linux下UsbMon-WireShark之USB协议抓取分析
usbmon配置
使用usbmon抓包分的,是需要 内核开启CONFIG_USB_MON=m, 重新编译内核, 编译ko :
make ARCH=arm64 CROSS_COMPILE=aarch64-himix100-linux- CONFIG_USB_MON=m M=./drivers/usb/ modules
设备挂载debugfs, 加载ko :
mount -t debugfs debugfs /sys/kernel/debug/
insmod usbmon.ko
查看是否成功产生/sys/kernel/debug/usb/usbmon/目录 :
[root@dvrdvs config] # ls /sys/kernel/debug/usb/usbmon/
0s 0u 1s 1t 1u 2s 2t 2u 3s 3t 3u 4s 4t 4u
找到所需监控的总线编号
运行“cat /sys/kernel/debug/usb/devices”。分别设备的信息,包括设备描述、Vendor、ProdID等。例如:
T: Bus=03 Lev=01 Prnt=01 Port=00 Cnt=01 Dev#= 2 Spd=12 MxCh= 0
D: Ver= 1.10 Cls=00(>ifc ) Sub=00 Prot=00 MxPS= 8 #Cfgs= 1
P: Vendor=0557 ProdID=2004 Rev= 1.00
S: Manufacturer=ATEN
S: Product=UC100KM V2.00
"Bus=03"指的是3号总线。通常使用使用lsusb得到设备的总线号。例如:
Bus 003 Device 002: ID 0557:2004 ATEN UC100KM V2.00
tcpdump 配置
下载最新libpcap和tcpdump, 当前是libpcap-1.9.1和tcpdump-4.9.3.
下载地址 :Index of /release
将libpcap-1.9.1和tcpdump-4.9.3放在同一个目录下, 先编译libcap :
./configure --host=aarch64-himix100-linux --with-pcap=linuxmake
再编译tcpdump :
./configure --host=aarch64-himix100-linuxmake
将tcpdump放到设备上, 运行./tcpdump -D :
[root@dvrdvs ] # ./tcpdump -D
1.eth0 [Up, Running]
2.lo [Up, Running, Loopback]
3.any (Pseudo-device that captures on all interfaces) [Up, Running]
4.usbmon0 (Raw USB traffic, all USB buses) [none]
5.usbmon1 (Raw USB traffic, bus number 1)
6.usbmon2 (Raw USB traffic, bus number 2)
7.usbmon3 (Raw USB traffic, bus number 3)
8.usbmon4 (Raw USB traffic, bus number 4)
9.eth1 [none]
可以看到有多个usbmon, 这里查看一下我们需要的设备 :
[root@dvrdvs config] # cat /sys/kernel/debug/usb/devices
T: Bus=01 Lev=00 Prnt=00 Port=00 Cnt=00 Dev#= 1 Spd=480 MxCh= 1
B: Alloc= 0/800 us ( 0%), #Int= 0, #Iso= 0
D: Ver= 2.00 Cls=09(hub ) Sub=00 Prot=01 MxPS=64 #Cfgs= 1
P: Vendor=1d6b ProdID=0002 Rev= 4.09
S: Manufacturer=Linux 4.9.37 xhci-hcd
S: Product=xHCI Host Controller
S: SerialNumber=12300000.xhci_0
C:* #Ifs= 1 Cfg#= 1 Atr=e0 MxPwr= 0mA
I:* If#= 0 Alt= 0 #EPs= 1 Cls=09(hub ) Sub=00 Prot=00 Driver=hub
E: Ad=81(I) Atr=03(Int.) MxPS= 4 Ivl=256ms
T: Bus=01 Lev=01 Prnt=01 Port=00 Cnt=01 Dev#= 2 Spd=480 MxCh= 4
D: Ver= 2.00 Cls=09(hub ) Sub=00 Prot=01 MxPS=64 #Cfgs= 1
P: Vendor=05e3 ProdID=0608 Rev=85.37
S: Product=USB2.0 Hub
C:* #Ifs= 1 Cfg#= 1 Atr=e0 MxPwr=100mA
I:* If#= 0 Alt= 0 #EPs= 1 Cls=09(hub ) Sub=00 Prot=00 Driver=hub
E: Ad=81(I) Atr=03(Int.) MxPS= 1 Ivl=256ms
