Buuctf Misc 刷题合集
浅记我在好久之前刷过的misc题目
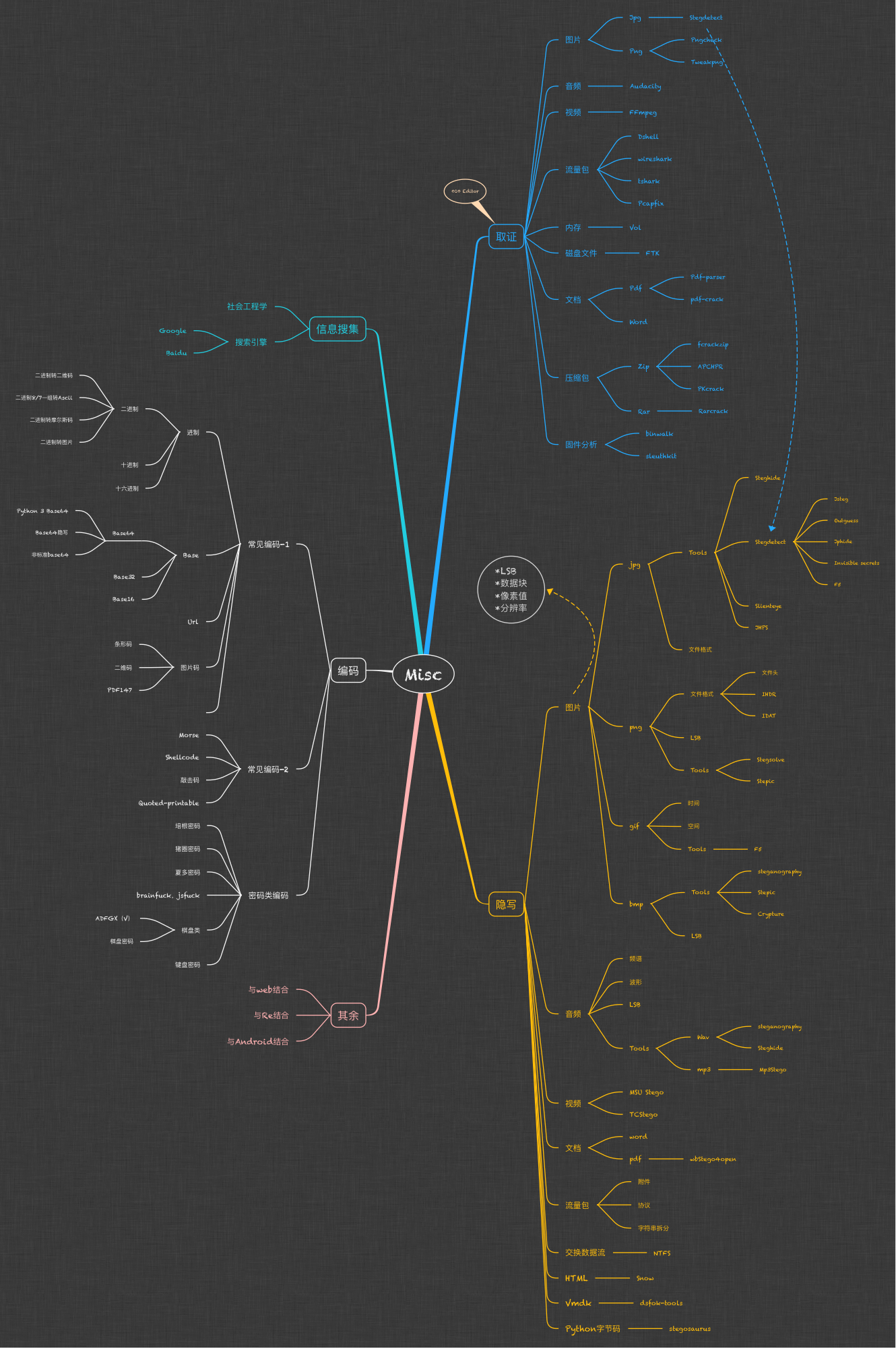
零、MISC知识架构图
一、面具下的flag -- misc 伪加密
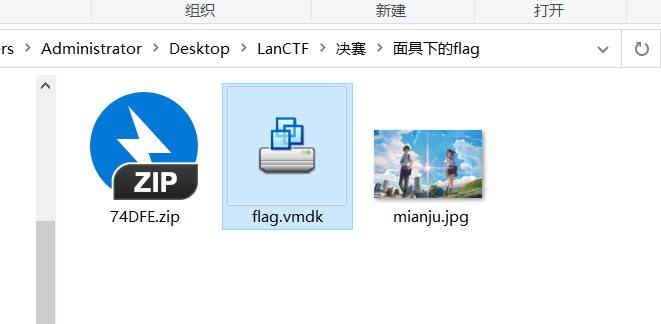
1、题目
2、解法
binwalk -Me ./mjanju,jpg 得到一张照片
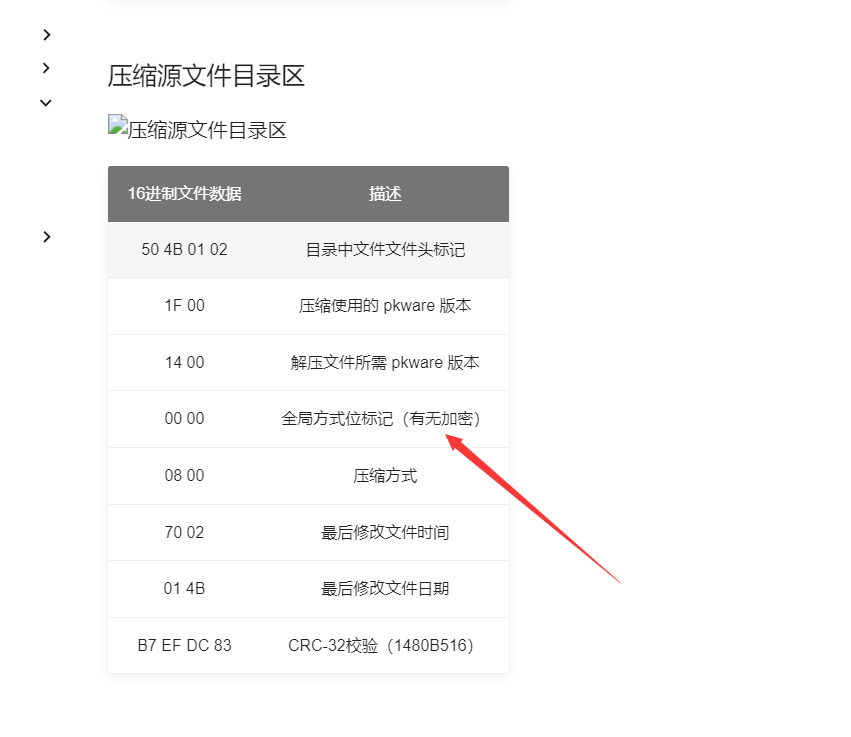
直接搜 50 4b 01 02
往后的第五个字节,把09 00 改为 00 00即可
得到一个vmdk文件
安装7z
得到 flag{N7F5_AD5_i5_funny!}
二、九连环
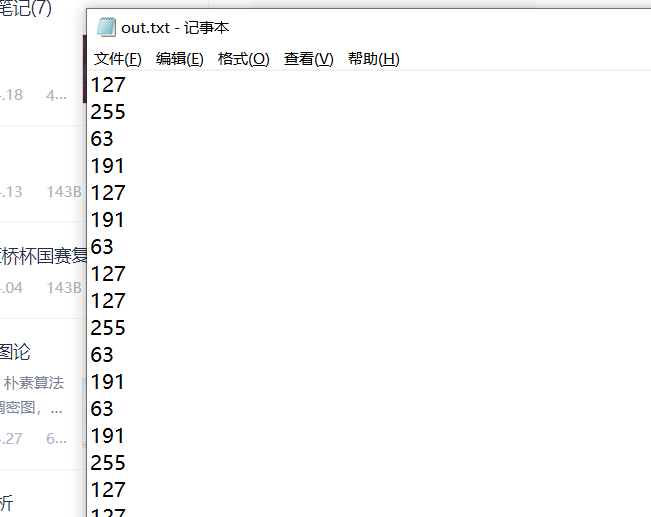
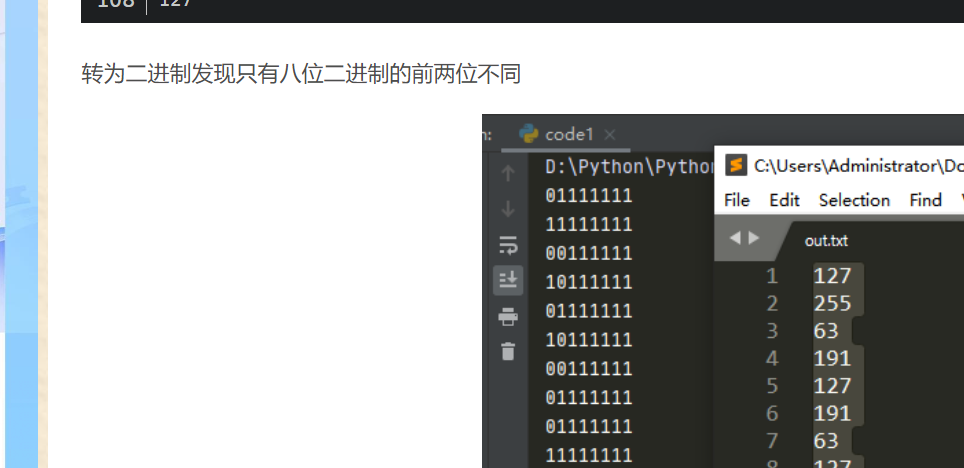
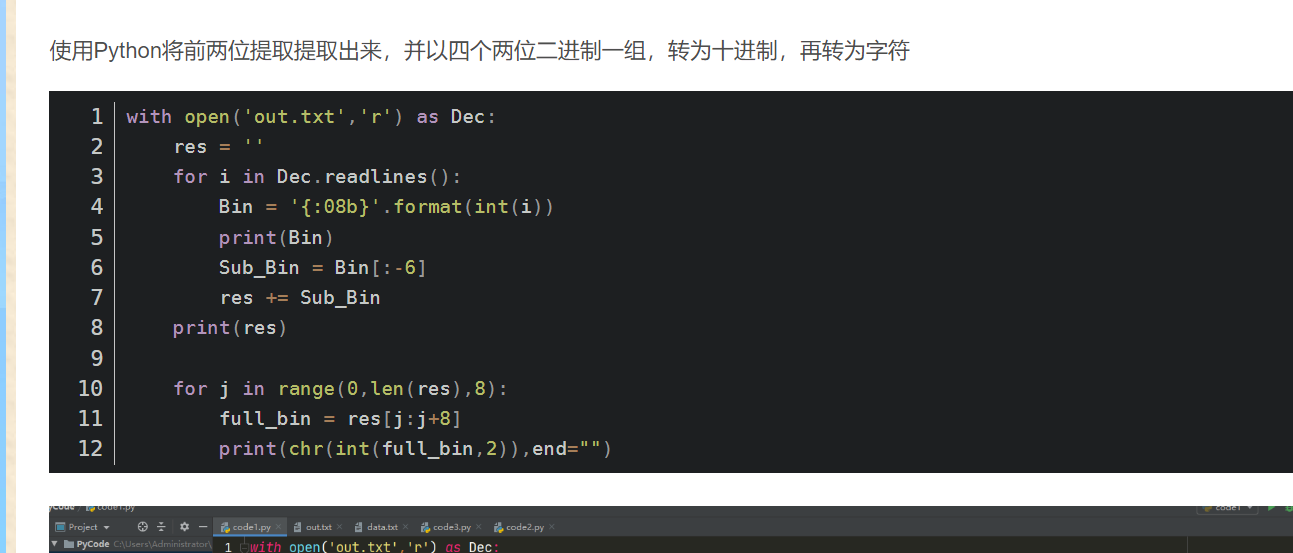
1、binwalk分离得到:
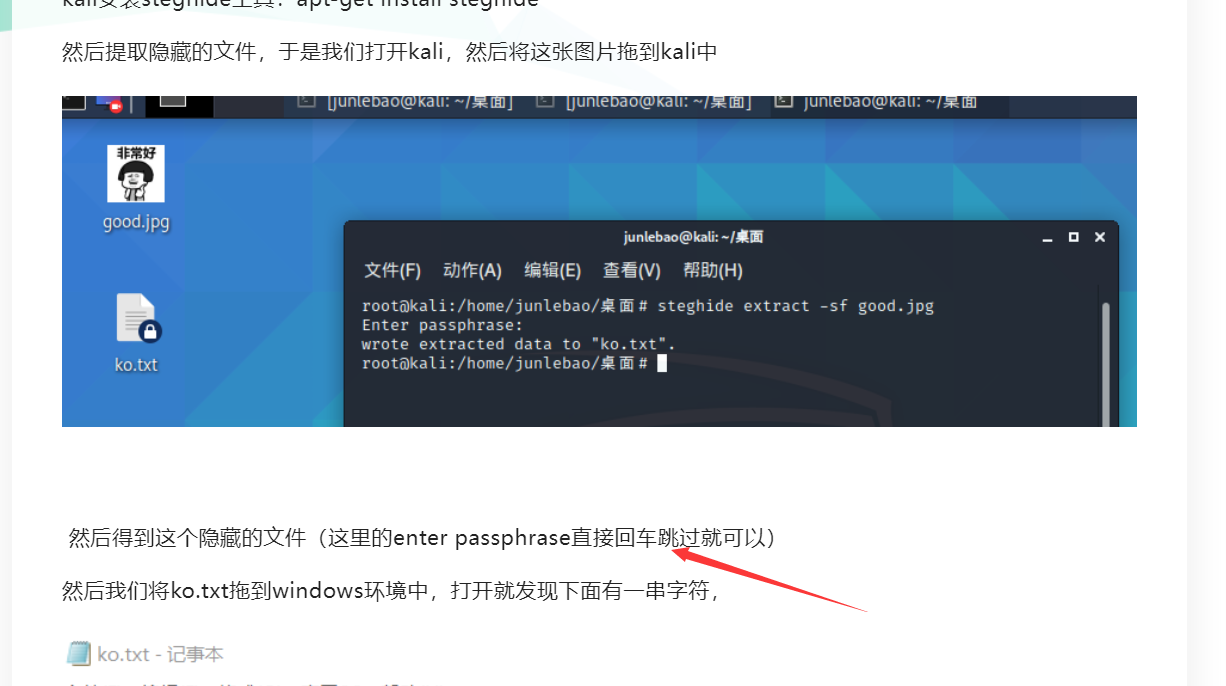
2、Steghide工具得到加密密码
steghide extract -sf ./good-已合并.jpg
拿到flag : flag{1RTo8w@&4nK@z*XL}
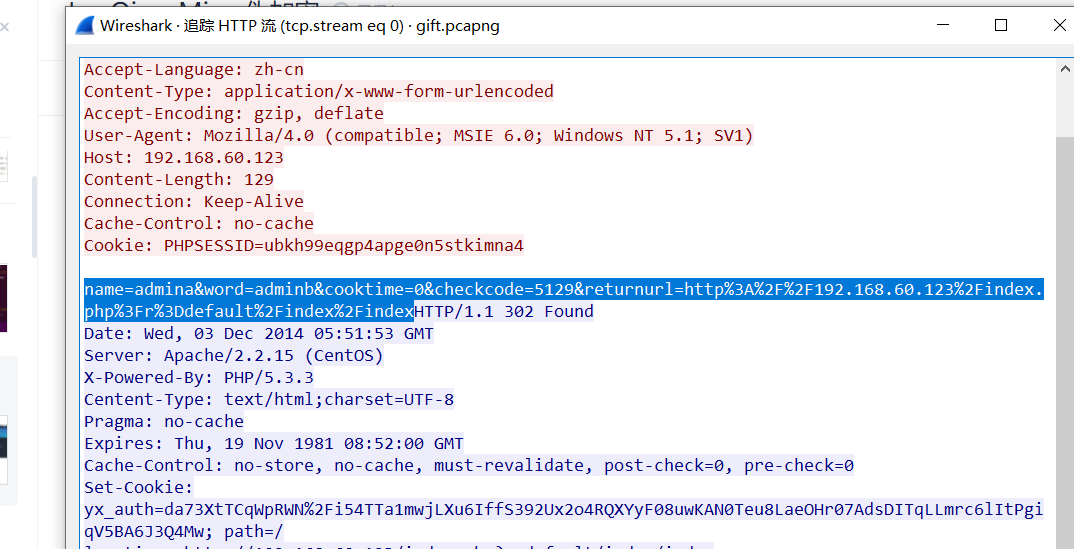
