linux中防火墙策略管理工具firewalld
firewalld拥有命令行界面(CLI)和图形用户界面(GUI)
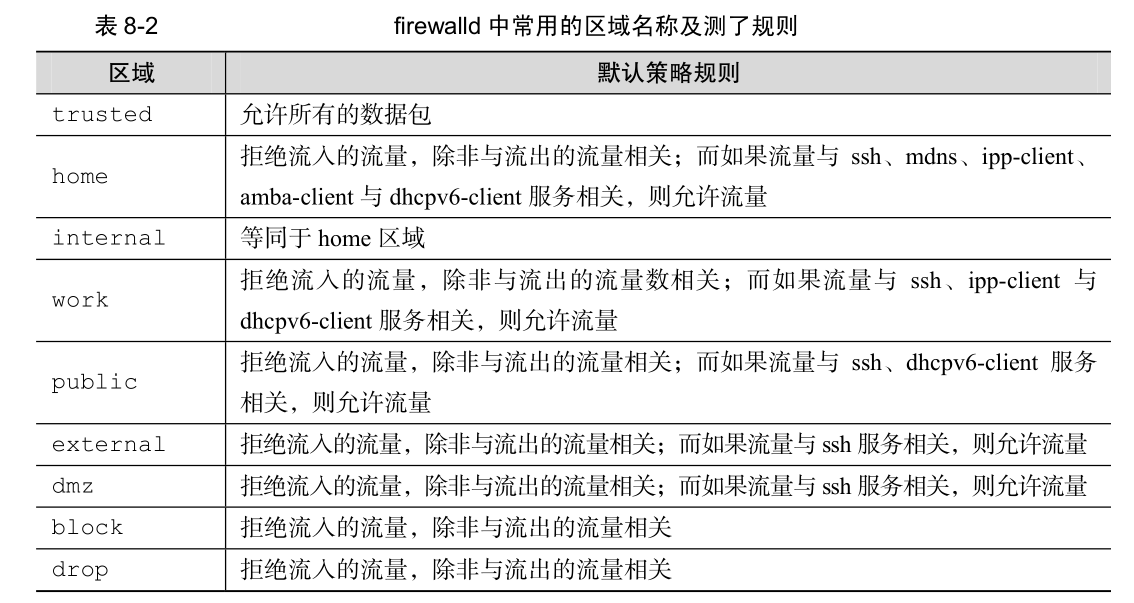
firewalld中有区域的概念,区域就是防火墙配置策略的模板。
firewalld中常用的区域名称及策略规则:
以下实验主要是命令行界面的常用命令
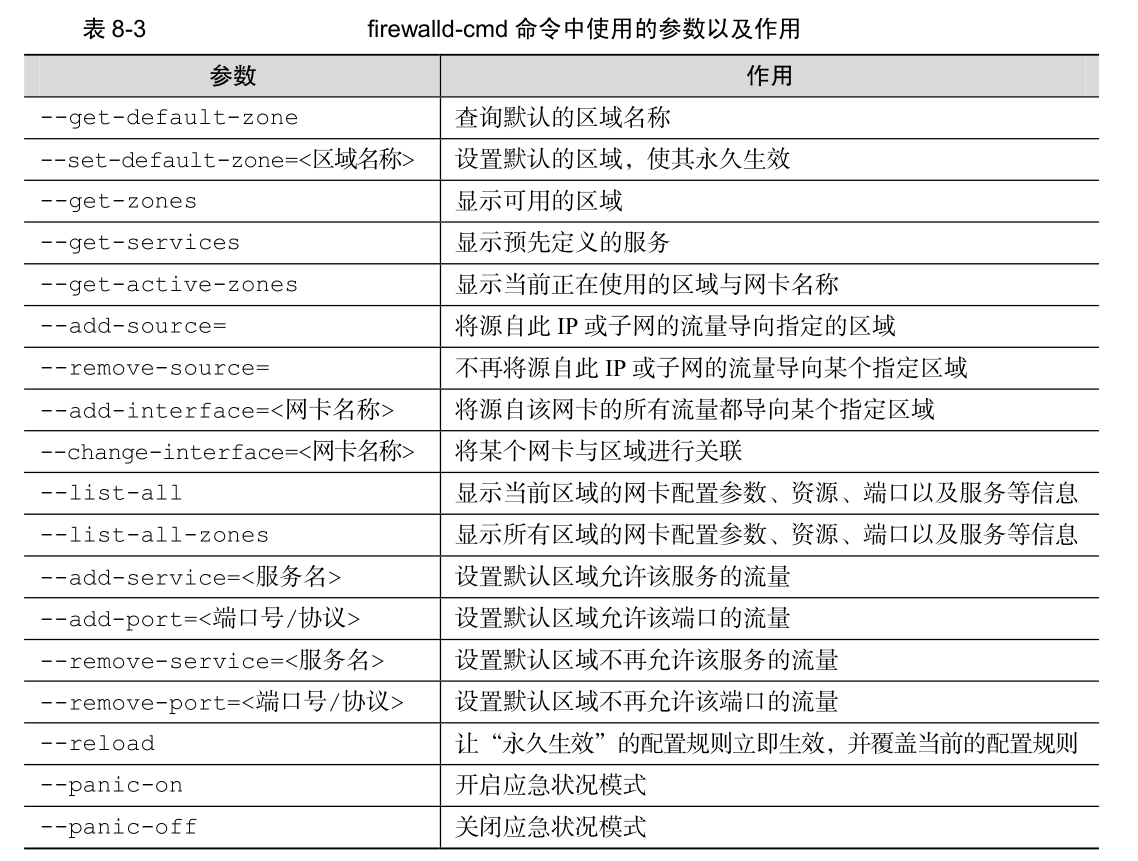
1、常用的参数表格
2、查看firewalld服务当前所使用的区域
[root@PC1 ~]# firewall-cmd --get-default-zone ## 当前的区域为public
public
3、查看eno16777728网卡在firewalld服务中的区域
[root@PC1 network-scripts]# nmcli connection show ## 查看网卡名称
NAME UUID TYPE DEVICE
eno16777728 d6f581bd-b571-43bf-bb9c-c37d935855ee 802-3-ethernet eno16777728
[root@PC1 network-scripts]# firewall-cmd --get-zone-of-interface=eno16777728 ## 网卡在firewalld服务中的区域为public
public
4、将eno16777728的网卡区域设置为external(模式为permanent)
[root@PC1 network-scripts]# firewall-cmd --permanent --zone=external --change-interface=eno16777728 ## 将网卡在firewalld服务中区域修改为external
success
[root@PC1 network-scripts]# firewall-cmd --get-zone-of-interface=eno16777728 ## 当前并未生效(因为使用的permanent模式)
public
[root@PC1 network-scripts]# firewall-cmd --permanent --get-zone-of-interface=eno16777728
external
5、将firewalld服务的当前区域设置为external(运行模式为runtime)
[root@PC1 network-scripts]# firewall-cmd --get-default-zone ## 当前的服务区域为public
public
[root@PC1 network-scripts]# firewall-cmd --set-default-zone=external ## 设置为external
success
[root@PC1 network-scripts]# firewall-cmd --get-default-zone ## 修改成功(因为运行模式为runtime)
external
6、测试应急模式(192.168.10.10位当前设置的主机, 192.168.10.20为另一台主机)
[root@PC2 ~]# ifconfig | head -n 3
eno16777728: flags=4163<UP,BROADCAST,RUNNING,MULTICAST> mtu 1500
inet 192.168.10.20 netmask 255.255.255.0 broadcast 192.168.10.255
inet6 fe80::20c:29ff:fe25:bb3e prefixlen 64 scopeid 0x20<link>
[root@PC2 ~]# ping -c 3 192.168.10.10
PING 192.168.10.10 (192.168.10.10) 56(84) bytes of data.
