[RH134] 6-selinux
1.什么是selinux
Selinux:Security-Enhanced Linux,安全增强型Linux。
Selinux的功能有点类似于windows下360软件在我们执行某个比较敏感或风险较高的操作时,对我们进行安全提示(是都允许操作)。Selinux实现类似的安全控制功能。
例如,我们使用CMD创建一个网络用户的时候,360会进行安全提示:
2.selinux开启与关闭
主动访问控制(DAC):在没有selinux的情况下,我们是否可以访问某个文件,是依赖于这个文件的权限的,例如777表示所有用户都可以对这个文件进行读写和执行。
Selinux:在有selinux的情况下,selinux会为所有的文件和进程都分配一个标签,这个标签我们称之为标识或上下文。只有相互对应的进程和文件之间才能访问,对应关系不正确则无法访问。
1)开启selinux
setenforce 1
2)关闭selinux
setenforce 0
3.selinux使用实验
1)实验准备:
首先,开启selinux: setenforce 1
我们安装一个httpd服务器,然后启动:
yum install httpd -y systemctl start httpd
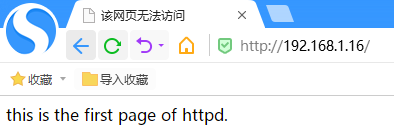
在/var/www/html下创建一个文件index.html写上任意内容。
我们访问http://192.168.1.16,可以看到默认页面(index.html)的内容:
2)查看httpd进程的selinux标签
[root@centos7 html]# ps axZ | grep httpd system_u:system_r:httpd_t:s0 1829 ? Ss 0:00 /usr/sbin/httpd -DFOREGROUND system_u:system_r:httpd_t:s0 1830 ? S 0:00 /usr/sbin/httpd -DFOREGROUND system_u:system_r:httpd_t:s0 1831 ? S 0:00 /usr/sbin/httpd -DFOREGROUND system_u:system_r:httpd_t:s0 1832 ? S 0:00 /usr/sbin/httpd -DFOREGROUND system_u:system_r:httpd_t:s0 1833 ? S 0:00 /usr/sbin/httpd -DFOREGROUND system_u:system_r:httpd_t:s0 1834 ? S 0:00 /usr/sbin/httpd -DFOREGROUND system_u:system_r:httpd_t:s0 4532 ? S 0:00 /usr/sbin/httpd -DFOREGROUND
3)我们再查看/var/www/html/index.html的selinux标签
[root@centos7 html]# ls -ldZ /var/www/html drwxr-xr-x. root root system_u:object_r:httpd_sys_content_t:s0 /var/www/html [root@centos7 html]# ls -ldZ /var/www/html/index.html -rw-r--r--. root root unconfined_u:object_r:httpd_sys_content_t:s0 /var/www/html/index.html
我们可以看到,/var/www/html目录和/var/www/html/index.html文件的标签是 httpd_sys_content_t ,而httpd进程的标签是 httpd_t 。http_t标签可以访问httpd_sys_content_t标签的文件。
4)修改httpd的配置文件,添加访问/www的权限
/www 是在根目录下创建的www目录。
修改/etc/httpd/conf/httpd.conf位置文件,添加如下标黄部分的内容:
<Directory "/var/www"> AllowOverride None # Allow open access: Require all granted </Directory> <Directory "/www"> AllowOverride None # Allow open access: Require all granted </Directory>
然后,重启httpd:
systemctl restart httpd
5)在/var/www/html下创建/www的软连接
cd /var/www/html ln -s /www www
