N1CTF Junior easy-rs & rust逆向
rust逆向题,看似逻辑复杂,细细分析后会发现逻辑不算太难
一、程序逻辑
1、输入格式检查
地址为 00005555555612FE(基址为0x555555554000)地方检查了输入的长度,不为63则退出程序
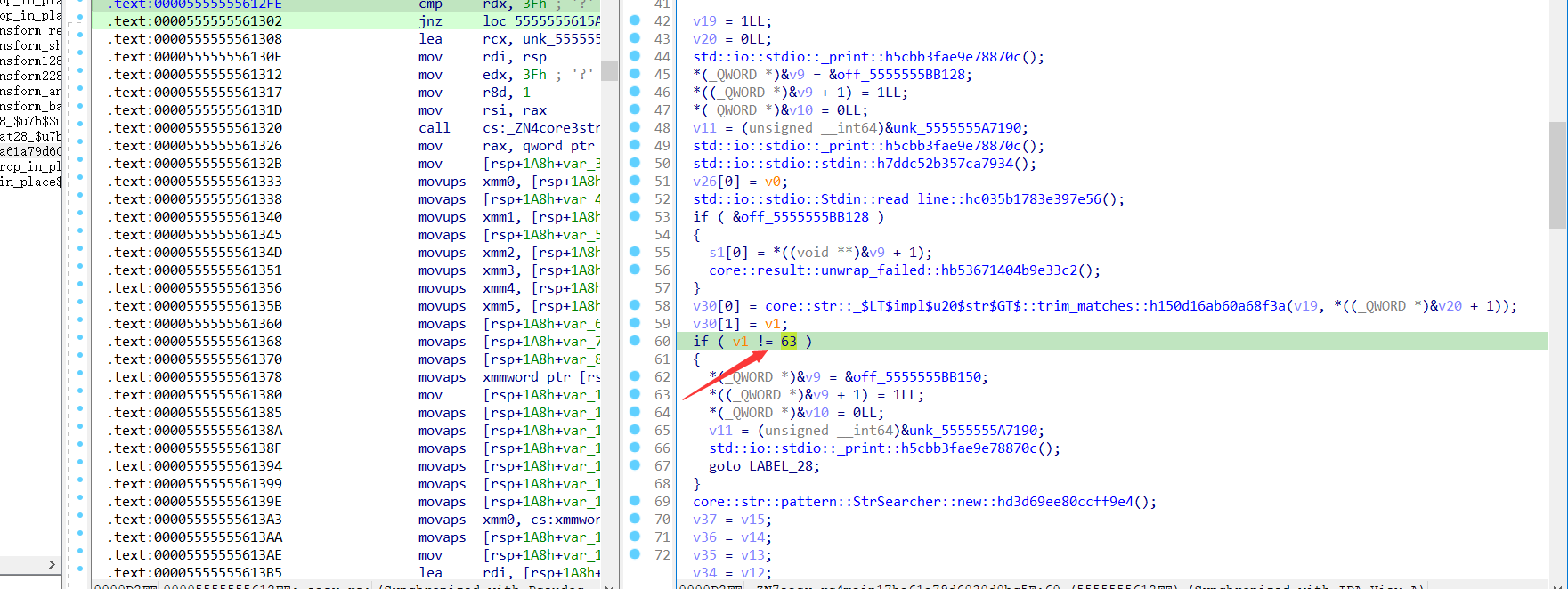
在地址为00005555555613C0(基址为0x555555554000)上的函数,其功能是检测"-"的个数,不等于8则异常退出
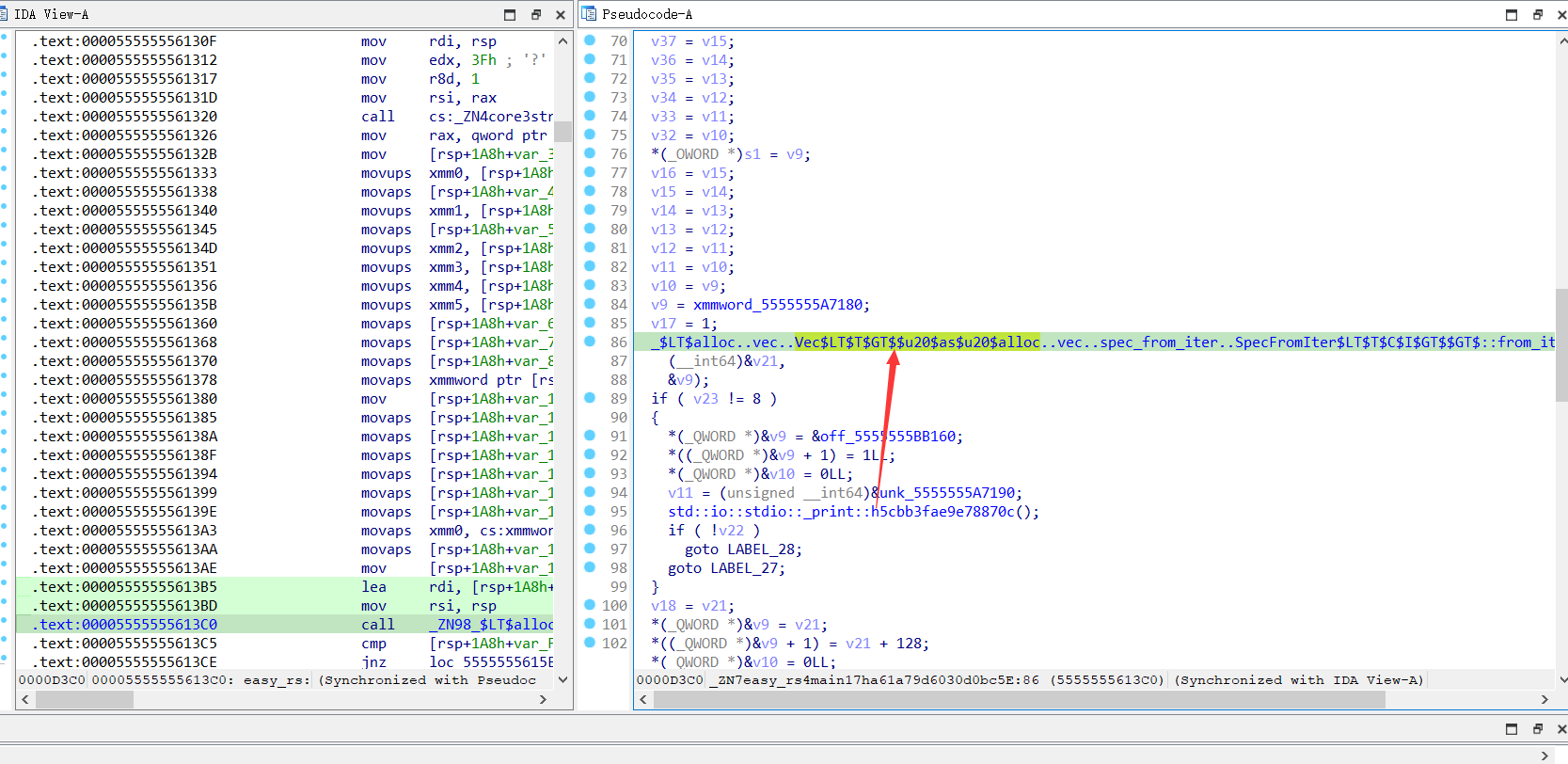
我们猜测输入的形式是类似 xxxxxxx-xxxxxxx-xxxxxxx-xxxxxxx-xxxxxxx-xxxxxxx-xxxxxxx-xxxxxxx
但不太清楚两个"-"之间的字符个数
在后面的调试的过程中,发现输入的形式必须是这样的 xxxxxxx-xxxxxxx-xxxxxxx-xxxxxxx-xxxxxxx-xxxxxxx-xxxxxxx-xxxxxxx
不然最后得到的密文不会有2055个字节大小
2、分析加密函数
加密函数大体由这些构成
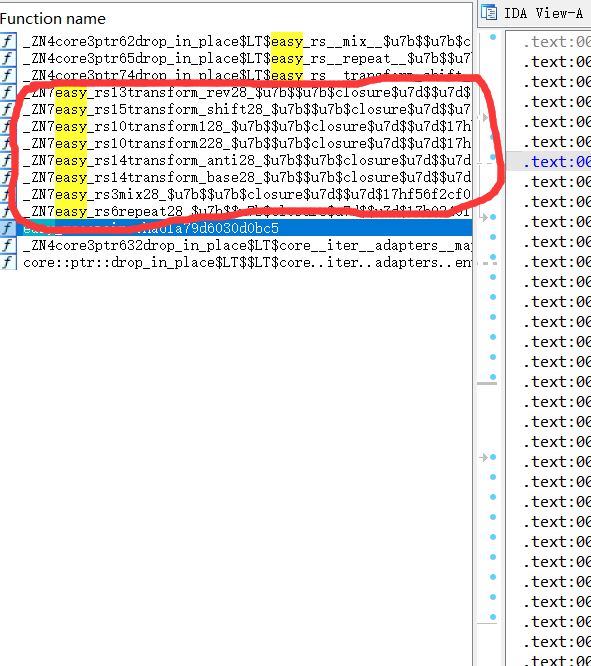
每个函数上都下好断点,之后开始调试
# IDAPython脚本 import idaapi breakpoints = [ 0x0005555555607E0, 0x000555555560F50, 0x000555555560ED0, 0x000555555560560, 0x000555555560C40, 0x000555555560990 ] for i in range(len(breakpoints)): idaapi.add_bpt(breakpoints[i])
经过调试发现程序加密流程大致是这样的:
程序把输入按“-”分组,共分8组
每组输入都执行5次以下加密流程
transform1 => transform2 => transform_base => transform_anti => transform_shift => transform_base => transform_anti => transform_rev
然后把每组最后的结果分别进行 transform_base 加密,再用“_”连接起来
二、分析加密函数
1、transform1 函数
其实现的功能是异或一个值,不同组异或的值不同,相同组异或的值相同,从第0组到第7组分别异或 0,1,2,3,4,5,6,7
transform1_key = [0,1,2,3,4,5,6,7] def transform1(inp,key): return B_xor(inp,uch2b(key)*len(inp))
2、transform2 函数
这个函数分析起来是有一些复杂的,由于每组要执行5轮加密函数,而transform2函数每次被执行的时候,其控制流都不相同。让人有点头大
我们不妨枚举分析,毕竟 只有5种情况。
在枚举下,加密逻辑就十分清晰了
大致如下:
transform2_key = [0xa, 0xb, 0x8, 0x9, 0xe, 0xf, 0xc, 0xd] def transform2(inp,key,ans): lenn = len(inp) v8 = [] if ans == 0: # len(inp) == 7 a2 = 0 for i in range(3): v8.append(inp[i]^(key + (a2 & 1))) a2 += 1 v31 = key+1 v32 = key v8.append(v31 ^ inp[3]) v8.append(v32 ^ inp[4]) v8.append(v31 ^ inp[5]) v8.append(v32 ^ inp[6]) return bytes(v8) elif ans == 1: # len(inp) == 0x10 v31 = key v32 = key + 1 for i in range(0,4): v8.append(v31 ^ inp[i*4]) v8.append(v32 ^ inp[i*4+1]) v8.append(v31 ^ inp[i*4+2]) v8.append(v32 ^ inp[i*4+3]) return bytes(v8) elif ans == 2: # len(cip) = 0x20 v8 = b"" float_expand = pack("B",key) * 16 si128 = lll2b(0x1000100010001000100010001000100) v8 += B_xor(inp[0:16],B_add(float_expand,si128)) v8 += B_xor(inp[16:32],B_add(float_expand,si128)) return bytes(v8) elif ans == 3: # len(cip) == 0x3c v8 = b"" float_expand = pack("B",key) * 16 si128 = lll2b(0x1000100010001000100010001000100) v8 += B_xor(inp[0:16],B_add(float_expand,si128)) v8 += B_xor(inp[16:32],B_add(float_expand,si128)) v31 = key v32 = key+1 for i in range(8,15): v8 += uch2b(v31 ^ inp[i*4]) v8 += uch2b(v32 ^ inp[i*4+1]) v8 += uch2b(v31 ^ inp[i*4+2]) v8 += uch2b(v32 ^ inp[i*4+3]) return v8 elif ans == 4: # len(cip) == 0x6c v8 = b"" float_expand = pack("B",key) * 16 v14 = lll2b(0xF0E0D0C0B0A09080706050403020100) v16 = lll2b(0x1010101010101010101010101010101) v17 = lll2b(0x40404040404040404040404040404040) val0 = B_xor(inp[0:16],B_add(B_and(v14,v16),float_expand)) val1 = B_xor(inp[16:32],B_add(B_and(v14,v16),float_expand)) val2 = B_xor(inp[32:48],B_add(B_and(v14,v16),float_expand)) val3 = B_xor(inp[48:64],B_add(B_and(v14,v16),float_expand)) si128 = B_and(v14,v16) val4 = B_xor(inp[64:80],B_add(float_expand,si128)) val5 = B_xor(inp[80:96],B_add(float_expand,si128)) v31 = key v32 = key+1 v8 += val0 + val1 + val2 + val3 + val4 + val5 for i in range(24,27): v8 += uch2b(v31 ^ inp[i*4]) v8 += uch2b(v32 ^ inp[i*4+1]) v8 += uch2b(v31 ^ inp[i*4+2]) v8 += uch2b(v32 ^ inp[i*4+3]) return v8
这个函数也是,不同组有不同的key
3、transform_base
这个函数每轮加密会执行两次,第一次是base64换表加密,第二次是正常的base64加密
功能如下:
def transform_base(inp,ans): if ans % 2 == 0: string1 = "+/ABCDEFGHIJKLMNOPQRSTUVWXYZabcdefghijklmnopqrstuvwxyz0123456789" string2 = "ABCDEFGHIJKLMNOPQRSTUVWXYZabcdefghijklmnopqrstuvwxyz0123456789+/" return ((str(base64.b64encode(inp)).translate(str.maketrans(string2,string1)))[2:-1]).encode() else: return base64.b64encode(inp)
4、transform_anti
这个函数每轮加密也是被执行了两次,第一次执行key是0x29,第二次是0xc5
这个函数内部有反调试
猜测反调试应该是procfs::process::Process::status::hcb60ea34dc13cf4b 这个函数,他检测有无被调试并修改了anti_val这个值
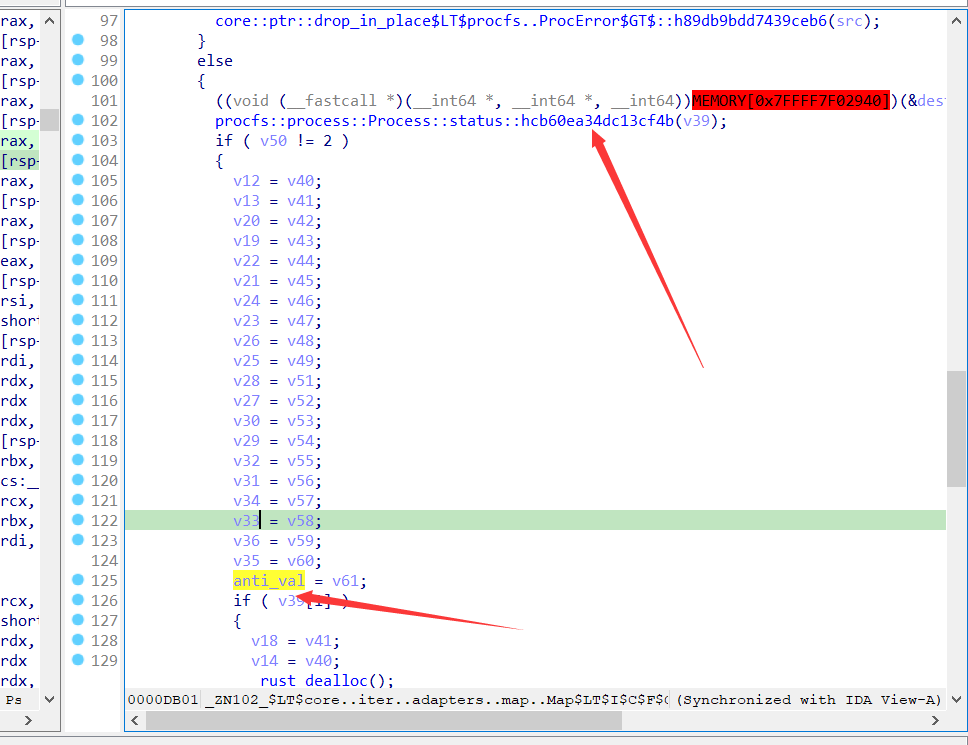
用frida hook一下,发现这个值应该为0
''' frida脚本 ''' import frida import time import sys Hook_addr = 0x000555555561B34 jscode = ''' Interceptor.attach(ptr("%s"), { onEnter: function(args) { var t = this.context.rax console.log(t); } }); '''% Hook_addr local = frida.get_local_device() # pid = local.spawn(r"fridaaaa.exe") pid = local.spawn(r"./easy-rs") local.resume(pid) time.sleep(1) # Without it Java.perform silently fails session = local.attach(pid) script = session.create_script(jscode) script.load() sys.stdin.read()
坑点拆除后,加密逻辑就很清晰了:
transform_anti_key = (0x29,0xc5) def transform_anti(inp,key1): key2 = 0 # 0x6f #0 000555555561D3D # 0xAD # 用frida获取其值是0 out = b"" for i in range(len(inp)): if i&1 != 0: v8 = inp[i]^(key1+1) else: v11 = inp[i]^key1 v8 = key2 ^ v11 out += pack("B",v8) return out