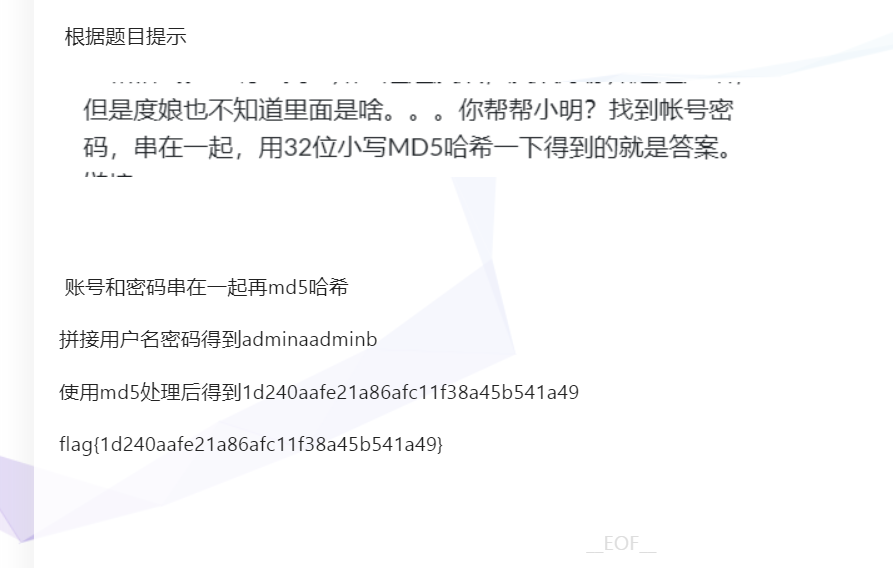
三、被劫持的神秘礼物
追踪http流
flag{1d240aafe21a86afc11f38a45b541a49}
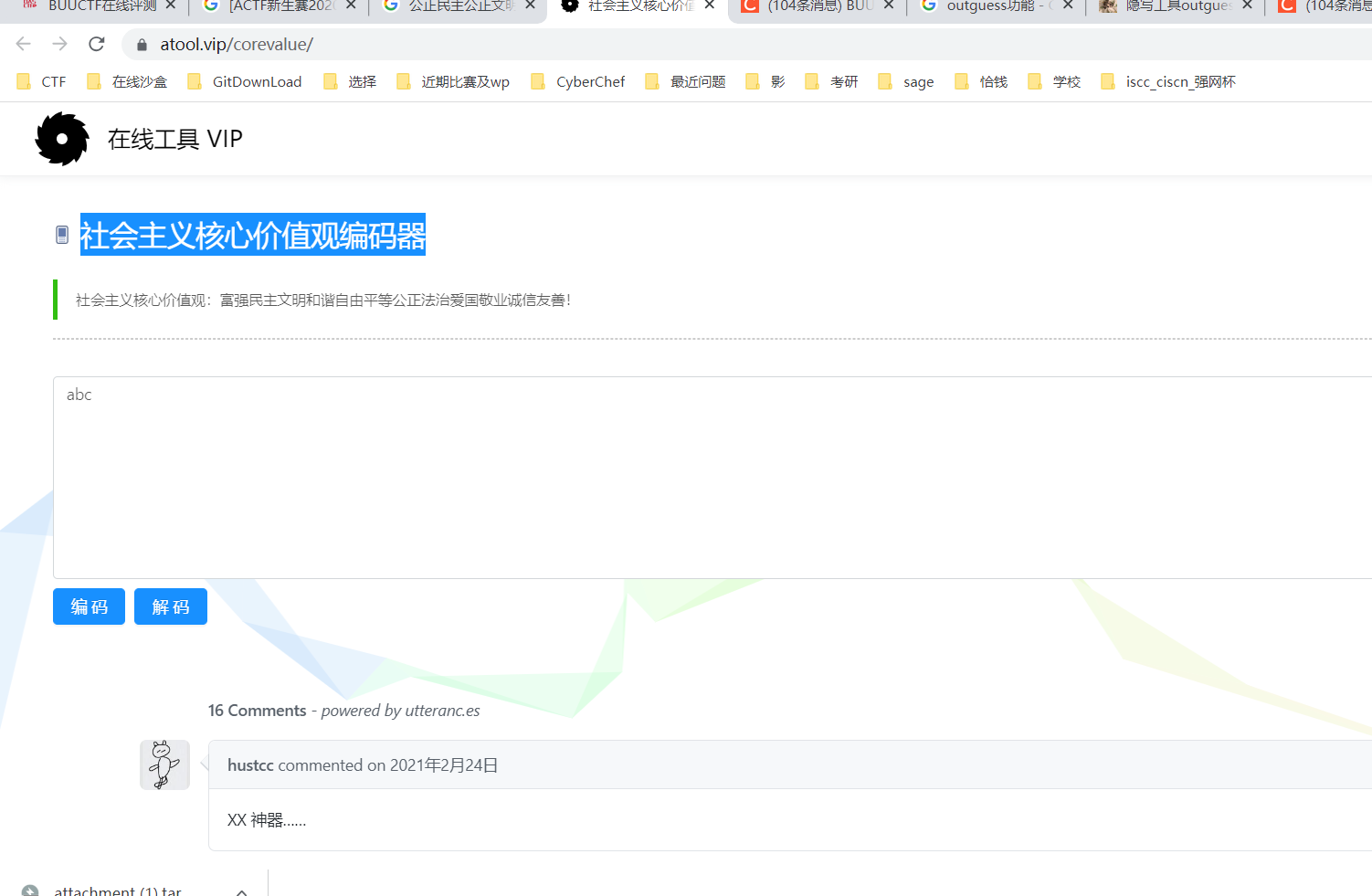
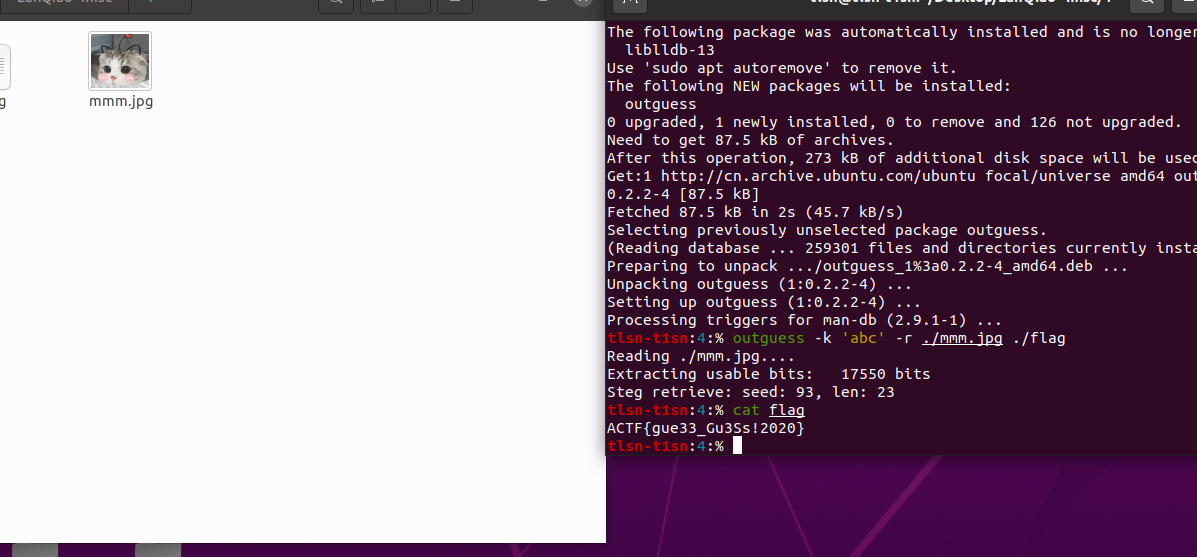
四、[ACTF新生赛2020]outguess
社会主义核心价值观编码器 :
安装 sudo apt-get install outguess
outguess -k 'abc' -r ./mmm.jpg ./flag
拿到flag
ACTF{gue33_Gu3Ss!2020}
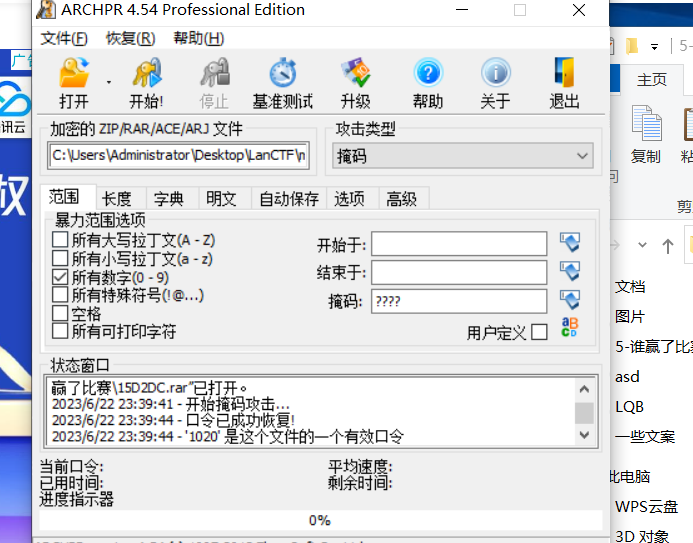
五、谁赢了比赛
1、binwarlk
2、ARCHPR爆破
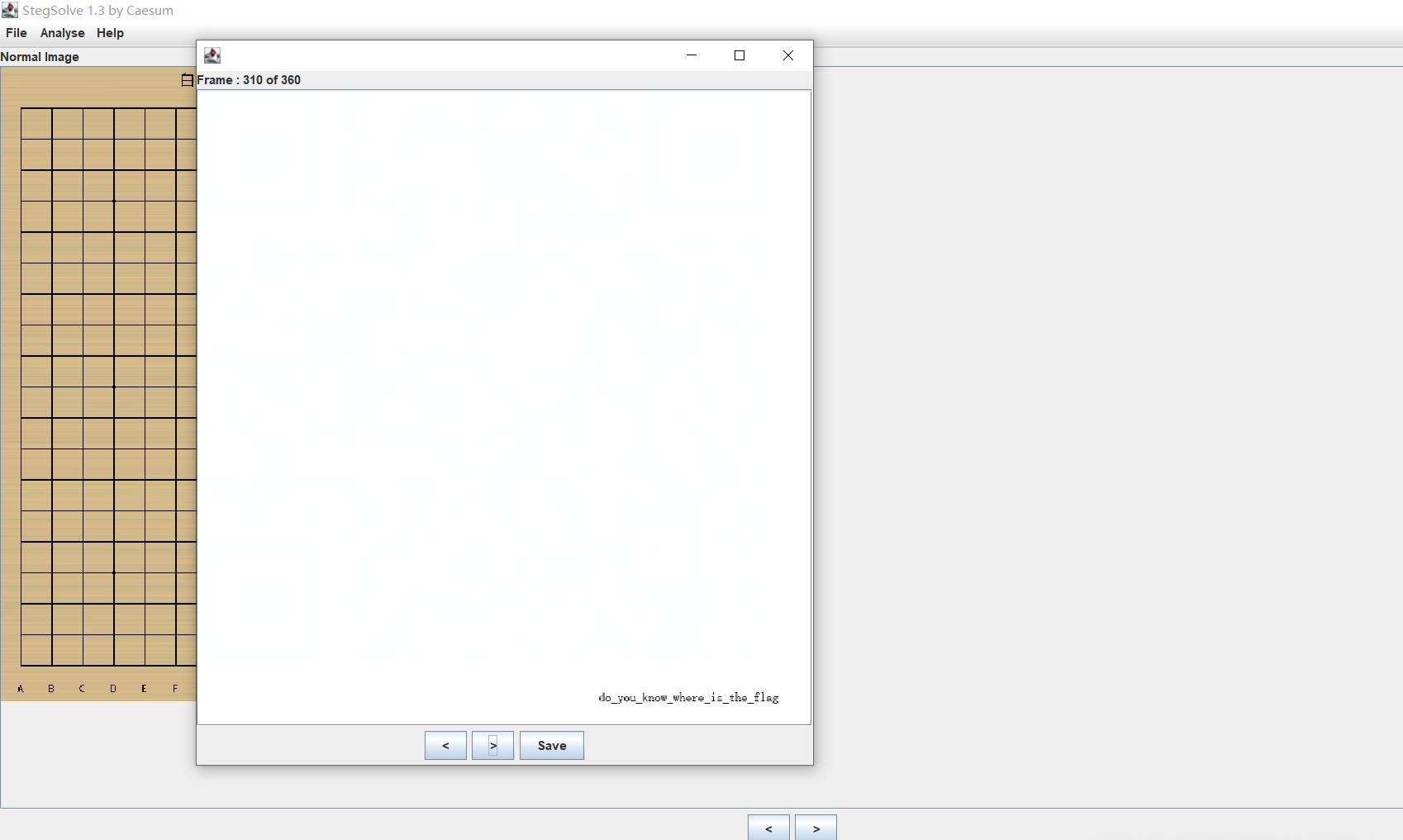
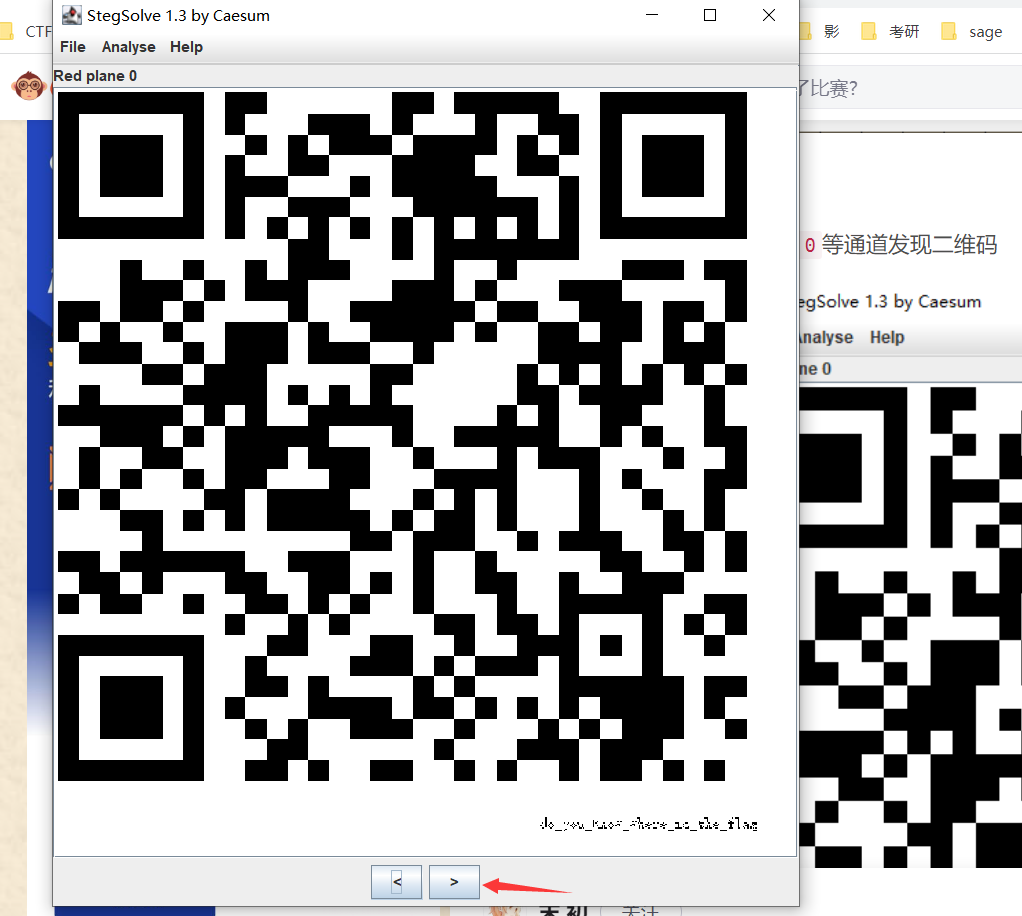
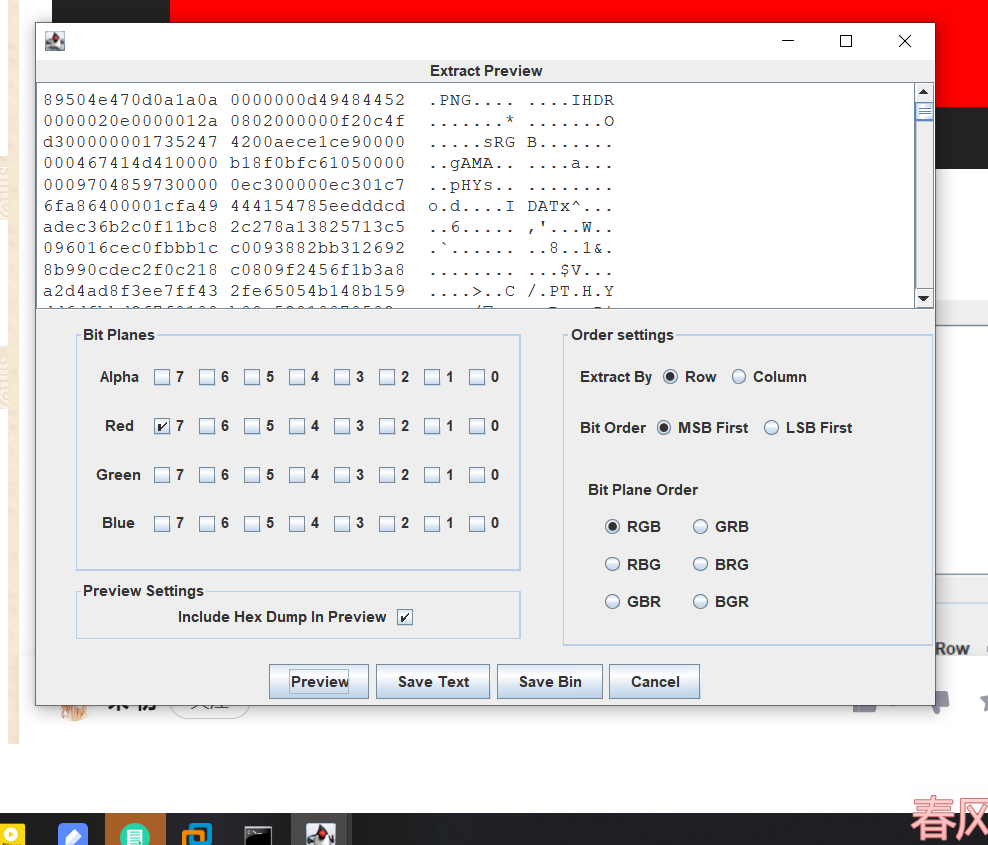
3、stegslove找到第310帧
保存后打开这一帧,不断右移直到 Red plane 0:
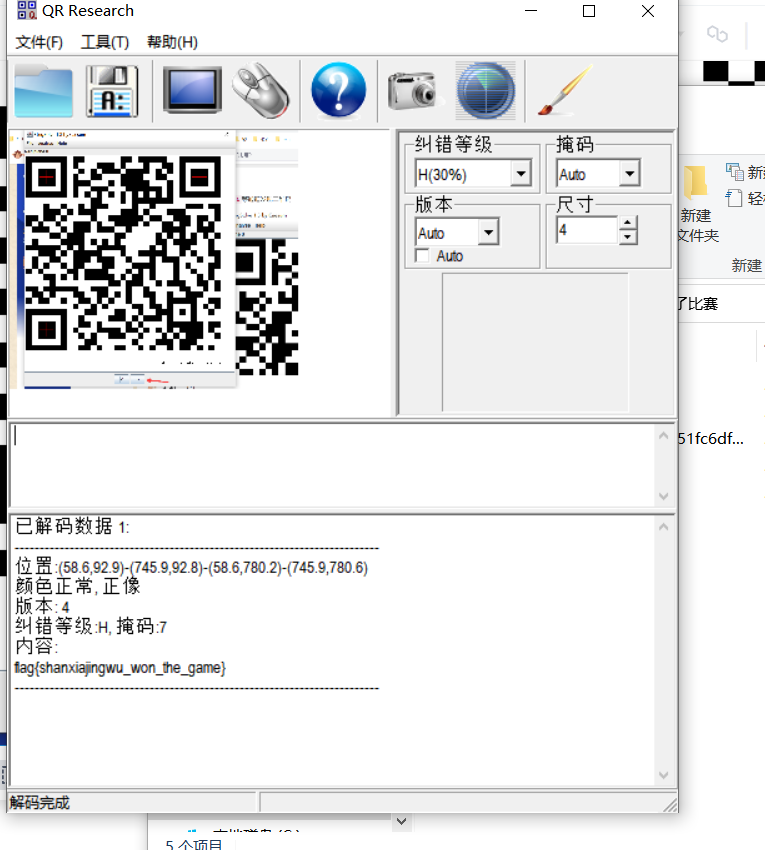
4、下载QR Research 拿到flag
