linux系统中防火墙管理工具iptables
1、iptables是什么
防火墙:内网与公网之间、主机之间的保护屏障,依据防火墙策略对流量进行过滤。
iptables是防火墙策略管理工具,用于设定防火墙策略。
防火墙会从按照从上至下的顺序来读取防火墙策略,如果匹配,则执行匹配规则定义的行为,如果没有匹配当前策略,则继续匹配下一条,如果都没有匹配,则执行默认行为。
防火墙的策略一般有允许和拒绝两种。当防火墙的默认策略是拒绝时,就要设置允许的规则,否则谁都进不来;如果防火墙策略是允许时,就要设置拒绝动作,否则谁都能进来。
一般来说,从内网向外网发送的流量一般都是可控和良性的,因此我们使用最多的就是INPUT进入流量规则设置。
2、iptables的使用
iptables是依据命令行进行防火墙策略设定的工具。常用参数如下:
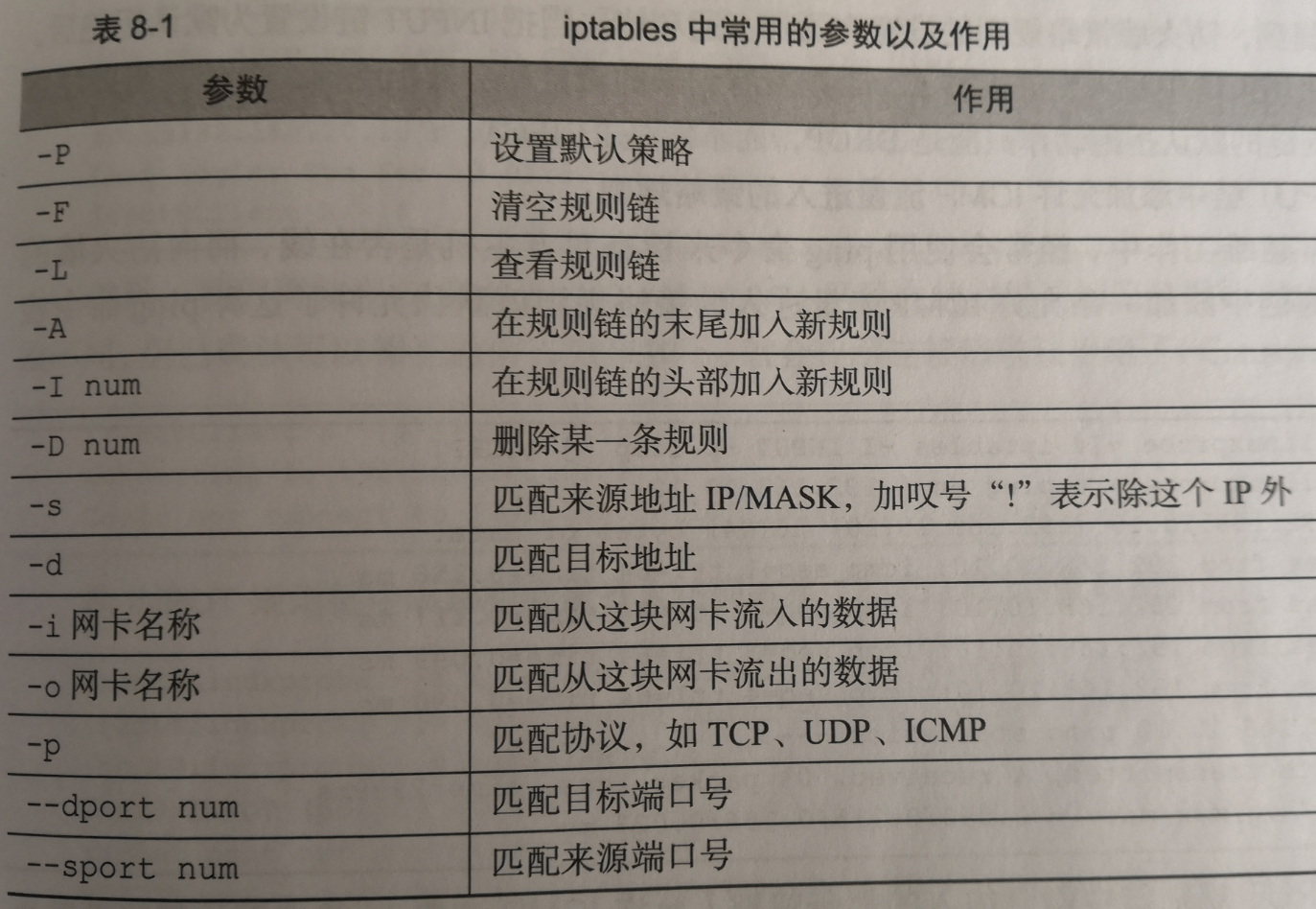
3、如何查看系统当前的防火墙策略规则链
## iptables -L 命令
[root@PC1linuxprobe test1]# iptables -L | wc -l 104 [root@PC1linuxprobe test1]# iptables -L | head -n 5 ## 查看前5行,进入流量INPUT默认是ACCEPT Chain INPUT (policy ACCEPT) target prot opt source destination ACCEPT all -- anywhere anywhere ctstate RELATED,ESTABLISHED ACCEPT all -- anywhere anywhere INPUT_direct all -- anywhere anywhere [root@PC1linuxprobe test1]#
4、清空当前的防火墙策略规则链
## iptables -F 命令
[root@PC1linuxprobe test1]# iptables -F ## 清空当前的防火墙策略规则链
[root@PC1linuxprobe test1]# iptables -L | wc -l ## 列出当前的防火墙策略规则链,由104行减少为71行
71
[root@PC1linuxprobe test1]# iptables -L | head -n 5 ## 查看前5行,可见只剩下标题,默认的INPUT策略仍然为ACCEPT
Chain INPUT (policy ACCEPT)
target prot opt source destination
Chain FORWARD (policy ACCEPT)
target prot opt source destination
5、使用另一台虚拟机(PC2linuxprobe)测试当前虚拟机(PC1linuxprobe的INPUT)流量
[root@PC1linuxprobe test1]# ifconfig | head -n 2 ##当前虚拟机的IP地址为192.168.10.10
eno16777728: flags=4163<UP,BROADCAST,RUNNING,MULTICAST> mtu 1500
inet 192.168.10.10 netmask 255.255.255.0 broadcast 192.168.10.255
[root@PC2linuxprobe test2]# ping -c 3 192.168.10.10 ## 测试ping连接,联通