5、transform_shift
这个函数基本上啥功能都没实现,直接忽略就行
6、transform_rev
闻名知意,反转字符串
知道这些功能后,我们很容易写出解密脚本
三、exp
from struct import pack,unpack import base64 def pt(p): print(p) def uch2b(m): return pack("B",m) def B_xor(m1,m2): return bytes([x^y for x,y in zip(m1,m2)]) def B_and(m1,m2): return bytes([x&y for x,y in zip(m1,m2)]) def B_add(m1,m2): return bytes([x+y for x,y in zip(m1,m2)]) def transform_rev(m): return m[::-1] def lll2b(m): res = [] n = m while(n): res.append(n % 0x100) n //= 0x100 return bytes(res) transform_anti_key = (0x29,0xc5) def transform_anti(inp,key1): key2 = 0 # 0x6f #0 000555555561D3D # 0xAD # 用frida获取其值是0 out = b"" for i in range(len(inp)): if i&1 != 0: v8 = inp[i]^(key1+1) else: v11 = inp[i]^key1 v8 = key2 ^ v11 out += pack("B",v8) return out def transform_base(inp,ans): if ans % 2 == 0: string1 = "+/ABCDEFGHIJKLMNOPQRSTUVWXYZabcdefghijklmnopqrstuvwxyz0123456789" string2 = "ABCDEFGHIJKLMNOPQRSTUVWXYZabcdefghijklmnopqrstuvwxyz0123456789+/" return ((str(base64.b64encode(inp)).translate(str.maketrans(string2,string1)))[2:-1]).encode() else: return base64.b64encode(inp) def de_transform_base(inp,ans): if ans % 2 == 0: string1 = "+/ABCDEFGHIJKLMNOPQRSTUVWXYZabcdefghijklmnopqrstuvwxyz0123456789" string2 = "ABCDEFGHIJKLMNOPQRSTUVWXYZabcdefghijklmnopqrstuvwxyz0123456789+/" return base64.b64decode(inp.decode().translate(str.maketrans(string1,string2))) else: return base64.b64decode(inp) def transform_shift(m): # nothing return m transform2_key = [0xa, 0xb, 0x8, 0x9, 0xe, 0xf, 0xc, 0xd] def transform2(inp,key,ans): lenn = len(inp) v8 = [] if ans == 0: # len(inp) == 7 a2 = 0 for i in range(3): v8.append(inp[i]^(key + (a2 & 1))) a2 += 1 v31 = key+1 v32 = key v8.append(v31 ^ inp[3]) v8.append(v32 ^ inp[4]) v8.append(v31 ^ inp[5]) v8.append(v32 ^ inp[6]) return bytes(v8) elif ans == 1: # len(inp) == 0x10 v31 = key v32 = key + 1 for i in range(0,4): v8.append(v31 ^ inp[i*4]) v8.append(v32 ^ inp[i*4+1]) v8.append(v31 ^ inp[i*4+2]) v8.append(v32 ^ inp[i*4+3]) return bytes(v8) elif ans == 2: # len(cip) = 0x20 v8 = b"" float_expand = pack("B",key) * 16 si128 = lll2b(0x1000100010001000100010001000100) v8 += B_xor(inp[0:16],B_add(float_expand,si128)) v8 += B_xor(inp[16:32],B_add(float_expand,si128)) return bytes(v8) elif ans == 3: # len(cip) == 0x3c v8 = b"" float_expand = pack("B",key) * 16 si128 = lll2b(0x1000100010001000100010001000100) v8 += B_xor(inp[0:16],B_add(float_expand,si128)) v8 += B_xor(inp[16:32],B_add(float_expand,si128)) v31 = key v32 = key+1 for i in range(8,15): v8 += uch2b(v31 ^ inp[i*4]) v8 += uch2b(v32 ^ inp[i*4+1]) v8 += uch2b(v31 ^ inp[i*4+2]) v8 += uch2b(v32 ^ inp[i*4+3]) return v8 elif ans == 4: # len(cip) == 0x6c v8 = b"" float_expand = pack("B",key) * 16 v14 = lll2b(0xF0E0D0C0B0A09080706050403020100) v16 = lll2b(0x1010101010101010101010101010101) v17 = lll2b(0x40404040404040404040404040404040) val0 = B_xor(inp[0:16],B_add(B_and(v14,v16),float_expand)) val1 = B_xor(inp[16:32],B_add(B_and(v14,v16),float_expand)) val2 = B_xor(inp[32:48],B_add(B_and(v14,v16),float_expand)) val3 = B_xor(inp[48:64],B_add(B_and(v14,v16),float_expand)) si128 = B_and(v14,v16) val4 = B_xor(inp[64:80],B_add(float_expand,si128)) val5 = B_xor(inp[80:96],B_add(float_expand,si128)) v31 = key v32 = key+1 v8 += val0 + val1 + val2 + val3 + val4 + val5 for i in range(24,27): v8 += uch2b(v31 ^ inp[i*4]) v8 += uch2b(v32 ^ inp[i*4+1]) v8 += uch2b(v31 ^ inp[i*4+2]) v8 += uch2b(v32 ^ inp[i*4+3]) return v8 transform1_key = [0,1,2,3,4,5,6,7] def transform1(inp,key): return B_xor(inp,uch2b(key)*len(inp)) def encry(Allcip): global transform_anti_key,transform1_key,transform2_key t1 = t2 = t3 = t4 = t5 = t6 = t7 = ming = 0 fin = b"" def debug(): pt(t1) pt(t2) pt(t3) pt(t4) pt(t5) pt(t6) pt(t7) pt(ming) for k in range(8): cip = Allcip.split(b"-")[k] for i in range(5): # 循环后进行base64加密 t1 = transform1(cip,transform1_key[k]) t2 = transform2(t1,transform2_key[k],i) t3 = transform_base(t2,0) t4 = transform_anti(t3,transform_anti_key[0]) t5 = transform_shift(t4) t6 = transform_base(t5,1) t7 = transform_anti(t6,transform_anti_key[1]) ming = transform_rev(t7) cip = ming[:] # debug() fin += transform_base(ming,1) + b"_" return fin[:-1] def decry(All_ming): flag = b"" global transform_anti_key,transform1_key,transform2_key for k in range(8): ming = All_ming.split(b"_")[k] ming = de_transform_base(ming,1) for i in range(4,-1,-1): t7 = transform_rev(ming) t6 = transform_anti(t7,transform_anti_key[1]) t5 = de_transform_base(t6,1) t4 = transform_shift(t5) t3 = transform_anti(t4,transform_anti_key[0]) t2 = de_transform_base(t3,0) t1 = transform2(t2,transform2_key[k],i) cip = transform1(t1,transform1_key[k]) ming = cip[:] flag += cip + b"-" return flag[:-1] if __name__ == "__main__": test_Allcip = b"0123456-abcdefg-hijklmn-opqrstu-ABCDEFG-HIJKLMN-OPQRSTU-7778889" test_cip = encry(test_Allcip) assert test_cip == b"sIO+gIv8qJKvh76C8a2Ul4vw9peEsa2XnICUpIGP9JKI8K2RgPSUkqCq96fyj4GRofCQl4W9k4Ksk62co6mUlKOPrZyFh5OAg5eTpKf0q5exh56Xi7GTjZzxhJeji6iU/5/2l4K9g6SOg4OjoZP2l6efg5eE/JSdo4iDjfGPq5K89JSCo4irnb+HroD+ra6RqLX3gIOxqp2JtYCXjY+okaeAlKeAqYGmoJytkaHwvpHpqa6mhbWUlIP8raaB8PaN_hICunZatgJyvh76k/vCtlIuH9Zectaido732p5SUk5eigPaAgfytnbGxqqDyoYOR6Z+tnJaPgaO/j62Xo/CEl62P9peLi6uSg5eDgq30npSSrfWciY+OnLz8k5ahqb6XjJ/2l4W9g6b/g/amhY+rkpafrZyXqqqRvI+DjZ+MqJe89K6mlKKrl7/w9qT+l62Ukqm+gIPwrZa8h76Nqam+l6WpkKeLvYSCo6Gtn6f0jpHph6umifyqlKy9k6C19PWN_sIO+gIv8qJKvh76C8a2Ul4vw9peEsa2XnICUpIGP9JKI8K2RgPSUkqCq96eiooSArPCQl4W9k4Cvk4Oc8q2UlI61rY2J8I6msouTkYn0kZeVoq6NgPCDnICHvqOUiKiUn72oppyHgaa88PaWo5f0kZyugJeXroGfn4itl/Kh9pKK9JSCo4yrlq+X9o2Ij5SXkoerjYS9qJaj8ZSUjY+okZKElKOc9IOmoJytkaHwvpHpqa6mhbWUlIP8raaB8PaN_toOukYupg6avh76n/vCTl4vw9pyW8I6goYeUl4mPgYC8taqNgIurlryLk5LyoZOU6fSEl4C1gKavj62ArK2UlLbwqp2Jj4Ggsoutn4WTk5LzvYGCgKmtlIOTg5exj4GAl/z1nJaHjpyf8ZOSgY+RnYGx9ZeD/KuSsYutl/709ZSvtaqmo/WRjbyP9qf+j6uUopCtkYGTrZaAj62XgfCukbCHqJyW9IOgp/SqnKeh9pGtn/acl4T3n7L8raani/WN_sIO+gIv8qJKvh76C8a2Ul4vw9peEsa2XnICUpIGP9JKI8K2RgPSUkqexgJKn9JGUqfD2nIKDrZ2nj62A8a2+kf7wgJ+Fg5OCg5etgrX0qJGhqb6NgLGTjZyAhIKArb6Xio+Tp4C9rZ2v8IOjo/CQnaeArpyXtoOcjvytnImPq5Khj62ciYurnb+HroCNqaqUgrWAn5S2qp2JtaqjgY+Bl5WAlKeBqaiUgIODnKf09JGfqa6mhbWUlIP8raaB8PaN_/4OunYefg6f/h4SC/vD2kratnpeEsZGArbWqp4mprpSWg/amn4uOoLyxqpzyoYOUsrWTgomhrZGOvZOktY+UnYCMk6OnjIGnspeDkaX1q5Sl/fWfiamRjYmHrZ219KiRh/yokYu9g5yyn62covGAlJWEgYKXiKiSp/CDjYCprY2pvfSmoq6rlq/8g4Kc9Y6RgYeBgoS9qJajpvajiamulPGXgYKWn4Omv/Cto6f09YKS/KicpIuDn7KPg5b+9PWN_sIO+gIv8qJKvh76C8a2Ul4vw9peEsa2XnICUpKOphICE8a2dhfyDo4CfrZyi9fSRrPD3poX8vpyOj62AtPSekr/0hIKJ8I6m/4+TlKOPqJG2qb6NgLGtkq+9g4Kirb6Xtp/2l4W9rZ2DqfeWoqKEgJfwqpyXkIOfn5CTjayLqI2/tfacha2RgqyX9o3pk62UlYS+gIStrZ2SgISkp/SolPODlKeBqaiUgIODnKf09JGfqa6mhbWUlIP8raaB8PaN_toOukYupg6avh76n/vCTl4vw9pyW8I6goYeUl4mPgYC8taqNgIurlryLk5LytfeRrPSUgpeIg6ank/aQjYurl5+frZyng5OAg5eDgoCTk5LzvYGCgK2DoLyDhJzy9IGAjI/2l4GHkY2DqZCSooyOgKWqkIKXtoGfvIuDjen09ZSxvfSmo6Krko6Tk42lppOXlaKEn5TxrZS/g4SSiam+l5KDlKOCj6uUo7WqnKeh9pGtn/acl4T3n7L8raani/WN" test_All_ming = b"sIO+gIv8qJKvh76C8a2Ul4vw9peEsa2XnICUpIGP9JKI8K2RgPSUkqCq96fyj4GRofCQl4W9k4Ksk62co6mUlKOPrZyFh5OAg5eTpKf0q5exh56Xi7GTjZzxhJeji6iU/5/2l4K9g6SOg4OjoZP2l6efg5eE/JSdo4iDjfGPq5K89JSCo4irnb+HroD+ra6RqLX3gIOxqp2JtYCXjY+okaeAlKeAqYGmoJytkaHwvpHpqa6mhbWUlIP8raaB8PaN_hICunZatgJyvh76k/vCtlIuH9Zectaido732p5SUk5eigPaAgfytnbGxqqDyoYOR6Z+tnJaPgaO/j62Xo/CEl62P9peLi6uSg5eDgq30npSSrfWciY+OnLz8k5ahqb6XjJ/2l4W9g6b/g/amhY+rkpafrZyXqqqRvI+DjZ+MqJe89K6mlKKrl7/w9qT+l62Ukqm+gIPwrZa8h76Nqam+l6WpkKeLvYSCo6Gtn6f0jpHph6umifyqlKy9k6C19PWN_sIO+gIv8qJKvh76C8a2Ul4vw9peEsa2XnICUpIGP9JKI8K2RgPSUkqCq96eiooSArPCQl4W9k4Cvk4Oc8q2UlI61rY2J8I6msouTkYn0kZeVoq6NgPCDnICHvqOUiKiUn72oppyHgaa88PaWo5f0kZyugJeXroGfn4itl/Kh9pKK9JSCo4yrlq+X9o2Ij5SXkoerjYS9qJaj8ZSUjY+okZKElKOc9IOmoJytkaHwvpHpqa6mhbWUlIP8raaB8PaN_toOukYupg6avh76n/vCTl4vw9pyW8I6goYeUl4mPgYC8taqNgIurlryLk5LyoZOU6fSEl4C1gKavj62ArK2UlLbwqp2Jj4Ggsoutn4WTk5LzvYGCgKmtlIOTg5exj4GAl/z1nJaHjpyf8ZOSgY+RnYGx9ZeD/KuSsYutl/709ZSvtaqmo/WRjbyP9qf+j6uUopCtkYGTrZaAj62XgfCukbCHqJyW9IOgp/SqnKeh9pGtn/acl4T3n7L8raani/WN_sIO+gIv8qJKvh76C8a2Ul4vw9peEsa2XnICUpIGP9JKI8K2RgPSUkqexgJKn9JGUqfD2nIKDrZ2nj62A8a2+kf7wgJ+Fg5OCg5etgrX0qJGhqb6NgLGTjZyAhIKArb6Xio+Tp4C9rZ2v8IOjo/CQnaeArpyXtoOcjvytnImPq5Khj62ciYurnb+HroCNqaqUgrWAn5S2qp2JtaqjgY+Bl5WAlKeBqaiUgIODnKf09JGfqa6mhbWUlIP8raaB8PaN_/4OunYefg6f/h4SC/vD2kratnpeEsZGArbWqp4mprpSWg/amn4uOoLyxqpzyoYOUsrWTgomhrZGOvZOktY+UnYCMk6OnjIGnspeDkaX1q5Sl/fWfiamRjYmHrZ219KiRh/yokYu9g5yyn62covGAlJWEgYKXiKiSp/CDjYCprY2pvfSmoq6rlq/8g4Kc9Y6RgYeBgoS9qJajpvajiamulPGXgYKWn4Omv/Cto6f09YKS/KicpIuDn7KPg5b+9PWN_sIO+gIv8qJKvh76C8a2Ul4vw9peEsa2XnICUpKOphICE8a2dhfyDo4CfrZyi9fSRrPD3poX8vpyOj62AtPSekr/0hIKJ8I6m/4+TlKOPqJG2qb6NgLGtkq+9g4Kirb6Xtp/2l4W9rZ2DqfeWoqKEgJfwqpyXkIOfn5CTjayLqI2/tfacha2RgqyX9o3pk62UlYS+gIStrZ2SgISkp/SolPODlKeBqaiUgIODnKf09JGfqa6mhbWUlIP8raaB8PaN_toOukYupg6avh76n/vCTl4vw9pyW8I6goYeUl4mPgYC8taqNgIurlryLk5LytfeRrPSUgpeIg6ank/aQjYurl5+frZyng5OAg5eDgoCTk5LzvYGCgK2DoLyDhJzy9IGAjI/2l4GHkY2DqZCSooyOgKWqkIKXtoGfvIuDjen09ZSxvfSmo6Krko6Tk42lppOXlaKEn5TxrZS/g4SSiam+l5KDlKOCj6uUo7WqnKeh9pGtn/acl4T3n7L8raani/WN" test_flag = decry(test_All_ming) assert test_flag == b"0123456-abcdefg-hijklmn-opqrstu-ABCDEFG-HIJKLMN-OPQRSTU-7778889" cip = bytes.fromhex("73494F2B67497638714A4B7668373643386132556C34767739706545736132586E494355704B4F706849434538613264686679446F344366725A7A796A3547556F6257446C344F586B5943636B4B3258676643556C493674395A794A715A47416E4B61546C4B4F50714A47327162364E674C47746B712B446736534E6A3669557459654F6C344B39725A3244672F6153675A65546E5A2B5072616144693736666E3479546A61795439704C7A725936436C364B5267717958396F3258395A4758725053456E4A536D725A53796A363258702F54306C4C61586B614F4A7159476D725053416E4B6630394A47667161366D686257556C495038726161423850614E5F684943756E5A6174674A79766837366B2F7643746C497548395A6563746169646F373332703553556B35656967506141676679746E624778717144796F594F52365A2B746E4A614C713532766B3632586E4A54326C496D74394A794F72613655673565446A6247586B354C7A76593643674975656A612B68396F3242692F5358724A2B44676F4339725A32732F4B32676F7053426B706566725A796B384B715276492B446A5A2B4D395A53787666536D6F4A53526749365439702B4E6A3553586A4B33317070794C714A532F6836365371616D2B6C3643446C4B654839494F6B725A2B7470714754673547666836756D696679716C4B79396B3643313950574E5F73494F2B67497638714A4B7668373643386132556C34767739706545736132586E49435570494750394A4B49384B3252675053556B714371393665696F6F5341725043516C3457506C4932666B4B3258676643556C4B2F3068494B4A2F4A364167356554704B4F50714A47327162364E674C47746B712B446736534672623658705032656C344B39725A322F7666615368592F306B5A7975674A65587270474E6A7679746E504C30395A4B667266574E6C4B4B726E595077396F324971617155692F53456E344774725A3253674953516E492B4F6C363648714B61636935535870344F746B614877767048707161366D686257556C495038726161423850614E5F746F4F756B597570673661766837366E2F7643546C34767739707957384936676F5965556C346D50675943387461714E674975726C72794C6B354C7974594352725053756E4A654D6A7161446B2F61516A5A4F546C342B506735654C715A4743673565446B4A79686B3565766835366A6A716D746C494F54673653786A3447417334656F6E4A61486A7079796B354F57703565546C4A6630717079586949366672492B446A627950394A47766A36326367616D726B762B506B344C706A3675556B6F69426770617471705363716F435869616D2B6C354B446C4B4F436A3675556F3757716E4B6568397047746E2F61636C3454336E374C387261616E692F574E5F73494F2B67497638714A4B7668373643386132556C34767739706545736132586E49435570494750394A4B49384B3252675053556B716578674A4B6E394A4755716643546C3457396B3443636B4B3258676643556C493674395A794A715