linux系统中firewalld防火墙策略工具firewall-config命令设置富规则
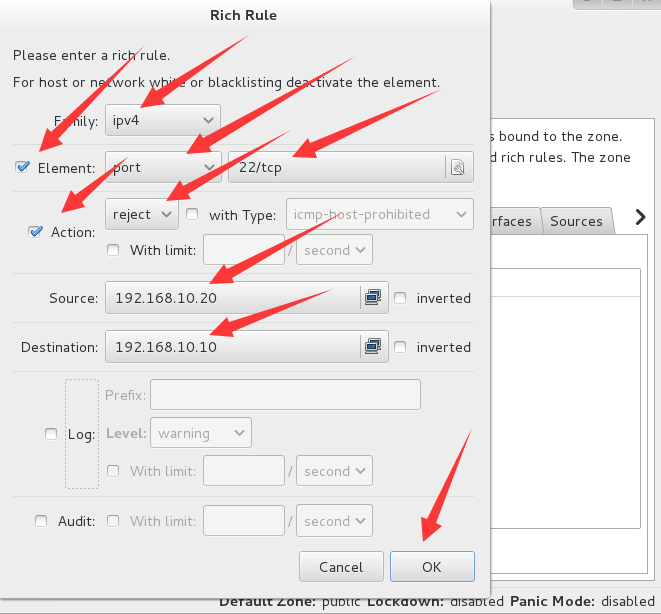
准备两台虚拟及PC1和PC2,设置PC1拒绝PC2访问PC1的22端口
1、
[root@PC1linuxprobe Desktop]# ifconfig | head -n 3 ## 查看PC1IP
eno16777728: flags=4163<UP,BROADCAST,RUNNING,MULTICAST> mtu 1500
inet 192.168.10.10 netmask 255.255.255.0 broadcast 192.168.10.255
inet6 fe80::20c:29ff:fe20:bf5e prefixlen 64 scopeid 0x20<link>
[root@PC2linuxprobe Desktop]# ifconfig | head -n 3 ## 查看PC2IP
eno16777728: flags=4163<UP,BROADCAST,RUNNING,MULTICAST> mtu 1500
inet 192.168.10.20 netmask 255.255.255.0 broadcast 192.168.10.255
inet6 fe80::20c:29ff:fe15:20b6 prefixlen 64 scopeid 0x20<link>
[root@PC2linuxprobe Desktop]# ping -c 3 192.168.10.10 ## 联通
PING 192.168.10.10 (192.168.10.10) 56(84) bytes of data.
64 bytes from 192.168.10.10: icmp_seq=1 ttl=64 time=0.235 ms
64 bytes from 192.168.10.10: icmp_seq=2 ttl=64 time=0.230 ms
64 bytes from 192.168.10.10: icmp_seq=3 ttl=64 time=0.220 ms
--- 192.168.10.10 ping statistics ---
3 packets transmitted, 3 received, 0% packet loss, time 2000ms
rtt min/avg/max/mdev = 0.220/0.228/0.235/0.013 ms
[root@PC2linuxprobe Desktop]# ssh 192.168.10.10 ## 测试远程登录,通过
root@192.168.10.10's password:
Last login: Sat Nov 7 20:57:14 2020 from 192.168.10.20
[root@PC1linuxprobe ~]# ifconfig | head -n 3
eno16777728: flags=4163<UP,BROADCAST,RUNNING,MULTICAST> mtu 1500
inet 192.168.10.10 netmask 255.255.255.0 broadcast 192.168.10.255
inet6 fe80::20c:29ff:fe20:bf5e prefixlen 64 scopeid 0x20<link>
[root@PC1linuxprobe ~]# exit
logout
Connection to 192.168.10.10 closed.
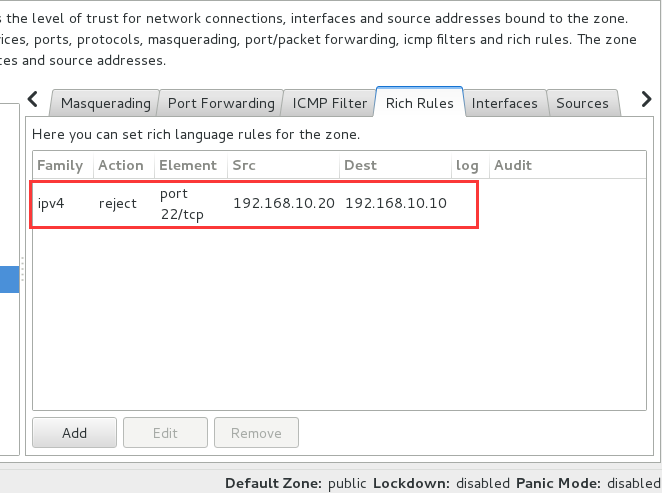
2、在PC1中设置富规则
3、在PC2主机中测试
[root@PC2linuxprobe Desktop]# ifconfig | head -n 3 ## 查看IP
eno16777728: flags=4163<UP,BROADCAST,RUNNING,MULTICAST> mtu 1500
inet 192.168.10.20 netmask 255.255.255.0 broadcast 192.168.10.255
inet6 fe80::20c:29ff:fe15:20b6 prefixlen 64 scopeid 0x20<link>
[root@PC2linuxprobe Desktop]# ping -c 3 192.168.10.10 ## 联通
PING 192.168.10.10 (192.168.10.10) 56(84) bytes of data.
64 bytes from 192.168.10.10: icmp_seq=1 ttl=64 time=0.220 ms
64 bytes from 192.168.10.10: icmp_seq=2 ttl=64 time=0.204 ms
64 bytes from 192.168.10.10: icmp_seq=3 ttl=64 time=0.221 ms
--- 192.168.10.10 ping statistics ---
3 packets transmitted, 3 received, 0% packet loss, time 2000ms
rtt min/avg/max/mdev = 0.204/0.215/0.221/0.007 ms
[root@PC2linuxprobe Desktop]# ssh 192.168.10.10 ## 无法远程登录(22端口为ssh服务)
ssh: connect to host 192.168.10.10 port 22: Connection refused
4、在PC1中移除富规则

在PC2中测试:
[root@PC2linuxprobe Desktop]# ssh 192.168.10.10 ## 可以远程登录 root@192.168.10.10's password: Last login: Sat Nov 7 21:03:05 2020 from 192.168.10.20 [root@PC1linuxprobe ~]# ifconfig | head -n 3 eno16777728: flags=4163<UP,BROADCAST,RUNNING,MULTICAST> mtu 1500 inet 192.168.10.10 netmask 255.255.255.0 broadcast 192.168.10.255 inet6 fe80::20c:29ff:fe20:bf5e prefixlen 64 scopeid 0x20<link> [root@PC1linuxprobe ~]# exit logout Connection to 192.168.10.10 closed.



 浙公网安备 33010602011771号
浙公网安备 33010602011771号