PING 192.168.10.10 (192.168.10.10) 56(84) bytes of data.
64 bytes from 192.168.10.10: icmp_seq=1 ttl=64 time=0.369 ms
64 bytes from 192.168.10.10: icmp_seq=2 ttl=64 time=0.222 ms
64 bytes from 192.168.10.10: icmp_seq=3 ttl=64 time=0.228 ms
--- 192.168.10.10 ping statistics ---
3 packets transmitted, 3 received, 0% packet loss, time 2000ms
rtt min/avg/max/mdev = 0.222/0.273/0.369/0.067 ms
[root@PC2linuxprobe test2]# ssh 192.168.10.10 ## 测试远程登录,可以
root@192.168.10.10's password:
Last login: Thu Nov 5 15:31:35 2020
[root@PC1linuxprobe ~]# ifconfig | head -n 2
eno16777728: flags=4163<UP,BROADCAST,RUNNING,MULTICAST> mtu 1500
inet 192.168.10.10 netmask 255.255.255.0 broadcast 192.168.10.255
[root@PC1linuxprobe ~]# exit
logout
Connection to 192.168.10.10 closed.
6、将当前虚拟机PC1linuxprobe虚拟机的INPUT默认策略设置为DROP(不能为REJECT)
## DROP和REJECT的区别:DROP拒绝不会有回复,REJECT拒绝有回复。
[root@PC1linuxprobe test1]# iptables -P INPUT DROP [root@PC1linuxprobe test1]# iptables -L | head -n 3 ## 设置后为DROP Chain INPUT (policy DROP) target prot opt source destination
在PC2linuxprobe中测试PC1中设定DROP的效果:
[root@PC2linuxprobe test2]# ping -c 3 192.168.10.10 ## ping,不能连接
PING 192.168.10.10 (192.168.10.10) 56(84) bytes of data.
--- 192.168.10.10 ping statistics ---
3 packets transmitted, 0 received, 100% packet loss, time 2000ms
[root@PC2linuxprobe test2]# ssh 192.168.10.10 ## 不能远程控制
ssh: connect to host 192.168.10.10 port 22: Connection timed out
7、设定允许icmp流量进入
默认INPUT策略已经设动为拒绝,需要设定允许规则,否则谁也进不来。
icmp协议是什么?
