ip route / ip rule /iptables 配置策略路由
ip route / ip rule /iptables 配置策略路由
来源 https://zhuanlan.zhihu.com/p/144585950
一,路由策略(使用ip rule命令操作路由策略数据库)
基于策略的路由比传统路由在功能上更强大,使用更灵活,它使网络管理员不仅能够根据目的地址而且能够根据报文大小,应用或IP源地址等属性来选择转发路径。
ip rule命令:
Usage: ip rule [ list | add | del ] SELECTOR ACTION (add 添加;del 删除; llist 列表)
SELECTOR := [ from PREFIX 数据包源地址] [ to PREFIX 数据包目的地址] [ tos TOS 服务类型]
[ dev STRING 物理接口] [ pref NUMBER ] [fwmark MARK iptables 标签]
ACTION := [ table TABLE_ID 指定所使用的路由表] [ nat ADDRESS 网络地址转换]
[ prohibit 丢弃该表| reject 拒绝该包| unreachable 丢弃该包]
[ flowid CLASSID ]
TABLE_ID := [ local | main | default | new | NUMBER ]
#例子1:通过路由表 inr.ruhep 路由来自源地址为192.203.80/24的数据包
ip rule add from 192.203.80/24 table inr.ruhep prio 220
#例子2:把源地址为193.233.7.83的数据报的源地址转换为192.203.80.144,并通过表1进行路由
ip rule add from 193.233.7.83 nat 192.203.80.144 table 1 prio 320在 Linux 系统启动时,内核会为路由策略数据库配置三条缺省的规则:
0:匹配任何条件,查询路由表local(ID 255),该表local是一个特殊的路由表,包含对于本地和广播地址的优先级控制路由。rule 0非常特殊,不能被删除或者覆盖。
32766:匹配任何条件,查询路由表main(ID 254),该表是一个通常的表,包含所有的无策略路由。系统管理员可以删除或者使用另外的规则覆盖这条规则。
32767:匹配任何条件,查询路由表default(ID 253),该表是一个空表,它是后续处理保留。对于前面的策略没有匹配到的数据包,系统使用这个策略进行处理,这个规则也可以删除。
注:不要混淆路由表和策略:规则指向路由表,多个规则可以引用一个路由表,而且某些路由表可以策略指向它。如果系统管理员删除了指向某个路由表的所有规则,这个表没有用了,但是仍然存在,直到里面的所有路由都被删除,它才会消失。
linux 系统中,可以自定义从 1-252个路由表,其中,linux系统维护了4个路由表:
0#表: 系统保留表
253#表: defulte table 没特别指定的默认路由都放在改表
254#表: main table 没指明路由表的所有路由放在该表
255#表: locale table 保存本地接口地址,广播地址、NAT地址 由系统维护,用户不得更改
路由表的查看可有以下二种方法:
ip route show table table_number
ip route show table table_name路由表序号和表名的对应关系在 /etc/iproute2/rt_tables文件中,可以手动编辑,路由表添加完毕及时生效,实例如下:
#实例1:在一号表中添加默认路由为192.168.1.1
ip route add default via 192.168.1.1 table 1
#实例2:在一号表中添加一条到192.168.0.0网段的路由为192.168.1.2
ip route add 192.168.0.0/24 via 192.168.1.2 table 1 二,路由表(使用ip route命令操作静态路由表)
所谓路由表,指的是路由器或者其他互联网网络设备上存储的表,该表中存有到达特定网络终端的路径,在某些情况下,还有一些与这些路径相关的度量。路由器的主要工作就是为经过路由器的每个数据包寻找一条最佳的传输路径,并将该数据有效地传送到目的站点。由此可见,选择最佳路径的策略即路由算法是路由器的关键所在。为了完成这项工作,在路由器中保存着各种传输路径的相关数据--路由表,供路由选择时使用,表中包含的信息决定了数据转发的策略。
三, ip rule,ip route,iptables 三者之间的关系
iptables:iptables其实不是真正的防火墙,我们可以把它理解成一个客户端代理,用户通过iptables这个代理,将用户的安全设定执行到对应的"安全框架"中,这个"安全框架"才是真正的防火墙,这个框架的名字叫netfilter。
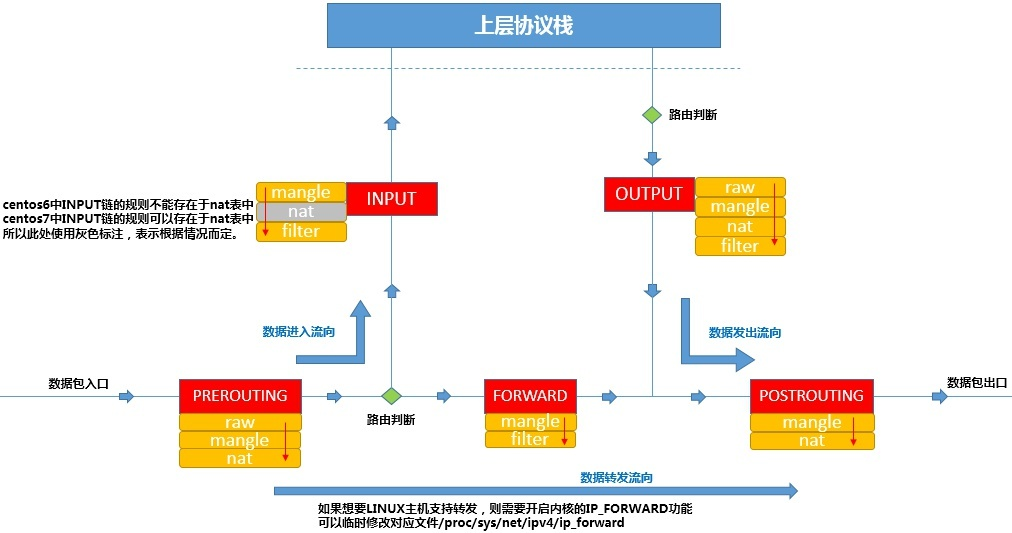
注:图中 “路由判断” 就是使用ip rule,ip route设置的规则,其中ip route配置的路由表服务于ip rule配置的规则。
以一例子来说明:公司内网要求192.168.0.100 以内的使用 10.0.0.1 网关上网 (电信),其他IP使用 20.0.0.1 (网通)上网。
1,首先要在网关服务器上添加一个默认路由,当然这个指向是绝大多数的IP的出口网关:ip route add default gw 20.0.0.1
2,之后通过 ip route 添加一个路由表:ip route add table 3 via 10.0.0.1 dev ethX (ethx 是 10.0.0.1 所在的网卡, 3 是路由表的编号)
3,之后添加 ip rule 规则:ip rule add fwmark 3 table 3 (fwmark 3 是标记,table 3 是路由表3 上边。 意思就是凡事标记了 3 的数据使用 table3 路由表)
4,之后使用 iptables 给相应的数据打上标记:iptables -A PREROUTING -t mangle -i eth0 -s 192.168.0.1 - 192.168.0.100 -j MARK --set-mark 3
================
ip route / ip rule /iptables 配置策略路由
来源 https://www.jianshu.com/p/5c70b536816b
ip rule:
进行路由时,根据路由规则来进行匹配,按优先级(pref)从低到高匹配,直到找到合适的规则.所以在应用中配置默认路由是必要的
路由规则的添加
ip rule add from 192.168.1.10/32 table 1 pref 100
如果pref值不指定,则将在已有规则最小序号前插入
PS: 创建完路由规则若需立即生效须执行
ip route flush cache
From -- 源地址
To -- 目的地址(这里是选择规则时使用,查找路由表时也使用)
Tos -- IP包头的TOS(type of sevice)域Linux高级路由-
Dev -- 物理接口
Fwmark -- iptables标签
采取的动作除了指定路由表外,还可以指定下面的动作:
Table 指明所使用的表
Nat 透明网关
Prohibit 丢弃该包,并发送 COMM.ADM.PROHIITED的ICMP信息
Reject 单纯丢弃该包
Unreachable丢弃该包, 并发送 NET UNREACHABLE的ICMP信息
