CentOS8.2 SSH服务使用与SFTP服务部署手册(1)
1、SSH密码验证
配置SSH服务器以从远程服务器
[1] 使用最小化安装centos,默认情况下一句安装OpenSSH,因此不需要安装新软件包,你可以使用默认密码身份验证登录系统,默认情况下,root用户账号是允许登录,最好修改设置,禁用root账号远程登录。
[root@sshserver ~]# vi /etc/ssh/sshd_config
PermitRootLogin yes 修改为 PermitRootLogin no
[root@sshserver ~]# systemctl restart sshd
[2] 如果Firewalld正在运行,请允许SSH服务。SSH使用[22 / TCP]。
[root@sshserver ~]# firewall-cmd --add-service=ssh --permanent
success
[root@sshserver ~]# firewall-cmd --reload
success
SSH客户端:CentOS
[3] 安装SSH客户端。
[root@sshclient ~]# dnf -y install openssh-clients
[4] 使用任何普通用户连接到SSH服务器。
#ssh [用户名@(主机名或IP地址)]
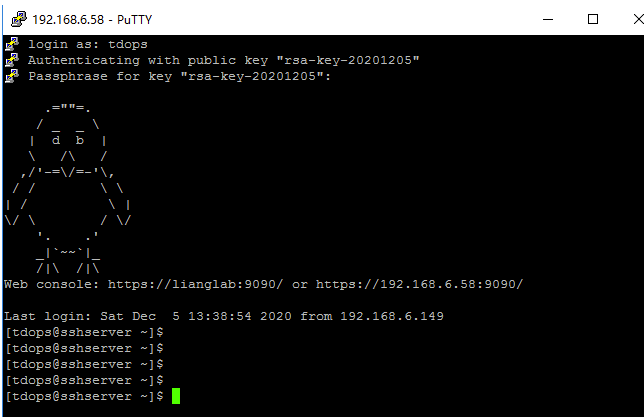
[root@sshclient ~]# ssh tdops@192.168.6.58
The authenticity of host '192.168.6.58 (192.168.6.58)' can't be established.
Are you sure you want to continue connecting (yes/no/[fingerprint])? yes
Warning: Permanently added '192.168.6.58' (ECDSA) to the list of known hosts.
tdops@192.168.6.58's password:
.=""=.
/ _ _ \
| d b |
\ /\ /
,/'-=\/=-'\,
/ / \ \
| / \ |
\/ \ / \/
'. .'
_|`~~`|_
/|\ /|\
Web console: https://lianglab:9090/ or https://192.168.6.58:9090/
Last login: Fri Dec 4 22:58:30 2020 from 10.57.237.13
[tdops@sshserver ~]$
[5] 可以使用SSH在远程主机上执行命令,如下所示。
[root@sshclient ~]# ssh tdops@192.168.6.58 "hostname"
tdops@192.168.6.58's password:
sshserver
[root@sshclient ~]#
2、SSH文件传输(CentOS与Windows)
通过ssh传输文件
[1] 使用SCP的实例
#命令⇒scp [选项]源目标
#将本地主机上的[test.txt]复制到远程主机[sshserver]
[root@sshclient ~]# rm -rf test.txt
[root@sshclient ~]# touch test.txt
[root@sshclient ~]# echo "sshclient test file" > test.txt
[root@sshclient ~]# scp test.txt tdops@192.168.6.58:/tmp
tdops@192.168.6.58's password:
test.txt 100% 20 16.9KB/s 00:00
[root@sshclient ~]# ssh tdops@192.168.6.58
tdops@192.168.6.58's password:
Last login: Fri Dec 4 23:17:41 2020 from 192.168.6.149
[tdops@sshserver ~]$ cat /tmp/test.txt
sshclient test file
[tdops@sshserver ~]$
#将远程主机[sshserver]上的[/home/tdops/test01.txt]复制到本地主机
[tdops@sshserver ~]$ touch test01.txt
[tdops@sshserver ~]$ echo "sshserver test01 file" > test01.txt
[tdops@sshserver ~]$ exit
logout
Connection to 192.168.6.58 closed.
