【Azure 环境】如何解决Principal 2330xxxxxxxxxxxxxxxxxxxx31efc5 does not exist in the directory xxxxxxxx-xxxx-xxxx-xxxx-xxxxxxxxxxxx问题
问题描述
在使用 Key Vault 和 Azure CLI 管理存储帐户密钥的官方文档中,其中有一步是“向 Key Vault 授予对你的存储帐户的访问权限”, 其中CLI命令中使用的--assignee-object-id参数值为2330fcd0-aceb-49c4-a58f-27980b31efc5,根据说明其值为Azure 中国云中 Key Vault 的对象 ID,固定不变。但是在执行时,则出现如下错误:
| Principal 2330fcd0aceb49c4a58f27980b31efc5 does not exist in the directory xxxxxxxx-xxxx-xxxx-xxxx-xxxxxxxxxxxx. |
完整的错误消息体为:
### 1
az role assignment create --role "Storage Account Key Operator Service Role" --assignee-object-id "xxxxxxxx-xxxx-xxxx-xxxx-efe0ge7cxxxx" --scope "/subscriptions/xxxxxxxx-xxxx-xxxx-xxxx-xxxxxxxxxxxx/resourceGroups/testrg/providers/Microsoft.Storage/storageAccounts/testsa01" 报错: Failed to query --assignee-principal-type for