Usage: ip rule [ list | add | del ]SELECTOR ACTION
SELECTOR := [ from PREFIX ] [ toPREFIX ] [ tos TOS ][ dev STRING ] [ pref NUMBER ]
ACTION := [ table TABLE_ID ] [ natADDRESS ][ prohibit | reject | unreachable ]
[ flowid CLASSID ]
TABLE_ID := [ local | main | default| new | NUMBER ]
详解看http://blog.csdn.net/scdxmoe/article/details/38661457
linux策略路由,路由策略(高级路由设置,多出口)
FROM http://rfyiamcool.blog.51cto.com/1030776/768562
功能说明:
由Linux实现流量分割,
1, 到202.96.209.133的数据从Linux路由器的eth2到路由器A,再到202.96.209.133。
2, 到Internet其他地方的数据从Linux路由器的eth1到路由器B,再到Internet。
实现方法:
打开Linux的路由功能:
echo 1 >/proc/sys/net/ipv4/ip_forward
首先添加一条规则,指定从172.16.16.2来的数据查找路由表5:
ip ru add from 172.16.16.2 lookup 5
1,实现第一个功能
(1),在路由表5中添加一条路由,到202.96.209.133的数据经过192.168.1.1:
# ip ro add 202.96.209.133 via 192.168.1.1 table 5
(2),这样就完成了路由的设置,因为172.16.16.2是私有地址,所以在Linux路由器的出口eth2处应该对其进行NAT的设置,如下:
# iptables -t nat -A POSTROUTING -s 172.16.16.2 -d 202.96.209.133 -j SNAT --to 192.168.1.3
(3),刷新路由缓存:
# ip ro flush cache
2, 实现第二个功能(在第一个的基础上)
(1),在路由表5中添加默认路由:
# ip ro add default via 10.10.10.2 table 5
(2),在Linux路由器的出口eth1处进行NAT设置:
# iptables -t nat -A POSTROUTING -s 172.16.16.2 -j SNAT --to 10.10.10.1
(3),刷新路由缓存:
# ip ro flush cache
注意:如果路由缓存不刷新的话,路由命令不能马上生效!
脚本如下:
#!/bin/sh
echo 1 >/proc/sys/net/ipv4/ip_forward
ip ru add from 172.16.16.2 lookup 5
ip ro add 202.96.209.133 via 192.168.1.1 table 5
iptables -t nat -A POSTROUTING -s 172.16.16.2 -d 202.96.209.133 -j SNAT --to 192.168.1.3
ip ro add default via 10.10.10.2 table 5
iptables -t nat -A POSTROUTING -s 172.16.16.2 -j SNAT --to 10.10.10.1
ip ro flush cache
你也可以将上面脚本中的几行iptables命令合为一行如下:
#iptables -t nat -A POSTROUTING -s 172.16.16.2 -j MASQUERADE
那么脚本如下:
#!/bin/sh
echo 1 >/proc/sys/net/ipv4/ip_forward
ip ru add from 172.16.16.2 lookup 5
ip ro add 202.96.209.133 via 192.168.1.1 table 5
ip ro add default via 10.10.10.2 table 5
iptables -t nat -A POSTROUTING -s 172.16.16.2 -j MASQUERADE
ip ro flush cache
可以使用tracert命令进行测试。不同点在于路由的第二跳,到202.96.209.133时,第二跳为:192.168.1.1,到其他地方时第二跳为:10.10.10.2。
注意:linux路由器是不能上网的,因为没有为他自己指定专门的路由或默认路由。为Linux路由器指定路由的命令如下:
ip ro add default via 192.168.1.1
ip ro flush cache
文章2:
实验名称:Linux下实现基于源地址的策略路由
操作系统:RedHat 7.2
所使用的内核:2.4.18
必须的模块: iproute2,iptables
功能描述:首先你必须明白策略路由和路由策略是两个不同的概念,策略路由是根据IP包中的源地址,端口号等来实现的;而路由策略可以理解为路由表中的一系列路由动作。
普通的路由是根据IP包中的目的地址来判断的,如:如果数据包是到http://linux.networksbase.com的,那么发送到网关192.168.1.1,如果到其他地方发送到192.168.2.1。
但很多时候我们需要对数据包的源地址也要作出判断,如:网络中有几条出口线路,那么优先权高的人走速率快的链路,其他人走速率慢的链路,这个时候就需要策略路由。
描述:实验中有两个局域网:LAN 1和LAN 2,我们要实现如下功能:
1,LAN 1中的192.168.2.25和192.168.2.128从路由器A上网;
2,LAN 1中的其他用户从路由器B上网;
3,LAN 2中的所有用户从路由器A上网
实现:
首先你要打开Linux服务器的路由功能,命令如下:
echo 1> /proc/sys/net/ipv4/ip_forward
然后设置LAN 1和LAN 2的IP伪装:
iptables -t nat -A POSTROUTING -s 192.168.2.0/24 -j MASQUERADE
iptables -t nat -A POSTROUTING -s 172.16.3.0/24 -j MASQUERADE
1,设置192.168.2.25和192.168.2.128的路由:
ip rule add from 192.168.2.25 lookup 5
ip rule add from 192.168.2.128 lookup 5
这两句话的意思是将来自192.168.2.25和192.168.2.128的数据查找路由表5
ip route add default via 192.168.0.1 table 5
定义路由表5的路由策略。
2,设置LAN 1中其他用户的路由:
ip rule add from 192.168.2.0/24 lookup 6
这句话的意思是让来自192.168.2.0的数据查找路由表6
ip route add default via 192.168.1.1 table 6
定义路由表6的路由策略。
3,设置LAN 2的路由:
ip rule add from 172.16.3.0/24 lookup 6
这句话的意思是让来自LAN 2的数据查找路由表6
ip route add default via 192.168.1.1 table 6(这条命令上面已经用过了!)