[root@sshclient ~]# scp tdops@192.168.6.58:/home/tdops/test01.txt ./
tdops@192.168.6.58's password:
test01.txt 100% 22 18.1KB/s 00:00
[root@sshclient ~]# cat test01.txt
sshserver test01 file
[root@sshclient ~]#
[2] 这是使用SFTP(SSH文件传输协议)的示例。SFTP服务器功能默认情况下处于启用状态,但如果未启用,则使其在[/ etc / ssh / sshd_config]中添加[Subsystem sftp / usr / libexec / openssh / sftp-server]行。
#sftp [选项] [用户@主机]
[root@sshclient ~]# sftp tdops@192.168.6.58
tdops@192.168.6.58's password:
Connected to tdops@192.168.6.58.
sftp> ls
test01.txt
#显示远程主机上的当前目录
sftp> pwd
Remote working directory: /home/tdops
#显示本地主机上的当前目录
sftp> !pwd
/root
sftp>
#显示远程主机上当前目录中的文件
sftp> ls -l
-rw-r--r-- 1 tdops users 22 Dec 5 12:44 test01.txt
#显示本地主机上当前目录中的文件
sftp> !ls -l
total 24
-rw-------. 1 root root 1327 Sep 27 16:24 anaconda-ks.cfg
-rw-r--r--. 1 root root 1437 Sep 27 16:38 initial-setup-ks.cfg
-rw-r--r--. 1 root root 4391 Dec 4 10:18 lianglab.ovpn
-rw-r--r--. 1 root root 22 Dec 5 12:45 test01.txt
-rw-r--r--. 1 root root 20 Dec 5 12:42 test.txt
sftp> ls
dir test01.txt
#更改目录
sftp> cd dir/
sftp> pwd
Remote working directory: /home/tdops/dir
sftp> put t
test.txt test01.txt
#将文件上传到远程主机
sftp> put test.txt
Uploading test.txt to /home/tdops/dir/test.txt
test.txt 100% 20 24.7KB/s 00:00
sftp> ls
test.txt
#将一些文件上传到远程主机
sftp> put *.txt
Uploading test.txt to /home/tdops/dir/test.txt
test.txt 100% 20 25.5KB/s 00:00
Uploading test01.txt to /home/tdops/dir/test01.txt
test01.txt 100% 22 32.2KB/s 00:00
sftp> ls
test.txt test01.txt
# 使用cd.. 切换到上一级目录
sftp> cd ..
sftp> ls
dir getfile.txt sshserver.txt test01.txt
#从远程主机下载文件
sftp> get getfile.txt
Fetching /home/tdops/getfile.txt to getfile.txt
#从远程主机下载一些文件
sftp> get *.txt
Fetching /home/tdops/getfile.txt to getfile.txt
Fetching /home/tdops/sshserver.txt to sshserver.txt
Fetching /home/tdops/test01.txt to test01.txt
/home/tdops/test01.txt 100% 22 17.1KB/s 00:00
sftp> ls
dir getfile.txt sshserver.txt test01.txt
#查看已经下载到本机的文件
sftp> !ls
anaconda-ks.cfg getfile.txt initial-setup-ks.cfg lianglab.ovpn sshserver.txt test01.txt test.txt
sftp>
#在远程主机上创建目录
sftp> mkdir testdir
sftp> cd t
test01.txt testdir/
sftp> cd testdir/
sftp> put *.txt
Uploading test.txt to /home/tdops/testdir/test.txt
test.txt 100% 20 24.1KB/s 00:00
Uploading test01.txt to /home/tdops/testdir/test01.txt
test01.txt 100% 22 35.1KB/s 00:00
sftp> ls
test.txt test01.txt
sftp> ls -l
-rw-r--r-- 1 tdops users 20 Dec 5 12:48 test.txt
-rw-r--r-- 1 tdops users 22 Dec 5 12:48 test01.txt
sftp> cd ..
sftp> ls
dir test01.txt testdir
#删除远程主机上的文件
sftp> rmdir testdir/
Couldn't remove directory: Failure #删除时有错误,说明目录有文件
sftp> rmdir testdir
Couldn't remove directory: Failure
sftp> ls
dir test01.txt testdir
#进入我们要删除的testdir目录,并删除里面的txt文件
sftp> cd testdir/
sftp> ls
test.txt test01.txt
sftp> rm t
test.txt test01.txt
#删除 test.txt和test01.txt文件
sftp> rm test.txt
Removing /home/tdops/testdir/test.txt
sftp> rm test01.txt
Removing /home/tdops/testdir/test01.txt
sftp> cd ..