64 bytes from 192.168.10.10: icmp_seq=1 ttl=64 time=0.261 ms
64 bytes from 192.168.10.10: icmp_seq=2 ttl=64 time=0.215 ms
64 bytes from 192.168.10.10: icmp_seq=3 ttl=64 time=0.195 ms
--- 192.168.10.10 ping statistics ---
3 packets transmitted, 3 received, 0% packet loss, time 2000ms
rtt min/avg/max/mdev = 0.195/0.223/0.261/0.032 ms
[root@PC1 network-scripts]# firewall-cmd --panic-on ## 开启应急模式
success
[root@PC2 ~]# ping -c 3 192.168.10.10
PING 192.168.10.10 (192.168.10.10) 56(84) bytes of data.
--- 192.168.10.10 ping statistics ---
3 packets transmitted, 0 received, 100% packet loss, time 1999ms
[root@PC1 network-scripts]# firewall-cmd --panic-off ## 关闭应急模式
success
[root@PC2 ~]# ping -c 3 192.168.10.10
PING 192.168.10.10 (192.168.10.10) 56(84) bytes of data.
64 bytes from 192.168.10.10: icmp_seq=1 ttl=64 time=0.291 ms
64 bytes from 192.168.10.10: icmp_seq=2 ttl=64 time=0.226 ms
64 bytes from 192.168.10.10: icmp_seq=3 ttl=64 time=0.193 ms
--- 192.168.10.10 ping statistics ---
3 packets transmitted, 3 received, 0% packet loss, time 2000ms
rtt min/avg/max/mdev = 0.193/0.236/0.291/0.044 ms
7、将firewalld服务的区域修改文public
[root@PC1 network-scripts]# firewall-cmd --get-default-zone
external
[root@PC1 network-scripts]# firewall-cmd --set-default-zone=public
success
[root@PC1 network-scripts]# firewall-cmd --get-default-zone
public
8、查看public区域是否允许请求SSH和HTTPS协议的流量
[root@PC1 network-scripts]# firewall-cmd --zone=public --query-service=ssh
yes
[root@PC1 network-scripts]# firewall-cmd --zone=public --query-service=https
no
9、把firewalld服务中请求HTTPS协议的流量设置为永久允许,并立即生效
[root@PC1 network-scripts]# firewall-cmd --zone=public --add-service=https --permanent
success
[root@PC1 network-scripts]# firewall-cmd --reload
success
[root@PC1 network-scripts]# firewall-cmd --zone=public --query-service=https
yes
10、将firewalld服务中请求HTTP协议的流量设置为永久拒绝,并立即生效
[root@PC1 network-scripts]# firewall-cmd --zone=public --query-service=http
no
[root@PC1 network-scripts]# firewall-cmd --zone=public --add-service=http --permanent
success
[root@PC1 network-scripts]# firewall-cmd --reload
success
[root@PC1 network-scripts]# firewall-cmd --zone=public --query-service=http
yes
[root@PC1 network-scripts]# firewall-cmd --zone=public --remove-service=http --permanent
success
[root@PC1 network-scripts]# firewall-cmd --reload
success
[root@PC1 network-scripts]# firewall-cmd --zone=public --query-service=http
no
11、把在firewalld服务中访问8080和8081端口的流量策略设置为允许,但仅限当前生效
[root@PC1 network-scripts]# firewall-cmd --zone=public --list-ports
[root@PC1 network-scripts]# firewall-cmd --zone=public --add-port=8080-8081/tcp
success
[root@PC1 network-scripts]# firewall-cmd --zone=public --list-ports
8080-8081/tcp
12、把原本访问本机888端口的流量转发到22端口,当前和长期均有效 (22端口为ssh服务的端口)
[root@PC2 ~]# ssh -p 888 192.168.10.10
ssh: connect to host 192.168.10.10 port 888: No route to host
[root@PC1 network-scripts]# firewall-cmd --permanent --zone=public --add-forward-port=port=888:proto=tcp:toport=22:toaddr=192.168.10.10
success
[root@PC1 network-scripts]# firewall-cmd --reload
success
[root@PC2 ~]# ssh -p 888 192.168.10.10
The authenticity of host '[192.168.10.10]:888 ([192.168.10.10]:888)' can't be established.