flag{shanxiajingwu_won_the_game}
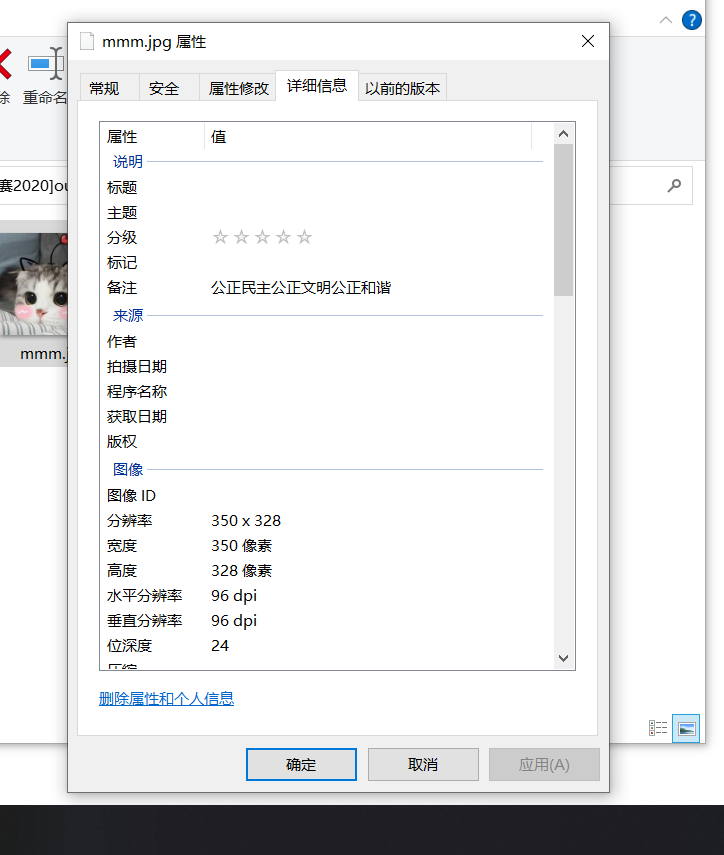
六、[WUSTCTF2020]find_me
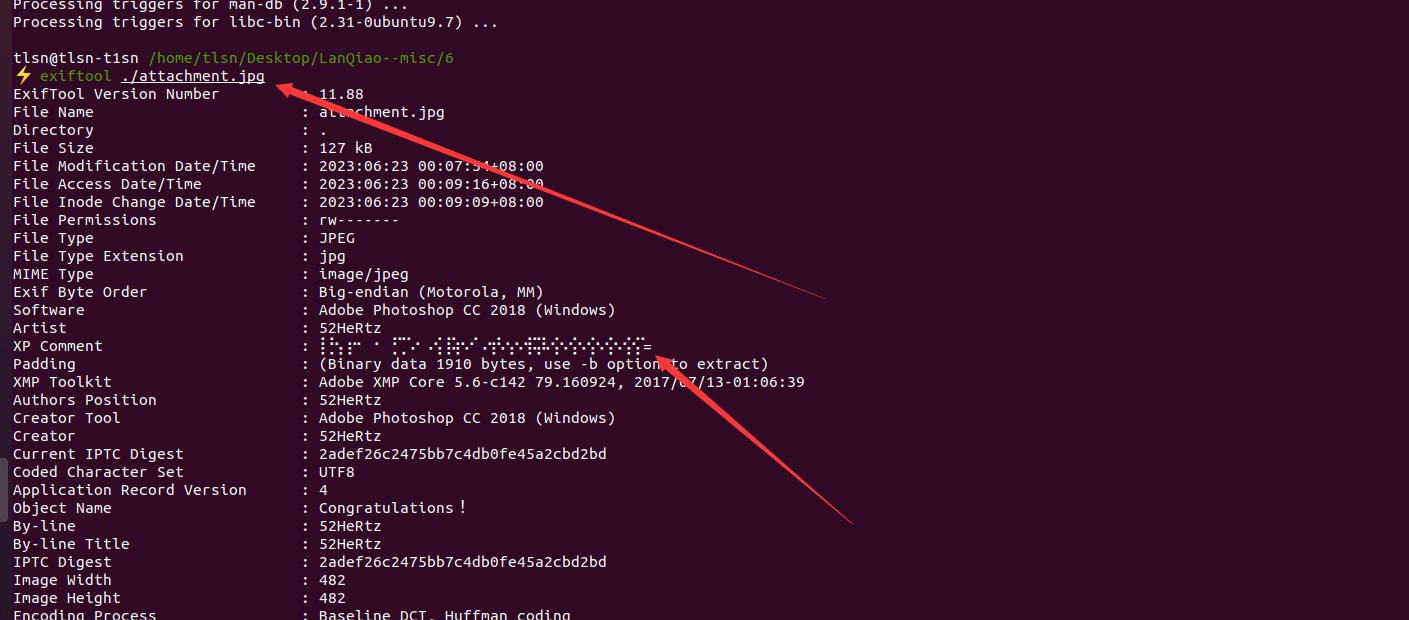
1、下载 exiftool
sudo apt-get install exiftool
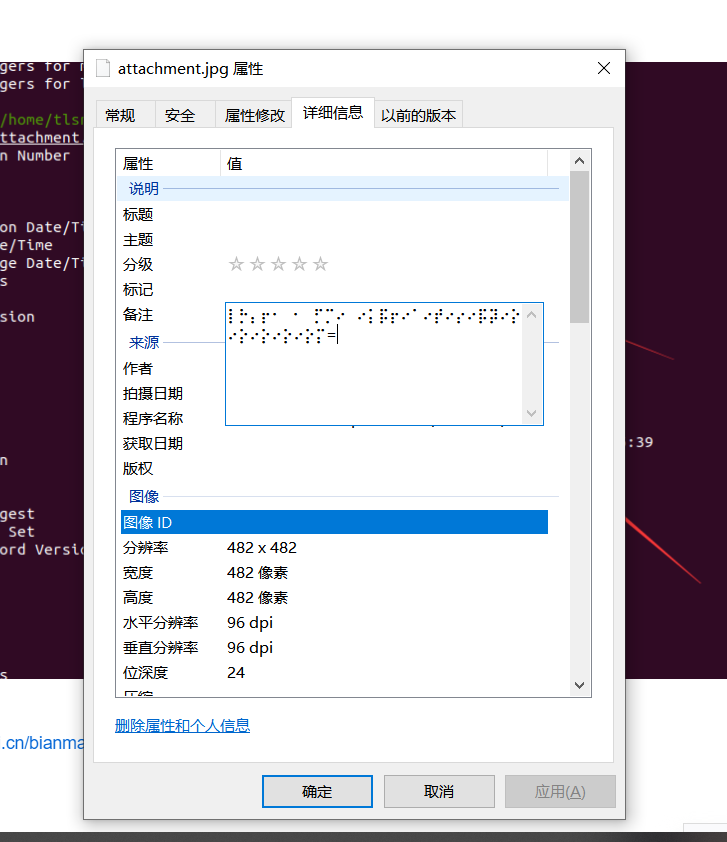
或者查看文件属性
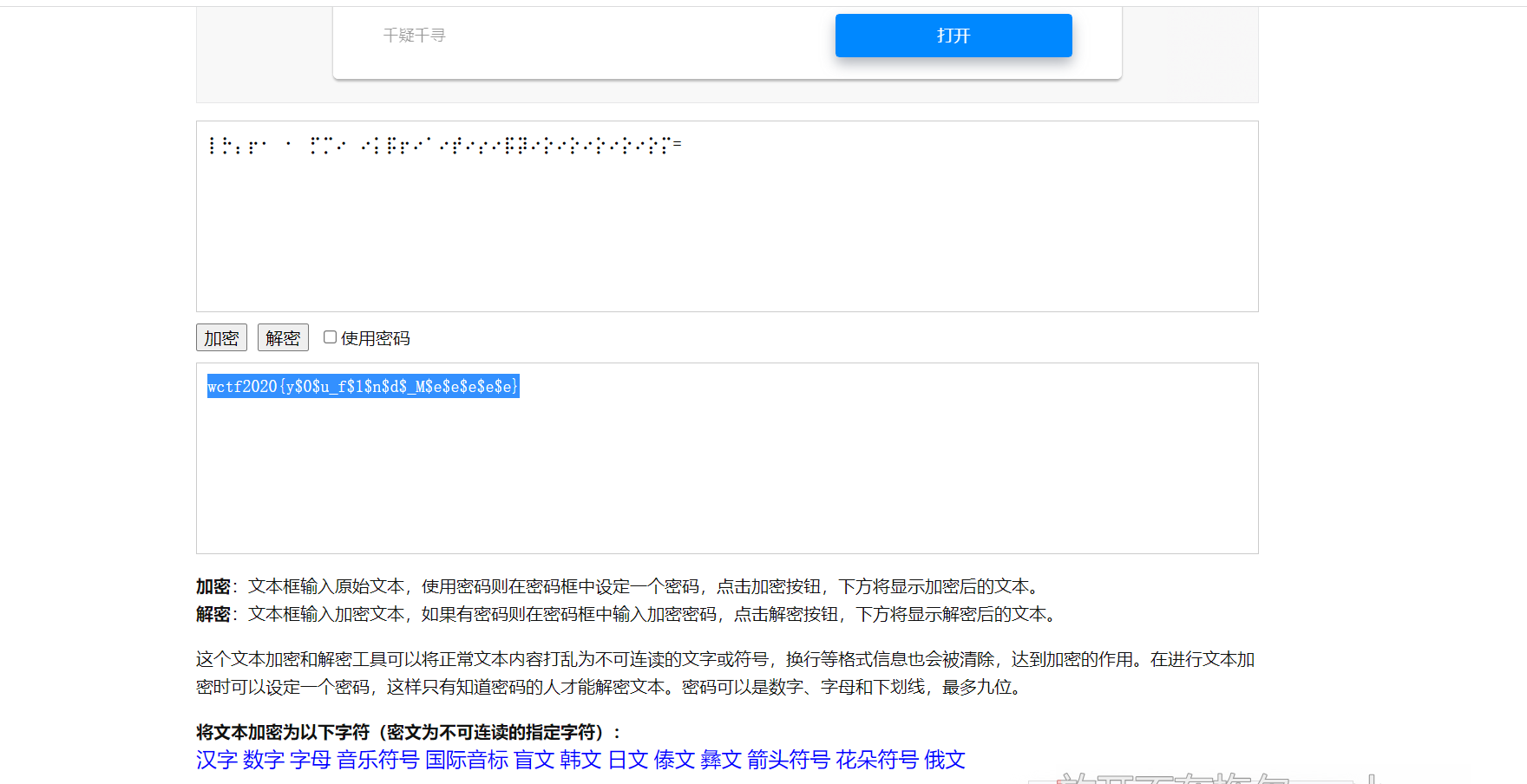
2、盲文在线解密
wctf2020{yu_fn_Mee$e}
七、[SWPU2019]我有一只马里奥
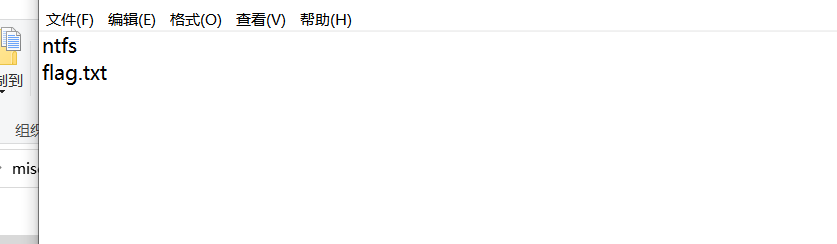
1、ntfs流隐藏
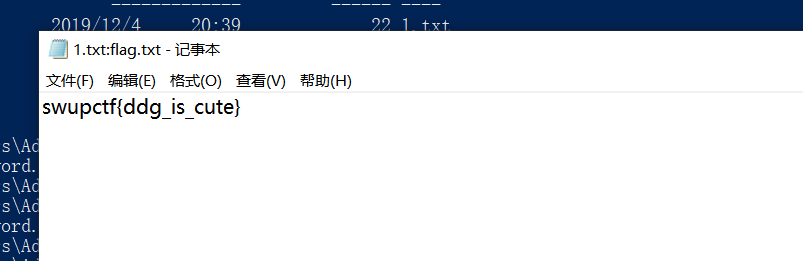
2、显示流
命令为: notepad .\1.txt:flag.txt
swupctf{ddg_is_cute}
ps:我们可以通过这种方式隐藏数据
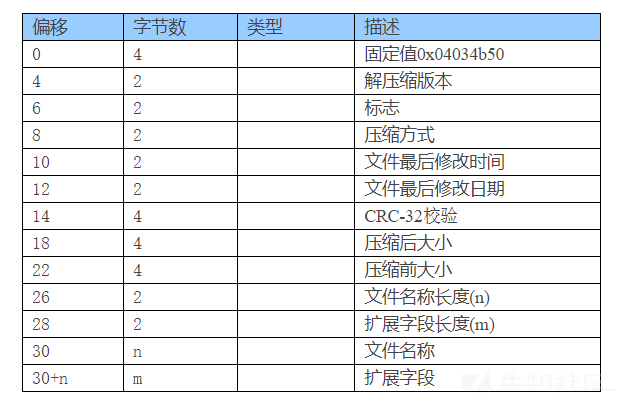
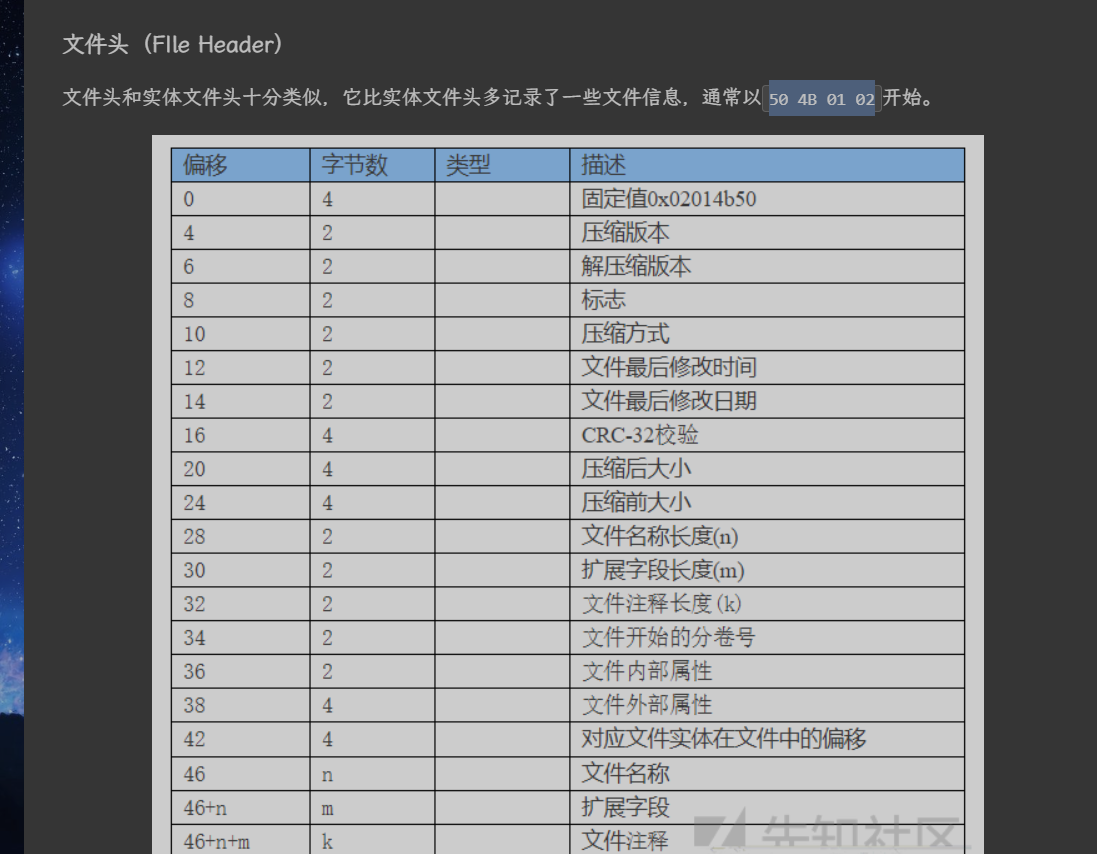
八、[ACTF新生赛2020]明文攻击
1、前置知识
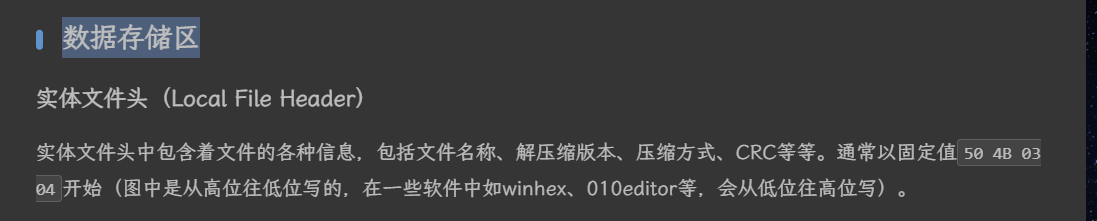
zip文件格式:
也就是说数据存储区中在 偏移 30 即 0x1e的地方应该是压缩包内文件的名称
同理:
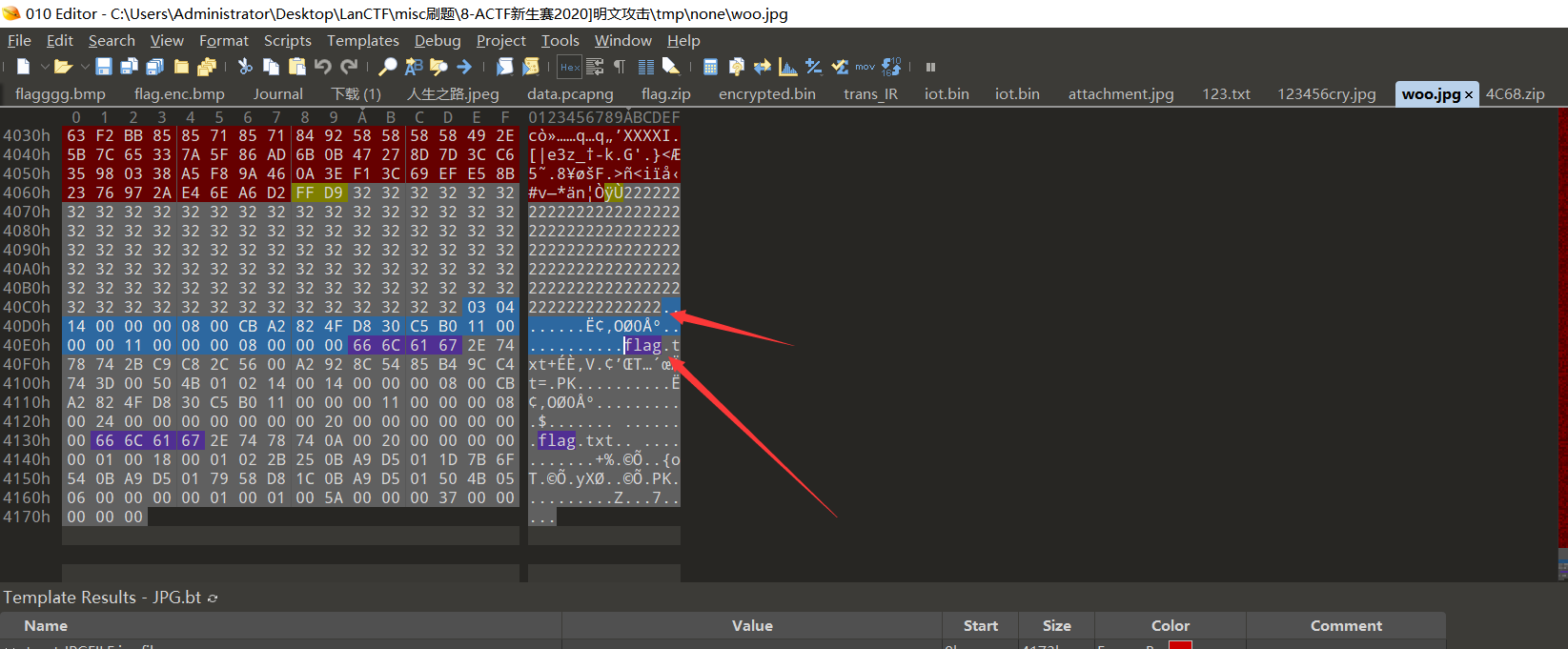
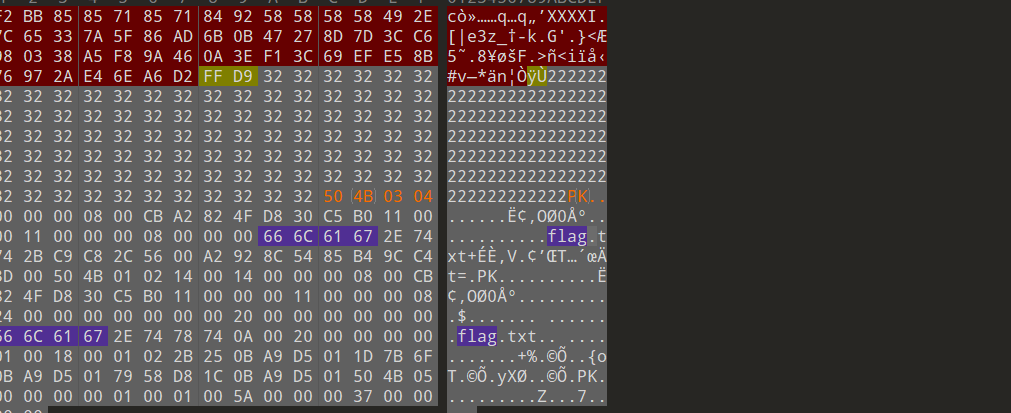
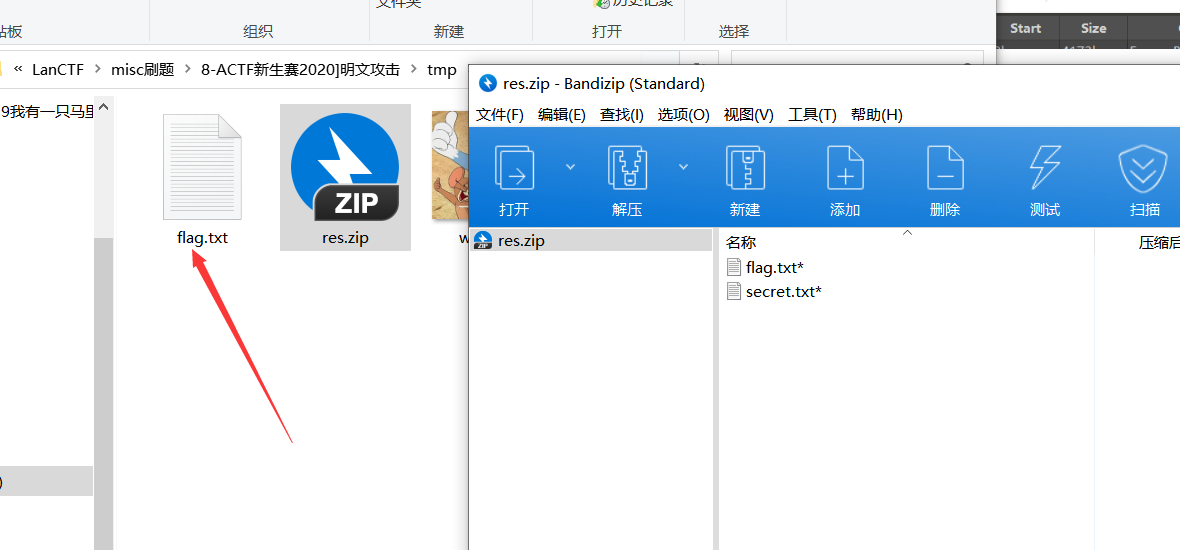
2、被隐藏zip
由题目明文攻击,猜测照片里存在zip
可以发现在flag.txt前0x1e字节处没有50 4B 03 04 标志
手动补齐:
再次binwarlk得到:
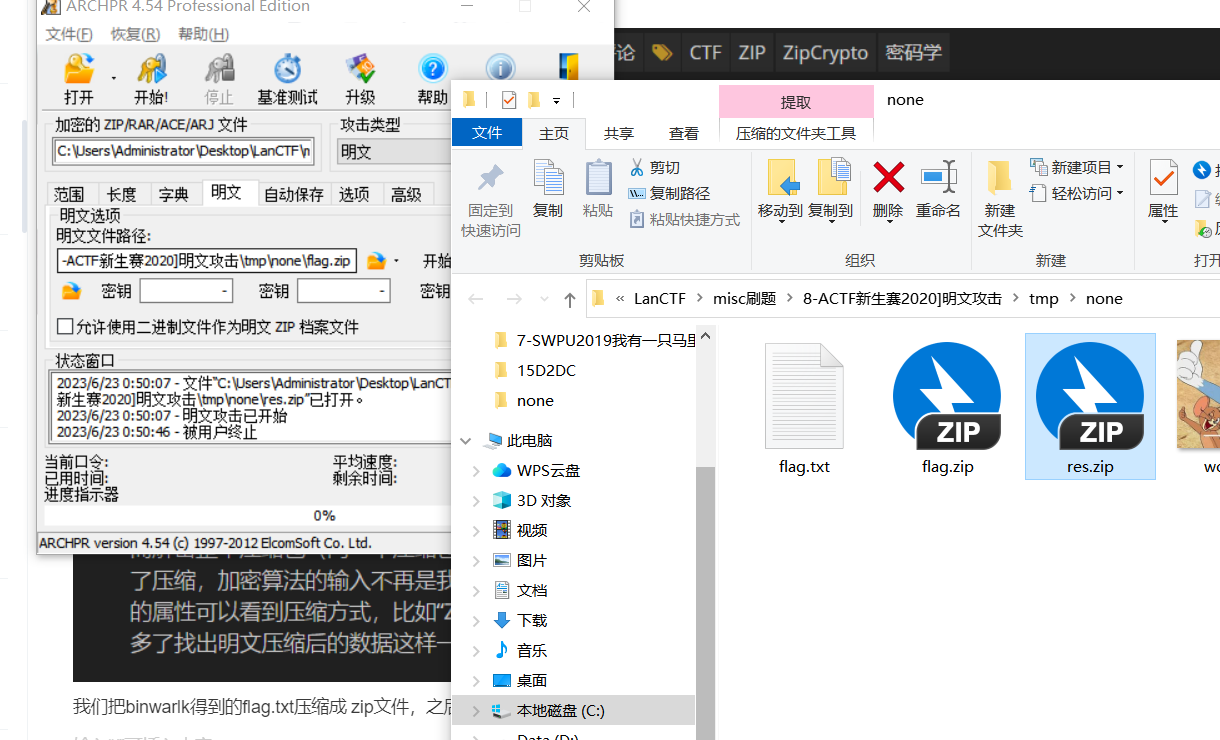
3、明文攻击
我们把binwarlk得到的flag.txt压缩成 zip文件,之后进行明文攻击;
flag{3te9_nbb_ahh8}
九、[MRCTF2020]Hello_ misc
1、Stegslove 发现red 通道有图片
得到图片
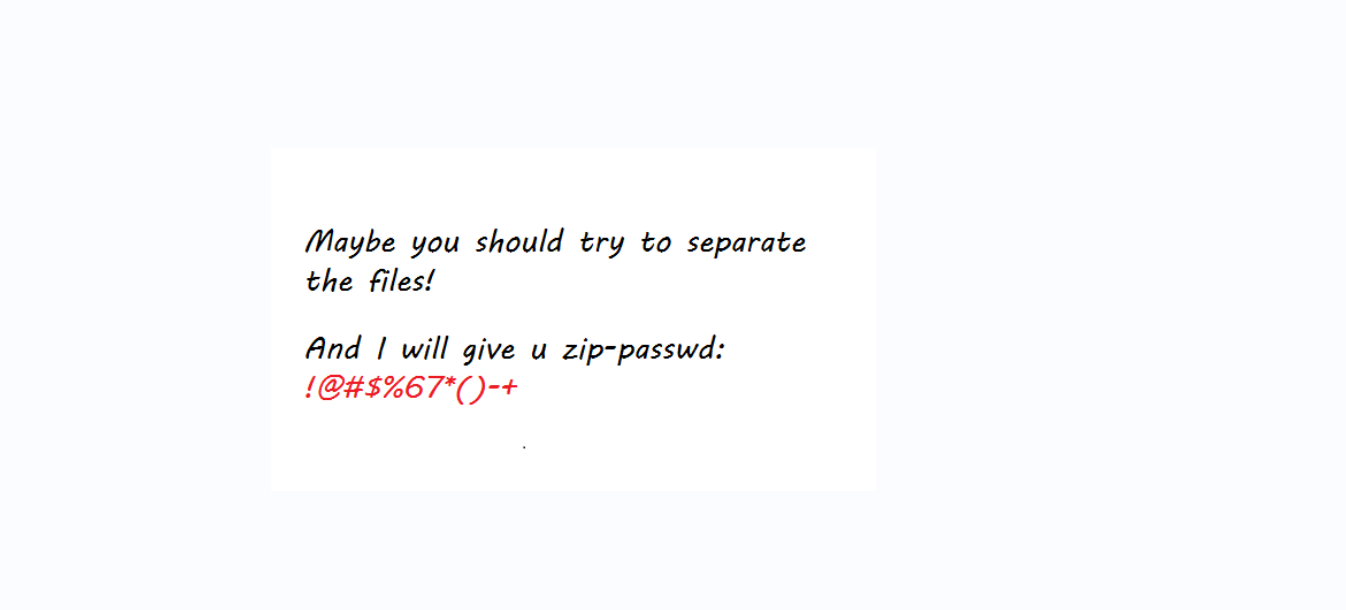
!@#$%67*()-+
2、binwarlk try to restore it.png
得到压缩包,密码为 !@#$%67*()-+
解压:
rar-passwd:0ac1fe6b77be5dbe
3、doc文档
doc文档解压就是这样的
直接改名: fffflag.doc
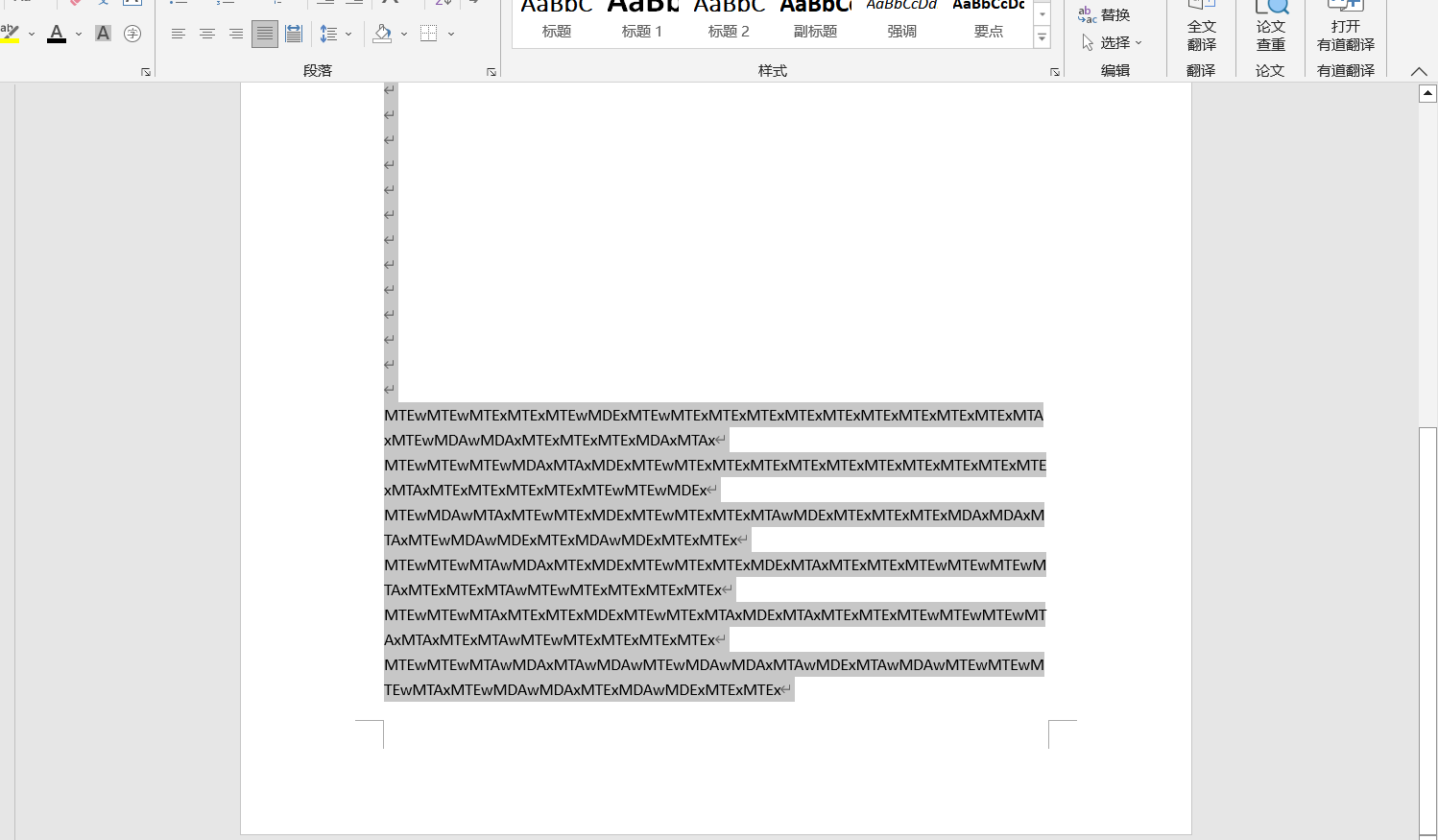