4,刷新路由:
ip route flush cache
5,脚本如下:
#!/bin/sh
echo 1> /proc/sys/net/ipv4/ip_forward
iptables -t nat -A POSTROUTING -s 192.168.2.0/24 -j MASQUERADE
iptables -t nat -A POSTROUTING -s 172.16.3.0/24 -j MASQUERADE
ip rule add from 192.168.2.25 lookup 5
ip rule add from 192.168.2.128 lookup 5
ip route add default via 192.168.0.1 table 5
ip rule add from 192.168.2.0/24 lookup 6
ip rule add from 172.16.3.0/24 lookup 6
ip route add default via 192.168.1.1 table 6
ip route flush cache
6,更明显一些,我们可以将上面脚本中的iptables命令行替换为下面的行
iptables -t nat -A POSTROUTING -s 192.168.2.25/24 -j SNAT --to 192.168.0.51
iptables -t nat -A POSTROUTING -s 192.168.2.128/24 -j SNAT --to 192.168.0.51
iptables -t nat -A POSTROUTING -s 192.168.2.0/24 -j SNAT --to 192.168.1.51
iptables -t nat -A POSTROUTING -s 172.16.3.0/24 -j SNAT --to 192.168.0.51
那么新脚本如下:
#!/bin/sh
echo 1> /proc/sys/net/ipv4/ip_forward
iptables -t nat -A POSTROUTING -s 192.168.2.25/24 -j SNAT --to 192.168.0.51
iptables -t nat -A POSTROUTING -s 192.168.2.128/24 -j SNAT --to 192.168.0.51
iptables -t nat -A POSTROUTING -s 192.168.2.0/24 -j SNAT --to 192.168.1.51
iptables -t nat -A POSTROUTING -s 172.16.3.0/24 -j SNAT --to 192.168.0.51
ip rule add from 192.168.2.25 lookup 5
ip rule add from 192.168.2.128 lookup 5
ip route add default via 192.168.0.1 table 5
ip rule add from 192.168.2.0/24 lookup 6
ip rule add from 172.16.3.0/24 lookup 6
ip route add default via 192.168.1.1 table 6
ip route flush cache 最后编辑于 :2017.12.07 07:04:37
================
root@gl-ar300m:~# root@gl-ar300m:~# ifconfig br-lan Link encap:Ethernet HWaddr 00:03:7F:11:23:C6 inet addr:192.168.11.1 Bcast:192.168.11.255 Mask:255.255.255.0 inet6 addr: fe80::203:7fff:fe11:23c6/64 Scope:Link UP BROADCAST RUNNING MULTICAST MTU:1500 Metric:1 RX packets:461 errors:0 dropped:0 overruns:0 frame:0 TX packets:282 errors:0 dropped:0 overruns:0 carrier:0 collisions:0 txqueuelen:1000 RX bytes:51234 (50.0 KiB) TX bytes:42087 (41.1 KiB) br-lan:0 Link encap:Ethernet HWaddr 00:03:7F:11:23:C6 inet addr:192.168.111.254 Bcast:0.0.0.0 Mask:255.255.255.0 UP BROADCAST RUNNING MULTICAST MTU:1500 Metric:1 eth0 Link encap:Ethernet HWaddr 94:83:C4:2B:31:28 inet addr:192.168.211.108 Bcast:192.168.211.255 Mask:255.255.255.0 inet6 addr: fe80::9683:c4ff:fe2b:3128/64 Scope:Link UP BROADCAST RUNNING MULTICAST MTU:1492 Metric:1 RX packets:47 errors:0 dropped:0 overruns:0 frame:0 TX packets:251 errors:0 dropped:0 overruns:0 carrier:0 collisions:0 txqueuelen:1000 RX bytes:6471 (6.3 KiB) TX bytes:22815 (22.2 KiB) Interrupt:4 eth1 Link encap:Ethernet HWaddr 00:03:7F:11:23:C6 UP BROADCAST RUNNING MULTICAST MTU:1500 Metric:1 RX packets:464 errors:0 dropped:3 overruns:0 frame:0 TX packets:277 errors:0 dropped:0 overruns:0 carrier:0 collisions:0 txqueuelen:1000 RX bytes:57868 (56.5 KiB) TX bytes:41529 (40.5 KiB) Interrupt:5 lo Link encap:Local Loopback inet addr:127.0.0.1 Mask:255.0.0.0 inet6 addr: ::1/128 Scope:Host UP LOOPBACK RUNNING MTU:65536 Metric:1 RX packets:82 errors:0 dropped:0 overruns:0 frame:0 TX packets:82 errors:0 dropped:0 overruns:0 carrier:0 collisions:0 txqueuelen:1 RX bytes:5282 (5.1 KiB) TX bytes:5282 (5.1 KiB) wlan0 Link encap:Ethernet HWaddr 94:83:C4:2B:31:28 inet6 addr: fe80::9683:c4ff:fe2b:3128/64 Scope:Link UP BROADCAST RUNNING MULTICAST MTU:1500 Metric:1 RX packets:0 errors:0 dropped:0 overruns:0 frame:0 TX packets:123 errors:0 dropped:0 overruns:0 carrier:0 collisions:0 txqueuelen:1000 RX bytes:0 (0.0 B) TX bytes:17266 (16.8 KiB) wwan0 Link encap:Ethernet HWaddr FA:52:E6:62:B9:B8 inet addr:100.64.32.73 Mask:255.255.255.252 inet6 addr: fe80::f852:e6ff:fe62:b9b8/64 Scope:Link UP RUNNING NOARP MTU:1500 Metric:1 RX packets:78 errors:0 dropped:0 overruns:0 frame:0 TX packets:97 errors:0 dropped:0 overruns:0 carrier:0 collisions:0 txqueuelen:1000 RX bytes:7836 (7.6 KiB) TX bytes:12815 (12.5 KiB) root@gl-ar300m:~#
root@gl-ar300m:~# ps | grep mwan
5778 root 1292 S /bin/sh /usr/sbin/mwan3track lte1 wwan0 2 1 2 5 3 3 100.64.0.1 10.0.0.1 4.2.2.1 114.114.114
23128 root 1292 S /bin/sh /usr/sbin/mwan3track wan eth0 2 1 2 5 3 3 100.64.0.1 10.0.0.1 4.2.2.1 114.114.114.1
23796 root 1284 S grep mwan