ICMP是Internet控制报文协议。它是TCP/IP协议簇的一个子协议,用于在IP主机、路由器之间传递控制消息。控制消息是指网络通不通、主机是否可达、路由是否可用等网络本身的消息。这些控制消息虽然并不传输用户数据,但是对于用户数据的传递起着重要的作用。ping命令就是基于ICMP的。
[root@PC1linuxprobe test1]# iptables -L | head -n 5 ## 设置前
Chain INPUT (policy DROP)
target prot opt source destination
Chain FORWARD (policy ACCEPT)
target prot opt source destination
[root@PC1linuxprobe test1]# iptables -I INPUT -p icmp -j ACCEPT ## 设置允许icmp流量
[root@PC1linuxprobe test1]# iptables -L | head -n 5 ## 设置后,可以看到效果
Chain INPUT (policy DROP)
target prot opt source destination
ACCEPT icmp -- anywhere anywhere
Chain FORWARD (policy ACCEPT)
测试效果:
[root@PC2linuxprobe test2]# ping -c 3 192.168.10.10 ## ping可以
PING 192.168.10.10 (192.168.10.10) 56(84) bytes of data.
64 bytes from 192.168.10.10: icmp_seq=1 ttl=64 time=0.382 ms
64 bytes from 192.168.10.10: icmp_seq=2 ttl=64 time=0.213 ms
64 bytes from 192.168.10.10: icmp_seq=3 ttl=64 time=0.253 ms
--- 192.168.10.10 ping statistics ---
3 packets transmitted, 3 received, 0% packet loss, time 2002ms
rtt min/avg/max/mdev = 0.213/0.282/0.382/0.074 ms
[root@PC2linuxprobe test2]# ssh 192.168.10.10 ## 不能远程控制
ssh: connect to host 192.168.10.10 port 22: Connection timed out
8、如何删除防火墙策略
删除刚才设置的icmp允许流量
[root@PC1linuxprobe test1]# iptables -L | head -n 5 ## 删除前 Chain INPUT (policy DROP) target prot opt source destination ACCEPT icmp -- anywhere anywhere Chain FORWARD (policy ACCEPT) [root@PC1linuxprobe test1]# iptables -D INPUT 1 ## 删除 [root@PC1linuxprobe test1]# iptables -L | head -n 5 ## 删除后 Chain INPUT (policy DROP) target prot opt source destination Chain FORWARD (policy ACCEPT) target prot opt source destination
9、将INPUT流量从DROP设置为ACCEPT(由拒绝设置为允许)
[root@PC1linuxprobe test1]# iptables -L | head -n 3 ## 设置前 Chain INPUT (policy DROP) target prot opt source destination [root@PC1linuxprobe test1]# iptables -P INPUT ACCEPT ## 设置 [root@PC1linuxprobe test1]# iptables -L | head -n 3 ## 设置后 Chain INPUT (policy ACCEPT) target prot opt source destination
10、将icmp流量分别设置为DROP和REJECT,对比效果
设置为DROP,并测试效果:
[root@PC1linuxprobe test1]# iptables -L | head -n 5 ## 设置前
Chain INPUT (policy ACCEPT)
target prot opt source destination
Chain FORWARD (policy ACCEPT)
target prot opt source destination
[root@PC1linuxprobe test1]# iptables -I INPUT -p icmp -j DROP ## 设置
[root@PC1linuxprobe test1]# iptables -L | head -n 5 ## 设置后
Chain INPUT (policy ACCEPT)
target prot opt source destination
DROP icmp -- anywhere anywhere
Chain FORWARD (policy ACCEPT)
测试DROP的效果:
[root@PC2linuxprobe test2]# ping -c 3 192.168.10.10 ## 可以看到没有拒绝消息
PING 192.168.10.10 (192.168.10.10) 56(84) bytes of data.