T: Bus=02 Lev=00 Prnt=00 Port=00 Cnt=00 Dev#= 1 Spd=5000 MxCh= 1
B: Alloc= 0/800 us ( 0%), #Int= 0, #Iso= 0
D: Ver= 3.00 Cls=09(hub ) Sub=00 Prot=03 MxPS= 9 #Cfgs= 1
P: Vendor=1d6b ProdID=0003 Rev= 4.09
S: Manufacturer=Linux 4.9.37 xhci-hcd
S: Product=xHCI Host Controller
S: SerialNumber=12300000.xhci_0
C:* #Ifs= 1 Cfg#= 1 Atr=e0 MxPwr= 0mA
I:* If#= 0 Alt= 0 #EPs= 1 Cls=09(hub ) Sub=00 Prot=00 Driver=hub
E: Ad=81(I) Atr=03(Int.) MxPS= 4 Ivl=256ms
T: Bus=03 Lev=00 Prnt=00 Port=00 Cnt=00 Dev#= 1 Spd=480 MxCh= 1
B: Alloc= 0/800 us ( 0%), #Int= 0, #Iso= 0
D: Ver= 2.00 Cls=09(hub ) Sub=00 Prot=01 MxPS=64 #Cfgs= 1
P: Vendor=1d6b ProdID=0002 Rev= 4.09
S: Manufacturer=Linux 4.9.37 xhci-hcd
S: Product=xHCI Host Controller
S: SerialNumber=12310000.xhci_1
C:* #Ifs= 1 Cfg#= 1 Atr=e0 MxPwr= 0mA
I:* If#= 0 Alt= 0 #EPs= 1 Cls=09(hub ) Sub=00 Prot=00 Driver=hub
E: Ad=81(I) Atr=03(Int.) MxPS= 4 Ivl=256ms
T: Bus=04 Lev=00 Prnt=00 Port=00 Cnt=00 Dev#= 1 Spd=5000 MxCh= 1
B: Alloc= 0/800 us ( 0%), #Int= 0, #Iso= 0
D: Ver= 3.00 Cls=09(hub ) Sub=00 Prot=03 MxPS= 9 #Cfgs= 1
P: Vendor=1d6b ProdID=0003 Rev= 4.09
S: Manufacturer=Linux 4.9.37 xhci-hcd
S: Product=xHCI Host Controller
S: SerialNumber=12310000.xhci_1
C:* #Ifs= 1 Cfg#= 1 Atr=e0 MxPwr= 0mA
I:* If#= 0 Alt= 0 #EPs= 1 Cls=09(hub ) Sub=00 Prot=00 Driver=hub
E: Ad=81(I) Atr=03(Int.) MxPS= 4 Ivl=256ms
T: Bus=04 Lev=01 Prnt=01 Port=00 Cnt=01 Dev#= 3 Spd=5000 MxCh= 0
D: Ver= 3.10 Cls=ff(vend.) Sub=00 Prot=00 MxPS= 9 #Cfgs= 2
P: Vendor=0525 ProdID=a4a0 Rev= 4.09
S: Manufacturer=Linux 4.9.37 with dwc3-gadget
S: Product=Gadget Zero
S: SerialNumber=0123456789.0123456789.0123456789
C:* #Ifs= 1 Cfg#= 3 Atr=c0 MxPwr= 8mA
I:* If#= 0 Alt= 0 #EPs= 2 Cls=ff(vend.) Sub=00 Prot=00 Driver=(none)
E: Ad=81(I) Atr=02(Bulk) MxPS=1024 Ivl=0ms
E: Ad=01(O) Atr=02(Bulk) MxPS=1024 Ivl=0ms
I: If#= 0 Alt= 1 #EPs= 4 Cls=ff(vend.) Sub=00 Prot=00 Driver=(none)
E: Ad=81(I) Atr=02(Bulk) MxPS=1024 Ivl=0ms
E: Ad=01(O) Atr=02(Bulk) MxPS=1024 Ivl=0ms
E: Ad=82(I) Atr=01(Isoc) MxPS=1024 Ivl=1ms
E: Ad=02(O) Atr=01(Isoc) MxPS=1024 Ivl=1ms
C: #Ifs= 1 Cfg#= 2 Atr=c0 MxPwr= 8mA
I: If#= 0 Alt= 0 #EPs= 2 Cls=ff(vend.) Sub=00 Prot=00 Driver=
E: Ad=81(I) Atr=02(Bulk) MxPS=1024 Ivl=0ms
E: Ad=01(O) Atr=02(Bulk) MxPS=1024 Ivl=0ms
选择包含有 P: Vendor=xxx ProdID=xxx Rev= xxx 的段落(即筛选出你要抓包的USB设备的PID/VID号), 如果总线号是1(即Bus=01), 则是1u, 如果总线号是2, 则是2u, 依次类推.