root@gl-ar300m:~# root@gl-ar300m:~# mwan3 status Interface status: interface wan is offline and tracking is active interface lte1 is online and tracking is active interface lte2 is unknown and tracking is down Current ipv4 policies: lte_p_wan_s: lte1 (100%) Current ipv6 policies: lte_p_wan_s: default Directly connected ipv4 networks: 127.0.0.0 192.168.11.0 192.168.211.0 100.64.32.72 192.168.211.0/24 192.168.111.0 192.168.11.0/24 192.168.11.1 100.64.32.72/30 192.168.111.254 192.168.111.255 127.0.0.1 192.168.11.255 192.168.211.255 192.168.211.108 100.64.32.75 192.168.111.0/24 224.0.0.0/3 127.255.255.255 100.64.32.73 127.0.0.0/8 Directly connected ipv6 networks: fe80::/64 Active ipv4 user rules: 12 936 - lte_p_wan_s all -- * * 0.0.0.0/0 0.0.0.0/0 Active ipv6 user rules: 0 0 - lte_p_wan_s all * * ::/0 ::/0 root@gl-ar300m:~# root@gl-ar300m:~# root@gl-ar300m:~# mwan3 interfaces Interface status: interface wan is offline and tracking is active interface lte1 is online and tracking is active interface lte2 is unknown and tracking is down root@gl-ar300m:~# root@gl-ar300m:~# route -n Kernel IP routing table Destination Gateway Genmask Flags Metric Ref Use Iface 0.0.0.0 100.64.32.74 0.0.0.0 UG 41 0 0 wwan0 0.0.0.0 192.168.211.1 0.0.0.0 UG 43 0 0 eth0 100.64.32.72 0.0.0.0 255.255.255.252 U 41 0 0 wwan0 192.168.11.0 0.0.0.0 255.255.255.0 U 0 0 0 br-lan 192.168.111.0 0.0.0.0 255.255.255.0 U 0 0 0 br-lan 192.168.211.0 0.0.0.0 255.255.255.0 U 43 0 0 eth0 root@gl-ar300m:~# root@gl-ar300m:~# ip rule show 0: from all lookup local 1001: from all iif eth0 lookup main 1002: from all iif wwan0 lookup main 2001: from all fwmark 0x100/0xff00 lookup 1 2002: from all fwmark 0x200/0xff00 lookup 2 2253: from all fwmark 0xfd00/0xff00 blackhole 2254: from all fwmark 0xfe00/0xff00 unreachable 32766: from all lookup main 32767: from all lookup default root@gl-ar300m:~# root@gl-ar300m:~# ip route show table 255 broadcast 100.64.32.72 dev wwan0 proto kernel scope link src 100.64.32.73 local 100.64.32.73 dev wwan0 proto kernel scope host src 100.64.32.73 broadcast 100.64.32.75 dev wwan0 proto kernel scope link src 100.64.32.73 broadcast 127.0.0.0 dev lo proto kernel scope link src 127.0.0.1 local 127.0.0.0/8 dev lo proto kernel scope host src 127.0.0.1 local 127.0.0.1 dev lo proto kernel scope host src 127.0.0.1 broadcast 127.255.255.255 dev lo proto kernel scope link src 127.0.0.1 broadcast 192.168.11.0 dev br-lan proto kernel scope link src 192.168.11.1 local 192.168.11.1 dev br-lan proto kernel scope host src 192.168.11.1 broadcast 192.168.11.255 dev br-lan proto kernel scope link src 192.168.11.1 broadcast 192.168.111.0 dev br-lan proto kernel scope link src 192.168.111.254 local 192.168.111.254 dev br-lan proto kernel scope host src 192.168.111.254 broadcast 192.168.111.255 dev br-lan proto kernel scope link src 192.168.111.254 broadcast 192.168.211.0 dev eth0 proto kernel scope link src 192.168.211.108 local 192.168.211.108 dev eth0 proto kernel scope host src 192.168.211.108 broadcast 192.168.211.255 dev eth0 proto kernel scope link src 192.168.211.108 root@gl-ar300m:~# root@gl-ar300m:~# ip route show table 254 default via 100.64.32.74 dev wwan0 proto static src 100.64.32.73 metric 41 default via 192.168.211.1 dev eth0 proto static src 192.168.211.108 metric 43 100.64.32.72/30 dev wwan0 proto static scope link metric 41 192.168.11.0/24 dev br-lan proto kernel scope link src 192.168.11.1 192.168.111.0/24 dev br-lan proto kernel scope link src 192.168.111.254 192.168.211.0/24 dev eth0 proto static scope link metric 43 root@gl-ar300m:~# root@gl-ar300m:~# ip route show table 253 root@gl-ar300m:~# root@gl-ar300m:~# ip route show table 3 root@gl-ar300m:~# root@gl-ar300m:~# ip route show table 2 default via 100.64.32.74 dev wwan0 root@gl-ar300m:~# root@gl-ar300m:~# ip route show table 1 default via 192.168.211.1 dev eth0 root@gl-ar300m:~# root@gl-ar300m:~# ip route show table 0 default via 192.168.211.1 dev eth0 table 1 default via 100.64.32.74 dev wwan0 table 2 default via 100.64.32.74 dev wwan0 proto static src 100.64.32.73 metric 41 default via 192.168.211.1 dev eth0 proto static src 192.168.211.108 metric 43 100.64.32.72/30 dev wwan0 proto static scope link metric 41 192.168.11.0/24 dev br-lan proto kernel scope link src 192.168.11.1 192.168.111.0/24 dev br-lan proto kernel scope link src 192.168.111.254 192.168.211.0/24 dev eth0 proto static scope link metric 43 broadcast 100.64.32.72 dev wwan0 table local proto kernel scope link src 100.64.32.73 local 100.64.32.73 dev