4、全选黑色字体
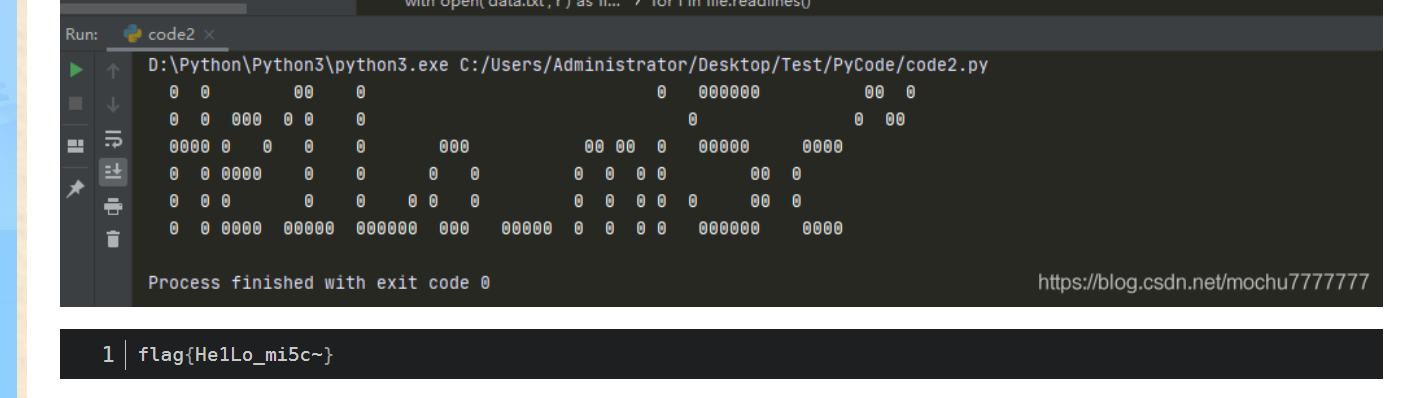
5、分行解base64
flag{He1Lo_mi5c~}
十、WUSTCTF2020-spaceclub
010打开
或者 sublime
发现是每一行的长短对应一个二进制位
拿到flag:
十一、[UTCTF2020]zero
0宽字符隐写
utflag{whyNOT@sc11_4927aajbqk14}
十二、[GKCTF 2021]签到
wireshark 导出http流
base64解密=>逐行反转=>base64解密
得到:
每两个连续重复出现的去重:
拿到flag:
flag{Welc0me_GkC4F_m1siCCCCCC!}
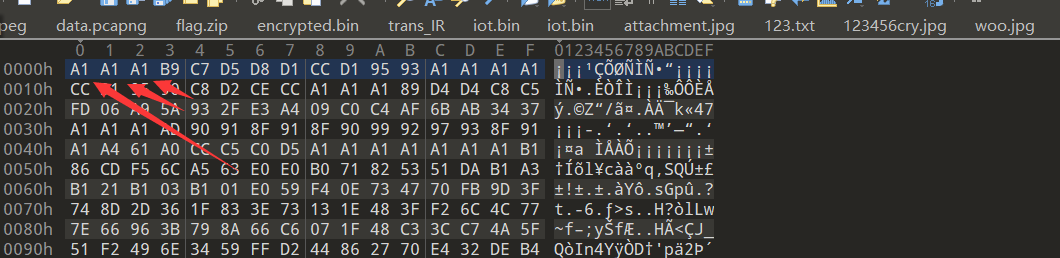
十三、[ACTF新生赛2020]music
对比音频文件格式
猜测文件被异或加密
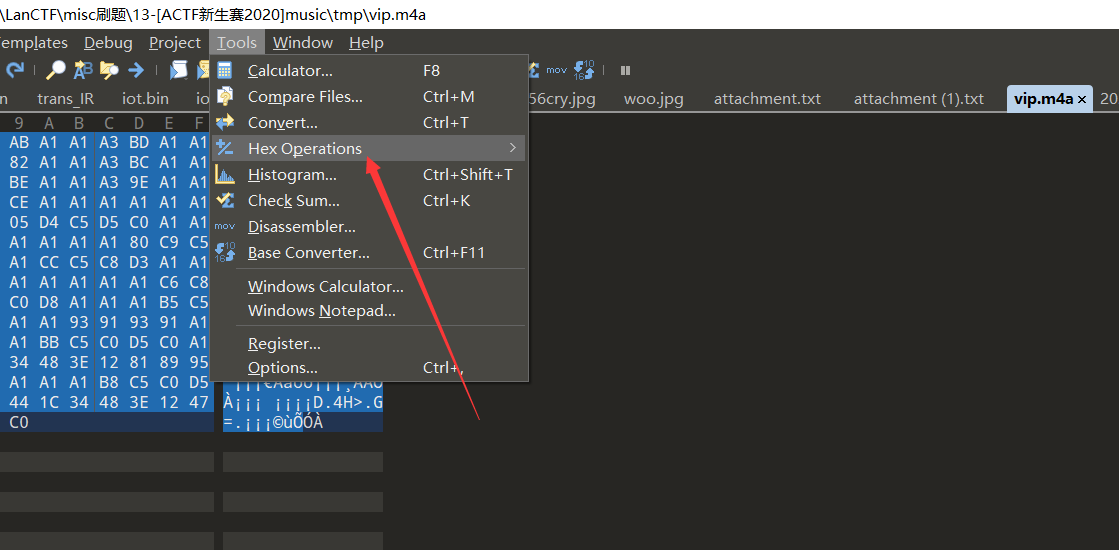
使用010edoitor对其进行异或解密
异或值为 0xa1
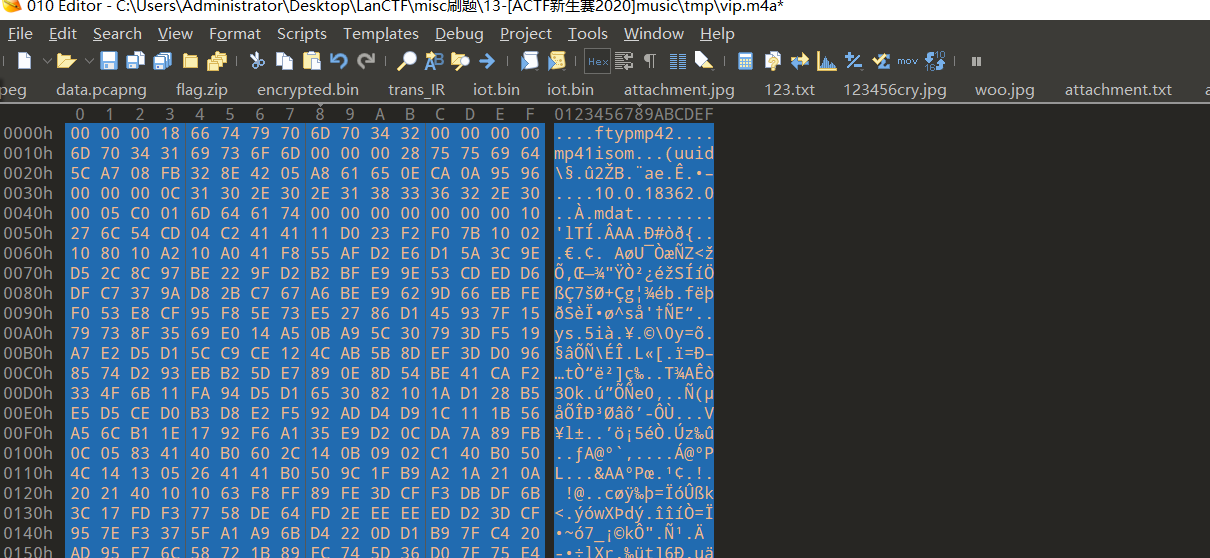
得到:
之后听音频得到:
abcdfghijk
flag即为:
flag{abcdfghijk}
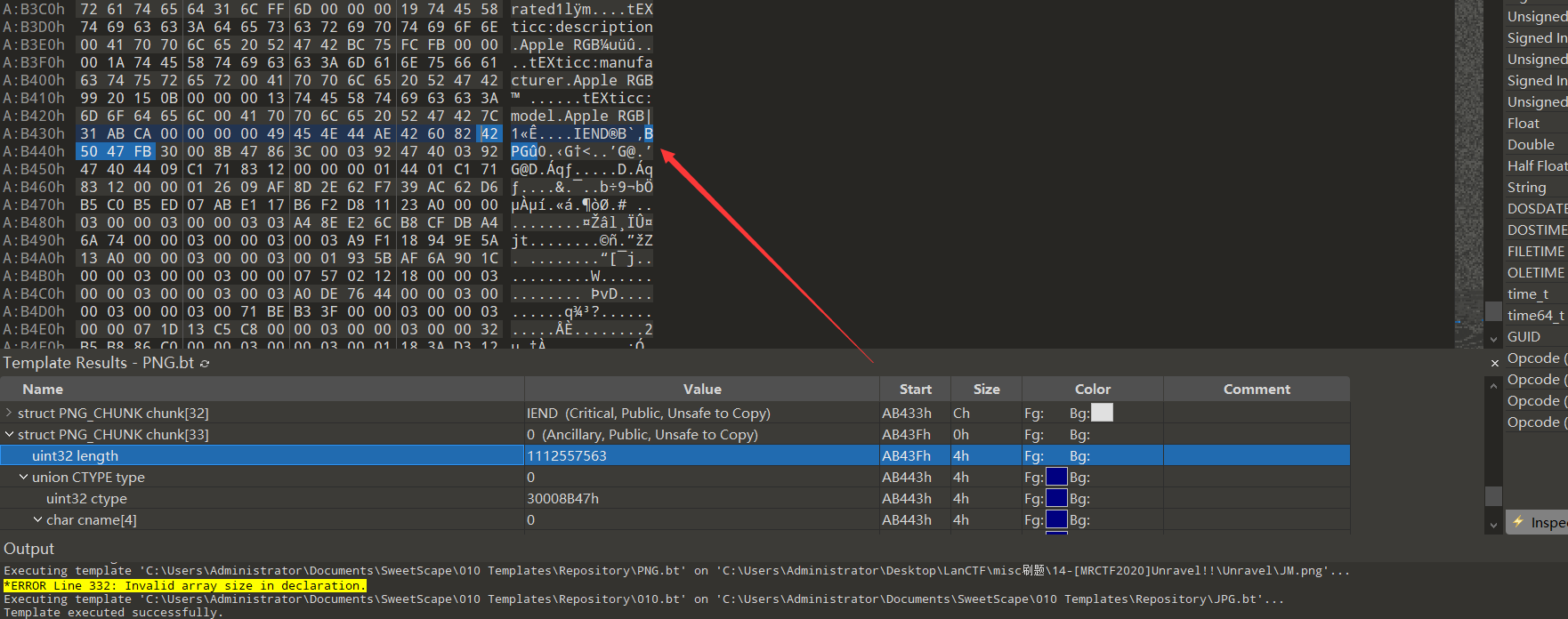
十四、[MRCTF2020]Unravel!!