[root@centos7 html]# ll total 4 -rw-r--r--. 1 root root 33 Mar 26 14:44 index.html lrwxrwxrwx. 1 root root 4 Mar 26 15:00 www -> /www
并在/www下创建index.html文件,内容为:
echo "this is the index.html file in /www." > /www/index.html
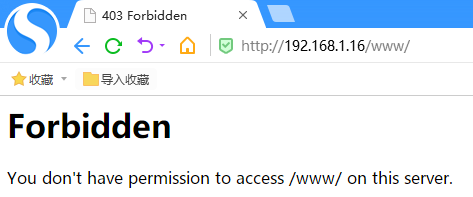
6)访问http://192.168.1.16/www
当我们访问http://192.168.1.16/www时,页面理论上应该显示/www/index.html的内容。但是当前页面显示:
7)我们查看/www/index.html的selinux标签
[root@centos7 html]# ls -ldZ /www/index.html -rw-r--r--. root root unconfined_u:object_r:default_t:s0 /www/index.html
可以看到/www/index.html文件的标签为 default_t ,表标签的文件无法被 httpd_t 的进程所访问,所以页面显示forbidden。
8)修改/www目录下所有文件的selinux标签
[root@centos7 html]# chcon -R -t httpd_sys_content_t /www/
将/www目录以及目录下的所有文件的selinux标签都修改为 httpd_sys_content_t 。
[root@centos7 /]# ls -ldZ /www drwxr-xr-x. root root unconfined_u:object_r:httpd_sys_content_t:s0 /www [root@centos7 /]# ls -ldZ /www/index.html -rw-r--r--. root root unconfined_u:object_r:httpd_sys_content_t:s0 /www/index.html
9)此时,再次访问http://192.168.1.16/www
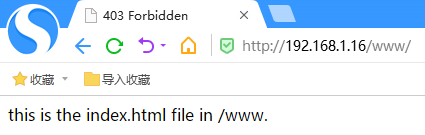
访问成功,说明标签只要对应上,就可以访问。
4.selinux其他操作
1)还原/www的selinux标签
[root@centos7 /]# restorecon -R /www
在查看/www和其下文件的标签:
[root@centos7 /]# ls -ldZ /www drwxr-xr-x. root root unconfined_u:object_r:default_t:s0 /www [root@centos7 /]# ls -ldZ /www/index.html -rw-r--r--. root root unconfined_u:object_r:default_t:s0 /www/index.html
可以看到,标签已经被还原了。
2)设置默认的selinux标签
可以对某个目录设置一个默认的selinux标签,用于其下创建的所有新文件。
[root@centos7 /]# semanage fcontext -a -t httpd_sys_content_t '/www(/.*)?'
其中的正则表达式'/www(/.*)?'表示/www目录和其他所有文件和子目录。
设置完默认标签后,使用restorecon来让其恢复为默认标签:
[root@centos7 /]# restorecon -R /www
此时,查看标签:
[root@centos7 /]# ls -ldZ /www drwxr-xr-x. root root unconfined_u:object_r:httpd_sys_content_t:s0 /www [root@centos7 /]# ls -ldZ /www/index.html -rw-r--r--. root root unconfined_u:object_r:httpd_sys_content_t:s0 /www/index.html [root@centos7 /]# ls -ldZ /www/ok.html -rw-r--r--. root root unconfined_u:object_r:httpd_sys_content_t:s0 /www/ok.html
可以看到,/www目录以及其下所有文件和子目录(包括新创建文件目录等)的标签都已经变为新的默认标签 httpd_sys_content_t 。
3)删除默认标签
semanage fcontext -d -t httpd_sys_content_t 'www(/.*)?'