sftp> ls
dir test01.txt testdir
#在删除testdir目录
sftp> rmdir testdir/
sftp> ls -l
drwxr-xr-x 2 tdops users 40 Dec 5 12:48 dir
-rw-r--r-- 1 tdops users 22 Dec 5 12:44 test01.txt
#用![command]执行命令
sftp> !cat /etc/passwd
root:x:0:0:root:/root:/bin/bash
bin:x:1:1:bin:/bin:/sbin/nologin
daemon:x:2:2:daemon:/sbin:/sbin/nologin
adm:x:3:4:adm:/var/adm:/sbin/nologin
3、SSH密钥对验证
OpenSSH:SSH密钥对认证2019/09/30
配置SSH服务器以使用密钥对身份验证登录。
为客户端创建一个私钥,为服务器创建一个公钥。
[1] 由每个用户创建密钥对,因此在SSH服务器主机上以普通用户身份登录并按如下方式工作。
[tdops@sshserver ~]$ ssh-keygen
Generating public/private rsa key pair.
Enter file in which to save the key (/home/tdops/.ssh/id_rsa):
Enter passphrase (empty for no passphrase): ##输入密码 liang123
Enter same passphrase again:
Your identification has been saved in /home/tdops/.ssh/id_rsa.
Your public key has been saved in /home/tdops/.ssh/id_rsa.pub.
The key fingerprint is:
SHA256:dGhKkO7u9OKhG2TPvxf3BCfziD81fh/r/alPiu2qsNY tdops@sshserver
The key's randomart image is:
+---[RSA 3072]----+
| .. |
| .. . |
| . . + . |
| .. + .+ . |
| o. . S. B |
| o o. o o = |
| ..= ..+ = . o |
| +o+ .+Eo = + =|
| o+o.=+ ..+o*+*=|
+----[SHA256]-----+
[tdops@sshserver ~]$ ll ~/.ssh
total 12
-rw-------. 1 tdops users 2655 Dec 5 13:34 id_rsa
-rw-r--r--. 1 tdops users 569 Dec 5 13:34 id_rsa.pub
-rw-r--r--. 1 tdops users 692 Oct 20 10:04 known_hosts
[tdops@sshserver ~]$ cp ~/.ssh/id_rsa.pub ~/.ssh/authorized_keys
[tdops@sshserver ~]$
[tdops@sshserver ~]$
[2] 将在服务器上创建的私钥转移到客户端,然后可以使用Key-Pair身份验证登录。
[tdops@sshclient ~]$ cd ~
[tdops@sshclient ~]$ ls
[tdops@sshclient ~]$ mkdir ~/.ssh
[tdops@sshclient ~]$ chmod 700 ~/.ssh
[tdops@sshclient ~]$ scp tdops@192.168.6.58:/home/tdops/.ssh/id_r* .ssh/
The authenticity of host '192.168.6.58 (192.168.6.58)' can't be established.
ECDSA key fingerprint is SHA256:oqQ+6i8P+QVs1UD7KlWGRTbavvD9P3BPWtWCdHyQtBY.
Are you sure you want to continue connecting (yes/no/[fingerprint])? yes
Warning: Permanently added '192.168.6.58' (ECDSA) to the list of known hosts.