ECDSA key fingerprint is 0d:69:cb:ad:61:42:f3:f7:7b:93:4b:b4:af:83:4d:8e.
Are you sure you want to continue connecting (yes/no)? yes
Warning: Permanently added '[192.168.10.10]:888' (ECDSA) to the list of known hosts.
root@192.168.10.10's password:
Last login: Wed Dec 2 16:39:39 2020
[root@PC1 ~]# ifconfig | head -n 3
eno16777728: flags=4163<UP,BROADCAST,RUNNING,MULTICAST> mtu 1500
inet 192.168.10.10 netmask 255.255.255.0 broadcast 192.168.10.255
inet6 fe80::20c:29ff:fe66:37f7 prefixlen 64 scopeid 0x20<link>
[root@PC1 ~]# exit
logout
Connection to 192.168.10.10 closed.
13、拒绝192.168.10.0/24网段的所有用户访问本机的ssh服务(firewalld中的富规则)
[root@PC2 ~]# ssh 192.168.10.10
The authenticity of host '192.168.10.10 (192.168.10.10)' can't be established.
ECDSA key fingerprint is 0d:69:cb:ad:61:42:f3:f7:7b:93:4b:b4:af:83:4d:8e.
Are you sure you want to continue connecting (yes/no)? yes
Warning: Permanently added '192.168.10.10' (ECDSA) to the list of known hosts.
root@192.168.10.10's password:
Last login: Tue Dec 22 14:18:10 2020 from 192.168.10.20
[root@PC1 ~]# ifconfig | head -n 3
eno16777728: flags=4163<UP,BROADCAST,RUNNING,MULTICAST> mtu 1500
inet 192.168.10.10 netmask 255.255.255.0 broadcast 192.168.10.255
inet6 fe80::20c:29ff:fe66:37f7 prefixlen 64 scopeid 0x20<link>
[root@PC1 ~]# exit
logout
Connection to 192.168.10.10 closed.
[root@PC1 network-scripts]# firewall-cmd --permanent --zone=public --add-rich-rule="rule family="ipv4" source address="192.168.10.0/24" service name="ssh" reject"
success
[root@PC1 network-scripts]# firewall-cmd --reload
success
[root@PC2 ~]# ssh 192.168.10.10
ssh: connect to host 192.168.10.10 port 22: Connection refused
以上实验演示了firewalld服务命令行形式的常规的防火墙配置。






【推荐】国内首个AI IDE,深度理解中文开发场景,立即下载体验Trae
【推荐】编程新体验,更懂你的AI,立即体验豆包MarsCode编程助手
【推荐】抖音旗下AI助手豆包,你的智能百科全书,全免费不限次数
【推荐】轻量又高性能的 SSH 工具 IShell:AI 加持,快人一步
· 基于Microsoft.Extensions.AI核心库实现RAG应用
· Linux系列:如何用heaptrack跟踪.NET程序的非托管内存泄露
· 开发者必知的日志记录最佳实践
· SQL Server 2025 AI相关能力初探
· Linux系列:如何用 C#调用 C方法造成内存泄露
· 震惊!C++程序真的从main开始吗?99%的程序员都答错了
· 【硬核科普】Trae如何「偷看」你的代码?零基础破解AI编程运行原理
· 单元测试从入门到精通
· 上周热点回顾(3.3-3.9)
· winform 绘制太阳,地球,月球 运作规律