elasticsearch linux 上安装
以下对应版本 8.11.3
1、下载安装包,放到服务器指定目录下:
2、解压,到指定文件夹 命令 tar -xzf elasticsearch-8.11.3-linux-x86_64.tar.gz
3、创建用户并授权:
sudo useradd es
sudo passwd es
用户授权指定目录权限: chown -R es:es /opt/module/es-7.8.0
给新创建的普通用户设置sudo权限 vim /etc/sudoers
在root ALL(ALL) ALL下面新增
es ALL=(ALL) ALL
或:
# 使用root用户执行
visudo
# 在 root ALL(ALL) ALL下面新增
es ALL=(ALL) ALL
4、 前置准备
每个进程可以打开的文件数的限制 vim /etc/security/limits.conf 末尾新增:
es soft nofile 65536
es hard nofile 65536
每个进程可以打开的文件数的限制;操作系统级别对每个用户创建的进程数的限制
vim /etc/security/limits.d/20-nproc.conf
es soft nofile 65536
es hard nofile 65536
* hard nproc 4096 注:* 带表 Linux 所有用户名称
sudo vim /etc/sysctl.conf
一个进程可以拥有的 VMA(虚拟内存区域)的数量,默认值为 65536
vm.max_map_count=655360
保存后执以下命令使配置生效
sudo sysctl -p
5、修改JVM配置 根据实际情况修改-修改 elasticsearch.yml 配置参数
##
-Xms1g -
Xmx1g
##
主要修改以下参数值
cluster.name: my-application node.name: node-1 path.data: ./data path.logs: ./logs network.host: 0.0.0.0 http.port: 9200 cluster.initial_master_nodes: ["node-1"]
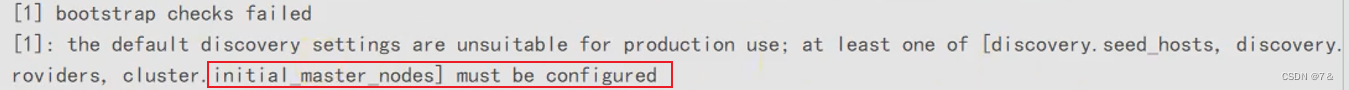
Note:cluster.initial_master_nodes必须配置(即使名字跟默认的一样,也要放开注释),否则启动失败,失败日志「elasticsearch.log」说如下:
# Enable security features
xpack.security.enabled: false
xpack.security.enrollment.enabled: false
# Enable encryption for HTTP API client connections, such as Kibana, Logstash, and Agents xpack.security.http.ssl: enabled: false keystore.path: certs/http.p12 # Enable encryption and mutual authentication between cluster nodes xpack.security.transport.ssl: enabled: false verification_mode: certificate keystore.path: certs/transport.p12 truststore.path: certs/transport.p12
https配置为 false
新版本下,不配置ssl可能不能添加密码,相关配置如下:
1)通过如下命令创建CA
./bin/elasticsearch-certutil ca
2)颁发证书
./bin/elasticsearch-certutil cert --ca elastic-stack-ca.p12
执行成功后后在节点路径中会增加 elastic-certificates.p12 和 elastic-stack-ca.p12 文件,
3)将这两个文件移动到 config 目录中
4)配置文件中:
xpack.security.enabled: true xpack.security.transport.ssl.enabled: true xpack.security.transport.ssl.verification_mode: certificate xpack.security.transport.ssl.client_authentication: required xpack.security.transport.ssl.keystore.path: elastic-certificates.p12 xpack.security.transport.ssl.keystore.password: 123qwe xpack.security.transport.ssl.truststore.path: elastic-certificates.p12 xpack.security.transport.ssl.truststore.password: 123qwe
6、启动es--在es用户下面执行
bin/elasticsearch -d
jps
ps -ef | grep es
命令行验证:
curl 127.0.0.1:9200
带密码:
curl -u elastic:"password" 127.0.0.1:19210

7、重启:
ps -ef|gerp elastic
kill -9 xxxx
8、重启脚本
#!/bin/bash #chkconfig: 2345 54 26 #description: elasticsearch #processname: elasticsearch ES_HOME=/var/local/elasticsearch start(){ su - es -c "$ES_HOME/bin/elasticsearch -d -p pid" echo "es is started" } stop(){ pid=`cat $ES_HOME/pid` kill -9 $pid echo "es is stopped" } status(){ ps aux | grep $ES_HOME } restart(){ stop sleep 1 start } case "$1" in "start") start ;; "stop") stop ;; "status") status ;; "restart") restart ;; *) echo "支持指令:$0 start|stop|restart|status" ;; esac
在/etc/init.d目录下创建启动、关闭服务的脚本,脚本中要设置运行级别、启动优先级、关闭优先级
chmod +x /etc/init.d/xxx
# 添加开机自启 chkconfig --add xxx
# 状态设置为启动 chkconfig xxx on
service elastic status
service elastic start
service elastics stop
9、添加密码:
修改配置文件: xpack.security.enabled: true 重启生效