A47416E4B61546C4B4F50714A47326836694E676247746B707A396B3562796A3669527459654F6C344B39725A324467344F6A715A4F546E6166777170796B67344F666E3479446A66476839704B4A7466656369616D726E61794C6B35794E6A3553586B6F65726A595339714A616A385A53556A592B6F6B5A4B456C4B4F6339494F6D6F4A79746B614877767048707161366D686257556C495038726161423850614E5F2F344F756E5965666736662F683453432F7644326B7261746E706545735A47417262577170346D7072705357672F616D6E34754F6F4943786B4B53686935476469725774706F6D4C39714F762F506155696679556C4B2F77717047696A49476E2F3566326C366630395A53426E36326369616D426F502B78684A4B74683447416C59656F6E4A613967365363716171516F3565426C35574567594B58694B6953736679546A66474C7149323168354758674B32726C707A7839714368384C3652693733306C3443397170324A746136433876534F6C354C306C4A654C716169556A494F746F36663039594B532F4B6963704975446E374B506735622B3950574E5F73494F2B67497638714A4B7668373643386132556C34767739706545736132586E494355704B4F706849434538613264686679446F344366725A7A796A354755366257746E49507768494B736B3632636F366D556C4B4F50725A79466E344F6D67356574677166307135667A68353658693747546A5A7941684A79556B4A4F55726F2B546F3443396736534F716665576F714B45674B6D44727161582F62366D702F79746E496D50395A65667266574E6C4B4B726E595077396F3258395A4758725053456E4A534D714A542F7461716A6C49696F6B5969446C4B4F636A3675586F344F746B614877767048707161366D686257556C495038726161423850614E5F746F4F756B597570673661766837366E2F7643546C34767739707957384936676F5965556C364B757270477A384B324E6749756F6B6247787170326E6F6661527161326570343738673661796A354F526F6147746B622F307670654A682F6567736F75446B4A79686B3565567476574E6766534F6E49434467352B696950535371496631706F6D486A714338384A4F53386F2F306C3447746C494B582F5947676F354F746C36483071354C7A394B366D6C364B726B6F36546B3433706A3536583834656570355478714A5366716F435869592B4F6C374348714A795739494F67702F53716E4B6568397047746E2F61636C3454336E374C387261616E692F574E") flag = decry(cip) print(flag)
flag即为:
welecom-toooooo-nu1lctf-2023hah-havegoo-odluckk-seeyouu-againnn
四、总结
发现自己有很多欠缺的地方
首先就是没有找到反调试,最后还是根据Lu1u师傅的提示找到的
其次就是面对杂乱的代码难以分析下去,比如这道题的transfrom2,5种不同的输入流,看着就想摆
我对rust程序的逆向分析手段也有问题,不能做到快准狠的找到加密逻辑
-------------------------------------------------------------------|人生如逆旅,我亦是行人|-------------------------------------------------------------------


 浙公网安备 33010602011771号
浙公网安备 33010602011771号