--- 192.168.10.10 ping statistics ---
3 packets transmitted, 0 received, 100% packet loss, time 2000ms
设置为REJECT,并测试效果:
[root@PC1linuxprobe test1]# iptables -D INPUT 1 ## 删除上一步设置的策略
[root@PC1linuxprobe test1]# iptables -L | head -n 5 ## 设置前
Chain INPUT (policy ACCEPT)
target prot opt source destination
Chain FORWARD (policy ACCEPT)
target prot opt source destination
[root@PC1linuxprobe test1]# iptables -I INPUT -p icmp -j REJECT ## 设置
[root@PC1linuxprobe test1]# iptables -L | head -n 5 ## 设置后
Chain INPUT (policy ACCEPT)
target prot opt source destination
REJECT icmp -- anywhere anywhere reject-with icmp-port-unreachable
Chain FORWARD (policy ACCEPT)
测试:
[root@PC2linuxprobe test2]# ping -c 3 192.168.10.10 ## 可以看到3条拒绝消息
PING 192.168.10.10 (192.168.10.10) 56(84) bytes of data.
From 192.168.10.10 icmp_seq=1 Destination Port Unreachable
From 192.168.10.10 icmp_seq=2 Destination Port Unreachable
From 192.168.10.10 icmp_seq=3 Destination Port Unreachable
--- 192.168.10.10 ping statistics ---
3 packets transmitted, 0 received, +3 errors, 100% packet loss, time 2001ms
##以上是从协议上来设定
11、设置拒绝22端口
22端口是什么:22端口是ssh服务使用的。
[root@PC1linuxprobe test1]# iptables -F ## 清空防火墙策略
[root@PC1linuxprobe test1]# iptables -L | head -n 5 ## 设置前
Chain INPUT (policy ACCEPT)
target prot opt source destination
Chain FORWARD (policy ACCEPT)
target prot opt source destination
[root@PC1linuxprobe test1]# iptables -I INPUT -p tcp --dport 22 -j DROP ## 把22端口设置为DROP
[root@PC1linuxprobe test1]# iptables -L | head -n 5 ## 设置后
Chain INPUT (policy ACCEPT)
target prot opt source destination
DROP tcp -- anywhere anywhere tcp dpt:ssh
Chain FORWARD (policy ACCEPT)
测试效果:
[root@PC2linuxprobe test2]# ping -c 3 192.168.10.10 ## ping不受影响
PING 192.168.10.10 (192.168.10.10) 56(84) bytes of data.
64 bytes from 192.168.10.10: icmp_seq=1 ttl=64 time=0.270 ms
64 bytes from 192.168.10.10: icmp_seq=2 ttl=64 time=0.239 ms
64 bytes from 192.168.10.10: icmp_seq=3 ttl=64 time=0.224 ms
--- 192.168.10.10 ping statistics ---
3 packets transmitted, 3 received, 0% packet loss, time 2002ms
rtt min/avg/max/mdev = 0.224/0.244/0.270/0.023 ms
[root@PC2linuxprobe test2]# ssh 192.168.10.10 ## 无法远程
ssh: connect to host 192.168.10.10 port 22: Connection timed out
把INPUT22端口设置为REJECT:
[root@PC1linuxprobe test1]# iptables -F ## 清空防火墙策略
[root@PC1linuxprobe test1]# iptables -L | head -n 5 ## 设置前
Chain INPUT (policy ACCEPT)
target prot opt source destination
Chain FORWARD (policy ACCEPT)
target prot opt source destination
[root@PC1linuxprobe test1]# iptables -I INPUT -p tcp --dport 22 -j REJECT ## 设置
[root@PC1linuxprobe test1]# iptables -L | head -n 5 ## 设置后
Chain INPUT (policy ACCEPT)
target prot opt source destination
REJECT tcp -- anywhere anywhere tcp dpt:ssh reject-with icmp-port-unreachable
Chain FORWARD (policy ACCEPT)
测试效果:
[root@PC2linuxprobe test2]# ping -c 3 192.168.10.10 ## ping不受影响
PING 192.168.10.10 (192.168.10.10) 56(84) bytes of data.