tdops@192.168.6.58's password:
id_rsa 100% 2655 1.9MB/s 00:00
id_rsa.pub 100% 569 543.6KB/s 00:00
[tdops@sshclient ~]$ ssh tdops@192.168.6.58
Enter passphrase for key '/home/tdops/.ssh/id_rsa': ##输入密码 liang123
Web console: https://lianglab:9090/ or https://192.168.6.58:9090/
Last login: Sat Dec 5 12:47:03 2020
[tdops@sshserver ~]$ exit
logout
[3] 如果设置[PasswordAuthentication no],则更加安全。
[root@sshserver ~]# vi /etc/ssh/sshd_config
# line 73: change to [no]
PasswordAuthentication no
[root@sshserver ~]# systemctl restart sshd
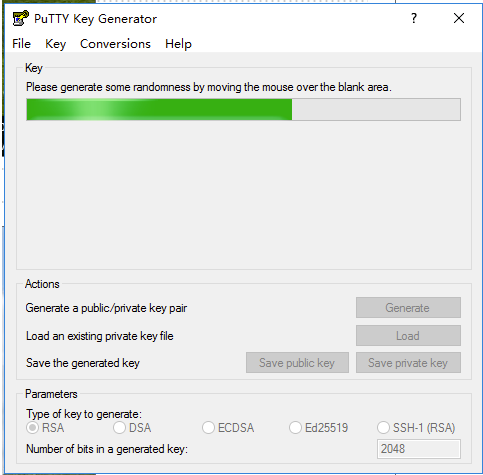
[4] 运行[Putty]中包含的[Puttygen.exe]。(也放置在[Putty.exe]文件夹中)。
如果不包括在内,请从官方网站(www.chiark.greenend.org.uk/~sgtatham/putty/)下载。
启动[Puttygen.exe]后,在以下窗口中单击[加载]按钮。

ssh-rsa AAAAB3NzaC1yc2EAAAABJQAAAQEAmV8IIRNWKiOA3xmH+harMU9M9244ryNKNUqC1tkinBTP2HiTdfgs7Jty14UJ011g3WtfGkU98acmumpH6DK0inM662fG+PpYeHgENCzgavUQ8WQuS8026yLhmghzsRQ7AnMeAIFsMmHdeUNzXkGknlUGTw3SwHihQlC7+pJZsa05mN8UNoDmE/yr4SWqYOe6MO+VLHUgpDRfvEpuBwS6KahdXeW/LM1l8PnC8gHMbAG1kc1W8IDvrZRHHFSBd1tbtPbt4DBNmn62zsn0uGHPNmqr0+oEJztNgJoqCisjDCLARL8KOmb3Glj+7cLR5s1z3rBDWbvN/1CJm4XysrTN+Q== rsa-key-20201205
Windows主机中生产的key添加到我们要登录的centos主机上
[tdops@sshserver .ssh]$ cat /home/tdops/.ssh/authorized_keys
ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAABgQCgzX4uLLO2Pq40Qn+it+leDtICiJHAf3jZr1NHuXaMs3QDA7kRDPzcL/YyTbrIOf2Y1QR/peEnJjChNQ7VfCD200Yq3LR0XsFVSqUzAwe+S7f3PhqJG5auI5w9iiuS2o2Eywk2PIV7CCSAHxszyMrsmxNwip/SkbdAg5w/ZVR+q6Uxj6h+vVsAqndsr94TI4xK97pVW2b3p3EFMogrrRDdtE4HfIA3Kkis5YHLauEjbgynCW3NrIMD3HHEN9mkgGl4V+GDQ1CbTFBc5B0fen41dGwJxpepGLH/9iRU8lfF3ZIwdasw0qdPFykRplPFF/pGKCsLTBOdiwqYskXeLKJIMVy8PHAEqKsMGdGP3E2hW2aflqKAnWh4Q7yYssB4ZLEbq+2sHC6HYL/VDaROHGsR6ShYgUcm8TqC0OjiGGzKH2OnF4W5VUkhLRNMEXmqIoA56HSJOZTKZgsxBQ5Gu7OH9Rrm1WJ5bLd5Pw5g/ijWpU6xrSEkBfuk61JargAAAX8= tdops@sshserver