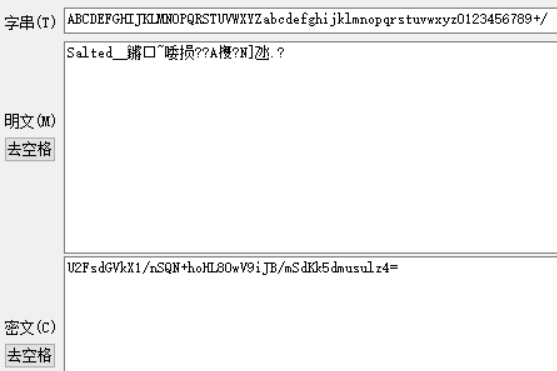
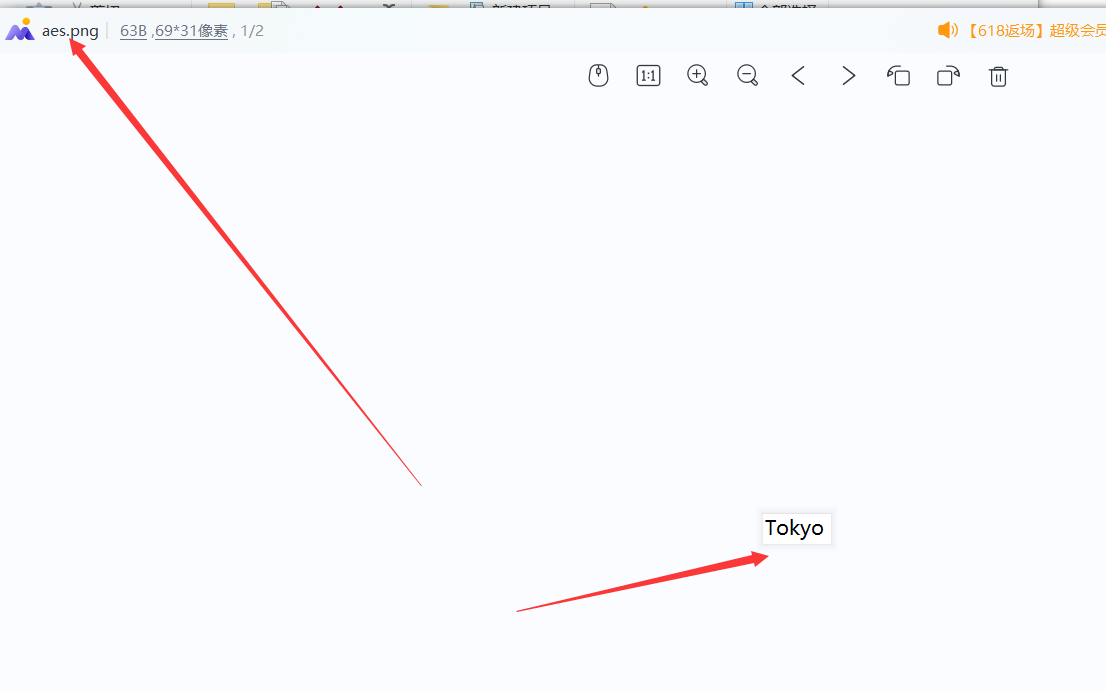
1、根据文件名提示找到一处base64:
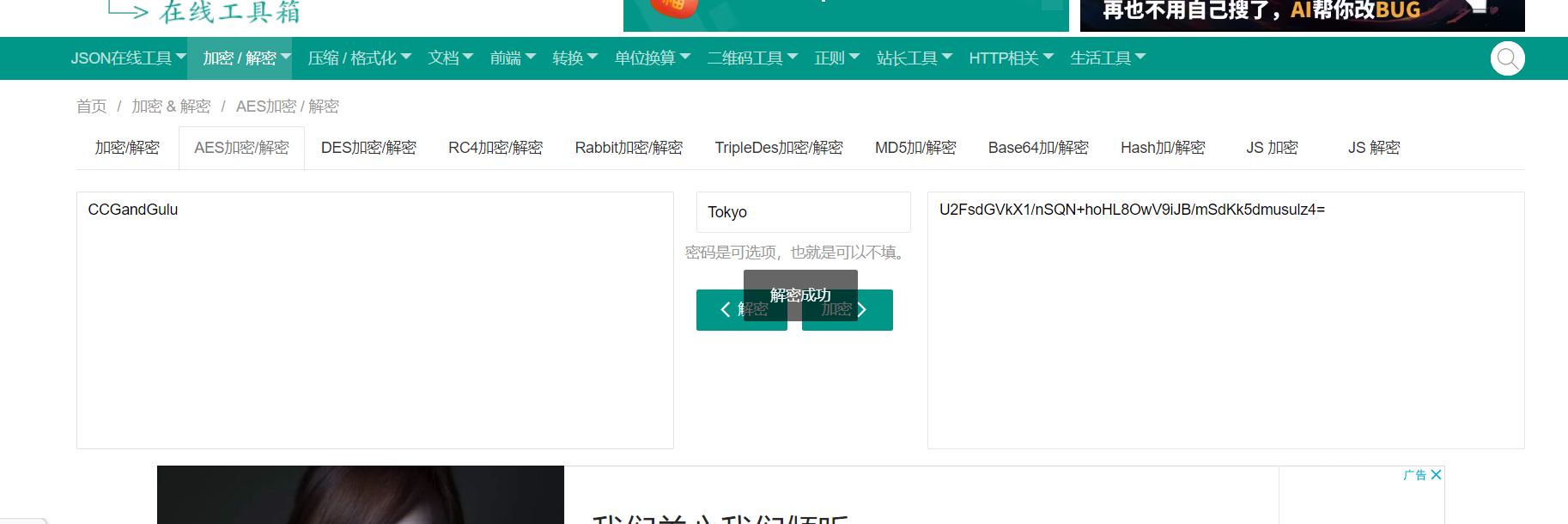
U2FsdGVkX1/nSQN+hoHL8OwV9iJB/mSdKk5dmusulz4=
2、binWarlk图片
得到:
AES解密得到:
CCGandGulu
这种属于base64加盐+AES,不用管它
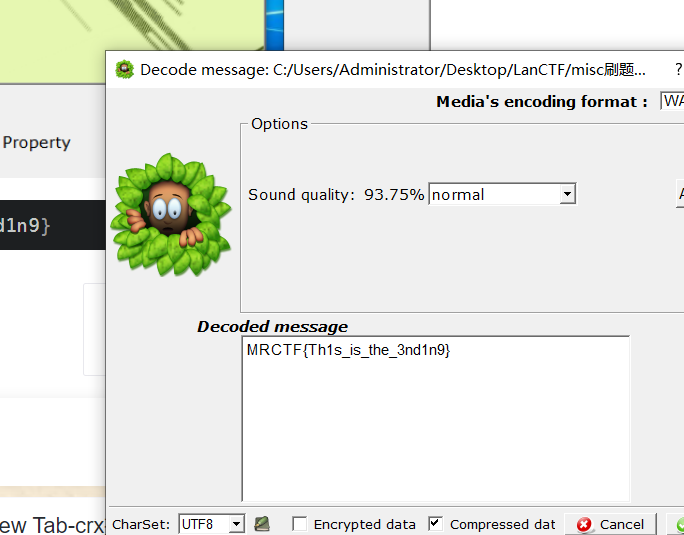
silenteye解密得到flag
flag{Th1s_is_the_3nd1n9}
十五、二维码
不太会
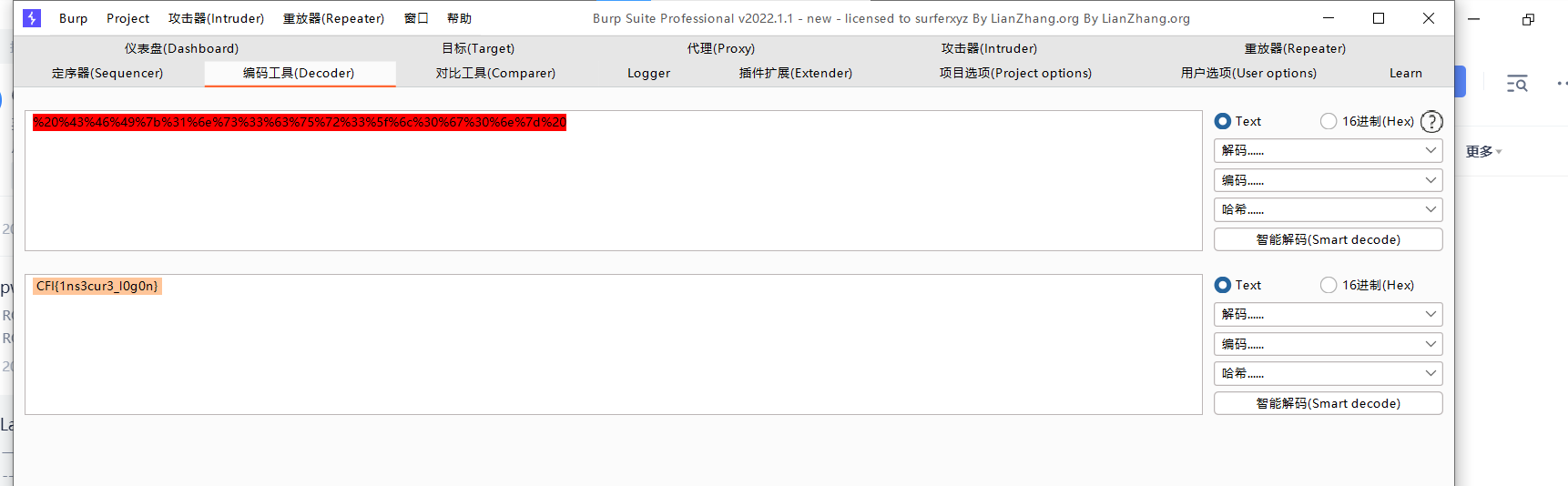
十六、[CFI-CTF 2018]webLogon capture
flag{1ns3cur3_l0g0n}
秒杀
十七、Beautiful_Side
1、formost分离
2、二维码在线补全
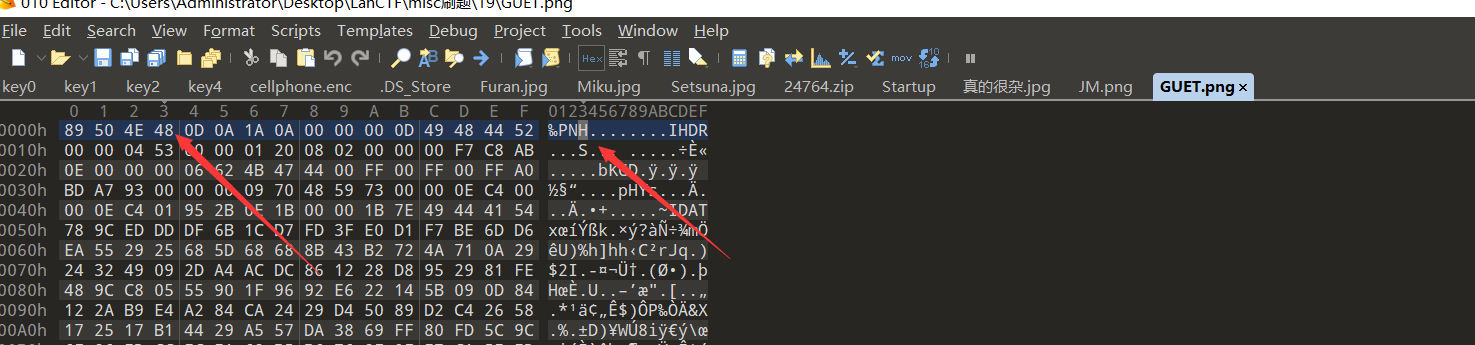
十八、[GUET-CTF2019]soul sipse
1、Steghide无密码分离
2、修复png
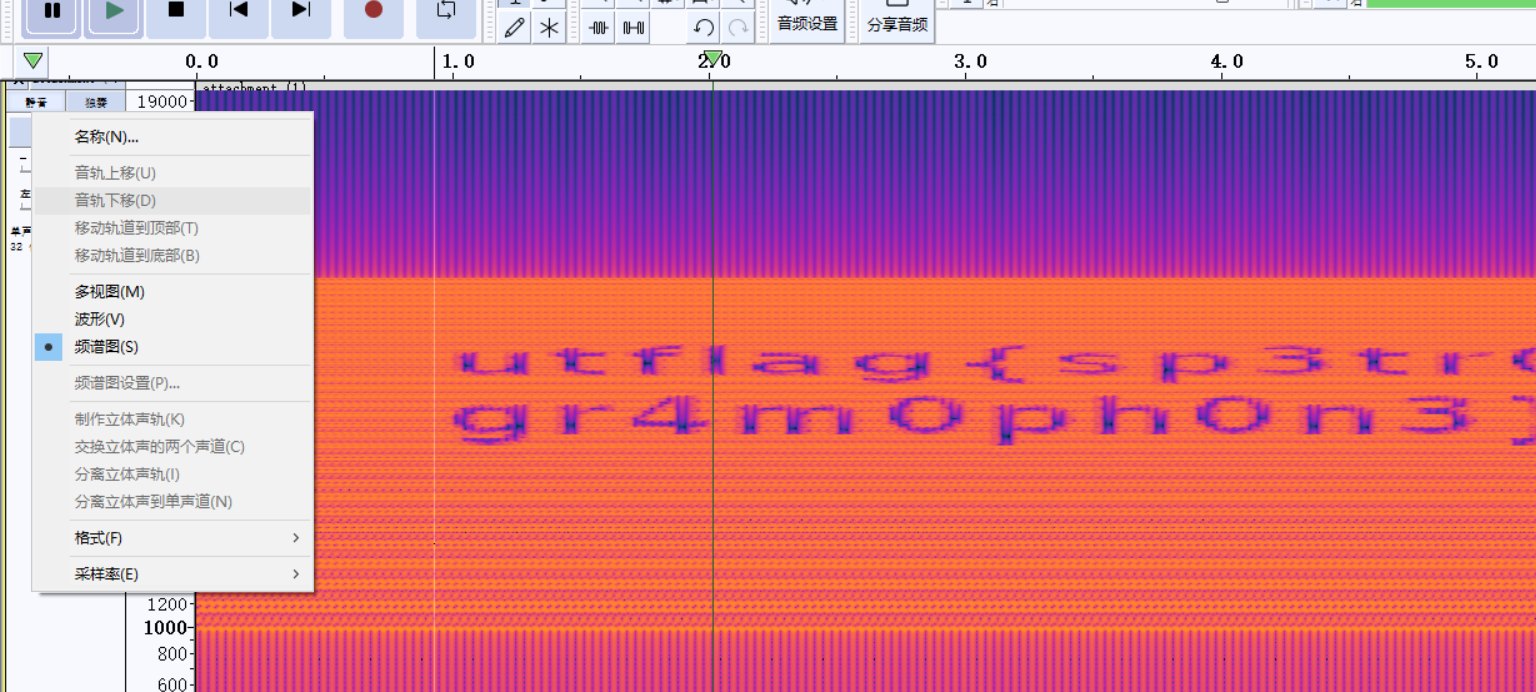
十九、[UTCTF2020]spectogram
义眼顶真
flag{sp3tr0gr4m0ph0n3}
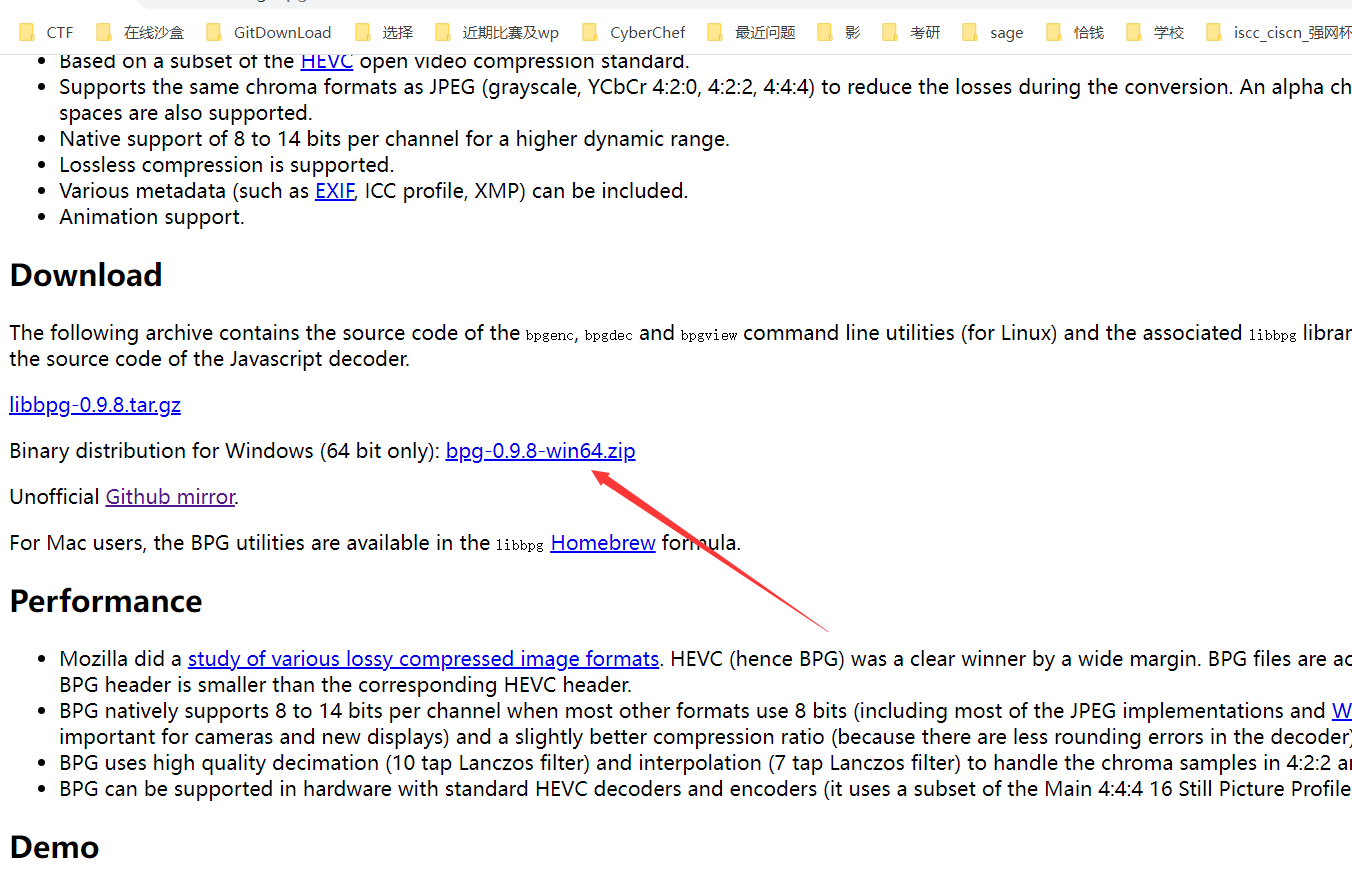
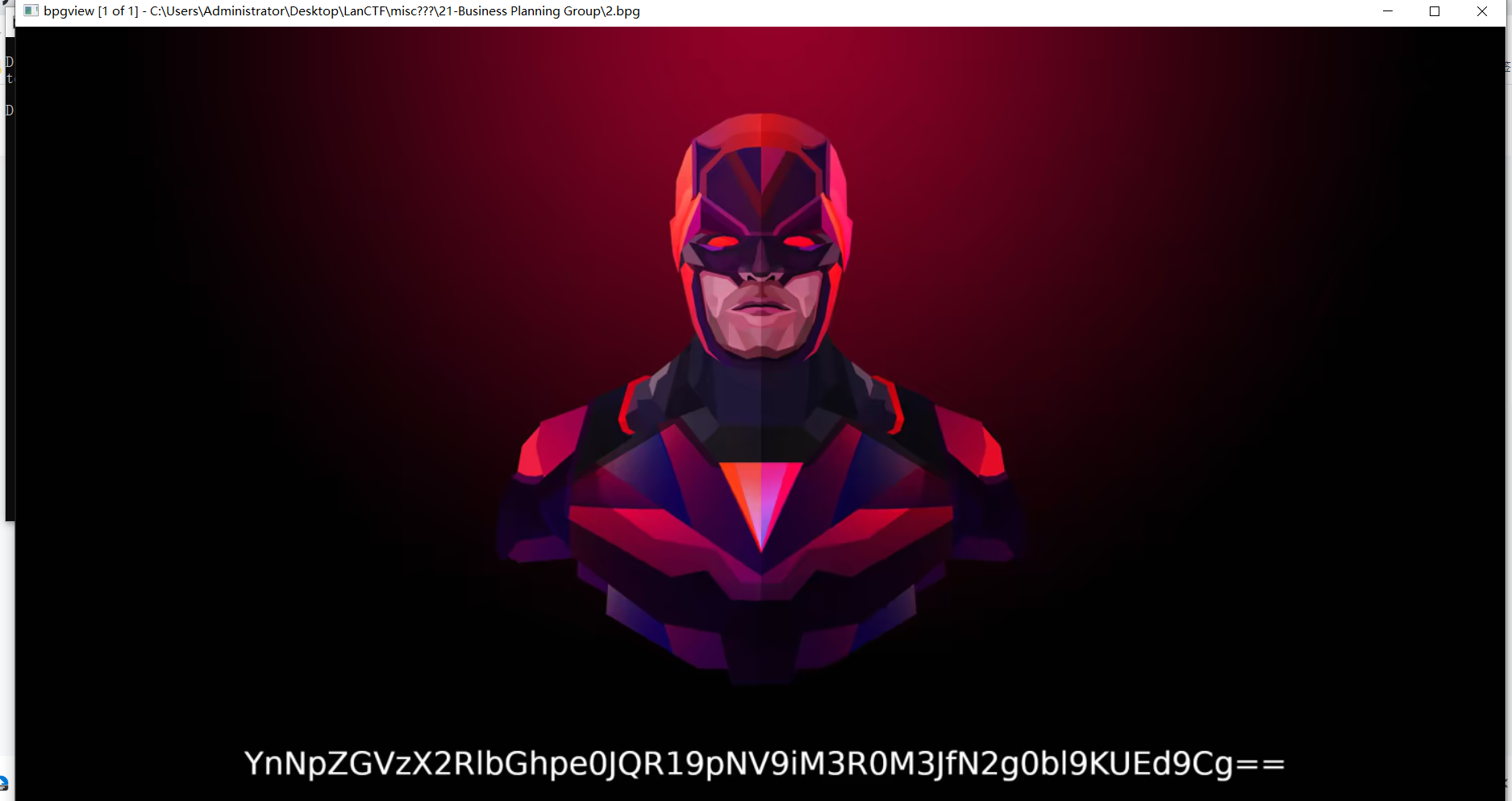
二十、Business Planning Group
010Editor打开,发现其隐藏了一个bpg文件
在 https://bellard.org/bpg/ 下载这个:
查看即可:
.\bpgview.exe .\2.bpg
base64解码得:
flag{BPG_i5_b3tt3r_7h4n_JPG}
二十一、湖南省赛Findme
1、修复名字
2、修复宽高
得到:
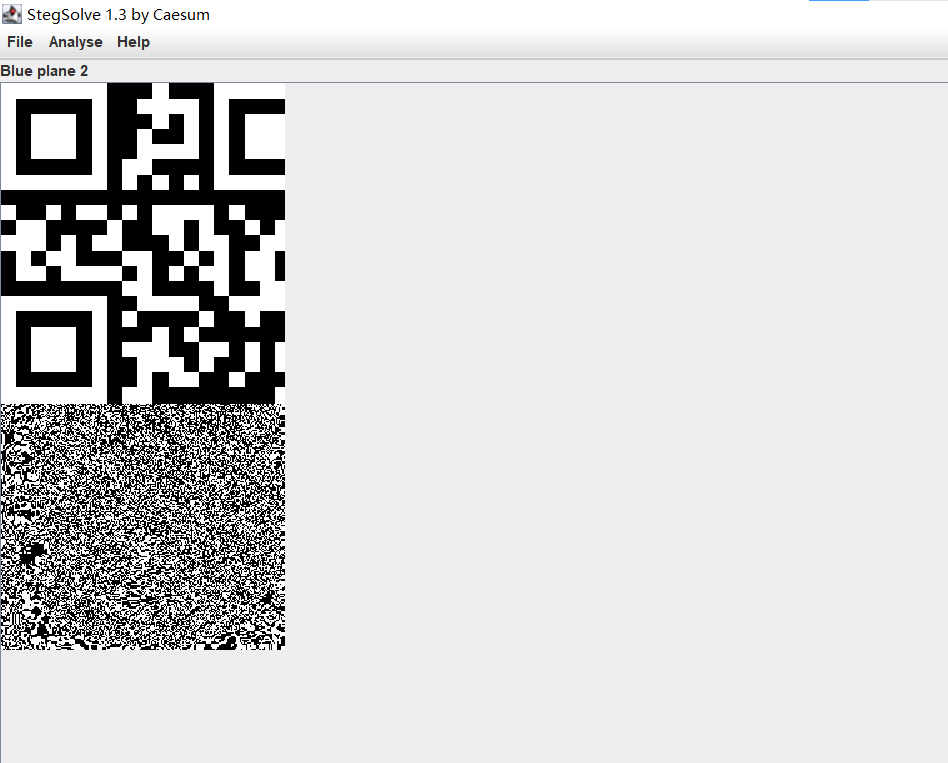