64 bytes from 192.168.10.10: icmp_seq=1 ttl=64 time=0.277 ms
64 bytes from 192.168.10.10: icmp_seq=2 ttl=64 time=0.215 ms
64 bytes from 192.168.10.10: icmp_seq=3 ttl=64 time=0.225 ms
--- 192.168.10.10 ping statistics ---
3 packets transmitted, 3 received, 0% packet loss, time 2000ms
rtt min/avg/max/mdev = 0.215/0.239/0.277/0.027 ms
[root@PC2linuxprobe test2]# ssh 192.168.10.10 ## 有拒绝消息
ssh: connect to host 192.168.10.10 port 22: Connection refused
12、针对IP地址进行设置,拒绝192.168.10.20 IP地址
[root@PC1linuxprobe test1]# iptables -F ## 清空防火墙
[root@PC1linuxprobe test1]# iptables -L | head -n 5 ## 设置前
Chain INPUT (policy ACCEPT)
target prot opt source destination
Chain FORWARD (policy ACCEPT)
target prot opt source destination
[root@PC1linuxprobe test1]# iptables -I INPUT -s 192.168.10.20 -j REJECT ## 设置
[root@PC1linuxprobe test1]# iptables -L | head -n 5 ## 设置后
Chain INPUT (policy ACCEPT)
target prot opt source destination
REJECT all -- 192.168.10.20 anywhere reject-with icmp-port-unreachable
Chain FORWARD (policy ACCEPT)
测试效果:
[root@PC2linuxprobe test2]# ifconfig | head -n 3
eno16777728: flags=4163<UP,BROADCAST,RUNNING,MULTICAST> mtu 1500
inet 192.168.10.20 netmask 255.255.255.0 broadcast 192.168.10.255
inet6 fe80::20c:29ff:fe15:20b6 prefixlen 64 scopeid 0x20<link>
[root@PC2linuxprobe test2]# ping -c 3 192.168.10.10 ## 拒绝
PING 192.168.10.10 (192.168.10.10) 56(84) bytes of data.
From 192.168.10.10 icmp_seq=1 Destination Port Unreachable
From 192.168.10.10 icmp_seq=2 Destination Port Unreachable
From 192.168.10.10 icmp_seq=3 Destination Port Unreachable
--- 192.168.10.10 ping statistics ---
3 packets transmitted, 0 received, +3 errors, 100% packet loss, time 2000ms
[root@PC2linuxprobe test2]# ssh 192.168.10.10 ## 拒绝
ssh: connect to host 192.168.10.10 port 22: Connection refused
[root@pc3 ~]# ifconfig | head -n 3
ens160: flags=4163<UP,BROADCAST,RUNNING,MULTICAST> mtu 1500
inet 192.168.10.15 netmask 255.255.255.0 broadcast 192.168.10.255
inet6 fe80::d7fe:9dfc:42ec:c255 prefixlen 64 scopeid 0x20<link>
[root@pc3 ~]# ping -c 3 192.168.10.10 ## 允许
PING 192.168.10.10 (192.168.10.10) 56(84) bytes of data.
64 bytes from 192.168.10.10: icmp_seq=1 ttl=64 time=0.265 ms
64 bytes from 192.168.10.10: icmp_seq=2 ttl=64 time=0.241 ms
64 bytes from 192.168.10.10: icmp_seq=3 ttl=64 time=0.226 ms
--- 192.168.10.10 ping statistics ---
3 packets transmitted, 3 received, 0% packet loss, time 62ms
rtt min/avg/max/mdev = 0.226/0.244/0.265/0.016 ms
[root@pc3 ~]# ssh 192.168.10.10 ## 允许
root@192.168.10.10's password:
Last login: Thu Nov 5 22:33:04 2020 from 192.168.10.15
[root@PC1linuxprobe ~]# ifconfig | head -n 3
eno16777728: flags=4163<UP,BROADCAST,RUNNING,MULTICAST> mtu 1500
inet 192.168.10.10 netmask 255.255.255.0 broadcast 192.168.10.255
inet6 fe80::20c:29ff:fe20:bf5e prefixlen 64 scopeid 0x20<link>
[root@PC1linuxprobe ~]# exit
logout
Connection to 192.168.10.10 closed.
13、同时设动IP地址和端口
[root@PC1linuxprobe test1]# iptables -F ## 清空防火墙策略
[root@PC1linuxprobe test1]# iptables -L | head -n 5 ## 设置前
Chain INPUT (policy ACCEPT)
target prot opt source destination
Chain FORWARD (policy ACCEPT)
target prot opt source destination
[root@PC1linuxprobe test1]# iptables -I INPUT -s 192.168.10.20 -p tcp --dport 22 -j REJECT ## 设置192.168.10.20 IP拒绝访问22端口
[root@PC1linuxprobe test1]# iptables -L | head -n 5 ## 设置后
Chain INPUT (policy ACCEPT)
target prot opt source destination
REJECT tcp -- 192.168.10.20 anywhere tcp dpt:ssh reject-with icmp-port-unreachable
Chain FORWARD (policy ACCEPT)
测试效果:
[root@PC2linuxprobe test2]# ifconfig | head -n 3
eno16777728: flags=4163<UP,BROADCAST,RUNNING,MULTICAST> mtu 1500
inet 192.168.10.20 netmask 255.255.255.0 broadcast 192.168.10.255
inet6 fe80::20c:29ff:fe15:20b6 prefixlen 64 scopeid 0x20<link>
[root@PC2linuxprobe test2]# ping -c 3 192.168.10.10 ## ping不受影响
PING 192.168.10.10 (192.168.10.10) 56(84) bytes of data.