ssh-rsa AAAAB3NzaC1yc2EAAAABJQAAAQEAmV8IIRNWKiOA3xmH+harMU9M9244ryNKNUqC1tkinBTP2HiTdfgs7Jty14UJ011g3WtfGkU98acmumpH6DK0inM662fG+PpYeHgENCzgavUQ8WQuS8026yLhmghzsRQ7AnMeAIFsMmHdeUNzXkGknlUGTw3SwHihQlC7+pJZsa05mN8UNoDmE/yr4SWqYOe6MO+VLHUgpDRfvEpuBwS6KahdXeW/LM1l8PnC8gHMbAG1kc1W8IDvrZRHHFSBd1tbtPbt4DBNmn62zsn0uGHPNmqr0+oEJztNgJoqCisjDCLARL8KOmb3Glj+7cLR5s1z3rBDWbvN/1CJm4XysrTN+Q== rsa-key-20201205
[tdops@sshserver .ssh]$

4、SFTP服务器+Chroot配置
仅配置SFTP + Chroot。
应用了此设置的某些用户只能使用SFTP和chroot目录进行访问。
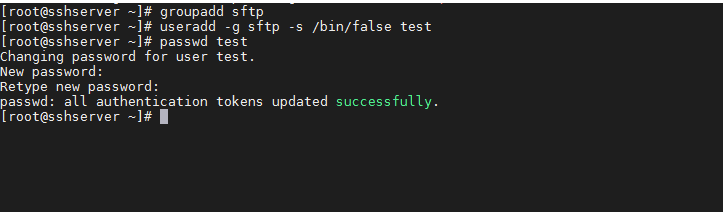
[1] SFTP创建一个组
# groupadd sftp
创建一个sftp用户test并加入到穿件sftp组中,同时修改test用户的密码
# useradd -g sftp -s /bin/false test
-g 加入到sftp组
-s 禁止使用命令
# passwd test #密码liang123
[2] 新建/opt/sftp目录,并将它指定为test组用户的home目录
[root@sshserver ~]# mkdir -p /opt/sftp
[root@sshserver ~]# usermod -d /opt/sftp test
编辑/etc/ssh/sshd_config
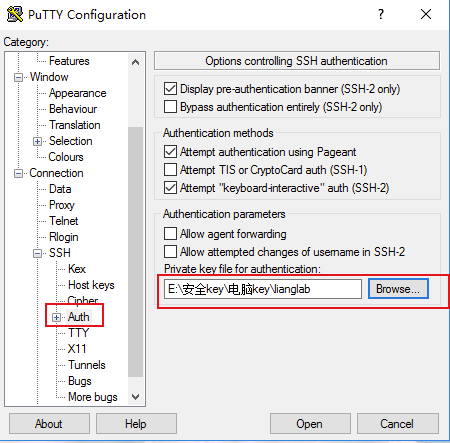
[root@sshserver ~]# vi /etc/ssh/sshd_config
将如下这行用#符号注释掉
#Subsystem sftp /usr/libexec/openssh/sftp-server
并在文后添加如下几行内容然后保存
Subsystem sftp internal-sftp
Match Group sftp
ChrootDirectory /opt/sftp
ForceCommand internal-sftp
AllowTcpForwarding no
X11Forwarding no
ChrootDirectory 指定登录后的根目录,并且将用户限制在该目录及其子目录下。
这里有条规则
1、由 ChrootDirectory 指定的目录开始一直往上到系统根目录为止的目录拥有者都只能是 root
2、由 ChrootDirectory 指定的目录开始一直往上到系统根目录为止都不可以具有群组写入权限(最大权限 755)
ChrootDirectory设置的目录权限及其所有的上级文件夹权限,属主和属组必须是root;
ChrootDirectory设置的目录权限及其所有的上级文件夹权限,只有属主能拥有写权限,也就是说权限最大设置只能是755。
[3] 设置Chroot目录权限
[root@sshserver ~]# chown root:sftp /opt/sftp/
[root@sshserver ~]# chmod 755 /opt/sftp/
[4] 创建一个目录 sftp用户上传目录
mkdir /opt/sftp/upload
chown test:sftp /opt/sftp/upload/
chmod 755 /opt/sftp/upload/
[5] 重启SSH服务
#systemctl restart sshd.service

[tdops@sshclient ~]$ sftp test@192.168.6.58
test@192.168.6.58's password:
Connected to test@192.168.6.58.
