如何做渗透测试时不暴露自己真实ip
需要有代理服务器(多台更佳)
vim /etc/proxychains4.conf
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 56 57 58 59 60 61 62 63 64 65 66 67 68 69 70 71 72 73 74 75 76 77 78 79 80 81 82 83 84 85 86 87 88 89 90 91 92 93 94 95 96 97 98 99 100 101 102 103 104 | # proxychains.conf VER 4.x## HTTP, SOCKS4a, SOCKS5 tunneling proxifier with DNS.# The option below identifies how the ProxyList is treated.# only one option should be uncommented at time,# otherwise the last appearing option will be accepted# 动态代理链,每个chain只能开启一个,且代理列表down掉节点将跳过向下找可用节点dynamic_chain## Dynamic - Each connection will be done via chained proxies# all proxies chained in the order as they appear in the list# at least one proxy must be online to play in chain# (dead proxies are skipped)# otherwise EINTR is returned to the app##strict_chain## Strict - Each connection will be done via chained proxies# all proxies chained in the order as they appear in the list# all proxies must be online to play in chain# otherwise EINTR is returned to the app##round_robin_chain## Round Robin - Each connection will be done via chained proxies# of chain_len length# all proxies chained in the order as they appear in the list# at least one proxy must be online to play in chain# (dead proxies are skipped).# the start of the current proxy chain is the proxy after the last# proxy in the previously invoked proxy chain.# if the end of the proxy chain is reached while looking for proxies# start at the beginning again.# otherwise EINTR is returned to the app# These semantics are not guaranteed in a multithreaded environment.##random_chain## Random - Each connection will be done via random proxy# (or proxy chain, see chain_len) from the list.# this option is good to test your IDS :)# Make sense only if random_chain or round_robin_chain#chain_len = 2# Quiet mode (no output from library)#quiet_mode# Proxy DNS requests - no leak for DNS data# 注释dns代理,不然nmap扫描端口会报错# proxy_dns # set the class A subnet number to use for the internal remote DNS mapping# we use the reserved 224.x.x.x range by default,# if the proxified app does a DNS request, we will return an IP from that range.# on further accesses to this ip we will send the saved DNS name to the proxy.# in case some control-freak app checks the returned ip, and denies to # connect, you can use another subnet, e.g. 10.x.x.x or 127.x.x.x.# of course you should make sure that the proxified app does not need# *real* access to this subnet. # i.e. dont use the same subnet then in the localnet section#remote_dns_subnet 127 #remote_dns_subnet 10remote_dns_subnet 224# Some timeouts in millisecondstcp_read_time_out 15000tcp_connect_time_out 8000### Examples for localnet exclusion## localnet ranges will *not* use a proxy to connect.## Exclude connections to 192.168.1.0/24 with port 80# localnet 192.168.1.0:80/255.255.255.0## Exclude connections to 192.168.100.0/24# localnet 192.168.100.0/255.255.255.0## Exclude connections to ANYwhere with port 80# localnet 0.0.0.0:80/0.0.0.0## RFC5735 Loopback address range## if you enable this, you have to make sure remote_dns_subnet is not 127## you'll need to enable it if you want to use an application that ## connects to localhost.# localnet 127.0.0.0/255.0.0.0## RFC1918 Private Address Ranges# localnet 10.0.0.0/255.0.0.0# localnet 172.16.0.0/255.240.0.0# localnet 192.168.0.0/255.255.0.0# ProxyList format# type ip port [user pass]# (values separated by 'tab' or 'blank')## only numeric ipv4 addresses are valid# Examples:## socks5 192.168.67.78 1080 lamer secret# http 192.168.89.3 8080 justu hidden# socks4 192.168.1.49 1080# http 192.168.39.93 8080 # proxy types: http, socks4, socks5# ( auth types supported: "basic"-http "user/pass"-socks )#[ProxyList]# add proxy here ...# meanwile# defaults set to "tor"# 格式:代理类型 IP port username passwd socks4 127.0.0.1 9050socks5 111.156.111.xx 8899 test testxxx |
测试代理:
1 | proxychains curl cip.cc |

访问网站:
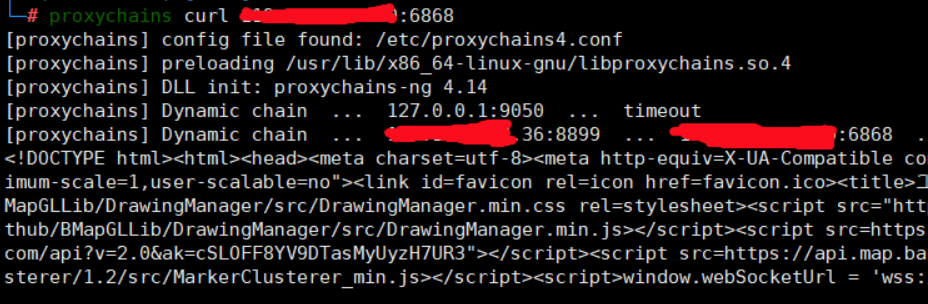
1 | proxychains curl 111.156.111.2:6868 |
扫描网站端口:
1 | proxychains nmap -p80 www.xxxx.com |





【推荐】国内首个AI IDE,深度理解中文开发场景,立即下载体验Trae
【推荐】编程新体验,更懂你的AI,立即体验豆包MarsCode编程助手
【推荐】抖音旗下AI助手豆包,你的智能百科全书,全免费不限次数
【推荐】轻量又高性能的 SSH 工具 IShell:AI 加持,快人一步
· 10年+ .NET Coder 心语,封装的思维:从隐藏、稳定开始理解其本质意义
· .NET Core 中如何实现缓存的预热?
· 从 HTTP 原因短语缺失研究 HTTP/2 和 HTTP/3 的设计差异
· AI与.NET技术实操系列:向量存储与相似性搜索在 .NET 中的实现
· 基于Microsoft.Extensions.AI核心库实现RAG应用
· TypeScript + Deepseek 打造卜卦网站:技术与玄学的结合
· 阿里巴巴 QwQ-32B真的超越了 DeepSeek R-1吗?
· 【译】Visual Studio 中新的强大生产力特性
· 10年+ .NET Coder 心语 ── 封装的思维:从隐藏、稳定开始理解其本质意义
· 【设计模式】告别冗长if-else语句:使用策略模式优化代码结构