3、使用StegSlove在Blue2行道发现二维码
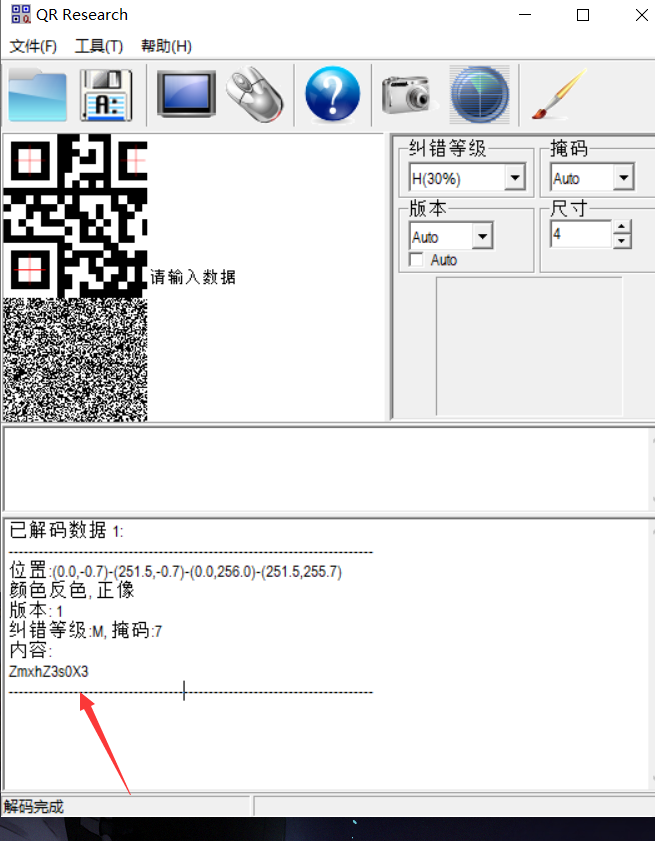
即: ZmxhZ3s0X3
4、2.png
虽然其写着7z标致,但其结构和7z压缩包完全不一样,倒是像zip,我们尝试把里面的7z全部换成PK
脚本如下
可以得到:
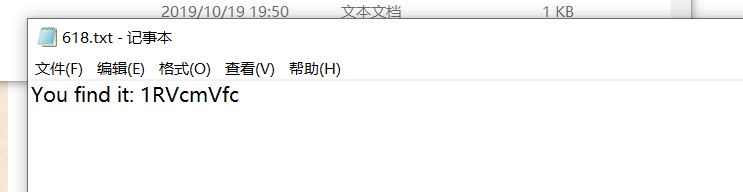
在618.txt中发现:
1RVcmVfc
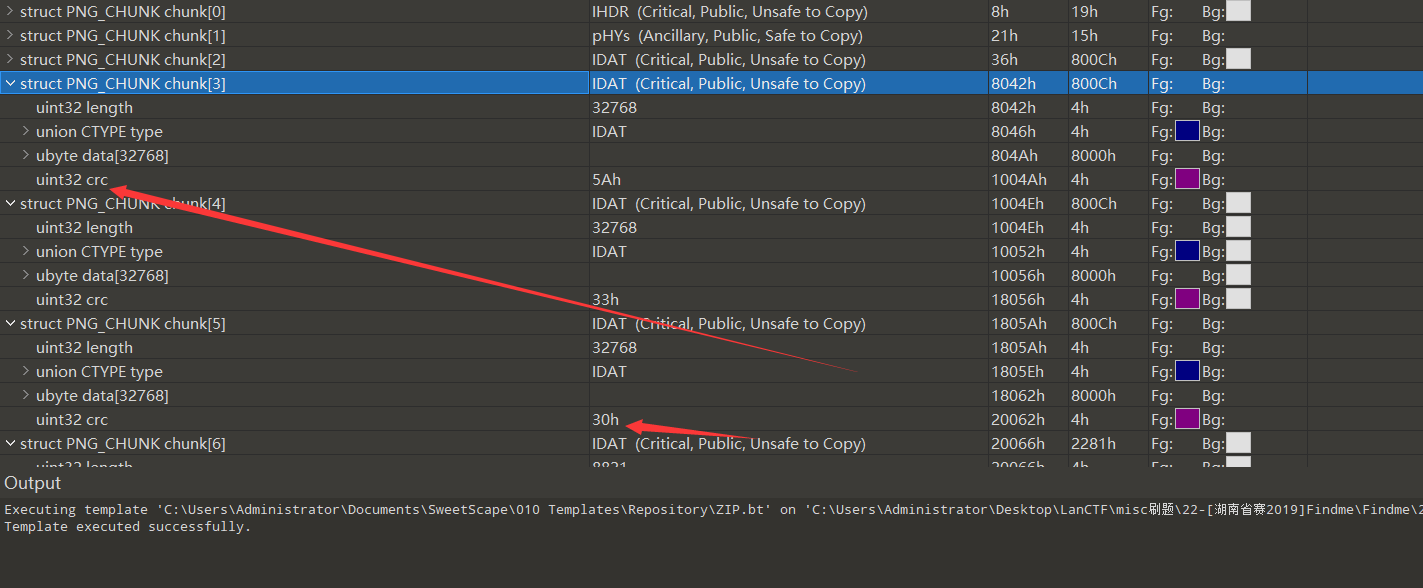
5、3.png
crc的值有些端倪
提取得到:
3RlZ30=
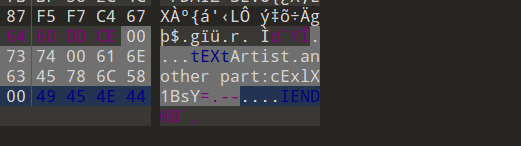
6、4.png
cExlX1BsY
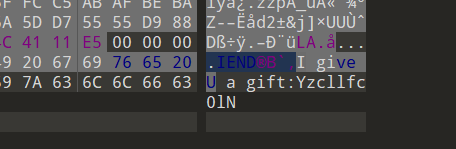
7、5.png
Yzcllfc0lN
8、拿到flag
按照 15423的顺序拼接flag
ZmxhZ3s0X3Yzcllfc0lNcExlX1BsY1RVcmVfc3RlZ30=
flag{4_v3rY_sIMpLe_PlcTUre_steg}
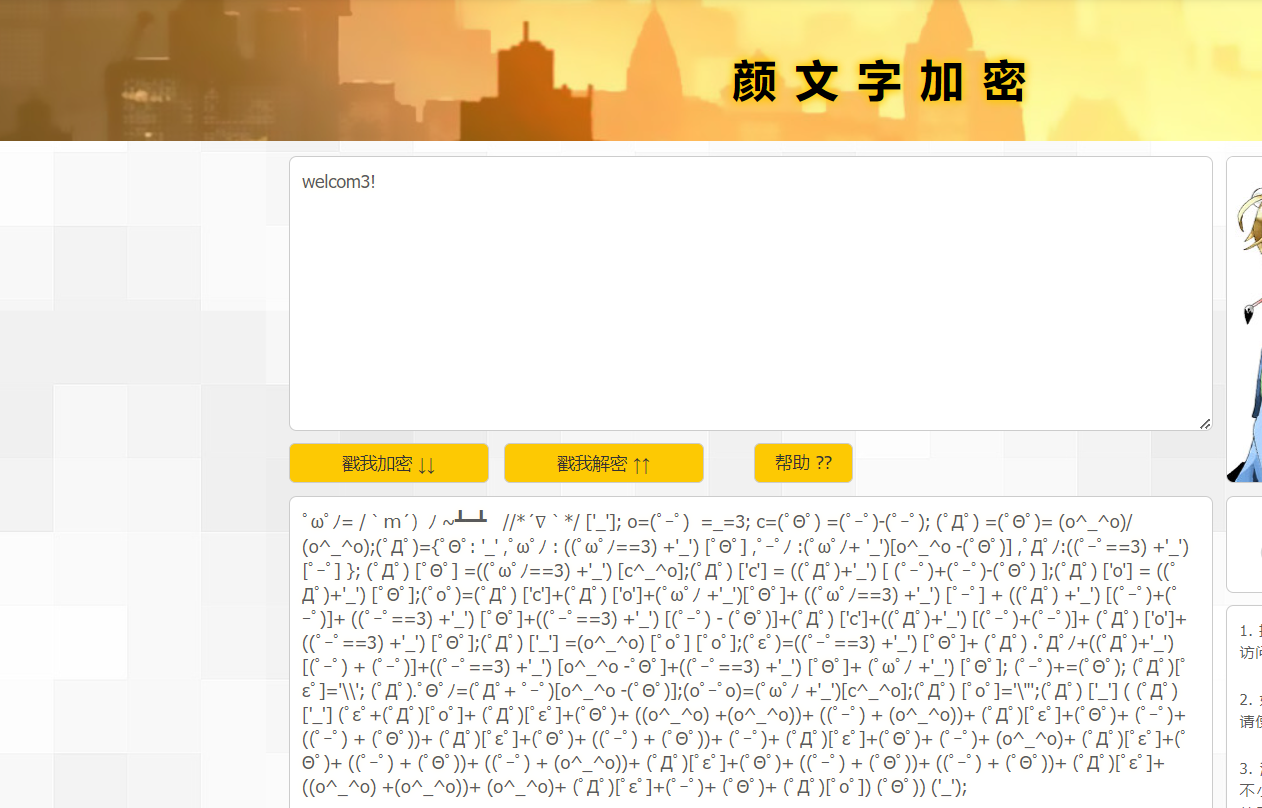
二十二、[ACTF新生赛2020]剑龙
1、颜文字解密
welcom3!
2、hh.jpg隐写
steghide extract -sf ./hh.jpg
key是 welcom3!
得到
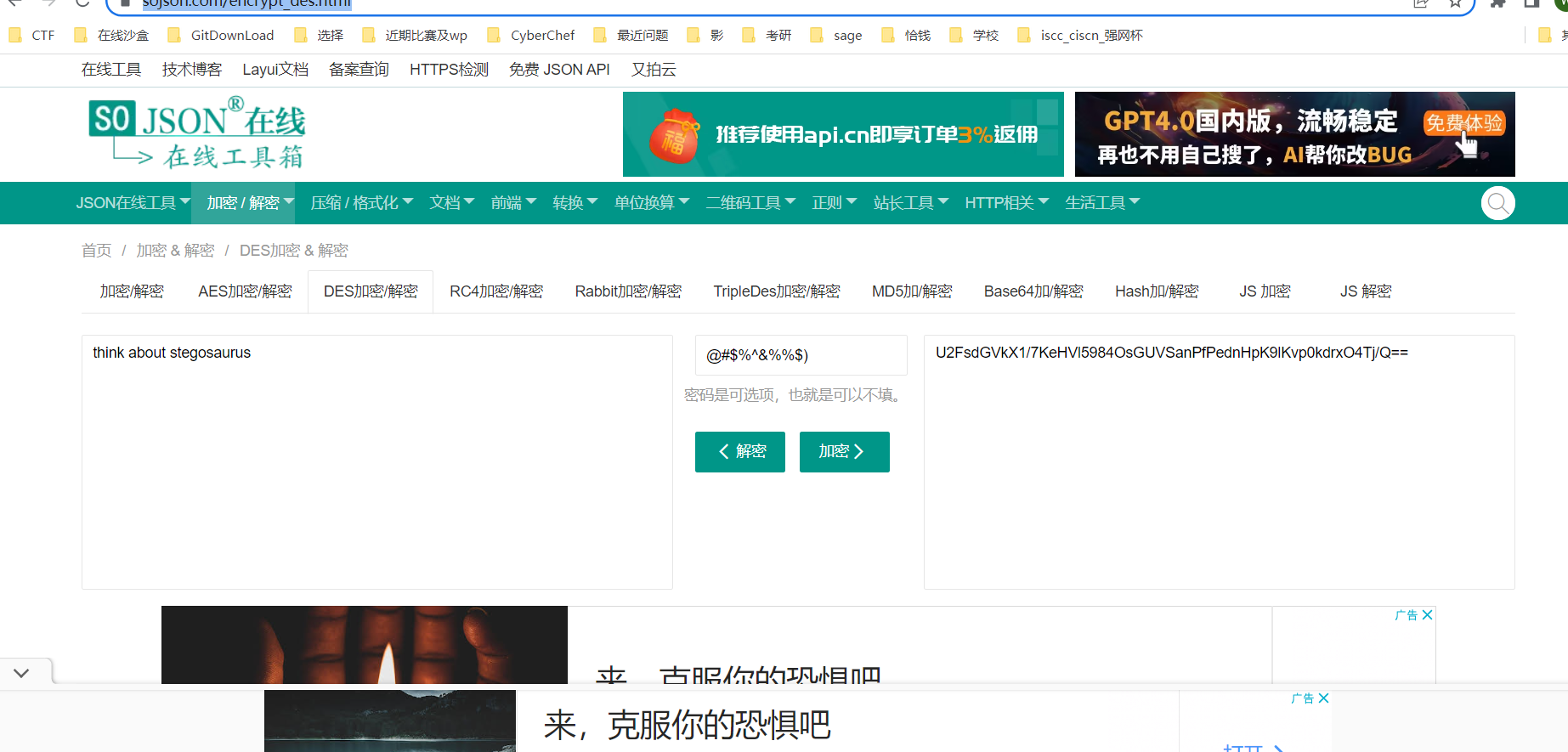
U2FsdGVkX1/7KeHVl5984OsGUVSanPfPednHpK9lKvp0kdrxO4Tj/Q==
3、DES解密
https://www.sojson.com/encrypt_des.html
think about stegosaurus
4、在github上使用stegosaurus
python3 stegosaurus.py -x O_O.pyc
得到flag:
flag{3teg0Sauru3_!1}
二十三、我爱Linux
1、改标志
没啥用
2、dump冗余字段