sftp> pwd
Remote working directory: /
sftp> ls
upload
sftp> cd upload/
sftp> ls
sftp> pwd
Remote working directory: /upload
sftp> !dir
sftp> !ls
sftp>

5、Sftp服务器部署案例
#1、创建sftp组
groupadd sftpadmin
#2、创建一个用户sftpadmin
useradd -g sftpadmin -s /bin/false sftpadmin
#3、设置sftpadmin用户的密码
passwd sftpadmin ## 例如BhYzk4MDAwNG
#4、创建一个sftp的上传目录
mkdir /data/sftp
#5、修改用户sftpadmin所在的目录
usermod -d /data/sftp sftpadmin
#6、设定Chroot目录权限
chown -R root:sftpadmin /data/sftp
chmod 755 /data/sftp/
#7、关闭SElinux
vi /etc/sysconfig/selinux
#找到如下这行
SELINUX=enforcing
#修改为
SELINUX=permissive或者SELINUX=disabled
#保存退出
#8、编辑sshd配置文件并重启ssh服务
root@sec-p-050056 src]# cat /etc/ssh/sshd_config
#HostKey /etc/ssh/ssh_host_rsa_key
#HostKey /etc/ssh/ssh_host_ecdsa_key
#HostKey /etc/ssh/ssh_host_ed25519_key
SyslogFacility AUTHPRIV
AuthorizedKeysFile .ssh/authorized_keys
PasswordAuthentication yes
ChallengeResponseAuthentication no
#GSSAPIAuthentication yes
GSSAPICleanupCredentials no
UsePAM yes
X11Forwarding yes
#UsePrivilegeSeparation sandbox # Default for new installations.
AcceptEnv LANG LC_CTYPE LC_NUMERIC LC_TIME LC_COLLATE LC_MONETARY LC_MESSAGES
AcceptEnv LC_PAPER LC_NAME LC_ADDRESS LC_TELEPHONE LC_MEASUREMENT
AcceptEnv LC_IDENTIFICATION LC_ALL LANGUAGE
AcceptEnv XMODIFIERS
LogLevel VERBOSE
#Subsystem sftp internal-sftp
#Match Group sftpadmin
# AllowTcpForwarding no
# ForceCommand internal-sftp
# ChrootDirectory %h
Subsystem sftp internal-sftp -l INFO -f LOCAL6
# add Below lines at the end of file
Match Group sftpadmin
#ChrootDirectory /home/sftp
X11Forwarding no
AllowTcpForwarding no
ChrootDirectory /data/sftp/%u
ForceCommand internal-sftp -f LOCAL6 -l INFO
#Ciphers aes128-ctr,aes192-ctr,aes256-ctr,aes128-cbc,3des-cbc,cast128-cbc,aes192-cbc,aes256-cbc
systemctl restart sshd
systemctl status sshd
#9、创建存放sftp账号目录和文件
mkdir -p /usr/local/src/users
touch /usr/local/src/users/user.txt
#10、创建自动添加sftp账号脚本并设置执行权限
#!/bin/bash
. /etc/init.d/functions
Path=/usr/local/src/users
Passwd=`echo $(date +%t%N)$RANDOM|md5sum|cut -c 2-12`
UserDb=$Path/user.txt
if [ -z "$1" ];then
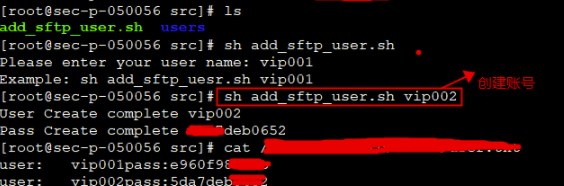
echo "Please enter your user name: vip001"
echo "Example: sh add_sftp_uesr.sh vip001"
exit
fi
useradd -d /data/sftp/$1 -G sftpadmin -s /bin/false $1
chmod -R 755 /data/sftp/$1
chown root:sftpadmin /data/sftp/$1
mkdir /data/sftp/$1/file
chown -R root:root /data/sftp/$1/file
chmod 777 /data/sftp/$1/file
echo "$Passwd"|passwd --stdin $1 >&/dev/null
echo "User Create complete $1"
echo "Pass Create complete $Passwd"
echo -e "user:\t$1pass:$Passwd" >>$UserDb
chmod 755 /usr/local/src/add_sftp_user.sh
6、一键部署sftp服务环境脚本
#############################一键部署sftp服务环境脚本################################
#!/bin/bash
#sftp server auto scripts
#linglab 2018-10-25
groupadd sftpadmin
useradd -g sftpadmin -s /bin/false sftpadmin
mkdir /data/sftp -p
usermod -d /data/sftp sftpadmin
chown -R root:sftpadmin /data/sftp
chmod 755 /data/sftp/
echo " ">/etc/ssh/sshd_config
cat >>/etc/ssh/sshd_config<<EOF
#HostKey /etc/ssh/ssh_host_rsa_key
#HostKey /etc/ssh/ssh_host_ecdsa_key
#HostKey /etc/ssh/ssh_host_ed25519_key
SyslogFacility AUTHPRIV
AuthorizedKeysFile .ssh/authorized_keys
PasswordAuthentication yes
ChallengeResponseAuthentication no
#GSSAPIAuthentication yes
GSSAPICleanupCredentials no
UsePAM yes
X11Forwarding yes
#UsePrivilegeSeparation sandbox # Default for new installations.