特殊情况是0u表示监听所有总线.
Gadget Zero的Bus=04, 利用tcpdump截取usb数据 :
./tcpdump -i usbmon4 -w /home/config/usb_log.pcap
wireshark
wireshark中选择文件->打开, 找到相应的数据, 打开. (如果没有, 安装稍微新一点的wireshark)如图 :
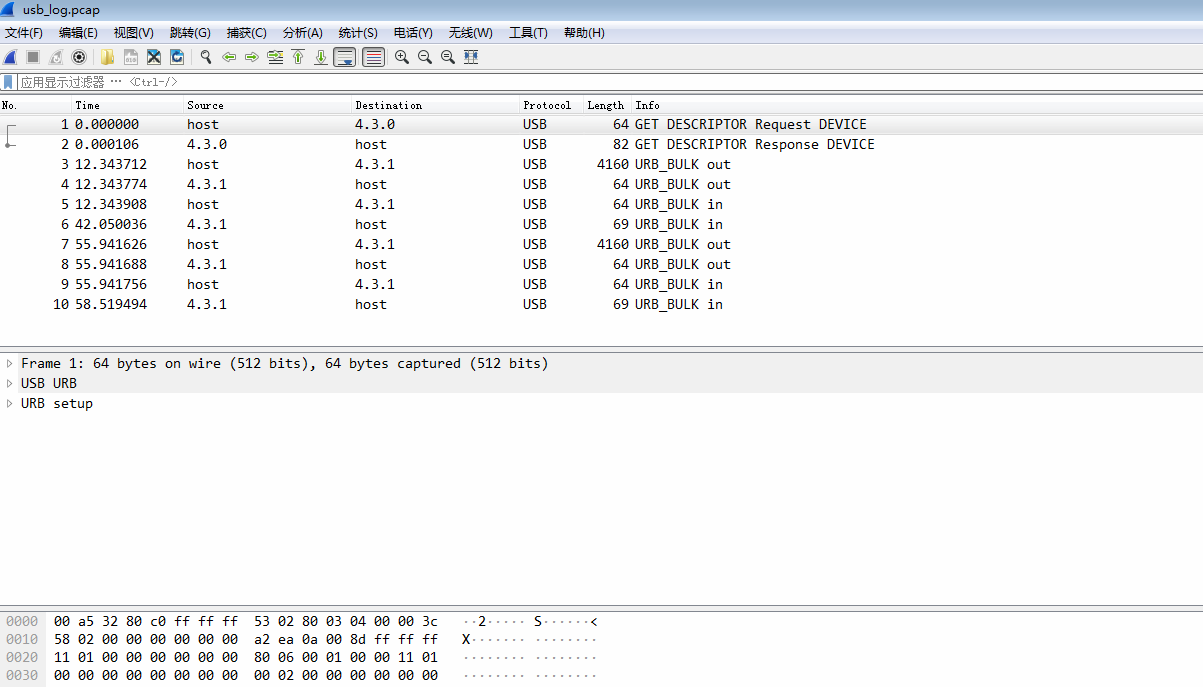
接下来就可以对里面的数据进行分析了.