xxxxxxxx-xxxx-xxxx-xxxx-efe0ge7cxxxx by invoking Graph API. RBAC server might reject creating role assignment without --assignee-principal-type in the future. Better to specify --assignee-principal-type manually. Principal xxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxx does not exist in the directory xxxxxxxx-xxxx-xxxx-xxxx-xxxxxxxxxxxx.
### 2
az role assignment create --role "Storage Account Key Operator Service Role" --assignee "https://vault.azure.cn" --scope "/subscriptions/xxxxxxxx-xxxx-xxxx-xxxx-xxxxxxxxxxxx/resourceGroups/testrg/providers/Microsoft.Storage/storageAccounts/testsa01" 报错: Cannot find user or service principal in graph database for 'https://vault.azure.cn'. If the assignee is an appId, make sure the corresponding service principal is created with 'az ad sp create --id https://vault.azure.cn'
问题原因
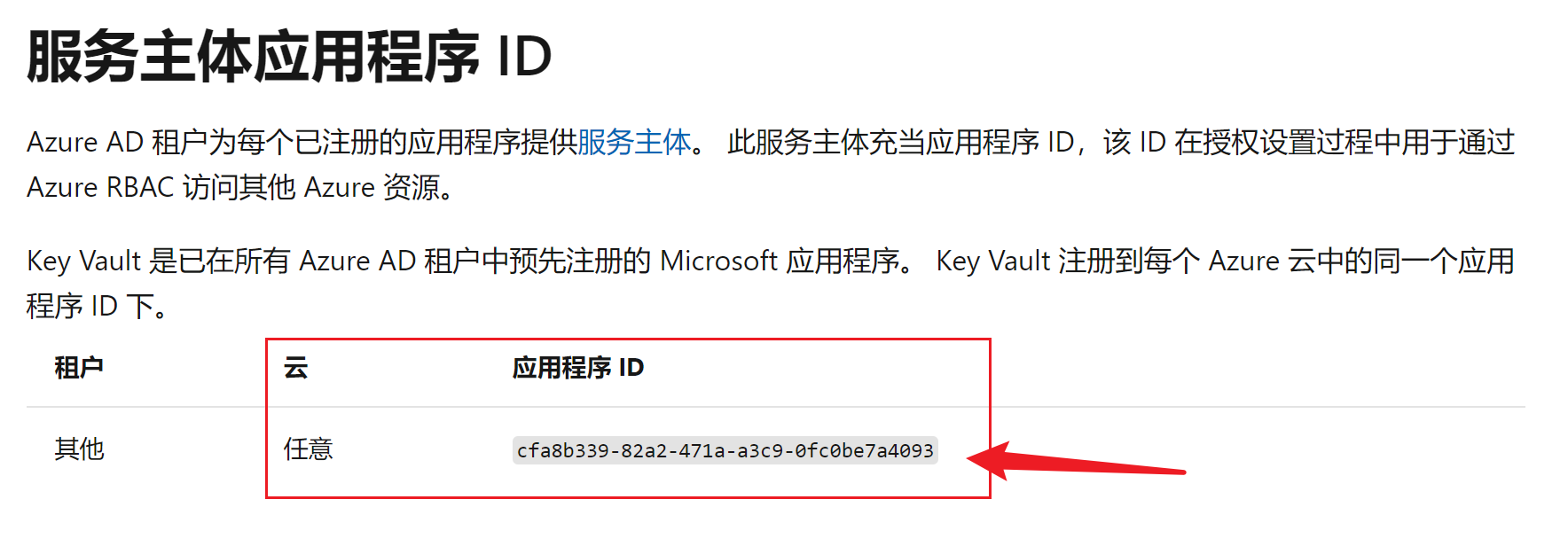
文档描述错误,Azure中国云为Key Vault注册的对象ID(Object)并不是固定不变,在每个不同的租户下,其值不同。只有Key Vault中Application ID保持不变。正如文档中描述的:
解决办法
根据Azure Key Vault的应用程序ID获取在Azure AAD中查找到正确的Object ID。然后执行az role assignment create命令
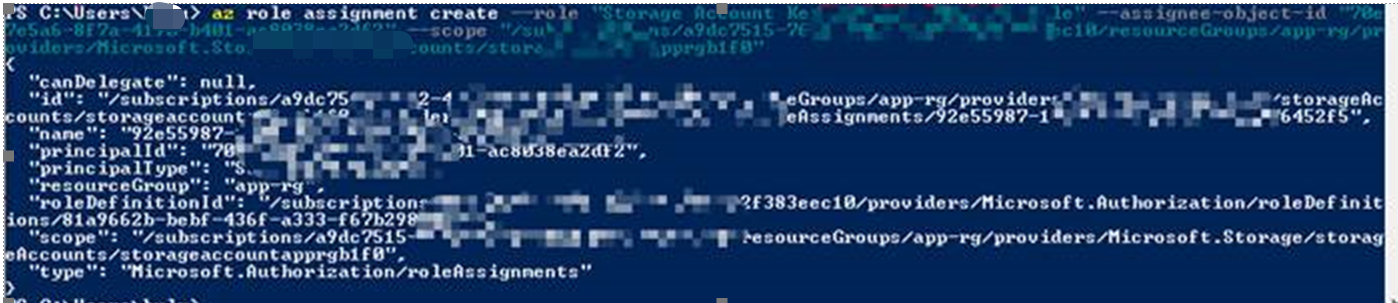
az role assignment create --role "Storage Account Key Operator Service Role" --assignee-object-id <right key vault object id in AAD> --scope "/subscriptions/<subscriptionID>/resourceGroups/<StorageAccountResourceGroupName>/providers/Microsoft.Storage/storageAccounts/<YourStorageAccountName>"
获取Key Vault的Object ID方式如下:
第一步:进入Azure AD, 在overview页面搜索key vault的application id(此ID为固定值 cfa8b339-82a2-471a-a3c9-0fc0be7a4093,见:https://docs.azure.cn/zh-cn/key-vault/secrets/overview-storage-keys#service-principal-application-id)