wwan0 table local proto kernel scope host src 100.64.32.73 broadcast 100.64.32.75 dev wwan0 table local proto kernel scope link src 100.64.32.73 broadcast 127.0.0.0 dev lo table local proto kernel scope link src 127.0.0.1 local 127.0.0.0/8 dev lo table local proto kernel scope host src 127.0.0.1 local 127.0.0.1 dev lo table local proto kernel scope host src 127.0.0.1 broadcast 127.255.255.255 dev lo table local proto kernel scope link src 127.0.0.1 broadcast 192.168.11.0 dev br-lan table local proto kernel scope link src 192.168.11.1 local 192.168.11.1 dev br-lan table local proto kernel scope host src 192.168.11.1 broadcast 192.168.11.255 dev br-lan table local proto kernel scope link src 192.168.11.1 broadcast 192.168.111.0 dev br-lan table local proto kernel scope link src 192.168.111.254 local 192.168.111.254 dev br-lan table local proto kernel scope host src 192.168.111.254 broadcast 192.168.111.255 dev br-lan table local proto kernel scope link src 192.168.111.254 broadcast 192.168.211.0 dev eth0 table local proto kernel scope link src 192.168.211.108 local 192.168.211.108 dev eth0 table local proto kernel scope host src 192.168.211.108 broadcast 192.168.211.255 dev eth0 table local proto kernel scope link src 192.168.211.108 fe80::/64 dev br-lan proto kernel metric 256 pref medium fe80::/64 dev wlan0 proto kernel metric 256 pref medium fe80::/64 dev wwan0 proto kernel metric 256 pref medium fe80::/64 dev eth0 proto kernel metric 256 pref medium unreachable default dev lo proto kernel metric 4294967295 error -128 pref medium local ::1 dev lo table local proto none metric 0 pref medium local fe80:: dev lo table local proto none metric 0 pref medium local fe80:: dev lo table local proto none metric 0 pref medium local fe80:: dev lo table local proto none metric 0 pref medium local fe80:: dev lo table local proto none metric 0 pref medium local fe80::203:7fff:fe11:23c6 dev lo table local proto none metric 0 pref medium local fe80::9683:c4ff:fe2b:3128 dev lo table local proto none metric 0 pref medium local fe80::9683:c4ff:fe2b:3128 dev lo table local proto none metric 0 pref medium local fe80::f852:e6ff:fe62:b9b8 dev lo table local proto none metric 0 pref medium ff00::/8 dev br-lan table local metric 256 pref medium ff00::/8 dev wlan0 table local metric 256 pref medium ff00::/8 dev wwan0 table local metric 256 pref medium ff00::/8 dev eth0 table local metric 256 pref medium unreachable default dev lo proto kernel metric 4294967295 error -128 pref medium root@gl-ar300m:~# root@gl-ar300m:~# ipset --list Name: local Type: hash:net Revision: 6 Header: family inet hashsize 1024 maxelem 65536 Size in memory: 1048 References: 0 Members: 192.88.99.0/24 10.0.0.0/8 100.64.0.0/10 172.16.0.0/12 192.168.0.0/16 224.0.0.0/3 192.0.2.0/24 203.0.113.0/24 127.0.0.0/8 192.0.0.0/24 0.0.0.0/8 198.18.0.0/15 198.51.100.0/24 Name: mwan3_connected_v4 Type: hash:net Revision: 6 Header: family inet hashsize 1024 maxelem 65536 Size in memory: 1496 References: 1 Members: 192.168.211.0 100.64.32.72/30 100.64.32.75 192.168.11.255 192.168.11.1 127.0.0.0/8 192.168.111.0/24 127.255.255.255 192.168.11.0 192.168.211.0/24 192.168.111.254 100.64.32.73 192.168.211.108 192.168.111.0 192.168.111.255 192.168.211.255 100.64.32.72 224.0.0.0/3 127.0.0.0 192.168.11.0/24 127.0.0.1 Name: mwan3_connected_v6 Type: hash:net Revision: 6 Header: family inet6 hashsize 1024 maxelem 65536 Size in memory: 1192 References: 1 Members: fe80::/64 Name: mwan3_connected Type: list:set Revision: 3 Header: size 8 Size in memory: 92 References: 4 Members: mwan3_connected_v4 mwan3_connected_v6
root@gl-ar300m:~# root@gl-ar300m:~# iptables -S -t mangle -P PREROUTING ACCEPT -P INPUT ACCEPT -P FORWARD ACCEPT -P OUTPUT ACCEPT -P POSTROUTING ACCEPT -N mwan3_connected -N mwan3_hook -N mwan3_iface_in_lte1 -N mwan3_iface_in_wan -N mwan3_iface_out_lte1 -N mwan3_iface_out_wan -N mwan3_ifaces_in -N mwan3_ifaces_out -N mwan3_policy_lte_p_wan_s -N mwan3_rules -A PREROUTING -j mwan3_hook -A FORWARD -o eth0 -p tcp -m tcp --tcp-flags SYN,RST SYN -m comment --comment "!fw3: Zone wan MTU fixing" -j TCPMSS --clamp-mss-to-pmtu -A FORWARD -i eth0 -p tcp -m tcp --tcp-flags SYN,RST SYN -m comment --comment "!fw3: Zone wan MTU fixing" -j TCPMSS --clamp-mss-to-pmtu -A FORWARD -o wwan0 -p tcp -m tcp --tcp-flags SYN,RST SYN -m comment --comment "!fw3: Zone lte1 MTU fixing" -j TCPMSS --clamp-mss-to-pmtu -A FORWARD -i wwan0 -p tcp -m tcp --tcp-flags SYN,RST SYN -m comment --comment "!fw3: Zone lte1 MTU fixing" -j TCPMSS --clamp-mss-to-pmtu -A FORWARD -o wwan1 -p tcp -m tcp --tcp-flags SYN,RST SYN -m comment --comment "!fw3: Zone lte2 MTU fixing" -j TCPMSS --clamp-mss-to-pmtu -A FORWARD -i wwan1 -p tcp -m tcp --tcp-flags SYN,RST SYN -m comment --comment "!fw3: Zone lte2 MTU fixing" -j TCPMSS --clamp-mss-to-pmtu -A OUTPUT -j mwan3_hook -A mwan3_connected -m set --match-set mwan3_connected dst -j MARK --set-xmark 0xff00/0xff00 -A mwan3_hook -j CONNMARK --restore-mark --nfmask 0xff00 --ctmask 0xff00 -A mwan3_hook -m mark --mark 0x0/0xff00 -j mwan3_ifaces_in -A mwan3_hook -m mark --mark 0x0/0xff00 -j mwan3_connected -A mwan3_hook -m mark --mark 0x0/0xff00 -j mwan3_ifaces_out -A mwan3_hook -m mark --mark 0x0/0xff00 -j mwan3_rules -A mwan3_hook -j CONNMARK --save-mark --nfmask 0xff00 --ctmask 0xff00 -A mwan3_hook -m mark ! --mark 0xff00/0xff00 -j mwan3_connected -A mwan3_iface_in_lte1 -i wwan0 -m set --match-set mwan3_connected src -m mark --mark 0x0/0xff00 -m comment --comment default -j MARK --set-xmark 0xff00/0xff00 -A mwan3_iface_in_lte1 -i wwan0 -m mark --mark 0x0/0xff00 -m comment --comment lte1 -j MARK --set-xmark 0x200/0xff00 -A mwan3_iface_in_wan -i eth0 -m set --match-set mwan3_connected src -m mark --mark 0x0/0xff00 -m comment --comment default -j MARK --set-xmark 0xff00/0xff00 -A mwan3_iface_in_wan -i eth0 -m mark --mark 0x0/0xff00 -m comment --comment wan -j MARK --set-xmark 0x100/0xff00 -A mwan3_iface_out_lte1 -s 100.64.32.73/32 -m mark --mark 0x0/0xff00 -m comment --comment lte1 -j MARK --set-xmark 0x200/0xff00 -A mwan3_iface_out_wan -s 192.168.211.108/32 -m mark --mark 0x0/0xff00 -m comment --comment wan -j MARK --set-xmark 0x100/0xff00 -A mwan3_ifaces_in -m mark --mark 0x0/0xff00 -j mwan3_iface_in_lte1 -A mwan3_ifaces_in -m mark --mark 0x0/0xff00 -j mwan3_iface_in_wan -A mwan3_ifaces_out -m mark --mark 0x0/0xff00 -j mwan3_iface_out_lte1 -A mwan3_ifaces_out -m mark --mark 0x0/0xff00 -j mwan3_iface_out_wan -A mwan3_policy_lte_p_wan_s -m mark --mark 0x0/0xff00 -m comment --comment "lte1 5 5" -j MARK --set-xmark 0x200/0xff00 -A mwan3_rules -m mark --mark 0x0/0xff00 -m comment --comment lte_first -j mwan3_policy_lte_p_wan_s root@gl-ar300m:~#
Software versions : OpenWrt - LEDE AR300M v1.0.1 17.01-SNAPSHOT 202305050225 LuCI - git-23.146.22336-9c6cf7f mwan3 - 2.0.2-1 mwan3-luci - 1.4-6 Output of "cat /etc/config/mwan3" : config globals 'globals' option mmx_mask '0x3F00' option rtmon_interval '5' config interface 'wan' option enabled '1' option initial_state 'online' option family 'ipv4' list track_ip '114.114.114.114' list track_ip '4.2.2.1' list track_ip '10.0.0.1' list track_ip '100.64.0.1' option track_method 'ping' option reliability '2' option count '1' option size '56' option check_quality '0' option timeout '2' option interval '5' option failure_interval '5' option recovery_interval '5' option down '3' option up '3' option flush_conntrack 'never' config interface 'lte1' option enabled '1' option initial_state 'online' option family 'ipv4' list track_ip '114.114.114.114' list track_ip '4.2.2.1' list track_ip '10.0.0.1' list track_ip '100.64.0.1' option track_method 'ping' option reliability '2' option count '1' option size '56' option check_quality '0' option timeout '2' option interval '5' option failure_interval '5' option recovery_interval '5' option down '3' option up '3' option flush_conntrack 'never' config interface 'lte2' option enabled '1' option initial_state 'online' option family 'ipv4' list track_ip '114.114.114.114' list track_ip '4.2.2.1' list track_ip '10.0.0.1' list track_ip '100.64.0.1' option track_method 'ping' option reliability '2' option count '1' option size '56' option check_quality '0' option timeout '2' option interval '5' option failure_interval '5' option recovery_interval '5' option down '3' option up '3' option flush_conntrack 'never' config member 'lte1_m1_w5' option interface 'lte1' option metric '1' option weight '5' config member 'lte2_m1_w5' option interface 'lte2' option metric '1' option weight '5' config member 'wan_m2_w2' option interface 'wan' option metric '2' option weight '2' config policy 'lte_p_wan_s' list use_member 'lte1_m1_w5' list