Kubernetes 部署Web UI (Dashboard)
Kubernetes-Dashboard 简介
Kubernetes-Dashboard 简单来说,就是一个 Kubernetes 集群的 Web UI 网页管理工具,提供了部署应用、资源对象管理、容器日志查询、监控系统等功能。
下面是官网的一些介绍:

Dashboard is a web-based Kubernetes user interface. You can use Dashboard to deploy containerized applications to a Kubernetes cluster, troubleshoot your containerized application, and manage the cluster resources. You can use Dashboard to get an overview of applications running on your cluster, as well as for creating or modifying individual Kubernetes resources (such as Deployments, Jobs, DaemonSets, etc). For example, you can scale a Deployment, initiate a rolling update, restart a pod or deploy new applications using a deploy wizard. Dashboard also provides information on the state of Kubernetes resources in your cluster and on any errors that may have occurred. ################## Dashboard是一个基于web的Kubernetes用户界面。您可以使用Dashboard将容器化的应用程序部署到Kubernetes集群,对容器化的应用程序进行故障诊断,并管理集群资源。您可以使用Dashboard来获得运行在您的集群上的应用程序的概述,以及创建或修改单个Kubernetes资源(例如部署、作业、守护集等)。例如,可以使用部署向导扩展部署、启动滚动更新、重新启动pod或部署新应用程序。 Dashboard还提供关于集群中Kubernetes资源的状态以及可能发生的任何错误的信息。
部署配置
1、角色创建与绑定
[root@master01 k8s]# mkdir dashboard [root@master01 k8s]# cd dashboard/ [root@master01 dashboard]# cat dashboard-configmap.yaml dashboard-controller.yaml dashboard-rbac.yaml dashboard-secret.yaml dashboard-service.yaml k8s-admin.yaml [root@master01 dashboard]# cat dashboard-rbac.yaml kind: Role #创建一个角色 apiVersion: rbac.authorization.k8s.io/v1 metadata: labels: k8s-app: kubernetes-dashboard addonmanager.kubernetes.io/mode: Reconcile name: kubernetes-dashboard-minimal #角色名字 被下面匹配 namespace: kube-system rules: #该角色拥有的权限 # Allow Dashboard to get, update and delete Dashboard exclusive secrets. - apiGroups: [""] resources: ["secrets"] resourceNames: ["kubernetes-dashboard-key-holder", "kubernetes-dashboard-certs"] verbs: ["get", "update", "delete"] # Allow Dashboard to get and update 'kubernetes-dashboard-settings' config map. - apiGroups: [""] resources: ["configmaps"] resourceNames: ["kubernetes-dashboard-settings"] verbs: ["get", "update"] # Allow Dashboard to get metrics from heapster. - apiGroups: [""] resources: ["services"] resourceNames: ["heapster"] verbs: ["proxy"] - apiGroups: [""] resources: ["services/proxy"] resourceNames: ["heapster", "http:heapster:", "https:heapster:"] verbs: ["get"] --- apiVersion: rbac.authorization.k8s.io/v1 kind: RoleBinding metadata: name: kubernetes-dashboard-minimal namespace: kube-system labels: k8s-app: kubernetes-dashboard addonmanager.kubernetes.io/mode: Reconcile roleRef: #通过这个关联角色 apiGroup: rbac.authorization.k8s.io kind: Role name: kubernetes-dashboard-minimal #这里的角色名字 匹配上面那个创建的角色名字 subjects: - kind: ServiceAccount #服务账号 给程序使用 下面会创建一个名为 kubernetes-dashboard 的SA name: kubernetes-dashboard namespace: kube-system [root@master01 dashboard]# [root@master01 dashboard]# kubectl create -f dashboard-rbac.yaml role.rbac.authorization.k8s.io/kubernetes-dashboard-minimal created rolebinding.rbac.authorization.k8s.io/kubernetes-dashboard-minimal created [root@master01 dashboard]# kubectl get role -n kube-system NAME AGE extension-apiserver-authentication-reader 12d kubernetes-dashboard-minimal 91s #新建的角色 system::leader-locking-kube-controller-manager 12d system::leader-locking-kube-scheduler 12d system:controller:bootstrap-signer 12d system:controller:cloud-provider 12d system:controller:token-cleaner 12d [root@master01 dashboard]# kubectl get rolebinding -n kube-system NAME AGE kubernetes-dashboard-minimal 2m9s #新建的角色绑定 system::leader-locking-kube-controller-manager 12d system::leader-locking-kube-scheduler 12d system:controller:bootstrap-signer 12d system:controller:cloud-provider 12d system:controller:token-cleaner 12d [root@master01 dashboard]#
2、创建配置文件
[root@master01 dashboard]# cat dashboard-secret.yaml apiVersion: v1 kind: Secret metadata: labels: k8s-app: kubernetes-dashboard # Allows editing resource and makes sure it is created first. addonmanager.kubernetes.io/mode: EnsureExists name: kubernetes-dashboard-certs namespace: kube-system type: Opaque --- apiVersion: v1 kind: Secret metadata: labels: k8s-app: kubernetes-dashboard # Allows editing resource and makes sure it is created first. addonmanager.kubernetes.io/mode: EnsureExists name: kubernetes-dashboard-key-holder namespace: kube-system type: Opaque [root@master01 dashboard]# [root@master01 dashboard]# kubectl create -f dashboard-secret.yaml secret/kubernetes-dashboard-certs created secret/kubernetes-dashboard-key-holder created [root@master01 dashboard]# [root@master01 dashboard]# cat dashboard-configmap.yaml apiVersion: v1 kind: ConfigMap metadata: labels: k8s-app: kubernetes-dashboard # Allows editing resource and makes sure it is created first. addonmanager.kubernetes.io/mode: EnsureExists name: kubernetes-dashboard-settings namespace: kube-system [root@master01 dashboard]# [root@master01 dashboard]# kubectl create -f dashboard-configmap.yaml configmap/kubernetes-dashboard-settings created [root@master01 dashboard]#
