[HDCTF2019]bbbbbbrsa
打开以后是两个文件,一个是py文件,另一个是.txt文件,打开看到
from base64 import b64encode as b32encode
from gmpy2 import invert,gcd,iroot
from Crypto.Util.number import *
from binascii import a2b_hex,b2a_hex
import random
flag = "******************************"
nbit = 128
p = getPrime(nbit)
q = getPrime(nbit)
n = p*q
print p
print n
phi = (p-1)*(q-1)
e = random.randint(50000,70000)
while True:
if gcd(e,phi) == 1:
break;
else:
e -= 1;
c = pow(int(b2a_hex(flag),16),e,n)
print b32encode(str(c))[::-1]
# 2373740699529364991763589324200093466206785561836101840381622237225512234632
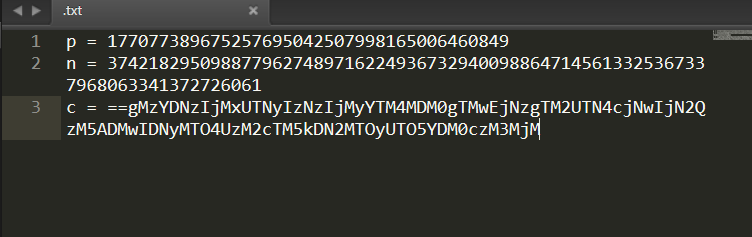
.txt文件内容为:
这道题有两个考点,一个是C,开始看以为是base32,实际上是base64,但是是反序的,简单弄一下得到C。
第二个是E,需要爆破一下即可。上才艺!
import gmpy2
import hashlib
import binascii
from Crypto.Util.number import *
'''
c = "==gMzYDNzIjMxUTNyIzNzIjMyYTM4MDM0gTMwEjNzgTM2UTN4cjNwIjN2QzM5ADMwIDNyMTO4UzM2cTM5kDN2MTOyUTO5YDM0czM3MjM"
print(c[::-1])
'''
c = 2373740699529364991763589324200093466206785561836101840381622237225512234632
p = 177077389675257695042507998165006460849
n = 37421829509887796274897162249367329400988647145613325367337968063341372726061
q = n//p
phi = (p-1)*(q-1)
for e in range(50000,70000):
if(gmpy2.gcd(e,phi)==1):
d = gmpy2.invert(e,phi)
m = gmpy2.powmod(c,d,n)
print(str(long_to_bytes(m)))
会得到好多结果,在这里可以手动选一下,还可以简单进行一下匹配即可
if 'flag' in flag or 'CTF' in flag or ("{" in flag and '}'in flag):
print(flag)
得到flag为flag{rs4_1s_s1mpl3!#}