use_member 'lte2_m1_w5' list use_member 'wan_m2_w2' option last_resort 'default' config rule 'lte_first' option dest_ip '0.0.0.0/0' option proto 'all' option sticky '0' option use_policy 'lte_p_wan_s' Output of "cat /etc/config/network" : config interface 'loopback' option ifname 'lo' option proto 'static' option ipaddr '127.0.0.1' option netmask '255.0.0.0' config globals 'globals' config interface 'lan' option type 'bridge' option ifname 'eth1' option proto 'static' option ipaddr '192.168.11.1' option netmask '255.255.255.0' config interface 'wan' option ifname 'eth0' option proto 'dhcp' option mtu '1492' option metric '43' config interface 'lte1' option ifname 'wwan0' option proto 'dhcp' option metric '41' config interface 'lte2' option ifname 'wwan1' option proto 'dhcp' option metric '42' Output of "cat /etc/config/wireless" : config wifi-device 'radio0' option type 'mac80211' option channel '11' option hwmode '11g' option path 'platform/qca953x_wmac' option htmode 'HT40' option noscan '1' option country 'CN' config wifi-iface 'default_radio0' option device 'radio0' option network 'lan' option mode 'ap' option ssid 'LEDE_3128' option encryption 'psk2' KEY HIDDEN Output of "ifconfig" : br-lan Link encap:Ethernet HWaddr 00:03:7F:11:23:C6 inet addr:192.168.11.1 Bcast:192.168.11.255 Mask:255.255.255.0 inet6 addr: fe80::203:7fff:fe11:23c6/64 Scope:Link UP BROADCAST RUNNING MULTICAST MTU:1500 Metric:1 RX packets:3003 errors:0 dropped:0 overruns:0 frame:0 TX packets:2202 errors:0 dropped:0 overruns:0 carrier:0 collisions:0 txqueuelen:1000 RX bytes:264170 (257.9 KiB) TX bytes:804422 (785.5 KiB) br-lan:0 Link encap:Ethernet HWaddr 00:03:7F:11:23:C6 inet addr:192.168.111.254 Bcast:0.0.0.0 Mask:255.255.255.0 UP BROADCAST RUNNING MULTICAST MTU:1500 Metric:1 eth0 Link encap:Ethernet HWaddr 94:83:C4:2B:31:28 inet addr:192.168.211.108 Bcast:192.168.211.255 Mask:255.255.255.0 inet6 addr: fe80::9683:c4ff:fe2b:3128/64 Scope:Link UP BROADCAST RUNNING MULTICAST MTU:1492 Metric:1 RX packets:742 errors:0 dropped:0 overruns:0 frame:0 TX packets:2562 errors:0 dropped:0 overruns:0 carrier:0 collisions:0 txqueuelen:1000 RX bytes:98800 (96.4 KiB) TX bytes:221928 (216.7 KiB) Interrupt:4 eth1 Link encap:Ethernet HWaddr 00:03:7F:11:23:C6 UP BROADCAST RUNNING MULTICAST MTU:1500 Metric:1 RX packets:3007 errors:0 dropped:4 overruns:0 frame:0 TX packets:2197 errors:0 dropped:0 overruns:0 carrier:0 collisions:0 txqueuelen:1000 RX bytes:306452 (299.2 KiB) TX bytes:803864 (785.0 KiB) Interrupt:5 lo Link encap:Local Loopback inet addr:127.0.0.1 Mask:255.0.0.0 inet6 addr: ::1/128 Scope:Host UP LOOPBACK RUNNING MTU:65536 Metric:1 RX packets:846 errors:0 dropped:0 overruns:0 frame:0 TX packets:846 errors:0 dropped:0 overruns:0 carrier:0 collisions:0 txqueuelen:1 RX bytes:55968 (54.6 KiB) TX bytes:55968 (54.6 KiB) wlan0 Link encap:Ethernet HWaddr 94:83:C4:2B:31:28 inet6 addr: fe80::9683:c4ff:fe2b:3128/64 Scope:Link UP BROADCAST RUNNING MULTICAST MTU:1500 Metric:1 RX packets:0 errors:0 dropped:0 overruns:0 frame:0 TX packets:986 errors:0 dropped:0 overruns:0 carrier:0 collisions:0 txqueuelen:1000 RX bytes:0 (0.0 B) TX bytes:124871 (121.9 KiB) wwan0 Link encap:Ethernet HWaddr FA:52:E6:62:B9:B8 inet addr:100.64.32.73 Mask:255.255.255.252 inet6 addr: fe80::f852:e6ff:fe62:b9b8/64 Scope:Link UP RUNNING NOARP MTU:1500 Metric:1 RX packets:1312 errors:0 dropped:0 overruns:0 frame:0 TX packets:1376 errors:0 dropped:0 overruns:0 carrier:0 collisions:0 txqueuelen:1000 RX bytes:111264 (108.6 KiB) TX bytes:128597 (125.5 KiB) Output of "route -n" : Kernel IP routing table Destination Gateway Genmask Flags Metric Ref Use Iface 0.0.0.0 100.64.32.74 0.0.0.0 UG 41 0 0 wwan0 0.0.0.0 192.168.211.1 0.0.0.0 UG 43 0 0 eth0 100.64.32.72 0.0.0.0 255.255.255.252 U 41 0 0 wwan0 192.168.11.0 0.0.0.0 255.255.255.0 U 0 0 0 br-lan 192.168.111.0 0.0.0.0 255.255.255.0 U 0 0 0 br-lan 192.168.211.0 0.0.0.0 255.255.255.0 U 43 0 0 eth0 Output of "ip rule show" : 0: from all lookup local 1001: from all iif eth0 lookup main 1002: from all iif wwan0 lookup main 2001: from all fwmark 0x100/0xff00 lookup 1 2002: from all fwmark 0x200/0xff00 lookup 2 2253: from all fwmark 0xfd00/0xff00 blackhole 2254: from all fwmark 0xfe00/0xff00 unreachable 32766: from all lookup main 32767: from all lookup default Output of "ip route