3、新建控制器
[root@master01 dashboard]# cat dashboard-controller.yaml apiVersion: v1 kind: ServiceAccount #新建的SA 已经被上面绑定了 所有该Nginx pod 有权限访问 metadata: labels: k8s-app: kubernetes-dashboard addonmanager.kubernetes.io/mode: Reconcile name: kubernetes-dashboard namespace: kube-system --- apiVersion: apps/v1 kind: Deployment metadata: name: kubernetes-dashboard namespace: kube-system labels: k8s-app: kubernetes-dashboard kubernetes.io/cluster-service: "true" addonmanager.kubernetes.io/mode: Reconcile spec: selector: matchLabels: k8s-app: kubernetes-dashboard template: metadata: labels: k8s-app: kubernetes-dashboard annotations: scheduler.alpha.kubernetes.io/critical-pod: '' seccomp.security.alpha.kubernetes.io/pod: 'docker/default' spec: priorityClassName: system-cluster-critical containers: - name: kubernetes-dashboard image: 10.192.27.111/library/kubernetes-dashboard-amd64:v1.8.3 resources: limits: cpu: 100m memory: 300Mi requests: cpu: 50m memory: 100Mi ports: - containerPort: 8443 protocol: TCP args: # PLATFORM-SPECIFIC ARGS HERE - --auto-generate-certificates volumeMounts: - name: kubernetes-dashboard-certs mountPath: /certs - name: tmp-volume mountPath: /tmp livenessProbe: httpGet: scheme: HTTPS path: / port: 8443 initialDelaySeconds: 30 timeoutSeconds: 30 volumes: - name: kubernetes-dashboard-certs secret: secretName: kubernetes-dashboard-certs - name: tmp-volume emptyDir: {} serviceAccountName: kubernetes-dashboard tolerations: - key: "CriticalAddonsOnly" operator: "Exists" [root@master01 dashboard]# kubectl create -f dashboard-controller.yaml serviceaccount/kubernetes-dashboard created deployment.apps/kubernetes-dashboard created [root@master01 dashboard]#
4、部署服务
[root@master01 dashboard]# cat dashboard-service.yaml apiVersion: v1 kind: Service metadata: name: kubernetes-dashboard namespace: kube-system labels: k8s-app: kubernetes-dashboard kubernetes.io/cluster-service: "true" addonmanager.kubernetes.io/mode: Reconcile spec: type: NodePort selector: k8s-app: kubernetes-dashboard ports: - port: 443 targetPort: 8443 nodePort: 30001 [root@master01 dashboard]# [root@master01 dashboard]# kubectl create -f dashboard-service.yaml service/kubernetes-dashboard created [root@master01 dashboard]#