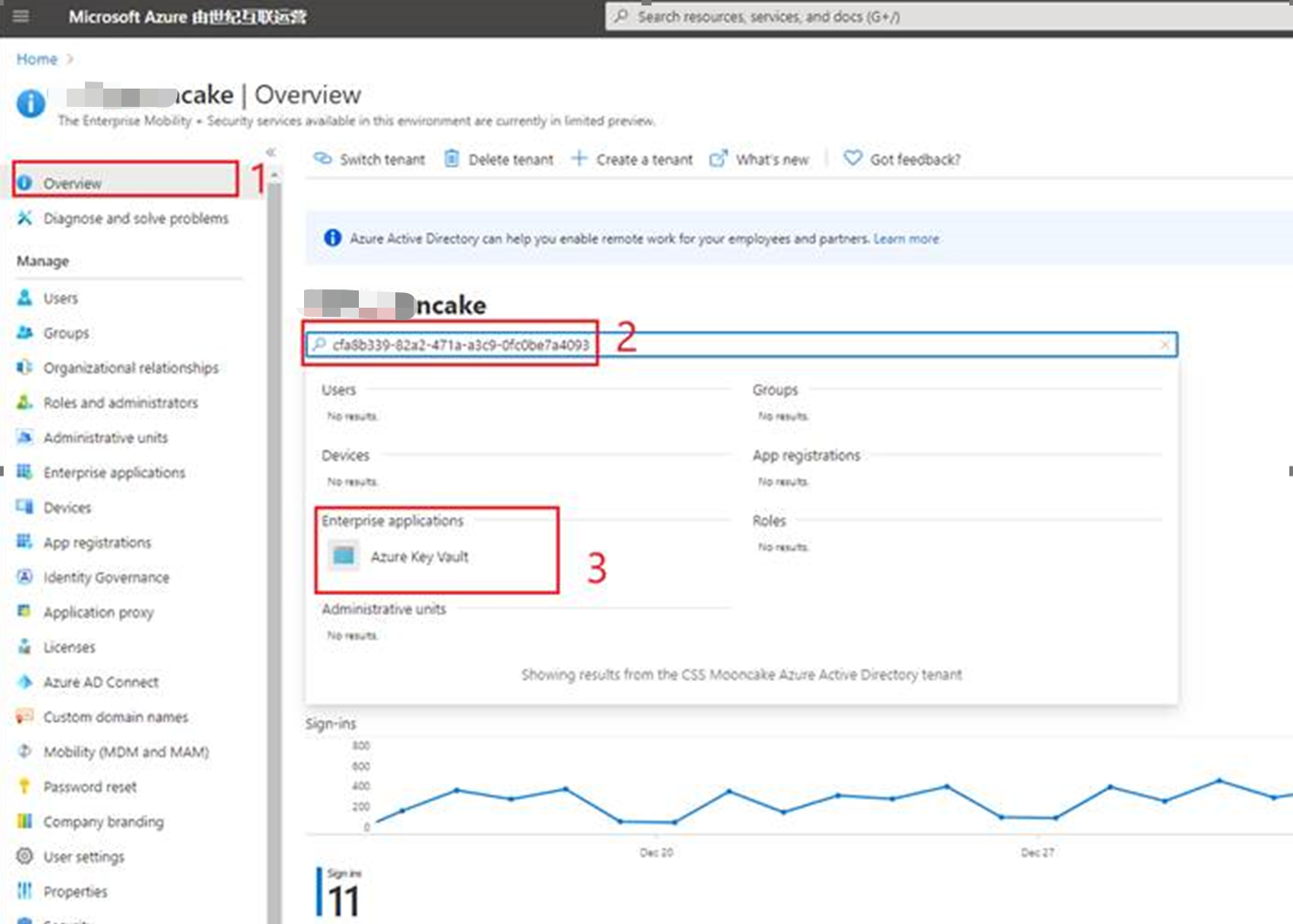
第二步:点击进入Key Vault页面查看Object ID
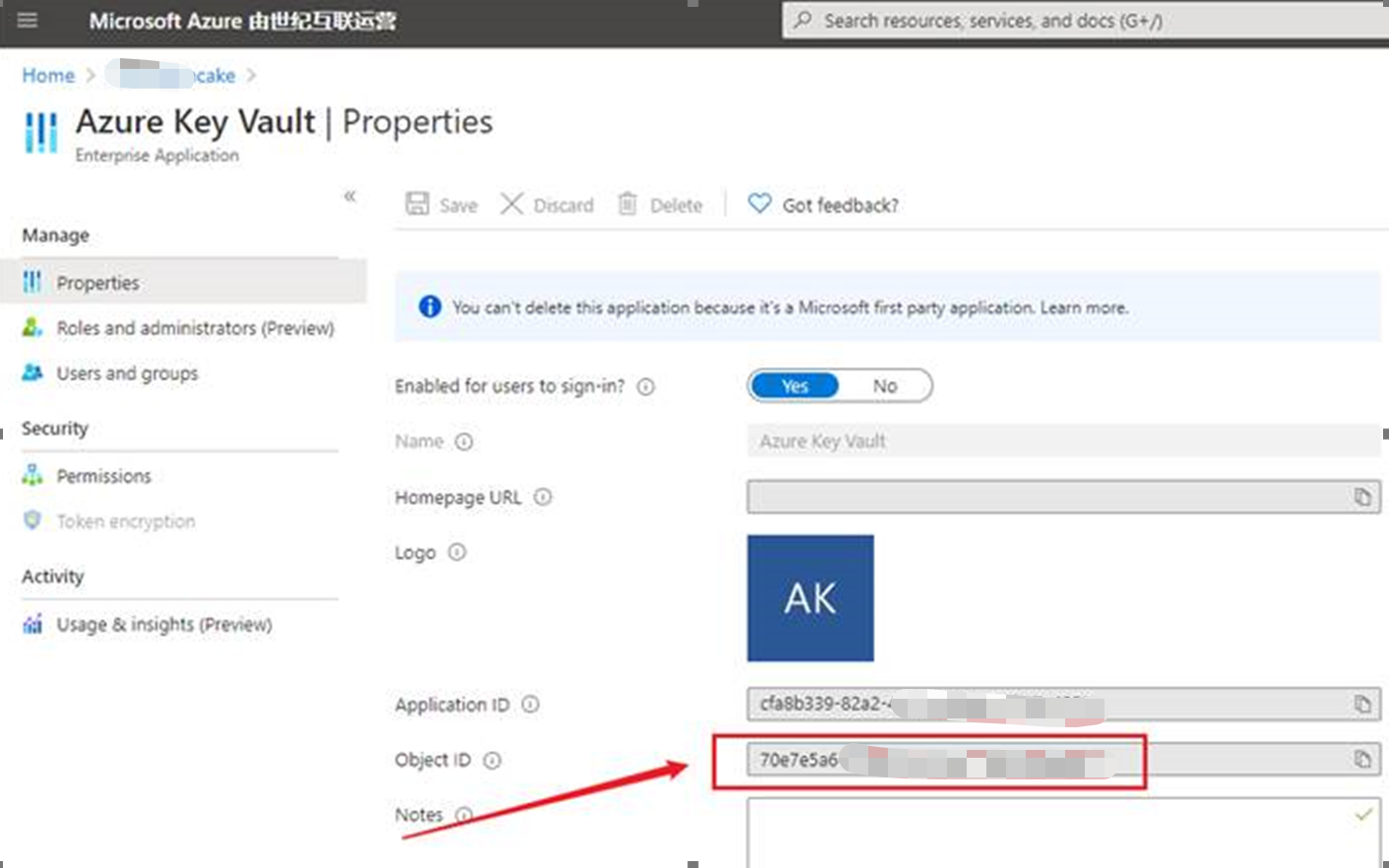
第三步:获取到Key Vault的Object ID后,执行CLI命令成功
参考文档
使用 Key Vault 和 Azure CLI 管理存储帐户密钥: https://docs.azure.cn/zh-cn/key-vault/secrets/overview-storage-keys#give-key-vault-access-to-your-storage-account
当在复杂的环境中面临问题,格物之道需:浊而静之徐清,安以动之徐生。 云中,恰是如此!




【推荐】国内首个AI IDE,深度理解中文开发场景,立即下载体验Trae
【推荐】编程新体验,更懂你的AI,立即体验豆包MarsCode编程助手
【推荐】抖音旗下AI助手豆包,你的智能百科全书,全免费不限次数
【推荐】轻量又高性能的 SSH 工具 IShell:AI 加持,快人一步
· Linux系列:如何用 C#调用 C方法造成内存泄露
· AI与.NET技术实操系列(二):开始使用ML.NET
· 记一次.NET内存居高不下排查解决与启示
· 探究高空视频全景AR技术的实现原理
· 理解Rust引用及其生命周期标识(上)
· DeepSeek 开源周回顾「GitHub 热点速览」
· 物流快递公司核心技术能力-地址解析分单基础技术分享
· .NET 10首个预览版发布:重大改进与新特性概览!
· AI与.NET技术实操系列(二):开始使用ML.NET
· 单线程的Redis速度为什么快?