执行命令:
./bin/elasticsearch-setup-passwords interactive
报错处理
当elasticsearch 设置用户名密码认证: [elk@goya config]$ elasticsearch-setup-passwords interactive Failed to authenticate user 'elastic' against https://192.168.88.3:9200/_security/_authenticate?pretty Possible causes include: * The password for the 'elastic' user has already been changed on this cluster * Your elasticsearch node is running against a different keystore This tool used the keystore at /usr/local/elasticsearch/config/elasticsearch.keystore You can use the `elasticsearch-reset-password` CLI tool to reset the password of the 'elastic' user ERROR: Failed to verify bootstrap password [elk@goya config]$ elasticsearch-reset-password -u elastic This tool will reset the password of the [elastic] user to an autogenerated value. The password will be printed in the console. Please confirm that you would like to continue [y/N]y Password for the [elastic] user successfully reset. New value: Kzp6I0Jvo8cS9EBRWe24(系统自动生成的密码) 说明:如果想设置自己想用的密码需要加参数-i [root@goya1 certs]# elasticsearch-reset-password -u elastic -i warning: ignoring JAVA_HOME=/app/elasticsearch/jdk; using bundled JDK This tool will reset the password of the [elastic] user. You will be prompted to enter the password. Please confirm that you would like to continue [y/N]y Enter password for [elastic]: Re-enter password for [elastic]: Password for the [elastic] user successfully reset.
10、用户设置
下面对于用户设置
1. 内置用户
执行下面对应命令,重置密码(自动生成)
bin/elasticsearch-reset-password --batch --user elastic
bin/elasticsearch-reset-password --batch --user logstash_system
bin/elasticsearch-reset-password --batch --user kibana_system
若是需要自己指定密码
利用重置的密码,去修改为自己需要的密码,注意,url里对应的用户, password 为
curl -XPUT -u elastic(用户):"otpKRXJZqe9Dzs5iXTjO"(密码) 'http://localhost:9200/_security/user/elastic(对应用户)/_password' -H "Content-Type: application/json" -d '{ "password": "1234qwer."(需要修改的密码)}'
2. 自己添加用户
创建 kibana_system用户
bin/elasticsearch-users useradd zhyqin (添加用户)
赋角色权限: 这一步要执行,不然无法访问
bin/elasticsearch-users roles -a superuser zhyqin ( 超级管理员角色)
bin/elasticsearch-users roles -a kibana_system zhyqin (kibana的用户角色 )
创建 logstash用户
bin/elasticsearch-users useradd logstash_zhyqin
bin/elasticsearch-users roles -a superuser logstash_zhyqin
bin/elasticsearch-users roles -a logstash_system logstash_zhyqin
自己创建用户密码修改
bin/elasticsearch-users passwd logstash_system
3. 测试是否能访问
es容器内测时
curl -u logstash_zhyqin:"1234qwer." 'http://localhost:9200/'
其他容器测试访问es
curl -u zhyqin:"1234qwer." 'http://elasticsearch:9200'
参考博客:https://blog.csdn.net/m0_52735414/article/details/128847505
参考链接:https://blog.csdn.net/shinexunmeng/article/details/132179443






【推荐】编程新体验,更懂你的AI,立即体验豆包MarsCode编程助手
【推荐】凌霞软件回馈社区,博客园 & 1Panel & Halo 联合会员上线
【推荐】抖音旗下AI助手豆包,你的智能百科全书,全免费不限次数
【推荐】博客园社区专享云产品让利特惠,阿里云新客6.5折上折
【推荐】轻量又高性能的 SSH 工具 IShell:AI 加持,快人一步
· 【.NET】调用本地 Deepseek 模型
· CSnakes vs Python.NET:高效嵌入与灵活互通的跨语言方案对比
· DeepSeek “源神”启动!「GitHub 热点速览」
· 我与微信审核的“相爱相杀”看个人小程序副业
· Plotly.NET 一个为 .NET 打造的强大开源交互式图表库
2023-01-10 JVM 调整和优化