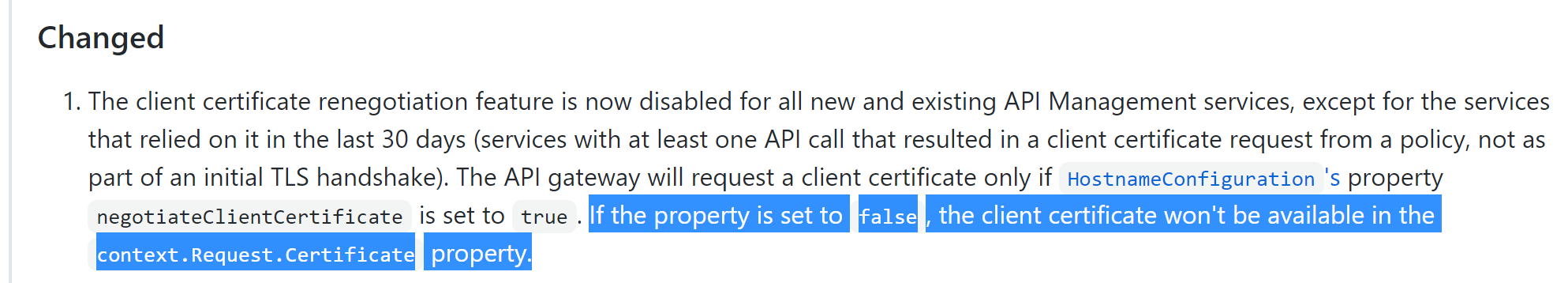
- The client certificate renegotiation feature is now disabled for all new and existing API Management services, except for the services that relied on it in the last 30 days (services with at least one API call that resulted in a client certificate request from a policy, not as part of an initial TLS handshake). The API gateway will request a client certificate only if
HostnameConfiguration's propertynegotiateClientCertificateis set totrue. If the property is set tofalse, the client certificate won't be available in thecontext.Request.Certificateproperty.
【END】
当在复杂的环境中面临问题,格物之道需:浊而静之徐清,安以动之徐生。 云中,恰是如此!


 浙公网安备 33010602011771号
浙公网安备 33010602011771号