5、查看结果
[root@master01 dashboard]# kubectl get all -n kube-system NAME READY STATUS RESTARTS AGE pod/kubernetes-dashboard-dc4889d87-mhpln 1/1 Running 0 2m43s NAME TYPE CLUSTER-IP EXTERNAL-IP PORT(S) AGE service/kubernetes-dashboard NodePort 10.0.0.204 <none> 443:30001/TCP 32s NAME READY UP-TO-DATE AVAILABLE AGE deployment.apps/kubernetes-dashboard 1/1 1 1 2m44s NAME DESIRED CURRENT READY AGE replicaset.apps/kubernetes-dashboard-dc4889d87 1 1 1 2m44s [root@master01 dashboard]#
6、访问

[root@master01 dashboard]# kubectl get ClusterRole -n kube-system NAME AGE admin 15d cluster-admin 15d #集群管理员权限 edit 15d system:aggregate-to-admin 15d system:aggregate-to-edit 15d system:aggregate-to-view 15d system:auth-delegator 15d system:aws-cloud-provider 15d system:basic-user 15d system:certificates.k8s.io:certificatesigningrequests:nodeclient 15d system:certificates.k8s.io:certificatesigningrequests:selfnodeclient 15d system:controller:attachdetach-controller 15d system:controller:certificate-controller 15d system:controller:clusterrole-aggregation-controller 15d system:controller:cronjob-controller 15d system:controller:daemon-set-controller 15d system:controller:deployment-controller 15d system:controller:disruption-controller 15d system:controller:endpoint-controller 15d system:controller:expand-controller 15d system:controller:generic-garbage-collector 15d system:controller:horizontal-pod-autoscaler 15d system:controller:job-controller 15d system:controller:namespace-controller 15d system:controller:node-controller 15d system:controller:persistent-volume-binder 15d system:controller:pod-garbage-collector 15d system:controller:pv-protection-controller 15d system:controller:pvc-protection-controller 15d system:controller:replicaset-controller 15d system:controller:replication-controller 15d system:controller:resourcequota-controller 15d system:controller:route-controller 15d system:controller:service-account-controller 15d system:controller:service-controller 15d system:controller:statefulset-controller 15d system:controller:ttl-controller 15d system:csi-external-attacher 15d system:csi-external-provisioner 15d system:discovery 15d system:heapster 15d system:kube-aggregator 15d system:kube-controller-manager 15d system:kube-dns 15d system:kube-scheduler 15d system:kubelet-api-admin 15d system:node 15d system:node-bootstrapper 15d system:node-problem-detector 15d system:node-proxier 15d system:persistent-volume-provisioner 15d system:volume-scheduler 15d view 15d [root@master01 dashboard]#
