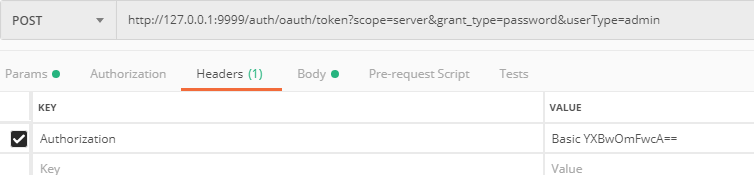
登录获取token
http://127.0.0.1:9999/auth/oauth/token?scope=server&grant_type=password&userType=admin
1.header:
Authorization:Basic dGVzdDp0ZXN0
参数说明:
Authorization:Basic Base64.encry(client_id:client_secret)
client_id、client_secret来自sys_oauth_client_details表。
dGVzdDp0ZXN0就是通过Base64.encry(client_id:client_secret)加密获取
如:Base64.encry(test:test)) 或 https://enc.pig4cloud.com/生成
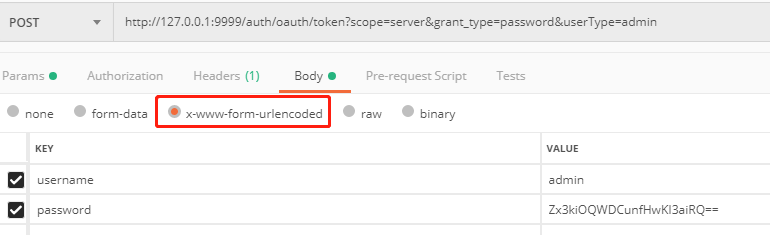
2.Body:
Content-Type:application/x-www-form-urlencoded
username:admin
password:Zx3kiOQWDCunfHwKI3aiRQ==
参数说明:
password:AES(明文密码)
如:AES('123456')=Zx3kiOQWDCunfHwKI3aiRQ==
刷新 token 请求接口
刷新 token 请求接口
http://127.0.0.1:9999/auth/oauth/token?scope=server&grant_type=refresh_token
Authorization:Basic dGFqaWE6dGFqaWE= ##Basic Base64.encry(client_id:client_secret)
refresh_token:5a058838-80e3-4ab5-ad28-d781e2609f77
注意:5a058838-80e3-4ab5-ad28-d781e2609f77来自于获取token接口返回的refresh_token字段
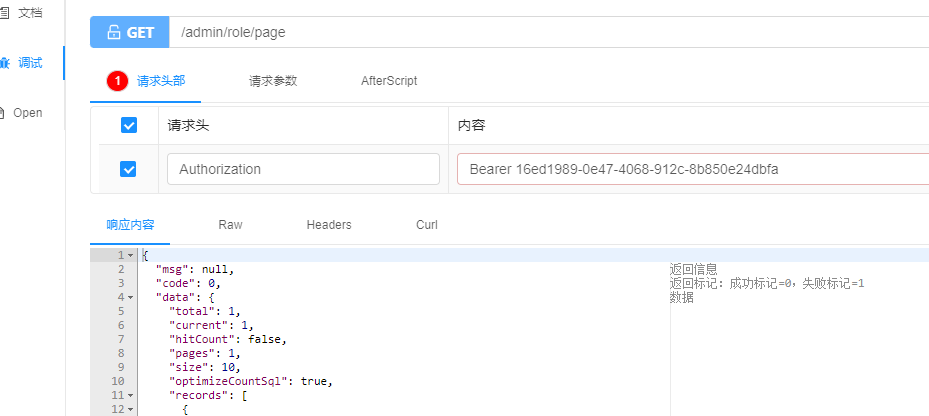
根据token请求url
url:http://localhost:8080/admin/role/page?current=1&size=20
application/json; charset=UTF-8
Authorization:Bearer 4f133126-ec7b-4788-89d3-6dc2f3df4192
注意:4f133126-ec7b-4788-89d3-6dc2f3df4192为用户token
Java AES加解密算法
@Test
public void testEnc() {
// 构建前端对应解密AES 因子
AES aes = new AES(Mode.CBC, Padding.ZeroPadding,
new SecretKeySpec("tax".getBytes(), "AES"),
new IvParameterSpec("tax".getBytes()));
String password = aes.encryptBase64("123456", Charset.defaultCharset());
System.out.println("加密password=" + password); //Zx3kiOQWDCunfHwKI3aiRQ==
}
@Test
public void testDec() {
// 构建前端对应解密AES 因子
AES aes = new AES(Mode.CBC, Padding.ZeroPadding,
new SecretKeySpec("tax".getBytes(), "AES"),
new IvParameterSpec("tax".getBytes()));
String password = aes.decryptStr("Zx3kiOQWDCunfHwKI3aiRQ==", Charset.defaultCharset());
System.out.println("解密password=" + password);
}






【推荐】国内首个AI IDE,深度理解中文开发场景,立即下载体验Trae
【推荐】编程新体验,更懂你的AI,立即体验豆包MarsCode编程助手
【推荐】抖音旗下AI助手豆包,你的智能百科全书,全免费不限次数
【推荐】轻量又高性能的 SSH 工具 IShell:AI 加持,快人一步
· 从 HTTP 原因短语缺失研究 HTTP/2 和 HTTP/3 的设计差异
· AI与.NET技术实操系列:向量存储与相似性搜索在 .NET 中的实现
· 基于Microsoft.Extensions.AI核心库实现RAG应用
· Linux系列:如何用heaptrack跟踪.NET程序的非托管内存泄露
· 开发者必知的日志记录最佳实践
· TypeScript + Deepseek 打造卜卦网站:技术与玄学的结合
· Manus的开源复刻OpenManus初探
· 写一个简单的SQL生成工具
· AI 智能体引爆开源社区「GitHub 热点速览」
· C#/.NET/.NET Core技术前沿周刊 | 第 29 期(2025年3.1-3.9)
2020-05-06 aaa
2019-05-06 Logstash-安装logstash-filter-multiline插件(解决logstash匹配多行日志)
2019-05-06 Elastic Kibana文档
2017-05-06 假如想要建设一个能承受500万PV/每天的网站,服务器每秒要处理多少个请求才能应对?
2014-05-06 Backbone Model——数据模型