list table 1-250" : 1 default via 192.168.211.1 dev eth0 2 default via 100.64.32.74 dev wwan0 Firewall default output policy (must be ACCEPT) : ACCEPT Output of "iptables -L -t mangle -v -n" : Chain PREROUTING (policy ACCEPT 198 packets, 17561 bytes) pkts bytes target prot opt in out source destination 5433 464K mwan3_hook all -- * * 0.0.0.0/0 0.0.0.0/0 Chain INPUT (policy ACCEPT 159 packets, 14019 bytes) pkts bytes target prot opt in out source destination Chain FORWARD (policy ACCEPT 0 packets, 0 bytes) pkts bytes target prot opt in out source destination 0 0 TCPMSS tcp -- * eth0 0.0.0.0/0 0.0.0.0/0 tcp flags:0x06/0x02 /* !fw3: Zone wan MTU fixing */ TCPMSS clamp to PMTU 0 0 TCPMSS tcp -- eth0 * 0.0.0.0/0 0.0.0.0/0 tcp flags:0x06/0x02 /* !fw3: Zone wan MTU fixing */ TCPMSS clamp to PMTU 0 0 TCPMSS tcp -- * wwan0 0.0.0.0/0 0.0.0.0/0 tcp flags:0x06/0x02 /* !fw3: Zone lte1 MTU fixing */ TCPMSS clamp to PMTU 0 0 TCPMSS tcp -- wwan0 * 0.0.0.0/0 0.0.0.0/0 tcp flags:0x06/0x02 /* !fw3: Zone lte1 MTU fixing */ TCPMSS clamp to PMTU 0 0 TCPMSS tcp -- * wwan1 0.0.0.0/0 0.0.0.0/0 tcp flags:0x06/0x02 /* !fw3: Zone lte2 MTU fixing */ TCPMSS clamp to PMTU 0 0 TCPMSS tcp -- wwan1 * 0.0.0.0/0 0.0.0.0/0 tcp flags:0x06/0x02 /* !fw3: Zone lte2 MTU fixing */ TCPMSS clamp to PMTU Chain OUTPUT (policy ACCEPT 199 packets, 73191 bytes) pkts bytes target prot opt in out source destination 6437 1084K mwan3_hook all -- * * 0.0.0.0/0 0.0.0.0/0 Chain POSTROUTING (policy ACCEPT 199 packets, 73191 bytes) pkts bytes target prot opt in out source destination Chain mwan3_connected (2 references) pkts bytes target prot opt in out source destination 2870 246K MARK all -- * * 0.0.0.0/0 0.0.0.0/0 match-set mwan3_connected dst MARK or 0xff00 Chain mwan3_hook (2 references) pkts bytes target prot opt in out source destination 11870 1547K CONNMARK all -- * * 0.0.0.0/0 0.0.0.0/0 CONNMARK restore mask 0xff00 3163 259K mwan3_ifaces_in all -- * * 0.0.0.0/0 0.0.0.0/0 mark match 0x0/0xff00 3159 258K mwan3_connected all -- * * 0.0.0.0/0 0.0.0.0/0 mark match 0x0/0xff00 2464 203K mwan3_ifaces_out all -- * * 0.0.0.0/0 0.0.0.0/0 mark match 0x0/0xff00 600 47457 mwan3_rules all -- * * 0.0.0.0/0 0.0.0.0/0 mark match 0x0/0xff00 11870 1547K CONNMARK all -- * * 0.0.0.0/0 0.0.0.0/0 CONNMARK save mask 0xff00 4669 399K mwan3_connected all -- * * 0.0.0.0/0 0.0.0.0/0 mark match ! 0xff00/0xff00 Chain mwan3_iface_in_lte1 (1 references) pkts bytes target prot opt in out source destination 0 0 MARK all -- wwan0 * 0.0.0.0/0 0.0.0.0/0 match-set mwan3_connected src mark match 0x0/0xff00 /* default */ MARK or 0xff00 0 0 MARK all -- wwan0 * 0.0.0.0/0 0.0.0.0/0 mark match 0x0/0xff00 /* lte1 */ MARK xset 0x200/0xff00 Chain mwan3_iface_in_wan (1 references) pkts bytes target prot opt in out source destination 0 0 MARK all -- eth0 * 0.0.0.0/0 0.0.0.0/0 match-set mwan3_connected src mark match 0x0/0xff00 /* default */ MARK or 0xff00 0 0 MARK all -- eth0 * 0.0.0.0/0 0.0.0.0/0 mark match 0x0/0xff00 /* wan */ MARK xset 0x100/0xff00 Chain mwan3_iface_out_lte1 (1 references) pkts bytes target prot opt in out source destination 1314 110K MARK all -- * * 100.64.32.73 0.0.0.0/0 mark match 0x0/0xff00 /* lte1 */ MARK xset 0x200/0xff00 Chain mwan3_iface_out_wan (1 references) pkts bytes target prot opt in out source destination 10 840 MARK all -- * * 192.168.211.108 0.0.0.0/0 mark match 0x0/0xff00 /* wan */ MARK xset 0x100/0xff00 Chain mwan3_ifaces_in (1 references) pkts bytes target prot opt in out source destination 3088 251K mwan3_iface_in_lte1 all -- * * 0.0.0.0/0 0.0.0.0/0 mark match 0x0/0xff00 78 6626 mwan3_iface_in_wan all -- * * 0.0.0.0/0 0.0.0.0/0 mark match 0x0/0xff00 Chain mwan3_ifaces_out (1 references) pkts bytes target prot opt in out source destination 2394 197K mwan3_iface_out_lte1 all -- * * 0.0.0.0/0 0.0.0.0/0 mark match 0x0/0xff00 45 3570 mwan3_iface_out_wan all -- * * 0.0.0.0/0 0.0.0.0/0 mark match 0x0/0xff00 Chain mwan3_policy_lte_p_wan_s (1 references) pkts bytes target prot opt in out source destination 35 2730 MARK all -- * * 0.0.0.0/0 0.0.0.0/0 mark match 0x0/0xff00 /* lte1 5 5 */ MARK xset 0x200/0xff00 Chain mwan3_rules (1 references) pkts bytes target prot opt in out source destination 35 2730 mwan3_policy_lte_p_wan_s all -- * * 0.0.0.0/0 0.0.0.0/0 mark match 0x0/0xff00 /* lte_first */
=========== End