#这时需要token验证 https://10.192.27.115:30001/ [root@master01 dashboard]# cat k8s-admin.yaml apiVersion: v1 kind: ServiceAccount #生成一个SA账号 并绑定系统默认的集群管理员权限 metadata: name: dashboard-admin namespace: kube-system --- kind: ClusterRoleBinding apiVersion: rbac.authorization.k8s.io/v1beta1 metadata: name: dashboard-admin subjects: - kind: ServiceAccount name: dashboard-admin namespace: kube-system roleRef: kind: ClusterRole name: cluster-admin apiGroup: rbac.authorization.k8s.io [root@master01 dashboard]# [root@master01 dashboard]# kubectl create -f k8s-admin.yaml serviceaccount/dashboard-admin created clusterrolebinding.rbac.authorization.k8s.io/dashboard-admin created [root@master01 dashboard]# kubectl get secret -n kube-system 当SA创建时会并绑定时 生成一个以SA名为前缀的 token相关的secret文件 NAME TYPE DATA AGE dashboard-admin-token-dblbd kubernetes.io/service-account-token 3 26s default-token-jdfrg kubernetes.io/service-account-token 3 12d kubernetes-dashboard-certs Opaque 12 8m35s kubernetes-dashboard-key-holder Opaque 2 24m kubernetes-dashboard-token-lmpxl kubernetes.io/service-account-token 3 19m [root@master01 dashboard]# kubectl describe secret dashboard-admin-token-dblbd -n kube-system Name: dashboard-admin-token-dblbd Namespace: kube-system Labels: <none> Annotations: kubernetes.io/service-account.name: dashboard-admin kubernetes.io/service-account.uid: b925ed38-0da5-11ea-9860-1866dafb2f54 Type: kubernetes.io/service-account-token Data ==== ca.crt: 1359 bytes namespace: 11 bytes token: eyJhbGciOiJSUzI1NiIsImtpZCI6IiJ9.eyJpc3MiOiJrdWJlcm5ldGVzL3NlcnZpY2VhY2NvdW50Iiwia3ViZXJuZXRlcy5pby9zZXJ2aWNlYWNjb3VudC9uYW1lc3BhY2UiOiJrdWJlLXN5c3RlbSIsImt1YmVybmV0ZXMuaW8vc2VydmljZWFjY291bnQvc2VjcmV0Lm5hbWUiOiJkYXNoYm9hcmQtYWRtaW4tdG9rZW4tZGJsYmQiLCJrdWJlcm5ldGVzLmlvL3NlcnZpY2VhY2NvdW50L3NlcnZpY2UtYWNjb3VudC5uYW1lIjoiZGFzaGJvYXJkLWFkbWluIiwia3ViZXJuZXRlcy5pby9zZXJ2aWNlYWNjb3VudC9zZXJ2aWNlLWFjY291bnQudWlkIjoiYjkyNWVkMzgtMGRhNS0xMWVhLTk4NjAtMTg2NmRhZmIyZjU0Iiwic3ViIjoic3lzdGVtOnNlcnZpY2VhY2NvdW50Omt1YmUtc3lzdGVtOmRhc2hib2FyZC1hZG1pbiJ9.hG1e-1XW3urSbMHxW3EATumPjHKwCVXUNBEVLUB9n5peJ6Ivh5vB65DO58KcENhUdiXe6eBlChNyWydur86l7wBwEKzsfpKGSi1hfZo0UAq7hjkj-xWw1uQsTLNCbr4hV69brVEs-HT2N69f_C1bgidX2OxVoJF9WRRo_6zSKdiyAmlBsGME0ubtIk_HyvEn_6cdboLvQicgpq6MKx8N0otZqHP1EmwYl7fajZf8-jLbwa_WnMddmFz1trcCCIt2oCns11rZcEeJDiQhiOyVX5NWkCvE8intaDL-Tp2h8zNwVH4lBsZhmQIgWDvBFy2e6gy-7KNJezwkn2p80hPNAg [root@master01 dashboard]#
这里使用谷歌浏览器 但是无认证凭据
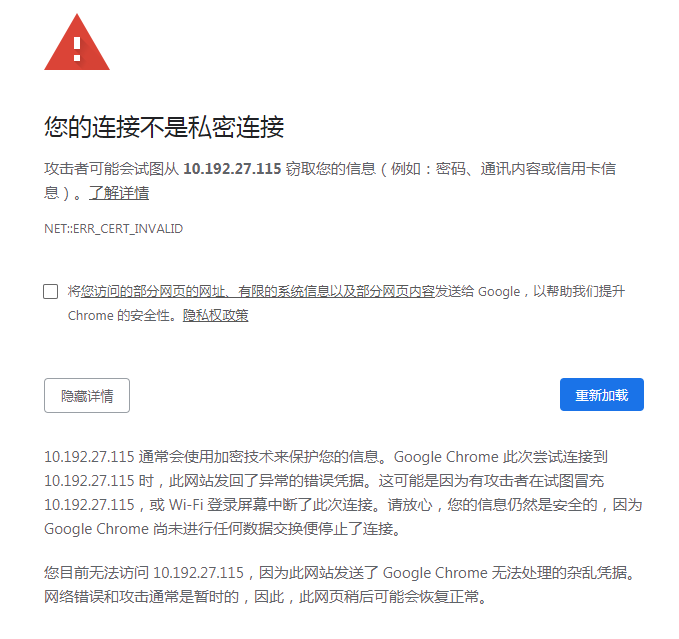
解决上面谷歌浏览器访问问题
[root@master01 dashboard]# vim dashboard-cert.sh cat > dashboard-csr.json <<EOF { "CN": "Dashboard", "host": [], "key": { "algo": "rsa", "size": 2048 }, "names": [ { "C": "CN", "L": "Beijing", "ST": "Beijing" } ] } EOF k8s_CA=$1 cfssl gencert -ca=$k8s_CA/ca.pem -ca-key=$k8s_CA/ca-key.pem -config=$k8s_CA/ca-config.json -profile=kubernetes dashboard-csr.json | cfssljson -bare dashboard kubectl delete secret kubernetes-dashboard-certs -n kube-system kubectl create secret generic kubernetes-dashboard-certs --from-file=./ -n kube-system [root@master01 dashboard]# kubectl get secrets -n kube-system NAME TYPE DATA AGE default-token-jdfrg kubernetes.io/service-account-token 3 12d kubernetes-dashboard-certs Opaque 0 14m kubernetes-dashboard-key-holder Opaque 2 14m kubernetes-dashboard-token-lmpxl kubernetes.io/service-account-token 3 10m [root@master01 dashboard]# bash dashboard-cert.sh /root/k8s/k8s-cert 2019/11/23 11:51:51 [INFO] generate received request 2019/11/23 11:51:51 [INFO] received CSR 2019/11/23 11:51:51 [INFO] generating key: rsa-2048 2019/11/23 11:51:51 [INFO] encoded CSR 2019/11/23 11:51:51 [INFO] signed certificate with serial number 174435950880265774665482626765748337233715752029 2019/11/23 11:51:51 [WARNING] This certificate lacks a "hosts" field. This makes it unsuitable for websites. For more information see the Baseline Requirements for the Issuance and Management of Publicly-Trusted Certificates, v.1.1.6, from the CA/Browser Forum (https://cabforum.org); specifically, section 10.2.3 ("Information Requirements"). secret "kubernetes-dashboard-certs" deleted secret/kubernetes-dashboard-certs created [root@master01 dashboard]# ls dashboard-cert.sh dashboard-controller.yaml dashboard.csr dashboard-key.pem dashboard-rbac.yaml dashboard-service.yaml dashboard-configmap.yaml dashboard-controller.yaml.bak dashboard-csr.json dashboard.pem dashboard-secret.yaml k8s-admin.yaml [root@master01 dashboard]# [root@master01 dashboard]# vim dashboard-controller.yaml 加下面两行 - --tls-key-file=dashboard-key.pem - --tls-cert-file=dashboard.pem