将创建默认标签命令中的"-a"选项变为"-d"选项就是删除。
4)参照其他目录或文件的上下文来设置
chron -R --reference=/var/www/html /www
这里参照/var/www/html的上下文来设置/www的标签。让httpd能够访问。
5)万能上下文
如果我们不清楚设置什么样的上下文,则可以使用一个叫做 public_content_t 的万能上下文。
chcon -R -t public_content_t /www
这种万能上下文所标记的文件,所有的进程都可以访问。
5.selinux的模式
selinux有两种模式:
- enforceing:强制模式,必须要满足selinux的条件,不满足的话,则阻止访问并告警。
- permissive:允许模式,可以不满足selinux的条件,也可以访问,但是由告警。
当我们访问不到服务的时候,就应该想想是不是selinux导致的,可以临时关闭selinux:
setenforce 0 # 即切换到permissive模式
如果想要切换到enforcing模式,则执行:
setenforce 1 # 即切换到enforcing模式
以上的切换方式(开关)是临时的,重启系统后会恢复到默认开启(enforcing)的状态。
如果我们想要永久使用关闭selinux(或设置一种模式永久生效),则需要修改 /etc/selinu/config 配置文件:
# This file controls the state of SELinux on the system. # SELINUX= can take one of these three values: # enforcing - SELinux security policy is enforced. # permissive - SELinux prints warnings instead of enforcing. # disabled - No SELinux policy is loaded. #SELINUX=enforcing SELINUX=disabled # SELINUXTYPE= can take one of three two values: # targeted - Targeted processes are protected, # minimum - Modification of targeted policy. Only selected processes are protected. # mls - Multi Level Security protection. SELINUXTYPE=targeted
将SELINUX=enforcing修改为SELINUX=disabled,重启服务器后,selinux即为默认不启用。
6.selinux布尔值
1)查看selinux的所有布尔值
getsebool -a

[root@centos7 ~]# getsebool -a abrt_anon_write --> off abrt_handle_event --> off abrt_upload_watch_anon_write --> on antivirus_can_scan_system --> off antivirus_use_jit --> off auditadm_exec_content --> on authlogin_nsswitch_use_ldap --> off authlogin_radius --> off authlogin_yubikey --> off awstats_purge_apache_log_files --> off boinc_execmem --> on cdrecord_read_content --> off cluster_can_network_connect --> off cluster_manage_all_files --> off cluster_use_execmem --> off cobbler_anon_write --> off cobbler_can_network_connect --> off cobbler_use_cifs --> off cobbler_use_nfs --> off collectd_tcp_network_connect --> off condor_tcp_network_connect --> off conman_can_network --> off conman_use_nfs --> off container_connect_any --> off container_manage_cgroup --> off container_use_cephfs --> off cron_can_relabel --> off cron_system_cronjob_use_shares --> off cron_userdomain_transition --> on cups_execmem --> off cvs_read_shadow --> off daemons_dump_core --> off daemons_enable_cluster_mode --> off daemons_use_tcp_wrapper --> off daemons_use_tty --> off dbadm_exec_content --> on dbadm_manage_user_files --> off dbadm_read_user_files --> off deny_execmem --> off deny_ptrace --> off dhcpc_exec_iptables --> off dhcpd_use_ldap --> off domain_can_mmap_files --> on domain_can_write_kmsg --> off domain_fd_use --> on domain_kernel_load_modules --> off entropyd_use_audio --> on exim_can_connect_db --> off exim_manage_user_files --> off exim_read_user_files --> off fcron_crond --> off fenced_can_network_connect --> off fenced_can_ssh --> off fips_mode --> on ftpd_anon_write --> off ftpd_connect_all_unreserved --> off ftpd_connect_db --> off ftpd_full_access --> off ftpd_use_cifs --> off ftpd_use_fusefs --> off ftpd_use_nfs --> off ftpd_use_passive_mode --> off ganesha_use_fusefs --> off git_cgi_enable_homedirs --> off git_cgi_use_cifs --> off git_cgi_use_nfs --> off git_session_bind_all_unreserved_ports --> off git_session_users --> off git_system_enable_homedirs --> off git_system_use_cifs --> off git_system_use_nfs --> off gitosis_can_sendmail --> off glance_api_can_network --> off glance_use_execmem --> off glance_use_fusefs --> off global_ssp --> off gluster_anon_write --> off gluster_export_all_ro --> off gluster_export_all_rw --> on gluster_use_execmem --> off gpg_web_anon_write --> off gssd_read_tmp --> on guest_exec_content --> on haproxy_connect_any --> off httpd_anon_write --> off httpd_builtin_scripting --> on httpd_can_check_spam --> off httpd_can_connect_ftp --> off httpd_can_connect_ldap --> off httpd_can_connect_mythtv --> off httpd_can_connect_zabbix --> off httpd_can_network_connect --> off httpd_can_network_connect_cobbler --> off httpd_can_network_connect_db --> off httpd_can_network_memcache --> off httpd_can_network_relay --> off httpd_can_sendmail --> off httpd_dbus_avahi --> off httpd_dbus_sssd --> off httpd_dontaudit_search_dirs --> off httpd_enable_cgi --> on httpd_enable_ftp_server --> off httpd_enable_homedirs --> off httpd_execmem --> off httpd_graceful_shutdown --> on httpd_manage_ipa --> off httpd_mod_auth_ntlm_winbind --> off httpd_mod_auth_pam --> off httpd_read_user_content --> off httpd_run_ipa --> off httpd_run_preupgrade --> off httpd_run_stickshift --> off httpd_serve_cobbler_files --> off httpd_setrlimit --> off httpd_ssi_exec --> off httpd_sys_script_anon_write --> off httpd_tmp_exec --> off httpd_tty_comm --> off httpd_unified --> off httpd_use_cifs --> off httpd_use_fusefs --> off httpd_use_gpg --> off httpd_use_nfs --> off httpd_use_openstack --> off httpd_use_sasl --> off httpd_verify_dns --> off icecast_use_any_tcp_ports --> off irc_use_any_tcp_ports --> off irssi_use_full_network --> off kdumpgui_run_bootloader --> off keepalived_connect_any --> off kerberos_enabled --> on ksmtuned_use_cifs --> off ksmtuned_use_nfs --> off logadm_exec_content --> on logging_syslogd_can_sendmail --> off logging_syslogd_run_nagios_plugins --> off logging_syslogd_use_tty --> on login_console_enabled --> on logrotate_read_inside_containers --> off logrotate_use_nfs --> off logwatch_can_network_connect_mail --> off lsmd_plugin_connect_any --> off mailman_use_fusefs --> off mcelog_client --> off mcelog_exec_scripts --> on mcelog_foreground --> off mcelog_server --> off minidlna_read_generic_user_content --> off mmap_low_allowed --> off mock_enable_homedirs --> off mount_anyfile --> on mozilla_plugin_bind_unreserved_ports --> off mozilla_plugin_can_network_connect --> off mozilla_plugin_use_bluejeans --> off mozilla_plugin_use_gps --> off mozilla_plugin_use_spice --> off mozilla_read_content --> off mpd_enable_homedirs --> off mpd_use_cifs --> off mpd_use_nfs --> off mplayer_execstack --> off mysql_connect_any --> off nagios_run_pnp4nagios --> off nagios_run_sudo --> off nagios_use_nfs --> off named_tcp_bind_http_port --> off named_write_master_zones --> off neutron_can_network --> off nfs_export_all_ro --> on nfs_export_all_rw --> on nfsd_anon_write --> off nis_enabled --> off nscd_use_shm --> on openshift_use_nfs --> off openvpn_can_network_connect --> on openvpn_enable_homedirs --> on openvpn_run_unconfined --> off pcp_bind_all_unreserved_ports --> off pcp_read_generic_logs --> off piranha_lvs_can_network_connect --> off polipo_connect_all_unreserved --> off polipo_session_bind_all_unreserved_ports --> off polipo_session_users --> off polipo_use_cifs --> off polipo_use_nfs --> off polyinstantiation_enabled --> off postfix_local_write_mail_spool --> on postgresql_can_rsync --> off postgresql_selinux_transmit_client_label --> off postgresql_selinux_unconfined_dbadm --> on postgresql_selinux_users_ddl --> on pppd_can_insmod --> off pppd_for_user --> off privoxy_connect_any --> on prosody_bind_http_port --> off puppetagent_manage_all_files --> off puppetmaster_use_db --> off racoon_read_shadow --> off radius_use_jit --> off redis_enable_notify --> off rpcd_use_fusefs --> off rsync_anon_write --> off rsync_client --> off rsync_export_all_ro --> off rsync_full_access --> off samba_create_home_dirs --> off samba_domain_controller --> off samba_enable_home_dirs --> off samba_export_all_ro --> off samba_export_all_rw --> off samba_load_libgfapi --> off samba_portmapper --> off samba_run_unconfined --> off samba_share_fusefs --> off samba_share_nfs --> off sanlock_enable_home_dirs --> off sanlock_use_fusefs --> off sanlock_use_nfs --> off sanlock_use_samba --> off saslauthd_read_shadow --> off secadm_exec_content --> on secure_mode --> off secure_mode_insmod --> off secure_mode_policyload --> off selinuxuser_direct_dri_enabled --> on selinuxuser_execheap --> off selinuxuser_execmod --> on selinuxuser_execstack --> on selinuxuser_mysql_connect_enabled --> off selinuxuser_ping --> on selinuxuser_postgresql_connect_enabled --> off selinuxuser_rw_noexattrfile --> on selinuxuser_share_music --> off selinuxuser_tcp_server --> off selinuxuser_udp_server --> off selinuxuser_use_ssh_chroot --> off sge_domain_can_network_connect --> off sge_use_nfs --> off smartmon_3ware --> off smbd_anon_write --> off spamassassin_can_network --> off spamd_enable_home_dirs --> on spamd_update_can_network --> off squid_connect_any --> on squid_use_tproxy --> off ssh_chroot_rw_homedirs --> off ssh_keysign --> off ssh_sysadm_login --> off staff_exec_content --> on staff_use_svirt --> off swift_can_network --> off sysadm_exec_content --> on telepathy_connect_all_ports --> off telepathy_tcp_connect_generic_network_ports --> on tftp_anon_write --> off tftp_home_dir --> off tmpreaper_use_cifs --> off tmpreaper_use_nfs --> off tmpreaper_use_samba --> off tomcat_can_network_connect_db --> off tomcat_read_rpm_db --> off tomcat_use_execmem --> off tor_bind_all_unreserved_ports --> off tor_can_network_relay --> off unconfined_chrome_sandbox_transition --> on unconfined_login --> on unconfined_mozilla_plugin_transition --> on unprivuser_use_svirt --> off use_ecryptfs_home_dirs --> off use_fusefs_home_dirs --> off use_lpd_server --> off use_nfs_home_dirs --> off use_samba_home_dirs --> off user_exec_content --> on varnishd_connect_any --> off virt_read_qemu_ga_data --> off virt_rw_qemu_ga_data --> off virt_sandbox_use_all_caps --> on virt_sandbox_use_audit --> on virt_sandbox_use_fusefs --> off virt_sandbox_use_mknod --> off virt_sandbox_use_netlink --> off virt_sandbox_use_sys_admin --> off virt_transition_userdomain --> off virt_use_comm --> off virt_use_execmem --> off virt_use_fusefs --> off virt_use_glusterd --> off virt_use_nfs --> on virt_use_rawip --> off virt_use_samba --> off virt_use_sanlock --> off virt_use_usb --> on virt_use_xserver --> off webadm_manage_user_files --> off webadm_read_user_files --> off wine_mmap_zero_ignore --> off xdm_bind_vnc_tcp_port --> off xdm_exec_bootloader --> off xdm_sysadm_login --> off xdm_write_home --> off xen_use_nfs --> off xend_run_blktap --> on xend_run_qemu --> on xguest_connect_network --> on xguest_exec_content --> on xguest_mount_media --> on xguest_use_bluetooth --> on xserver_clients_write_xshm --> off xserver_execmem --> off xserver_object_manager --> off zabbix_can_network --> off zabbix_run_sudo --> off zarafa_setrlimit --> off zebra_write_config --> off zoneminder_anon_write --> off zoneminder_run_sudo --> off
可以看到,selinux有非常多的布尔值,值为on或off。每一条都代表一个功能。
如果值为on,则表示启用对应功能,off表示不启用对应功能。
在没有selinux的情况下,我们要启用某功能,只要对这个功能进行配置即可。
但有了selinux后,除了配置,还需要让selinux同意开启这个功能。
2)selinux开启某个功能
例如ftp匿名用户上传文件到服务器,在服务器上如果开启了selinux,就需要设置这个功能的布尔值,让其为on。
setsebool ftpd_anon_write 1 setsebool ftpd_anon_write on
以上是临时生效的,如果要让其写到配置文件中,则加上"-P"选项:
setsebool -P ftpd_anon_write on
3)selinux关闭某个功能
setsebool ftpd_anon_write 0 setsebool ftpd_anon_write off
setsebool -P ftpd_anon_write off
7.selinux的一个配置工具
system-config-selinux
查看安装什么包,可以提供这个命令:
[root@centos7 ~]# yum whatp\rovides */system-config-selinux Loaded plugins: fastestmirror, langpacks Loading mirror speeds from cached hostfile * base: mirrors.aliyun.com * extras: mirrors.aliyun.com * updates: mirrors.aliyun.com base | 3.6 kB 00:00:00 docker-ce-stable | 3.5 kB 00:00:00 epel | 4.7 kB 00:00:00 extras | 2.9 kB 00:00:00 updates | 2.9 kB 00:00:00 (1/3): epel/x86_64/updateinfo | 1.0 MB 00:00:00 (2/3): epel/x86_64/primary_db | 6.8 MB 00:00:00 (3/3): epel/x86_64/group_gz | 95 kB 00:00:00 epel/x86_64/filelists_db | 11 MB 00:00:00 extras/7/x86_64/filelists_db | 217 kB 00:00:00 updates/7/x86_64/filelists_db | 4.5 MB 00:00:00 policycoreutils-gui-2.5-33.el7.x86_64 : SELinux configuration GUI Repo : base Matched from: Filename : /usr/bin/system-config-selinux Filename : /usr/share/system-config-selinux
安装policycoreutils-gui-2.5-33.el7.x86_64:
yum install policycoreutils-gui-2.5-33.el7.x86_64 -y
安装完后,确认selinux是启动的:
[root@centos7 ~]# getenforce
Enforcing
运行system-config-selinux:
system-config-selinux &
在图形界面里,可以进行enforce的设置,以及各种功能的布尔值设置。
8.修改端口的上下文(标签)
1)httpd监听端口808
我们知道httpd服务器默认监听的是80端口,如果我们想将其端口修改为808的话,开启selinux的情况下,只修改httpd的配置文件是无法成功修改的。
因为808端口的selinux标签(上下文)与httpd的上下文不匹配,也就是说httpd无法使用808端口。
我们要想httpd监听808端口,则需要修改808端口的上下文。
查看80端口的上下文:
[root@centos7 ~]# semanage port -l | grep '\b80\b' http_port_t tcp 80, 81, 443, 488, 8008, 8009, 8443, 9000
可以看到,80端口的上下文是 http_port_t 。
我们将808端口的上下文也设置为 http_port_t :
[root@centos7 ~]# semanage port -a -t http_port_t -p tcp 808
这样,httpd服务器就可以在配置文件中将监听端口修改为808,并且能够重启后生效。
2)sshd监听端口222
同上,sshd服务器也可以修改监听端口为222。
我们同样查看一下原本22端口的上下文:
[root@centos7 ~]# semanage port -l | grep '\b22\b' ssh_port_t tcp 22
可以看到上下文是ssh_port_t。
同样修改222的上下文为ssh_port_t:
[root@centos7 ~]# semanage port -a -t http_port_t -p tcp 222
===