3、使用文件识别工具Trld识别
注意是下载可执行文件和数据
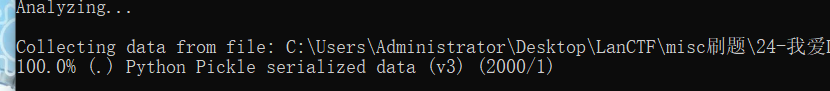
4、识别
Python Pickle序列号数据
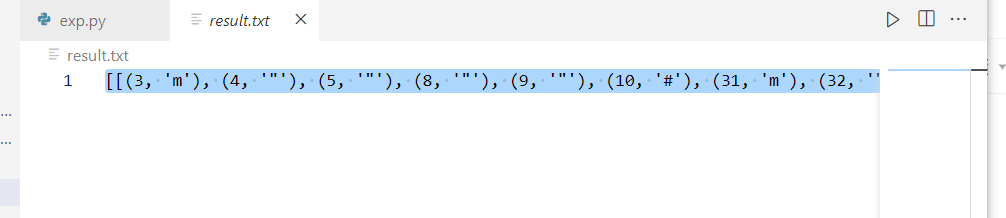
5、脚本转化
__EOF__

本文作者:_TLSN
本文链接:https://www.cnblogs.com/lordtianqiyi/articles/17591672.html
关于博主:评论和私信会在第一时间回复。或者直接私信我。
版权声明:本博客所有文章除特别声明外,均采用 BY-NC-SA 许可协议。转载请注明出处!
声援博主:如果您觉得文章对您有帮助,可以点击文章右下角【推荐】一下。您的鼓励是博主的最大动力!
本文链接:https://www.cnblogs.com/lordtianqiyi/articles/17591672.html
关于博主:评论和私信会在第一时间回复。或者直接私信我。
版权声明:本博客所有文章除特别声明外,均采用 BY-NC-SA 许可协议。转载请注明出处!
声援博主:如果您觉得文章对您有帮助,可以点击文章右下角【推荐】一下。您的鼓励是博主的最大动力!













【推荐】国内首个AI IDE,深度理解中文开发场景,立即下载体验Trae
【推荐】编程新体验,更懂你的AI,立即体验豆包MarsCode编程助手
【推荐】抖音旗下AI助手豆包,你的智能百科全书,全免费不限次数
【推荐】轻量又高性能的 SSH 工具 IShell:AI 加持,快人一步
· AI与.NET技术实操系列:基于图像分类模型对图像进行分类
· go语言实现终端里的倒计时
· 如何编写易于单元测试的代码
· 10年+ .NET Coder 心语,封装的思维:从隐藏、稳定开始理解其本质意义
· .NET Core 中如何实现缓存的预热?
· 分享一个免费、快速、无限量使用的满血 DeepSeek R1 模型,支持深度思考和联网搜索!
· 基于 Docker 搭建 FRP 内网穿透开源项目(很简单哒)
· 25岁的心里话
· ollama系列01:轻松3步本地部署deepseek,普通电脑可用
· 按钮权限的设计及实现