64 bytes from 192.168.10.10: icmp_seq=1 ttl=64 time=0.236 ms
64 bytes from 192.168.10.10: icmp_seq=2 ttl=64 time=0.208 ms
64 bytes from 192.168.10.10: icmp_seq=3 ttl=64 time=0.182 ms
--- 192.168.10.10 ping statistics ---
3 packets transmitted, 3 received, 0% packet loss, time 1999ms
rtt min/avg/max/mdev = 0.182/0.208/0.236/0.027 ms
[root@PC2linuxprobe test2]# ssh 192.168.10.10 ## 无法远程控制
ssh: connect to host 192.168.10.10 port 22: Connection refused
[root@pc3 ~]# ifconfig | head -n 3
ens160: flags=4163<UP,BROADCAST,RUNNING,MULTICAST> mtu 1500
inet 192.168.10.15 netmask 255.255.255.0 broadcast 192.168.10.255
inet6 fe80::d7fe:9dfc:42ec:c255 prefixlen 64 scopeid 0x20<link>
[root@pc3 ~]# ping -c 3 192.168.10.10 ## ping不受影响
PING 192.168.10.10 (192.168.10.10) 56(84) bytes of data.
64 bytes from 192.168.10.10: icmp_seq=1 ttl=64 time=0.301 ms
64 bytes from 192.168.10.10: icmp_seq=2 ttl=64 time=0.191 ms
64 bytes from 192.168.10.10: icmp_seq=3 ttl=64 time=0.170 ms
--- 192.168.10.10 ping statistics ---
3 packets transmitted, 3 received, 0% packet loss, time 39ms
rtt min/avg/max/mdev = 0.170/0.220/0.301/0.059 ms
[root@pc3 ~]# ssh 192.168.10.10 ## 远程控制不受影响
root@192.168.10.10's password:
Last login: Thu Nov 5 22:47:57 2020 from 192.168.10.15
[root@PC1linuxprobe ~]# ifconfig | head -n 3
eno16777728: flags=4163<UP,BROADCAST,RUNNING,MULTICAST> mtu 1500
inet 192.168.10.10 netmask 255.255.255.0 broadcast 192.168.10.255
inet6 fe80::20c:29ff:fe20:bf5e prefixlen 64 scopeid 0x20<link>
[root@PC1linuxprobe ~]# exit
logout
Connection to 192.168.10.10 closed.
14、iptables设定的防火墙策略只是临时起效,重启系统之后恢复系统默认设置,如何使iptables设置的防火墙策略永久生效
[root@PC1linuxprobe test1]# service iptables save
iptables: Saving firewall rules to /etc/sysconfig/iptables:[ OK ]






【推荐】国内首个AI IDE,深度理解中文开发场景,立即下载体验Trae
【推荐】编程新体验,更懂你的AI,立即体验豆包MarsCode编程助手
【推荐】抖音旗下AI助手豆包,你的智能百科全书,全免费不限次数
【推荐】轻量又高性能的 SSH 工具 IShell:AI 加持,快人一步
· 基于Microsoft.Extensions.AI核心库实现RAG应用
· Linux系列:如何用heaptrack跟踪.NET程序的非托管内存泄露
· 开发者必知的日志记录最佳实践
· SQL Server 2025 AI相关能力初探
· Linux系列:如何用 C#调用 C方法造成内存泄露
· 震惊!C++程序真的从main开始吗?99%的程序员都答错了
· 【硬核科普】Trae如何「偷看」你的代码?零基础破解AI编程运行原理
· 单元测试从入门到精通
· 上周热点回顾(3.3-3.9)
· winform 绘制太阳,地球,月球 运作规律