AcceptEnv LANG LC_CTYPE LC_NUMERIC LC_TIME LC_COLLATE LC_MONETARY LC_MESSAGES
AcceptEnv LC_PAPER LC_NAME LC_ADDRESS LC_TELEPHONE LC_MEASUREMENT
AcceptEnv LC_IDENTIFICATION LC_ALL LANGUAGE
AcceptEnv XMODIFIERS
LogLevel VERBOSE
#Subsystem sftp internal-sftp
#Match Group sftpadmin
# AllowTcpForwarding no
# ForceCommand internal-sftp
# ChrootDirectory %h
Subsystem sftp internal-sftp -l INFO -f LOCAL6
# add Below lines at the end of file
Match Group sftpadmin
#ChrootDirectory /home/sftp
X11Forwarding no
AllowTcpForwarding no
ChrootDirectory /data/sftp/%u
ForceCommand internal-sftp -f LOCAL6 -l INFO
#Ciphers aes128-ctr,aes192-ctr,aes256-ctr,aes128-cbc,3des-cbc,cast128-cbc,aes192-cbc,aes256-cbc
EOF
mkdir -p /usr/local/src/users
touch /usr/local/src/users/user.txt
echo -n '#!/bin/bash
. /etc/init.d/functions
Path=/usr/local/src/users
Passwd=`echo $(date +%t%N)$RANDOM|md5sum|cut -c 2-12`
UserDb=$Path/user.txt
if [ -z "$1" ];then
echo "Please enter your user name: vip001"
echo "Example: sh add_sftp_uesr.sh vip001"
exit
fi
useradd -d /data/sftp/$1 -G sftpadmin -s /bin/false $1
chmod -R 755 /data/sftp/$1
chown root:sftpadmin /data/sftp/$1
mkdir /data/sftp/$1/file
chown -R root:root /data/sftp/$1/file
chmod 777 /data/sftp/$1/file
echo "$Passwd"|passwd --stdin $1 >&/dev/null
echo "User Create complete $1"
echo "Pass Create complete $Passwd"
echo -e "user:\t$1pass:$Passwd" >>$UserDb' > /usr/local/src/add_sftp_user.sh
chmod 755 /usr/local/src/add_sftp_user.sh
systemctl restart sshd
systemctl status sshd
7、使用SSHpass
使用SSHPass在密码验证时自动输入密码。
这很方便,但存在安全隐患(密码泄漏),如果使用,请格外小心。
[1] 安装sshpass命令
# install from EPEL
[root@sshclient ~]# dnf --enablerepo=epel -y install sshpass
[2] 使用 sshpass
# 使用-p参数指定登录密码
[root@sshclient ~]# sshpass -p tdops密码 ssh tdops@192.168.6.58 hostname
sshserver
[root@sshclient ~]#
# [-f file] : from file
[root@sshclient ~]# echo 'tdops密码' > sshpass.txt
[root@sshclient ~]# chmod 600 sshpass.txt
[root@sshclient ~]# sshpass -f sshpass.txt ssh tdops@192.168.6.58 hostname
sshserver
# [-e] : from environment variable
[root@sshclient ~]# export SSHPASS=tdops密码
[root@sshclient ~]# sshpass -e ssh tdops@192.168.6.58 hostname
sshserver
[root@sshclient ~]#
# 通过scp上传文件
[root@sshclient ~]# sshpass -p tdops密码 scp local_file tdops@192.168.6.58:remote_file
# 通过scp下载文件
[root@sshclient ~]# sshpass -p tdops密码 scp tdops@192.168.6.58:remote_file local_file
广告时间:
- 关于我 :全国7*24高效代维服务
- 微信:lianglab
- QQ:867266199
- 淘宝店:全国7*24高效代维服务
- 全国高效代维:为中小型企业,提供云计算咨询代维、架构设计、降低成本。



 浙公网安备 33010602011771号
浙公网安备 33010602011771号