[root@master01 dashboard]# cat dashboard-controller.yaml apiVersion: v1 kind: ServiceAccount metadata: labels: k8s-app: kubernetes-dashboard addonmanager.kubernetes.io/mode: Reconcile name: kubernetes-dashboard namespace: kube-system --- apiVersion: apps/v1 kind: Deployment metadata: name: kubernetes-dashboard namespace: kube-system labels: k8s-app: kubernetes-dashboard kubernetes.io/cluster-service: "true" addonmanager.kubernetes.io/mode: Reconcile spec: selector: matchLabels: k8s-app: kubernetes-dashboard template: metadata: labels: k8s-app: kubernetes-dashboard annotations: scheduler.alpha.kubernetes.io/critical-pod: '' seccomp.security.alpha.kubernetes.io/pod: 'docker/default' spec: priorityClassName: system-cluster-critical containers: - name: kubernetes-dashboard image: 10.192.27.111/library/kubernetes-dashboard-amd64:v1.8.3 resources: limits: cpu: 100m memory: 300Mi requests: cpu: 50m memory: 100Mi ports: - containerPort: 8443 protocol: TCP args: # PLATFORM-SPECIFIC ARGS HERE - --auto-generate-certificates - --tls-key-file=dashboard-key.pem #新增 - --tls-cert-file=dashboard.pem #新增 volumeMounts: - name: kubernetes-dashboard-certs mountPath: /certs - name: tmp-volume mountPath: /tmp livenessProbe: httpGet: scheme: HTTPS path: / port: 8443 initialDelaySeconds: 30 timeoutSeconds: 30 volumes: - name: kubernetes-dashboard-certs secret: secretName: kubernetes-dashboard-certs - name: tmp-volume emptyDir: {} serviceAccountName: kubernetes-dashboard tolerations: - key: "CriticalAddonsOnly" operator: "Exists" [root@master01 dashboard]# [root@master01 dashboard]# kubectl apply -f dashboard-controller.yaml Warning: kubectl apply should be used on resource created by either kubectl create --save-config or kubectl apply serviceaccount/kubernetes-dashboard configured Warning: kubectl apply should be used on resource created by either kubectl create --save-config or kubectl apply deployment.apps/kubernetes-dashboard configured [root@master01 dashboard]#
现在就有证书了
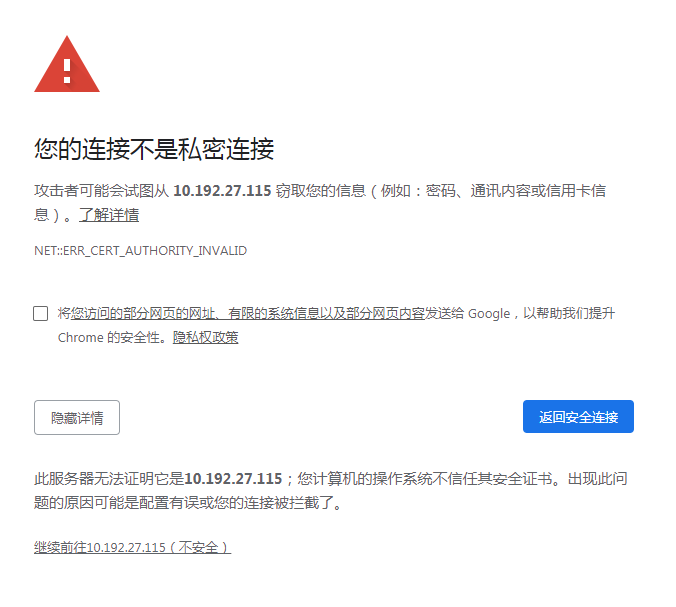
访问任意一个节点:https://10.192.27.115:30001/ 输入上面的那个token值
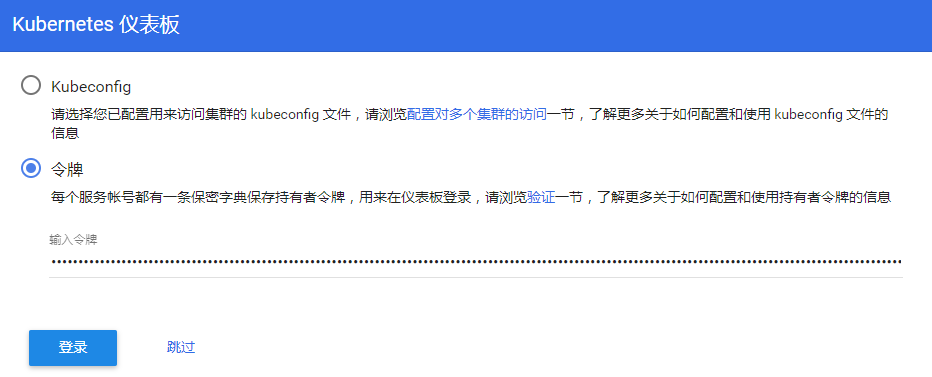
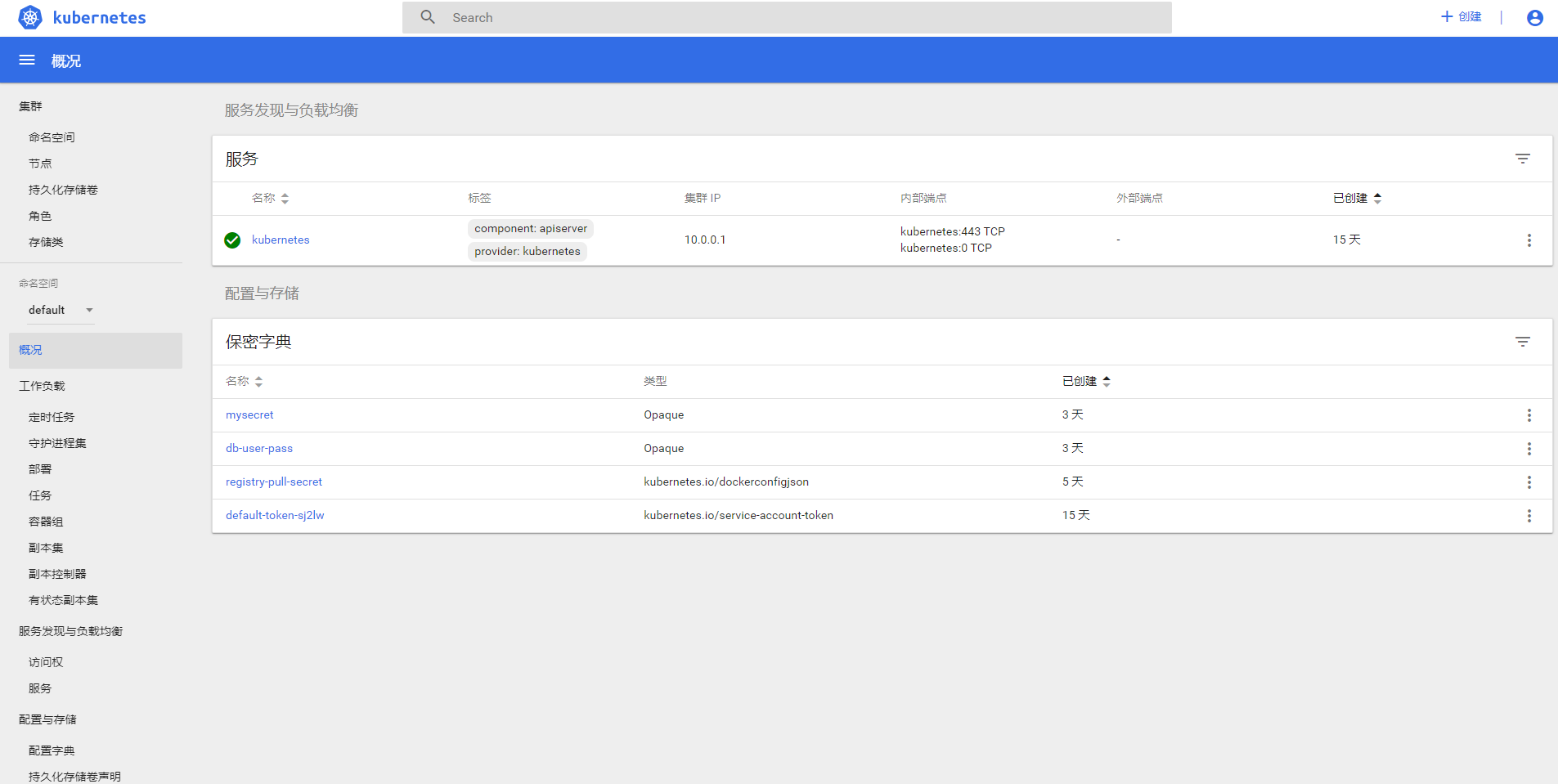



 浙公网安备 33010602011771号
浙公网安备 33010602011771号